Smartcards are becoming ever-more popular in today’s world. When people are looking for security in their applications and they are not willing (or able) to put lots of resources towards ensuring that the security is effective, they turn to someone who is willing to do the job for them. Smartcards offer a very cheap and (potentially) secure solution. Some of the examples of smartcards in use today are: phone cards (mainly in Europe), pay TV services (DSS, Direct TV), GSM phones, an increasing number of credit card companies are combining smartcards with regular magnetic stripe cards, they can be used as an access control device, several banks in Europe are using them to authenticate users, and they can be used as a stored value card or e-purse.
alt.technology.smartcards has an excellent FAQ on smartcards which is available at http://www.scdk.com/atsfaq.htm. Although the FAQ will go into much more depth than this file, I intend to only give an overview of smartcards and focus mainly on the security issues.
Before going any further, it should be made clear that there are two types of smartcards, only one of which is truly ‘smart’. Memory cards that simply store information and have no onboard processor are not truly smartcards but are occasionally grouped in the same category. True smartcards are basically computers on a small chip without a power supply; they have memory storage and a processor.
The idea behind smartcards has good intentions, but the truth is that from a security standpoint, some implementations of smartcards are unreasonable. In some applications the end user has in their possession the card which contains the chip with the secret information, they can assault the card indefinitely and have no fear of being caught by authorities, or arousing suspicion from invalid attempts. The whole idea with smartcards is that the single card is secure enough to authenticate a user, so that a central server does not need to be accessed, however this is not to say that it is never accessed. Also a record of transactions can be kept, but there is no way to distinguish a valid transaction with an illegitimate one. Times when a smartcard is not a good idea to use as a security control device are when the actual card is the only record or holder of the transaction or authentication information. Cases that stand out as bad ideas for use with smartcards include: phone cards, pay TV, and as an e-purse. In other cases, smartcards may add a degree of security; however the network carrying the smartcard data should also come into consideration.
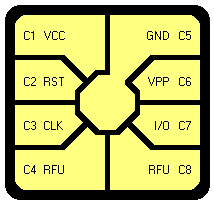 |
Smartcards are described under the ISO 7816 standard which defines everything from physical and electrical characteristics of integrated circuit cards down to communication to and from the card. It should be noted that there were cards made before 1990 that had a different standard contact location and therefore can not be used with ISO 7816-2 compliant smart card readers. Although contact location and function is now standardized, the design of the contacts is not. Most contact designs are patented and make it easy to distinguish a manufacturer’s cards. The contact layout at left is the ISO 7816 standard as follows:
- VCC : Power supply input (optional use by the card).
- RST : Either used itself (reset signal supplied from the interface device) or in combination with an internal reset control circuit (optional use by the card). If internal reset is implemented, the voltage supply on Vcc is mandatory.
- CLK : Clocking or timing signal (optional use by the card).
- GND : Ground (reference voltage).
- VPP : Programing voltage input (optional use by the card).
- I/O : Input or Output for serial data to the integrated circuit inside the card.
- RFU: Reserved for Future Use
Unlike magnetic stripe cards that can be easily read and written to by anyone with the money to buy an encoder, or the know how to build one (that’s another file); smartcards restrict read and write operations. There are varying levels of protections that can be implemented in smartcards because essentially a smartcard is a computer without a power supply. However, smartcards are limited to either being read or written to simultaneously. This was done to slow down attacks on the card. The nice thing about smartcards is that in order to read or write to them, no special equipment is needed; only an interface to a computer which could consist of contacts and a power supply, or the power could be provided by the computer. If you are planning on obtaining a smartcard programmer, I would suggest (for the technically inclined) building your own. It is not a terribly complicated project, but not recommended as a beginning project. There are several sites that provide schematics for building smartcard programmers. Note that a reader is the same as a programmer, i.e. it can read and write data to a smartcard because there is no special hardware involved.
What happens during a typical smartcard transaction: 1) After the smartcard is inserted into the reader, the reader generates a random number which is sent to the card. 2) The card is asked to perform a secret calculation with the random number, which the reader also performs. 3) The card sends the result back to the reader, which compares the numbers. If there is a match, the card is authenticated and the transaction is allowed to proceed. This authentication procedure is commonly known as a challenge response.
While one may think that simply by analyzing the data between the card and the reader, all cards could be compromised. Such a 'replay' attack could be beneficial to understanding what goes on during a session. Although a capture of the data between the reader and card may be encrypted, no doubt it will help in analyzing the card. Protection against replay attacks includes using a digital signature and a counter on the card to refuse replayed transactions.
Until this point, smartcards seem fairly secure and difficult to attack. A flaw in smartcards was found by Paul Kocher of http://www.cryptography.com that allows for the extraction of the secret key. The flaw was that by analyzing the power consumption of the smartcard you would be able to determine the secret key from the spikes in power (high for 1, low for 0). This attack is known as Differential Power Analysis (DPA), which at the time of its discovery all smartcards were vulnerable to this attack. However a solution to prevent or thwart DPA was put forward, that is by running a random number generator on the card separate from the meaningful processing, an attacker trying to extract the key would be foiled. It is not known how widely the solution has been implemented.
In order to carry out DPA an attacker would need an oscilloscope capable of sampling at a rate equal to or higher than the card's transaction and highly technical knowledge.
DPA is not the only attack that can be used against smartcards. By physically opening the card and modifying the fuses inside (after dissolving the protective black epoxy on the EPROM) with microprobes it is possible in some cases to gain access to secret parts of the card, or bypass certain 'features'. Also there are many other timing attacks possible by applying much higher or lower voltage than usual to the card. By altering voltage levels, the card’s processor clock may speed up or slow down significantly, allowing an attacker to learn more about each clock cycle.
A similar attack to DPA which was recently brought to my attention could use thermal imaging to observe very small changes in temperature on different areas of the chip, and if a random number generator was implemented separately from the main processor, it could be isolated. By correlating the changes in temperature to processing cycles, like DPA the secret key could be extracted.
It should be noted that chip manufactures should not want to lock down their chips from all analysis; they want to be able to examine chips that fail to determine the cause of malfunction. Invasive attacks can be made easier by the fact that silicon is transparent to infrared light.
In the case of Pay TV, pirates have been able to write protect their access card and only use the decrypting functions on the card by the use of an emulator and a legitimate card. Pay TV companies retaliate by adapting their signal to try to cut off pirates, and a cat and mouse game ensues. Some more advanced pirates have figured ways to bypass the need for updating scripts on their cards by modifying the receiver unit, this only goes to show that more than just the smartcard must be considered in application. Many satellite TV hacking web sites have cropped up as a result of its popularity, and while some have valuable information, most have little information of interest to the smartcard hacker.
Smartcards are very interesting pieces of technology that you can count on seeing more of in the future. In the near future smartcards could replace identification cards and records could be stored right on the card. There are definitely privacy issues at hand with smartcards and related technologies. Unfortunately Microsoft and other corporations see the use of cryptographic hardware as a means of controlling what applications can be run on their hardware. The Xbox only runs Microsoft – signed code (without a modchip or a buffer overflow exploit from a legitimate piece of code). Microsoft’s current project (which deserves its own article), Trusted Computing Platform Alliance (TCPA), Palladium, or “Next Generation Secure Computing Base” (NGSCB) as they are calling it now (due to negative publicity) will use the same type of technology to control what programs you can run on your computer. As technology advances and chips become even smaller, attacking hardware invasively becomes harder. Also, manufactures will become devious and integrate the cryptographic chips right into their processors of your computer making any attacks very difficult to carry out.
Essential Smartcard links:
Markus Kuhn’s webpage – Many excellent papers on smartcards, and other very interesting topics: http://www.cl.cam.ac.uk/~mgk25/
Center for Information Technology Integration, at university of Michigan: http://www.citi.umich.edu/projects/smartcard/
Bo Lavare’s Smartcard Security Page
http://www.geocities.com/ResearchTriangle/Lab/1578/smart.htm
(unfortunately the original site is no longer active but has been
archived on http://web.archive.org)
Ross Anderson’s webpage – Some papers on smartcards and a good FAQ on TCPA: http://www.cl.cam.ac.uk/~rja14/
More information on smartcards with some links to related projects
to build: http://www.epanorama.net/links/smartcards.html

