Start Menu Cleaner v1.2
- (14k, 14,335 bytes).
Teleport
Pro v1.29 - Webpage.
Welcome to this new reversers tutorial, I'll explain here all of the steps in greater detail than in other tutorials so that you can follow easily. So without further ado launch Start Menu Cleaner, you'll notice from the message box that there is a Register button, so select that. You should now be looking at a dialog box asking for a Name and Code. I'll assume at this stage that you have installed SoftICE and that you have configured your winice.dat file (if you have not done this read the SoftICE installation guide), now just check that you can enter SoftICE using the key combination Ctrl+D, use the same combination or F5 to exit back to Windows.
Now type in your name and a fake code, I use CrackZ & 0123456789, but don't push O.K. yet, lets Ctrl+D into SoftICE and set some breakpoints. Now what we are going to do is break in on the code that is responsible for retrieving the contents of the 2 dialog boxes (and then verifying their contents), programmers usually achieve this by using functions from the Windows 32 API, you should be able to locate a list of 'reversers API's' around the web. This program uses the function GetDlgItemTextA (use QuickView or a disassembler if you want to verify this), most of the time it is a question of trial and error.
In SoftICE you should type >bpx GetDlgItemTextA, and then F5 to return to Start Menu Cleaner, when you click O.K, SoftICE should pop up, immediately you should push F11 (return to caller), remember that these functions are exported from Windows and called by the application. Now, we are at the stage where 1 of the dialog boxes has been retrieved so push F5 and you'll get another break on GetDlgItemTextA (the 2nd dialog box contents), and once again push F11.
You can now disable the breakpoint by typing >bd *. If you have performed the above steps correctly you should be looking at this code.
:004011C7 PUSH 00406030
:004011CC PUSH 00406130 <-- Name entered.
:004011D1 CALL 00401280 <-- Calculate good code.
:004011D6 LEA EAX,[ESP+18] <-- Code entered.
:004011DA ADD ESP,08 <-- Stack correction.
:004011DD PUSH EAX <-- Push code entered to stack.
:004011DE PUSH 00406030 <-- Push good code to stack.
:004011E3 CALL [KERNEL32!lstrcmp] <-- String compare function.
:004011E9 TEST EAX,EAX <-- Test EAX for 0.
:004011EB JNZ 00401271 <-- Jump_bad_code.
In SoftICE we use the F10 key to single step each of these instructions, so press F10 twice (the highlight bar should now be on CALL 00401280), now type >d 00406130, you should see the name you entered. Now press F10 another 2 times so that the highlight bar is now on ADD ESP,08. If you type >d eax you'll be able to see the code you entered. Another 2 steps with F10 will place the highlight bar on CALL [KERNEL32!lstrcmp], now type >d 00406030, you should be able to read the good code from the data window.
You should obviously make a note of the good code and now you can register this program. This is obviously the most simple example but go now and read more about how to use SoftICE and assembly language if the code you see above doesn't make any sense. Reading some of the other tutorials on my page may help you learn more.
Start Menu Cleaner v1.2
Name: CrackZ
Code: 1254-11586-1981-389
Welcome to the world of reversing - note that this program is now given out freely by the author hence the publishing of this code is not illegal in anyway.
This extension for newer reversers covers the subject of HEX editing with Hiew and generating a patch with GPatch, you'll find both of these programs available for download around the web. I'll assume that you have read the tutorial above on how to reverse Start Menu Cleaner v1.2 and that you are aware that the instruction shown below is the controlling good_guy/bad_guy check, you should understand that we don't want the program to ever 'jump' at this instruction.
:004011EB JNZ 00401271 <-- Jump_bad_code.
So lets begin. Firstly make a spare directory on your HD and copy the original unedited file (startcln.exe) and GPatch.com to it, now rename the original file to startcln.bak. You will also need to create a small file named GPatch.txt which is used by GPatch as a banner file, so just create a simple text file with Start Menu Cleaner v1.0 crack by ..... in it (if your any good at ASCII art then you can obviously use it as part of your patch).
The next thing to do is find the values of the bytes we need to patch, for this you can use SoftICE live but I prefer W32Dasm. After disassembling the program with W32Dasm, place the highlight bar directly over the JNZ 00401271 instruction, and press the button Code/Hex, you should then make a note of the top line of numbers (bytes), in this case.
0F 85 80 00 00 00 8D 44 <-- This is the HEX for the instruction JNZ 00401271, 8D and 44 form part of the next instruction.
Lets now close the disassembler and use Hiew. Place the original startcln.exe file in the hiew directory on your HD (not the copy you renamed I hasten to add), (I'm afraid if you can't copy, rename or understand files in DOS then reversing is not going to be your forte). Now type >hiew startcln.exe - obviously from a DOS prompt.
* Note that to get Hiew to display under Windows XP/2000 you'll need to follow the steps below (taken from the FAQ).
Q. I was moving over to Win2000/WinXP and was very surprised
that I can't run HIEW.
A. HIEW works up to 120x50 mode, but the setting for every DOS
mode window on Win2000/WinXP is 80x300. You can solve this problem
by setting the default mode to 80x25 for every window.
How you can do it :
Open the DOS mode window;
Click on the picture of the DOS mode window in the left up angle
of the window;
Choose "Default" (it's important);
After that choose "Properties";
Open "Layout" dialog;
In the "Screen Buffer Size" area put the number 25 into
"Height" control (by default it's 300);
Press OK button, it's all done.
The file will now be opened in Hiew, so lets change the viewing mode by pressing F4 and select HEX with the arrow keys. Now lets search for the bytes we noted by pressing F7 and typing the numbers, press Enter when complete. Hiew will now locate those bytes, so lets change the mode once again to Decode with F4. Now we want to change this instruction so that it never jumps, so lets use the NOP (no operation) which is 1 byte long and 90h. Note our instruction is 6 bytes long so we will need 6 NOP's for an equal swap.
So in Hiew lets change the mode to edit mode with the F3 key. Now write over the 0F 85 80 00 00 00 with 90 90 90 90 90 90, when complete press F9 to save the changes to disk and F10 to exit, note how each NOP goes on a separate line as each is a valid instruction. Be very careful when HEX editing, changing the wrong bytes is a very common error amongst newer reversers.
Now launch your newly edited version of Start Menu Cleaner and check that it does indeed except any registration code, then copy the file to the directory where you placed GPatch and startcln.bak earlier. Now from the DOS prompt you should type >gpatch startcln.exe - this will then generate the file patch.com which you can now distribute to those around the web less intelligent than yourself (and you better believe it there are zillions of them out there :-) ).
![]() ?ferret's Tutorial.
?ferret's Tutorial.
![]() PaRKeR's Tutorial.
PaRKeR's Tutorial.
Skill Level : Newbie.
Attack Plan : Serial #.
Target : Teleport Pro v1.29 build 1107.
Tools Needed : SoftICE, W32Dasm.
OK...First things first....Fire up the program & go through
the registration routine to see what happens. What? You didn't
get lucky and guess a correct serial? Oh well, I guess we'll have
to crack it :-)). Make a note of the bad message. ("We're
Sorry! The registration number...."). Notice that when you
click "OK", it goes back to the registration screen
& your data is still in the text boxes (a sure sign of a weak
protection).
Now, this isn't always the easiest way , but in this case it is very simple to trace back in W32Dasm. So, fire up W32Dasm and disassemble pro.exe. Search for the text from your bad reg message. You should see :-
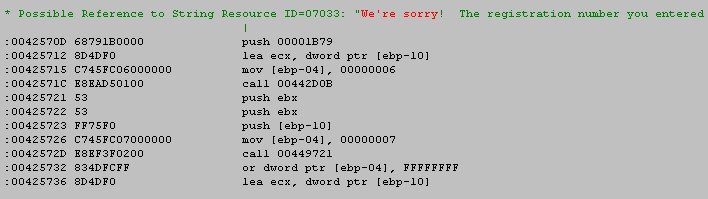
Make a note of the beginning code location. Just for grins, let's
search for "Thank You". There are several....the 3rd
occurence says the proggy is now registered...hmm...I guess that's
the one we want to try to get to huh?.
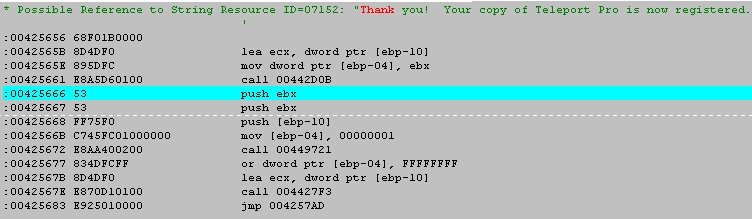
Now back to the error reference. Referenced by a conditional jump
@ 004256D7. Let's see what gets us to the error message. Click
on "Goto code location". Enter 4256D7 and hit <enter>.
Nothing suspicious here, but this section is also referenced by
a conditional jump, so, once again, let's see how we got here.
Goto code location 425691. Well, here we have a compare statement,
BUT, the "Thank You" message is right ABOVE this section
of code. So, let's check out the location of the conditional jump
that got us here (logically [but not definitely] the registration
check will be before the "Thank You" message in the
code). So, goto code location 42564C.
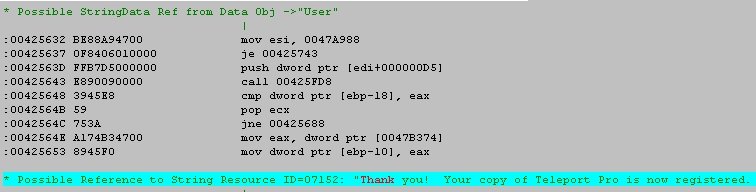
Eureka! I do believe we've found it!. Write down the code location of the line before the CMP statement. (i.e. 425643) (which is PROBABLY the call to the routine that calculates the serial number if you're interested in trying a keygen). Shut down W32Dasm, fire up Teleport Pro and set a bpx on CS:425643, (or, break on GetWindowTextA and step through using F10 until you get to this location). Try to register the program ..... SoftICE breaks.
If you do a ? EAX now you'll see your bogus serial in the command window. After the serial calculation, it is accessible through a pointer (DWORD PTR (EBP-18)). F10 to the next line (425648), do a d *(EBP-18) or dd *(EBP-18) to show the contents of the address referred to by the pointer. Your bogus #?, what do you suppose it will get compared to? :-). Do a ? EAX & write down the number shown in the command window.
BC * to clear all breakpoints, CTRL+D out of SoftICE and enter
the number you wrote down. VOILA!!! You are now registered!. Congratulations!.
Greets to all of the people who've helped me at the Newbies Forum.
?ferret.
Firstly I'd like to thank to tKC, Flu[X] and many others, I have learned how to crack and I'd like to share with other persons the few things I know now. So let's start this first tutorial with a small piece of shareware, Teleport Pro, which is a rather useful www site grabber. To crack this shareware, you'll need SoftICE and an assembler / compiler to make the key generator (easier in assembler).
First of all, if it's your first use of SoftICE, you'll need to edit your winice.dat file. Remove the ";" before the lines where you see kernel32.dll, gdi32.dll and user32.dll. Then restart your computer. OK, now you are ready. Launch Teleport Pro. In the help menu, you'll see the "Register" choice. An input box will appear and in the left bottom corner, three text fields : Name, Organization and Serial.
Hmm, let's see what happens. Name : PaRKeR, Organization : <Left Blank>, Serial : 12345. OK. Not Registered. Let's reverse engineer this monster. Ctrl-D brings you to the SoftICE window. Let's modify some stuff now : "lines 43" add more lines, "wr" brings the registers window, "wd" brings the data window. We add the breakpoints now : to read the info. from text fields, the functions usually are GetWindowTextA, GetDlgItemTextA, or GetDlgItemInt. Try "bpx getwindowtexta", "bpx getdlgitemtexta" first.
Ctrl+D and your are back to the Register window. Press OK. You are returned to SoftICE due to GetWindowTextA. Let's think a bit. Three text fields, it would be logical to have three breaks. Get out of the call by pressing F11. Press F11 again to continue. Another break. F11, F11, last break, F11. If you press another time F11, you'll get out of the SoftICE because there aren't anymore breaks.
So let's trace with F10 now. It will allow you to step over calls. Press F10 again and again till you get to the following lines :
:004246CD XOR EBX,EBX <-- Clear EBX.
:004246CF PUSH 0A
:004246D1 PUSH EBI
:004246D2 PUSH PTR [ESI+000000DD] <-- Push parameters.
:004246D8 CALL 0042A960
Just after the call, you'll see that the register EAX has changed. Now EAX=00003039 and 3039 hex is 12345 decimal. We've located our input code. Let's continue :
:004246DD MOV EBP,EAX <--- The code is now in EBP.
:004246DF MOV EAX,[00484C5C]
:004246E4 ADD ESP,0C
:004246E7 CMP [EAX+0000029F],BL
:004246ED JZ 0042482A
:004246F3 CMP EBP,EBX <--- Interesting compare.
:004246F5 MOV EDI,00429AD4
:004246FA JZ 00424755
Hmm, EBP is compared here with our code ... but EBX=0 : not the good code. Let's trace on :
:004246FC PUSH DWORD PTR [ESI+000000D5]
:00424702 CALL 00424FAF <--- Interesting function call.
:00424707 CMP EBP,EAX <--- Hmmm, interesting compare again.
:00424709 POP ECX <-- ECX from the stack.
:0042470A JNZ 0042471B <-- Deciding jump.
Now EBP is compared with EAX. Type "? eax" and it will give you an ASCII string, a value in hex and a decimal number. We'll write it down. We disable the breakpoints by typing "bd *", press Ctrl+D. Enter 1944573845 as the new serial # - (the number I got in EAX), and now I'm Registered. That rocks ! Close Teleport Pro.
Well, we'll have to check the key generation routine now. To unregister the shareware (thing that you MUST do if you are not the owner of a license). Launch Regedit.exe, and remove HKEY_CURRENT_USER/Software/Tennyson Maxwell directory. Close Regedit and head back to an unregistered Teleport Pro.
Open the Register window and enable the breakpoints by typing "be *" in SoftICE. Let's have a look at the piece of code above; you feel a while and it appears clearly that the key is generated at 00424FAF and is stored in EAX. Press OK, the break. Clear all breakpoints by typing "bc *". Now you can add a new breakpoint by typing "bpx 424702" : that is where the code generation call is - hmmm. Press F11. Now we are at the good address. Let's step into the call by pressing F8. F8 until you reach :
:00424FCE MOV ESI,5DFEE4A4 <--- I think this is important.
:00424FD3 XOR EBX,EBX <--- EBX will be the number of the char
considered.
:00424FD5 TEST EDI,EDI <--- Is name entered in EDI empty ?.
:00424FD7 JZ 00424FE2 <--- Bye, bye.
:00424FD9 PUSH EDI
:00424FDA CALL 0042A020 <--- Step over this call.
:00424FDF POP ECX
:00424FE0 JMP 00424FE4 <-- Good_guy.
:00424FE2 XOR EAX,EAX <-- Bad_guy.
:00424FE4 ADD EAX,-4 <--- Length-4.
:00424FE7 CMP EBX,EAX <--- Have we reached Length-4?.
:00424FE9 JAE 00424FF7 <--- If yes, let's go out.
:00424FEB XOR ESI,[EDI+EBX] <--- If not, let's XOR ESI with
a strange number.
(It's the 4 bytes of the name char EBX - reversed).
:00424FEE TEST BL,40
:00424FF1 JZ 00424FF4
:00424FF3 INC EBX
:00424FF4 INC EBX <--- Next char.
:00424FF5 JMP 00424FD5 <--- And we loop.
:00424FF7 MOV EAX,ESI <--- And we finally have it.
I would advise you code the key generator as an exercise. I chose TASM to make mine (source code attached in CrackZ's key generator archive). ASM is easier IMHO because you just have to copy some of the code and adapt it to your own. Just a hint : if you didn't get it, just before the piece of code above, Teleport Pro checks if the length of your name is greater or equal than 5.
I hope you had fun with the tutorial, and I'll be back soon for other adventures. Special thanks go to tKC and CrackZ.
Mail comments, suggestions to parker__@caramail.com