 In six regions (the slide in the lower right), in fact, the killing and the pattern of the killing were such that it constituted genocide.
In six regions (the slide in the lower right), in fact, the killing and the pattern of the killing were such that it constituted genocide.
This event took place on the sunny afternoon of July 14, 2001 during the DEF CON 9 conference in Las Vegas.
The session was conducted in a huge outdoor tent with woefully inadequate air conditioning.
The panelists were Dr. Patrick Ball, Greg Walton, and Drunken Master. Dr. Ball gave the keynote address. The affair was moderated by Reid Fleming.
Check out the mp3 version.
Reid Fleming: Welcome, everybody, to the cDc hacktivism panel. I've been asked by our sponsors to mention that coming up next is Jim Christy's Fed panel, so I guess that's for all the feds. And after that is Brian Glancey's "The Weakest Link".
Let me sort of explain how this is going to work and then you can decide whether or not you want to stay and watch it.
I'm Reid Fleming from the Cult of the Dead Cow. This is the panel about hacktivism. [light applause] (All my fans.)
We're pleased to present today's keynote speech and panel discussion entitled "Hacktivism and Human Rights: Using Technology to Raise the Bar".
The format is simple. There's going to be a speech; and then afterwards will be a panel discussion; and then tonight after 5:30 you can find us in the bar at the Hard Rock Hotel. You can talk to us about basically anything you hear here.
Patrick Ball: And buy our beers.
Reid Fleming: Yeah.
Our keynote speaker is Dr. Patrick Ball, Deputy Director of the Science and Human Rights Program with the American Association for the Advancement of Science, or AAAS. They are located in Washington, D.C.
AAAS examines how the progress of science impacts the well-being of people. The association facilitates communication among science, government and the public on a wide variety of topics that affect people around the world.
AAAS's Directorate for Science and Policy Programs is an authoritative source on research and development in the federal budget and explores a host of science and technology issues that face Congress. It works to ensure research competitiveness and high ethical standards and encourages a dialogue on science, ethics and religion. Its Science and Human Rights Program helps guarantee human rights worldwide.
The AAAS Science and Human Rights Program was established in 1976 to give scientists a way to help their colleagues around the world whose human rights are threatened or violated.
Mobilizing effective assistance to protect the human rights of scientists around the world remains central to its mission, as well as making the tools and knowledge of science available to benefit the field of human rights.
Since 1991, Dr. Ball has designed information management systems, provided training on the use of cryptographic tools, and conducted quantitative analysis for large-scale human rights projects for truth commissions, non-governmental organizations, tribunals and United Nations missions in El Salvador, Ethiopia, Guatemala, Haiti, South Africa, Kosovo and Sri Lanka.
AAAS has published three books by Dr. Ball:
I give you Dr. Patrick Ball.
[applause]
Patrick Ball: Thanks a lot. It's really cool to hear yourself introduced.
I want to be very clear how thankful I am to the cDc for inviting me to give this talk. I hadn't thought of what I do as hacktivism, but as I talk to these guys I realize that what we do is incredibly similar. What I do and what they do, they're very similar in a lot of different ways. I found that similarity very exciting, and I hope I can share some of that excitement with you today.
As Reid said, we apply science and technology to human rights. We take a broad view of what science is. What people in this room do, we would count as science. So at least for this afternoon or for the next 30 minutes, think of yourself as a scientist, as someone who applies a systematic and rational approach to solving a problem, to figuring something out, to discovering something.
And with that, let me talk a little bit about what I think hacking is. I think hacking is finding things out. It is discovery, especially when the knowledge you're looking for is hidden, obscure, and important.
Hidden, obscure, and important.
When governments commit mass killings, when they commit a program of ethnic cleansing, drive hundreds of thousands of people from their homea, when they detain arbitrarily thousands or tens of thousands of people, when they commit torture over a period of years or decades... this is not knowledge that they wish for others to know about.
For hundreds of years, the Quakers have had an idea of speaking truth to power. It's a very strong idea. It's an idea that has brought repressive regimes down over periods of time when people have continuously, tirelessly, and truthfully speak truth to power.
I think we can agree it's a valuable idea, but it's not always as easy as one might think to figure out what the truth is.
It might be easy enough to say "Oh yeah, that guy was killed, and he was killed by the government." The government, I assure you, when you make that claim will dismiss it: "well, he wasn't really killed" or "he was killed in a crossfire" or "the agents involved were rogues and we've sanctioned them."
But if you can demonstrate that not just that guy was killed, but 10,000 other people were killed just like him, then you'll speak truth to power in a way that power will be unable to deny.
The only way you can aggregate that much information is with technology.
I won't explain these slides, I'll point you to the URL. But I can say that these slides are a way of speaking truth to power. And so are these.
Hacktivism is finding ways to speak truth to power using technology in this way. It's technology or hacking in the service of human rights, or civil liberties, or the environment.
When the truth commission in Guatemala was able to conclude that we find that more than 200,000 were killed during the armed internal conflict, more than 93% were people killed by the government. The army of Guatemala can no longer deny that this occurred, because the basis on which we made this claim was defensible on scientific grounds.
There's no more pretending that this didn't happen, or that it was a few violations, or that violations were committed equally by the government and by the agents of the insurgency. No. Now, in fact, we have some scientific data that allow us to say, "This happened." It can't be denied.
 In six regions (the slide in the lower right), in fact, the killing and the pattern of the killing were such that it constituted genocide.
In six regions (the slide in the lower right), in fact, the killing and the pattern of the killing were such that it constituted genocide.
What I'm going to talk about today, briefly, is: What are human rights? What do we mean by them? Human rights are not just good ideas. How does information technology help human rights work?
I'll talk a little bit about the use of massive data and information systems. I'll talk about cryptography. And I'll talk about distributed web-based databases.
And finally, I'll talk about why I decided to come out here and sit in this breathtakingly hot tent. Does anyone else in here feel that their natural home environment is a server room that's about 45 degrees colder than in here? [cheers and applause]
And I'll say what you can do. It turns out that there's an awful lot that people in this room can do. The fact that you've come to this conference means you have certain interests, and I think that those interests mean you have certain skills. And if you have those skills, I'd like to get email from you. I'd rather not see you have root on my machine, if that's all right. [laughter]
Human rights are defined in international law. In 1948, after the Holocaust in Europe, after the Nazi atrocities, the world said to itself, "We needed some way of saying this was wrong."
People said during the Holocaust that it was wrong, but no one had the right under international law to say that the Nazi government could not do what it did, because they had this bad idea called sovereignty. Sovereignty means that governments can do what they want and other governments can't say anything about it.
So in 1948, governments said sovereignty has a limit, and that limit is defined by certain rights that everyone has. You do not have the right to do anything you want, but you do have certain rights. And these are the rights defined as goals for international law in the Universal Declaration of Human Rights, which essentially all governments of the world agreed to in 1948, with some rather sad exceptions.
In the years that followed, these ideas, these goals were given the force of international law. This law is codified in two covenants: the Covenant on Civil and Political Rights, and the Covenant on Economic, Social, and Cultural Rights. These were ratified and came into force in 1976. "Coming into force" means they have the force of international law.
Governments that are party to these agreements may not violate these rights without being in the wrong. You may say, "So what? So what if they're in the wrong?"
Well, it turns out that being in the wrong is the basis on which other governments bring pressure to bear on them. Other governments don't want to have diplomatic relations with them. Other governments don't want to trade with them. Other governments don't want to have cultural and sports missions with them.
This may sound light, but when I was working in South Africa in 1996-1998, the South Africans told me that the thing that hit them hardest was that they couldn't have other sports team come play with them. This erodes the fabric of what it means to live in a nice place. We all want to live in a nice place.
So when the things that make a place nice are taken away, regular citizens start to say, "Wait, wait. This isn't okay."
Those little bits of pressure come to bear, they aggregate across all sorts of different arenas, and they pressure bad governments to behave better.
Of course, now, on the basis of crimes of war we have tribunals. Tribunals which try people who have violated international humanitarian law and send them to prison. It would be very nice if we had a round of applause for the extradition of Slobodan Milosevic to the Hague last week. [applause] And I hope you're all excited as I am by the prospect of his very pleasant and drawn-out trial, which will begin in about six months.
The Convention Against Genocide is the strongest of all international humanitarian law. It means that no government can decide because they don't like some group because of its ethnicity, its religion, its race, its color, its ideas even... it means that they cannot target that group for elimination.
It's a strong idea. It may sound obvious, but it was only ratified in 1948, and we've only had two findings under international law that genocide has been committed. (It doesn't mean that only two times it's occurred, it's only that officially constituted bodies have made legal findings that genocide happened twice.)
Making a finding about genocide is making a finding about policy. If you want to say that something has happened as a question of policy, you need an awful lot of data. An awful lot of data.
And to get that much data in one place and to do something about it, you need a lot of technology.
When we build these mechanisms for pressure, we use standards. We use the standards of international law.
The pressure comes from public groups, like the United Nations missions. It comes from big international human rights groups, like Amnesty International or Human Rights Watch. But, more than anything, it comes from tiny grassroots groups on what I call the cold face.
It comes from the groups that look the police who do disappearances in the eye. It comes from people who go to the police stations and say, "Do you have this guy? Could we have him back before you disappear him, please?"
There are more than 8,500 of these groups worldwide, and they desperately need a lot more technology. I'll tell you about the technology that they need and the ways we've applied technology in a few of these cases, over the course of the next 20 minutes.
For this pressure to be effective, it's much more important that it be focused than that it be massive. This is an important understanding. If we say: "Oh, you know the government of (to pick a case out of the air) Burma has done some terrible things. I know -- let's set up a website where people can mailbomb different instances of the government of Burma, say their embassies in various countries." And people write hate mail in email to the government of Burma... they're just going to put up a spam filter.
That's not going to mean anything because they'll realize because of the unfocused nature of the action, the government of Burma will quickly realize that the people sending this email don't really know what they're talking about. And they aren't going to be committed to a long-term pressure campaign against the government.
Human rights groups that do mass advocacy have very carefully planned strategies. They know exactly who in the government might be receptive. They understand if there are reformist elements that can undermine the hardliners and ultimately force them out of power. They know how to turn a campaign on and then turn it off if the government does what you want.
So I would urge you in your human rights work, if you decide to participate in these kinds of direct actions, please do so in networks of professional human rights groups. Don't create your own networks. These people have been doing it a long time and they know what works, and more importantly, they know what doesn't work.
So go to Amnesty. I'll put the URL up later. There's a lot more you can do, and I'll talk about that.
Why do we build databases?
 A little human rights group in Guatemala, the International Center for Human Rights Research (CIIDH), between 1991 and 1997 built a database of only 65 megabytes of data. That takes an awful lot of work. That's more than 19,000 cases. That's more than 45,000 individual violations. That's a lot of dead trees.
A little human rights group in Guatemala, the International Center for Human Rights Research (CIIDH), between 1991 and 1997 built a database of only 65 megabytes of data. That takes an awful lot of work. That's more than 19,000 cases. That's more than 45,000 individual violations. That's a lot of dead trees.
If you guys see all that paper up on the wall, those are the coding forms and the interview documents that we went out in the field and took. More than 100 people worked for five years to take these interviews.
The database was densely relational and had 40 tables. We ran it under FoxPro for DOS on Toshiba 386 monochrome laptops. We put the data all together, we encrypted it using PGP and PKZIP and wiped every night.
We aggregated it all on a single machine using sneakernet, people bringing things over. Ungodly amounts of FoxPro code to insure the relational integrity. (It didn't work that well, I admit. I wrote it.) [laughter]
But the encryption worked. A laptop went missing during the process, and as far as we know there was no data leakage. That's a lot of discipline, folks. And it's a lot of pushing hard to do crypto on platform like this.
About a year and a half ago, Carl Ellison (a cryptographer at Intel, a great guy) formulated what I call Ellison's Law, which states that the userbase for strong cryptography declines by half with every additional keystroke or mouseclick required to make it work. Think about that when you're designing tools.
When we put together a lot of statistics, we get big pictures. We see the large profile, we see when things happen.
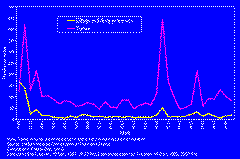 Here's a graph from Haiti pointing out that during the de facto regime, there was a huge spike in October of 1993. Anybody who can remember back that far (I can only remember it because I've had this slide in a couple of my talks) remember that the Clinton administration was threatening intervention and the paramilitaries on the street turned up the pressure. They turned up the pressure by grabbing folks off the street and torturing them, killing them.
Here's a graph from Haiti pointing out that during the de facto regime, there was a huge spike in October of 1993. Anybody who can remember back that far (I can only remember it because I've had this slide in a couple of my talks) remember that the Clinton administration was threatening intervention and the paramilitaries on the street turned up the pressure. They turned up the pressure by grabbing folks off the street and torturing them, killing them.
You learn two things from this slide, by looking at patterns. One, that there is this (unsurprising, perhaps) coincidence between a huge spike in the amount of political violence correlated to some political event. We also learn that types of violence move together. The little yellow line at the bottom spikes at the same time as the purple line at the top. Killings go up at the same time as torture.
Why would that happen? It happens because they respond to the same cause. They're coordinated. It's policy.
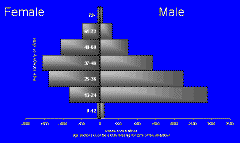 Similarly, if we look at the demographic structure of people who suffer a particular kind of violence in South Africa, we find a structure. We find a structure that's different for men and for women who are victims of this violation. Men are younger than women who suffer this violation. Buy me a beer and I'll tell you why.
Similarly, if we look at the demographic structure of people who suffer a particular kind of violence in South Africa, we find a structure. We find a structure that's different for men and for women who are victims of this violation. Men are younger than women who suffer this violation. Buy me a beer and I'll tell you why.
 These are some projects I won't talk about. It would take too much time and I don't want information overload. The reason I put this slide up is to show how widespread this practice is.
These are some projects I won't talk about. It would take too much time and I don't want information overload. The reason I put this slide up is to show how widespread this practice is.
We're doing statistics all over the place, the truth commission in Haiti, we're doing it in a little NGO project in Guatemala, in the truth commission in South Africa, in the truth commission in Guatemala, and now in Kosovo. Recently also in Sri Lanka. We've got projects going in East Timor, in a couple of different countries in West Africa.
Stuff is happening.
The reason that this is important for you guys is that just means there's that much more data for people to take away from us. So let's think about ways that we can aggregate data more safely.
Building tools like Bastille. I appreciate it from this morning. Hey, I've got Bastille on my machine, that means none of you guys is going to hack it, right? [laughter] Right, just checking.
I'm going to go into detail on the first project that I did, the nongovernment human rights commission in El Salvador. I worked there in 1991-1992.
This work took over 9,000 testimonies, from 1977 to 1991. 9,000 people they sat down with and listened to as they told stories about watching people getting killed in front of them, or their children being taken away and never returned.
They did legal work on most of these cases. There are more than 17,000 documented in these testimonies, more than 29,000 violations.
We put the data together in an incredibly simple format.
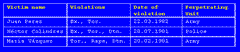 This little flat (it wasn't flat, but for the case of this example, I'll call it flat)... this little flat table, where we had the victim's name in one column, a list of the violations that they suffered in the second column (actually, an array), the date of the violation, and the perpetrating unit.
This little flat (it wasn't flat, but for the case of this example, I'll call it flat)... this little flat table, where we had the victim's name in one column, a list of the violations that they suffered in the second column (actually, an array), the date of the violation, and the perpetrating unit.
Okay, it's a flat structure. If these things occurred on different days I had to repeat the record. If there were multiple perpetrators, I had to repeat the record. Let's leave that aside for the purposes of this invented example.
So we see that Juan Perez was tortured and executed on the 22nd of March 1982, and the witnesses allege it to have been done by the army. And on, and on, and on for 17,000 records.
 Well, we also collected the career histories of individual military officers. For example, we found that Hernán Galindo (this is invented, there is no Hernán Galindo in the army in El Salvador) was a colonel, and from the 2nd of August until the 31st of December 1983, he was commander of the army.
Well, we also collected the career histories of individual military officers. For example, we found that Hernán Galindo (this is invented, there is no Hernán Galindo in the army in El Salvador) was a colonel, and from the 2nd of August until the 31st of December 1983, he was commander of the army.
In fact, we had over 40 different units that we looked at. We had 14,000 of these segments of career structure. And we see on the third record that Hernán Galindo we also know commanded the police for a period before he commanded the army. And on, and on for 14,000 segments.
Anyone in here ever written a SQL statement? You know what's coming, right? It's a JOIN. It's a big JOIN. It's a really big JOIN, and the point of this JOIN is to develop an individual statistical dossier on every one of these officers.
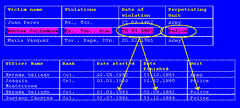 So we link the execution, torture, and detention of Héctor Colindres with the career segment of Hernán Galindo, thereby attributing these violations to Colonel Galindo at this point in his career.
So we link the execution, torture, and detention of Héctor Colindres with the career segment of Hernán Galindo, thereby attributing these violations to Colonel Galindo at this point in his career.
 This converts into a table that says that, for example, Rogelío Acevedo Palacios was responsible for 17 arbitrary executions (the first column), 44 forced disappearances (the second column), 86 cases of torture. No massacres, but 225 involuntary disappearances. (There's two categories of disappearance under Salvadoran law. Again, buying a beer tells you why.)
This converts into a table that says that, for example, Rogelío Acevedo Palacios was responsible for 17 arbitrary executions (the first column), 44 forced disappearances (the second column), 86 cases of torture. No massacres, but 225 involuntary disappearances. (There's two categories of disappearance under Salvadoran law. Again, buying a beer tells you why.)
If you go on and on looking through this statistical structure, what jumps out at you as your eye scans is that most of these guys are not involved in that much stuff.
But look at Juan Alcides Aviles. He jumps out at you. We allege him to have been responsible for 222 arbitrary executions, 91 cases of forced disappearance, 149 cases of torture, five massacres, and on and on.
So when we looked across this list of officers, we determined that about 100 of them were really bad guys, who've been into it really deeply. We passed the statistical findings into two structures set up by the negotiations that ended the war in 1991. These two structures have the power to force guys into retirement. They took our list as the basis for the list of people that they took out of the army. We didn't get them sent to prison, but we got them taken out of positions of power. That's a big step. [applause]
We published the tables in a newspaper, we put pictures of these guys on posters with a statistical summary underneath them, with some very simple text explaining what the tables meant and we wheatpasted them all over San Salvador.
I left the country, I came back home. But I've been back since, and now one of these guys that we nailed has got a talk show with one of the guerrilla generals. And sometimes he makes jokes about how he doesn't know how we did our statistics. But in fact, he does know because they sued us for defamation after we published these results. If it had been a few years earlier, of course, they would have just killed us all. But because it was after the peace process, they sued us.
So we went into court with what lawyers go into court with. That is, dozens of cases of paper. But we also went in with diskettes with my code, and we gave it to the judge and said "Here's how it was done." The judge looked at the code (he didn't read the code, but he figured, he said to the officers with whom he'd been in bed for years, he said, "you know you guys, if you guys had technicians review this stuff, what if they're right? You want to go to court and have them proved right?" And they backed off.
They backed off and withdrew their suits. That's the news that people remember now. That's the news they remember.
The reason it worked? Big data. Technology is why it worked.
If we'd gone with a few cases like lawyers always do, they would have been able to come up with a few cases that went the other way. And then we'd come up with a few more, and then they'd come up with a few more... We're talking about tens of thousands of violations. You'd never exhaust even a tiny fraction of the universe that way.
You need to have the big picture. The point is, we were able to target. We were able to be focused. All the officers were implicated in something, sure. But who was really involved, who just peripherally?
To make that decision, our choices about which officers were targeted, was a fair decision, a scientific decision, a technological decision, not a political one... we had to look at all of them and discard the ones who were not so deeply implicated.
Only large-scale methods, big data, big technology, allows us to do that.
I'll move on to cryptography. It may be obvious to you that human rights groups have a lot of sensitive data. And in fact, we had stuff like the addresses of witnesses.
From: pball@aaas.org
To: HRC-Elmville@human.rights.org
Subject: the Smith murder case
Date sent: Mon, 21 Oct 1996 11:02:17
Thanks for the information. According to our files, the most important
witnesses in the case are Betty Smith and Jane Jones. You can contact Betty at
her home, 123 North State Street. She usually comes home around 5pm. Sometimes
Betty stays with her mother at 345 Main Street, apartment 6. Be sure to keep
this information confidential!
And then send it in cleartext? Obviously not.
You can see the date on this. I've been giving this particular slide for a long time. Human rights group get it. Not as much as they should, but many groups use PGP.
If you guys are going to applaud, applaud for Phil Zimmerman. PGP has had an enormously positive impact on the human rights community. [applause] In spite of various weaknesses (and God knows I'm sick of the command line), for all its weaknesses it's done a lot of good for us and we need to keep pushing that technology.
We're also vulnerable to spoofing. What would happen if somebody posted a message that appears to come from Human Rights Watch saying
From: hrwatchnyc@igc.apc.org
To: hrw-news@igc.apc.org
Subject: China -- HRW announces end to human rights violations
Date sent: 8/1/97
(August 1, 1997, NY) -- Human Rights Watch today announced that Iraq no longer
violates any internationally-recognized human rights. "According to our
investigations, the Iraqi government has released all political prisoners,
ceased torturing all detainees, has closed forced-labor production, and now
permits the full exercise of rights to free speech, religion, assembly, and
association," reported Bill Smith, Human Rights Watch Deputy General Counsel.
"The time for criticism is past. Now let's accentuate the positive. Let's stop
being whiners."
I would hope that people would recognize that this is a spoof, but hope is not enough to stake your legitimacy on. Reputation is as important to us as it is to you.
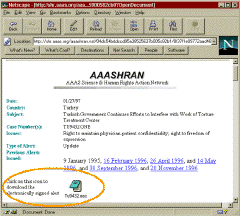 So serious human rights groups include digital signatures with their messages now. They may not distribute the messages with digital signatures on them (largely because sending digital signatures in cleartext messages get mangled, so you get a lot of false rejections), but they put them on their websites so that you can download a digitally-signed version and verify that in fact this came from the group that it claims to have come from.
So serious human rights groups include digital signatures with their messages now. They may not distribute the messages with digital signatures on them (largely because sending digital signatures in cleartext messages get mangled, so you get a lot of false rejections), but they put them on their websites so that you can download a digitally-signed version and verify that in fact this came from the group that it claims to have come from.
At my group, when we send out urgent actions about scientists, we put everything up with our signature. We've never had a spoof, but many other groups have. We may just be too small to bother with.
Let me go on to one more example. This is the Martus Project.
Most of what human rights groups do is text. I wish that we had more structured data so that I had more examples of the first kind. (And I wish that there were more groups using crypto.) But most of what human rights groups do is text.
Somebody comes into your organization, they say "I want to tell you a story. I want to tell you a story about something that happened that I saw. And here comes my story, blah blah blah." That's their story.
A good human rights group writes it down. They usually write it down on paper. In fact, a group that I'm working with in Sri Lanka right now wrote down 3,000 stories on paper, and these stories were then eaten by termites. So paper's not a good place to put a story.
Paper's not a good place to put a story (as I showed in the first slide) if you're looking for something that's in any of those stories, because very soon after you start taking things on paper, you have tens of thousands of pages. It's not a useful searching mechanism, paper.
What you need is some sort of information management system. So what groups do is, they type it all into Word files. Well, it's not eaten by termites, but the searching capability is not much greater.
What we really need is a way to prevent them from losing all that data when their hard disks crash, or their offices blow up, or their CPUs go missing (either because of theft or because of some sort of attack).
Or because somebody just saves a new file with the same name. These are not technologically sophisticated people. What happens? Well, people lose data. Has anyone here worked in an office where people lost data, just because they didn't know well enough? All right, you may have some sense of the scale of the problem.
What we need is some way to take lightly-fielded text data, encrypt it locally (in case a CPU goes missing), replicate that data through encrypted channels to servers in remote locations, so that if the local machines are attacked, the faraway machines are safe.
And then maybe we can add a little value and put up a public interface to those servers so that information the groups want to make public can be searchable through some sort of relatively simple web interface.
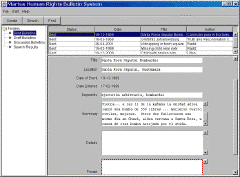 Check out http://www.martus.org/. Here's what the client looks like:
Check out http://www.martus.org/. Here's what the client looks like:
We're in very early development. The client, I think at this point, shows that screen and right after that it crashes. [laughter] But we're working on it, and when it works it will be GPL'd, it will have a SourceForge home, and it will be cross-platform. We're going to write it once and debug it everywhere. [laughter]
We are hoping for some help on that debugging. Maybe there are people in here who write in Java. So watch for that. We're looking at the end of the year, we hope to have that out.
We hope that this solution will solve many of those problems. We've gone to human rights groups in Cambodia, Sri Lanka, Guatemala and demoed it. We said, "Hey, if we write it, would you use it?" They were like, "You demoed it, so it must work. Can we have it?" So we had to explain what a demo is. [laughter] That was a lot of fun.
What is to be done, folks? What can you guys do?
Let me say that I think that everyone in here who has ever called himself or herself a geek, the first thing you should do is support your own community.
There are terrific, terrific civil liberties groups in your community, day in and day out, doing important work.
That includes the Electronic Privacy Information Center, the Electronic Frontier Foundation, the Center for Democracy and Technology, and Computer Professionals for Social Responsibility.
These folks are terrific, they deserve your support. Read their stuff. You should send them money, you should be in touch with what they're up to.
But we can get a little bit more focused.
$geek{you} = [
join => http://www.aiusa.org,
read => http://www.hrw.org
http://shr.aaas.org
] ;
(Sorry. Once I used the double arrow, I couldn't help myself.)
There's more stuff you can do, more in the human rights line. You can join Amnesty and write one letter a month. You're not doing this for Amnesty; it helps you. It helps you to think about what human rights means.
It's not an abstraction, it's about somebody in prison being tortured. Think about that person for 20 minutes while you write a letter or fax or an email. Think about it, just for 20 minutes. I'm not asking for much; join Amnesty.
Read the Human Rights Watch site. Read my site at http://shr.aaas.org/. Keep in touch with that people are doing.
People may have seen in the news recently (NPR and even the New York Times covered it) that a sociologist in Egypt was put in prison for seven years because he wrote a scientific report in which he claimed that certain things was doing weren't working.
Hello? What if he'd written a piece of code they didn't like? How much closer to home does it have to come?
So let's stay in touch, let's stay in touch with that stuff. But you're just warming up when you do that. Let's get to what you do.
You can write code. You can write code that promotes privacy.
You can make utilities that hack the embedded ID numbers out of things that embed them. That's a bad thing for human rights groups. Any document structure that embeds an ID number in it, destroys the anonymity of our ability to produce that document. Write us a utility that shreds that but retains the integrity of the document.
We can't stop every human rights group in the world from using Word, that's not a realistic goal. They're going to use Word. But we can make that a little less devastating for a lot of these data leakage issues.
You can support version one of privacy services. Not necessarily because they work, but because if we don't support version one we'll never get version two.
We can build, we can port, we can contribute to, we can review and bugfix existing freedom-supporting software. I'm not going to give you a list of freedom-supporting software; you decide what you think that means. (I think the cDc guys may have some ideas.)
Let's keep going. Support free and open-source software. Free the DOC format. Give me a translator that works every time. Some of our DOC files are really complicated legal documents, and even the best translators break on those.
Remember that human rights folks (and other people protecting their privacy) are users. They're not geeks. If your mom can't use the software, we can't either. [laughter] So keep that in mind as your reference point.
Finally... maybe you could do me a favor or two?
Is there anyone in here who's really good at PostScript and would want to write me a little PERL? I've got a really interesting little hack.
And finally, is there anyone in here who really knows his or her way though XFree86 4.1 and an ATI card under Redhat 7.1? I've got a problem, and it's so far defeated Linuxcare. Maybe somebody in here can help me out.
Anyway, thanks a lot for your tolerance. I hope this really gets you excited.
[ovation]
Reid Fleming: Thank you, Dr. Patrick Ball.
Now it's time to throw popsicles into the audience [loud commotion] and also introduce the other two members of our panel. Next to Dr. Ball is... [loud commotion continues] I'll try that again.
Sitting next to Dr. Ball is Greg Walton, who is a human rights researcher working with the Canadian human rights group Rights and Democracy. http://www.ichrdd.ca/ He lives in Dharamsala, India.
And sitting on the end is Drunken Master: member of Hacktivismo, and technical lead for the upcoming product Peekabooty.
[applause]
I think the first question I want to start out with is... I noticed in the discussions we've had before this panel about what we consider hacktivism... I think the main thing is, we want to straighten out what it isn't, in that it isn't any sort of cyberterrorism or disabling computers or trying to make things harder for a repressive regime by taking down their webserver. Does anyone disagree with that?
Greg Walton: I think it's important to make that clear right from the start. That we're not talking about cyberterrorism, we're not talking about information warfare, we're not talking about taking down the Chinese backbone. We're talking about more constructive, positive ways of dealing with human rights abusers. I think that's something we all agreed on, straight away.
Reid Fleming: We passed out copies of the Hacktivismo Declaration, and hopefully most people have seen it (or at least looked at the art). What do you guys think about the Hacktivismo Declaration?
Drunken Master: Well, I'm part of the group that actually wrote it, so I think it's great. [laughter] It's basically our founding declaration. Various countries around the world have signed these two documents that are mentioned in the declaration, saying that everyone has the right to their own opinions, to view whatever documents out there that they want. Even though a lot of countries have signed that, they don't uphold it.
The program that I'm the technical lead on is called Peekabooty and it's basically going to route around any censorship.
Greg Walton: I think that one of the interesting things about this declaration is that it's come from the Cult of the Dead Cow, and it's in the language of a human rights group. When I was explaining Peekabooty to some of the human rights that I work with, they were like "Wow, that's incredible. That would really change a lot. Who made it?" "Cult of the Dead Cow." And they'd be like, "What? Cult of the Dead Cow?" [laughter] They know nothing about hacking.
All they've heard about them is a few media reports from Defcon: Cult of the Dead Cow... alien anal probe... stage shows... [laughter]
There's a big gulf between the hacking and human rights communities. There's a lack of understanding about a lot of things. One of the things that impressed the human rights groups that read it is that it was so professional. Written in their language, something they can understand, something really very reasonable.
Patrick Ball: I think it's really valuable that you guys read this document. Let me tell you why I think that is. I agree with what Greg said. My first reaction was "Cult of the Dead Cow, what's this?" I read it and it's really balanced, it's really thoughtful, it really gets at what the balances are and the tradeoffs in international human rights law.
When we get an international instrument established, we have to get governments like Saudi Arabia to agree to it. Now, Saudi Arabia in fact hasn't agreed to a bunch of them. But we do have to get two-thirds of the countries in the United Nations to sign on before something becomes really useful.
To do that... it's politics, guys. We're horse-trading. There's a lot of stuff in international instruments that maybe isn't as strong as everyone in this room would like, certainly not as strong as I'd like. But that's the way it is. We use what we've gotten before and we keep pushing.
This document gets it. When you read this document, look at the carefulness of the language.
Look at the very clear things that it grants to governments. It's not saying "Government can never look at anything of mine ever." Frankly, that's just not the way international law is. If you've got kiddie porn on your disk, you're hosed.
What we have to do is think about this in balanced terms. If we want not only the international human rights groups to get it... Greg has said they're going to read it, they are going to get it, they're going to like it, they're going to work for it. When we're talking about human rights, let's remember that human rights is not the right to everything we want.
Let's work with those rights, and then push them. If you want more, let's keep pushing, absolutely. Keep going. No reason to stop now, we've got some momentum. We've got one of the worst badguys ever in jail (at least in my lifetime).
Let's go with it. This is a great document.
Reid Fleming: I only had one more thing, and then maybe we'll open it up to a couple of quick questions. We were talking before, and it seems to me that if the choice were between giving $50 to a human rights organization or instead donating an hour of PERL scripting, that the PERL scripting would be worth way more than $50. You couldn't buy an hour's worth of PERL scripting for $50. [applause] The beauty of this is you could actually help one of these groups without ever leaving your bedroom. [laughter] They could ask you to do something, you could send them the script, it would be entirely by email.
Patrick Ball: I totally agree with that. In fact, I'm pleading and begging for scripts myself.
It's true that you can help human rights groups without leaving your bedroom, and I think that's terrific, and I'm not suggesting necessarily that you should leave your bedroom. But I do think we should leave the world of PERL scripting for twenty minutes a month. I think you should engage this idea.
If this talk has engaged you a little bit today, if hearing me talk about ways to respond to mass killing, to mass detention, to ethnic cleansing, and to torture, if that rings a bell for you, stay engaged.
Writing a letter for Amnesty every month is not just about that guy in jail that you're writing about. It's about you. It's about you understanding what's going, keeping your enthusiasm up, keeping your solidarity going, keeping your focus on what the world's about clear.
So do that for yourself. And, by the way, it may help Amnesty. And it may help that guy in jail. [applause]
Deth Vegetable: I'm Deth Veggie of cDc, for those of you who don't know me. We wanted to see if anyone had any questions. We have about ten minutes for questions. Anyone? You in the front.
Audience Member: Are you concerned that hackers, if they take on a more active role in political campaigns around the world, will become targets of hostile governments? And what will you do to prevent that?
Drunken Master: Maybe no more than we already are. I don't think so. We use aliases, we know how to keep ourselves secret.
Patrick Ball: It's also worthwhile to think about who the hostile governments actually are. What kind of reach does a hostile government have into wherever it is that you actually live? Sometimes, that may be very significant.
During the 1980s, we learned over and over again as the FBI trashed our offices that people who opposed the US support of the war in El Salvador were targets, and we got nailed. If there had been hackers helping us out back then, I'm sure you guys would have been targets too.
So sometimes you are going to be targets. Watch yourselves. Use anonymity. You know how to use these tools. You wrote them.
That's one thing. On the other hand, be strategic. Think about what you're doing.
Greg Walton: I think that's very important to do, and to do it very well. But it's an occupational hazard, I think, if you're going to get involved with taking on repressive regimes. It could be a danger.
Deth Vegetable: Anyone else?
Audience Member: Hi, are you planning on making localized language versions of your Martus software? And if so, what languages?
Patrick Ball: Actually, the demo runs now in English and Spanish. That's just because it was really easy for me to translate it to Spanish.
Our current target languages include Khmer, Tamil, and Sinhala. Those are harder because they're different character sets, and so far not all of them are Unicode. So there's going to be some struggle there. But we're definitely committed to a Unicode solution.
Audience Member: Could you tell us more about Peekabooty and the ways that it will assist people in a country like China to get access to information?
Drunken Master: Well, I can't talk about the technical details, but I can say that anyone around the world should be able to use it. It will be small and able to run on hardware that's five years old.
Audience Member: I was just wondering if you could repeat the name of the website where you can get more information about Martus?
Patrick Ball: http://www.martus.org/ [laughter] So other people know, Martus is the Greek word for "witness". Hence the name.
Audience Member: This is mainly for the people making Peekabooty. You're using sort of a P2P network doing this thing, right?
Drunken Master: Yes.
Audience Member: Okay. I know a few groups who are really concerned about the plausibility of using a peer-to-peer network for anticensorship. I've talked to a lot of people from Yak.net and Peacefire. They're a little bit skeptical. Will there be any specifications released for open comment?
Drunken Master: It's going to be open source, yes. And all of our documentation will be released when that happens.
Audience Member: But beforehand? If you don't do it right the first time, you have potentially people's lives on the line.
Drunken Master: We can't really discuss it too much.
Greg Walton: One thing we can say for sure: it's not being released today. It's gone back to the drawing board. Why? Because if people could lose their lives because of it... It's got to work. It's not a word processor.
I've heard about some of these concerns. I've read some great critiques of the idea by people like Yak.net, but on the other hand, I think some of those concerns --
Drunken Master: We do have people from security firms reviewing it. We have designed in safeguards to keep people safe.
Audience Member: I think the concern that the last questioner was bringing up is that not having it open source before its release doesn't put it out for peer review. So you can run into the problem that once it gets out there, it's like, say, some large company whose initials are "Microsoft" does. It gets out there and suddenly you find out that it has lots of holes in it because it hasn't had the peer review.
Drunken Master: That's a good point, but we will have time to test this obviously.
Reid Fleming: I think the other thing is, we are talking about having it peer reviewed, but it may not be open for public review.
Drunken Master: Once it's released, there's going to be an arms race. When we release it, everyone gets it all at once, the goodguys and the badguys. After that, it's going to be a race to see who can block the other faster.
Audience Member: While I really admire the way that a lot of these groups speak truth to power and take the people out of power, take away their guns who violate human rights, we all know that nothing hates a vacuum more than power. I'd like you to address what some of your efforts are to keep groups (multinational corporations, governments) from exploiting the lack of leadership in some of these countries where you take down the leadership. [applause]
Patrick Ball: I think "taking down the leadership" is a little strong. We don't usually bring governments down. Usually we're able to pull out some of the worst guys and maybe effect some structural reforms.
But I think that's really an interesting question, and it's a question that the whole human rights community has been grappling with for about ten years, since we actually having an impact.
At the grassroots, what most groups end up doing after there's some significant transition... the groups lose a lot of their mandate. "What were you doing?" "Well God, we were all really busy documenting political killings when there were dozens a month. Now that there's only one or two a month, what do we do?"
What we do is democratization projects. Democratization projects have a wide variety of mechanisms and a wider variety of effectiveness. Most of them don't have much effectiveness at all, I think.
The point is to figure out how we can use the networks of people that have been built to build a meaningful grassroots political party structures to express yourself in democratic transitions and in a democracy. Build effective citizenship training programs.
In a country coming out of a dictatorship, nobody knows what it means to be the citizen of a democracy. In order for democracies to work, citizens have to know that they can participate, and there are ways to do it, and here's how you do it, and here's how you have input.
A lot of human rights group in this transition (in particular, I'm thinking of Central American groups because those are the cases I know best in the post-transition) work on these democratization projects.
I think what is -- I'll say ironic -- is that a lot of the funding for democratization projects comes from USAID. But USAID has been a really big player in Central America, promoting democratization and some of the projects work.
There are in fact all sorts of ways that people in really low-resource communities are able to express themselves politically and bring pressure to bear and protect civil rights, which are stronger in a democracy and often more relevant than the human rights issues were ever before.
Audience Member: I wanted to plug one hacktivism project that I think deserves mentioning: the Independent Media Center [applause] It's basically an activist hacker media collection/democratic media federation. Maybe you guys can comment on what you think about IndyMedia.
But I also wanted to ask a technical question. Why should I think about using Peekabooty over Freenet or something?
Drunken Master: First of all, I definitely support IndyMedia. I think they're awesome. They're one of the groups that opened my eyes to a lot of things.
Freenet does publishing, we do getting the media. Sort of the opposite.
Greg Walton: IndyMedia's great. I think hacktivism means more than hacking on a computer. Maybe it means over the airwaves, with video, pirate radio, this kind of thing. IndyMedia's fantastic. Democratic media movement, this is crucial to what we're talking about. Crucial.
Reid Fleming: Okay, does anyone have any last words before we dismiss everyone?
Drunken Master: I'd just like to say that Peekabooty is just one instance of hacktivism. There's going to be a lot more in the coming years. I encourage everyone to get involved with some group where you can support human rights.
When I came to this conference, I wasn't sure how well we'd get along. But we've had such a great melding of ideas. Bringing these disparate groups together has generated tons of ideas. It's been quite an experience.
Greg Walton: With Peekabooty, I think right now is just the genesis of something which we can't really even imagine what's coming next. It's a very exciting field.
I'd just like to keep on hearing from people that I've been meeting over the weekend, sharing ideas and giving me technical advice, answering my questions. That's been great.
Patrick Ball: I want to really thank cDc. It's really exciting for me to get involved with these guys.
I want to echo what's been said. I think we've had a terrific meeting of ideas. It's been really exciting. I've enjoyed being here, and I really look forward to about 24 hours more of some very intense conversation about hacking, about security, and about human rights.
Thanks. [applause]
Reid Fleming: For more information about Hacktivismo and updates on Peekabooty, you should check out the Cult of the Dead Cow website over the next weeks, months.
And if you want to talk to us after 5:30 today, we will be in the bar of the Hard Rock Hotel. You walk in the door, there's that little circular bar right in the middle. We'll be there.