Name: Advanced Batch Mutator
Creator/Origin: Duke / Russia
AKA: ABM
Type: Mutation Tool
Known versions:
ABM 1.0 - May 2000
ABM 1.1 - May 2000
ABM 1.2 - May 2000
ABM 1.3 - June 2000
Features:
An input/output tool capable of mutating batch viruses to decrease chances of detection by AV software. The tool uses techniques such as junk creation and renaming command names to mutate batch files while maintaining functionality.
Author's note:
Features :
- size of generated file very different
- mutated virii not detected with any AV !!!
- mutated virii not suspected with any AV heuristic !!! (anti-NOD and anti-BatChecker algorithm ;-))) Batch-emulator will be added to next version of BAT Checker (special for Reminder ;-))
- mutated files very hard to read and understand ;)
Name: A**** B**** Mutation Engine
Creator/Origin: Procedure / Russia
AKA: ABME
Type: Polymorphic Engine
Known versions:
ABME - September 1998
Features:
Unknown. Released with a demo virus.
Name: Amazing Code Generator
Creator/Origin: Mad Daemon / Slovakia?
AKA: ACG
Type: Polymorphic Generator
Known versions:
ACG 1.0B - December 1997
Features:
Author's note:
Amazing Code Generator is a new generation polymorphic compiler which can make viruses undetectable to all scanners and algorithmic analysers. It is NOT a MtE-like polymorphic engine which encrypts code & generates decryption loop. It's a compiler that generates the whole code of the program. The code is each time different. The code is not encrypted. The program contains a portion of a compiler & pre-compiled source code and so it can at any time recompile itself so that registers, addresses, do-nothing instructions are changed. Because your program doesn't contain any static
Name: Awfully Nice Instruction Assembling System
Creator/Origin: Sea4 /
AKA: ANIAS
Type: Polymorphic/Oligomorphic Engine
Known versions:
ANIAS 0.1 - June 1998
Features:
Released with the author's Chelle virus.
Author's note:
"This file makes use of my brand new Polymorphic engine Anias v0.1 ( Awfully Nice Instruction Assembling System ). Its the first release of it, so its pretty simple. Not even Advanced Polymorph, its oligo- morphic. It loads BX as a reader of a table of variables... and SI as a reader of possible code variants. Using random values it chooses 1 of several variations of each command and writes that into itself to be written to the infected file. It utilizes two types of encryption, ASCII encryption which converts all encrypted bytes to their ASCII value which causes doubling of encrypted area size. Second, before the ASCII encryption takes place it uses the host file's own bytes to XOR against making the encryption random based on the file it infects. It uses the MCB method, introduced to me by Spo0ky, to go resident and while there hooks Int 21h, and infects upon file runs. Contains a few text strings, one being partial lyrics of 'Something in the Way She Moves'. This virus sometimes causes flags to pop up in TBav, such as '#' ( encryption ), 'J' ( Strange jump ), and 'c' ( Invalid or missing CRC )... but even with all those flags, and on High heuristics it doesn't suspect a virus. AVP, and F-Prot can find nothing wrong with it, McAfee as always can't find anything unusual, DrWeb finds it but I think the good Doc picks up just about anything... and DSav finds a possible new virus. Soon I will improve this Poly engine so it can be added to just about any virus, and so it uses more advanced poly techniques."
Name: AntiLogic Engine
Creator/Origin: Metal Satan / Japan
AKA: ALE
Type: Polymorphic Engine
Known versions:
ALE 1.0 - Unknown
Features:
Unknown. The engine is included in Neko.2697, by the same author.
Name: Amber
Creator/Origin: Reminder / Russia
AKA : --
Type: Mutation Engine
Known versions:
Amber 1.07B - Summer 1996
Features:
Unknown. Released with issue #2 of the E-zine Chaos AD released by the Death Virii Crew. Three viruses using the engine were included in the release.
Name: Anvil Of Crom Polymorphic Engine
Creator/Origin: Bumblebee / Spain
AKA: AOCPE
Type: Polymorphic Engine
Known versions:
AOCPE - December 1999
Features:
Unknown. Used in the Anvil Of Crom virus by the same author. Released in 29A#4.
Name: Advanced Polymorphic Engine
Creator/Origin: Dark Prince / Russia
AKA: APE
Type: Polymorphic Engine
Known versions:
APE 1.0 - March 1994
APE 2.0 - December 1994
Features:
Similar to TPE it has more complex decryptors and is one of Russia's first polymorphic engines.
Name: Another Polymorphic Engine
Creator/Origin: Bumblebee / Spain
AKA: APE
Type: Polymorphic Engine
Known versions:
APE 1.0 - June 1999
Features:
Polymorphic engine entered in a contest by Virusbuster. Since it was the only entry it was also the winner.
Name: Antisocial Poly Encryption Engine
Creator/Origin: Lys Kovick
/ Unknown
AKA: APEE
Type: Polymorphic Engine
Known versions:
APEE 1.0 - October 1999
Features:
Polymorphic tool for macro viruses. Used in the AAA virus by the same author. It was also released with LineZero Zine #2.
Name: Advanced Polymorphic Macro Replication System
Creator/Origin: Pyro / UK?
AKA: APMRS
Type: Polymorphic Engine
Known versions:
APMRS 1.0 - April 1997
Features:
One of the first attempts at a polymorphic engine for Word For Windows macro viruses. The engine was specifically created for Word 8.0 (Word 97) macro viruses which use the Visual Basic for Applications (VBA) language.
Name: Alpha PolyMorphic Engine
Creator/Origin: Viking / Unknown
AKA: APME
Type: Polymorphic Engine
Known versions:
APME - 1.04b Unknown
Features:
APME is an ordinary polymorphic generator such as MtE and TPE. There is only one known virus "APME.Demo" that is included in APME.ZIP distribution package as APME.COM file. The virus opens APME.COM file, and overwrites it with new virus copy. Then the virus displays:
[_PME] Alpha PolyMorphic Engine by ViKing - Version 1.04b
Name: Antigen's Radical Tunneler
Creator/Origin: Antigen
/ Australia
AKA: ART
Type: Tunneling Engine
Known versions:
ART 1.0 - February 1995
ART 2.2 - April 1995
Features:
Author's description: "This is by far the most revolutionary (and largest) tunneler that I have encountered, and I hope that you will agree with me in awe of its might and power. ;) The basic idea is that very few AV packages test for tunneling, but those that do can render a mega-krad polymorphic stealth armoured IRQ hooking virus absolutely useless with just a few opcodes. I found this to be somewhat unjust, and decided to take matters into my own hands. Here is the fruit of my labors!" "The total size of ART is 1.6k, which I consider to be a small price for complete invulnerability to common and even most uncommon detection/disabling methods."
See also:
Tunneling shortcuts.
Name: ASM Swap Engine
Creator/Origin: TechnoRat / Unknown
AKA: ASE
Type: Code Modification Tool
Known versions:
ASE 1.0 - January 1997
ASE 1.1 - February 1997
ASE 1.2 - March 1997
ASE 1.3 - August 1997
Features:
A Pascal tool that scrambles assembler source codes to create a form of polymorphism. An engine derivative is used in the Harrier series viruses by the same author.
Third party analysis:
"The polymorphic engine may be classified is an average one, but it generates from nine till seventeen decryption loops, decrypting virus code layer-by-layer, mixed with many junk instructions, and it generates about ten kilobytes of polymorphic code. "
Harrier virus analysis:
"Being decrypted the virus code appears in very strange form. Each virus instruction is followed by JMP opcode that passes control to another place in the virus code. The virus assembler instructions seem to be randomly mixed in the virus code and linked by JMP commands. Instructions of any virus routine may be found at any position in the virus code, they may distant each other by several kilobytes. Fortunately, the virus has no "mixing" (mutating) engine in its code, the sequences of virus instructions stays the same in each infected file. It seems that virus author used some special tool to mix source assembler code before compiling it to the first-generation EXE file. "
Name: Anti Web Mutation Engine
Creator/Origin: AD / Russia
AKA: AWME
Type: Mutation Engine
Known versions:
AWME 1.0 - June 1995
AWME 1.1 - August 1995
Features:
It was used in a harmless nonmemory resident parasitic virus that searches in the current directory for COM files except several anti-virus scanners and COMMAND.COM, then writes itself to the end of the file. The virus contains the text strings, the second one is the names of anti-viruses (two bytes per name):
Anti WEB Mutation Engine [AWME] by AD. v1.0
AIWESCCOVSADAN-V
*.com*
This is a simple [AWME] demo virus by AD.
Name: Advanced Zombie Code Mutation Engine
Creator/Origin: Zombie / Russia
AKA: AZCME
Type: Mutation Engine
Known versions:
AZCME 0.4 - July 1998
Features:
Unknown. Apparently an advanced version of Zombie's Code Mutation Engine (ZCME). An attempt at an 32-bit version is known to exist.
Name: Bumblebee's AGGRessive Polymorphic Engine
Creator/Origin: Bumblebee / Spain
AKA: BAGGRPE
Type: Polymorphic Engine
Known versions:
BAGGRPE - Unknown 1999
Features:
Unconfirmed and unknown. By the author of APE, BUME and HKPE.
Name: Benny's Compression Engine for Win32
Creator/Origin: Benny
/ Czech Republic
AKA: BCE32
Type: Compression Engine
Known versions:
BCE32 - May 1999
Features:
478 bytes large compression engine released with 29A#4.
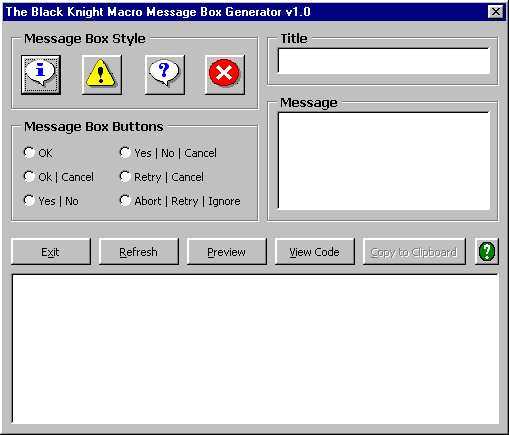
Name: Black Knight Macro Message Box Generator
Creator/Origin: Black Knight / Philippines
AKA: BKMMBG
Type: Coding Utility
Known versions:
BKMMBG 1.0 - June 2000
Features:
Author's note:
"BKMMBG is a small utility made specially for macro virus writers, this utility will help you easily create message boxes in a macro virus, no more hassle, just run the program, and copy the generated code to your favorite txt editor/directly to VB editor and your're ready. "
Name: Benny's Polymorphic Engine for Win32
Creator/Origin: Benny
/ Czech Republic
AKA: BPE32
Type: Polymorphic Engine
Known versions:
BPE32 - May 1999
BPE32 bugfix - May 1999
Features:
A polymoprhic engine for the Win32 environment released in DDT#1. The bugfixed version was released with 29A#4.
Author's note:
This poly engine is able to:
1) Create SEH handler, cause exception and so fuck some tiny debuggers and AV emulators.
2) Randomly change registers in instructions.
3) Generate different instructions, which do the same thing.
4) Swap groups of instructions between them.
5) Create calls and jumps to dummy routines.
6) Generate junk instructions between real code.Special features:
1) It uses one Pentium instruction (RDTSC for gettin' random numbers)
2) It creates variable decryptor size.
3) It encrypts and decrypts whole DWORDs.
4) It's optimized as well, its size is "only" 1507 bytes. (1498 bytes bugfixed)
Name: Bliem
Creator/Origin: jackie twoflower / Austria
AKA: --
Type: Polymorphic Engine
Known versions:
Bliem - June 1999
Features:
A polymorphic infection engine by the author of LiME, CMK, PiE, SPS and SOPS. Released in issue #1 of LineZero Magazine. Evolved into JSMP/JUMP.
Author's note:
"The most bad thing about the already existing polymorphic engines for vba was that the always inserted the code at the same lines or the volume of the source code growed and growed and ... So 'bliem' doesn't have such problems. The main good thing in 'bliem' is that it always 'keeps an eye' on the actually size of the source code and reduces it when it's too big. Let's say something about the technic of inserting the junkcode: The junkcode is inserted into the viruscode not in the common way. The junkcode is inserted while infection. This means that the whole viruscode is stored in arrays and the junkcode is stored in some of this arrays. Like the main code is stored there, also junkcode is also there and will be inserted while infecting the new class object. While inserting the actual code into arrays, the 'bliem brain' is checking for the actually size of itself and if its too big, it deletes some junk arrays. I use this method because the old one with the command '.deletelines' only screwed up the code."
Name: Biological Warfare Mutation Engine
Creator/Origin: Mnemonix / USA
AKA: BWME
Type: Polymorphic Engine
Known versions:
BWME 1.0 - June 1994
Features:
This polymorphic engine was released with version 1.0 of Mnemonix' Virus Creation Tool Biological Warfare. According to the author it is basic engine using 609 bytes. Many viruses using the engine are known and most scanners will detect them.
Name: Bubble
Creator/Origin: Lethal Mind / Unknown
AKA: --
Type: Polymorphic Engine
Known versions:
Bubble - March 1999
Features:
Used in the Champagne virus by the same author.
Author's Note:
"It's not a revolutionnary polymorphic engine, but it's quite a good one... It uses register sliding, multiple opcodes randomly generated encryption algorythm, junk generator... It's slow polymorphic and will change it's decryptor every day only..."
Name: Bumblebee Ultimate Mutator Engine
Creator/Origin: Bumblebee
/ Spain
AKA: BUME
Type: Mutation Engine
Known versions:
BUME - April 1999
Features:
Author's note:
"Bumblebee Ultimate Mutator Engine [BUME] for EXE infectors (and works fine with COM infectors).
I wrote it for VirusBuster's polymorphic engine competition. HKPE is small and crypt algo is better. But BUME includes some anti-debug in the generated procs and also includes some push's for EXE infectors. "
Name: Code Generator
Creator/Origin: Zombie / Russia
AKA: CGEN
Type: Anti Detection / Mutation / Metamorphic Tool
Known versions:
Code Generator 1.00 - Unknown 2000
Code Generator 1.50 - July 2000
Code Generator 1.60 - August 2000
Features:
Tool to generate metamorphic code (varying opcodes that will get the same results but will look different to AV software). Version 1.6 was released with Matrix Zine #2 together with an article explaining some of the details. Uses ETG by the same author.
Name: Cookie Scramble Engine
Creator/Origin: jackie twoflower / Austria
AKA: CSE
Type: Mutation Routine
Known versions:
CSM 0.666 - May 2000
Features:
Author's Note:
[VBA.Cookie Scramble Engine v0.666 aka CSE]
This engine was coded as an idea I followed when I thought about scrambling procedures. The CSE scrambles all your procedures you have in your source code. Just follow a few easy steps to include the engine into your creation.
- Includeable for all VBA viruses, Word97, Excel97, etc.
- Scrambles all procedures every infectionIt was also released with LineZero Zine #2.
Name: Chromatos Self-behavior Mutation Engine
Creator/Origin: Mr. Sandman / Spain
AKA: CSME
Type: Mutation Engine
Known versions:
CSME - August 1999
Features:
A "self-behavior" mutation engine used in the Girigat virus by the same author. Released with VXtasy #1.
Name: Crazy Lord Mutation Engine
Creator/Origin: Crazy Lord / Hong Kong?
AKA: CLME
Type: Mutation Engine
Known versions:
CLME 0.61 - 1996
CLME 0.62 - 1996
Features:
Unknown. Used in the CLME.Ming.1528 and CLME.Ming.1952 (Amoeba 1.00) viruses.
Name: Cybertech Mutation Engine
Creator/Origin: Apache Warrior
/ UK
AKA: CME
Type: Mutation Engine
Known versions:
CME 1.0 - 1992
CME 2.0 - 1992
Features:
Used in the Jo(anna).911 virus by the same author. There is a maximum of 3 unchanged bytes in the encrypted code.
Name: Code Mixer
Creator/Origin: Zombie / Russia
AKA: CMIX
Type: Anti Detection Tool
Known versions:
CMIX 1.50 - March 2000
Features:
Together with ETG and LDE32 used in EXPO.
Author's Note:
"CODE MIXER is an utility (subroutine, library, engine, include file, ...) to mix 2 code buffers. The destination buffer will contain all instructions of the source buffers mixed between each other in random order.
Features:
- code is offset-independent, so it can be displaced or permutated
- no external data used, only own stack vars
- jmps/calls (E8,E9,7x,0F 8x) are fixed (to point correctly to the new addresses)
- external jmps/calls (i.e. out of the source buffers) are fixed correctly
- short jmps (7x,EB) are expanded into near jmps
- if next command is jxx (short or near), it will be stored after current command, without inserting other buffer commands before jxx
- commands jecxz,loop,loopz,loopnz (E0/E1/E2/E3) are ignoredWhere CODE MIXER can be used:
- to create polymorphic decryptors
1. generate simple decryptor (as in crypt-virus)
2. generate some trash (easy with ETG engine)
3. mix buffers- to mix some commands from host 's startup and from virus's startup
- to generate some hash-alike functionsfor example:
dst-reg-set = [REG_EAX],
src-reg-set = [REG_EBX],
so generated function will return EAX=f(EBX)
Name: Code Pervertor
Creator/Origin: Zombie / Russia
AKA: CPER
Type: Anti Detection / Mutation Tool
Known versions:
Code Pervertor 1.00 - January 2000
Code Pervertor 2.00 - April 2000
Features:
External mutation tool that replaces some instructions or instruction groups with equivalents of the same length. Because binary images of files will change the result will be no or harder detection by AV software. Version 2.00 is completely rewritten and has some major changes.
Name: Compact Polymorphic Engine
Creator/Origin: unknown / unknown
AKA: CPE
Type: Polymorphic Engine
Known versions:
CPE 0.11b - December 1994
Features:
Contains advanced anti-tracing features
Name: Cryptgen LITE
Creator/Origin: Case / USA
AKA: CL5
Type: Polymorphic Engine
Known versions:
CL5 5.8883.19 ZXr47.3 - December 1996
Features:
Author's note:
"it makes a few anti-tracing, anti-debuging traps (armor level: none to weak) it can make decryptors that use a counter register or ones that compare the value of the pointer to determine when the loop should terminate. it can use just about any register for the counter (can't use SP). the encryption it makes is like this: xor, add/sub/rol, xor, add/sub/rol, etc it can make jz/jnz/jae/jbe/ja/jb/jmp/ret/jmp reg to loop it can make inc ptr/scasb/lodsb/cmpsb to increment the pointer it sets up the registers in a random order garbage can be turned off (for poly in memory!), just do mov [garbage],-1 before calling the engine." ... "it's 1381 bytes long (slightly smaller than one of Lapse's new viruses :) Dark Angel helped/showed me how to remove a ton of bytes :) the maximum length of the generated decryptors is B7h bytes"
Name: CrkV Mutation Engine
Creator/Origin: CrkV / Russia
AKA: --
Type: Mutation Engine
Known versions:
CVME 1.0 - July 1999
CVME 1.01 - July 1999
Features:
Mutation engines released with Moonbug #11. Details unknown.
Name: Dark Angel's Multiple Encryptor
Creator/Origin: Dark Angel / Canada
AKA: DAME
Type: Polymorphic Engine
Known versions:
DAME 0.90 - June 1993
DAME 0.91 - December 1993
Features:
Naturally enough, Phalcon/SKISM didn't want to be upstaged by NuKE. In 1993, this virus group, which originates from Canada, joined the fray with Dark Angel's Multiple Encryptor, DAME. The new generator's name may have been meant as a dig at some members of the anti-virus community, who had been using the name DAME for Dark Avenger's Mutation Engine, MtE.
Dark Angel published his generator during the summer of 1993 in issue 11 of Phalcon/SKISM's magazine, 40Hex. Dark Angel has also written the two virus creation toolkits published by Phalcon/SKISM, the PS-MPC and G2.
Like NED, DAME was distributed as commented source code. Along with the generator, Dark Angel published an article which dealt with polymorphism and the writing of polymorphic generators in
general.
Dark Angel was apparently not completely satisfied with his initial product, because he introduced an improved version of DAME in the next issue of 40Hex.
The first version of DAME, 0.90, took up 1574 bytes. The improved 0.91 version had grown to 1960 bytes.
Name: Dark Elf Mutation Engine
Creator/Origin: Unknown / Unknown
AKA: DEME
Type: Polymorphic Engine
Known versions:
DEME 1.0 - November 1996
Features:
Unknown. Used in the Dark Elf 3.0 [DarkElf.3691] virus.
Name: Darwinian Genetic Mutation Engine
Creator/Origin: Mark Ludwig / USA
AKA: DGME
Type: Polymorphic Engine
Known versions:
DGME 1.0 - December 1993
Features:
The Darwinian Genetic Mutation Engine works in conjunction with a conventional mutation engine like the Trident Polymorphic Engine to implement darwinian evolving viruses which can outsmart anti-viral products via evolution.
The DGME is fully documented in the book "Computer Viruses, Artificial Life and Evolution" by Mark Ludwig of American Eagle Publications, Inc.
Name: DINA
Creator/Origin: Voodoo / Russia
AKA: --
Type: Stack Mutation Engine
Known versions:
DINA 2.2 - July 2000
Features:
Unknown. Released with DVL #10.
Name: Dr. Jekill Diskette Infector
Creator/Origin: Dr. Jekill / Unknown
AKA: DJDI
Type: Boot Sector Infector
Known versions:
DJDI 1.0 - January 1998
Features:
Similar to EVI and DropBSV this tool is capable of infecting a diskette boot sector with several boot sector viruses.
The viruses are:
- PingPong.A
- NYB
- Stoned.March6.A
- AntiCMOS
- Stoned.AntiEXE
- Bye
Name: Dark Killer Mutation Engine
Creator/Origin: Dark Killer /
Taiwan
AKA: DKME
Type: Mutation Engine
Known versions:
DKME 1.0 - April 1995
Features:
Unknown
Name: DickLip$ Random Garbage Macro Polymorphic
Creator/Origin: Ultras / Russia
AKA: DLRGMP
Type: Mutation Routine
Known versions:
DLRGMP - May 2000
Features:
VBA mutation / garbage routine for macro viruses.
Name: Deviator Morphic Engine
Creator/Origin: Deviator / Russia
AKA: DME
Type: Metamorphic Engine
Known versions:
DME 0.0001beta - July 2000
Features:
Largely unknown. Development of a "full morphing" engine.
Name: Dutch Mutation Unit
Creator/Origin: Bit Addict
/ Netherlands
AKA: DMU
Type: Mutation Engine
Known versions:
DMU 1.0 - December 1993
Features:
Unknown. Used in the Mirror virus by the same author.
Name: Dumb Oversized Poop Engine
Creator/Origin: Yosha /
Unknown
AKA: DOPE
Type: Polymorphic Engine
Known versions:
DOPE 1.0 - January 1997
WinDOPE - Unknown
Features:
Unknown. Used in the Smegma virus by the same author. A Windows optimized version of DOPE is used in the Win.Dragon virus by the same author released in Metaphase Zine #2.
Name: Demo Polymorphic Engine
Creator/Origin: Bozo / Italy
AKA: DPE
Type: Polymorphic Engine
Known versions:
DPE - June 1998
Features:
Unknown. This demonstration of a polymorphic engine was released with issue #3 of the Butchered From Inside (BFI) zine. It is based on Bozo's SPWM engine. Author of SMPE.
Name: Dumb Polymorphic Engine
Creator/Origin: Mental Driller
/ Unknown
AKA: DPE
Type: Polymorphic Engine
Known versions:
DPE - Unknown 1999
Features
Basic and generic polymorphic engine used in the Nazka virus by the same author. Released with 29A#4.
Name: Direct Phantom Simulated Polymorphic Generator
Creator/Origin: Daemonserj / Russia
AKA: DPH
Type: Polymorphic Engine
Known versions:
DPH 1.0 - August 1998
DPH 2.0 - August 1998
DPH 2.1 - September 1998
Features:
Unknown. An includable polymorphic generator. Released with DVL #10.
Name: D**** P**** T****
Creator/Origin: Retch / Ph33r? / Unknown
AKA: DPT
Type: Polymorphic Engine
Known versions:
DPT - Unknown
Features:
Unknown.
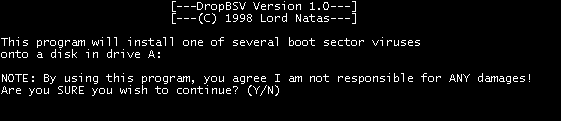
Name: DropBSV
Creator/Origin: Lord Natas / USA
AKA: --
Type: Boot Sector Virus Dropper Tool
Known versions:
DropBSV 1.0 - January 1998
Features:
Similar to EVI and DJDI this tool is capable of dropping a number of boot sector viruses to disk.
Author's notes:
This program installs one of several boot sector viruses onto a disk in drive A: This program is similar to EVI except:
- The viruses are more modern
- This program actually saves the old boot sector, so the disk still boots
- The infected disks look like a 'natural infection' by the virus
- All of the viruses are capable of infecting 1.44 Megabyte disks
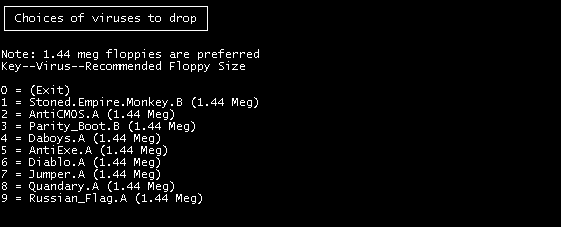
- Better user interfaceThe viruses this program can install are:
- Stoned.Empire.Monkey.B
- AntiCMOS.A
- Parity_Boot.B
- Da'boys.A
- AntiExe.A
- Diablo.A
- Jumper.A
- Quandary.A
- Russian_Flag.A
Name: Dark Side Compression Engine
Creator/Origin: EvilRats / Unknown
AKA: DSCE
Type: Compression Engine
Known versions:
DSCE 0.99R5B - September 1999
Features:
An engine based on the Huffman algorithm, used in the Aldebaran virus released with Xine #4.
Name: Dark Slayer Confusion Engine
Creator/Origin: Dark Slayer
/ Taiwan
AKA: DSCE
Type: Polymorphic Engine
Known versions:
DSCE 1.0 - April 1994
Features:
This is a polymorphic generator which has so far eluded the antivirus researchers. It is written by the same author as DSME. A file that demonstrated DSCE's abilities was sent to F-PROT Professional Support during April 1994. Deductions based on this demo indicate that DSCE is a rewritten version of DSME, and capable of creating far more complicated samples.
Name: Dark Slayer Mutation Engine
Creator/Origin: Dark Slayer
/ Taiwan
AKA: DSME
Type: Polymorphic Engine
Known versions:
DSME 1.0 - September 1993
Features:
DSME is the first polymorphic generator from Taiwan. Interestingly, DSME contains documentation both in English and Chinese. The author sends greetings to Dark Avenger and Nowhere Man and thanks for the inspiration he received from earlier polymorphic generators. DSME is not as advanced as the generators produced before it. Dark Slayer admits this in his notes. The actual size of the generator is little over 2 kilobytes.
Name: Duke's Simple Virus Cloner Tool
Creator/Origin: Duke /
Russia
AKA: DSVCT
Type: Junk Generator
Known versions:
DSVCT 1.0 - June 1999
DSVCT 1.1 - June 1999
Features:
DSVCT is a command line tool which modifies source codes of detected viruses with junk code. The resulting viruses are still functional but often no longer detected since the known virus signature is absent.
Name: Engine of Eternal Encryption
Creator/Origin: Unknown / Unknown
AKA: EEE
Type: Polymorphic Engine
Known versions:
Unknown
Features:
Used in the DarkParanoid virus that was released in Moon Bug #7.
The difference between ordinary polymorphic engines and "DarkParanoid"'s engine is the fact that in this virus there is no decryption loop in polymorphic code - it just hooks INT 1 and starts tracing the main code. This code in different infected files may appear in different form - while generating this code the virus randomly selects the registers, commands, data access modes and so on.
Similar for INT 1 handler that contains on-the-fly encryption/decryption routine. This code in different files is also different - more than ten encryption functions are randomly selected from the set: ADD, SUB, XOR, NEG, NOT, ROR, ROL, as well as byte and word access. Also random registers are used, and offset of INT 1 handler is randomly selected within some limits.
Name: Explosion's Mutation Machine
Creator/Origin: Vyvojar / Slovakia
AKA: EMM
Type: Mutation Engine
Known versions:
EMM 1.0 - April 1995
Features:
Unknown. Published / released with the Level 3 virus in Issue #14 of the 40 Hex E-Zine.
Name: Eternal Maverick Multilevel Encryptor
Creator/Origin: Eternal Maverick / Ukraine
AKA: EMME
Type: Mutation Engine
Known versions:
EMME 1.0B - February / March 1995
EMME 1.0 - February / March1995
EMME 2.0B - April 1995
EMME 2.0 - April 1995
EMME 3.0 - May 1996
EMME 4.0 - 1996
EMME 5.0 - 1996
Features:
Unknown. Published / released in Issue #5 (Russian) (v. 1.0), Issue #6 (Russian) (v. 2.0) and Issue #1 (English) (v. 3.0) of the Infected Voice E-Zine.
Name: Eternal Machine Polymorphic Decryptor
Creator/Origin: Henky
/ Spain
AKA: EMPD
Type: Polymorphic Decryptor
Known versions:
EMPD - October 1999
Features:
Unknown. Used in the W95/Nathan virus of the same author.
Name: Eternal Maverick Small Mutation Engine
Creator/Origin: Eternal Maverick / Ukraine
AKA: EMSME
Type: Mutation Engine
Known versions:
EMSME 1.1 - April 1997
EMSME 1.5 - September 1997
Features:
Unknown. Version 1.5 was published / released in Issue #2 (English) of the Infected Voice E-Zine. It is based on one of Eternal Maverick's earlier creations, EMSPE.
Name: ENFK
Creator/Origin: Unknown / Unknown
AKA: ENFK
Type: File Dropper / Conversion Engine
Known versions:
ENFK - Unknown
Features:
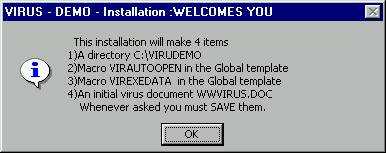
This utility inserts executable binary files in Word macros (using WordBasic). It can create a new document called WWVIRUS.DOC in a newly created directory. It gets an EXE file, converts it to text data and then puts this data into a macro. The document is able to convert the text data back to an EXE file and execute it.
Name: Eternal Maverick Small Polimorphic Encryptor
Creator/Origin: Eternal Maverick / Ukraine
AKA: EMSPE
Type: Mutation Engine
Known versions:
EMSPE 3.0 - May 1996
Features:
Unknown. Published / released in Issue #9 (Kiev edition) of the Infected Voice E-Zine. It uses parts of the demo program of Burglar's PME but the engine is new.
Name: Expressway To My Skull
Creator/Origin: Bozo / Italy
AKA: ETMS
Type: Polymolrphic Engine
Known versions:
ETMS 0.1 - September 1999
Features:
Released with Xine #4 and used in the Aldebaran virus.
Author's Note:
Basic features:
- Encryption using XOR/ADD/SUB/ROL/ROR on bytes/words/dwords with either fixed (fixed immediate or fixed reg) or changing key
- Can use all registers as pointers, counters and key holders
- Can encrypt from start to end and from end to beginning
- Can create memory reference with offset (ie. [ECX + 1234h])
- Counter with random costants added, counts both decrementing or incrementing its value
- Key change using XOR/ADD/SUB/ROL/ROR/INC/DEC on bytes/words/dwords of the key register
- Quite some different ways of counting loop
- Some garbage is encrypted aswell
- Lenght of generated decryptors range somewhere between 400 bytes up to 4kbs
Garbage:
- All the normal math, logical and comparation operations and assignations on registers, immediates and memory references
- Moving and exchanging of registers
- Push of regs/imms/mem_data, pop to regs
- Creation of fake subroutines
- Conditional and unconditional jumps
- Usual one byte opcodes
- Temporary saves somewhere (to another register or to stack) importan registers (such as key, counter and pointer) and makes garbage with them.
- More or less all the usual code you could find around in normal programs, excepts memory writes and such. Anyway you'd better give a look to some decryptors, it is not easy to write too deeply what it does.
Name: Executable Trash Generator
Creator/Origin: Zombie / Russia
AKA: ETG
Type: Anti Detection Tool
Known versions:
ETG 1.00 - March 2000
Features:
Routine that can create code to avoid successful decryption emulation by AV software. Together with CMIX and LDE32 used in EXPO.
Author's note:
- ETG may be used to generate trash, which is placed between polymorphic decryptor and your code, so after emulating decryptor AV will suck.
[HOST FILE] [POLYMORPHIC DECRYPTOR] '->[TRASH] (encrypted) //etg(bufsize=1024,regs=REG_ALL,cmds=ETG_ALL) '->[VIRUS] (encrypted)- ETG may be called from some polymorphic engine, to generate trash between really decrypting instructions. (specify NCMDS=1 and ETG will generate single instructions)
... ; etg(dst=REG_ALL,src=REG_ALL,ETG_ALL) mov r1, offset virus ... ; etg(dst=REG_ALL-r1,...) mov r2, virus_size ... ; etg(dst=REG_ALL-r1-r2,...) c1: not byte ptr [r1] ... ; --//-- inc r1 ... ; --//-- dec r2 ... ; --//-- jnz c1 ... ; etg(dst=REG_ALL,...)- ETG may be used to generate some unreversible "hashing" subroutines. In this case you should kill some user's data and use hash, so no one will be able to restore infected objects completely.
Name: Ejecutor Virus Inserter
Creator/Origin: El Ejecutor / Argentina
AKA: EVI
Type: Boot Sector Virus Dropper Tool
Known versions:
EVI 1.0 - Unknown
Similar to DJDI and DropBSV this program can insert viruses on a floppy disk inserted in the A: drive.
The viruses are:
Antitel Disk Killer
Aircop Exebug 2
Boothrs2 Michelangelo
Brain Ping Pong
Cansu StonedReleased by the the creator of Ejecutor Virus Creator.
See also: DropBSV
Name: EVOL-1
Creator/Origin: Mnemonix / USA
AKA: --
Type: Polymorphic Engine
Known versions:
EVOL-1 1.0 - November 1995
Features:
A module, when attached to any virus, that will render the virus more difficult to scan for. It will encrypt any code it is given with a unique key and create a self-decrypting module that contains this code. It contains a special feature that will allow for wildcard mutation. The module is 2051 bytes long.
Name: Evol(ve)
Creator/Origin: Paddingx? / unknown
AKA: --
Type: Polymorphic / Metamorphic Engine
Known versions:
Evol(ve) - July 2000
Evol(ve) bugfix - July 2000
Features:
Used in the Evol virus.
Author's Note:
" The only particularity of Evol is its evolution engine - meaning that the virus will mutate every 4 copy of itself. The engine is not an usual polymorphic engine, but rather a metamorphic engine (see Benny description in 29A #4), which means that there is no encrypted code : the whole code of the virus, engine included, is variable. Furthermore, the engine inserts random code, so as to make detection by antivirus more difficult. The virus contains no fixed data : it is only a massive piece of code. "
Name: EXample POlymorphic Engine
Creator/Origin: Zombie / Russia
AKA: EXPO
Type: Polymorphic Engine
Known versions:
EXPO 1.00 - March 2000
EXPO 1.01 - March 2000
EXPO 1.02 - March 2000
Features:
A demo polymorphic engine that uses a combination of ETG, LDE32 and CMIX.
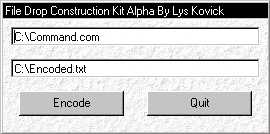
Name: File Drop Construction Kit
Creator/Origin: Lys Kovick
/ Unknown
AKA: FDCK
Type: Conversion / Encryption tool
Known versions:
FDCK Alpha - August 1999
Features:
Tool that converts binary files into a series of Chr() expressions, specifically created to create a file dropping capability in macro viruses. By the author of PCK.
Name: FAT16 Independent Replicative Emultaor
Creator/Origin: Zombie / Russia
AKA: FIRE
Type: Viral Infection Tool
Known versions:
FIRE 1.00B - May 1998
Features:
Author's intro:
- Using IDE IO-port access method find all physical IDE drives
- For each physical drive find all logical disks with FAT16 system
- For each logical disk scan directory tree with selected max directory level
- Delete all AV-files (by filemasks), including file name/cluster chain
- Infect each EX?/CO? file (with selected min. size)
*** Infection Method ***
- Allocate some free cluster(s) in the FAT
- FAT.LastOurCluster <- DirEntry.StartCluster
- DirEntry.StartCluster <- 1stOurCluster
*** Program ***
Name: Floating Point Polymorphic Engine
Creator/Origin: Super
AKA: FPPE
Type: Polymorphic Engine
Known versions:
FPPE - May 1999
Features:
Unknown. Released in DDT #1.
Name: Fire/Space Mutation Machine
Creator/Origin: Unknown / Russia
AKA: FSMM
Type: Polymorphic Engine
Known versions:
FSMM 1.0 - Unknown
Features:
Unknown.The engine is included in FSMM.2971, by the same author.
Name: First Mutation Engine for Batch
Creator/Origin: Reminder / Russia
AKA: FMEB
Type: Mutation Engine
Known versions:
FMEB - May 1996
Features:
Released with issue #2 of the E-zine Chaos AD released by the Death Virii Crew. The Batalia6 batch virus using the engine was included in the release. Below a short explanation on the virus/engine combination.
"It is a harmless nonmemory resident polymorphic parasitic BAT virus. It searches for BAT files in the current directory, then infects them. While infecting a file the virus runs the ARJ archiver to pack the necessary files. If there are no ARJ.EXE file in PATH, the virus fails to replicate itself.
The infected contains two parts of code and data. The first part(the header) contains five DOS commands, the second part (the rest) contains a random named BAT file that is compressed by using the ARJ archiver and a password. So, the infected file contains the text strings (DOS commands) and the binary data (ARJ archive).
That BAT file also contains two parts: the main virus code (batch commands) and the compressed data. The compressed data contains several files: the host file, the virus data and code files. The infected files look as ARJ archive within ARJ archive:
Infected BAT file:
+--------------------+ |BAT instructions | - Header1, startup virus code |--------------------| | ARJ archive: | - Random named BAT file packed with ARJ | +----------------+ | | |BAT instructions| | - Header2, main viruscode | |----------------| | | | ARJ archive: | | - The set of files | | +------------+ | | | | |BATALIA6.BAT| | | - Infection,polymorphic and random | | | | | | generator routines | | |hostfile.BAT| | | - Theoriginal host file | | |ZAGL | | | - Virus datafile | | |RULZ | | | - Virus datafile | | |FINAL.BAT | | | - Deletesthe temporary files and | | +------------+ | | subdirectory | +----------------+ | +--------------------+Header1 contains five commands that are selected from several
variants and have different lengths, for example:@echo off rem arj e %0 %compec% -g5 C:\COMMAND.COM nul /carj x %0 -g2 :nul arj x %0 -g7 C:\COMMAND.COM w HOST.BAT @EcHo OfF rem COMMAND.COM nul /carj x %0 -g1 %comspec% nul /c arj e HOST.BAT -g3 :echo C:\COMMAND.COM nul /carj x %0 i HOST.BATThe ARJ archive is encrypted with a random selected password, so the virus does not contain constant bytes, and as a result it is the first known polymorphic BAT virus.
When executed, the virus (header1) runs ARJ archiver, extracts the second part (BAT file) and executes it. The code of second part creates the temporary directory, extracts the files from the second archive to the temporary directory, then runs the searching, infecting and polymorphic routines, then executed the host file and deletes the temporary files and temporary directory."
Name: Fucking Small Engine
Creator/Origin: Rajaat
/ United Kingdom
AKA: FSE
Type: Polymorphic Engine
Known versions:
FSE - Unknown
Features:
Unknown. Made by the author of LPE.
Name: Funky Opcode Generator
Creator/Origin: Eclypse / Australia
AKA: FOG
Type: Mutation Engine
Known versions:
FOG 1.0 - July 1995
Features:
Mutation engine included in VLAD Magazine #5. Four of it products were included by the author. The engine is configurable and is capable of including junk instructions. The author quotes its vulnerability to heuristic scanners as one of its weaknesses.
Name: Golden Cicada Abnormal Engine
Creator/Origin: Golden Cicada / Taiwan
AKA: GCAE
Type: Polymorphic Engine
Known versions:
GCAE 1.0 - January 1995
GCAE 2.0 - January 1995
Features:
Joining the wave of polymorphic engines originating in Taiwan this one is created by someone who calls himself Golden Cicada. The engine looks similar to Dark Slayer's Mutation and Confusion Engine and could be from the same source. No viruses using the engine are known.
Name: Guns'n'Roses Polymorphic Engine
Creator/Origin: Slash Wu / Taiwan
AKA: GPE
Type: Polymorphic Engine
Known versions:
GPE 1.0 - February 1994
GPE 2.0 - Unknown
Features:
The Guns'n'Roses Polymorphic Engine is a newcomer, written by a person calling himself Slash Wu. Like the Dark Slayer Mutation Engine, this generator originates from Taiwan - and it only comes with Chinese documentation. In the generator's documentation, the author prohibits the use of the generator in viruses and other malicious software. He claims to have developed GPE solely for the purpose of protecting data and programs from unauthorised use. These claims are lent some credence by the fact that the author has included his apparently real name and phone number in the introductory notes.
So far, the generator is not known to have been linked to any virus. It's size is about two kilobytes.
Name: Great Permutation System
Creator/Origin: Tahorg / Unknown
AKA: GPS
Type: Permutation Engine
Known versions:
GPS - April 1999
Features:
Unknown.
Name: Gory Ruthless Opcode Generator
Creator/Origin: Wintermute / Spain
AKA: GROG
Type: Polymorphic Engine
Known versions:
GROG - September 1998
Features:
Together with RNME used in the Ithaqua virus by Wintermute. It was released in 29A#3.
Author's note:
"The MBR infection is polymorphic, due to my "Gory Ruthless Opcode Generator", which is a new about 600 bytes long boot-oriented poly engine, creating two encryption layers. The original MBR is encrypted and stored in sector two; maybe the most interesting thing about this poly engine is that it's so compact, as new instructions or instruction groups can be easily added to make a new polymorphic engine; also has some stack tricks that can only be done in a boot oriented engine."
Name: Hail and Kill Polymorphic Engine
Creator/Origin: Bumblebee
/ Spain
AKA: HKPE
Type: Polymorphic Engine
Known versions:
HKPE - April 1999
Features:
This simple polymorphic engine is the predecessor to BUME and is from the same author.
Name: Hatred Polymorphic Engine
Creator/Origin: T-2000 / Invaders
AKA: Hatred
Type: Polymorphic Engine
Known versions:
Hatred 0.92B - June 1998
Hatred 0.99B - June 1998
Features:
Author's note:
Instead of the obvious dummy-instructions this engine produces standard codefragments. Therefore the constant signatures will be larger, but they will also be found in normal clean programs. The codefragments can vary from standard codingstyle, to codefragments of common programs (including compression-programs like PKLITE & EXEPACK).
It only generates short JMPs forwards with legal instructions between them.
With the garbage-generator disabled it can probably be detected with a wildcard search. There will be 5 constant bytes in the decryptor.
This isn't a engine like SMEG which generates a enormous amount of instructions, it only generates some simple garbage, NOT those stupid obvious one-byte dummy instructions! Also forward JMPs.
It also isn't some complex engine like DAME, but It'll get the job done, at that's what counts.
Name: Huge Overhead Polymorphic Engine
Creator/Origin: 1nternal / Australia
AKA: HOPE
Type: Polymorphic Engine
Known versions:
HOPE 2.0 - January 1998
HOPE 2.1b - February 1998
HOPE 2.2b - February 1998
HOPE 2.3b - February 1998
HOPE 2.4b - February 1998
HOPE 2.41b - February 1998
HOPE 2.5b - March 1998
HOPE 2.51b - March 1998
HOPE 2.52b - March 1998
Features:
According to the author this engine was created for generic purposes, but it can be used for viral purposes. Looking at his HISTORY.TXT it was tested against TBAV's heuristic features. It can be found here [March 1998].
Author's note:
"HOPE uses advanced modulartiy to incorporate techniques from various other polymorphic engines into one complete engine. Standard polymorphic engines either choose from many skeleton encryptor/decryptors to use or greatly modify one decryptor / encryptor, and of course they all use junk instructions. HOPE uses all of these methods and is more powerful in each area. It chooses a random module to use from each of the four sections of a decryptor/encryptor.
- Initialisation Modules
- Counter Modules
- Encrypting Modules
- Loop Modules
Interspersed between each section is a random junk module. This in itself isn't too complicated, but there is more to it. Each module, including the junk modules are headed by certain codes which tell HOPE how the module can be modified, see the codes definition text for a rundown of the codes available to modules. This means the HOPE engine is a kind of parser for polymorphic modules which may be linked in, it then constructs a skeleton and then further mutates this. For instance there are codes to tell HOPE where to insert a random unused register, where an instruction may be reversed, as in the MOV ev,rv instructions, where som junk code may be inserted and so on. There is no need for a sliding key module as the junk modules can modify the register being used as the seed, creating a very unique slide in the key with each decryptor/encryptor. Don't think that HOPE's polymorphism is based just on the selection of modules. The actual mutation of each decryptor/encryptor using a fixed set of modules is very good and superior to most other engines due to my good understanding of the opcodes and x86 instruction set. To write your own modules you too should have a good (bitwise) knowledge of the instruction set such as the layout of Mod/rm bytes and first opcode bytes etc."

Also see: SLIM
Name: Inconstant Decoding Algorithm
Creator/Origin: Serg Enigma / Russia
AKA: IDA
Type: Polymorphic Engine
Known versions:
IDA 0.01 - Unknown
Features:
Unknown. Used in the IDA.1490 virus and created by the author of the SEEG engine and viruses.
Name: Internal ENCryptor
Creator/Origin: Billy Belcebu / Spain
AKA: IENC
Type: Encryption/Decryption Engine
Known versions:
IENC 1.0 - September 1999
Features:
Released with Xine #4 and used in the Legacy virus by the same author. It works in conjunction with MMXE and PHIRE.
Author's Note:
"The Internal ENCryptor is a RDA encryptor/decryptor that brings you the possibility of encrypt/decrypt blocks of code inside the virus itself. It's very simple,besides that is very useful for annoy a bit more the AV people. And that is my target."
"It's another engine included in Win32.Legacy. This one encrypts only the code you wnat to use when you want to use. the result is that, even when the poly code has decrypted all the virus body, there are still a lot of code blocks encrypted with different keys, and the keys aren't stored. The decryption of those blocks is made by a simple RDA 8-bit loop, because we've stored previously the CRC32 of the code."
Name: Intruder
Creator/Origin: Ivan Hammer
AKA: ---
Type: Boot Sector Virus Dropper Tool
Known versions:
Intruder 3.0 - July 1993
Features:
Similar to other such tools this program can insert boot sector viruses on diskettes. It also offers the capabi;ity to clean those diskettes. In comes with 6 boot sector virus images: Stoned, Ping Pong, Michelangelo, Aircop, Antitel and Brain.
Name: Intelliqent Slow Polymorphic Engine
Creator/Origin: Lucky / Germany
AKA: ISPE
Type: Polymorphic Engine
Known versions:
ISPE 1 - March 1999
ISPE 2 - April 1999
ISPE 3 - June 1999
Features:
Unknown. Version 3 is meant for use in a 32-bit environment.
Name: Jackie's Stupid Macro Poly
Creator/Origin: jackie twoflower / Austria
AKA: JSMP
Type: Polymorphic Tool
Known versions:
JSMP 0.3 - Unknown 1999
JSMP 0.4 - Unknown 1999
JSMP 1.0 - Unknown 1999
JSMP 1.1 - July 1999
JSMP 1.2 - November 1999
Features:
Tool to decrease detectability of macro viruses. It exchanges variable names in the viral code after every infection. Version 0.4 was also released with LineZero Zine #2.
Author's note:
"A very fast variable changing polymorphic module for VBA. Its is part of CMK 1.0"
Name: Jackie's Simple Poly for VBS
Creator/Origin: jackie twoflower / Austria
AKA: JSPV
Type: Polymorphic Engine
Known versions:
JSPV - Unknown
Features:
Unknown. Polymorphic engine for use in VBS viruses/worms. Released with Metaphase Zine #2.
Name: Jackie's Ugly Macro Poly
Creator/Origin: jackie twoflower / Austria
AKA: JUMP
Type: Polymorphic Tool
Known versions:
JUMP 1.0 - May 1999
Features:
Author's note:
"A self thinking polymorphic module, which keeps its size in an acceptable range. The first polymorphic module for macro which has size control, the engine checks it's actual size and decrease if it needed."
It was also released with LineZero Zine #2.
Name: Jerk1N's Virus Scrambler
Creator/Origin: Jerk1N
/ UK
AKA: JVS
Type: Scrambling Engine
Known versions:
JVS 1.0 - February 1998
JVS 1.3 - February 1998
JVS 2.0 - June 1998
Features:
Author's note:
"The world's first Virus Scrambler (Which is polymorphic!) and it's 131 Bytes (Still smaller than all mutation engines). The engine is self encrypting so that's different everytime, However the virus, once scrambled, is always the same (This will be placed randomly in V2).
eg. Orig Code Scrambled Code {4D 6E} 77 3D (05 B7) 77 3D 9E AA |72 32| 9E AA {4D 6E} (05 B7) 8D <92 |72 32| 8D [73 09> [73 32] 77 32] <92 09> 77NOTE: Brackets show where the code has moved to"
Name: Köhntark Decryptor Generator
Creator/Origin: Köhntark / USA
AKA: KDG
Type: Polymorphic Engine
Known versions:
KDG 0.5 - Unknown
Features:
Generates relatively simple decryptor's, with a lot garbage including interrupt 21h call's. The decryptor is placed before the encrypted code.
The engine is included in K_Hate.1128, by the same author.
Name: Kewl Mutation Engine-32
Creator/Origin: Zombie / Russia
AKA: KME32
Type: Mutation Engine
Known versions:
KME32 1.00 - November 1999
KME32 1.01 - November 1999
Features:
32-bit compatible mutation engine (Win9x/WinNT, ring0/ring3) by the author of AZCME, ZCME, FIRE, PE and PGPME32.
Name: Köhntark's Recursive Tunneling Toolkit
Creator/Origin: Kohntark / USA
AKA: KRTT
Type:Tunneling Engine
Known versions:
KRTT 4.1 - August 1993
Features:
Author's description: "Kohntark's Recursive Tunneling Toolkit is an object module that can be linked to any virus. KRTT41 will get the DOS's original INT 21h / 2Ah / 13h, in most cases, and can turn your virus into a 'smart' one by warning about the possibility of strange AV software present in memory. Once DOS's original interrupts are found you can call them directly to memory freely, bypassing any AV software present in memory and infecting other files.The ability to locate DOS's original INT 13h is provided by KRTT to implement potentially destructive code. You could also use the original int 21h to allocate/free memory and disable any software present in memory. Such scenarios are
possible but they have not tested fully,so no claims can be made.
KRTT41's strength lies in a recursive nature which allows tracing and scanning through multiple hooked INT 21h's. KTTR41 is very small due to its recursive nature. And it is fast since it uses no memory locations for data storage; all the operations are done directly in the CPU registers.
KTTR41 is fully compatible with Trident's Polymorphic Engine Version 1.4 and future polymorphic engines."
See also:
Tunneling shortcuts.
Name: Lady Death's Cosmetic Kit
Creator/Origin: Dark Fiber / NuKE
AKA: LDCK
Type: Mutation Engine
Known versions:
LDCK - August 1995
Features:
Unknown. Used in the Lady Death virus by the same author.
Name: Length-Disassembler Engine 32
Creator/Origin: Zombie / Russia
AKA: LDE32
Type: Virus Programming Tool
Known versions:
LDE32 1.00 - December 1999
LDE32 1.01 - December 1999
LDE32 1.02 - March 2000
LDE32 1.03 - April 2000
LDE32 1.04 - May 2000
Features:
Author's Note:
LDE32 is a library which may be used to determine length of any x86 instructiion, i.e. to provide partial disassembling. LDE32 has only two subroutines.
1. void pascal disasm_init(void* tableptr);
This subroutine used to build internal data table of 2048 byte length.
2. int pascal disasm_main(void* opcodeptr, void* tableptr);
This subroutine used to disassemble one instruction. It returns length of instruction in bytes, or -1 if an error occured. Subroutines preserves all registers; code is offset-independent; no data used except 2k at *tableptr.
To include LDE32 into your source you should add the following line:
include lde32bin.inc
Name: Little ENcryptor/DEcryptor
Creator/Origin: Bumblebee / Spain
AKA: LENDE
Type: Anti Debugging Tool
Known versions:
LENDE - December 1999
Features:
Used in the Anvil Of Crom Virus by the same author released in 29A#4.
Author's Note:
" Contains a little trick that allows the virus to check if it's being debugged. If this occurs the virus hangs the process. But if the aver is good using the debugger, there is nothing to do. Due to this i coded LENDE. If the guy debugging modifies some code to avoid a check of the virus, he must restore the change 'cause other pieze of code is encrypted and the decryptor uses it as key of encryption. This is used to protect different parts of the virus i want unmodified. Moreover LENDE works as another layer of encryption."
"Trying to do the virus harder to analize i coded LENDE. 'Little ENcryptor/DEcryptor' allows to encrypt little piezes of the virus using the CRC32 of another part of the virus as key."
Name: Lord Julus' Huffman Compression Engine
Creator/Origin: Lord Julus / Rumania
AKA: LJHCE32
Type: Compression Engine
Known versions:
LJHCE32 1.0 - January 2000
LJHCE32 1.1 - January 2000
Features:
A 32 bit compression engine based on the Huffman compression algorithm. A demo using the engine was released with 29A#4.
See: Tutorials - Compression (Part I).
Name: Little Mutation Engine
Creator/Origin: Cybershadow / Russia
AKA: LME
Type: Mutation Engine
Known versions:
LME 1.0 - April 2000
Features:
Unknown. Used in the CesInf virus by the same author.
Name: Lamer's Macro Engine
Creator/Origin: Nasty Lamer & Ugly User / Slovakia
AKA: LME
Type: Polymorphic Engine
Known versions:
LME 1.0 - March 1997
Features:
Author's note:
"Dis is the first world true polymorphic macro !"The world's first full polymorphic engine for macro viruses for Word for Windows. While Pyro's Advanced Polymorphic Macro Replication System [APMRS], is the world's first polymorphic engine for Word for Windows 97, Lamer's Macro Engine v 1.00 is the first polymorphic macro engine and it can be found in WordMacro.SlovakDictator by the same authors.
Name: LordDark Mutation Engine
Creator/Origin: Lord Dark / Russia
AKA: LME
Type: Mutation Engine
Known versions:
LME 1.0 - Unknown 1999
LME 1.1 - Unknown 1999
LME 1.2 - Unknown 1999
LME 1.7 - February 2000
LME 1.8 - March 2000
Features:
Unknown. These engines, by the creator of MME32, were released with and used in viruses (Elf.2647, Elf.2731, Merlin) by the same author. Version 1.0 was released with DVL#9 while version 1.2 can be found in 29A#4. Newer versions are available on the author's website.
Name: LordDark Mutation Engine 32
Creator/Origin: Lord Dark / Russia
AKA: LME32
Type: Mutation Engine
Known versions:
LME32 0.9 -June 2000
LME32 1.0 - August 2000.
Features:
32 bit version of LME by the same author. Version 1.0 was released with Matrix Zine #2.
Name: Luna Poly Engine
Creator/Origin: Bumblebee / Spain
AKA: LPE
Type: Polymorphic Engine
Known versions:
LPE - Unknown 1999
Features:
Unknown. By the author of APE, BUME, BAGGRPE and HKPE. Originally written for a contest this engine was included in the W9X.Luna virus released in 29A#4.
Name: Ludicrous Poly Engine
Creator/Origin: Rajaat / United Kingdom
AKA: LPE
Type: Polymorphic Engine
Known versions:
LPE - Unknown
LPE bugfix - August 1998
Features:
Unknown. Made by the author of FSE.
Author's note: "This engine is only 50 bytes and generates very polymorphic code in respect to its size."
Name: Little ShittyCompression Engine
Creator/Origin: Billy Belcebu / Spain
AKA: LSCE
Type: Compression Engine
Known versions:
LSCE 1.0 - September 1999
Features:
Released with Xine #4 and used in the Thorin virus by the same author.
Author's Note:
"This is a very simple packing engine, based in the repetition of zeros that the PE files have, thus it is able to compress a PE file... Hehehe, i can put a dropper without caring about its space! That was the only reason of make this little shit. Maybe one day i will make a 'real' compression engi ne, but today i'm too busy :) "
Name: Lempel Ziv Compression Engine 32
Creator/Origin: Sexy Dufus / Russia
AKA: LZCE32
Type: Compression Engine
Known versions:
LZCE32 Original - May 2000
LZCE32 Improved - May 2000
Features:
Author's Note:
" I've looked inside most of the 32bit packing engines, and you know what i have found? They are suck. So, I decided to do something about it. Results of this one week research are presented below. And that is...
LZCE32 - LEMPEL-ZIV 32BIT COMPRESSION ENGINE
It contains two routines:
lz_compress (347 bytes) and
lz_decompress (365 bytes)Features:
+ all code and data are delta-independent
+ much better compression than huffman or RLE packing
+ no signatures, copyrights or other pathetic shit is placed into the output buffer. it contains just data, data and nothing more.
+ ready to use "
Name: MBOP
Creator/Origin: [K]alamar / Argentina
AKA: --
Type: Polymorphic Engine / Routine
Known versions:
MBOP - July 2000
Features:
Polymorphic routine used in the viruses by the same name. A slightly altered version was used in Mbop.C after Mbop.A and Mbop.B were detected by AV software. By the author of VBSWG.
Author's note (Mbop.A):
"About the Poly engine:
It's new stuff that i created.
As you can see in the source code below, the word mbop is in all the variables, before and after he two letters that are the variable name.
The trick is that the virii creates a random word of 15 char. and replace it all the times that is shown in the virii, so the virus changes really a lot, and some times more than 2 or 3 times in the same line.
I expect that the Av softwares are not going to be able to detect it, I HOPE; but if they detect it, i will made a new one, ;o)."
Name: Macro Crypted Polymorphic Realistic Antiheuristic
Code Engine
Creator/Origin: Cybershadow / Russia
AKA: MCPRACE
Type: Encryption Tool
Known versions:
MCPRACE 2.0 - November 1999
Features:
Similar to many other tools (ME/U, ME/D, VVSC, RPMCE) MCPRACE uses encryption, polymorphism and antiheuristic techniques to decrease detection of macro viruses. It was released with DVL #9.
Name: MDevice
Creator/Origin: Unknown / SVL
AKA: --
Type: Polymorphic Engine
Known versions:
MDevice - February 1996
Features:
Unknown. This polymorphic engine originated in Slovakia, was released by SVL and is used in several Slovakia viruses. It contains anti-debugging code that will not work with Pentium computers.
Name: Multi Decriptor Poly Engine
Creator/Origin: Nigro / Spain
AKA: MDPE
Type: Polymorphic Engine
Known versions:
MDPE - May 1999
Features:
32-bit polymorphic engine released in DDT #1. Created by the author of NEP.
Name: Macro Encryptor
Creator/Origin: Ultras / Russia
AKA: ME
Type: Conversion/Encryption Tool
Known versions:
ME 1.0 - July 1998
ME 1.0c - August 1998
Features:
Similar to VVSC, ME/D, MCPRACE and RPMCE this tool by the creator of UCK, UAMP, UMPE, ZSZPE and UMP encrypts clear text in macro viruses. ME 1.0c was released with DVL #9.
Name: Macro Encryptor
Creator/Origin: Deviator / Ukraine
AKA: ME
Type: Encryption Tool
Known versions:
ME 1.0 - July 1999
Features:
Similar to ME by Ultras this tool uses encryption and heuristic techniques to decrease detection of macro viruses.
Name: Mutating deCryptor Generator?
Creator/Origin: Doctor Revenge / Italy
AKA: MCG
Type: Polymorphic Engine
Known versions:
MCG 0.31ß - May 1994
Features:
Generates several parts of garbage, much like Bomber and the OneHalf family, which passes the control to the decryptor, which is placed before the encrypted code.
The engine is included in PeaceKeeper, by the same author.
Third party analysis:
"The poly itself is quite simple (but it wasn't for the times the virus was actually written). It generates decryptors that can use ADD/SUB/XOR math operations on either bytes or words with a fixed encryption key as immediate. The counter register is fixed to CX, while the pointer can be either SI or DI, that can be also associated with a fixed offset (ie. [DI + 100h]). There are two ways to create the loop check for the decryptor, using a LOOP instruction or by just using the DEC CX with a counter check. It is interesting that most of the exact structure of the decryptor is already decided at the poly calling time in the register with decryptor flags, this is BL. Most of the poly is written using tables. The assignation of the registers infact (counter and pointer one) is done by selecting one of the four possible constructs from an offset table that are quite simillar and have all the same task to assign a given value to the given register (look at comments in code for the exact structure of each of this code blocks). As for the incrementation of the pointer there are a few possibile ways to do the work, depending on the used register infact a SCASB or CMPSB (or word if encrypting by words) could be used instead of the more usual INC. As for garbage there are 7 different types of garbage generation routines (tables are used here aswell) that generate usual one byte instructions, some assignment and logical instructions, conditional jumps and comparations between registers or between a register and an immediate. Garbage instruction can be either 16bit or 8bit ones. All the garbage generated doesn't affect in any way any of the registers (infact only logical operations between the register and itself like OR and AND are used), except flags, so the poly doesn't have to keep reference of which registers must be preserved or which registers have been changed during the decryptor. This of course makes the garbage generation easier to manage, but on the other side makes the possible generated garbage very reduced and generated instructions are not likely ones that could be found in a normal program, since they don't act on the registers at all. "
Name: Mass Destruction Library
Creator/Origin: Evil Avatar
/ USA
AKA: MDL
Type: Destructive Routines
Known versions:
N/A
Features:
A collection of 9 routines which can be incorporated in virus source codes that do not contain any payloads. Used in the LAVI virus creator.
Name: Mental Driller Polymorphism Engine
Creator/Origin: Mental Driller
/ Unknown
AKA: MeDriPolEn
Type: Polymorphic Engine
Known versions:
MeDriPolEn 0.1 - December 1998
Features:
The engine is used in the Squatter viruses by the same author. It was released in 29A#3.
Author's note:
"The created decryptor contains CALLs, un/conditional JMPs with non-zero displacement, conditional JMPs to invalid code, anti-emula- ting and anti-debugging code, indexed memory writes and LOTS of weird 8/16/32 bit garbage, including coprocessor ones with memory read/write instructions. "
Name: Mutation Engine For MIRC
Creator/Origin: Mongoose
/ Russia
AKA: MEFM
Type: Mutation Engine
Known versions:
MEFM 0.05 - December 1999
MEFM 0.06 - December 1999
Features:
Unknown. An assembler written mutation engine for MIRC script viruses (worms).
Name: Mutation Engine for Mad
Creator/Origin: Black Angel / Russia
AKA: MEM
Type: Polymorphic Engine
Known versions:
MEM 1.0 - September 1996
MEM 1.1 - November 1996
Features:
Unknown. These engines are included in the MAD 1.6 and 1.8 viruses, by the same author.
Name: MutaGen
Creator/Origin: MnemoniX / USA
AKA: MGEN
Type: Polymorphic Engine
Known versions:
MGEN 0.90B - February 1994
MGEN 0.95B - February 1994
MGEN 1.00 - March 1994
MGEN 1.10B - April 1994
MGEN 1.10 - April 1994
MGEN 1.20 - May 1994
MGEN 1.30 - June 1994
MGEN 2.00 - July 1994
Features:
In the beginning of 1994, a new author entered the stage. Calling himself MnemoniX, this American virus writer proudly presented a new generator called MutaGen. Each successive version is more complex than the previous ones. In MutaGen's documentation, MnemoniX criticizes the other polymorphic generators for being too unreliable and easy to detect.
The author's revision history:
0.80B 1/94 - personal release
0.90B 2/94 - first offical beta test version released. Sometimes scanned as TPE, contained minor bugs.
0.95B 2/94 - fixed bugs & made less scannable.
1.00 3/94 - first official version. Functionally perfect, as far as I can see.
1.10 4/94 - Added more variability in code and optimized existing code. Also added another demonstration virus.
1.10B 4/94 - Fixed protected mode bug, I think. (Thanks Memory Lapse)
1.20 5/94 - Improved code yet more, added more power & polymorphism. (Also, the first demo virus no longer scans as Ash.)
1.30 6/94 - Optimized some code and added more weird twists and turns in the code.
2.00 7/94 - The definitive version. If there is a next version, it will simply be smaller.
Name: Mild Mutation Engine
Creator/Origin: JHB /
Italy ?
AKA : --
Type: Mutation Engine
Known versions:
MildMut - October 1996
Features:
Unknown. Released with issue #1 of the E-zine Xine released by the HPACV group International Knowledge eXchange.
Name: MIni Mutation Engine
Creator/Origin: ArChung Lai / Taiwan
AKA: MIME
Type: Polymorphic Engine
Known versions:
MIME 1.0 - December 1994
Features:
Joining the wave of polymorphic engines originating in Taiwan this one is created by someone who calls himself ArChung Lai. No viruses using the engine are known.
Name: Multi Layer Coder
Creator/Origin: Lord Asd / Unknown
AKA: MLC
Type: Mutation Engine
Known versions:
MLC 2.0 - July 1996
Features:
Unknown. Used in the Apparition II virus, co-authored by Stainless Steel Rat.
Name: Metamorphic Mutation Engine 32
Creator/Origin: Lord Dark / Russia
AKA: MME32
Type: Mutation Engine
Known versions:
MME32 - Unknown 1998/9
Features:
Unknown. Published / released in Issue #11 of the Moonbug E-Zine. It was used in the W95.Merinos virus by the same author.
Name: Mayhem Mutation Engine
Creator/Origin: Unknown / Ukraine
AKA: MME
Type: Mutation Engine
Known versions:
MME 1.1 - July 1995
Features:
Unknown. Published / released in Issue #7 of the Infected Voice E-Zine.
Name: MetaMorphic Generator
Creator/Origin: ML / Unknown
AKA: MMG
Type: Polymorphic/Mutation Engine
Known versions:
MMG 1.0 - December 1995
Features:
Unknown. The engine is included in the Lightning.4251 virus
Name: MultiMedia eXtensions Engine
Creator/Origin: Billy Belcebu / Spain
AKA: MMXE
Type: Polymolrphic Engine
Known versions:
MMXE 1.0 - Unknown
MMXE 1.01 - September 1999
MMXE 1.02 - Unknown
MMXE 1.2 - Unknown 2000
Features:
Version 1.01 was released with Xine #4 and used in the Legacy virus by the same author. It works in conjunction with PHIRE and IENC. Version 1.2 is used in the Win32.Forever virus by the same author.
Author's Note:
"This engine will generate two decryptors, that will be able to decrypt the first encryption layer of the virus (but the only one that is polymorphic). Why two decryptors? Well, the execution of one or another depends of the existence of the MMX opcodes (i.e. if the CPU is MMX). One of them, the one that will be executed firstly, has MMX opcodes used as gar bage, and its decryption operation is also a MMX opcode. The second decryptor is an 'usual' polymorphic one. "
"This engine was build after an idea i had when playing with copro opcodes at Win9x.PoshKiller virus. I thought that copro opcodes weren't emulated by any AV, but i was wrong, as someone told me that DrWeb emulates them. So, in an attack of madness, i decided to make a poly using something that any known emulator could be able to emulate, and there were the MMX opcodes. The result was this engine. It builds all the normal garbage opcodes, and it also generates in its MMX part a lot of MMX opcodes used as garbage (almost all the MMX opcodes). But don't believe what AVP says, IT WORKS IN NON-MMX MACHINES. This is because i check polymorphically if the chip supports MMX opcodes, and if not, it jumps to a NON MMX decryptor. So there aren't problems with old machines. It was included in Win32.Legacy virus. The decryptors' size are always 2k. Version 1.01 was the released in that virus, it had a bug fixed from previous version. The version 1.02 has a much more enhaced garbage generator, and it's almost 1K bigger than 1.01 version. The generated decryptors by it are much bigger, 4K each one."
Name: Multiple OpCode Fantasies
Creator/Origin: Lord Julus / Rumania
AKA: MOF
Type: Polymorphic Engine
Known versions:
MOF 0.1B - April 1998
MOF 1.0 - May 1998
MOF 2.0 - May 1998
MOF 3.0 - May 1998
MOF 4.0 (MOF32 0.99) - March 1999
Features:
MOF 4.0 is the 32-bit continuation of the MOF project.
Author's note (16-bit):
"Hi ! This is the official Comment of the author on behalf of his poly engine. This engine will scramble the given Code using one of the three operations: Xor, Add, Sub. As you noticed, the encrypted Code may be different from the entire Code processed by the engine Into it`s Buffer, giving more flexibility. After the Code is copied, the part to be encrypted is encrypted using a random Key. After that, the poly decryptor is generated. Basicly, the decryptor will hook an interrupt (15/19/12,etc) And set it`s vector to a special routine. This routine will provide decryption during the decryption phase. The registers used here are ax, bx, cx, dx, si, di. Each of these can hold the Code, Key, Counter. Also, bx, di, si can be used to point Into the Code. The engine chooses randomly one of these leaving 2 junk general registers And 1 junk pointer register. Between the real intructions of the decryptor, the engine will generate a random number of junk instructions. These instructions may contain also jumps, calls to fake routines, interrupt calls And privileged instructions. Also, many instructions that `look` like the ones inside the decryptor, so it`ll be very hard to find the real instructions."
See also some tutorials on the virus infection subject by the same author.
Name: Multiple OpCode Fantasies 32 bit
Creator/Origin: Lord Julus / Rumania
AKA: MOF32
Type: Polymorphic Engine
Known versions:
MOF32 0.99 (MOF 4.0) - March 1999
MOF32 2.5 - August 1999
Features:
MOF32 is the 32-bit continuation of the MOF project.
Name: Metamorphic Mutation Engine
Creator/Origin: Stainless Steel Rat / Russia
AKA: MME (SSR)
Type: Polymorphic Engine
Known versions:
MME 2.0 - April 1996
MME 3.0 - 1997
Features:
Unknown. The engine is included in SSR.18273,18364, by the same author.
Name: Mesomorph Mutation Engine
Creator/Origin: Werewolf / Unknown
AKA: MME (WW)
Type: Polymorphic Engine
Known versions:
MME - 1995
Features:
It uses OB (On-fly Bit) decryptor generating technology for better polymorphic level and it uses Jumps, AntiWEB, AntiDebug, Wise Fragments, Dummy instructions, Calls (Subroutines) and AntiTBAV techniques.
Name: Mini Polymorphic Engine
Creator/Origin: Kiminwoo
/ Korea
AKA: MPE
Type: Polymorphic Engine
Known versions:
MPE 0.01 - February 1997
MPE 0.02 - February 1997
MPE 0.02 (bugfix) - July 1997
Features:
Published / released in Issue #1 of the CVC Magazine. The bugfix version of 0.02 was released with Issue #2 of CVC Magazine.
Third party analysis of MPE:
MPE can be considered a hack of the Small Polymorphic Engine [SPE]. This hack hasn't been improved, on the contrary this polymorphic engine is a lot worse than the original. The differences between Mini Polymorphic Engine [MPE] and Small Polymorphic Engine [SPE], are as follows:
- Both versions of the Mini Polymorphic Engine [MPE] is vulnerable to the X-Ray technique (cryptoanalysis). Small Polymorphic Engine v 0.01 [SPE] is less vulnerable, but still vulnerable and Small Polymorphic Engine v 0.02 [SPE] ain't vulnerable.
- All decryptor's generated by Mini Polymorphic Engine v 0.01 [MPE] is of equal size. All decryptor's generated by Small Polymorphic Engine v 0.01 [SPE] is of random size.
- Mini Polymorphic Engine v 0.01 [MPE] has seven stable bytes, Small Polymorphic Engine v 0.01 [SPE], has a single stable byte.
- Both versions of the Mini Polymorphic Engine [MPE] is not EXE infection compatible, both versions Small Polymorphic Engine [SPE] is.
- Both versions of Mini Polymorphic Engine [MPE], is far from being as optimized as both versions of Small Polymorphic Engine [SPE].
- The size of the different versions of the different engines is as follows:
- Mini Polymorphic Engine v 0.01 [MPE] size: 229 bytes.
- Mini Polymorphic Engine v 0.02 [MPE] size: 366 bytes.
- Small Polymorphic Engine v 0.01 [SPE] size: 380 bytes.
- Small Polymorphic Engine v 0.02 [SPE] size: 1273 bytes.
Name: Monster Polymorphic Engine
Creator/Origin: LordAsd / Unknown
AKA: MPE
Type: Polymorphic Engine
Known versions:
MPE 1.0 - September 1997
Features:
Unknown. A HLL polymorphic engine written for C++.
Name: Mutation Engine
Creator/Origin: Dark Avenger / Bulgaria
AKA: MtE
Type: Polymorphic Engine
Known versions:
MtE 0.91B - August 1991
MtE 1.00B - April 1992
Features:
One of the first of the polymorphic generators Dark Avenger's Mutation Engine started a new way of virus writing sending the AV producers back to the drawing board to find the solution to what looked like an insurmountable problem. Though revolutionary in its time, Mutation Engine is currently somewhat outdated. Practically all anti-virus products can detect MtE-hidden viruses. Nevertheless, MtE continues to be a source of inspiration for people aspiring to write polymorphic generators - for example, many generators written after MtE mimic the documentation provided with MtE.
See also:
MtE review
Name: Multiformer
Creator/Origin: Fulvian
/ Indonesia
AKA: --
Type: Polymorphic Engine
Known versions:
Multiformer - Unknown 1999
Features:
Used in the MIA.9000 virus by the same author, released with 29A#4.
Author's Note:
"This polymorphic engine is a development of existing engine created by GriYo (29A) that has been implemented on CRI-CRI and IMPLANT.6128 virus. So, a ton of thanks go to him."
Name: Mutator
Creator/Origin: Lapidario / Argentina
AKA: Mutator
Type: Polymorphic Engine
Known versions:
Mutator 1.0 - November 1994
Features:
The 1774 byte long Mutator has been released by Lapidario, a member of the Argentinian virus group "Digital Anarchy" (DAN) and was included in one of their magazines.