

Fravia's Anonymity Academy
Fravia's
STEGANOGRAPHY
(STARTING PAGE)
Updated September 1998
(Only basic readings and a sieve: my tricks are elsewhere)
How to hide information effectively
~
Cracking steganographical algorithms
Easy entrance to Advanced stenography provided
by Tsehp
 Courtesy of Fravia's page
of reverse engineering
Courtesy of Fravia's page
of reverse engineering
Files related with this section
(related essays from my software reverse engineering section)
Well I remember a beautiful essay by Frog's print about
something related with steganography: Watermarking of digital images, here it is:
 PhotoShop 4.0 / Digimarc
Commercial stupidity - Digimarc downfall where you'll be able
to see how easy it is to reverse some 'very heavy' (and expensive) watermarking
commercial
applications, like Digimarc. If you are interested in Watermarking problems, you'll find on
the web watermarking tools and tools to 'unwatermark' images (like Unzign and Stirmark).
PhotoShop 4.0 / Digimarc
Commercial stupidity - Digimarc downfall where you'll be able
to see how easy it is to reverse some 'very heavy' (and expensive) watermarking
commercial
applications, like Digimarc. If you are interested in Watermarking problems, you'll find on
the web watermarking tools and tools to 'unwatermark' images (like Unzign and Stirmark).
How to reach Fravia's 'advanced steganography'
pages, the hard way
Jean Flynn's "A Journey within Steganos" ('light' version)
10 february 1998
__NEW__
How to reverse engineer Steganos (First step)
Mrf's "Speed up brute force cracking"
13 february 1998
__NEW__
I'll add here more essays as soon as you start writing them. Some short essays about
advanced steganographical
cracking (cracking of the steganographocal algorithms themselves of course, not
of the software programs to perform steganography, which, as you will see, are all
either not at all or ridicously protected :-) are or will be asap
in the 'advanced steganography' page of mine (see below).
Of course we are
a little 'cheating' here. In order to crack at ease you'll get the ORIGINAL
image used as carrier (something you won't get in real life) and I have used
very easy password options, as you'll see.
Reasons for this section
Well, I have received so many questions about steganography, after having written
inside my revamped anonymity academy page the
following...
Morale: keep your sensitive data ON THE WEB somewhere where nobody
in his right mind would ever look, nor understand them even if he did
(say steganographed inside the dull images of a bogus page like "me
and my little dog Barkie" :-) they will be MUCH more safe there than
inside your own harddisk!
...that I realized that many among my readers
don't even know the most elementary basic of hiding (and/or retrieving hidden)
data on the web and elsewhere...
Yet hiding (and retrieving hidden :-) data
is a VITAL question, on the web and in life,
when so many people are
continuously (and increasingly) trying to get their hands on your money/convinctions/future
through your data, using all known
tricks of the books (and some less known ones as well, as +ORC explains in his slaves
of the supermarkets famous essay... btw there are some passages about
steganography itself in his "6" lessons, if
I'm not mistaken)
So, dear reader, just do what you're supposed to do anyway: READ! In fact I believe
you better read and
head the following, and then start your own studies on this matter as soon
as you'll be able to.
Unfortunately, for
once, this time I will and cannot explain too much publicly (because I'm actually
using
myself quite a lot of the tricks I have to describe) yet I want to explain everything
nevertheless: the whole idea of my site is that knowledge should be passed on to
anybody who cares... but i need a 'sieve' in order to see if you really care... I
have taken the idea from
+ORC's famous gates, and it works!.
Hope you'll understand me: lamers
and leechers must be
kept somehow away, at least for a little while, else they will immediately start
using the same tricks
'en masse' for some stupid purpose and spoil the game for me and all other
real +crackers around.
So this page is and will remain only a 'start' platform. Don't be deceived!
You'll get on this very page enough information to
make you happy, and you will be able to deepen it and work on it at leisure
(and this page will be updated, and you'll always find a lot here)... yet you
WILL NOT get to the advanced steganography page, unless you crack the BMP and GIF
images that you'll find on this page.
This should sieve lamers and leechers out, I hope.
Purpose of the sieve
The sieve has another purpose: to teach you how to reverse the algorithms used by
the main steganographical applications (admittely using the softer forms of
encryption allowed, in order to 'offer you the throat' for your attacks :-)
You see:
this is a reverse engineering site (may be THE reverse engineering
site :-) and
you'll therefore now begin to use some of the techniques that you
have learned reversing and cracking
software in order to proceed further.
Yes. You won't be able to go further without having studied (at least a little),
+ORC's tutorial and his students' essays, in other words: you need to know (at least a
little) how to reverse engineer software in order to understand many other aspects
of the web, inter alia steganography (but I think you'll be thankful that you did learn
our techniques: I reckon that this is more and more useful
regarding life in general as well... without reverse engineering knowledge you are only
a Guinea pig for the commercial slaughtering powers of our disgusting
society). So let's start cracking, and working, and getting onwards...
Let's not forget what +ORC wrote:
"...I need your knowledge
as much as you need mine, so build some and start contributing..."
right so! And this applies here as well,
you'll therefore have to perform some 'applied steganographical cracking':
An easy first step (I will use as 'bait' some secret locations on the web)
where you'll have to crack either the algos used by CONTRABAND (version 9g) for BMPs images
or those used by
Hide and seek (version 4.1) for GIF's images.
A less easy second step (I will use as 'bait' the location of
the 'advanced steganography page'). Here you'll have to crack the algos used
for BMP files by Steganos for windows 95 (version 1.0a).
Ah yes, a last thing: as images I'll use only Tamara de Lempicka's pictures... you may not be excused for not knowing
her paintings and this will remind you that
there are other things to reverse in life (like culture, duh :-)
Fravia's
STEGANOGRAPHY STARTING PAGE
The word steganography is derived from greek and means "coverted writing", from
stegein, to cover... the same root as in Stegosaur, a quadrupedal, herbivorous
ornithiscian dinosauar of Jurassic films and early Cretaceous times, well
known for being quite 'covered' through an armor of triangular bony plates on
his back spine.
Steganography is the art (and science) of communicating hiding THE EXISTENCE of
communication, in contrast with cryptography. Ideally, your enemies, or the one
you are fighting against, or even your friends, should not even imagine
that there IS a message
concealed somewhere.
This very characteristic makes steganography the IDEAL
science for hiding messages on the web, which is flooded by non-significant
data. Your whole passwords and everything you need can without any problem be
hidden inside three or four 'fake' pages you'll have uploaded somewhere, with
images like 'my sister Sally and his favourite banana fishes' or whatever.
You
will download all fake images from the web (geocities page are a never ending source
of incredibly dull lifes and fotographies :-), you will MODIFY them (the greatest
risk for steganography is the confrontration between 'original' image without
concealed message and steganated image with message, of course), and only after
these modifications you will hide your concealed message inside them with one of
the many programs that you'll find around.
Basically, using steganography, you can smuggle any file(s) over any
communication-line (BBS, network, modem, diskmail, etc.) in a format
which leaves the smuggled data untraceable and unreadable.
Here you have a link to my own copy of a BMP graphic format stegonograpical
utility:
 CONTRABAND (version 9g, by Hens Zimmerman and
Julius Thyssen... their web location is:
http://www.GalaxyCorp.com/009 or,
alternatively, http://come.to/us. It's freeware,
so there is nothing to crack. In my own copy you'll find also THE COMPLETE SOURCE
CODE (in Borland C++ 4,5) of Contraband, which may be of interest for you.
CONTRABAND (version 9g, by Hens Zimmerman and
Julius Thyssen... their web location is:
http://www.GalaxyCorp.com/009 or,
alternatively, http://come.to/us. It's freeware,
so there is nothing to crack. In my own copy you'll find also THE COMPLETE SOURCE
CODE (in Borland C++ 4,5) of Contraband, which may be of interest for you.
Here you have a link to my own copy of a GIF graphic format stegonograpical
utility:
 Hide and Seek (version 4.1), by
colin maroney. It's freeware,
so there is nothing to crack. In my own copy you'll find also
THE COMPLETE SOURCE
CODE (in Borland C++ 3.1) of Hide and Seek, which may be of interest for you. In
general I love working with programs (and onto programs) I have the source
code of. In fact, I like it so much that if I really use a program and do not have
the source code I re-create it myself reversing the whole bazaar, or at least
the parts I need or fancy to change...
Hide and Seek (version 4.1), by
colin maroney. It's freeware,
so there is nothing to crack. In my own copy you'll find also
THE COMPLETE SOURCE
CODE (in Borland C++ 3.1) of Hide and Seek, which may be of interest for you. In
general I love working with programs (and onto programs) I have the source
code of. In fact, I like it so much that if I really use a program and do not have
the source code I re-create it myself reversing the whole bazaar, or at least
the parts I need or fancy to change...
I'm sure therefore that you'll
appreciate the presence of the source code for BOTH programs, this will allow you
to delve pretty deep inside all mysteries and vagaries of our applied and
advanced stegonography.
You may find A LOT
more UNIX source code here
Now try cracking these images! (a first easy step)
I will give you a "bait" in order to pull your reversing capacities, Let's start with
a bmp image... you'll have to perform here an (easy) crack of CONTRABAND (version 9g)
Here you have two zipped bmp(s) images with a famous picture from
Tamara de Lempicka: Andromeda. You may download the  original
andromeda and the
original
andromeda and the  stegonated andromeda.
stegonated andromeda.
Both images have been zipped (from bmp format)
Unzip them and have a look.
You wont spot any differences, yet inside the second one I have
hidden -using contraband- a small text file: secfiles.txt which was only
587 bytes long.
Inside secfiles.txt, if you ever reverse it 'out' of the BMP image, you'll
be able to find
a LIST OF SOME SECRET LOCATIONS of files on the Web, files that you may
find interesting and locations which are not given
anywhere else inside my sites.
I'm sure that you will probably enjoy some of those files... well, you
won't get them unless you crack the stegonated bmp picture above :-)
Now try cracking these images! (a second easy run)
I'll offer another run -this time in gif format- to the reversing capable among my readers:
Here you have two copies of the famous Andromeda by Tamara de Lempicka:
 ~
~

the original
Andromeda and the 'stegonated' Andromeda.
This time you have the two GIF images above, and the same file as above (587 bytes
long) has been
hidden inside
the 'stegonated' GIF using hide and seek version 4.1.
I used a very short and easy to crack (4 numbers)
encryption key (the same used for the 'contraband' bmp(s) above, by the way), so it's a
very easy brute force attack, yet you can crack this in a more 'zen' way, as you'll see,
later, when you arrive to my advanced steganography page.
Inside secfiles.txt, if you ever reverse it 'out' of the GIF image, you'll find
a LIST OF SOME SECRET LOCATIONS of files on the Web, locations
which are not given anywhere else inside my sites.
Well... crack this one instead of the previous one, if you prefer :-)
Come on... you should manage it... and anyway I believe you'll find it a
worthy approach to steganographycal cracking!
Inside the steganographed images above you'll NOT find as an added bonus
the location of my
'advanced steganography academy' pages, which are NOT linked from my 'common'
sites, nor dwell on this server. You'll find some 'secret' files, tough, as I said,
and you'll find it relatively EASY to crack. In order to reach my advanced
steganography pages you'll have to crack the two BMP pictures at the BOTTOM
of this page.
See you there!
A little steganographical history
You'll find it on the History of Steganography ad hoc page.
Additional Information
WARNING: The following has been pilfered from a
VERY GOOD PAGE:
http://members.iquest.net/~mrmil/stego.html
I'll slowly modify and add links here as time goes by, for the following information you
should not thank me, but
Eric's Milbrandt Home Page
(hope Eric wont mind)
- A brief History and Discussion (Michael Sattler)
- Steganography, a detailed scientific paper covering the history and theory behind steganography. Includes evaluations of
many of the available stego programs.
- The Annotated Stego Bibliography with references and links to specific articles in scientific journals.
- Mimic functions, another type of steganography.
- Copywrite protection of digital images with Highwater's FBI.
- Covert Channels in the TCP/IP Protocol Suite__NEW__
A paper
concerning methods of encapsulating concealed data within the
headers of the TCP/IP protocol suite. Includes functional Linux compatible
source code
to take advantage of this interesting area.
- Weakness in Watermarking and Steganography Tools __NEW__
Software is now available to alter the extra information stored
in images, making it possible to test the robustness of watermarking
technologies as well as to erase stego'd info from images.
Watermarking Weakness - discusses attacks on the current software
Unzign - unmarking software (Win 95 and Linux versions)
Stirmark - unmarking sofware (several versions available)
- Other Useful Stego Pages
Neil F. Johnson - Papers, Links, and Software
Bob Tinsley - Steganography and Watermarking
WEPIN Store - Definition and Discussion
Tools for Privacy - Excellent Historical Review
Preston Wilson - Ranks the Stego Programs __NEW__
Steganography Downloads
Windows
- Hide and Seek for Win95 (96k) __NEW__
- Hide and Seek for Windows 95 is a BMP-based steganography program by Colin Moroney, the author of the dos versions of Hide and Seek.
This version is a considerable step up from his previous efforts. Its professional-looking interface
makes it easy to use. The file wiping options and blowfish header encryption method are added bonuses. Unfortunately,
downloads are ITAR restricted, however, a 40-bit key version is available for international downloads.
- Steganos for Win95 (1085k) __NEW__
- Steganos for Windows 95, by Deus Ex Machina Communications, is an easy to use, yet powerful wizard style
program to encrypt files and hide them within BMP, DIB, VOC, WAV, ASCII, and HTML files.
A significant improvement over the DOS version, Steganos for Win95 even contains its own Shredder, a program which
permanently wipes files from your hard disk. There is also a German version.
With all of the new features and added functionality, Steganos for Win95 is a serious contender.
- S-Tools4 (272k) (alternative site) (alternative site)
- S-Tools v4 is an excellent Win 95/NT based steganography tool that hides files in BMP, GIF, and WAV
files. It will not run with Win 3.1. S-Tools v4 has a number of new
improvements over the previous version.
- S-Tools3 (283k) (alternative site)
- An excellent Windows based steganography tool. Hides files in BMP,
GIF, WAV, and unused space on floppies!
- Contraband (281k) __NEW__
- Windows-based program which embeds and extracts any thinkable file into 24-bit BMP's.
Includes source code.
- PGPn123 (428k)
- PGPn123 is primarily a pgp "windows clipboard" shell program that makes using pgp for Eudora, Agent, or Pegasus Mail very easy.
The latest version includes a steganography option that is implemented after the message is pgp encrypted.
The algorithm is based on the Texto program, making encrypted
text files look like something between mad libs and bad poetry.
- Scytale (575k) __NEW__
- Scytale is a pgp shell program that has the added feature of hiding data in PCX images. Other strengths of the
program include a built-in wiper and batch mode capabilities.
DOS
- JSteg (462k) __NEW__
- JSteg, by Derek Upham, is currently the only
DOS program available for hiding data within the popular JPG format. Prior to hiding data in a JPG file, you will need to
save that file in the TGA (targa) format. After the data is stego'd into the image, the resulting output file will be in the
JPG format, with all of the compression advantages that JPG entails. Previously only available for Unix,
Preston Wilson and Randall Williams have been kind enough to compile this
DOS version for your stego pleasure. It requires this support file (40k)
placed in your path.
- Texto (59k) __NEW__
- Texto is a text steganography program which transforms uuencoded or PGP
ascii-armoured data into English sentences. Texto text files look like
something between mad libs and bad poetry. This is the only DOS implementation of the Unix source code and is compiled
courtesy of Preston Wilson. It requires this support file (40k)
placed in your path. Be sure to visit the online demo page!
- GZSteg (346k) __NEW__
- GZSteg hides data in GZip compressed files. It was compiled for DOS by Preston Wilson
and requires this support file (40k)
placed in your path.
- Hide4PGP v1.1 (70k)
- Hide4PGP v1.1 by Heinz Repp is a steganographic program that hides data within BMP, WAV, and
VOC files. It is designed to be used with both PGP and Stealth, but also works well as a stand-alone program. Hide4PGP now comes in both DOS and OS/2
executables.
The source is also included and should compile on any platform without major problems. Also new to this version, you now can use any number
of least significant bits (up to eight) to hide your data.
- Steganos v1.4 (12k)
- Steganos is a small, easy to use DOS based stego program by
Fabian Hansmann that hides data inside BMP, VOC, WAV and even ASCII files!
- Pretty Good Envelope (25k)
- Pretty Good Envelope (PGE) is a DOS based program that hides a message in another file by the
very simple method of appending the message to the file, and then appending a 4 byte little endian
number which points to the start of the message. A companion program UNPGE retrieves the
message. PGE can be used with graphic files (GIF and JPG) or any other binary files, including .COM and .EXE files.
- Stealth (19k) (alternative site)
- Stealth is a simple filter for PGP which strips off all identifying header
information to leave only the encrypted data in a format suitable for
steganographic use. That is, the data can be hidden in images, audio
files, text files, CAD files, and/or any other file type that may contain
random data, then sent to another person who can retrieve the data from
the file, attach headers, and PGP decrypt it.
- Hide and Seek v4.1b (264k) (alternative site)
- Data hiding/seeking using GIF image files. These DOS programs take data, usually
text, including encrypted text, and hide it in a GIF file.
- Hide and Seek v5.0 (199k) (alternative site)
- The latest version of Hide and Seek has been totally redesigned. It is still a DOS
based program, but now includes a user interface (no more command line operations) to hide info in GIF files.
- Snow (27k) (alternative site)
- Snow is a text-based stego program by Matthew Kwan
that conceals messages in text files by appending tabs and spaces on the end of lines. Tabs and spaces are invisible
to most text viewers, hence the steganographic nature of this encoding scheme. Snow includes a compression function to allow
you to stego more information into a given file and has some basic crypto functions via the ICE algorithm.
Check out the homepage for DOS, Java, Java applet, and source code versions.
- FFEncode (12k)
- FFEncode is an interesting little DOS program that "hides" a file in a text file by using a "morse code" of NULL
chararcters. Unpack the zip file and type FFENCODE or FFDECODE at the DOS prompt for the simple
command line parameters.
- StegoDos (22k) (alternative site)
- This DOS based picture encoder consists of a group of programs designed
to let you capture a picture, encode a message in it, and display it so that
it may be captured again into another format with a third-party program,
then recapture it and decode the message previously placed inside it.
- Wnstorm (84k) (alternative site)
- Wnstorm (White Noise Storm) is a cryptography and steganography software
package which you can use to encrypt and hide files within PCX images.
Java
- EZStego Java
- EZStego Java is from Romana Machado,
the author of Stego for Mac. It reportedly has similar
steganographic functions as it's Mac-based predecessor, but is written in the platform independent Java language instead.
It is currently it is being tested in an online version, allowing you to stego images from your web browser! The author plans
to release the java code once the online testing is complete.
- Snow (34k) __NEW__
- Snow is a text-based stego program by Matther Kwan
that conceals messages in text files by appending tabs and spaces on the end of lines. Tabs and spaces are invisible
to most text viewers, hence the steganographic nature of this encoding scheme. Snow includes a compression function to allow
you to stego more information into a given file and has some basic crypto functions via the ICE algorithm. Be sure to download
the Java sources and
classes.
Also available as a Java applet.
Macintosh
- Stego (266k)
- Stego is a steganography tool that enables you to embed data in
Macintosh PICT format files, without changing the appearance or
size of the PICT file. Thus, Stego can be used as an "envelope" to hide a
previously encrypted data file in a PICT file, making it much less likely to
be detected (available as a binhexed StuffIt archive).
- FatMacPGP 2.6.3
- FatMacPGP 2.6.3 is the most recent version of MacPGP optimized for PowerMacs.
It has a Stealth option
which strips off all identifying header information to leave only the encrypted data in a format suitable for
steganographic use.
- Paranoid (80k) (alternative site) (65k)
- Paranoid is primarily an encryption program that allows you to encrypt
files with IDEA, triple DES, and an algorithm written by the author Nathan Mariels.
It is a steganography program in that it allows you to hide files in sounds.
Amiga
- Textego (41k)
- Textego is based on the Texto program by Kevin Maher (with a few added improvements).
It is a substitution cipher that makes text files look like something between mad libs and bad poetry. The
source code is available, as is a
homepage
covering some of the highlights of the program. Be sure to visit the online demo page!
OS/2
- Hide4PGP v1.1 (70k) __NEW__
- Hide4PGP v1.1 by Heinz Repp is a steganographic program that hides data within BMP, WAV, and
VOC files. It is designed to be used with both PGP and Stealth, but also works well as a stand-alone program. Hide4PGP now comes in both DOS and OS/2
executables.
The source is also included and should compile on any platform without major problems. Also new to this version, you now can use any number
of least significant bits (up to eight) to hide your data.
- Texto (36k)
- Texto is a text steganography program which transforms uuencoded or PGP
ascii-armoured data into English sentences. Texto text files look like
something between mad libs and bad poetry, (although they do sometimes contain
deep cosmic truths) and should be close enough to normal english to get past
simple-minded mail scanners. Be sure to visit the online demo page!
- Stealth (94k)
- Stealth is a simple filter for PGP which strips off all identifying header
information to leave only the encrypted data in a format suitable for
steganographic use. That is, the data can be hidden in images, audio
files, text files, CAD files, and/or any other file type that may contain
random data, then sent to another person who can retrieve the data from
the file, attach headers, and PGP decrypt it.
- Wnstorm (108k)
- Wnstorm (White Noise Storm) is a cryptography and steganography software
package which you can use to encrypt and hide files within PCX images.
Source Code
(for the Unix users out there)
- Snow - source code here
- Hide4PGP - source code here __NEW__
- TCP/IP - source code here __NEW__
- J4-jpeg - source code here (Alpha release)__NEW__
- Hide and Seek - source contained in zip file (dos section above)
- Stealth (v1.2) - source code (Site #1) (Site #2)
- White Noise Storm - source contained in zip file (dos section above)
- Texto - source code (Site #1) (Site #2) for a text-based stego program
- MandelSteg - source code (Site #1) (Site #2) for a gif-based stego program
- Steganosaurus - source code (Site #1) (Site #2) for another text-based stego program
The secret 'advanced steganography page
This is one of the letters I have received two days after having opened this
section:Fravia+,
I am the author of Steganos for DOS and Windows 95
(http://www.steganography.com)
I think your pages are very useful so I just cracked the picture on
your stego.htm page - all I got are some zipped files, no URLs.
Will there ever be something like 'advanced steganography academy' pages?
Thanks, Fabian fabian(at)demcom(point)com
And Fabian was not the only one (nor the first one :-) to have reacted immediately
along these lines... OK, so I lied when I published the first version of this page, back
in 1997... in fact I put only the 'secret files' inside the stegonated Andromeda picture,
therefore you'll find no secret URL for an 'advanced steganography page' there (but
I believe you will enjoy some of those files nevertheless)... mea
culpa: I
was not quick enough, and pleasingly surprised by your fast answers!!
The (not at all sad :-) fact is
that (many among) my readers are TOO QUICK! You already cracked everything
before I had a chance to prepare 'as it should' my 'advanced steganography page... yet that page begins to be ready now. So you'll now
be able to start roaming using that "coveted" URL.
But, since it was such an easy cracking, with my 'Andromedas' above, I'll push up the
ante! You will have to work a
little more (do not complain! You are all here for the sake of cracking, aren't you?)
Here follows ANOTHER couple of a Tamara de Lempicka's picture, original and stegonated, in
BMP format (zipped of course). I have
enclosed the URL of my advanced page inside the stegonated one.
This time I have used Fabian's program itself: Steganos for Windows 95,
that you'll be able to download
at his URL (given in the letter above), or else
 here (1085k).
here (1085k).
Now crack it and find the 'advanced URL', where you'll find some of the solutions
essays I have received (+ReZiDeNt's lazy brute force approach, zeezee's "source
code reversing", Massimiliano's "anticontraband" own utility
and a small essay by Fabian himself, the author of Steganos, plus a very
interesting complete essay by Flynn; more recently Gary Benson's "Unconventional access", with a
clever exalination of Hide and Seek weak points)

You'll find BELOW two images (corresponding to the GIF above: portrait of Suzy Solidor, painted by Tamara
in 1933)
in zipped BMP format,
the one that I have 'stegonated' (through Fabian's Steganos ver. 1.0a) carries 'inside'
the URL of my "advanced steganography" page (which is under construction,
yet already exist :-)
You may download here the  original picture
by Tamara de Lempicka (9282 bytes),
original picture
by Tamara de Lempicka (9282 bytes),
and here the  stegonated one with the hidden
URL inside (8914 bytes).
stegonated one with the hidden
URL inside (8914 bytes).
New add_on: 2 January 1998
Advanced steganography URL (and password) have changed! (Password above was too easy)
December_help
Some help
information: I have used very small images, a password still with 8
simple (yet no more extremely simple) alfabetic chars and no numbers
nor punctuation signs, the
hidden text is only an ASCII url, 36 bytes long (which has the following
form: http://*.htm).
Moreover I have
used BMP images with very few colours... something you should NEVER do
if you stegonate for true.
Hint: try using yourself the various options of Fabian's
Steganos on the original image...
Well, you have your chance, now crack! :-)
New_year's_add_on_help
Should the server given in the hidden URL not
answer, (could happen, particularly during holydays) there is another
server of mine with the SAME name_you_have_to_find.htm
advanced steganography page, a 'second copy' that is, so you may as well access it there... once you find the name and
have learned how to finger and NSLookup servers, an important and easy technique which
you should master anyway)
Now try cracking these images! (a second easy run)
's-tools version 4.00, by Andy Brown)
I'll offer another run -this time in gif format- to the reversing capable among my readers: Here you have two copies of
another famous picture by Tamara de Lempicka:

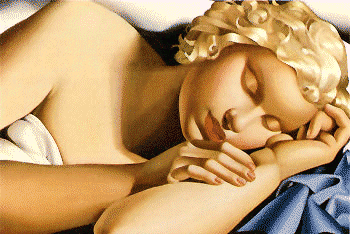
the original
asleep girl and the 'stegonated' one
This time you have the two GIF images above, and the same
text file as above (36 bytes
long) has been
hidden inside
the 'stegonated' GIF using s-tools 4, by Andy Brown may be the
best of the tools around. You can download it
right HERE on my site.
I used the same key used for the 'steganos' bmp(s) above, by the way), so it's
up to you how to devise an attack, you can crack this in a more 'zen' way,
as you'll see.
Inside adva.txt, if you ever reverse it 'out' of the GIF image, you'll find
the URL of the advanced steganography page
OK, OK, so you find this too difficult, yet I want you to be able to crack s-tools
algos as well and not only steganos... so... here once more two SMALL images, in gif format: the same 36 bytes
long adva.txt file is hidden inside, the same 8 characters password has been used,
the option chosen have been, once more, IDEA and attempt to lower number of colours...
well, I think you should have enough data now... crack!
 ~
~

the original
asleep girl's hand and the 'stegonated' one.
Well... crack this one instead of the previous one, if you prefer :-)
Of course to reach the advanced page is not very important if you
do not contribute to it as well... if you send to me your own reversing
approach, once you have reached that page, I'll publish
it -there- with the other ones (see below). Choose whatever
handle you prefer, send anonymously and without a return email address only
if you really find you should)
What's on the advanced URL?
As of today 23 September 1998, on my 'advanced steganography URL', you'll
find
+ReZiDeNt's lazy brute force approach
zeezee's "source code reversing"
caprine's approach
Massimiliano's "anticontraband" own utility (!)
an essay by Fabian Hansmann (Steganos' Author): Fighting steganography detection
and then:... (of course these links won't work)
Jean Flynn's "A Journey within Steganos"
("How to find the Fravia's Advanced Steganography Page the hard way")
10 February 1998
Caprine's short answer to Jean Flynn
("Let's work together")
12 February 1998
Joe Peschel's Steganos, The Duke of Earl, and The Dancing Men
("Cracking the T_tamra7.bmp")
04 March 1998
Edi's work
("I had to reverse engineer steganos again, on my own")
26 March 1998
Caprine's beautiful story A great dragon
known as Steganos
(Steganos Key Relief (Reducing the key search burden))
22 April 1998
Gary Benson's Unconventional Access: My
way into the Advanced Steganography pages
(Steganos Key Relief (Reducing the key search burden))
23 September 1998
Here you have, as 'teaser' my own comments to Fabian's essay:
Well, for once I'm hosting an essay of a person that does not use handles
nor avatars nor nicknames: Fabian Hansmann, the Author of Steganos, one of
the most interesting Stenographical applications on the scene. His idea of using
a benign virus in order to spread noise is interesting, yet not new (some
+masters have already prepared long ago a 'benign' cracking virus -antibil7.com-
that registers Micro$oft's timelimited targets WITHOUT NOTICING the owner
of the PCs where these targets are found :-)
So Fabian's idea can be implemented if needs be,
moreover we will of course begin ourselves,
during 1998, to 'deepen' (in a reversing sense) our knowledge of the whole
steganographical existing bazaar... and I'm happy that we'll work hand in hand
with steganographical experts (and nette Leute) like Fabian (and maybe
other Authors as well as it seems).
Another hint
Here you have as teaser a 'light' version of Jean Flynn's essay (that you will find
complete on the advanced page): A Journey within Steganos,
you should be able to figure out the advanced page entrance reading this... that is,
if you work a little :-)

Back to Fravia's Anonymity Academy
 homepage
homepage
 links
links
 +ORC
+ORC
 students' essays
students' essays
 counter measures
counter measures
 antismut CGI tricks
antismut CGI tricks
 academy database
academy database
 tools
tools
 javascript tricks
javascript tricks
 cocktails
cocktails
 search_forms
search_forms
 mail_Fravia
mail_Fravia
 Is software reverse
engineering legal?
Is software reverse
engineering legal?
 (c) Fravia, 1995, 1996, 1997, 1998.
All rights reserved
(c) Fravia, 1995, 1996, 1997, 1998.
All rights reserved

 ~
~



