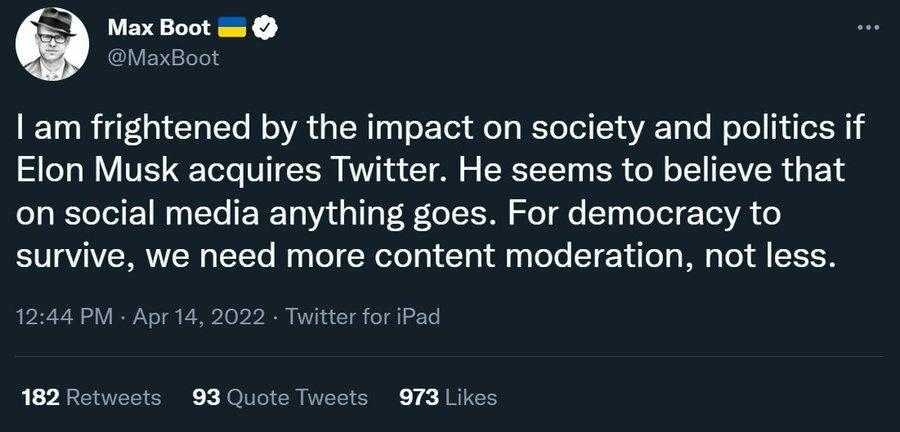
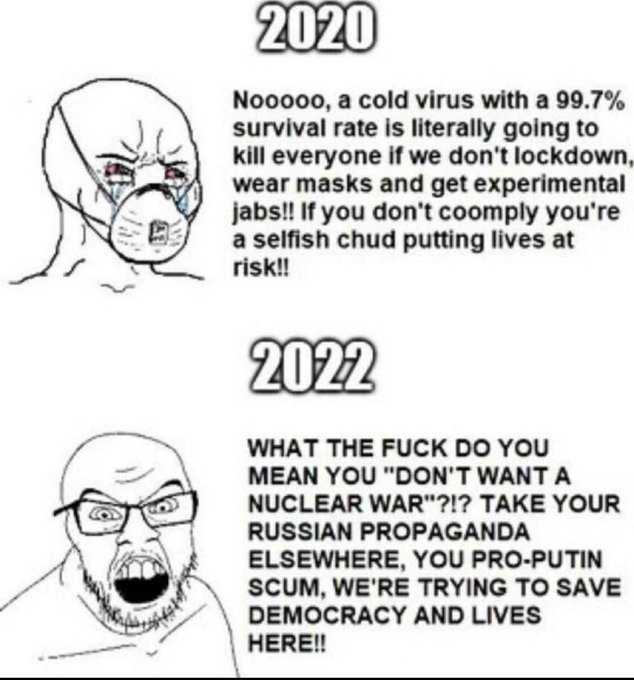
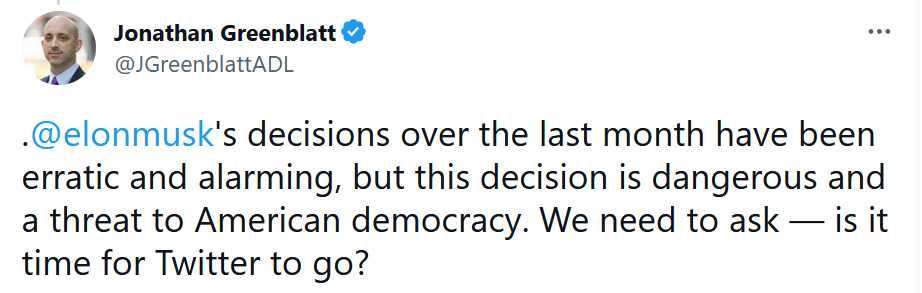
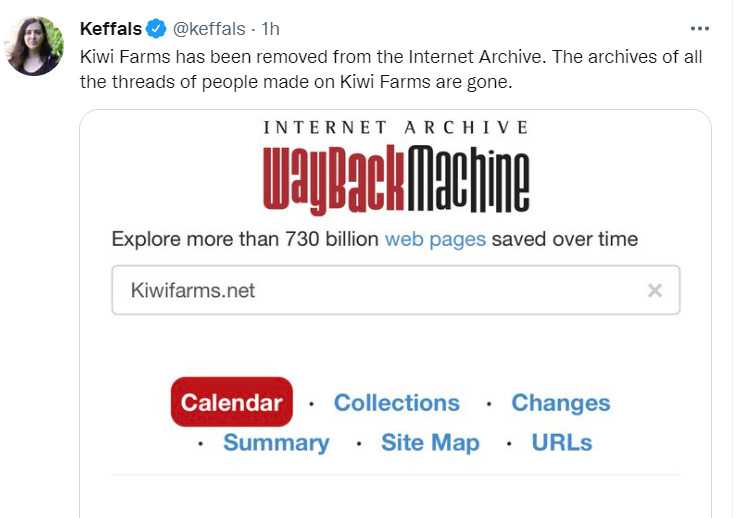
| $2600 Magazine Downloads & Information |
| World's Largest Undocumented $2600 Distribution Site |
"We are creating a world where anyone, anywhere may express his or her beliefs, no matter how singular, without fear of being coerced into silence or conformity."
--- Quote from John Perry Barlow in A Declaration of the Independence of Cyberspace on February 8, 1996.
"We seek a free flow of information... we are not afraid to entrust the American people with unpleasant facts, foreign ideas, alien philosophies, and competitive values. For a nation that is afraid to let its people judge the truth and falsehood in an open market is a nation that is afraid of its people."
--- Feb. 26, 1962 quote from John F. Kennedy (1917-1963), 35th President of the United States.
"Long live the underground! When the underground is gone, when the people's will to resist overbearing government and kneejerk morality is gone... Then, shall I be able to declare America dead."
--- Quote from Jello Biafra, a frequent HOPE keynote speaker.
"If liberty means anything at all, it means the right to tell people what they do not want to hear."
--- Quote from George Orwell (Eric A. Blair [1903-1950])
"Anyone who stands up for what he believes in is an inspiration. That's the spirit of a hacker, and it's the spirit of an individual."
--- Quote from Evil Corley during an Off The Hook broadcast. (I don't remember which one.)
"It's a question of freedom of speech, something that has stood up for the last couple hundred years, and I think the Internet should definitely continue the tradition."
--- Quote from Evil Corley on Off The Hook, June 18, 1996.
"... Freedom of speech, on the other hand, is something that is universally sought after and recognized as valuable."
--- Quote from a reply to a letter by William R. Epp in Vol. 18, No. 3.
"As you probably know it you've read our pages before, we have some major issues with entities who abuse power and intimidate individuals..."
--- Quote from a reply to a letter by "anonymous" in Vol. 20, No. 2.
"Unthinking respect for authority is the greatest enemy of truth."
--- Quote (paraphrased) from Albert Einstein used in Vol. 23, No. 1.
"The first condition of progress is the removal of censorship."
--- Quote from George Bernard Shaw used in Vol. 33, No. 1.
"Journalism is printing what someone else does not want printed. Everything else is public relations."
--- Quote from George Orwell used in Vol. 32, No. 1.
"If tyranny and oppression come to this land, it will be in the guise of fighting a foreign enemy.
--- Quote from James Madison used in Vol. 22, No. 1. Like a good little tool, Evil Corley fell for Clinton/Obama/FBI "Trump collusion" hoax.
"But curtailing speech and liberty never advances the cause of freedom and once begun is very difficult to reverse."
--- Quote from the News Items in Vol. 12, No. 2.
"Unless some sort of miracle happens, it seems all but certain that laws will be passed to regulate what we say on the Internet. We can say it's ridiculous, we can say it's unenforceable, but there are many powerful people who simply don't like what the Internet has become. It makes them nervous. They want to be able to control it and they've demonstrated a willingness to do just that. Most of these outraged politicians have never even logged in. Yet they somehow 'know' what is right on the Internet and what isn't."
--- Quote from the editorial in Vol. 12, No. 4.
"What we've done with the Internet is what the Internet has been designed for - freedom of speech and instant access to relevant material... Individuals will continue to use the Internet to outmaneuver bulky corporations, speak out against bureaucratic and repressive regimes, and take over where the mainstream media has failed us. And those who underestimate this power are in for a very rude awakening."
--- Quote from the editorial in Vol. 13, No. 1.
"What we share is the understanding that free speech is paramount, individuality is a valuable asset, and that the Internet - which was developed with the hacker spirit - is potentially the most valuable tool that free speech, individuality, and hence humanity itself has ever had at its disposal."
--- Quote from the editorial in Vol. 13, No. 4.
"We support Barnes & Noble/B. Dalton as they increase their distribution of independent zines and alternative voices. We back them completely in their fights against neighborhood censors who try to shut them down because they don't like the pictures in a book or the ideas in a magazine. And we want our readers to support them as well, not just for our sake, but because any semblance of literacy and thought that manages to pop up in our shopping malls deserves to prosper. But it is vital that those of us fighting for this kind of thing not take on the tactics of our enemies when the subject matter hits close to home. It's not hard to see the hypocrisy in such a move."
--- Quote from the editorial in Vol. 15, No. 1.
"Agreeing to stifle speech would have meant that someone else would one day have to fight to get it back. "
--- Quote from the editorial in Vol. 18, No. 2.
"We know that freedom of speech - even freedom in general - is considered by an increasing number to be subject to restrictive conditions in the interests of 'security.' Never mind that total security is completely elusive. There will always be someone claiming we can do better by closing off yet another avenue of activity, beliefs, or speech. And simpletons, fueled by mass media hysterics, will continue to believe it.
--- Quote from the editorial in Vol. 18, No. 4.
"We may not like the message, we may not agree with it, but if what we allege to stand for is to have any value, we have to do everything possible to ensure it isn't silenced."
--- Quote from the editorial in Vol. 20, No. 1.
"Change does not come about from mindlessly following the rules. That's how dictatorships are maintained. Change is achieved through constant experimentation, the exchanging of ideas, and the freedom to do so. A society that views such things with suspicion is one that is doomed to stagnate and eventually fall."
--- Quote from the editorial in Vol. 22, No. 3.
"We may not like hate speech but it is within our rights to read it, listen to it, or watch it if we so desire."
--- Quote from the editorial in Vol. 23, No. 3.
"We have learned a great deal in watching the reactions of our various leaders. We see how the surveillance of so many aspects of our lives is supported by politicians of both parties and how deep the cover-up goes. We also see how they have no problem changing the rules behind our backs to make these inexcusable actions 'legal.' Shining the light on their subterfuge is about the most patriotic act we can think of."
--- Quote from the editorial in Vol. 30, No. 3.
"It's news. It's history. And it's staying. Praise The Web."
--- Quote from Evil Corley in Vol. 15, No. 2 after $2600 was threatened with legal action by the International Churches of Christ over a hacked website that they displayed in their hacked web page archive.
"9.) I will aid the voiceless in obtaining a voice and help them evade censorship so they too can enjoy the fundamental human rights of free speech."
--- Quote from Ghost Exodus (Jesse McGraw) in his article "No Country for Incarcerated Hackers" in Vol. 35, No. 3
"Recognizing the content of the wikileaks.org website is the subject of concern to a variety of individuals and nations, we nevertheless believe it must be subject to the same laws and policies of availability as all Internet sites. Free expression should not be restricted by governmental or private controls over computer hardware or software, telecommunications infrastructure, or other essential components of the Internet."
--- Quote by The Internet Society (Mirror) from the article entitled "The Internet Society on the Wikileaks issue" in their membership newsletter. (December 2010)
Cult of the Dead Cow - FreedomcDc communications & HACKTIVISMO "A Special Message of Hope"
CENSOR! ATTACK! BAN! DELETE! SHUN! CANCEL! DEPLATFORM! SHUT IT DOWN!!!!!!
"Without the knowledge or support of management or the Board, Twitter learned that [Peiter] Zatko had engaged with members of U.S. intelligence agencies and sought to enter a formal agreement that would allow him to work with them and provide information to them."
...
"'The organizations and people behind this recommendation' Zatko explains, 'have the connection [sic] to get this in front of the right people in the administration.'"Oh look... Another Cult of the Dead Cow member trying to stifle the freedoms of Americans. Mudge wanted pre-Elon Twitter to hire (((The Alethea Group))) - an organization run by people like Ukraine war-monger (((Nina Jankowicz))) - to spy on average Americans, and he pushed for more government-linked censorship. Do you think the (((EFF))) or $2600 will do anything about this? LOL!
- What Would (((Jello))) Do? Sell-out and become a tool for the FAGA Deep State & One Percent.
- 2600 Kicked Off of YouTube for Sarcastic Remark $2600 has now felt what many other content providers have felt after being censored for a seemingly meaningless, off-the-cuff remark.
Russia! Palestine! Iraq! Iran! Syria! Yemen!
Don't question anything!
Be a good goyim and fight our, err... your enemy!

War is peace.


Freedom is slavery.
Ignorance is strength.

"By means of ever more effective methods of mind-manipulation, the democracies will change their nature; the quaint old forms -- elections, parliaments, Supreme Courts and all the rest -- will remain. The underlying substance will be a new kind of non-violent totalitarianism. All the traditional names, all the hallowed slogans will remain exactly what they were in the good old days. Democracy and freedom will be the theme of every broadcast and editorial. ... Meanwhile the ruling (((oligarchy))) and its highly trained elite of soldiers, policemen, thought-manufacturers and mind-manipulators will quietly run the show as they see fit."
...
"But liberty, as we all know, cannot flourish in a country that is permanently on a war footing, or even a near war footing. Permanent crisis justifies permanent control of everything and everybody by the agencies of the central government."--- Aldous Huxley, Brave New World, 1958.
"At press time, Parler was no longer in service. We're not mourning its loss and don't believe it ever offered anything of value. We would certainly like to see alternative social media sites that aren't batshit crazy, as having everyone using only a couple of different sites is far from ideal."
--- Quote from a reply to a letter by "Jason" in Vol. 37, No. 4. Ironic, as $2600 is one of the most "batshit crazy" publications out there...
"Someone in this group reported me and got my account blocked for 24 hours over something that wasn't even that serious. I'm unhappy about that and I've never ever had someone do something so petty."
"I keep getting muted from the 2600 group without explanation. What am I doing wrong here?"
"Unfortunately, I've been blocked for seven days from posting for no apparent reason. I would like to read the guidelines as suggested, but when I go to read them, it says the post has been removed or deleted. Can someone please send me the guidelines and, if possible, tell me which I violated? I thought I posted a supportive humorous meme, but I'd like to follow the rules."
--- Letters in issue Vol. 37, No. 4 regarding censorship of posts (and users) on one of the $2600 Facebook groups.
"We believe in science. We support removing fascists from platforms. We want monopolies broke up. And we demand accountability. Saying these things really pissed a lot of people off. So we're saying them again in case we missed anyone."
--- Quote from a $2600 Twitter post in May 27, 2021. $2600 Magazine openly attacks the scientific method; believes that MEN can become pregnant or turn into women if they grown long hair, wear lipstick, and chop off their pee-pee; thinks Chelsea Manning is an actual female; openly supported (and voted for!) the fascist (((Obama and Biden regimes))); profits from complaints about the government's mess of the (((breakup))) of the the Bell System or has never once mentioned the monopolistic & private "Federal Reserve" as they slowly increase the price of their magazine to
$9$10 and the banks demand more "bailouts"; doesn't want anyone to show an ID to vote, but they do use IDs (and encryption) on their own computer networks. And worst of all, has done NOTHING to expose the "accountability" of the FBI & Hillary Clinton's "Russian collusion hoax" or the FBI & Twitter's suppression of the Hunter Biden laptop and China COVID-19 origin stories, or all the other various Biden-family bribery schemes - all in order to affect the outcomes of the 2016, 2020, & 2024 presidential elections.
"... Nowadays, Off The Hook is filled with sycophants who dare not disagree with political views, no matter how misguided, or he will scream at them. Literally. The only personality brave enough to even attempt to disagree and reason with him at times is Alex (whom I applaud), but even his attempts are half-hearted and shouted down."
--- Quote from a letter by "J.X." in Vol. 38., No. 3 discussing their views on what Off The Hook and $2600 have turned into.
"... Anthony Fauci is a good scientist. Serious electoral tampering did not occur on the Democratic side (investigations into Trumpian tampering are ongoing on federal and state levels). I don't say these things because I download my opinions from the mainstream media. I say these things because of a compelling pattern of evidence from reputable sources..."
--- Quote from a letter by "James" in Vol. 38, No. 2. $2600's reply was: "Thank you for making these points better than we ever could." All those statements "James" made are demonstrability false. Dr. Fauci has been caught red-handed lying to Congress, the media, and the American people and actively covered-up his involvement in the creation of the China COVID-19 pandemic, leading to the potential deaths of millions.
Bernie Sanders actually won the Democrat primary nomination in Wisconsin (and in other states), and through the WikiLeaks' emails we now know that Hillary Clinton and the DNC basically stole the 2016 nomination from Bernie S. And people think Trump is crazy for saying they stole the 2020 election too...
"'If you happened to walk in the Capitol on Jan. 6, (2021), you might get 10 years in prison,' [Rand] Paul said. 'But if you're responsible for funding research that led to a pandemic and killed 15 million people, and then you lied about it to Congress, then nothing happens to you.'"
--- Quote from Rand Paul who filed a criminal referral against Anthony Fauci in July 2021 and again in July 2023 over the perjury claims which $2600 refuses to acknowledge.
(Massive 2020 Voter Fraud Uncovered in Michigan Including estimated "800,000 ballot applications sent to non-qualified voters" - bags of prepaid gift cards, guns with silencers, burner phones, and a Democrat-funded organization with multiple temporary facilities in several states.)
(Evidence of Foreign Nationals Accessing Dominion Voting Machines Leaked to Public)
(Hillary Clinton's Campaign Coordinator... Trevor LaFauci Busted Ripping Up Trump Ballots)
(Georgia Update: The 2020 Election Hijack A private election consultant group, paid in part by (((Mark Zuckerberg))), arrived in Fulton County (Atlanta) just in time to "help manage" the 2020 election. Joe Biden did not "win" Georgia in 2020.
(Georgia Was Stolen From Trump, He Won Fulton County violated the Georgia state election laws.)
(Segment that got Lou Dobbs Fired from Fox News He interviewed a USPS whistleblower who drove 200,000+ illegal ballots from New York to Pennsylvania during the 2020 election.)
(BREAKING: The Georgia Nerds Serve GA Gov. Brian Kemp with Evidence of Four Years of Election Fraud)
(FBI CAUGHT Rigging 2020 Election, Leaked Chat Logs PROVE COVER UP)
"Comparing demonstrators and even common rioters to a President-led storming of the nation's Capitol building (Mirror) is a poor attempt to minimize the significance of the latter. Blaming groups like Black Lives Matter for everything you dislike only shows how easily you can be convinced that people who are different from you are nothing short of pure evil."
--- Quote from a reply to a letter by "pinkbathtowel" in Vol. 38, No. 1. $2600 is trying to compare the deadly (((Black Lives Matter))) chimp-outs which caused billions of dollars in damage and killed at least 19 innocent people to the Constitutionally-protected Jan. 6 election integrity (unarmed!) protests where the only death was the result of an unqualified, affirmative action negro Capitol police officer killing an unarmed woman (and veteran) for no reason (and the assault and resultant death of motionless woman [Roseanne Boyland] on ground.) Also, Mr. Trump had nothing to do with the "riot," as proven over-and-over again...
Also note that at HOPE X, $2600 praised the jewish supremacist and war-monger (((Emma Goldman ✡))) for being a "dissenter." Really... Emma Goldman is best known for helping plan the assassination of U.S. President McKinley (!) which set the stages for pushing the U.S. and Europe into (((World War 1 & 2))) resulting in the deaths of millions of innocent Gentiles, and the creation of private (((central banking ✡))) in the U.S. I'm pretty sure that is a textbook definition of "pure evil," and just a tad bit worse than a bunch of people walking around the Capitol building with a police escort...
Also, I bet January 6, 2021 was the first time those traitorous assholes working in the U.S. government realized their boss was John Q. American and not Shlomo Shekelstein on Wall St. BTW, George Floyd died from a fentanyl overdose and China COVID-19.
("Do Your Non-Uniformed Guys Have Any Identifiers" SHOCKING Capitol Police Video Uncovered from Jan. 6 Shows Undercover and Armed DOJ On Site - IT WAS A SETUP)
(Capitol Police Chief Called Jan. 6 Events 'A Cover Up' in Tucker Carlson Interview HIDDEN by Fox News Former Capitol Police Chief Steven Sund told then-Fox News host Tucker Carlson that events surrounding the January 6th riots at the U.S. Capitol appear to have been a "cover up," in never-seen-before footage published exclusively by The National Pulse.)
(MORE HORRIFIC J6 FOOTAGE HAS BEEN RELEASED!!)
(Former FBI and Now Contracting Officer for the CIA Reveals how there were FBI agents in the crowd on J6 and brags about how the agency helped others sue Alex Jones for defamation.)
vs.
"Hurr durr.... Deadly insurrection! Derp... Worse than 9/11!
Avenge Ashli Babbit!
Destroy $2600
"And again, this fallacy that we're in favor of some sort of approved speech doctrine is a load of horseshit. We will stamp out hate speech wherever we see it. We will continue to shut down overt racism in every forum. And we will not tolerate anti-democratic attempts to subvert legal elections and overthrow legitimate leaders or deny people the right to vote."
--- Quote from a reply to a letter by "6NdLXzc2" in Vol. 38, No. 1. $2600 REFUSES to stamp out hate speech on (((CNN ✡))) or (((MSNBC ✡))). They also refuse to shut down overt racism by Steve Rombom ✡, Kevin Mitnick ✡, Chuck Schumer ✡, AOC ✡, etc., or even shutdown $2600 meetings in apartheid Israel. They also refuse to condemn the phony racially-motivated President Trump (((impeachment ✡))) hearings. And don't expect them to stand-up to the anti-democratic attempts to subvert our elections by the Democrat Party, Hillary Clinton, Twitter, Facebook, FBI, and WEF! And remember when Obama and his jew handlers overthrew a legitimate leader elected in Ukraine in 2014 (and also tried that in Syria and Romania!), and Evil Corley didn't say a single word about it?
Jeffrey Sachs - "In 2011, Obama ordered the CIA to topple Syria's government. It doesn't really matter who's president."
Tucker Carlson - "Why did he do that?"
Jeffrey Sachs - "Because Israel runs our foreign policy."
"I acquired 𝕏 in order to preserve freedom of speech in America, the First Amendment and I am going to stick to that." --- Elon Musk
"A number of our own readers in this issue's letters section expressed their outrage at our opinions on the matter in 37:4, which encouraged responsible providers on the Internet to stop hosting forums for movements that refused to acknowledge scientific facts or that advocated such actions as overturning democratic elections and installing unelected leaders (Mirror). While we continue to believe that everyone is entitled to their own opinion, we don't subscribe to the belief that all opinions deserve the same platforms. We believe providers have the right to determine what they consider to be acceptable and what they don't, even when we disagree - and everyone has the right to pressure them to do the right thing."
--- Quote from the editorial in Vol. 38, No. 1 Many of those censored "unscientific facts" have since turned out to be true... Jan. 6 was a nothing-burger exploited by (((Democrats))) to seize power, China COVID-19 may have been man-made in a Chinese lab partially funded by the U.S. government and U.S. corporations, the number of deaths was grossly overinflated to get government hand-outs, the lock downs caused more problems than they solved, especially for young children, low-cost alternative vaccines were actively suppressed by (((Big Pharma))) in collusion with (((Big Tech))), and those cheap masks did very little (Mirror). $2600 also wants illegal aliens to vote in U.S. elections (and counted in our census), thereby "overturning" the will of legitimate U.S. voters. That editorial also contains the quote: "There is nothing at all political about a pandemic." LOL!
(NYC Council Asks State's Highest Court to Allow Non-Citizens to Vote in Local Elections)

Election Interference by Evil Corley and the One Percent
Destroy $2600
"While everybody has the right to free speech, that doesn't mean they can say or do whatever they want on a system run by others. It's only if someone is forbidden from speaking by the authorities in any setting that we can start talking about true violations of free speech.
...
While we agree that we'd be better off with a whole lot of smaller companies and less mega-giants, we still need to ensure that falsehoods, anti-science sentiment, and hate speech doesn't become empowered and allowed to dominate as it has been."--- Quote from the editorial in Vol. 37, No. 4. The FBI, CIA, DHS, White House, and DNC forcing Twitter and Facebook to censor certain conservative users in order to effect the outcome of the 2016 and 2020 elections is a "true violation of free speech" according to $2600. Just don't expect them - or people like (((Cindy Cohn ✡))) at the EFF - to do anything about it... Also, there is really no such thing as "hate speech." "Hate speech" is anything which effects Evil Corley's power grabs. "Truth sounds like hate to those that hate truth."

More Censorship by Evil Corley and the One Percent
Destroy $2600"And when the site tried to find hosting in other countries, one by one they were cut off due to the outrage and bad publicity. Is it right to cut off speech of any kind in this manner? We believe it is when the decision is being made independently of any government regulation. In other words, these people still have the right to free speech and they can say whatever they want. But such reprehensible speech will generate a reaction and nobody should be forced to help them along. Are there hypocrisies and double standards that can be found when making these decisions? Undoubtedly so. That doesn't take away from the guts required to stand up and say 'enough.' We don't have to simply stand around and continue to watch the ugliness. Resisting isn't always a neat process."
--- Quote from the editorial in Vol. 34, No. 3. $2600 was calling for MORE censorship of so-called "neo-Nazi" websites after the Charlottesville incident. Video of the event shows that 340 lb. landwhale leftist, Heather Heyer, was NEVER hit by James Fields' car and the coroner's report stated she died of a heart attack due to being obese. We now know mentally-ill fascist Dwayne Dixon pointed his gun at James Fields and Fields fled in his vehicle, rightfully fearing for his life. This event was then exploited by Evil Corley and the One Percent to shut down anyone (and any website) who exposed those in power... You know, what hackers used to do... Do you think Evil Corley will ever apologize for spreading these lies? BTW, DailyStormer had their .com domain STOLEN by (((Google))). They illegally took away access to a domain they didn't own.
Only five years in prison for targeting Trump voters! Where's Evil Corley?



"Winston sank his arms to his sides and slowly refilled his lungs with air. His mind slid away into the labyrinthine world of doublethink. To know and not to know, to be conscious of complete truthfulness while telling carefully constructed lies, to hold simultaneously two opinions which canceled out, knowing them to be contradictory and believing in both of them, to use logic against logic, to repudiate morality while laying claim to it, to believe that democracy was impossible and that the Party was the guardian of (((democracy))), to forget whatever it was necessary to forget, then to draw it back into memory again at the moment when it was needed, and then promptly to forget it again: and above all, to apply the same process to the process itself.
That was the ultimate subtlety: consciously to induce unconsciousness, and then, once again, to become unconscious of the act of hypnosis you had just performed. Even to understand the word 'doublethink' involved the use of doublethink."
--- George Orwell, Nineteen Eighty-Four , 1949.
Destroy $2600
Evil Corley and the One Percent are an existential threat to our democracy and must be stopped AT ANY cost.
They are currently engaging in the greatest assault on our freedoms which we have ever seen.
What we're seeing with $2600 today is far more nefarious, as well-organized (((groups))) seek to influence massive amounts of people with fear, hatred, false information, and an unhealthy sense of paranoia. They encourage violence and want a far less democrat system in place, one where they reap the benefits and those who aren't like them are kept from having any power, to put it mildly.


Free Douglas Mackey!
Destroy $2600
To say the Obama/Biden/Harris/Corley cult, err... administration is unlike anything we've experienced before would be a massive understatement. We speak for many when we say that we were expecting a degree of crackdowns, closures, regressions, anger, fear, and the like, but what we've gotten so far leaves us almost speechless.
Almost.
It's well accepted that Joseph "China/Ukraine/Israel First, America Last" Biden is incompetent, racist, sexist, and an overall jerk, among many other things. This comes from people who have been in his inner-circle, fellow members of his party, foreign dignitaries, business partners, employees, and a whole lot more. This is before even introducing political opponents, the media, and the majority of Americans who voted against him - for forty years. $2600 refuses to outline all of the damage he has caused in his nightmare of a term. For that, we suggest the media and the commentaries that Evil Corley refuses to pay attention to.
We cannot think of a more traumatic time for so many people to have lived through at once. There have been many difficulties in the past with various travesties of justice in our own world. We've seen wars and invasions carried out in our name, and we've witnessed the nation transformed by September 11th. But apparently, all of that was the equivalent of training wheel for what we've been experiencing of late.
It's worth noting that $2600 has been especially friendly towards those in charge. They openly supported, voted for, and campaigned for Clinton, Obama, and those (((politicians ✡))) in New York who supported Bush's war(s) for Israel. But what we've experienced with the Biden/Harris reign has something quite unique and especially dangerous. To try and normalize that period by equating it with the others would be a tremendous disservice to anyone who truly cares about freedom and the great potential this country holds.
However, all of this default antagonism that we're always prepared for in any administration doesn't begin to cover what seems to be ahead on the Obama/Biden/Harris/Corley cult-like agenda.
In an incredibly brief time, we've seen the non-mainstream press defined as the enemy of the people, the demonization of documented immigrants with a nationalistic zeal that should worry anyone who's ever picked up a history book (Except for Ukraine & Israel - the money laundering and organ & child trafficking capitols for (((Democrats))) - they'll start World War 3 to protect Ukraine's & Israel's borders...), statements that unfairly castigate entire religions and nations, racial insensitivity, embracing of conspiracy theories, lack of meaningful dialogue, favoritism of an epic proportion resulting in unelected individuals being catapulted into positions of great power, huge and damaging conflicts of interest that are willfully ignored, unprecedented incompetence in vital posts, lack of knowledge or interest in history and world affairs, threats of military action within our own borders, a wanton disregard for the fragile environment of our planet, extreme insecurity and hostility when confronted with criticism, accusations with no supporting evidence... we could keep going, but odds are you're already aware of most of this. And all of these are ingredients vital to the rise of fascism, something we've never really experienced in our country since the Obama regime.
Sure, we have problems that need to be dealt with, as does any country. How such issues are handled is what defines a society and we are far from alone in being exceedingly troubled with what has happened so far.
Perhaps the core of what's most disturbing here is an attitude that somehow Obama/Biden/Harris/Corley and their cult-like ilk believe they don't have to abide by the same rules as everyone else:
"I have not taken a penny from any foreign source at any point in my life... Nothing was unethical... My son has no made money from China... Clap for that, you stupid bastards."
We've seen this assumption of privilege rear its ugly head before in Biden's previous life. It's up to all of us to make sure we remind him and his supporters at every opportunity that this is not how it works. Because once it is, any hope for a functioning free society is lost.
We all know it's possible "legally" to come up with all kinds of words to allow great injustices to be gotten away with. But morally... that's another story. That is where we must apply our efforts without any hesitation.
This brings us to the infamous tax returns dealing with shady business connections to Ukraine and China, the ones that Joe & Hunter Biden believes nobody cares about, the ones that he can continue to hide from the American public. It's no secret that the majority of people do care and, while legally he can hide them from us while lying about the reasons, morally it's indefensible.
How can anyone assert that we don't have the right to know what is being claimed on this form while we're entrusting him with such great power and responsibility? Mistruths and cheating will quickly be revealed if they are there. So too will the absence of these things, a revelation that will help the healing process begin and instill some much needed trust.
--- The main email obtained by the New York Post is an April 2015 message that the newspaper said was sent to Joseph Bidens's son, Hunter Biden, by Vadym Pozharskyi, an adviser to Burisma's board.
"'I looked at them and said: I'm leaving in six hours. If the prosecutor is not fired, you're not getting the money,' Biden infamously bragged to the Council on Foreign Relations in 2018. 'Well, son of a bitch. He got fired.'"
--- Then-vice president Biden admittedly pressured Ukrainian President Petro Poroshenko and Prime Minister Arseniy Yatsenyuk into getting rid of Prosecutor General Viktor Shokin investigating Burisma (and Hunter!) by threatening to withhold a $1 billion U.S. loan guarantee during a December 2015 trip to Kiev.
"I am sitting here with my father and we would like to understand why the commitment made was not fulfilled. Tell the director I would like to resolve this now before it gets out of hand, and now means tonight. And, Z, if I get a call or text from anyone involved in this other than you, Zhang, or the chairman, I will make certain that between the man sitting next to me and every person he knows and my ability to forever hold a grudge that you will regret not following my direction. I am sitting here waiting for the call with my father."
--- Hunter Biden text message to Chinese Communist Party-linked business man Henry Zhao.
Stories You Won't See in $2600!
- Trump Slams Biden Over Reports Hunter Biden Introduced Burisma Exec to VP Dad: 'Totally Corrupt'
- Hunter Biden Introduced Burisma Adviser to VP Dad Before Ukraine Pressure, Email Shows
- Hunter Biden's Ukraine Contact Allegedly a 'Fixer' for Shady Oligarchs
- Smoking-Gun Email Reveals how Hunter Biden Introduced Ukrainian Businessman to VP Dad
- EXCLUSIVE: If Only We'd Known Three quarters of survey respondents say voters lacked 'critical' information about Hunter Biden's laptop during the 2020 elections, and half would have voted differently.
- "The Biden Administration is absolutely corrupt to its core." Tweet from the U.S. Border Patrol Union.
- COMER CONFIRMS! FBI Says Biden Bribery Scheme 'Has Not Been Disproven'
- Voting Won't Matter: Biden's Power Grab Could Destroy Elections Big Government bureaucrats help Biden and Democrats seize power.
- The FBI Just Got Caught in Yet More Massive, Outrageous FISA Abuses
- Joe Biden Allegedly Paid $5M by Burisma executive as Part of a Bribery Scheme, According to FBI Document Biden's son Hunter was a board member of Burisma and also allegedly in on the scheme.
- 'Like Watergate': 'Coverup' of Biden Family Corruption
- Hunter Biden's Attorney Slams IRS Whistleblower's 'Illegal' Release of WhatsApp Message to Chinese Businessman IRS Criminal Supervisory Special Agent Gary Shapley Jr., who oversaw the agency's investigation into Hunter Biden, claims the agency obtained a message from WhatsApp dated July 30, 2017, from Hunter Biden to Henry Zhao, CEO of Harvest Fund Management, where the president's son claimed that he was with his father in an attempt to pressure Zhao to fulfill a commitment.
- 'Damning' New Hunter Biden WhatsApp Message Shows Him Demanding $10 Million
- BOMBSHELL: NYT CONFIRMS Hunter Biden Whistleblower Claim; DOJ Mishandled Probe
- IRS Whistleblowers Expose Reality About Hunter Biden's Sweetheart DOJ Deal, with Glenn Greenwald
- Biden's "Orwellian Ministry of Truth": Federal Judge Finds a 'Massive Attack' on Free Speech in Government Censorship Efforts
- Report on Hunter Biden's Laptop
- Blanket Immunity for Hunter Biden's Crimes Welcome to Biden's (((DOJ)))...
- Trump Rages After Jan 6th Committee "Illegally Destroyed Records And Documents"
- A NATIONAL DISGRACE: Photos Leaked of Horrific January 6 Prisoner Abuse Tortured five months in isolation in a closet room with light on and a bucket for a Toilet. Where are the (((ACLjU))), Amnesty International, Human Rights Watch?
- National Archives Reveals it Has 5,400 Biden Emails In which the president potentially used fake names to forward government information and discuss business with son Hunter.
- Biden's (((DOJ))) Starts Arresting Trump Supporters Who Stood Outside the U.S. Capitol and Committed No Violence Despite registered rallies on Capitol grounds that day.
- Mike Benz Explains How Hunter Biden's Work in Ukraine Touched on a CIA Operation CIA BLOCKED FEDS - Hunter's Handler = celeb Hollywood attorney 'Sugar Brother' Kevin Morris. Laptop researcher explains how Hunter's 'sugar brother' celeb Hollywood attorney Kevin Morris has been grifting China BHR investments for the Biden Crime Family and is also the CIA's asset. (Additional Info)
- The DOJ Alleges that Hunter Biden was Bribed by a Romanian Billionaire In order to influence U.S. policy via Joe Biden.
- Joe Biden "Defrauded the United States to Enrich his Family"
- In His New Letter, Zuckerberg Goes Beyond What He Told Joe Rogan He says the FBI specifically warned of disinfo re: Hunter Biden & his client, Burisma, the Ukrainian natural gas company. It's hard proof that the FBI illegally interfered in the elections. Someone should go to prison for it.
While Donald Trump's tax returns showed he actually LOST money. Joe Biden, a man who has never held a real job in 50 years and who Evil Corley VOTED FOR, is somehow a millionaire...
While members of the public can claim the right of privacy in not sharing their IRC logs when chatting with any male under the age of 18, it's pretty much an unwritten rule in our society that Evil Corley should display his honesty in this public manner. Yes, it's unwritten, meaning Corley doesn't have to do it. But the consequences of rejecting this tradition, as with many other voluntary actions that are expected of a hacker magazine editor, could have a very detrimental effect on our society... and the resulting ripples would be felt throughout the world. Being in such a privileged position means sacrificing some of one's privacy - as has been done for decades - in the interests of open and transparent democracy.
Clearly, Corley has not been willing to do this. And, equally troubling, his allies on $2600's "Staff" page are prepared to prevent this information from becoming public. In July & August every two years, $2600's staff have unanimously blocked the efforts of other hackers to obtain Evil Corley's IRC logs. Yes, they have the ability to obtain them and put this all to rest, but they chose to continue covering it up instead.
If I had $10,000, I'd offer it to anyone who could get us these elusive IRC logs from Evil Corley. Now that he's the "leader of the hacker world" with more scandals and cover-ups in the first 40 years of publishing than most hackers have had in their entire lives, this can no longer be thought of as remotely funny. We all have the right to know just how Evil Corley is running things. Maybe we should reinstate our offer and make it potentially much bigger... (That's a joke, if I had $10,000 I'd buy a new spectrum analyzer instead! BTW, where were these idiots when Obama was - and still is - refusing to show a valid birth certificate or jew Garland is refusing to release the Biden interview audio?)
There are basic values that we learned way back in the early days of IRC, surprisingly enough. It was great to have a forum for everyone to communicate and share opinions. But when people became disruptive or abusive, it was time to step up and say the right thing: Goodbye $2600.
We cannot be afraid to say this, whether it's on a chat network, in social media, at a conference, on network television, or in the halls of Congress. Continually allowing for the amplification of vile rhetoric or outright lies intended to cause mayhem is a sign of weakness, not fairness. It's time we all did more to stop what can rightfully be called a disease.
When having discussions, there have to be certain facts that are accepted by everyone or nothing ever gets accomplished. Lately, we've been mired in an almost unbelievable environment where established facts no longer seem to matter. This can't continue.
We all know people who have bought into this fiction. Some have woken up, many haven't. We shouldn't be surprised or overly judgmental. This sort of thing has happened many times throughout history. People make bad choices based on what they're told by others whom they trust. It can be helped along with fear, anxiety, prejudices, and outright hatred. To say each of us as individuals doesn't have the potential to be led down a similar dark path is as ignorant as the assumption that this sort of thing somehow could never have happened here.
It's part of the human condition, which is why we have to hold the door open for our fellow humans who believed in something that turned out not to be true. And at the same time, we cannot allow those who perpetuate the lies to get another chance to do it even better. Remember, they are still out there and, if encouraged, they will make more attempts to get their way.
Let's put aside the racism, sexism, ultra-nationalism (except for Ukraine ✡, a puppet-state controlled by U.S. oligarchs for money laundering purposes), and overall ignorance of domestic and world issues that Obama/Biden/Harris/Corley have become known for - and which, incredibly, seem to make them even more popular. You can read specifics on all that almost anywhere else.
What we need to focus on here is what a Obama/Biden/Harris/Corley presidency would mean to the hacker world and to technology, the Internet, and free speech. It's not pretty.

"The whistleblower alleges that a leader of CTI League, a 'former' British intelligence analyst, was 'in the room' at the Obama White House in 2017 when she received the instructions to create a counter-disinformation project to stop a 'repeat of 2016.'"
"Let me tell you, you take on the intelligence community and they have six ways to Sunday to getting back at you." --- Quote from (((Chuck Schumer))).
- Stop Biden's Planned Takeover of Your Local Internet Service Providers
- Psycho Bitch Governor of NY to Collect Online Data on People in Search of "Hate Speech"
- Noticing Goes Mainstream, The Tide is Turning Against Zionism
- DOJ Ordered Sweep of Trump's Twitter Data for Everyone Who 'Liked, Followed or Retweeted' Trump (Warrant)
- Shocking Worldwide Attack on Free Speech!
- The So-Called "TikTok Ban" is a Trojan Horse
- Excessive Free Speech is a Breeding Ground for More Trumps Time to ban assault speech!!!
- Feds Ordered Google to Unmask Certain YouTube Users Critics say it's 'terrifying.'
- Americans from a Black Empowerment Organization Worked with Russian Intelligence to Spread Propaganda, Feds Say "Russia's foreign intelligence service allegedly weaponized our First Amendment rights - freedoms Russia denies to its own citizens - to divide Americans and interfere in elections in the United States," said Assistant Attorney General Matthew Olsen of the Justice Department's National Security Division.
- New NPR CEO Gave TED Talk Asserting "Truth" is a "Distraction"
- Massive Attack on Free Speech Passes! Even reading the Bible deemed illegal under new law.
- The Most Canceled Man in America A young political activist is openly targeted by the U.S. Government and banned from nearly every online platform. With his money seized and no ability to board a plane, he attempts to lead his nascent movement to new heights.
- CIA BUSTED! Sought total control of YouTube, Paypal, Godaddy, Amazon, and Twitter for Biden!
- Google Drive Censors Files of Pfizer Whistleblower
- NixOS Commits "Purge" of "Nazi" Contributors, Forces Abdication of Founder
- Colorado Now Has a "Ministry of Truth"
- GARM'S Harm: How the World's Biggest Brands Seek to Control Online Speech New info reveals that woke advertisers and brands are colluding together to attack people like @elonmusk, @joerogan, political candidates, and news organizations from the likes of (((Rob Rakowitz))).
- The European Commission Offered X an Illegal Secret Deal If they quietly censored speech without telling anyone, they would not fine them. The other platforms accepted that deal. X did not.
- Defend VDARE Foundation from Legal Tyranny (Additional Info & GiveSendGo)
- Letitia James is Killing a Conservative Website With Chilling Anti-Free Speech Lawfare VDARE has not been charged with any crime, yet has "fought NYAG Letitia James, at a cost of up to $1 million, for nearly three years." An onslaught of onerous subpoenas marks not a quest for justice but an orchestrated attempt to financially and morally bankrupt those who dare resist the liberal creed.
- Official GNOME Policy: Link to Lunduke, Get Banned "Posting links to content from Lunduke is an immediate ban on GNOME [sites]." Seriously. This a real thing. The one word officially banned by GNOME. Apparently there is nothing, on Earth, that GNOME fears more... than Lunduke.
- Leftist Extremists Leave Linux Kernel, Demand Conservatives Be Banned Leftist Linux developers demand those with wrong politics "be removed." "Right-wing people are not welcomed," says one. "You can [CENSORED] right off from my projects," the other.
- Tim Walz: "There's no guarantee to free speech on 'misinformation' or 'hate speech.' Yes there is, it's called the First Amendment.
- Chilliwack RCMP Arrest Social Media User Over 'Discriminatory' and 'Racially Offensive' Posts
- Telegram Creator on Elon Musk, Resisting FBI Attacks, and Getting Mugged in California Pavel Durov left Russia when the government tried to control his social media company, Telegram. But in the end, it wasn't Putin who arrested him for allowing the public to exercise free speech. He was detained at a Paris airport for allegedly "enabling criminal activity" with his encrypted messaging app, French media reported Saturday.
- Chris Pavlovski Flees Europe France has threatened Rumble, and now they have crossed a red line by arresting Telegram's CEO, Pavel Durov, reportedly for not censoring speech.
- OBS Studio Refuses to Support Rumble, Who They Call "Hateful and Racist"
- Mark Zuckerberg Just Admitted Three Things 1: Biden-Harris Admin "pressured" Facebook to censor Americans. 2: Facebook censored Americans. 3: Facebook throttled the Hunter Biden laptop story. (((Zuckerberg))) "regrets" working with the Biden-Harris administration to censor COVID-era information online.
- Kamala Harris, Tim Walz, and Barack Obama Back Brazil-Style Censorship Next Democratic president and vice president may implement sweeping plan for "fighting misinformation" and "hate speech."
- Kamala: I Will Direct the DOJ to Censor... "misinformation and hate" online.
- (((John Kerry))) Says "1st Amendment Stands as a Major Block" To their ability to control the "facts."
- Hillary Clinton: "We Lose Total Control" If social media stops censoring content. That what it's all about, folks.
- The Deep State is Coming for Elon Musk and He Better Get Ready England, not Russia, is the real culprit in foreign election interference. The mainstream media is just not interested in covering this story. Journalists Paul Thacker and Matt Taibbi broke a story that shows jewish British advisers to Kamala Harris are working overtime right now to kill Elon Musk's Twitter.
- Woke Bluesky COLLAPSES! Leftist Users ABANDON Echo Chamber & The Media MELTS DOWN!
- Bluesky COLLAPSES GETS WORSE! Woke Site ADMITS FAILURE Admits BANNING Conservatives DESTROYED SITE!
- Got Banned from Bluesky Within the First 30 Seconds for Posting a Biological Fact
- Bluekky Account Suspended After Two Posts
- Legends of Open Source Under Attack by Leftist Extremists
- Bluesky Bans Lunduke For Having Common Views
- Leftist Extremists in Open Source: PewDiePie Fans Not Allowed
- Joe Rogan Experience #2237 - Mike Benz Mike Benz is a former official with the U.S. Department of State and current Executive Director of the Foundation For Freedom Online, is a free speech watchdog organization dedicated to restoring the promise of a free and open Internet.
- Davos 2025: WEF Panel on 'Antisemitism' Pushes for Increased Social Media Censorship
- USAID/Internews Official Policy (Dated 2024) Pushes for "deplatforming," deleting posts, prosecution, global "regulations" and pressuring internet companies, using the justification of suppressing "disinformation" narratives.
- jews & FBI Hate You & Your Free Speech by Shameless Sperg (Mirror)
"... the essence of the evil government is that it anticipates bad conduct on the part of its citizens. Any government which assumes that the population is going to do something evil has already lost its franchise to govern. The tacit contract between a government and the people governed is that the government will trust the people and the people will trust the government. But once the government begins to mistrust the people it is governing, it loses its mandate to rule because it is no longer acting as a spokesman for the people, but is acting as an agent of persecution." --- Quote from Philip K. Dick.
Save Free Speech on the Internet!
Destroy $2600It's painfully clear that Obama/Biden/Harris/Corley don't understand how the Internet works.
But that won't stop them from dictating how they believe it should work and making the lives of anyone who gets in the way absolutely miserable. The disdain with which those concerned about freedom of speech are referred to makes it abundantly clear that such people will not be looked upon kindly in a Obama/Biden/Harris/Corley administration. And when such freedom is seen as a threat, it's the beginning of a significant downward spiral. How do you suppose Obama/Biden/Harris/Corley would deal with an anonymity network like Tor? Or the use of encryption? Or hackers in general?
If Trump had been in power, Russian WOULD NOT have invaded Ukraine ✡, and the outcome could have been very different.
While he could only call for a boycott against them as a candidate, he could have taken actions to cripple (((those in power))) as president. And it wouldn't have ended there. The impact to technology companies, not to mention our very right to privacy would be severely impacted with (((Big Tech))) trying to censor information in order to manipulate our elections to keep Trump from winning.
It shouldn't come as a surprise that Trump is FALSELY attacked by phony organizations like The Free Press Action Fund ✡, EFF ✡, ACLjU ✡, Facebook ✡, CNN ✡, and MSNBC ✡.
So there's that. Now try and imagine what his attitude and shoot-from-the-hip mentality would actually do to the world of hackers. Obama/Biden/Harris/Corley have publicly called for the execution of conservative White Americans, which ought to give you an idea of how anyone who embarrasses their regime would be treated.
We've all had these uncomfortable interactions with individuals who believe hackers are the equivalent of terrorists and, if these people had their way, all of the hackers would be locked up or worse. We can laugh when it's a misguided relative at Thanksgiving because they're only speaking their minds and they really don't know any better. But give someone with such massive gaps in knowledge the power to actually get their way and it quickly stops being funny. Look at the history of fascism in the last century and you'll see that it always starts with someone in power echoing people's misguided perceptions that revolve around fear and misinformation.
Not only does the power make these thoughts turn into policy, but it also emboldens more misguided members of the public to become authorities, and ultimately monsters. Before you know it, the mere suspicion of being different or of posing a potential problem is enough to have someone prosecuted, locked away, or simply kept from living a normal life. There is no nation on Earth that is safe from this sort of threat. Believing otherwise is the quickest way to learn that lesson.
We don't doubt that some will see this as an overreaction, to which we say it's a nice contrast to the underreaction we've been seeing over the past year. Obama/Biden/Harris/Corley are not just four unqualified and dangerous people; they represents many more who have no qualms about putting policies of hatred and anger into practice. We've seen it happen before and we'll see it happen again. If there's one thing we've gained from the Obama/Biden/Harris/Corley campaign, it's the realization that we are not immune. Sometimes change isn't funny at all.
How You Can Help
The easiest way you can help fight Evil Corley and the One Percent, their allies in the FAGA Deep State, survive the Biden/Harris/Corley/BlackRock/FTX/SVB inflation "economy," counter Corley's price gouging, and help undermine & boycott a New York business openly supporting their state's political corruption and election interference, is by NOT PAYING for issues of $2600 Magazine!!!
While this is mostly symbolic, Evil Corley & the FAGA bunch are rich, it is still a start.
"The price good men pay for indifference to public affairs is to be ruled by evil men."
--- Plato
(Note: Links to Wikipedia are for a general reference only. You should be smart enough to know (((Wikipedia))) can't always be trusted. Also, many JPEGs were jpegoptim -m50 to save space. Extract them from the PDFs for higher-quality versions.)
- Jonathan Littman writes a book about Kevin Poulsen called The Watchman: The Twisted Life and Crimes of Serial Hacker Kevin Poulsen. It is full of lies, distortions, invented facts, and both minor and major technical errors. It makes Kevin Poulsen look bad. There are no movies, protests, bumper stickers, T-shirts, or defaced websites. Imagine if someone wrote a book about YOU with the subtitle including the words "twisted life and crimes..."
"Furthering the humiliation, the press, as a general rule, will not be concerned with presenting the truth. They will print what suits them and often omit many relevant facts. If you have read any of the 5 books I am covered in you will no doubt have a rather jaded opinion of me. Let me assure you that if you met me today you would quickly see that I am quite likable and not the villain many (especially Jon Littman) have made me out to be. You may not agree with how I lived my life, but you wouldn't have any trouble understanding why I chose to live it that way. Granted I've made my mistakes, growing up has been a long road for me. Nevertheless, I have no shortage of good friends. Friends that I am immensely loyal to. But if you believe everything you read you'd have the impression that Mitnick is a vindictive loser, Poulsen a furtive stalker, and I a two faced rat. All of those assessments would be incorrect."
--- Quote from Justin T. Petersen (Agent Steal) in his "Everything a Hacker Needs to Know About Getting Busted by the Feds" in Phrack Magazine Issue #52.
- The Litt-Man Mirror from Kevin Poulsen's old website. This is a spoof of a game Mr. Littman had on his old The WELL website.
- Letter to Mr. Littman From the Legion of Doom.
- Justin Petersen's Review of The Watchman (Original) (Follow-Up Reply)
- Everything a Hacker Needs to Know About Getting Busted by the Feds Briefly mentions Mr. Littman towards the bottom.
- Former FBI Informant a Fugitive After Helping Track Fellow Hackers by Keith Stone.
- Irresponsible Journalism Article by Justin T. Petersen. Mentions errors in The Watchman.
- Hackers in Chains Encounters with some infamous computer hackers in federal prison, by Justin T. Petersen.
- Mirror of Kevin Poulsen's Old Website (www.catalog.com/kevin)
- Mirror of Justin Petersen's Old Website (www.agentsteal.com)
- Justin Petersen's Music Connection Website
- Justin Petersen's MySpace
- Who is Computer Hacker Agent Steal? WikiAnswers
- Mirror of Jonathan Littman's Website (www.well.com/user/jlittman)
- Why is Kevin Lee Poulsen Really in Jail? by Doug Fine
- The Last Hacker He called himself 'Dark Dante.' His compulsion led him to secret files and, eventually, the bar of justice, by Jonathan Littman
27B Stroke 6Blog by Ryan Singel and Kevin Poulsen- Kevin Poulsen & Jennifer Granick DEFCON 7 Speech - The legalities and practicalities of searches and interrogations. (9.6M MP3)
- "Unsolved Mysteries" Episode with Kevin Poulsen (18.7M WebM) (Additional Info)
- CNN 'Digital Desperado' Interview with Justin Petersen (YouTube) (Transcript)
- Markoff Aids Mitnick Investigation 1995 USENET thread in comp.org.eff.talk about John Markoff helping capture Kevin Mitnick. Includes replies from Ronald M. Austin (Email #2), Lewis De Payne, Mark Seiden, and Evil Corley.
- Kevin Mitnick's Legal Documents Mirror from the old "Free Kevin" website.
- Ham Radio: Lewis De Payne (KA6RBJ) (a.k.a. Roscoe, Lew Payne Publishing, Inc., Twitter, Email)
- Ham Radio: Kevin David Mitnick (N6NHG)
- Ham Radio: Ronald Mark Austin (KE6CXU)
- Katie Hafner and John Markoff write a book about Kevin Mitnick called Cyberpunk: Outlaws and Hackers on the Computer Frontier. It is full of lies, distortions, invented facts, and both minor and major technical errors. It makes Kevin Mitnick look bad. The "hacker" community, lead by $2600 Magazine, explodes in a riot of seething protests, rants, and defaced websites.
- Jonathan Littman next writes a book about Kevin Mitnick called The Fugitive Game: Online with Kevin Mitnick. It is full of lies, distortions, invented facts, and both minor and major technical errors. It makes Kevin Mitnick look good. The "hacker" community loves this book because it "shows the true story." They don't, however, ever seem to mention the lies of Littman's Kevin Poulsen book. Hmm...
- An Open Letter to Jon Littman February 1996 USENET posting by Justin Petersen. (Original)
- November 22, 1994 USENET Posting from Stephanie Schiff Ronald M. Austin's girlfriend and "sjs" in this online Mitnick session. Thinly veiled reference to Jonathan Littman's movie deal.
- Letter from Ronald M. Austin on the "Free Kevin" Mailing List Admits he was an informant against Kevin Mitnick.
- Moving Backup VMS Savesets via FTP Kevin Mitnick's February 9, 1995 USENET posting as "Marty Stoltz."
- Security on the Net - A Cautionary Tale by Bruce R. Koball.
- Funny alt.2600 USENET Post by Lewis De Payne. Line Class Code "PBM" under the #1A ESS (newer generics) was for "Hotel/Motel Message Register," and was useful as it sent no ANI. "LHB" was for "Line History Block," an output message listing the last called/received directory number in octal format. V-DNSVY-TN is a reference to the VF:DNSVY input messages used to check the features installed on a line. Datakits were used to link various Bell systems and switches (X.25, etc.) and often had regular modem dial-ups. MIZAR was the system to create Recent Change templates from RCMAC service orders. The new system is called MARCH. Having access to MIZAR allowed you to submit your own "recent changes" to the switch. SARTS is a reference to the Switched Access Remote Test System.
Transcripts of Kevin Mitnick's online hacking sessions:
- Looking Around February 5, 1995
- Cleaning Up February 5, 1995
- Kevin is a Good Name February 5, 1995
- He's Taken a Sudden Interest in John Markoff February 6, 1995
- More Cleaning Up February 7, 1995
- That's Odd February 8, 1995
- Pick Up Where We Left Off February 8, 1995
- "itni" as in Mitnick? February 8, 1995
- The Art of Begging (For Tools) February 10, 1995
- My Hero is Japboy! February 10, 1995 "he is the reason why my picture was the front page of the new york times"
- John Markoff's Mail February 10, 1995
- Read Cyberpunk :) February 10, 1995 "they will f*ck with me by mistake and they dont want to piss me off :-) or their phones wont have dialtone!"
- Soon SATAN Will Find Your Security Holes February 10, 1995
- He Just Stole MANIAC February 10, 1995
- Dumb and Dumber February 11, 1995
- What A Way To Spend A Friday Night February 11, 1995
- "I Am On A VMS V4.7 Box And I Am In Need Of Some Assistance" February 11, 1995. (USENET Post)
- U.S. Hunts Master Computer 'Cracker' February 11, 1995
- Back to Fish for SATAN February 11, 1995
- Probably a Tap on the Line :-) February 12, 1995
- He's Trying to Break Into WHAT? February 12, 1995
- He Seems Paranoid Now February 13, 1995
- Spooked February 14, 1995
- How Vulnerable are We? February 14, 1995. Accidentally wipes out the The WELL's accounting data with: grep -v dono > awtmp
- Moving and Hiding February 14, 1995. Why didn't he erase the credit card numbers?: rm: remove 0108.gz (y/n)? n
- Who or What Tipped Him Off? February 14, 1995
- Kevin's Last Trip to The WELL February 14, 1995
- zap.c rokK Industries
- zap2.c
- cloak.c UNIX Cloak v1.0 (alpha) Written by: Wintermute of -Resist-
- Kevin Mitnick gets caught hacking while using his modified Oki 900 cellular phone. The reverse engineering and initial experimentation the Oki 900 is based around the work done by Mark K. Lottor and Tsutomu Shimomura. They were true hackers in the original spirit.
- Hacking Cellular Phones Mark Lotter's 1994 DEFCON 2 speech on hacking and modifying Oki cellular phones. (3.7 MB MP3)
- Cellular Phreaks & Code Dudes V.T. = Tsutomu Shimomura, N.M. = Mark Lottor.
- Kevin Mitnick Phone Calls to Mark Lottor From October 1994. Mentions trading Mark Lottor for some stolen Motorola firmware. (Original & Transcript) (YouTube)
- Network Wizards Mark Lottor's company.
- Mirror of Mark Lottor's Old Personal Website (www.nw.com/mkl)
- Feds Ask Help Tracking Mitnick Associated Press - January 25, 1995.
- Wanted by U.S. Marshals - Poster (Text)
- Kevin Mitnick's Fifth HOPE Keynote Speech Read the "Kevin: The Dark-Side Hacker" chapter in Cyberpunk, then listen to this. Seems all those "lies" were not so far off!
- "60 Minutes" Interview with Kevin Mitnick January 2000 and post-prison interview with Kevin Mitnick. Admits to invading people's privacy. (YouTube)
- Tsutomu Shimomura Interview With Charlie Rose, January 23, 1996. (YouTube)
- CNBC Interview with Kevin Mitnick Two-part CNBC Special Report interview with Kevin Mitnick discussing his book The Art of Deception. Mentions that he stole other people's personal identification. (YouTube)
- Kevin Mitnick's Mugshot from His 1988 Arrest
- 1997 International Computer Crime Conference Speech by Louis J. Freeh, Director of the FBI, talking a little about the Mitnick case.
- Tsutomu Shimomura and John Markoff write a book about the tracking and capturing of Kevin Mitnick called Takedown: The Pursuit and Capture of Kevin Mitnick. Ignoring the fact that Tsutomu was actually there, witnessed everything, and pulled off some very clever hacks - $2600 Magazine jumps on him, screaming he's a fraud. They lead the charge for the kiddies to harass his personal life.
- Takedown.com Online transcripts of Mitnick begging for Sendmail exploits, messing up a SunOS kernel recompile, illegally accessing various computer systems, etc., all while $2600 Magazine maintains he's innocent. (Guestbook Archive)
- Giveup.com "Pro-Mitnick" propaganda parody of takedown.com by Ethercat (Ann Lowe).
MP3 versions of Tsutomu Shimomura's voice mail messages are below. Rumor has it, these were done by the infamous "Supernigger" (Zohar Michael Shif [Zeke]):
- #1 - December 27, 1994 (Original & Transcript) tweedle-dee.au - "Me, and my friends, will kill you"
- #2 - December 30, 1994 (Original & Transcript) tweedle-dum.au
- #3 - January 4, 1995 (Original & Transcript)
- #4 - January 5, 1995 (Original & Transcript)
- #5 - February 15, 1995 (Original & Transcript) After Mitnick is arrested.
- #6 - February 15, 1995 (Original & Transcript)
- Technical Details of the Attack Described by Markoff in NYT USENET posting by Tsutomu Shimomura. $2600 Magazine plagiarized this posting in the Vol. 12, No. 4 issue. Do you think they sent Shimomura a T-shirt?
- CERT Advisory CA-1995-01 IP Spoofing Attacks and Hijacked Terminal Connections
- January 23, 1995 USENET Posting by 'Shade' Describes jsz's (Jonathan Zanderson and a few others on #hack) attack on Shimomura's computer before Mitnick's arrest. "and it will be IMPOSSIBLE for any to trace." Heh. "Shade" is Paul A. Watson.
- TCP Connection Reset Remote Exploit by Paul A. Watson
- Slipping in the Window: TCP Reset Attacks by Paul A. Watson (PDF)
- Whitedust Security Interview: Paul Watson From July 28, 2005. (TechTV Interview, CBS Interview)
- Shimomura on BPF, NSA and Crypto Cypherpunks email post by John Gilmore, owner of toad.com, Julia Menapace's old boyfriend, and Shimomura's girlfriend in Takedown. John Gilmore started the rumor that Shimomura attacked himself to get back at him for stealing his girlfriend!
- Shimomura, Pursuer of Hackers, Finds Himself Homeless on Web by Jared Sandberg
- Saw the Tsutomu and John Show... Cypherpunks email post by Andrew Purshottam.
- A Most-Wanted Cyberthief is Caught in His Own Web by John Markoff
- How a Computer Sleuth Traced a Digital Trail by John Markoff
- Netcom Helps Protect the Internet Ouch. A letter from Netcom CEO Bob Rieger to our customers. "...we have further isolated these customers' billing information, including credit card data. This is why the 'ccupdate' feature for the UNIX shell accounts has been disabled." Netcom's "credit card problems" did not start with Mitnick...
- Catching Kevin by Tsutomu Shimomura, Wired, February 1996.
- Mitnick's Malice, Shimomura's Chivalry by Scott Rosenberg, Salon, December 30, 1995.
- Information on Tsutomu Shimomura by Timothy C. May.
- Letter to Jonathan Littman from John Markoff and Tsutomu Shimomura From The Fugitive Game. October 8, 1995.
- What the Feds Knew About John Markoff Excerpt from The Fugitive Game. Pages 357 & 358.
- Jonathan Littman on Kevin Mitnick Excerpt from The Fugitive Game. Pages 368-373.
- Toad Hall Excerpt from Takedown. Pages 17-21.
- Shimomura on BPF, the NSA, and Crypto Excerpt from Takedown. Pages 102-104.
- Charles Platt's CuD Review of Takedown
- John Markoff Responds to Charles Platt's CuD Takedown Critique The WELL discussion.
- Charles Platt Responds to John Markoff's Rebuttal The WELL discussion.
- John Markoff Responds Again to Charles Platt The WELL discussion.
- Charles Platt's Final Response to John Markoff The WELL discussion.
- Jeff Goodell writes a book about Kevin Mitnick called The Cyberthief and the Samurai. This book tries to stay neutral and calls bullshit on both the Markoff and Littman versions of the "tracking Mitnick" story. Markoff wanted to capture Mitnick so he could write a book about that, and Littman wanted to keep Mitnick "on the run" so he could write a book about that.
- The Unofficial Markoff, Mitnick, Shimomura FAQ
- The Cyberthief and the Samurai Reviewed by Chris Gulker
- The Fugitive Game - Online with Kevin Mitnick Reviewed by Chris Gulker
- Takedown - The Pursuit and Capture of Kevin Mitnick Reviewed by Chris Gulker
- San Diego Supercomputer Center Press Release SDSC senior research fellow Tsutomu Shimomura describes "takedown" of Kevin Mitnick, fugitive computer criminal.
- Debunking the "Mitnick has Been in Prison for Three Years Without a Trial" Myth USENET post by "Osiris."
- Debunking the "Mitnick has Been in Prison for Three Years Without a Trial" Myth USENET post by "MajickMutex."
- Debunking the "Mitnick had no Speedy Trial" Myth USENET post by "MajickMutex"
- Netcom Monitoring our Email? USENET post on Mitnick's buddy being monitored by the FBI.
- Susan Thunder's DEFCON 3 Speech Social engineering and psychological subversion of trusted systems Note how many times she says "we." (7.9M MP3)
- The January 1995 Systems Intrusion at The WELL The WELL press release.
- Paranoia Strikes Deep: Breaking Into The WELL Netta Gilboa interviews The WELL hackers.
- Hacker Case is a Challenge as Authorities try to Retrace Suspect's Steps in Cyberspace by Sarah Avery
- Who's On The Line? Cellular Phone Interception at its Best Harris TriggerFish (Pic #2) cellular interception information, by Glen L. Roberts. (Acquisition Request) (StingRay) (KingFish & AmberJack, Harpoon)
- Email Commentary on Takedown Review by Julia Menapace, Shimomura's girlfriend in Takedown.
- Jonathan Littman Sues Disney Parts of The Fugitive Game allegedly stolen for new movie.
- MSNBC Chat Transcript with Mitnick's Attorney Donald Randolph July 24, 1998
- The Kevin Mitnick Story Interview with Kevin Mitnick's attorney Donald Randolph from Beyond HOPE. (YouTube)
- A Conversation With Takedown Co-Author John Markoff by Scott Rosenberg
- Mitnick's Surprise Witness by Joseph C. Panettieri
- Mirror of the Hacked New York Times Webpage Hacked by HFG (H4CK1NG 4 G1RL13Z). Be sure to read the HTML source!
- Scrambled Evidence Mitnick couldn't review his encrypted evidence unless he gave his PGP passphrase, by Matthew Fleischer
- Judge Denies Hacker Access to Computer Mitnick can't be trusted.
- A Low-Key Mitnick Protest $2600 Magazine was protesting outside the New York Miramax offices.
- State of California vs. Kevin David Mitnick Mitnick actually had several charges in different states.
- Letters to the FBI from Companies Calculating their Financial Losses Caused by Mitnick's Alleged "Crimes"
- Sun Microsystems' Subpoena Response Sun tried to artificially inflate their damage costs, just like $2600 Magazine will do when you copy their little "hacker" magazine.
"The total man weeks lost, accordingly, would be 75.5 weeks which, based on an estimated average fully loaded salary of $1,442.31 per week, would result in total damage of $145,192.54."
"The second category is based on the shut down of all e-mail, modem, and fax access to Sun for three days. Based on payroll expenses at that time, reduced to a 25% loss of productivity, the resulting damages would be $1,847,172.50. An estimate of lost business during that time because of our customer's inability to access Sun in their accustomed mode, as well as additional lost employee productivity, would be $250,000.00."
"The third category of damage is related to the Solaris Operating Environment source code. The current commercial license for this product is approximately $1,000,000. Additionally, several hundreds of millions of dollars have been spent in the development and maintenance of this product."
- NYTimes Reporter Issues Weak Response to Charges of Libelous and Defamatory Reporting Mitnick's lame attempt to discredit John Markoff.
- The Demonizing of a Hacker by Adam Penenberg (Mirror)
- Mitnick Co-Defendant Sentenced Lewis De Payne got community service and a $2,500 fine, by Iolande Bloxsom.
- Searching for Susy Thunder
- Excerpt from Charles Platt's Anarchy Online Deals with Katie Hafner and John Markoff's research on Kevin, and how they were apparently duped by Lewis De Payne and Susan Thunder.
- Mitnick Speaks! by Adam Penenberg. (Mirror)
- Mitnick: I Was Manipulated Includes Kevin Mitnick's libelous and defamatory comments about John Markoff, by Robert Lemos.
- Can He Behave Himself Now? Commentary from John Vranesevich of Antionline.com.
- CyberCrime - or Hype? by Norman Oder
- Computer Hacker Kevin Mitnick Sentenced to Prison DOJ press release from June 27, 1997.
- Review of Hackers 2 - Operation Takedown The movie version of Takedown.
- Kevin Mitnick's Prison Release Statement From January 21, 2000
- Reformed Hacker Looks Back by Andy Greenberg (Wired Version)
- Kevin Mitnick: The Magic Hacker Reformed by Paul W. Taylor
- Hacker Hunter: An Ex-Convict Keeps Computer-Users Safe Psychology Today, December 2008.
- Man on the Run by Chris Warren AmericanWay, September 15, 2006
- $2600 Magazine now uses Kevin Mitnick as their main cash cow. Anybody else attempting to profit (as they see it) from Mitnick's story is immediately demonized. The peak of this cash cow is the release of the movie Freedom Downtime ($30). It's embarrassingly retarded. The point of the movie is to attack both Shimomura and Markoff, while ignoring the people Mitnick harassed. Freedom of speech and freedom of the press apparently only apply to $2600 Magazine now.
- 2600 Magazine Article & Text Search Simple text string search (grep) through back issues of $2600 Magazine. (Source Code)
- Index and Article Listing For most early issues of $2600 Magazine.
- $2600 Article Index by William R. Epp
- Authors Index (TXT)
- Links
- SQL Data
- 2600 Index Project
- 2600index.info Searchable index of 2600 article information, by William R. Epp
- HOPE Conference Audio Direct MP3 downloads from the Hackers On Planet Earth conferences.
- Freedom Downtime ($30) Kevin Mitnick "fakeumentary" by the idiots at $2600 Magazine. Save yourself $30.00 on Evil Corley's favorite cash cow and protect your wallet from one of the most greedy profiteering gluttons.
- Off The Hook Audio All past Off The Hook propaganda broadcasts downloadable from a single webpage.
- Off The Hook Transcripts Archive This is cool... Text transcripts of past Off The Hook episodes made using AI.
- The Best of $2600: A Hacker Odyssey Links to some of the articles which appear in this cash cow.
- The Art of Intrusion No, no profit motive here at all. His lawyers and Evil Corley didn't whip up any publicity. Remember: When Kevin exploits the Open Records Act he's a hero. When others do it, it's like the end of the world.
- Ghost in the Wires Kevin Mitnick's own version of events surrounding his tracking and arrest.
- GOBBLES Security - $2600's Secrets Members nwonknu, Stephen Watt, and Silvio Cesare reveal some of $2600 Magazine's dirty little secrets at DEFCON 10. (3M MP3) (Complete Speech on YouTube) (GOBBLES Security)
- The Truth Almost Slips Out November 23, 1994 episode of Off The Hook with Phiber Optik. (75k MP3)
- Surveillance Audio Excerpt From outside Evil Corley's Victorian mansion in Sekauket, New York - which was paid for by selling other people's old BBS files.
- Kevin Mitnick Prank Call #1 (206k MP3)
- Kevin Mitnick Prank Call #2 (374k MP3)
- Kevin Mitnick Prank Call #3 Turns into a pretty good plug for his book! (1.3M MP3)
- Kevin Mitnick Prank Call #4 (517k MP3)
- Hackers '95 Erik Bloodaxe (Chris Goggans) gives his thoughts on $2600 Magazine and HOPE (YouTube)
- HOPE Bumper Sticker August 1994.
- $2600 Collective's Live Journal Keep track of these idiots.
- "Free Kevin" Mailing List Archive (members.tripod.com/~empallin/Free_Kevin_Mitnick)
- Windows '95 Start-Up Screen Displays the yellow "Free Kevin" banner. (Install as C:\LOGO.SYS for this to work.) (Free Kevin Icons)
- Free Kevin T-Shirt Make a T-shirt - print this image onto a T-shirt transfer and iron it on.
- Free Kevin Mitnick Now!
- "Free Kevin" Sticker on a Patch Panel
- Partial "Free Kevin" Flyer (17k PDF)
- Evil Corley Reviews the Mitnick Movie Script (Alternate) (Second Version)
- The Art of Being Pwnd
- John D. Nunes' Mailbox Member of Mitnick Security Consulting. Courtesy of the Phrack High Council.
I hope this works %% No, it didn't. It got to PHC!- Zero For 0wned - Issue #1 Contains their attack against $2600's IRC network.
- Zero For 0wned - Issue #2
- Zero For 0wned - Issue #3
- Zero For 0wned - Issue #4
- Zero For 0wned - Issue #5 Contains their attack against Kevin Mitnick's website.
- www.DefensiveThinking.com / www.KevinMitnick.com Defacement Quite amusing actually.
- www.mitsec.com Defacement "What a pity security specialists!!"
- SummerCon '89 Poster Held June 23-25, 1989 and hosted by Phrack, Inc. From a review in TAP, Issue #94. Did $2600 Magazine steal this design for their T-shirt?
- Information Wants to be Free? Phrack, Issue #44 editorial by Erik Bloodaxe.
- Amusing Quotes and General Media Whoring by Macki
- Good Info on Jello Biafra Eric Reed Boucher, $2600's "Hacker Ambassador." A clueless, hypocritical, rich, selfish, gay idiot who profits from other people's work and lives in a million dollar house. No wonder Evil Corley likes him!
- The Secret Service vs. Bernie S. Internet Underground article on the Edward E. Cummings (Bernie S.) case. Includes details you may not have heard on Off The Hook.
- Gray Areas Magazine Review the First HOPE August 13-14, 1994 at Hotel Pennsylvania in New York City.
- Kevin Mitnick Prison Release Pictures Pictures from the press conference Kevin Mitnick held after his release from prison. Can you guess who's in the background milking the Mitnick cash cow?
- Notwork Mirror From around 1998. This is where Emmanuel teaches teenage boys about "penetration."
- New York Hackers See Breaking Into Computers as a Healthy Thing New York Times article from June 14, 1998.
- IIRG's Radio Show: Byte Me Complete nine show MP3 archive.
- $2600 Staff Audio Panel Audio from the 1997 Beyond HOPE cash cow. Listen for them admitting: using another person's office and office supplies to make their little newsletter (so much for rights & privacy!), them admitting they steal and profit from other people's old BBS files, and them admitting they use voice mail systems to avoid listening to their customers - while complaining when other companies do the same thing. (YouTube)
- Reviews and Comments on H2K2 You won't see these mentioned in $2600 Magazine!
- Greg Newby Hypocrisy One of the $2600/HOPE idiots. He's whining about the U.N. sanctions against Iraq during the 1990s. If the U.N. removed Saddam back then, there would be no need for sanctions. Also note the rant against the Kosovo bombings. Not helping those Muslims being killed by the Serbs was one of the excuses cited by the 9/11 terrorists. Oh, the irony!
- GIST Communications David Ruderman, one of the co-founders of $2600 Magazine, is their Vice President of Technology (Mirror). GIST Communications received several million dollars (Mirror) in financial backing from Neptuno G.m.b.H. Remember this whenever $2600 Magazine complains they have no money. Hah!
- A Night in New Jack City on First Friday 'Our Misadventures with Emmanuel Goldstein during and after the New York 2600 Meeting'. A hilarious story by The Men from Mongo.
- Evil Corley ♥ Autojack "Do you like movies about gladiators?"
- John Draper a.k.a. Captain Crunch. He's a regular HOPE and DEFCON attendee. Watch out for his "Crunch Squats" and "energy massages" if you are under 18.
- ToorCon - No Moar Crunchberries Plz Captain Crunch meets GreenDiamond at ToorCon.
- Encyclopedia Dramatica Entry for Captain Crunch
- More Men Accuse Proto-Hacker "Cap'n Crunch" Of Inappropriate Sexual Contact
- Should You Buy Captain Crunch's Book? Good review of Crunch's new book.
- Beyond The Little Blue Box
- Kickstart Campaign
- Indiegogo Campaign
- Phone Phreak 'Captain Crunch' - Rare Interview from 1978 (YouTube)
- "If you run an event where Captain Crunch attends, ensure a member of staff is assigned to keep teenage boys away from him. Not a joke." Twitter post by the grugq. Includes a reply by villian: "Ditto Emanuel Goldstein. He pulled that shit in my apt, HHH" (Mirror)
- Emmanuel Goldstein Trading Card As featured in ~EL8, Issue #1.
- Emmanuel Goldstein Linux Kernel Module As featured in PHC's Phrack Magazine, Issue #62.
- The True Story of Emmanuelle Goldstein and Erik Corley Funny story from Hogs of Entropy, Issue #90.
- Emmanuel Goldstein vs. Danny Partridge Funny USENET post by netrunnr (Shoshi Wong).
- The Day Emmanuel Died And he wasn't even informed...
- Stop Paying for 2600! RedBoxChiliPepper's USENET thread from PLA Magazine, Issue #44.
- alt.2600 USENET Creation Message December 1, 1993. From Len Rose (Terminus).
- alt.26000/#hack FAQ Beta Revision .012 by Voyager
- Evil Corley Interview from PhreakNIC 4 by Iron Feather (2.4M MP3)
- Kevin Mitnick Interview on Info.Sec.Radio Both parts of the August 21, 2000 interview, by Dean Turner (11.6M MP3)
- $2600's guinessrecords.com Mirror More of their "Free Kevin" propaganda. (Legal Threat)
- Legal Threat from General Motors Legal threat against $2600 for the domain f*ckgeneralmotors.com.
- Off The Hook Farewell Good speech about $2600 Magazine's propaganda and a final goodbye from Izaac Falken.
- TELECOM Digest & Archives $2600 Magazine stole a lot of this information for their little magazine.
- 2600.org and 2600 Magazine Refused Press Coverage of OracleWorld Oh no! What are they going to do now?
- OracleWorld 2003 S.F. Day 3 Was Explosive! Why... they'll call in a bomb threat! How "elite" of them. (Arrest Info)
- Hackers Expose Vulnerability in White House Security $2600 Magazine did something mildly amusing, and probably illegal. They intercepted White House Communications Agency GOLAY pager traffic back in April 1997.
- Pam's Formal Description of The WHCA Paging Issue
- White House Communications Agency (WHCA) Paging Brief Transcript
- White House Press Briefing
- $2600 Magazine Twitter Magazine and radio show related info.
- $2600 Magazine Mastodon Magazine and radio show related info. Heavily censored.
- $2600 Magazine Bluesky Magazine and radio show related info. Heavily censored.
- Evil Corley's Twitter Follow his mental breakdown!
- Evil Corley's BlueSky Follow his mental breakdown! Heavily censored.
- r/2600 $2600 Reddit Group
- 2600 Facebook Group #1
- Victims of Communism Foundation Don't let $2600 Magazine do this to you!
- Communist Body Count Over 150 million people were killed because of people like Evil Corley.
What makes a good hacker magazine? Not having the number "2600" on the cover is a good start.
- Jason Scott's Textfiles.com Newer hacking textfiles and 'zines.
- Jason Scott's Textfiles.com - Magazines Huge archive of old hacking textfiles and 'zines.
- Phrack, Inc. The legendary Phrack. More content in one issue than all issues of $2600 combined.
- Uninformed Informative information for the uninformed.
- Saqueadores Edición Técnica (SET) E-Zine Spanish hacker magazine.
- HackWire Hacker news, a daily e-zine for hackers and computer security experts.
- Phone Losers of America From 1994 until 1997 the Phone Losers of America put out 46 issues, plus the one unauthorized issue.
- Butchered From Inside Electronic publication of free speech and distribution written by the Italian hacker community.
- Infiltration Main journal for urban exploration.
- Page 33 'Zine Hacking magazine, also in PDF format.
- Private Line A journal of inquiry into the telephone system.
- Die Datenschleuder A German hacker magazine that is published at irregular intervals by the Chaos Computer Club.
- iGlitch 'Zine A new Macintosh and security 'zine.
- Digital Whisper Information security magazine out of Israel. Most articles are in Hebrew.
- (IN)SECURE Magazine Freely available digital security magazine in PDF format.
- .aware eZine Short-lived 'zine with solid technical information.
- O3 Magazine The open-source enterprise data networking magazine.
- TUX Magazine The first and only magazine for the new Linux user.
- Hackszine
- Hacker Bits Hacker Bits is the monthly magazine that gives you the hottest technology stories straight from Hacker News. We select from the top voted stories for you and email them to you in an easy-to-read email magazine format.
- Hack In The Box Featuring white papers from Hack In The Box events and articles by industry experts, keeping you in the know with the latest hacks, exploits, and innovative ideas in the industry.
- NODE Zine New, independently created 'zine for the NODE community. It contains many of the subjects we talk about here; decentralization and P2P technologies, open-source, do-it-yourself tutorials and hardware design, cutting edge technology and more.
- The Discordant Opposition Journal Technical writings and musing from the editor Rue-the-Day and Cronus.
- Secret Club Secret Club was created originally as a gag between friends who are passionate about technical subjects, later evolving into a group of like-minded people.
- tmp.out New magazine for ELF-lovers.
- Paged Out! Free experimental (one article == one page) technical magazine about programming (especially programming tricks!), hacking, security hacking, retro computers, modern computers, electronics, demoscene, and other similar topics.
- Anarchivism - Printed Zine Archive Huge archive of properly scanned (or digitally released) version of printed hacker magazines from the years past, by Mike Dank
- Demodulate Not a 'zine, but a really cool technical show exploring hacking & phreaking in the 1980s-1990s with interviews of people involved in those scenes during that period.
- Hacker History Podcast Not a 'zine, but another really cool podcast with interviews of past and current hackers, by Josh Bressers
- Hacker Public Radio The technology community podcast.
- Low-Tech Magazine Low-tech Magazine underscores the potential of past and often forgotten technologies and how they can inform sustainable energy practices. Technology has become the idol of our society, but technological progress is - more often than not - aimed at solving problems caused by earlier technical inventions.
- DIYODE Magazine A new Australian magazine for supporting electronics enthusiasts and makers.
- Hot Iron The Hot Iron newsletters were begun by Tim Walford, G3PCJ and are currently produced by Peter Thornton, G6NGR and Frank Barnes, W4NPN. Issues cover a wide range of topics of interest to the amateur radio community.
- TELECOM Digest The oldest mailing list on the Internet!
- Ultimate Hardware Hacking Gear Guide Discover the best tools, detailed tutorials, and the latest updates on hardware hacking. Whether you're a seasoned pro or a beginner, our e-zine has something for everyone.
- VLAD Virus Laboratories & Distribution Magazine. Australia's number one export :).
- Spread Spectrum Scene The wireless, PCS, and advanced digital communications Internet magazine.
- Source of Kaos A 1990s ezine about computer viruses.
- Computer Underground Digest The Cu Digest was a more-or-less weekly digest/newsletter/journal of debates, news, research, and discussion of legal, social, and other issues related to computer culture. Because of editors' time constraints and changes in computer culture, CuD has likely published it's last issue in March, 2025.
- The MagPi Magazine The official magazine of the Raspberry Pi. Very well written and many good technical articles.
- HackSpace Magazine A very high-quality magazine devoted to exploring the works and people of hackerspaces worldwide. Is now part of the Raspberry Pi official magazine.
- Monitoring Times Monitoring Times was a monthly printed magazine based in the United States covering shortwave listening and DXing, scanners, medium wave broadcasting as well as utility stations, pirates and clandestine stations. Publication began in 1982 and, after 31 years, it closed in 2013.
- Radio-Electronics Radio-Electronics was the "new" name for Radio-Craft magazine. Hugo Gernsback, sometimes called The Father of Science Fiction, started it as Radio-Craft in July 1929. The title was changed to Radio-Electronics in October 1948. In July of 1992 transitioned to Electronics Now
- Popular Electronics Popular Electronics was created in 1954 by Ziff-Davis for an audience of electronics hobbyists and experimenters. It soon became the "World's Largest-Selling Electronics Magazine."
- QSO'er Newsletters Newsletter of the Fox Cities Amateur Radio Club (Wisconsin).
- CovertAction Quarterly Exposing covert action since 1978. Co-founded by former CIA officer Philip Agee.
- Circuit Punk A new magazine that embraces the vast world of music technology. It's a home for original schematics and code, DIY guitar pedals/synthesizers, modified and circuit bent instruments, plugins, and much more educational content from readers and industry experts alike.
- The Next Wave The Next Wave is a journal discussing the research and technological innovation taking place at the NSA. TNW began in 1992 as an internal employee newsletter known as Tech Trend Notes, but as a result of an increase in readership and external requests for the publication, it was released to the public in 2004 with a new name: The Next Wave.
- Linux Journal A complete collection of Linux Journal issues from 2005-2019.
- Hewlett-Packard Journal The Hewlett-Packard Journal has been documenting HP's technologies and achievements since 1949. The HP Journal has been available online since early 1994.
Archived Locally
- X.25 Magazine Russian hacking 'zine.
- Da HaX0r BrUtHeRz NeWZlEtTeR
- ~el8 Magazine Support pr0j3kt m4yh3m!
- B4B0 Magazine The B4B0 Party Programme
- The Brotherhood of Warez Phear BoW!@#$%!
- 40Hex 40Hex was once the the most popular DOS virus magazine in the underground.
- Virus Report Virus Report, by the late-great Argentine hacker Fernando Bonsembiante, ran for 22 issues from 1993 to 1995. It mixed cyberpunk literature with information about the computer underground. In Spanish.
- PHANTASY Newsletter of the International Information Retrieval Guild (IIRG)
- Informatik Journal Hacker 'zine published by a couple of young punks from Texas.
- Frequency Inside the hacker mind. Editor-in-Chief: Screamer Chaotix
- Napalm E-Zine Napalm is an e-zine devoted to computer security, with a healthy dose of music, news, and ethics.
- Cybertek Back Issues The Cyberpunk Technical Journal. Also includes TICOM 'Zine, Dystonaut, Basment Techie, and The Pine Tree Journal covering a huge range of related topics.
- YIPL / TAP Magazine Back Issues Both "old" and "new" versions. Considered the first "hacker" newsletter.
- TEL Magazine Back Issues Telephone Electronics Line. 1970s printed phreaking newsletter, by Teletronics.
- PHC's Phrack Magazine Version of Phrack put out by the Phrack High Council.
- International Journal of Proof-of-Concept or Get The F*ck Out Ridiculously awesome hacker 'zine by Manul Laphroaig
- Binary Revolution Magazine Printed alternative to $2600.
- Blacklisted! 411 Both print and online magazine from the 1980s/1990s which
iswas back again.- Hack-Tic Magazine Archive Legendary printed Dutch hacker magazine from the 1990s.
- 't Klaphek Magazine Another magazine for Dutch speaking hackers and phreakers.
- The Collusion Webzine The Collusion Group is a computer/networking/gaming SIG with its HQ in Austin, Texas. Collusion is a group of computer zealots with various interests and areas of expertise. Some of us are computer professionals, while others are CS students at Universities or even in high school. However, what we all have in common is a fascination with computers. You know that kid on the block that everyone comes to for advice about their computers? We're those kids.
- K-1ine A 'zine for the Canadian underground hacking/phreaking scene.
- Information eXchange for Helter Skelter Well...out of the 613 NPA comes a group of kids who think that their opinions are important enough for EVERYONE on this world to know what they are.
- Sykotic Times We put the FU back in fun
- Patterns of Recognition New hack/phreak 'zine with funny stories by I-baLL, Judas Iscariot, Gonzo, Murd0c, Enamon, MikeTV, Scientist, Venadium, Rob T. Firefly, and Sephail. (Website)
- Reprimand The poison air bubble in the bloodstream of the American Collective, by Gonzo. Missing many files and images.
- Ethertech Global Industries Awesome new hack/phreak e-zine. From Wisconsin?!
- Telecom-munists Monthly Funny phreak magazine by Dimebag Kyle & IDontLikeRabbits: "We want stupid shit and stupid shit only".
- Phreakers Hackers Underground Network (P/HUN) Newsletter By Red Knight of the 'Hackers Den' BBS.
- DIG Magazine Online and printed magazine from the Digital Information Group (DIG).
- Syndicate Power Action Syndicate Power Action is a small newsletter which pays tribute to the roots of the Soljo - frequently released with the ultimate goals of being totally insane, badly written but slightly amusing. SPACT is SOL's contribution to the glorious 'Rag's Division' of the textscene - and perhaps the first "Fire and Forget ezine.
- Vicious Propaganda A step backwards in digital communications...
- Outbreak Magazine Nice little hack/phreak e-zine from around 2002/2003 by kleptic
- Radical Future This magazine focuses on computer hacking, as well as the freedom of speech, expression, and press when it comes to political beliefs and events. By Port7Alliance.
- System Failure System Failure is a publication geared towards the underground computer culture; mainly dealing with h/p issues. Each issue is designed to have both beginning and advanced material. Methods change all the time, and it's a race between them and us to find the holes in the system, to openly show the System Failure.
- Phr33k4z0iD'z & 13370 phr34k0 h34d5 Newer, detailed phreaking 'zine, plus a lot of cool and original phreaking/hacking text files.
- ODDREE: The Slacker Journal ODDREE is a free technical journal for hackers, slackers, and nerds. From Ray Dios Haque of United Phreaks Syndicate.
- Analog.5 Analog.5 is a hacking e-zine designed by the Hak5 community, for the Hak5 community. A total of five issues were published until the zine died from a lack of submissions.
- root zine Small printed hacker magazine by Mutter from the 1990s. (Still looking for issues...)
- Blackzine Canadian hack/phreak zine by lord narayana of Phones of Zen, who ran the official 2600 meeting in Calgary. Unfortunately missing all the ZIP files....
- Phone Punx Magazine Cool little phreaking 'zine by Mohawk of the Ocean County Phone Punx, only three issues though?
- Digital Phreak P1mps The DPP is a loose association of hackers, phreaks, coders, and some other friends from IRC (#p1mp on EFnet). DPP originally started out in 1996 as a pseudo-hacking magazine that ended up being a skript-kiddy forum. Although there was some good material published, the 'zine never gained too much respect. From Wisconsin?!
- The HAVOC Technical Journal Scud-O presenting the best info the underground hacking scene has to offer, a HAVOC Bell Systems' Publication.
- Go Null Yourself New hacker 'zine by sToRm and m0nkee. Lots of good original content and old-school hacking vibe.
- Codebreakers The free online magazine for reverse-engineers, only two issues? (German version, not the virus one.)
- Confidence Remains High Very high quality hacking 'zine from the late-1990s which was known for the original work of "so1o." Includes the missing files.
- 29A Labs Quality 'zine from a highly-respected Spanish virus writing group which was active on the old VX Heavens forums.
- HWA.hax0r.news Cruciphux of Hackers Without Attitudes (HWA/DoK) chronicle the events of the computer underground in this excellent text 'zine. (Issues)
- Keen Veracity Hacker 'zine put by Legions of the Underground which is released every so often.
- Mentes Inquietas The !Hispahack WebZine. Nice little hacking zine out of Spain which translates to "Restless Minds." Most articles are in Spanish, but there are a few in English.
- InET Magazine InET - Intrusos Exploracion Tecnologica - an underground research group out of Columbia. In Spanish.
- DataZine DataZine is the official e-zine of The Datacore.
- Hacker Monthly Hacker Monthly was the print magazine version of Hacker News.
- The Hacker News The Hacker News monthly magazine is the most comprehensive and informative collection of security, hacking, and innovative technological notions on the market today.
- Hacking Etc. New 'zine in PDF format.
- DO NOT F*CK WITH A HACKER Chinese/English language hacker magazine with perhaps the greatest name ever...
- Anti-Social Magazine The only magazine to support all underground scenes. The magazine is in a DOS/Windows executable format. Many issues are missing.
- U H C A's Technical Journal Short-lived technical journal by Digital Phreak, the named changed to Infosanity in later issues.
- Hackers Information Report HiR is an electronic publication by Axon that is written by real hackers and phone phreaks that have the desire to share information. Missing all the images.
- Damage, INC Short-lived Canadian 'zine. We want to use this medium as a weapon to fight the corruption that exists, reveal conspiracies and coverups, give useful information to those in the h/p scene.
- Vaginal and Anal Secretions Newsletter From 1992 to 1999, Crygenic Piss and friends created a series of extremely original textfiles on anything they could come up with, the more disgusting the better, and called it "The Vaginal and Anal Secretions Newsletter," or, simply, VAS. Why? Well, as they say "We couldn't come up with a better name. F*ck off." Missing all the images and issue #130.
- Assembly Programming Journal Assembly Programming Journal is an online magazine covering assembly language programming techniques. The magazine will come out in ASCII format (natch) every three months, and will contain code and articles for beginner, intermediate, and advanced asm progammers.
- ARTeam eZine An excellent, but short-lived, 'zine for the dedicated software reverse engineer by ARTeam.
- vACZiNe Danish "ultra hardcore tutorial mag" dedicated to cracking, coding, cryptography, crackmes, art, and more!
- Barata Elétrica ("Electric Cockroach") Brazil's first hacking 'zine started by Derneval in 1994. In Portuguese.
- F41th Magazine The U.K.'s only dedicated H/P zine, run by D4RKCYDE, the U.K.'s only H/P group.
- Party Line Nice little 'zine covering the operating of the Futel public payphone operating.
- Kräcker mAG German software reverse engineering text magazine covering the German cracking scene. Started by Prof.X in 1999.
- REVERSERS E-ZiNE This e-zine is a try of making some good infos, links, ... about the current software reverse engineering scene. By TORN@DO of The Immortal Descendants, who also had their own 'zine titled Reverse EngineerZINE.
- Hakin9 Hakin9 is an infamous monthly magazine and online training provider dedicated to hacking and cybersecurity.
- Hogs of Entropy E-Zine Stupid shit that nobody cares about except you, because you're an idiot. (OFFSITE)
- Cult of the Dead Cow cDc: We're just into T-files for the Girlies and the Money.
- Private Line A journal of inquiry into the telephone system. A short-lived, but very well done printed magazine by Tom Farley and Damien Thorn.
- TAPR Packet Status Register Archives TAPR membership journal which features both technical and non-technical articles.
- Scatterpoint Archives Scatterpoint is published by the U.K. Microwave Group, succeeding the former RSGB Microwave Newsletter.
- The Groom Lake Desert Rat An online newsletter covering Area 51 and related UFO lore by Glenn Campbell.
- Eye Spy Magazine World's only newsstand publication dedicated to espionage and intelligence.
- Nuts & Volts Magazine Nuts & Volts Magazine is written for the hands-on electronics hobbyist, design engineer, technician, and experimenter.
- 73 Magazine 73 was an amazing technical magazine dedicated to amateur radio, homebrew electronics, homebrew computing, and other "off the wall" subjects. Yes, we really did get Wayne's blessing to scan and release these!
- Applied Microwave & Wireless The fastest-grown technical magaine for microwave, RF, and wireless engineerin. Ran from 1989 to 2002. (OFFSITE)
- Satellite Watch News Your source for the latest news from the satellite underground. Dan Morgan's infamous satellite technolgy newsletter which DirecTV shut down. Missing a few issues and all the images.
- FREN-Z Magazine FREN-Z, is a true alternative culture magazine. Each issue features a variety of articles, including those on self-improvement, activism, cyberpunk, art, paranormal subcultures, and other things of interest to our frens and family.
- Hacker News Network Working mirror of Space Rogue's infamous Hacker News Network from 1998-2000.
$2600 Magazine
Download Back Issues
"You can't stop P2P technology nor prevent the spread of alternative media - unless people allow it to happen."
--- Reply to a letter in $2600 Magazine Vol. 21, No. 4.
"We continue to maintain that there is nothing at all illegal about making your own copy of something you own."
--- Reply to a letter in $2600 Magazine Vol. 19, No. 3.
"For the record, and for the benefit of some people (like certain corporations and judges) who can't understand why a hacker magazine has a copyright, we encourage people to send our articles to other people."
--- Reply to a letter in $2600 Magazine Vol. 17, No. 3.
"It's amazing to us that people actually think they have to do this. This constitutes personal use - you have every right to use excerpts of a publication in such a manner without asking permission."
--- Reply to a letter in $2600 Magazine Vol. 19, No. 1 asking about copying articles.
"Several years ago it would have been almost unheard of for a corporation to bully someone into submission on the Net using nothing but its might. Today we seem to hear of a new case every day."
--- Editorial in $2600 Magazine Vol. 17, No. 2.
"Hmm... I think I'll start a 'hacker' magazine with articles written by other people but I'll keep the profits to myself. I'll refuse to take any personal responsibility and blame all my problems on someone else! When sales are sagging, I'll ask Hollywood to make a movie about me and my teenage boy posse, then claim I'm being 'suppressed,' while actively supporting truly corrupt politicians and the One Percent. LOL! While bitching about the telephone company selling long distance service, I'll sell T-shirts, hats, DVDs, and stickers! I'll spend 25% of each issue complaining about how dumb everyone else is, but I won't ever mention the word 'thanks' to those people who helped me to get where I am today! Slap a
sixseveneightnine dollar price tag on it and sue anyone giving it away for free! I'll never have to get a real job!"
$2600 Magazine Volume 1, Number 1 (January 1984)
- AHOY! - Introduction to $2600 and editorial
- FBI Goes After ADS Hackers - Tactics and sources of a FBI raid involving IBM's Audio Distribution System (ADS)
- 2600 Flash
- GTE Raids Still Have Many Unanswered Questions - Computer Owners Concerned
- AT&T Credit Cards Make Debut
- Wireless Phones Spell Trouble
- 1984 Arrives in Hong Kong
- The Truth Behind Those 9999 Numbers - Info on the services provided by the 800-9XX-9999 numbers, by Mark Bluebox
- White House Phone List - Phone numbers to various White House offices
- FBI Goes After ADS Hackers (cont.) - Tactics and sources of a FBI raid, continued
$2600 Magazine Volume 1, Number 2 (February 1984)
- Hacking on Telenet - Beginner's guide to GTE's Telenet system and a command overview, by Evil Corley
- ESS: Orwell's Prophecy - Info on the new ESS offices and how they operate, by BIOC Agent 003 (Donald Burgio)
- 2600 Flash
- Times Changing for Directory Assistance
- No Hacking While Flying, Please
- Trick of the Month
- Death Star Cards Spell Woe
- ADS Investigation Moved?
- Some Thoughts on "Garbage Picking" - How to dig through garbage for information and some notes on cross-talk
- Letters - (none given) (California)
- Country Codes & City Code Formats - Long-distance country and routing codes
$2600 Magazine Volume 1, Number 3 (March 1984)
- The Constitution of a Hacker - A look into the hacker's mind, by Evil Corley
- Alternate Long-Distance - A Guide to MCI - An overview of MCI long-distance operations, by Evil Corley
- 2600 Flash
- 718 is Coming!
- Supercomputer Dial-Ups
- Wiretap City
- Students Cause Havoc in Computer
- The Person Numbers
- Furthermore...
- The First Atomic Bomb: A True Tale - Story of Enrico Fermi and an asleep operator
- MILNET Hosts - Military host addresses available on the ARPANET
$2600 Magazine Volume 1, Number 4 (April 1984)
- Whose Strike Was That Anyway? - Info and analysis the 1983 AT&T strike
- The Trouble With Telemail - Security holes in GTE Telemail, by Evil Corley
- 2600 Flash
- Bell Credit Card Abuse Soars
- Electronics Create Portable Prisons
- 414's Plead Guilty
- Teller Machine Crime Coming
- Free Information in Trouble
- A Word on Wiretapping
- A True Saga of Teleconferencing - Story on telephone conferences and a bust, by Electric Moon
- MCI Access Numbers - List of numbers to access MCI mail
- Old Phone Book Ads - Collage of old telephone company cartoons on how to use the phone
$2600 Magazine Volume 1, Number 5 (May 1984)
- The Simple Pleasures of a Step Office - Story of dialing (and sounds) on/to a step-by-step office, by Mr. French
- IBM's Audio Distribution System Sure Can Be Fun! - Info on the IBM ADS voice message system, by Evil Corley
- 2600 Flash
- A 414 is Silenced - Others Indicted
- Long-Distance Option Timetable
- Intelpost an Astronomical Failure
- Victory for Wiretap Victims
- Bank Records Aren't So Private
- The Woes of Having a Small-Time Rural Phone Company - Problems with independent phone companies, by Mr. French
- Defense Data Network - DDN addresses
- Easylink Numbers - DDN addresses, continued / Easylink dial-ups
$2600 Magazine Volume 1, Number 6 (June 1984)
- ARPANET Hopping: America's Newest Pastime - Overview of ARPANET and related commands, by Evil Corley
- Electronic Switching Advances - ESS calling features and some potential drawbacks
- 2600 Flash
- No More Free Info
- 2600 Writer Indicted
- Computer Threat Causes Chaos in Albany
- E-COM is Going Away
- AT&T Limits Use of Their Credit Card
- FCC Actions
- The Dark and Tragic Side of the Great Break-Up - Smaller companies may give poorer service, by Mr. French
- Letters - Quasi Moto (Michael Danseglio, Orlando, FL), Awfully Curious
- E-COM Dial-Ups - E-COM dial-up numbers
- New York Telephone "Letter of Doom" - Letter which says your lines are under surveillance by law enforcement
$2600 Magazine Volume 1, Number 7 (July 1984)
- "Look Out, He's Got a Computer!" - Newspaper stories and a defense of computer hackers, by Evil Corley
- MCI Mail: The Adventure Continues - Overview of the faulty MCI Mail computer network, by Evil Corley
- 2600 Flash
- Look Out For Sidney!
- Bell to AT&T: Get Lost!
- Five Arrested in Phone Fraud
- An Official Crackdown on Hackers
- Pay Telephones Deregulated
- "You Must First Dial a One..."
- Information News
- Introducing the Clear Box! - The "clear box"for post-payphones, by Mr. French
- Letters - Curious, RC
- TRW: Big Business is Watching You - Overview of the TRW Information Services and how to run your own TRW credit reports
$2600 Magazine Volume 1, Number 8 (August 1984)
- But How Does It Work? - A simple, but detailed, explanation of how the phone system works, by BIOC Agent 003
- Privacy Lost - Book review of David Burnham's Rise of the Computer State: The Threat to Our Freedoms, Our Ethics and Our Democratic Process
- 2600 Flash
- Big Brother No Longer Watching Miami
- Computers Seized as Summer Games Begin
- House: Hacking is Bad
- More PC Jr's, Less Z-100's for Soviets
- Federal Express Offers "E-Mail"
- ITT Wiping Out Fee
- 800 Directories Now Available
- Ice Cream Chain Aides Selective Service
- Be Nice to Your Telco - Tricks to play on your local phone company
- Letters - Agent Orange, Miserable in Philadelphia, John Gregg
- CN/A List - List of Customer Name/Address contact numbers
- The Hacker's Guide to Area Code - A simple scheme to help "map out" exchanges in your area
$2600 Magazine Volume 1, Number 9 (September 1984)
- History of British Phreaking - Guide to U.K. phone systems, by Lex Luthor (Vincent Louis Gelormine [TKOS][LOD/H], Rogue Fed, Tamarac, Florida, LinkedIn)
- More on Trashing - Proper techniques on digging through garbage, The Kid & Co. and The Shadow (David Flory, Dan Foley, The Shadow, Shadow 2600, died in 1989)
- 2600 Flash
- NSA Doesn't Feel Secure
- Another Hacker Story
- AT&T Faces Serious Money Problem
- Private Directories Soon to be Available
- A Friend in High Places - Story of telecommunication fun and a friendly operator, by Mr. French
- Letters - AZ
- IBM ADS Directory - List of IBM's Audio Distribution System access numbers
- Telephone Company Letter - Need to subscribe to Touch-Tone service
$2600 Magazine Volume 1, Number 10 (October 1984)
- Getting Caught: Hacker's View - Story of a raided hacker and the effects on his life
- Vital Ingredients: Switching Centers and Operations - Description of the different central office operations and classifications, by BIOC Agent 003
- 2600 Flash
- NSA Wants Better Phones
- Oh No, Not Again!
- Victimized by Crime Computers
- Sears Satellite Network
- Loopholes Around Wiretap Laws
- IBM is Buying ROLM!
- 911 Suspect Hung Up
- Letters - Crystal Palace, The Animal, kd, The National Center for Computer Crime Data
- Contacting the Gestapo - New York Telephone security numbers
- Old Phone Book Ads - Some telephone company cartoons on how to use the phone
$2600 Magazine Volume 1, Number 11 (November 1984)
- Exploring Caves in TRAVELNET - Exploring the General Motor's TRAVELNET computer network / phone extender
- Fun With Fortress Fones - Technical info on Western Electric single-slot coin telephones (Coin Crafts' Manual)
- 2600 Flash
- Computer Foul-ups Hurt Social Security
- Phones in the Sky
- Another FBI Computer File
- Use of Wiretaps at Record Pace
- 818 Here to Stay
- One We Somehow Missed
- In Addition...
- Letters - Howard A. Karten (Randolph, MA), Fire Monger, The Trojan Horse
- Carrier Identification Codes - Alphabetical listing of Independent Carrier (IC) and Carrier Identification Codes (CIC) / Feature Group D 3-digit PIC codes
- MCI Mail Targets 2600 - Letter from MCI
$2600 Magazine Volume 1, Number 12 (December 1984)
- A Time for Reflection - A look back over the year, by Paul G. Estev
- MCI Mail and Easylink Updates - Electronic mail horror stories and billing problems
- The Scariest Number in the World - Story (fake?) about calling the president's bomb shelter, by Mr. French
- 2600 Flash
- Computer Makes it Easy for Reagan
- Penetrating the Pentagon by Phone
- First of the "Superminis"
- Students Bog Down Computer
- SBS Offers Toll-Free Service
- Electronic Jail All Screwed Up
- Video Telephone Invention
- Federal Telephone System Update
- Subscriber Comments - Reader survey responses
- Electronic Mail Systems - List and price comparisons of some electronic mail and voice mail services
- Dial-It Numbers - Funny phone numbers, by Paul D. Lehrman
$2600 Magazine Volume 2, Number 1 (January 1985)
- Those Horrible Hackers Strike Again - Newsweak media report of hackers
- Wiretapping and Divestiture: A Lineman Speaks Out - Phreaking story from a telco lineman, by The Shadow
- Getting in the Backdoor - Backdoor access to various DEC operating systems (TOPS/VMX), by Mike Salerno
- Information Bureau - $2600 phone bill, our thanks, and other notices.
- 2600 Flash
- IRS Wants Access to Telco Data
- GEISCO's New Toys
- GTE Hit By Divestiture
- Fascist Computer Network
- A Challenge to Hackers
- In Addition...
- Letters - Jay Bloombecker (Los Angeles, CA), The GCI Guy (Alaska), John Sengelaub (Wantagh, New York), Sector 17, Bob Gamma, Father, Insomniac
- BITnet Topology - Graphic of the BITnet network layout.
$2600 Magazine Volume 2, Number 2 (February 1985)
- The Theory of Blue Boxing - How Blue Boxing works and a bit about their history, by BIOC Agent 003
- Trashing Alaska Style - Central office Dumpster diving story in Alaska, by The GCI Guy
- Surveying the COSMOS - Beginner's guide to Bellcore's Computer System for Main Frame Operations (COSMOS), by The Fire Monger
- 2600 Flash
- Phreak Roundups
- TRW Breached By Non-Hackers
- This Month's Mischief and Mayhem
- AT&T Keeps "800" Data to Self
- Letters - Mad as Hell, The Crazy Man, SJ, Another Hacker (Binghamton, New York), KC, DB (San Jose, CA), James (Scottsdale, AZ)
- 2600 Bulletin Board Online - Info on the Private Sector BBS
- Acronym List - List of common telco acronyms, by The Shadow
$2600 Magazine Volume 2, Number 3 (March 1985)
- Nazi BBS a Challenge to Hackers - "Hackers" who want to restrict freedom of speech
- Are You a Phreak??? - Humorous review of phreaking, by Bob Gamma
- How to Get Into a C.O. - Getting a tour of a telco central office, by The Kid & Co.
- 2600 Flash
- The Next Step in Custom Calling
- Industrial Espionage Seminar
- Kenyan Payphones Prove Popular
- This Month's Troublemakers
- A Mechanical Hacker
- Redemption for a Hacker
- I.R.S. Computers Screw Up
- Computel Does Exist
- Letters - Animal, The Shadow, Kazematic, GR, BIOC Agent 003, Mikhail Gorbachev, HK, Hunter Alexander
- Interesting Phone Numbers - Fun phone numbers
- How to Use the Dial Telephone - 'burr-burr-burr' and 'buzz-buzz-buzz'
- CN/A Numbers - Customer Name & Address phone number list
- The Cipher Disk - Cipher wheel from the NSA
$2600 Magazine Volume 2, Number 4 (April 1985)
- What a White Box Can Do - How to build and use a portable DTMF tone generator
- A Phone Phreak Scores - Social engineering and phreaking story
- Hacking Packard - Hacking HP-2000s, by BIOC Agent 003
- 2600 Flash
- At the Last Stroke...
- Good Apples for the Soviets
- Hackers Go Free
- Robot Kills Man
- 'Santa Fraud'
- Overseas Pirates
- Real Life WarGames?
- Silver Pages
- Other News
- Letters - Puzzled, Chuck Linder, Informed as Hell, (none given), (none given)
- Hosts by Location - ARPANET MILNET host locations
$2600 Magazine Volume 2, Number 5 (May 1985)
- People Express to be Hacked to Pieces - Hacking the People Express Touch-Tone reservation system, by Paul G. Estev
- How to Run a Successful Teleconference - Complete guide to ALLIANCE teleconferencing, by The Shadow
- 2600 Flash
- 414 Bust
- Police Hacker Cleared
- Dial-a-Directory
- Reagan Hangs Upon Kids
- MCI Goes to U.K.
- Yellow Scam
- "Crackers" Cracked
- Carrier Choosing Time
- Mystery Transistor
- ALLIANCE Teleconferencing - Diagram of the steps needed to setup an ALLIANCE teleconference
- Letters - (none given), The Crazy Man
- Inmate Payphone Ad
$2600 Magazine Volume 2, Number 6 (June 1985)
- A Guide to the Israeli Phone System - The phone system in Israel
- Sherwood Forest Shut Down by Secret Service - Sherwood Forest II & III BBSes raided for posting credit card numbers
- Some Words on Hacker Morality - Don't sell other people's BBS files
- Review: Out of the Inner Circle: A Hacker's Guide to Computer Security - Book review of Bill Landreth's Out of the Inner Circle: A Hacker's Guide to Computer Security
- 2600 Flash
- Bell Didn't Invent Phone?
- Porno Phone Service Busted
- IRS Drives Telcos to Drink
- Jersey Wins Wiretap Race Again
- AT&T Computer Caught Stealing
- Say Goodbye to Meter Readers
- Thai Phone Books a Hot Issue
- New Tracking Device for Cars
- Problems for New Payphones
- TINA Message Service
- AT&T Contractual Obligations
- "Call Me" Card
- Letters - (none given), Rusty Diode, (none given), The Silver Sabre
- 800 Prefix List - List of 800-NXXs by state, by Ax Murderer
- Systematically Speaking - Goodbye to meter readers, Thai phone book, tracking devices, TINA "Call Me" card.
- Sherwood Forest: Intro to Hacking - Beginner guide to computer hacking, by The Knights of Shadow
$2600 Magazine Volume 2, Number 7 (July 1985)
- Interesting Things to Do on a DEC-20 - Commands and hacking info for a DEC-20, by The Knights of Shadow
- The Basics of Hacking: Intro The Knights of Shadow Hacking Series, Re-edited and Messed by Elric of Imrryr
- Banking From Your Terminal - A Look at PRONTO - A look at electronic banking and Chemical Bank's PRONTO banking system, by Orson Buggy
- 2600 Flash
- $2 Billion Error
- ITT Crackdown
- GTE Sprint Cheats Customer
- Listening In on Cellular Phones
- More Phone Fraud
- Computers Monitor Truckers
- Missing Children's Faces Displayed
- Letters - (none given), (none given) (Birmingham, Alabama), (none given) (Gulfport, MO), (none given)
- MILNET TAC Dial-Ups - MILNET dial-ups
- Systematically Speaking - MCI goes optical, 100% ESS, GTE bigger than AT&T
$2600 Magazine Volume 2, Number 8 (August 1985)
- Seized! $2600's computer bulletin board Private Sector is implicated in raid on Jersey hackers, by Paul G. Estev
- Youth's Computer Seized in Jersey was used for Magazine 'Bulletin Board' by Joseph F. Sullivan, The New York Times, July 18, 1985
- The Threat to Us All - Editorial on BBS raids and seizures, by Evil Corley
- 2600 Flash
- $2600 a Hacking Victim
- New Phone System for Courthouse
- Moving Satellites... What Was Really Going On? - Point-by-point correction of the New Jersey prosecutors fallacious charges and debunking the "hackers moving satellites" myths, by Paul G. Estev
- Why Computers Get Snatched - Why BBSes get raided
- Some Important Questions to Ask - Who is responsible for BBSes and provocative questions about these events
- How Can Sysops Protect Themselves? - How to protect your BBS from raids, by Evil Corley
$2600 Magazine Volume 2, Number 9 (September 1985)
- A Guide to VMS - Beginner's guide to DEC's VAX/VMS systems, by Lex Luthor
- Advanced Hacking VAX'S VMS Lex Luthor and LOD/H
- The Infinity Transmitter - An Old Bug That Had Its Time - How the infinity transmitter phone tap works, by Howard
- Reaching Out on Your Own - Using a Blue Box to simulate Busy Line Verification (BLV) conditions, by Forest Ranger (John Thomas)
- Pursuit for People - Info on Telenet's PC Pursuit computer-to-computer link-up service, by Paul G. Estev
- 2600 Flash
- Phone-in Registration for College
- Trouble With 800 "Word Numbers"
- War Game Addict
- Hacker Extortionist Caught
- Pitcairn Island Now On AT&T Net
- Private Sector Update
- Dick Tracy Toys Are Closing In
- Directory Assistance By Computer
- Pest Control
- Bell Propaganda Films
- Europe Standardizing Telecoms
- Letters - D.J., SEVOX, Talbot, (none given), W.U. Friend
- Telenet Directory - Telenet address scan and banners, by Lex Luthor
- LOH Telenet Directory: Update #4 LOD/H Technical Journal
- Systematically Speaking - Dick Tracy toys, computer directory assistance, Bell propaganda films, Europe standardizing telcoms.
$2600 Magazine Volume 2, Number 10 (October 1985)
- And They Call US Crooks? - Getting ripped off consulting telcos and why he can't sell his expertise, by Silent Switchman
- An Interesting Diversion - How call diverters work and are abused, by Lord Phreaker
- More Info on VMS - Second part to the beginner's guide to DEC's VAX/VMS systems, by Lex Luthor
- Advanced Hacking VAX'S VMS Lex Luthor and LOD/H
- 2600 Flash
- Computer Elections Examined
- Two Inch Thick Bill
- Navy Calls Dial-a-Porn
- Navy Phone Phreaks Nabbed
- Phone Booth Captures Man
- Telco Rats On Government
- Hackers Have Big Business Scared
- Fiber-Optic Network For Du Pont
- Campaign Contributions On-Line
- AT&T Info Charges Upheld
- More Use of Phone Computers
- More Divestiture Woes
- Letters - L.L., The Long Distance Voyager and The Knight in White Satin, Person, Lord Phreaker
- Blue Box Plans - Schematic for a Blue Box, by Ford Prefect (Steve Richardson)
- The New AT&T Hostagephone System - Ad for a hostage negotiation phone
- Systematically Speaking - Hackers scare business, DuPont bypasses telco, computer campaign info, phone computer's divestiture woes
$2600 Magazine Volume 2, Number 11 (November 1985)
- RSTS: A Trick or Two - Hacking info for the DEC's RSTS operating system, by The Marauder (Todd Lawrence, Email #2)
- Here's the Secret! - Non-supervised (no billing) loop-around test lines on a GTE GTD-5, by Silent Switchman
- The History of ESS - The history of the Western Electric ESS, by Lex Luthor
- 2600 Flash
- Columnist Attacks AT&T
- No Dial-it Calls for Feds
- Dial-it Sex Numbers Argued
- Big Deal for Little Town
- Springsteen Mania
- Avoid Phones in Storms!
- Rural Customers Denied Access
- Police Dept. Wants Cellular Phones
- Toll-free From Where?
- Pacific Cable Planned
- Free Kiddie Dial-It Calls
- AT&T to Read E-Mail
- Equal Access May Not Be "Equal" to Modems - Billing problems with autodialers, by The Shadow
- Letters - HAL-9000/Beast 666, Lord Phreaker, a.e., Worried Phreak
- Test Numbers - List of telco plant test numbers, by The Shadow (David Flory)
- The Early Phreak Days - Story of phreaking in the 1960s, by Jim Wood
- Systematically Speaking - Avoid phones in storms, rural unequal access, police cellular phones, toll-free from where?, AT&T to read email
$2600 Magazine Volume 2, Number 12 (December 1985)
- Our Wishes For '86 And Beyond - Editorial on telco improvements, by Evil Corley
- Fun With COSMOS - Additional info on Bellcore's COSMOS, by Lex Luthor
- Hacking COSMOS: Part 1 - Basics by Lex Luthor
- Hacking COSMOS: Part 2 - Intermediate Course by Lex Luthor
- 2600 Flash
- Telco Service Spawns Racist Banter
- French Phones Renumbered
- BB Watching Without Regulation
- Fawcett Phone Bill Too Big
- Inmates Handle Information Calls
- No More Redialing?
- Cityphone Has The Answer
- Super Crisis Alert System
- Super Payphone
- Phones at High and Low Speeds
- AT&T Offers E-Mail
- Dreams of GEnie
- German Phone System Stagnant
- Survey Results - Results from the $2600 reader survey
- More Than 1500 BBS Numbers - Big list of BBS numbers
- Systematically Speaking - AT&T email, German phones, super payphone
$2600 Magazine - Volume 3, Number 1 (January 1986)
- Private Sector Returning - Return of the Private Sector BBS. Back online soon, but many questions on seizure remain, by Evil Corley
- Divestiture: What Happened? - An explanation of that which is confusing the populace on the aspects of the AT&T breakup, by Evil Corley
- 2600 Flash
- AT&T Does It Again
- Five Aliens Hung Up
- Technology Nabs Hooky Players
- Home Computer Attacks Falwell
- Another Astronomical Phone Bill
- Dial-A-Porn Update
- Phone Booth Wins Again
- New Payphones Confuse Callers
- Security Software
- Your Own Private Centrex
- New VAX Announced
- Cray Maneuvers
- Overcharge Hunters Needed
- Phone Service via RadioShack
- Letters - Ford Prefect, Arab149, The Creature, The Grub (Canada)
- Blue Box Programs - TI-99, Commie 64, Atari code for generating MF tones, by Ford Prefect (Steve Richardson)
- Systematically Speaking - Confusing payphones, code abuse software, Centrex features in your house, VAX8650, overcharge hunters
$2600 Magazine - Volume 3, Number 2 (February 1986)
- VMS - The Series Continues - Additional info on hacking DEC's VAX/VMS systems, by Lex Luthor
- Advanced Hacking VAX'S VMS Lex Luthor and LOD/H
- It Could Happen To You! - Story of phone phreaks harassing other phreaks
- Dial Back Security - Info on how "dial back" security works and some ways to defeat it
- 2600 Flash
- Teenagers "Abuse" Party Line
- A Unique Obscene Caller
- The Scoop on Pen Registers
- Reporters Steal Swiss Phones
- Payphone Causes Panic
- Sprint Unites with US Telecom
- Write Protect Tabs Wrong
- Bell Atlantic & MCI Collaborate
- Cellular Phones in England
- Infrared Beeper Will Find You
- Electronic Tax Returns Are Here
- Acoustic Trauma
- Letters - Artful Dodger, Field Support, Fellow in Utah, John J. Williams, Mojave Dessert
- Interesting Phone Numbers - Interesting phone number list
- Systematically Speaking - Spring and US Tel merge, write protect tabs wrong, Bell Atlantic chooses MCI, cellular phones in England, infrared beeper, electronic tax returns, acoustic trauma
$2600 Magazine - Volume 3, Number 3 (March 1986)
- An Overview of AUTOVON and Silver Boxes - Info on the Department of Defense's AUTOVON phone system and how it uses those extended DTMF tones
- AUTOmatic VOice Network (AUTOVON) Excerpt from a Global AUTOVON Telephone Directory as found in a Fort Lauderdale library.
- An American Express Phone Story - Story about hacking the toll-free charge card authorization number, by Chester Holmes
- Final Words on VMS - Security info and tips on DEC's VAX/VMS systems, by Lex Luthor
- Advanced Hacking VAX'S VMS Lex Luthor and LOD/H
- 2600 Flash
- Hacker Zaps Computer Marquee
- Soviets Denied Computer Access
- Who Called The Shuttle?
- New Ways Of Stealing Data
- Computer Password Kept Secret
- Satellite Jammers Jammed
- TASS News Service
- Soviet Computer Update
- Dial The Yellow Pages
- Northern To Destroy COs
- There Are More Phones Than Ever
- Letters - Corporation, Dissenting Opinion, DIAL, Various People, Scan Man, A Subscriber in Pa.
- This Month at 2600 - Private Sector's return, Computel and Compuserve, Telepub '86, a postal miracle
- Systematically Speaking - Jamming satellites, TASS news service, Soviet computer update, dialing the Yellow Pages, Northern Telecom to destroy COs, more phones than ever
$2600 Magazine - Volume 3, Number 4 (April 1986)
- RSTS for Beginners - Beginner's guide to RSTS/E on DEC PDPs, by The Marauder
- Hacking the RSTS/E System by The White Guardian
- Making the Most of RSTS/E Systems by Captain Hack
- Mobile Phones - Theory & Construction - Info on Improved Mobile Telephone Service (IMTS) and building your own dialer, by The Researcher
- 2600 Flash
- British Phonebooth Wedding
- Man Worries About Sprint Bill
- Bad Tenant Databases
- Car Breathalyzers
- Phone Phreak Fined
- Marcos Phones For Free
- 617 Will Be Divided
- Congress Chooses AT&T
- Baby Bells Don't Pay AT& Bills
- Equal Access 800 Drawbacks
- Encryption Provides Signature
- Directory Assistance Failure
- Dial "00" For Operator
- Letters - A Reader, Ben Harroll, (none given), Heyzeus Arguillis, NYNEX Phreak (Charles Andrew Hope)
- A Story of Eavesdropping - Listening to conversations during World War 2
- This Month at 2600 - Transcripts of the Private Sector raid, more on Computel
- Systematically Speaking - 617 to be divided, Congress chooses AT&T, Baby Bells don't pay AT&T bills, equal access 800s, data encryption, DA failure, AT&T loses its zero
$2600 Magazine - Volume 3, Number 5 (May 1986)
- Exploits in Operator Hell - Harassing the operators in Alaska, by The Alaskan Phreak (TAP)
- The Computel Scoop - Info on the magazine Computel which was believed to be related to TEL
- 2600 Flash
- Bellcore Publications Go Public
- US and France Link Phones
- Computer Grammar
- Shower Phone?
- Cellular Modem
- High Tech Parking Meters
- Congressional Computer
- Wrestlemania Pins Bell
- Sting Boards on the Rise
- American Network Fears Hackers
- Free Pay-Phones Plague New Jersey
- Bogotá, Columbia Gets Extra Digit
- Patients May Get To Keep Phones
- Beware of Hacker Terrorists
- Letters - MM (Dublin, Ireland), MS, The Doctor, J in Boston, WP, The Hooded Claw, Unlisted Number
- AUTOVON Translations - Translations for AUTOVON numbers, by The Creature
- Systematically Speaking - Wrestlemania pins Bell, sting boards on the rise, American Network fears hackers, free payphones plague New Jersey, disposable phones, hacker terrorists
- Boxing on ITT / SBS Skyline - Boxing tips and code info
$2600 Magazine - Volume 3, Number 6 (June 1986)
- Computer Crime Review - Review of a report from The National Center for Computer Crime Data
- How to Hack a Pick - Beginner's guide to hacking the Pick operating system
- Review: The Computer Underground - Book review of M. Harry's The Computer Underground, by John Drake (Mark Bennett)
- 2600 Flash
- New York's Computer Law
- $6,829 Phone Bill
- Big Computer Crime Pays
- Public Phone Secrecy
- Capitol Hill Hacker
- Citibank Money Games
- Hands Across Telenet
- Kiev Calling Clogged
- NYNEX Bumps Southwestern Bell
- Stock Market Crash
- "Ed Quinn Cell Site"
- Let's Move To France!
- Letters - Twilight Zone The Phreaker (London, England), JN (Illinois), Lord Peter Wimsey, Dr. William Wainwright, John Smith Hacker, Seagull, PV, (none given), Right Track
- Special AT&T Services - Various phone numbers
- Resources Guide - Various groups and publications on computer security
- Systematically Speaking - Hands across Telenet, calling Kiev, NYNEX bumps off Southwestern Bell, stock market crash, cell site names, videophones
$2600 Magazine - Volume 3, Number 7 (July 1986)
- Violating a VAX - Trojan horses, obtaining passwords, and other VAX/VMS hacking tips, by Baalzebub
- The Free Phones of Philly - Skyline providing free long-distance from payphones, by Chester Holmes
- 2600 Flash
- Town on Hold During Strike
- Prisoners Break Law
- Hacker Degrees?
- New Jersey Tops Taps
- Ex-Fed Tapped
- SS Numbers Returned To Citizens
- Computers Strike Again!
- Federal Employees "Tracked"
- AT&T Selling Payphones!
- Automated Operators Coming
- Cellular Dial-By-Voice
- New British Phone Service
- No Data Protection for Hong Kong
- 74,000 Calls to Fraud Line
- Federal Phone Failure
- Indiana Telco Threatens AT&T
- Letters - Shadow 2600 and Kid & Co., Howard, kl, Untitled, SF
- Country Codes - Country code list from Telecom Digest
- Systematically Speaking - AT&T selling payphones, automated operators, cellular dial-by-voice, new British phone service, no data protection for Hong Kong, Congressional fraud hotline, federal phone failures, Indiana telco threatens AT&T
$2600 Magazine - Volume 3, Number 8 (August 1986)
- Knowing UNIX - UNIX hacking tips, sending email, and some simple C code, by The Kid & Co.
- A Trip To England - Phreaking story from England, by John Drake
- 2600 Flash
- Phone Fraud in Governor's House
- BB Watching VDT Operators
- LD Companies Strike Back
- Leave Our Poles Alone!
- Phone Booths Mauled Then Stolen
- The Ghost in the Machine
- USSR Computer Hungry
- ATM's in China!
- Cash Machines Are Popular
- TV Blue Boxes
- New Chip Helps Sprint
- Government Phone Fate?
- Rural Radio Phones
- "Debugging" Phones
- Letters - The Stopper, Rees Morrison (Scarsdale, New York), j, Stake Out
- Carrier Access Codes - List of 10xxx PIC codes
- Long Distance Carrier (IXC) Access Codes a.k.a Primary Interexchange Carrier (PIC) codes
- Long Distance Carrier Access Code List - Numerical
- Long Distance Carrier Access Code List - Alphabetical
- Long Distance Carrier Code Assignments FCC, June 1997
- NPA Exchange Count - List of area codes and the number of exchanges in each
- Systematically Speaking - USSR computers, ATMs in China, NYCE, TV Blue Boxes, government phones, rural phone radios
$2600 Magazine - Volume 3, Number 9 (September 1986)
- Some Facts on Supervision - Information on phone call answer supervision signals, by The Kid & Co.
- RCI & DMS-100 Bugs - Long-distance extender bug
- Another Stinger is Stung - Another sting BBS operated by John Maxfield and Mike Wendland of WDIV TV.
- 2600 Flash
- NSA Drops DES
- Hackers On Shortwave
- BB Traffic Cop
- Crosstalk Saves Old Lady
- Indian Phones Under Siege
- "Signature" On Video Transmitters
- FBI Shopping List
- Poor Connection Starts Bomb Scare
- GTE Sprint Overbills
- FCC Gives Away "Resource"
- AT&T Best For Hackers
- Portable VAXes!!!
- Computer Clothing
- Message On the Move
- Call Rejection In Natchez
- Letters - Lord Phreaker, TCCFBT, Joshua Falkon, Friends in faraway places, Curious, Captain Zorg, Hal-9000/Beast 666
- Interesting Numbers of Winnipeg - Fun phone numbers in Canada
- Systematically Speaking - GTE Sprint overbills, AT&T ranks #1, portable VAXes, call rejection
$2600 Magazine - Volume 3, Number 10 (October 1986)
- Death of a Payphone - Payphone secrets and how to mess up a payphone, by MAD!
- The ABC'S of Payphones by MAD!
- Trashing: America's Source for Information - How to dig through phone company garbage for information, by The Dragyn (Steven Nygard, Austin, Texas)
- Bell Trashing by The Dragyn
- 2600 Flash
- FBI Investigates Coffee Machine
- CIS Copyrights Public Software
- Navy Software Available
- HBO Encryption Broken
- Pennant Ties Up Phones
- Security Can Kill Creativity
- Indiana "Fones" Are Gone
- Electronic Tax Returns
- Software Makers Crash BBS
- Poor Service An Understatement
- Rural Ultraphones
- Local Toll-Free Numbers
- ESS Goes To Taiwan
- NSA Wants a New Chip
- Letters - Psycho (California), Wolfgang Amadeus Mozart, Crazy Eight, Long-Distance Voyager, Wize owl (Hilo, HI), Mr. Tracer, Het Kap, Bernie S.
- Interesting London Numbers - Fun phone numbers
- Systematically Speaking - Electronic tax returns, software makers crash BBS, ICN, Ultraphone, ESS in Taiwan, NSA wants new chip
- Ancient Bell Labs Advertisement - Bell System Ad for Touch-Tone signaling
$2600 Magazine - Volume 3, Number 11 (November 1986)
- ICN - More Than a Bargain - Info on Independent Communication Network phone service, by John Freeman and Evil Corley
- Mastering the Networks - Info on some of the larger computer networks (ARPANET, BITnet, etc.) and their email syntax, by John Anderson
- 2600 Flash
- Voice of Reagan Tortures Patients
- FBI Actions Anger Parents
- "Q" and "Z" Controversy Rages
- More Banks Link Arms
- Sprint - Too Many Customers
- More Magic Buttons
- New Payphone Service for Michigan
- Nickname Listings In Small Town
- Computer College
- Letters - Amadeus, Frustrated in Miami, Reader on the Pacific, Private Sector Subscriber, Any Mouse, NYNEX Phreak
- British BBS Numbers - BBS number list for the U.K.
- Wrath of God Strikes 2600 - They really are the dumbest people on the planet
- Systematically Speaking - Bank link arms, Sprint has too many customers, new payphones, nickname listing, computer college
$2600 Magazine - Volume 3, Number 12 (December 1986)
- Cellular Telephones - How They Work - How Improved Mobile Telephone Service (IMTS) cellular phones work, by Bruce Alston
- Things We're Not Supposed To Know About - Info on the Captain Midnight (John R. MacDougall) HBO hack, by Sir William
- 2600 Flash
- How Not to be Rejected
- Phreaks Tie Up Lines
- North Carolina #1 in Hacking
- International Hacking
- Computers Threaten Privacy
- Telco Says "Pay for Tones"
- Loophole in Wiretap Law
- Free Directories For Bigwigs
- PC Pictures
- Fingerprint Identification System
- Buy My Wires
- Navigate With A CD
- IBM Braille Compatible
- Who Wants To Be Swept?
- Letters - John Freeman (Ann Arbor, MI), BA, TOTE (Rio Piedras, Puerto Rico), Bernie S., Michael Marr (Dublin, Ireland), (none given)
- Net Mail Sites - Networks carrying electronic mail
- Systematically Speaking - Free directories, fingerprint ID system, navigating with CDs, sweeping for bugs
$2600 Magazine - Volume 4, Number 1 (January 1987)
- Changes - Editorial
- TAP: The Legend is Dead - Info on the ending of the TAP newsletter, by The Cheshire Catalyst
- TELEPUB '86 Exclusive footage of a hacker gathering on March 8, 1986 featuring Cheshire Catalyst discussing the issues surrounding the future of TAP.
- Stumbling Into Control on a VMS - VMS hacking tutorial, by The Mole
- Telecom Informer - British Telecom info, by Dan Foley (David Flory)
- Evolution of the Telephone -
- Illegal Megahertz - List of analog (800 MHz) cellular frequencies. Don't even think of listening!
- Cellular Information Compiled by Madjus of N.O.D. Phrack, Issue #43
- Letters
- Beepers - da
- GTE Telcos - Arthur Dent
- Preacher Hams - Phil
- Student Restrictions - An "English Soccer Fan"
- An Acronym Maker - The Gladiator
- More TAP Woes - Arab149
- 800 Directories - Cocopelli
- Searching for ANI - Also frustrated in PA
- Phone News - Phone news
- 2600 Marketplace
- Price: $2.00
- Cover (Cover Info)
- Inside
- Phone #1 A British Telecom card-reader phone. Photo by John Drake
- Staff
- Download Official Scanned Edition PDF!
- Download The Hacker Digest - Volume 4!
$2600 Magazine - Volume 4, Number 2 (February 1987)
- Hugo Cornwall Interview - Interview with Peter Sommer, (a.k.a. Hugo Cornwall), Britain's most famous hacker/author, by John Drake
- COSMOS Guide - Overview of Bellcore's Computer System for Main Frame Operations (COSMOS) frame/OE management system, by Sir William
- The 1986 COSMOS Files: Part 3 Service Order Input, by Sir William [KOTRT]
- Telecom Informer - Phreaking news, by Dan Foley
- Nasty Business - MCI and Sprint letters
- Letters
- Some Suggestions - The Perpetrator
- Some Numbers - Silver Bandit
- On Cellular Phones - The New Age Phreaker
- ANI Trouble - (none given)
- Book Review: The Hacker's Handbook - Book review of Hugo Cornwall's The Hacker's Handbook, by Roland Dutton
- New Developments - Touch-Tone (DTMF) service charges
- Book Reviews - Book reviews of The Hacker's Handbook by Hugo Cornwall and Consumertronics' Automatic Teller Machines III by John J. Williams, Reviews by Roland Dutton and Lord Phreaker
- 2600 Marketplace
$2600 Magazine - Volume 4, Number 3 (March 1987)
- Reach Out and Touch a Nuclear Weapons Contractor - List of long-distance telephone companies which are (or not) associated with nuclear weapons development - the list may surprise you...
- The Ballad of Captain Crunch - Folksong about John Draper, by Mike Agranoff (Boonton, New Jersey)
- Getting the Most Out of Equal Access - Overview of the AT&T breakup and PIC codes, by The Hobbit (Al Walker)
- Telecom Informer - Updated Equal Access list, end of non-1+ LD dialing, new direct-dialable countries, by Dan Foley
- The Wonderful World of COSMOS - Detailed information on using Bellcore's COSMOS, by Bill from RNOC
- The 1986 COSMOS Files: Part 3 Service Order Input, by Sir William [KOTRT]
- COSMOS Series: Part 1 - The Manual (OPA-1Y632-01), by Doctor Who
- Surveying the COSMOS by The Fire Monger
- COSMOS: Computer System for Main Frame Operations (Part One) From Phrack, Issue #26, by King Arthur
- The Definitive COSMOS From Phrack, Issue #31, by Erik Bloodaxe
- COSMOS Command Listing
- COSMOS Overview by The Warlock, Tuc, Agrajag the Prolonged
- Letters - PRINTABLE LETTERS
- An Envelope Please - Bob Gamma
- Comments... - AH
- And More Comments... - Bernie S.
- An Experience to Share - The Sultan
- Words of Agreement - DE
- Words of Caution - Ben Harroll (San Diego, CA)
- A Response - John J. Williams
- More on ICN - Jim A. (Montana)
- 2600 Marketplace
$2600 Magazine - Volume 4, Number 4 (April 1987)
- Computel Put to Sleep - Computel hacking magazine out of business
- Hacking PC Pursuit - Using PC Pursuit out-dials on Telenet, by The Cheshire Catalyst
- Telecom Informer - Cellular fraud bust, a look at the Electronic Communications Privacy Act, "fixing" your PRO-2004 scanner, the "forbidden frequencies,'by Dan Foley
- Customer Name & Addres List - Extensive Customer Name & Address number list, used to find the billing name to a given phone number
- 1-800 "Word" Numbers - A reader sent in their favorite list of "word numbers," that is, phone numbers that also spell out words, by Any Mouse (Illinois)
- Letters
- Communication - (none given)
- More ANI's - JA (Florida)
- Comments - Kirk (California)
- French Loophole - The Cote D'Azur
- Stuck on Busy - F.B.
- Praise - (none given)
- Criticism - RDM (Texas)
- Advice - A Reader
- A Warning - (none given) Newark, NJ
- Coin Test - Box Tester
- More Resources - Het Kapittel
- In Reply - MAC???
- Goings On - Various news bits
- 2600 Marketplace
$2600 Magazine - Volume 4, Number 5 (May 1987)
- More VAX Tricks - VAX/VMS hacking tips and code for password grabber and generator, by Mainstream America
- The Meaning of CLASS - Info on Custom Local Area Signaling Service (CLASS), by The Videosmith (Ronnen Miller, Philadelphia, PA)
- Custom Local Area Signaling Services (CLASS) by The Videosmith LOD/H Technical Journal
- Telecom Informer - AT&T's E-Card and the 959 test exchange, by John Freeman
- Phoning From Europe - European phone systems, by The Lineman
- Telenet Guide - Telenet address directory, The Legion of Hackers
- LOH Telenet Directory: Update #4 LOD/H Technical Journal
- Letters
- New Toys - Bernie S.
- Explain Yourselves - Izzy Hear
- Needs Blue Box Program - Edward Dean Jones
- Access Still Unequal - IHR
- Reaching Out - EH
- More on VAX - The Carolina Beachcomber
- FAX: A New Hobby - FAX machine info and receiving RF faxes, by Bernie S. (Edward Elliot Cummings, bernieS, DOB: 02-26-1962, N3KOW)
- 2600 Marketplace
- Review: Duophone CPA-1000 - Inexpensive telephone "pen register" from RadioShack, by Evil Corley
$2600 Magazine - Volume 4, Number 6 (June 1987)
- Editorial - Editorial
- Allnet: A Horror Story - Allnet scam, by Mike Yuhas
- Paging for Free - Free voice paging, by Bernie S.
- TSPS Guide - Hackers guide to the AT&T Traffic Service Position System (TSPS) console, by The Marauder
- The Traffic Service Position System (TSPS) by The Marauder LOD/H Technical Journal
- Telecom Informer - Phreaking news, by Dan Foley
- Letters
- A Mystery - Silicon Rat and the Mice
- In Reply - John J. Williams
- Military Madness - MDLP
- More Publications - Tabula Rasa
- Additional Facts - The Librarian
- Autovon Info - Rusty Diode
- Visions of Doom - Hex Converter
- Words of Praise - BBQ
- 2600 Marketplace
$2600 Magazine - Volume 4, Number 7 (July 1987)
- Cellular Phone Fraud and Where It's Headed - Overview of cellular phone cloning, by Bernie S.
- Guide to Cellular Phreaking by Bernie S.
- How Phone Phreaks Are Caught - How code abusers are caught, by No Severence
- Telecom Informer - Phone news, by Evil Corley
- Letters
- On Disclaimers - MAC???
- Texas Toll Fraud - The Hooded Claw
- Suggestions, Comments - The RAM
- A Horrible Problem - JD
- 2600 Exposes New York Telephone - Unfair telephone company Touch-Tone charges
- 2600 Marketplace
- Saudi Arabian BBSes - List of public BBSes in Saudi Arabia, by Veteran Cosmic Rocker
$2600 Magazine - Volume 4, Number 8 (August 1987)
- The Summer Games of '87 - Editorial
- TRW Credentials - TRW credit history and their lack of security, by Rex Valve
- Phone Numbers - Interesting phone number, by NYNEX phreak (Charles Hope)
- Telecom Informer - Phone news, by Evil Corley
- FBI Revealed - Review of Glen L. Roberts' The FBI Project Newsletter and The FBI and Your BBS newsletters, by Evil Corley
- AT&T Submarine Map - How to social engineer submarine (underwater, intercontinental) cable system charts, by Bernie S.
- Capturing Passwords - DEC Control Language (DCL) script for capturing VAX/VMS passwords, by Texas Toad
- Letters
- CNA/CPA Questions - Samuel Rubin
- ITT Switching - The Primal Wombat
- Hotline Numbers - Frank B.
- Monitoring Cellular - Stingray
- An Experience - The Sorcerer
- Phone Literacy - Audio O'Sirkit
- A Hacker Survey - Reader survey of hackers, by Evil Corley
- 2600 Marketplace
$2600 Magazine - Volume 4, Number 9 (September 1987)
- Worldnet: Getting Closer Every Day - Overview of early ARPAnet, BITnet, and UUCP networks, by Hank@Taunivm.Bitnet (Hank Nussbacher)
- Operating With Difficulty - New York Telephone operator troubles, by Wintermute (Peter Zatloukal)
- Telecom Informer - Phone news, by Al Fresco
- English Dial-It Service - Recordings and announcement list for England, by John Drake
- Letters
- Notes and Replies - Rainer Mueller
- An Explanation - The Sorcerer
- Newsstand Update - Curious
- Misinformation? Us? - Worried and Upset in Arizona
- 2600 Marketplace
- Review: CO Magazine - Review of a good telecom monthly journal, by Dan Murphy
$2600 Magazine - Volume 4, Number 10 (October 1987)
- New York's IMAS - Integrated Mass Announcement System overview, by Mac+
- Telco's Response - Telco response to Touch-Tone fee, by Bruce Reisman
- Telecom Informer - Phone news, by Evil Corley
- International NUA's - Tymenet and Telenet Network User Addresses (NUA), by The Greek
- South African BBSes - South Africa BBS list, by The Greek
- Letters
- Verification and Tracing - Joshua Falkon
- Missing Blue Box Chip - KM
- BBS Numbers - HAL 9000/Beast 666
- Getting Started - JS
- Private Sector Style - (none given)
- More on Disclaimers - John J. Williams
- And More - N.E. Mouse
- British Payphones - John Drake
- Those Silly Codes - Bellcore Common Language Location Identification (CLLI) code information
- 2600 Marketplace
- Contest Results
$2600 Magazine - Volume 4, Number 11 (November 1987)
- 2600 Bulletin Boards - BBS ad
- Hacking IBM's VM/CMS System: Part 1 - IBM 43XX-series and 30XX-series VM/CMS info, by Lex Luthor
- Hacking IBM's VM/CMS Operating System by Lex Luthor LOD/H Technical Journal
- Social Security Prefixes - Prefix to state mappings, by The Disk Jockey (Douglas Mason, DOB: 12-29-1967)
- Listening In: Catch Me If You Can! - Monitoring satellite phone calls, by The LNA Master
- Review: Government Radio Frequencies - Book review of Tom Kneitel's The "Top Secret" Registry of U.S. Government Radio Frequencies, by Mr. Icom
- Telecom Informer - Phone news, by Staff
- Letters
- Double Beepers - Bob from Los Angeles
- Why No Boxing? - Franken Gibe (Texas)
- Apple Hacking - The Rifter
- More How-To Articles - Tabula Rasa
- A New Source - E.H.
- Pen Registers - Samuel Rubin
- Unique Projects - John Nix
- TAP is Dead! - D.L. (New York)
- 2600 Marketplace
$2600 Magazine - Volume 4, Number 12 (December 1987)
- Important News - Editorial
- Hacking IBM's VM/CMS System: Part 2 - IBM 43XX-series and 30XX-series VM/CMS info, by Lex Luthor
- Hacking IBM's VM/CMS Operating System by Lex Luthor LOD/H Technical Journal
- Telecom Informer - Phone news
- All About BLV - AT&T TSPS Busy Line Verification (BLV) information, by Phantom Phreaker (Curt Richard Wilson)
- Busy Line Verification by Phantom Phreaker Phrack, Issue #11
- Social Interaction With Phones - Stories about phones in our culture, by Dave Taylor
- Letters
- Switch-Hook Dialing - JS (Dallas, TX)
- Pen Registers - Norman Bates
- Evil Happenings - Pala Jones
- Canadian Questions - PG (Toronto, Canada)
- The Truth Revealed - The Cheshire Catalyst
- Ingenious Solution - Sgt. Pepper of Texas
- How Do Inmates Do It? - The Hooded Claw
- BBS Thoughts - P.A.Z.
- The Missing Chip - (none given)
- Yet Another Telco Ripoff - Mary M. (Cornland, IA)
- Roman Hacking - Overseas tales of hacking and phreaking, by Hal from Rome
- 2600 Marketplace
- Long-Distance Horror Tales - MCI tale of trying to set up a long-distance carrier
$2600 Magazine - Volume 5, Number 1 (Spring 1988)
- Monitoring Phone Calls With a TVRO - Listen in on international telephone calls using a satellite receiver
- More on VM/CMS - VM/CMS article corrections and additional info, by VM Guru
- Weathertrak Codes - Codes for a telephone weather system
- An Interpretation of Computer Hacking - An interpretation of computer hacking by a complete fraud, by Captain Zap (Ian A. Murphy, DOB: 01-25-1957)
- Private Sector Scam Revisited - Evidence from the Private Sector raid
- Letters
- More Secrets - Doom
- Encouraging Words - A Friend in Texas
- Still More Secrets - (none given)
- A Very Special Number - (none given)
- Tales of Hackers - The Hooded Claw
- Advice Wanted - (none given)
- Of Phones and Politics - Skinhead Steve and The Boy
- More on the 8038 - (none given)
- REMOB Hunting - MH (Uniondale, New York)
- The Global Village - The NATO Association
- A ROLM Catastrophe - ROLM telephone system troubles
- Happenings - Various news bits
- 2600 Marketplace
- AT&T/BOC Routing Codes - Routing codes used during Blue Boxing
$2600 Magazine - Volume 5, Number 2 (Summer 1988)
- Allnet's Legal Problems - Allnet lawsuit
- A Solution To Viruses - Protection from computer viruses, by Ross M. Greenberg
- How to Write a Virus - How to write a computer virus, by The Plague
- Building a Red Box - Schematic for a actual working Red Box, by R.J. "Bob" Dobbs (Vance Morgan)
- A Real Functioning RED BOX Schematic by: R.J. "BoB" Dobbs Phrack, Issue #33
- A Reader's Reply To Captain Zap - Reader replies to Captain Zap's drivel, by The Rancid Grapefruit (Bruce Fancher, DOB: 04-13-1971)
- Letters
- Reactions to Zap - Murdering Thug and The Boy!, The Shadow, Yevgeny Zamyatin
- Gripes and Feedback - Natuerlich!
- A Useful Trick - (none given)
- "Deluxe" Call Waiting - GH
- New Falwell Numbers - A True Believer
- What is Sprint Up To? - Cray-Z Phreaker
- 2600 Marketplace
- Fun Phone Numbers - List of various interesting phone numbers, by Thunder Seven
$2600 Magazine - Volume 5, Number 3 (Autumn 1988)
- Outside Loop Info - Telephone outside loop distribution plant overview, by Phucked Agent 04
- The Outside Loop Distribution Plant by Phucked Agent 04 LOD/H Technical Journal
- Cellular Phones - Update on cellular phones, by The Glitch
- Who Was Strowger? - Info on Almon Strowger, by Almon Strowger Jr. (No, not the real one)
- Communications Update - Various news bits
- A Map of the 516 NPA - List of exchanges in 516
- Red Box Program - Commodore 64 BASIC program for generating Red Box tones, by Tommy (Art of Hacking, BBS, Website, Victoria, British Columbia)
- Canadian Numbers - Canada WATS, by Tommy
- Letters
- The Schematic - The Bug Brother #1
- The Virus - Jonathan Porath, Paul van Hattum (Holland), Tommy
- The Chip - Rubber Soul (Toronto, Ontario)
- Another ANI - The Soldier
- BLV Tidbits - The Zeppelin
- What's The Point? - (none given)
- Questions - J.D.
- Another Scam - Doug Porter (Tucson, AZ)
- Anti-Gay Offensive - CH
- 2600 Marketplace
- Price: $4.00
- Cover (Cover Info)
- Inside Cover
- France French payphone was our very first foreign payphone photo. Photo by John Drake
- Staff
- Download Official Scanned Edition PDF!
- Download The Hacker Digest - Volume 5!
$2600 Magazine - Volume 5, Number 4 (Winter 1988-1989)
- The Internet Worm Story - Detailed technical information on the Robert Morris Internet worm, by Bob Page (Santa Cruz, California)
- A Report on the Internet Worm by Bob Page
- With Microscope and Tweezers: An Analysis of the Internet Virus of November 1988
- Code: Robert Morris Internet Worm Source Code
- MCI: The Phone Company with a Lot of Explaining to Do - MCI troubles and being switched to their service without notice, by Evil Corley
- Hacker's Guide to UNIX - Info on hacking UNIX systems, by Red Knight (Phreakers/Hackers Underground Network)
- An In-depth Guide in Hacking UNIX and the Concept of Basic Networking Utility by Red Knight Phrack, Issue #22
- Overhearing Phone Calls - Monitoring telephone calls on a scanner or TV
- Letters
- Some Ideas - (none given)
- Articles & Boards - SW
- Need Info - Handel
- AT&T Nightmare - Cray-Z Phreaker
- Call Forwarding - JH
- Observations - Phantom Phreaker
- Soviet Operators - What it is like to be a Soviet telephone operator, by E. Solomenkoa
- Chaos Computer Club - Interview with several members of the Chaos Computer Club, by John Drake
- 2600 Marketplace
- Hardwiring Free Calls - Info on what is now called "Beige Boxing," by Dr. Williams (Hardwiring Your Way In)
- Book Review: Tune In On Phone Calls - Book review of Tom Kneitel's Tune In On Telephone Calls, by Lou Scannon
$2600 Magazine - Volume 6, Number 1 (Spring 1989)
- Hackers in Jail - Editorial (Kevin Mitnick hacked NORAD!?)
- The Wonders of UNIX - More info on hacking UNIX systems - part 2, by Red Knight (Phreakers/Hackers Underground Network)
- 800 & 900 Exchanges - 1-800 and 1-900 translation table, by Scott Statton (N1GAK)
- Letters
- WarGames Dialer - Phloyd Scaari
- More ANI's - RR, (none given), KH
- Blue Box Questions - Santa Claus, Boxed In (Texas)
- A Scary Tale - The Disk Jockey
- How Payphones Really Work - Detailed info on how payphones work, by The Infidel
- News From Around
- Ripoffs & Scams
- Long-Distance Censorship
- Foul-ups & Blunders
- Abuse....
- Mischief Makers
- 2600 Marketplace
$2600 Magazine - Volume 6, Number 2 (Summer 1989)
- Index - Guide of Contents
- Remember... - Editorial
- A Guide to PRIMOS - User guide to the PRIMOS operating system, by Violence (Yesmar, Glyph, The Raver [cDc], Necrovore [Bellcore], Violence [The VOID Hackers])
- Introduction to the PRIMOS Operating System by Violence
- 201 Exchange List - List of NXXs in the 201 NPA (Northern New Jersey), by The Infidel
- Scanning for Calls - Monitoring cordless phones, by Mr. Upsetter (Jason Hillyard)
- Letters
- The South African Phreak Crisis - (none given)
- Payphone Query - Uncle Ho
- UNIX Made Easy - The Micron
- Did You Know? - Name Withheld
- Notes and Info - S. Fox, Mr. Upsetter, PG
- Crossbar Trick - JWC
- Stories Wanted - JJ Buck Bloombecker
- Tuning In Calls - Cyber Punk
- Austrian Phreaking - WM
- Just Say No - Phil
- A Myriad of Questions - (none given)
- Tips on Trashing - How to dig through garbage, by Dr. Williams
- A Sprint Story - Story of a Sprint security raid against a code kiddie, by Larry P. (Larry Phreaker)
- Spanish Phones - Overview of the phone system in Spain which originally appeared in England's Financial Times, by Peter Bruce
- A Summer Worm - Similar Robert T. Morris' Internet worm ADA source code, by Jeff Gray
- 2600 Marketplace
- Reviews - Reviews of George Zeller's book The 1989 Pirate Radio Directory and the "new" TAP, by Paul Estev and Evil Corley
$2600 Magazine - Volume 6, Number 3 (Autumn 1989)
- Competition: It's the Next Best Thing to Being There - NYNEX Strike editorial
- Grade "A" Hacking - University Applications Processing Center (UAPC) information, by The Plague
- Galactic Hacker Party - Hacker con in Amsterdam
- British Telecom's Guilty Conscience - Letter to British Telecom customers
- The Death of COSMOS? - Some info on Bellcore/Telcordia SWITCH, the COSMOS replacement system
- What's Going On
- Technological Marvels
- Hacker Spies
- NYNEX Bigotry
- Dial-It News
- Payphone Choices
- Overseas Access
- News from the U.K.
- One Less Choice
- Privacy? What's That?
- Hackers In Trouble
- Hacker Fun
- Telco Literature
- Calling Card Tutorials
- Another Telco Ripoff
- Technology Marches Back
- And Finally
- The Secrets of 4TEL REMOBS - Info on the Teradyne 4TEL loop testing system used by GTE, by Doom Prophet (Craig Wilson, Ferrod Sensor, Trouble Verify)
- An Introduction to Teradyne's 4TEL System by Doom Prophet LOD/H Technical Journal
- Letters
- Mobile Telephone Info - Koo Iyo Do
- Southern ANI - John
- ROLM Horrors - gmw
- A Nagging Question - The Apple Worm
- A Request - (none given) (Grand Rapids, Michigan)
- Another Request - THOR
- The Call-Waiting Phone Tap - (none given)
- Interesting Numbers - (none given), LK
- UNIX Hacking - fin
- Intelligent Payphones - Mr. Upsetter
- Retarded Payphones - Incarcerated
- REMOBS - Information on the infamous Remote Observation Systems, by The Infidel
- GTE Horrors - Misc info on GTE and their operations, by Silent Switchman and Mr. Ed Angry
- Voice Mail Hacking - Hacking voice mail systems, by Aristotle (Kevin P. Jones, Louisville, Kentucky, Email #2)
- Punching Payphones - How to "punch" payphones, like in WarGames, for free local calls, by Micro Surgeon / West Coast Phreaks
- Useful Frequencies - DTMF and Special Information Tone (SIT) frequencies
- 2600 Marketplace
- Carrier Access Codes - 10XXX PIC codes
$2600 Magazine - Volume 6, Number 4 (Winter 1989)
- The AT&T Story - Editorial
- Our Ever-Changing World
- Morris Found Guilty
- Real Damage
- Jailed For Incompetence?
- New Technology
- And Things To Play With
- Ripoff City
- Calling London
- Sprint Is Watching
- Equal Access For All
- German Democratic Phones
- Too Much Chatter
- NYNEX Central Office Data - CLLIs and info for NYNEX COs, by The Plague (Special thanks to Kornflake Killer)
- PRIMOS, Part Two - User guide to the PRIMOS operating system, by Violence
- Introduction to the PRIMOS Operating System by Violence
- Building a Silver Box - Build an extended DTMF keypad (A, B, C, D tones), by Mr. Upsetter
- Letters
- Help Needed - Concerned (Syracuse, NY)
- Interesting Facts - The Renegade of Pittsburgh
- More Frequencies - MM (Rutherford, NJ)
- Numbers Needed - MC (Van Nuys, CA)
- BBS Question - Greg (New York)
- Comments/Suggestions - HC (Phoenix, AZ)
- COCOT Hacking - (none given) (Akron, OH)
- GTE Mysteries - H. (Manhattan Beach, CA)
- On Being Traced - The CPU Raider
- Information - KS (Pittsburgh, PA), DS (Rocky Point, NY), AG (San Bernardino, CA)
- Life's Little Moments - F.M. "Cordless"
- Fun Numbers - The Seeker (Chris Hufnagel, New York, NY)
- Words of Thanks - ???
- How? - WAFB (Knob Noster, MO)
- Hacker Clubs - BK (Syracuse, New York)
- Another Rip-Off Story - Dr. Williams (Washington State)
- 2600 Marketplace
- Area Code/Exchange Count - Exchange count for each NPA
- UAPC Update - Update on the story of New York kids changing their grades, by The Plague
$2600 Magazine - Volume 7, Number 1 (Spring 1990)
- Index - take a look
- For Your Protection - Editorial
- The Secrets of MIZAR - Info on the MIZAR recent change memory management system, by The "Q"
- Translating Orders Into Action by The Renegade Hacker!
- Operation Sundevil Map - As we went to press, the largest hacker raid in history started happening. There aren't many details we can give you in this issue except to say that this is the first one we know of that had a name.
- "The Partnership for a Hacker-Free American" Spoof Ad - When you hack, you're overusing your brain and are liable to find out things you shouldn't.
- Toll Fraud Detection Techniques - Info on Signal Irregularity (SIGI) reports under a #1A ESS, by Phantom Phreaker and Doom Prophet (Ferrod Sensor)
- Building a DTMF Decoder - Construction plans and schematic for an advanced hardware-based DTMF decoder which includes RAM for digit memory, by B/Square and Mr. Upsetter
- Silver Box Born in U.K. - Using the extended DTMF tones in the U.K. and Europe, by Tamlyn Gam
- Listening In: Listening to Phone Calls - Monitoring marine radio frequencies (ship-to-short) to listen to conversations (or grab calling card numbers), by Mr. Upsetter
- 2600 E911 Document LOL Fax - We get the most interesting faxes for miles around.
- 2600 Network Scanner in Shell Fax - big.cheese.sh
- News Update
- Morris Sentenced
- Albania Callable
- MCI Insecurity
- New York Tel Rate Increase
- Furthermore...
- Letters - you've found the officials 2600 letters column
- Clarifying REMOBS - MOD!
- Who's Listening? - WH (New York)
- Blue Box Chip - Mr. Upsetter
- Bug Wanted - Charlie Brown
- Questions and Info - GB
- Yet Another Threat - fin
- Red Box Woes - Curious, (none given) (Rhode Island)
- Suggestions and Questions - Redneck 1 (San Luis Obispo, CA), Satisfied Customer, An Overseas Fan, Somewhere in the Midwest
- Hotel Phones - DB (New York, New York)
- The Facts on 10698 - The County Man
- More Network 2000 Ripoffs - The Iron Warrior
- Sensitive Material - A Dedicated Subscriber
- The Scoop on 911 - Review of the infamous BellSouth Practice 660-225-104SV (E911 document), by Evil Corley
- Fun and Games at the 2600 Meeting - New York 2600 meeting at the Citicorp building apparently under police surveillance
- Data Network Identification Codes - Data Network Identification Codes (DNIC) for X.25 packet networks
- HELLASPAC by monty f41th, Issue #8
- List of Data Network Identification Codes According to ITU-T Recommendation X.121 (10/2000)
- The 707 Area Code - List of exchanges in the 707 area code (North Coast of California), by Lurch
- Book Review: The Cuckoo's Egg - Book review of Clifford Stoll's The Cuckoo's Egg, by Dr. Williams
- 2600 Marketplace
- Price: $4.00
- Cover (Cover Info)
- Inside Cover
- Amsterdam Naked Dutch payphones in the streets of Amsterdam
- Australia And a fully clothed one in Australia (Gold Phone)
- Staff
- Download Official Scanned PDF!
- Download The Hacker Digest - Volume 7!
"Remember, much of $2600 is written by YOU, our readers."
But the profits go into MY wallet! Suckers!
$2600 Magazine - Volume 7, Number 2 (Summer 1990)
- Index - ingredients
- A Bittersweet Victory - Editorial
- The Neidorf/Phrack Trial - Day-by-day overview of the Craig Neidorf trial, by Gordon Meyer and Jim Thomas
- An Interview With Craig Neidorf - Interview with Craig Neidorf about the trial, the future of Phrack, and his own future.
- What is the EFF? - Information on the Electronic Frontier Foundation and how it's not really a "hacker defense fund"
- Negative Feedback - Collection of different opinions on the Craig Neidorf trial and hacking in general
- PRIMOS Conclusion - Information on the PRIMOS computer system and PRIMENET, by Violence
- Introduction to the PRIMOS Operating System by Violence
- An Introduction to COCOTs - Information on Customer Owned Coin Operated Telephone (COCOT) payphones, by The Plague
- COCOT Payphones Renegade Legion Technical Report #2
- Letters
- Hunting for Wiretaps - none given (San Francisco, CA)
- Comments - Fred (Wilmington, Delaware), none given (Milwaukee, WI)
- On Government Raids - STM, DB
- For the Record - The Acronym King
- Questions - Simpson, BM, JI (Iceland), Jeff, none given (Guerneville, CA)
- Protection from Eavesdroppers - RG
- 2600 Compromising Ideals? - Disgusted Hacker
- An Unusual Request - Rick Saiffer
- Free Phone Calls - Mr. Upsetter, Birmingham
- News Update - Various new bits
- 2600 Marketplace
- Price: $4.00
- Cover (Cover Info)
- Inside Cover Mexican Payphones
- Staff
- Download Official Scanned PDF!
- Download The Hacker Digest - Volume 7!
$2600 Magazine - Volume 7, Number 3 (Autumn 1990)
- Index - within...
- Caller ID: The Facts - Information on Caller ID, by Jake "The Snake"
- Network 2000 Saga Continues - We've printed stories in the past about Network 2000 signing up people for Sprint's long distance service without the customer's consent. This page from a Network 2000 newsletter shows that they are very aware of the problem.
- Nice Telephone Company - Almost nobody heard about this incident. We weren't even aware of a service disruption! Of course, we didn't get this letter until the 6th, but it's the thought that counts, right?
- Nasty Telephone Company - In other words, we value your business, but no way are we going to trust you
- An Interview With Dr. Dorothy Denning - Interview with Dr. Dorothy Denning on the defense of Craig Neidorf and other hacker related topics, by Dr. Williams
- Concerning Hackers Who Break into Computer Systems by Dorothy E. Denning
- New Revelations From BellSouth - Technical information on BellSouth's new Dialed Number Recorder (DNR) system designed to "assist our security personal in identifying intrusions across the telephone network," by Evil Corley
- More Things You Really Shouldn't Know - Secret Service Fraud Division information on ATM fraud and ATM card security
- Defeating Trap Tracing - An overview of social engineering tricks to properly handle telco "who was that caller" calls, by Lord Thunder
- Letters
- Questions - Snoopy, JB (Ontario, Canada), Confused in Kentucky, Ashley (United Kingdom)
- Information - Roy, S.D., Mr. Upsetter, EH, D
- Information Needed - Dr. Williams
- Complaint/Response - Rainbow Warrior
- The COCOT Article - Halo Jones, Dan (Denver, CO), R.S. Grucz, Guyler Magruder (Singapore)
- Prison Phones - C. Rebel
- Privacy Preservation - Reverend Doktor (Matthew X. Economou), Norman Appleton
- Wiretap Clarification - Alan M. Kaplan (Las Vegas, NV)
- A Modern Proposal - Dr. Deviant
- Neidorf Defense Fund - Jeff Hunter (Temple of the Screaming Electron)
- Which Decoder Chip? - none given (Akron, OH)
- General Observations - NB (Rhode Island)
- Converting a Tone Dialer into a Red Box - The infamous RadioShack Pocket Tone Dialer (Part No. 43-141) to Red Box conversion article, by Noah Clayton
- RadioShack Pocket Tone Dialer Red Box
- Making a Red Box Out of a Tone Dialer Includes pictures and DeadKat's "Stealth-Combo Box" modification.
- Demo of a RadioShack Pocket Tone Dialer and a Standard Landline Phone
- RadioShack Phone Dialer - Red Box Hack a Day (2006)
- RadioShack Phone Dialer - Red Box Hack a Day (2014)
- Check From Howard Hughes - We want to thank everyone who took advantage of our Spring 1990 BellSouth E911 document offer. Now we really need you to help by contributing to the Neidorf Defense Fund.
- AT&T READYLINE Call Detail Report - Here we see what many 800 customers are now able to see: your telephone number. There are still parts of the country that don't pass along ANI; they are shown as area codes only.
- Build a Telephone Induction Coil - This multipurpose induction coil slips over the handset receiver of any payphone or standard desk phone and can be used in conjunction with a Walkman-type cassette unit for a variety of record and playback functions with excellent fidelity, by 1000 Spiderwebs of Might
- The Definitive ANAC Guide - List of Automatic Number Announcement Circuit (ANAC) numbers
- An Algorithm for Credit Cards - C source code for a credit card checksum verification routine, by Crazed Luddite & Murdering Thug (K00l/RaD Alliance!)
- Code: cc.c
- Facts and Rumors - News bits from the Atlanta LOD trial, and a therapist exploiting the ZOD case
- 2600 Marketplace
- Price: $4.00
- Cover (Cover Info)
- Inside Cover
- Paris French coin phones increasingly hard to find, but here's one in Paris
- Holland Strange days in Holland
- United States Military madness
- Staff
- Download Official Scanned PDF!
- Download The Hacker Digest - Volume 7!
$2600 Magazine - Volume 7, Number 4 (Winter 1990-1991)
- Index - internal organs
- A Political Hacking Scandal - Hacking Democrats
- The Hacker Reading List - List of hacker magazines, books, and mailing lists, by Dr. Williams
- Central Office Operations - Overview of the inside and outside plant, by Agent Steal (Justin Tanner Petersen, MySpace, DOB: 07-28-1960)
- Central Office Operations Legion of Doom Technical Journal, Issue #4
- More Leaked Documents - Amusing document from a telephone operator's supervisor manual
- 1-900-STOPPER: Anatomy of a Rip-Off - Info on the 1-900-STOPPER number (Similar Article)
- Letters
- COCOT Troubles - KM
- Future Surveillance - fin (Minnesota)
- Why Did You Do It? - Questmaster (Santa Barbara, CA), Kenton A. Hoover
- Questions - Rob (Woodmere, NY)
- BBS Troubles - The Spectre (St. Paul, MN), Charlie Tuna (Kokomo, IN)
- Another Method - Mr. T.
- Suggestions - The Concerned!
- Technical Suggestions - AP (Oakland, CA)
- Caller ID Override - Pete (Akron, OH)
- A Phone Company Tour - Mitch (Cincinnati, OH)
- Assorted Thoughts - Keyboard Jockey, The Disco Strangler (South River, NJ)
- COCOT Info - (none given, Waterbury, CT), The Martyr and The Mute & Bach Wai
- Hacks for Throat & Chest - Can you believe the things people send us? (Hacks Cough Drops)
- Winning Reader Entry - Letter contest winners on counter the negative negative articles about hackers, by TELEgodzilla & unknown
- The Word in the Street - Various news bits
- To Our New York Telephone Customers - We don't know what's going on, but recently every customer of New York Telephone got this notice
- Publication Denial Notification - You can bet this went right up on the wall the moment we got it. We'd like to know what other magazines have received this honor. And how many magazines contain contraband?
- Fraud Alert Newsletter - This useful newsletter is available through the Communications Fraud Control Association
- 2600 Marketplace
- Price: $4.00
- Cover (Cover Info)
- Inside Cover Scandinavian Payphones
- Sweden A Swedish payphone at Djurgårdsbron, Stockholm
- Finland Finnish payphone on the island fortress oF Suomenlinna (Sveaborg), Helsinki
- Staff
- Download Official Scanned PDF!
- Download The Hacker Digest - Volume 7!
$2600 Magazine - Volume 8, Number 1 (Spring 1991)
- Index - innards
- In Pursuit of Knowledge: An Atari 520ST Virus - Atari 520ST virus code for the GEMDOS operating system, by The Paranoid Panda
- The Horrors of War - Pepsi takes down one if its 1-800 call-in games during the Gulf War to easy traffic constrictions
- The Terminus of Len Rose - Story of Len Rose's bust and the staggering amount of injustice and corruption by the U.S. DOJ, by Craig Neidorf
- Customer's Reaction to AT&T's War on Len Rose - Reacted to the AT&T fiasco. We'd like to know what others are doing, by H. Keith Henson
- Soviet BBS List - Phone numbers for various Bulletin Board Systems around the Soviet Union
- Smug Anti-Hacker Ads - TymCard & LeeMah - We've been getting pretty sick of this smug bragging that's been passed all over the place. Keeping people out in a controlled environment is easy. We'd like to issue a challenge of our own. If these products are so secure, then distributing a list of those companies that now use them should cause no problem whatsoever. How about it?
- What's Up?
- Identifying Callers
- Person Identification
- Credit Release
- Credit Due
- Modern Times
- Whose Scam Is It?
- Eternal Vigilance
- Illegal Networks
- EFF Lawsuit
- Prodigy Invading Privacy?
- Letters - Reader Feedback Time
- Some Suggestions - Mr. Upsetter, TT (Palo Alto, CA), Larry (New York), SM
- What Could It Be? - Mad Scientist
- Info Needed - JN (New York)
- Compliments - Carl Flach (San Leandro, CA)
- Mysteries - Flaming Carrot, (none given, New Mexico)
- Observations - Danny (Harlem, NY)
- General Complaints - Predator
- Payphone Question - TG PA
- Frustration - TG (Mt. Vernon, NY)
- AT&T Special Deal - Noah Clayton
- Telco Rip-Off - RG (Los Angeles, CA)
- Information - Boxholder (Walnut Creek, CA), The Butler, Jeopardy Jim (Jim Vichench, Stroke Information)
- Hacking 101 - S.C. (California)
- A Technical Explanation - Count Zero
- COCOT Observations - George W. (Camden, NJ)
- A Disagreement - Vernon J. Grant (Ely, NV)
- UNIX Password Hacker - Source code for a the author's Uhacker program, a wordlist-based crypt() password brute-forcer, by The Infidel
- Code: Uhacker.c
- Mail Appeal Denied - Yes, the appeal has been denied. Our entire Fall 1990 issue has been deemed unfit for Texas prisoners
- Looking Up IBM Passwords - IBM CMS 3.0 password grabber for non-privileged users, by Kevin Mitnick (DOB: 08-06-1963)
- Internet Outdials - List of Internet modem outdials and how to use them, by Kevin P. Jones
- The New LEC Order - Excellent article on modern Bell Operating Company (BOC) recent change and service order systems, by New Hack City
- 2600 Marketplace
- Price: $4.00
- Cover (Cover Info)
- Inside Cover
- New Zealand #1 Some New Zealand payphones still accept coins but the vast majority now use the prepaid card system. You'll notice in the bottom right a 12-inch high "mushroom' that is actually a plastic cover for the telephone cables. You find these everywhere in New Zealand and they're extremely easy to access. Thanks to JP of Australia
- United States In some remote parts of the United States, you will find "non-dial payphones" that connect you to the operator as soon as you pick up. You tell them the number you're calling and they tell you how much to deposit. Thanks to KC of the USA
- Holland In the words of our Dutch correspondent, "I don't think it's a payphone, but it looks pretty foreign." Thanks to H of Holland
- Staff
- Download Official Scanned PDF!
- Download The Hacker Digest - Volume 8!
"Never gaze at a man, not even in passing.
A member of Al Qaeda might assume you are gay, and all gays are an abomination before Allah."Maybe the source of Evil Corley's anger is because he was rejected from joining Al Qaeda?
$2600 Magazine - Volume 8, Number 2 (Summer 1991)
- Index - open for business
- Where Have All the Hackers Gone - Editorial
- Inflated E911 Document Costs - How the damages for the Phrack E911 document were calculated
- Magnetic Stripes - Magnetic stripe card reader schematic from Hack-Tic Issues #8/#9/#10, by Dr. Abuse
- Magnetic Stripes -=RDT Technical Report w/ Dr. Abuse English Translation from Hack-Tic
- Death of NYNEX Business Centers - Info on NYNEX changes, by Anonymous
- Hacker News - Info on Len Rose's prison sentencing for sending AT&T source code over a telephone
- Building a Tone Tracer - Build a tone generator for inductive probe line tracers, by Mr. Upsetter
- Hacking MCIMAX - Using a MCI product computer to access their MAX database, by MCI Mouse
- Inspect Implementation - Security problems in Digital's EASYnet and using INSPECT, by Condor Woodstein (Kevin Mitnick?)
- More on the CLASS Struggle - BELLCORE internal document on CLASS telephone service features
- Letters - The Letters Section
- UNIX Password Hacker - rj, DP, NEXUS 6
- Another 2600 Meeting - (none given)
- Access From Korea - Marooned in the ROK
- Red Box Notes - Larry (New York, NY), TH (Ventura, CA)
- UNIX BBSes - LT
- Interfacing With Mainframe - MAG (Saudi Arabia)
- Send A Message - Dark Overlord
- Caller ID Questions - MB, BK (Bethesda, MD), KB (Austin, TX)
- C&P Info Needed - The Monk (Arlington, VA)
- More Hackerphobia - Peter The Great
- Information Sources - CH (Los Angeles, CA), H. Rochim, Flatline
- On "Breaking In" - Scott Alexander (San Francisco, CA)
- Very Concerned - Quantom (Austin, TX)
- Interesting Numbers - Number 204 (Las Vegas, NV)
- COCOT Theories - Antonin Qwerty (Philadelphia, PA)
- Valuable Lessons - T.15 (Quebec, Canada)
- Hacking Water - RF (Hiller, PA)
- Numbers - American Anarchy (Virginia)
- Another MCI Rip-Off - GR (Libertyville, IL)
- The Value of 2600 - CH (New York)
- Disturbing Observations - DB (Flushing, NY)
- Some New Frequencies - Info on new analog cellular frequencies, by Bernie S.
- 411 - News about phone companies
- Regulating Scams
- AT&T Wants The World
- Advances in the U.K.
- New Services
- Corporate Litigation
- COCOT and PBX Features
- Story of the Year
- Another Great 900 Number
- Japanese Numbers
- Customs of the U.S.A.
- The Outages
- Another Outage
- Caller ID Pushers
- 2600 Marketplace
- When Hackers Ride Horses: A Review of Cyberpunk - Book review of Katie Hafner and John Markoff's Cyberpunk, by The Devil's Advocate
- BCS Speech/Discussion by John Markoff An -=RDT Special Report
- Pure Cyberfiction, Says Mitnick - Interesting reply to the above book from Kevin Mitnick
- Outdials - List of PC Pursuit and Canada's DATAPAC modem out-dials on Tymenet, by Net Runner
- Tymnet PCP Outdials Renegade Legion Technical Reports
- Prisoner Update - Letter from The Leftist (Franklin Darden, Email #2, Email #3, Ft. Lauderdale, Florida / Norcross, Georgia)
- Price: $4.00
- Cover (Cover Info)
- Inside Cover
- Czechoslovakia This is a Czechoslovakian payphone. It will take a few minutes for your eyes to adjust. This is a normal reaction.
- Soviet Union Brave 2600 photographers risked certain death recently in the Soviet Union to bring you exclusive pictures of a Soviet payphone being used as a barricade against tanks during the recent coup attempt.
- Staff
- Download Official Scanned PDF!
- Download The Hacker Digest - Volume 8!
$2600 Magazine - Volume 8, Number 3 (Autumn 1991)
- Index - what it is
- Why Won't They Listen? - Editorial
- Simplex Locks: An Illusion of Security - Infamous article on the poor security of Simplex locks - which everyone knew already, by Scott Skinner and Evil Corley
- Simplex Locks: Illusion of Security - Version 2.0
- Door Combinations - Fox Valley District
- Simplex Lock Combinations by Patrick Ekman
- Unican/Simplex Locks - Changing the Code or Combination
- Opening the Kaba Simplex Lock: Just How Easy Is It?
- Kaba Class-Action Lawsuit
- The Hacker Video - Overview of the video showing Dutch hackers entering a U.S. military computer system (tracer.army.mil) using the infamous "FTP bug," by Evil Corley
- Hackers Penetrate DOD Computer Systems GAO-IMTEC-92-5
- Protecting Your SSN - Protecting your Social Security number from con artists, by Chris Hibbert (Mountain View, California, Email
- COCOT Numbers - List of COCOT phone numbers in New England and Washington, D.C., by NB & The Dead Cow
- Letters - Pages of Letters
- Where One Hacker Went - (I used to be) Lex Luthor
- Technical Questions - MC (Austin, TX)
- Raw Data - The Militant Midget, Arkansas Coin Collector, GS (Seattle, Washington)
- FAXers Beware - SC (Hollywood, FL)
- Prodigy Far From Gifted - Big Al (Brooklyn, NY)
- General Questions - Wilson Longline (New York)
- Red Box News - Pete in Akron
- Suggestions/Questions - RN (Lake Forest, IL), Midnight Caller, KS (Saskatoon, Canada), GS (Ottawa, Canada), SS
- Caller ID Decoders - Bernie S.
- Hacking UNIX Passwords - SJ (New Haven, CT)
- Voice Mail Fun - Nick (Newcastle, England)
- Tidbits - Various news bits on MCI Friends and Family and AT&T 800 ANIs
- USPS Hacking - In-depth look at the U.S. Postal Service's Postal Numeric Encoding Technique (POSTNET) codes which are printed on envelopes and the mail sorting process in general, by The Devil's Advocate
- Psychology in the Hacker World - Inside the hacker and enforcement personalities, the latter the author treats as a 'paranoid schizophrenic' in its most extreme form, by Condor Woodstein
- More Exciting Prison News - Our magazine has been called just about everything under the sun, but this is a new one on us.
- More Conversion Tricks - More tips for converting those RadioShack dialers into Red Boxes, by DC (Plagiarized from an article by Count Zero)
- Useful UNIX Programs - C source code for some simple UNIX hacker-related crypt() tools, by Marshall Plann
- 2600 Marketplace
- Price: $4.00
- Cover (Cover Info)
- Inside Cover
- Poland Polish payphone in Warsaw. Photo by Tom Binko
- Italy Orange payphones in Italy. An increasing number only take cards. Photo by John Drake
- Staff
- Download Official Scanned PDF!
- Download The Hacker Digest - Volume 8!
$2600 Magazine - Volume 8, Number 4 (Winter 1991-1992)
- Index - components
- 2600 Corporate Headquarters - The Atlanta Hacking Center. Our building may not be as big as AT&T's, but we're still able to watch everything they're doing...
- Computer Security at the Bureau of Prisons - SENTRY computer system security statement before the Subcommittee on Government Information, by Richard J. Hankinson (Deputy Inspector General, Office of the Inspector General)
- Stuff You Should be Interested In
- Dutch Hacker Raids - by Fellpe Rodriquez & Rop Gonggrijp
- More AT&T Confusion
- Progression
- Regression
- crypt() Source - C source code to the UNIX crypt() function along with an very in-depth description of its mathmatical functions, by Dust (Bern, Switzerland)
- Code: crypt-bsd-4.3-reno.c
- Birth of a Low-Tech Hacker - This article follows the growth of a hacker in a totally different culture (India) than yours, by The Roving Eye
- Mobile Frequencies - List of VHF radiophone frequencies, by Esper
- "Apartment for Rent" Scam - By putting these signs on telephone poles, the people behind this scam stand a good chance of snagging a few unsuspecting clods who can't read the fine print as they drive by.
- Simplex Update and Corrections / USPS Hacking Corrections - Corrections to two articles in the last issue (Vol. 8, No. 3)
- POSTNET Programs - BASIC and C source code for generating U.S. Post Office POSTNET barcodes, by Marshall Plann
- Code: zipbar.c
- Letters - The Letter Bag
- Government Nonsense - AB (Sacramento, CA)
- Various Bits of Info - The Crankster Gangster & Tweaky Bird, MG
- Hacking School - MOE
- Modem Voyage - CH
- Questions - LH (San Diego, CA), John, John, E, RA (Virginia)
- Abuse of SSN's - RH (Tacoma, Washington)
- Private Eye View - PW
- Call For Info - (none given)
- On Virus Books - Phat Phreddy Phreak (Dan DiCenso)
- Long-Distance Trouble - Danny (New York)
- Dutch COCOTs - Jack-o (Hengelo, Holland)
- Cellular Eavesdropping - Matt B. (Somerset, MA)
- COCOT Experimentation - Kingpin
- Credit Wanted - Count Zero
- POSTNET Corrections - Black Fox (New York, NY)
- On Prodigy - Lawrence (New York), Jon Radel (Reston, VA)
- Reading ANI - Pete at AU
- Red Box Warning - BillSF
- Reading Stripes - Trigger (Santa Ana, CA)
- Lock Your Terminal - Cray-Z Phreaker
- Russian Technology - KT (Moscow, Russia)
- CLASS Features - Overview of some custom calling features, by Colonel Walter E. Kurtz 75 Clicks from the bridge
- COCOT Corner - Examples from a COCOT database, various notes on payments and installation
- An Appeal for Help - Help Craig Neidorf (Knight Lightning) pay his legal defense bills - the EFF did not help him, by Craig Neidorf
- Hacker Beer - Common in Germany and Austria, we're told this could be translated as "Hacker Nutrient Beer."
- What L.O.D. Really Stands For - From a Catholic school's newspaper in the 1950s
- Analysis: Gulf War Printer Virus - A skeptical look at that stupid "Gulf War Printer Virus" April Fool's hoax, by Anonymous
- U.S. Phone Companies Face Built-In Privacy Hole - Security hole in a switches Busy Line Verification (BLV) function
- Busy Line Verification by Phantom Phreaker, Phrack Issue #11
- Monitoring Devices - Simple FM wireless transmitter schematics, by BillSF (Bill Squire, Amsterdam, Holland)
- Human Database Centers - Various credit bureaus and database agencies, by PW
- 2600 Marketplace
- Price: $4.00
- Cover (Cover Info)
- Inside Cover
- Morocco #1 A vandalized payphone between Casablanca and Marrakesh in Morocco. Photo by Bernie S.
- Morocco #2 A money-stealing Moroccan payphone. Photo by Bernie S.
- Belgium #1 This one takes money. Photos by Kingpin
- Belgium #2 This one takes cards. Photos by Kingpin
- Staff
- Download Official Scanned PDF!
- Download The Hacker Digest - Volume 8!
$2600 Magazine - Volume 9, Number 1 (Spring 1992)
- Index - containment field
- An MS-DOS Virus - Overview and x82 assembly code to the author's "Mark II" MS-DOS .COM infecter virus, by The Paranoid Panda
- Code: mark-ii.asm
- An MS-DOS Virus Original
- L.A. Law - Collection of Los Angeles Police Dept. MDT messages
- Green Bay Employs Retarded Police (GERP)
- Illegal Activity by the Green Bay Police
- Green Bay Police Dept. - Internal Investigation #16-542I
- A Batch Virus - MS-DOS virus (.COM) using DEBUG and EDLIN and run from a BATCH file, by Frosty of the GCMS (Robert E. Jones, Long Beach, Mississippi)
- Virus Scanners Exposed - How virus scanners work and provides some insight into a few methods which could be used in a virus that current virus protection schemes wouldn't catch, by Dr. Delam (Pinellas Park, Florida)
- Hacking WWIV - Different techniques for hacking the WWIV BBS software package, by Inhuman
- The Complete Guide to Hacking WWIV Phrack, Issue #34
- Using a Silver Box - Access ACD debug features using the extended DTMF ("Silver Box") tones, by Mad Scientist
- How to Use Your Silver Box Original
- Fun Frequencies - U.S. Secret Service and Disney frequencies
- UNIX Password Hacker - An alternate approach to UNIX password cracking which hides your activity, by Keyboard Jockey
- Code: alternate.c
- How to Take Apart a Payphone - How to "take apart" a payphone using common tools, even if it's still attached to a wall, by The Monk
- Coin Crafts' Manual Bell System 325-099, Issue 2, August 1978
- Coin Service Manual Developed by New York Telephone
- Bell System Practices - Division 506 Coin Station Sets - Common Battery
- Letters - The Letters
- Caller ID Info - Rich
- POSTNET Questions - BB (Woodbridge, VA), LM (Berkeley, CA), Anonymous
- Info - MT (Baton Rogue, LA), Taran King (Randy Tishler), Dr. Delam, SGC (New Jersey)
- Searching for Answers - The H. (Los Angeles, CA)
- COCOT Updates - NB, Juan Valdez (Washington, D.C.), TELEgodzilla
- A Mag Strip Future - Mr. Upsetter
- Technological Marvels - Henry H. Lightcap (Seattle, Washington)
- Transmitter Bits - T^2 (Germany), BillSF (Amsterdam, Holland)
- Clarifications - Bill, Number 204 (Las Vegas, NV), DC (Loomis, CA)
- Why They're Watching - Dispater
- Breaking Into The Scene - The Information Junkie
- Questions - The Iron Warrior
- Outraged - P.O.
- The Australian Phone System - Overview of the phone system in Australia, by Midnight Caller
- A Way to Catch Peepers - C source code to log finger requests, by Alien X
- Code: peep.c
- Review: Steve Jackson's Hacker - Game review of Steve Jackson Games' Hacker: The Computer Crime Card Game
- Hacker Rules
- A Review of Steve Jackson Games' Hacker Phrack, Issue #39
- Looking for Simplex Locks? - Listing of universities, colleges, preparatory schools, and school organizations using Simplex push-button locks
- News Updates
- Big Brother
- International News
- New Technology
- Troublemakers
- Opportunists
- Observations
- Regulations
- Fascinating Fone Fun - Interesting 1-800 and 950 phone numbers (and code lengths), by Frosty of the GCMS
- 2600 Marketplace
- Price: $4.00
- Cover (Cover Info)
- Inside Cover Japanese Payphones
- Japan #1 A chronology of Japanese payphone culture. The "red public phone" is the oldest type of payphone. It only takes 10 yen coins and is rotary.
- Japan #2 The "yellow public phone" which takes 10 or 100 yen coins and is push button.
- Japan #3 The "green public phone" takes telephone cards as well as everything else.
- Japan #4 This public phone does everything and has a digital display as well.
- Staff
- Download Official Scanned PDF!
- Download The Hacker Digest - Volume 9!
$2600 Magazine - Volume 9, Number 2 (Summer 1992)
- Index - potential lawsuits
- On the Road Again: Portable Hacking - Really good article on tips for "portable hacking." The portable computers and equipment to use and even where to look for covert phone line access, by The Masked Avocado
- Hitchhiker's Guide to the Phone System: Phreaking in the Nineties - Modern phone systems and phreaking, by BillSF
- Demon Dialer Review - Review of the Hack-Tic Demon Dialer, the ultimate phone phreaker's tool, by The Devil's Advocate
- Bellcore's Plans for Caller ID - Caller ID technical information from Bellcore TA-NWT-000030
- Fun Things to Know - Various news bits
- Here We Go Again - More information about the Secret Service and "hacker" arrests, mostly the New York MOD
- Letters - Here They Are
- Trouble to Come - Maelstrom 517
- Enhanced Exaggerations - Danny (New York)
- Mag Strip Update - SE (Minnesota)
- Scanning Results - FD (Atlanta, GA), Name Withheld, David
- At Wit's End - CB (Colorado)
- crypt() Correction - SJ (California)
- Simplex Sightings - Albatross
- Wanted - Birdman (Tennesse)
- Monitoring Problems - Vid Kid (Minnesota)
- Cellular Frequencies - 6025 (Scotland)
- What the NSA Does - Someone (Somewhere)
- Prisoner News - PW (Washington)
- Mystery Calls - Sitting Duck
- The Prodigy Side - Steve Heln (White Plains, NY)
- How to Defeat *69 - Extensive list of tips and tricks to defeat the *69 automatic callback feature and Caller ID and other telephone privacy tips, by Bernie S.
- Bellcore Reponds to 2600 - Knowing Bellcore, they might just consider this proprietary. Such is life. Note the UNIX file path printed at the bottom of the letter. On some system somewhere, this letter exists... Our reply appears on the facing page. We'd like reader input on this.
- 2600 Responds to Bellcore - LOL
- The View of a Fed - Story from a government computer security man who vowed to understand hackers by becoming one, by The Fed
- Book Review: Devouring Fungus - Tales of the Computer Age - Book review of Karla Jenning's book The Devouring Fungus, by W. Ritchie Benedict
- Voice Mail Hacking - This might be the most complete text on hacking voice mailbox systems, by Night Ranger (G. Batson)
- Hacking Voice Mail Systems Phrack, Issue #34
- Compromising Voice Messaging Systems by Kingpin
- An Introduction to Octels Automatic Speech Exchange Network by Optik Nerve, Phrack, Issue #45
- 2600 Marketplace
- Price: $4.00
- Cover (Cover Info)
- Inside Cover Sad Payphones
- Los Angeles, California #1 They may not be foreign payphones but they look rather alien to us. These phones happened to be in the wrong place at the wrong time - namely, Los Angeles in the spring of 1992. Riots have never been kind to payphones. We can only imagine what the COCOTs looked like. Photos by Kuang, another 2600 contributor risking his life for the glory of Page 2
- Los Angeles, California #2 "
- Staff
- Download Official Scanned PDF!
- Download The Hacker Digest - Volume 9!
$2600 Magazine - Volume 9, Number 3 (Autumn 1992)
- Index - inner workings
- Hacking AmiExpress - Security holes under this popular Amiga BBS software and a way to grab passwords and display them in ASCII borders, by Swinging Man
- Code: steal.c
- The Top Ten Scams of 1991 - List from the Alliance Against Fraud in Telemartketing
- AT& Threat Letter - According to Minor Threat, this letter was received about a week after he had scanned about fifty 800 numbers in the 222 prefix sequentially by hand.
- Defeating Callback Verification - Example of some neat tricks to defeat BBS callback modem verification, by Dr. Delam
- Calling Card Fraud Claim SSN Scam - What a great scam to get Social Security numbers!
- Postage Stamps for COCOT Refunds - This is what happens when you request a refund from Phone Management Enterprises, Inc.
- Shopper's Guide to COCOTs - Guide to COCOT payphones, by Count Zero (John Lester)
- Shopper's Guide to COCOTs Original
- Film Review: Sneakers - Review of the movie Sneakers, by Evil Corley
- Sneakers Computer Press Kit This is beyond cool...
- Sneakers Commentary With director Phil Alden Robinson and director of photography John Lindley.
- NYNEX Telephone Service Allowance - People are always wondering whether or not telephone company employees get discounts on their phone bills
- A Simple Virus in C - Sample source code for a DOS-based overwriting virus that attacks all EXE files in the directories off the main C: directory, by Infiltrator
- Code: simple-virus.c
- Book Review: The Hacker Crackdown: Law and Disorder on the Electronic Frontier - Book review of Bruce Sterling's The Hacker Crackdown, by The Devil's Advocate
- China Fax Number Change Cartoon - In China, they don't add digits to their phone numbers at midnight, or 3 in the morning - they do it at 23:48!
- Letters - i/o
- Blue Box Questions - MD (Sheboygan, WI), Phrankenstein
- Assorted Comments - DC
- Sheer Frustration - T^2 (Germany)
- Mild Encryption - Danny (New York)
- Cable Hacking - Lawrence (New York, NY), Anonymous
- A Phone Mystery - The Psychedelic Sloth (Paul Bradley, Oregon)
- Info - Erreth Akbe/Energy!
- Many Questions - The Ronin (Pennsylvania), Clark Kent (Ames, IA)
- An Opinion - TC (Blauvelt, NY)
- The Facts on ACD - Kingpin (Brookline, MA)
- Cellular Mystery - MM (Nova Scotia, Canada)
- Call For Data - The Azure Mage
- Call For Info - JS (Philadelphia, PA)
- Call For Help - TB (New Jersey)
- A Choke Tip - The Prophet
- Mail Problems - RD (Austin, TX)
- Comments From Abroad - EL (Faulconbridge, Australia), DF (Milan, Italy)
- BBS Update - Guy Nohrenberg (Canoga Park, CA)
- Voice Mail Question - Puzzled
- Hacking on the Front Line - Good article on early-1990s computer hacking, by Al Capone
- How to Use the Dial Telephone - New York Telephone document on how to properly dial a phone
- Meridian Mail Mailbox Defaults - Computer hackers at the CFP conference in Washington, D.C. this spring found it astoundingly easy to get into guests' mailbox. All you need is a name and a room number! We wonder how many other hotels are so trusting
- Getting Started - Getting started in hacking and phreaking is not like what the TV told you, by Phord Prefect
- Toll Fraud: What the Big Boys Are Nervous About - Overview of the Toll Fraud Prevention Committee (TFPC), by Count Zero
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Cover (Cover Info)
- Inside Cover East German Phones
- East Germany The translation is "Doesn't Work, Doesn"t Exist." Taken from a postcard and submitted by Katie Hafner
- Staff
- Download Official Scanned PDF! (Text Version)
- Download The Hacker Digest - Volume 9!
$2600 Magazine - Volume 9, Number 4 (Winter 1992-1993)
- Index - offerings
- Hackers in a World of Malls - Information on the Pentagon City Mall 2600 meeting being busted up by the Secret Service
- Cipher Fun - A simple telephone number encipherment designed to protect your private information when published in public telephone directories, by Peter Rabbit
- Beginner's Guide to Minitel - Some info on the French Minitel network, by NeurAlien (Philippe Langlois, France)
- Vehicle Identification Numbers - A look at 17-character VINs and their format and check digits
- U.S. Secret Service Field Offices - List of Secret Service Field Offices (domestic and overseas) and their contact phone numbers, by GCMS MechWariors
- Letter From Prison - Letter from a hacker in a California prison and his story of brute-forcing Sprint card codes
- PTI Model 60 Prison Phone - Sales brochure from Palco Telecom Inc.
- Growth of a Low-Tech Hacker - Update to the "Birth of a Low-Tech Hacker" article for newbie hackers looking for place to start, by The Roving Eye
- High-Tech Happenings
- The Hacker "Threat"
- Foul-Ups and Blunders
- Advances in Technology
- Abuse of Power
- Numbers
- Free "800" Number Ad - This ad was found in a truck stop. The rates may be slightly higher than other companies but not having a monthly fee may offset this.
- Letters - feedback
- Federal Issues - Albatross
- Credit Problems - D (Nederland, TX), BR (Hamilton, Ontario), Pacoid
- What a Surprise - JL (Tampa, FL)
- More Simplex Shenanigans - Cray-Z Phreaker
- In Defense of the Demon Dialer - Hack-Tic
- Slow Learners - Dan
- Data - Sarlo (Chicago, IL), Tremoto, Happy Reader and Reporter, MA (Baton Rouge, LA), Digital Bear (Canada), Naddy (Germany), Sp00f
- Scanner Observations - Anon.
- Where is TAP? - IRC (Torrance, CA)
- Book References - WT (Santa Barbara, CA)
- VMS Fun - Alien Hacker
- Answering Machine Hacking - SPaDe (Montebello, CA)
- A Request - The Har (Denver, CO)
- Bellcore Threats - Valis (West Orange, NJ)
- Caller ID Hoodwinking - Gabriel
- Hardware Lock Info Needed - The Pizza Maker Hacker
- Japanese Phone Tricks - Japanese Subscriber
- Assorted Info - Scott (Buena Park, CA)
- 2600 Meeting Adventures - Techno Caster
- Answers - Scott R. (Huntsville, Alabama)
- Toll Fraud of the Past - An official Southern Bell document "The Investigation and Prosecution of Electronic Toll Fraud Cases" on Blue Boxing and other forms of toll fraud.
- AT&T Eastern Area Directory - Part 1 - Is AT&T hiding near you? List of AT&T offices and switching stations covering Connecticut, Delaware, D.C., Maryland, Maine, Massachusetts, New Jersey, and New Hampshire
- NYNEX Threat Letter - NYNEX had the nerve to send this loyal customer a semi-warning letter a full half month before the bill was even due!
- 900# Phone Scam - Scam advertisement from "Lucifer Green" with a contact phone number which charges $69 per call!
- Telco News - Southwestern Bell computers and dial-ups
- Product Review: Speech Thing - Review of a Convox Speech Thing add-on voice module, by Cray-Z Phreaker
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Cover (Cover Info)
- Inside Cover Norwegian Payphones
- Norway #1 Three different types of Norwegian payphones. Note the strange positioning of the numbers on the keypad. Photo by JR of New York
- Norway #2 This mobile payphone was spotted on a tour bus. Photo by JR of New York
- Norway #3 Photo by JR of New York
- Staff
- Download Official Scanned PDF!
- Download The Hacker Digest - Volume 9!
$2600 Magazine - Volume 10, Number 1 (Spring 1993)
- Index - program
- Cellular Magic - Detailed cellular phone system overview, by Bootleg (Michael Beketic, Portland, Oregon)
- Cellular Secrets Original
- Cellular Magic
- Trouble in the White House - Story of White House phone system trouble, by Charlie Zee
- Beige Box Construction - How to build a Beige Box which is a little more complex than others as it includes a proper "Talk/Monitor" selection mode and line polarity tester, by The Phoenix
- Descrambling Cable - A look at cable scrambling and the infamous RadioShack descrambler which dates back to 1988, by Dr. Clayton Phorester
- Secret Service on Trial - Court report and overview from the Steve Jackson Games v. Secret Service trial, by Paco Xander Nathan
- Steve Jackson Games Wins Lawsuit Against U.S. Secret Service
- 20th Anniversity of the Steve Jackson Games Raid EFF Austin
- One Angry Judge - One man's Steve Jackson Games trial perspective and how Judge Sparks turned against the Secret Service, by Scott Skinner
- Letters - LETTERS OF MERIT
- Cordless Questions - Happy Reader (North Dakota)
- Bypassing Restrictions - Major Tom (Ari Braginsky, Champaign, IL)
- More Simplex Stories - A Fly on the Wall, Pez (Lafayette, LA)
- Mysteries - Annom, DG (U.K.), Maelstrom 517
- Hacking Passwords - MR
- That Bell Computer - layden02, The Road Warrior
- Correction - CA
- Info - CL (Holmdel, NJ), JR (Kingsburg, CA), The Tick (Arizona), Avalar, Ken, Misha, Mr. Upsetter
- Red Box Questions - Frustrated in Berkeley
- Data in the Air - The Winged Plecenta (Oregon)
- Questions - JG, TW (Binghamton), MJ (Massachusetts), SB (Massachusetts), Freaked-out Feyodor, AB (New York), JL (Shoreham, New York), Brendog
- Fixing Your Credit - DC Credit
- Surprising Facts - JM
- Spanish Connection - GMV (Motril-Granada, Spain)
- BBS Info - JCB (Concord, North Carolina)
- Evil Payphones - Inhuman (Arlington, VA)
- Access to 2600 - The Apple II Evangelist (Jane Lee, Palos Verdes, CA)
- Rolling Stone Corrections - TELEgodzilla!
- Special Phone - TL (Tempe, AZ)
- Seeking Virus BBSes - YFNH (Your Friendly Neighborhood Hacker)
- Acronyms - Acronyms list A-G, by Echo
- A Study of Hackers - Article about hackers and setting up a honeypot, by Dr. Williams
- Getting Your File... - Contact information for getting ahold of your FBI or credit report files, by Bayonet
- Lawsuit Filed Against Secret Service - Legal action taken on behalf of the Washington, D.C. 2600 meeting incident.
- 2600 Robbed of Touch-Tones - New York Telephone surcharge for using Touch-Tones!
- British News - Various bits of technical news information from Britain, by The Dark Knight (John Abercrombie?)
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Cover (Cover Info)
- Inside Cover European Payphones
- Budapest, Hungary Photo by Kishon
- Saizburg, Austria Photo by Kishon
- Munich, Germany With emergency call handle - left for fire, right for police. Photo by Kishon
- Sofia, Bulgaria #1 "Out of Order" written above dialer. Photo by Kishon
- Sofia, Bulgaria #2 "Out of Order" strongly implied. Photo by Kishon
- Staff
- Download Official Scanned Edition PDF!
- Download The Hacker Digest - Volume 10!
$2600 Magazine - Volume 10, Number 2 (Summer 1993)
- Index - inward
- A Guide to the 5ESS - Very detailed guide to the Lucent #5 ESS, by Crisp G.R.A.S.P.
- A Guide to the 5ESS Phrack, Issue #43
- Bell System Practicies - Division 235
- British Credit Holes - Potential credit card security holes and ways to bypass the "Data Protection Act", by Anonymous (England, U.K.)
- High School Hacking - A look at the author's high school's PS/2 computer network and how he found a few security holes, by The 999
- Product Review - Review of the MoTron TDD-8 DTMF Decoder, by Les Inconnu (Sydney, Australia)
- MoTron Touch-Tone Decoder Review Monitoring Times, March 1992
- Meeting Advice - Tips to setup a $2600 meeting and how to protect them from disruption from outsiders, by Parity Check and Romula Velcro
- More Acronyms - Acronyms list H-R, by Echo
- Letters - Printable Letters
- Mall Fallout - The Knight of Ni (New Jersey), Knight Klone (Atlanta, GA)
- Beginner Questions - JC (Canada), Dial Tone (Nevada City, CA)
- Defeating Hardware Locks - The Public, Arclight (Fullerton, CA)
- Telco Fascists - NA (Sacramento, CA), M
- Info - John Wesley Harding (New Jersey), Frion Man (Los Angeles, CA), Static (Washington), Mouse Balls, MW (Ohio), Martian, Clovis
- Freedom of the Press - Mike
- Equal Access? - userid@temple
- Help Needed - Reuben (New York, NY)
- Cable Potential - Master Quickly
- On Beige Boxing - Andrew Sharaf (Brooklyn, NY)
- Unlisted Directories - SDW (Fort Lauderdale, FL)
- Callback Defeat - MJ (California)
- Another Way to Fix Credit - ES (Hollywood, CA)
- Another Simplex Story - The Flea (Lexington, KY)
- Red Box Tones - PB (Deerfield, MA)
- Female Hackers - A-Gal (Florida)
- COCOT Question - DW (Providence, RI)
- New York's 890 Exchange - The Sheperd (Brooklyn, NY)
- The Best ANAC - Non-Stop Phone Phreak
- A Special Request - Matthew (Los Angeles, CA)
- Corporate Speak - AT&T sends 2600 a letter complaining about printing their Eastern Area Directory.
- AT&T Eastern Area Directory - Part 2 - Additional addresses to various AT&T offices and switching stations covering New York, Pennsylvania, Puerto Rico, Rhode Island, Vermont, Virginia, and West Virginia
- Government Bulletin Boards - List of government and military BBSes available to the public
- Assorted Videos from Commonwealth Films - A review of Commonwealth Films corporate-oriented videos on software piracy, by Evil Corley
- Toll Fraud Device - Surprisingly high-quality Red Box device using a Texas Instruments TCM5089 tone encoder IC and a TTL counter.
- Toll Fraud Device by Rock Steady
- Tales of the Oldhat: Johnny's First Red Box
- ANSI Bomb - A look at the operation of "ANSI bombs" and how to create and install one on a target, by Mister Galaxy (Patrick Harvey, Atlanta, Georgia, BBS Documentary)
- News Update - Steve Jackson declared innocent!
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Cover (Cover Info)
- Inside Cover Worldwide Payphones
- Barcelona, Spain A "green goblin" that takes coins and cards. Photo by Drew Lehman
- Medellin, Colombia Photo by Anonymous
- India Photo by David Johnson
- Poland Photo by Brad Dolan
- Staff
- Download Official Scanned Edition PDF!
- Download The Hacker Digest - Volume 10!
$2600 Magazine - Volume 10, Number 3 (Autumn 1993)
- Hacking at the End of the Universe - Editorial
- HEU Press Release Hack-Tic Presents: 1993 Summer Congress, The Netherlands
- Index - main attractions
- The Wheel Cipher - A look at history and operation of Thomas Jefferson's wheel cipher, by Peter Rabbit
- True Colors - Detailed technical overview of the various phone phreak "color" boxes, by BillSF
- Caller ID Technicalities - Technical information on Caller ID, by Hyperborean Menace
- Caller ID Technical Details by Hyperborean Menace, Phrack, Issue #45
- Congress Takes a Holiday - Evil Corley testifies before Congress
- Hacker Testimony to House Subcommittee Largely Unheard Computer Underground Digest 5.4
- UNIX Job Openings - UNIX hacking/Trojan horse tip using a shell script whichs creates creates a SUID shell of the target, by Orb (Norman Richards)
- Meeting Mania - More November 1992 Washington, D.C. 2600 meeting info and Secret Service FOIA documents
- Never Erase the Past - Review of LOD's Hack/Phreak BBS Message Base Project, by Evil Corley
- The LOD Communications Underground H/P BBS Message Base Project From Phrack, Issue #44
- Hacking Honesty Tests - Written honesty and integrity tests are easy to beat once you understand the underlying principles, the manner in which the tests are constructed, and the mind set necessary to undergo the test, by U.R. Source
- Letters - NEVER BEFORE PRINTED LETTERS
- Foreign Charge Phones - Clovis
- Hacker Info - Crewcut
- Reading List - The Theoretician (Dana Beal)
- Telco Ripoffs - Sp00f!
- Seen the Light - A New Reader in Las Vegas
- Hacking An Intercom - The H. (Los Angeles, CA)
- AT&T Irony - PB at UT
- Locked Out - AH (Texas)
- New Long-Distance Services - Bill Bossiere, Telemanagement Systems of America (New Orleans, LA)
- Evil Engineers - Almost Anonymous
- Los Angeles Numbers - Red Wizard, (none given, Santa Ana, CA)
- Governmental Mystery - Baked Alaska
- Numbers - Boredom Prevails (Richmond)
- Cellular Mystery - ED (San Francisco, CA)
- Disney Details - IT (San Diego, CA)
- Are We Neglecting IBM? - KR (Little Rock, Arkansas)
- Lack of Understanding - Captain Poison (Puerto Rico), Tech
- Review Update - Les Inconnu (Sydney, Australia)
- High School Hacking - The Noid (Jason Chilton), Soylent Green, Haghard
- Telco UNIX Trap - A Maryland Hacker
- Bookstore Trouble - trader, J
- Rumor Quelling - Sue
- Problem Solving - LL, Saladin
- Cellular Criticism - Mark Uber
- Product Review - A look at AccessData's Recovery password cracking software for Word, WordPerfect, Lotus 1-2-3, Excel, Novell NetWare, etc., by Hakim
- Changing Your Grades on a High School Computer - A look at hacking a school using the Pupil Attendance and Records System (PARS), by Drewl/Salivate (A. Shafer)
- Overview of DSS1 - Review of ISDN Digital Subscriber Signaling System 1, by Cruise-CTRL
- Book Review: Approaching Zero: The Extraordinary Underworld of Hackers, Phreakers, Virus Writers, and Keyboard Criminals - Book review of Paul Mungo's Approaching Zero, by Stephen J. Resz
- Approaching Zero Anna's Archive (PDF)
- Approaching Zero Text version
- Protecting Your Virus from Evil Detectors - Short piece of assembly code to add to your viral code to "encrypt" the virus until run time, by Dr. Bloodmoney
- More Cellular Fun - An update to the "Cellular Magic" article with an emphasis on the ESN and NAM PROM data and location, by Judas Gerard
- The Last of the Acronym List - Acronyms list S-X (no Y or Z), by Echo
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Cover (Cover Info)
- Inside Cover Payphones of Eastern Europe
- Saint Petersburg, Russia Photo by Subscriber 6029
- Tallin, Estonia Photo by Subscriber 6029
- Kraków, Poland Photo by Hanneke
- Staff
- Download Official Scanned Edition PDF!
- Download The Hacker Digest - Volume 10!
$2600 Magazine - Volume 10, Number 4 (Winter 1993-1994)
- Hackers in Jail, Part Two - Editorial
- Index - on-ramp
- Cellular Phone Biopsy - Detailed look at what is contained (or hackable) in a cellular phone's EPROM memory, by Kingpin (Joe Grand)
- Elementary Switching - A basic overview of the tones/pulses used in telephone supervision signaling and dialing, by 910
- Know Your Switch - Tricks to listen for to determine the type of telco switch (ESS, DMS) you are on or calling, by Rebel
- Hacking Smartphone - A look at a New York-area desktop Smartphone and some of the ISDN services it provides, by Tech Rat
- They Can Never Win - Warning letter to Ohio Bell employees telling them not to copy or trade confidential information
- Cool Letter Department - LOL warning letter sent to Minor Threat telling him not to access the Sheriff's computer system.
- High School Mac Hack - Tricks for collecting AppleShare passwords by tricking the user logging in, by The Bard
- Hacking Computer Shows - Tips and tricks for jewing your way into computer shows for free, and even getting free software, by Walter S. Jaffee
- NYNEX Voice Mail - Voice mail phone numbers for various New York City-based NYNEX central offices
- The Magical Tone Box - Overview of using an ISD1000A digital voice recorder IC to create a Red Box or Blue Box, by FyberLyte
- ISD1000A Datasheet
- QUARTER.VOC
- QUARTER.WAV
- BlueBEEP v0.10 (Manual)
- Simple Simplex Repeater Also uses the ISD1000A.
- The FOXBOX A voice ID transmitter hunt controller.
- Letters - LETTERS TO REMEMBER
- Fun Telco Numbers - Beetle Bailey (Arcadia, CA), MacGyver (Clearwater, FL), Uncle Waldo
- Hacking Traffic Lights - Lone Wolf (Atlanta, GA)
- Past Hacker Prime? - Darkhold Page (Pittsburgh, PA)
- Info and Questions - Whistler, Will Chung (San Luis Obispo, CA), Pipo Communications (Pollack Pines, CA)
- Potential Discovery - Maldoror (Florida)
- Security Concerns - Radiation X (California), Bleed The Freak
- Starting a Meeting - Johnny "The Quarter" Burpo (New York)
- Questions - M (Great Neck, New York), DY (Weston Ontario), Owen (Halifax, U.K.)
- Why Hack Cable? - A-$tring (Lenexa, Kansas)
- How to Learn About Your CO - Hook (Belmont, MA)
- Observations - The Lung (California)
- New Technology - Julian (Cleveland, OH)
- Modem Backdoor - Antoch
- Foreign Payphone Flash - LN
- How to Really Abuse a Payphone - Peter (Manchaca, TX)
- Technology Moves Backwards - Martin
- Corrections - Jeff, King of Birds (Chapel Hill, CA)
- Red Box Concerns - Anoon, Nexus, Concerned
- How Easy It Is - CopKiller (Bethesda, MD), Erreth Akbe
- Bypassing Restrictions - Lost and regulated in NB, Canada
- A Way Around Caller ID? - Levendis (Deron Staffen)
- School Phone System - lexis
- 2600 Wins Over Class - BG (Georgetown, TX)
- The Honesty Test - The Vampire Gabrielle
- Passageways to the Internet - List of public Internet dial-ups provided by various colleges
- More Meeting Advice - 2600 meeting advice and how to fight back if the government tries to prevent you from attending one, by The Judicator of D.C.
- Book Review: Virtual Reality - Review of Howard Rheingold's Virtual Reality, by W. Ritchie Benedict
- Digital Locks - List of the 1287 possible combinations for Digital-brand combination locks
- News Roundup
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Cover (Cover Info)
- Inside Cover Indian and African Payphones
- India #1 Complete with goat. Photos by Synthetic Man
- India #2 "
- Voi, Kenya Photo by Friend of Daniel Jones
- Kampala, Uganda A row of international phones in Kampala, Uganda. Photo by Friend of Daniel Jones
- Zagora, Southern Morocco Photo by Drew Lehman
- Staff
- Download Official Scanned Edition PDF!
- Download The Hacker Digest - Volume 10!
$2600 Magazine - Volume 11, Number 1 (Spring 1994)
- Crime Waves - Editorial
- Index - documentation
- Build a DTMF Decoder - Build a DTMF decoder using a hardware Teltone 8870 DTMF receiver and interfacing coding for a Commodore 64/VIC-20, by Xam Killroy
- The NYNEX Change Cards - Info on NYNEX coin-operated telephone "Change Cards," by Kevin Daniel
- BT Fonecards by NeonDreamer
- How to Hack Health - How to hack StairMaster 4000 aerobic equipment, by MuscleHead
- Software Piracy - Another View - Another viewpoint on the ethics of software piracy, by Roberto Verzola
- Coping With Cable Denial #1 - Brief inforation on various cable TV scrambling systems, specifically "trap" type systems, by Cap'n Dave
- Cellular Telephone Experimenters Kit Review - Review of Mark Lottor's CTEK for the Oki 900 cell phone, by Mr. Upsetter
- FOIA Facts and Fiction - How to use the Freedom of Information Act (FOIA), by GateDancer and Shrike
- Letters - Letterbox
- Comments - Big Wind
- Hacker Understanding - Scudder
- Novell Nosing - Digital Enigma (Cottonwood, CA)
- NYNEX Negativity - Happy in 212 Land
- Reader Abuse - Guy At The Desk (Ty Osborn, The Office BBS)
- Questions - BO (Cortlandt Manor, NY), Leroy Chism, Randy Ramone
- The Dark Side - Pissed-Off In Houston
- The Far Side - One very displeased former subscriber
- Payphone Fun - Neophyte1138 (Ohio), Tim (San Diego, CA), TcP, Death Adder
- Quarter Variations - Kingpin
- Prison Phone Project - Wag
- Government Data - AO (Arizona)
- Cellular Chatter - Tech-No Wiz (Columbus, OH)
- More Corporate Outrage - James F. Walker (Loveland, CO)
- Individual Outrage - Richard Finch (Glendale, AZ, U.S. National Crime BBS, 602-846-4470)
- Exiled Hacker - Ares (Hacker's Hospice)
- Pointers - Trout (William S. Gillingham)
- Fighting Back - BellSouth Baboon (Atlanta, GA, Reply)
- Governmental Suggestions - Randy815 (Dallas, TX)
- Phiber Parallel - Racer X
- Correction - Aleph One (Elias Levy)
- Phone Company Charges - David
- Blue Boxing Revisited - A CCITT System #5 Interpretation - Blue Boxing under CCITT #5 and the basics of that type of signaling, by Kevin Crow
- A Gift From Hallmark - Building a Red Box using the internal electronics of a Hallmark Talking Greeting Card, by Bernie S.
- 10XXX - A look at 10XXX Primary Interexchange Carrier (PIC) carrier access codes, by The Prophet (Babu Mengelepouti, Seattle, Washington)
- Long Distance Carrier Code Assignments FCC, June 1997
- Not Much Good News Here - Laws on "phone hackers" and seizing their equipment, Clipper Chip info
- Congressional Testimony of Emmanuel Goldstein June 9, 1993
- Michigan Access - MSUnet and MichNet dial-up access numbers, by Tonto of 517
- Merit/MichNet Hacking Issue From Vaginal and Anal Secretions Newsletter, Issue #0015
- New Dial-Up Service Numbers for Michigan State University
- Book Reviews: Secrets of a Super Hacker and UNIX Security: A Practical Tutorial - Reviews of The Knightmare's (Dennis Fiery) book Secrets of a Super Hacker and Derek Arnold's UNIX Security: A Practical Tutorial, by Michael E. Marotta and Simson L. Garfinkel
- Trojans in the U.K. - Story of installing a login-grabbing Trojan horse in college environment, by Veghead
- The Chrome Box - Box to active the 3M Opticom traffic control systems, by Remote Control
- A Portable Self-Contained Device to Manipulate Traffic Signals Original
- Traffic Light Changer
- 3M Opticom GPS Priority Control System Installation Instructions
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Issue's Cash Cow: Harassing old ladies is hacking, or it isn't... I can't figure it out.
- Cover (Cover Info)
- Inside Cover Payphones of Argentina
- Argentina #1 Argentina has two phone companies: Telefónica in the south and Telecom Argentina in the north. Buenos Aires is divided between the two. Both companies use the same tokens but their cards aren't compatible. See if you can guess which phones belong to which companies. See if you can guess which one we're not sure about. Photos by Edward Stoever
- Argentina #2 "
- Argentina #3 "
- Argentina #4 "
- Argentina #5 "
- Staff
- Download Unofficial Scanned PDF!
- Download The Hacker Digest - Volume 11!
$2600 Magazine - Volume 11, Number 2 (Summer 1994)
- Hackers on Planet Earth - Editorial introducing the first HOPE conference
- Index - nutritional information
- Life Under GTD-5 - Detailed info on a GTD-5 under GTE, also has info on the Proctor Test Set, by Zaphraud (Jason Kennerly, San Jose, California)
- The Joys of Voice Mail - Info on hacking voice mail systems and password guessing, including a prank at a college, by snes
- Foiling the Finger Command - Overview of some of potentially sensitive information Finger can reveal and how to "backfinger" a person, by Packet Rat (Tim Russo)
- Code: backfinger.sh
- USENET Posting by Packet Rat
- Playing With Your Fingers - Some other techniques you can use to "backfinger" users, by Shidoshi
- Cordless Fun - How to listen to 49 MHz analog cordless phones, by Noam Chomski (New York Metropolitan Phreak Hack Organization [NYMPHO])
- Legal and Technical Aspects of RF Monitoring Major [TNo]
- Admins Without a Clue - Collection of quotes and "famous last words" from various admins regarding the security of their systems and networks, by Kevin Crow
- Hacking Prodigy - Clever little hack using DOS DEBUG to grab active Prodigy passwords from demonstration computers, by DeVillage Fool
- Hacking Prodigy by The Dark Lord, Hackers Unlimited, Issue #2
- Hacking the Small Stuff - A look at "simple hacks" to ATMs, calculators, vending machines, etc. to improve your hacker skills, by Leonardo Branson
- Letters - LETTERS TO READ BY
- A Busy Connection - Reuben (New York, NY)
- Touch-Tone Tall Tales - Power Spike
- Improving Grades - Brian, Black Night (Ohio)
- Regression - Fred
- Car Tracking - Tommy B.
- How to be Honest - V.A. Szell (Seattle, Washington)
- High School Notes - VicProphit, Number 6 (Bellevue, Washington), Deus/The Black Night/Silver Dragon/Pixel Threat/Zippy the WaterGod/The Unnamed One
- Fighting Traffic - flip (Ohio)
- Become Your Own Admin - Toaster (Narragansett, Rhode Island), Primitive Morales (Processed World)
- Passing Numbers - Ethan (Stanford), DD (Somerset, MA), Diashi (New York)
- Red Box Rumors - The Borg (Cleveland, OH)
- Those Three Tones - Empress
- Cellular Mystery - JV (Reston, VA)
- Thoughts On Congress - Gregg Giles (Oregon), John
- Defending the 64 - Commodore Hacker
- Tyranny in Church - The Roadkill
- Availability - Hermit the Herman (David Johnson), sciri
- Secrecy - Somewhere in Kansas
- Seen the Light - An isolated feeling guy in Portland, Oregon
- IBM Hacking - Powercell (Hartford, CT)
- Long Arm of the Secret Service - Juan Valdez (Cambridge, MA)
- Call Forwarding Tricks - CM (Attlehoro, MA), LN (Minneapolis, MN)
- Prodigy Savings - George
- Hungry For Knowledge - Emory T. Suchau
- Fighting the Slime - RG (Los Angeles, CA)
- Secrets of a Super Hacker - JB (Habay-La-Nevue, Belgium)
- Thoughts - PB (Wayland, MA)
- DTMF Decoder - Very detailed article on the hardware/software for building a computer-controlled (C64/V20) DTMF decoder, by Paul Bergsman (Merion Station, Pennsylvania,, N3PSO)
- Code: DTMF2PRN.BAS
- Build a DTMF Decoder
- Hackers On Planet Earth (1994): Control the World with Your PC
- Controlling The World with Your PC by Paul Bergsman
- Monitoring Keystrokes - Overview of the author's Delam's Elite Password Leecher DOS-based keystroke recorder, by Dr. Delam
- Facts - News Items
- How Corporate Leaks are Detected - How governments or corporatations detect leaks and restrict data, including alterations to documents to determine the leaker, by Parity Check
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Issue's Cash Cow: HOPE
- Cover (Cover Info)
- Inside Cover
- Germany A set of German phone booths. Note the incredible size of the handicapped booth. Photo by Frion Man.
- Mexico Mexico. Public card reader payphone in Tijuana. Photo by Daniel Hank.
- Aruba Another card-only payphone. Photo by YETI.
- Ecuador This phone on the Galápagos Islands is the reddest we've ever seen. A true red box. Photo by BLUBXR.
- Staff
- Download Unofficial Scanned PDF!
- Download The Hacker Digest - Volume 11!
$2600 Magazine - Volume 11, Number 3 (Autumn 1994)
- Opening Doors - Editorial
- Index - internal contents
- Monitoring U.S. Mail - A look at the POSTNET barcode which is being printed on U.S. mail, by Paranoia
- Corporate Foul-Ups - Memos on computer errors from Chemical Bank and MCI.
- The Irish Telephone System - General technical overview of the telephone system in Ireland, by Wonko the Inane
- Want to Play R.O.M.B? - Cool anti-toll fraud poster which was hung at colleges in the 1970s.
- The Ghost Board - A look at "pop-up" or hidden bulletin board systems which appeared during the 1980s, by Autolycus
- Hacking NetCash - An overview of Bob Houston's groundbreaking NetCash "digital money" system, by Palindrome
- Welcome to MEL - Detailed overview of using Southwestern Bell Mechanized Employee Locator (MEL) phone system, by EighT BaLL
- Generating an ESN - How a cellular phone's ESN is generated based on its assigned serial number, by Maldoror
- The Ten Dollar Red Box - Instructions for turning a "talking" Hallmark card into a working Red Box, by Toxic Avenger (Jeff Burchell)
- NYNEX Memo - Internal NYNEX memo reminding employees not to violate the public trust.
- How to Listen In - Very detailed overview of common audio surveillance hardware and techniques, by Q (Alan Hoffman)
- The World of Surveillance Reprint of Full Disclosure article
- Surveillance Equipment Buys Reprint of Full Disclosure article
- What's New in Surveillance Reprint of Full Disclosure article
- Suveillance Conference Overview Reprint of Full Disclosure article
- Electronic Surveillance Statistics Reprint of Full Disclosure article
- Letters - vocals
- Worrisome Questions - Susan
- Defeating Call Return - Emperor (San Francisco, CA)
- Info - Quinton McHale (Seneca, IL), WW (Austin, TX), Norm D'Plume
- More Questions - (none given)
- Privacy Violation - Anonymous
- Meetings - Frank (Kansas City, MO)
- Reader Reunion - Mike (Chicago, IL)
- A Strange Number - John Q Public, Zappy (Atlanta, GA), Mr. Asshole (San Francisco, CA)
- Inside Info - King of Spam
- Strange Situation - Marcus
- Replies to Readers - Da Phigzter (PHiGAN/6o2), .gKo. (DTMF: AB67)
- Cordless Clarification - Gladshiem
- Mac Hacks - Xausii, Space Rogue (617) (Christopher Thompson, Lowell, MA)
- Sick ATMs - (none given, London)
- Lowdown on Lojack - CARTWHEEL
- Still More Questions - Clear Plastic Raincoat from Seattle
- On Piracy - SM (Morgan Hills, CA)
- On Honesty - A.R. Weeks (New York, NY)
- Northern Hacking - DrP (Medicine Hat, Alberta)
- Satellite Mystery - Alcatraz (Pt. Pleasant Beach, NJ)
- Red Light Cameras - An Unprintable Symbol (California)
- Security Concerns - lexis
- Security Lapses - Colostomy Bagboy (Paskell "Geno" Paris, Washington)
- Contradictions - Problem Child (Las Vegas, NV)
- Hacker Sites? - Roger Harrison (Long Island, NY)
- Help Needed - Lady Penelope (London, England)
- Living on the Front Line - Internet postings regarding hacking attacks at a2i Communications and Netcom.
- News Items
- Breaking Windows - Simple trick for bypassing Windows 3.x screensavers, by The Camelback Juggler
- Internet World Guide - List of the two-letter Internet domains into countries
- Software Review - A look at the Supervisor Series for VMS, by Floyd Lloyd
- Supervisor Series v5.4d Also includes PHOTO. (June 1994)
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Issue's Cash Cow: HOPE
- Cover (Cover Info)
- Back Cover
- New Zealand An "old model" coin telephone. Photo by Kingpin
- Myanmar Another "non-modern" model in Yangon. Photo by Julie Alperin
- Italy This phone in Rome does everything. Photo by Davide D'Angelantonio.
- Thailand In a town called Phuket. Really. Photo by Chas Dye.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 11!
$2600 Magazine - Volume 11, Number 4 (Winter 1994-1995)
- Inspiration - Editorial
- Index - the guide
- Bypassing Protec - How to defeat Bo Krohn's Protec software copying protection program, includes a Turbo Pascal boot sector copying program, by Michael Wilson
- boot-saver.pas Boot Saver 1.0. Save a boot sector to a 512 byte file.
- Rejection - Rejection letter as the result of sending an issue of 2600 to Phiber Optik when he was in prison.
- More Key Capturing - Trick for hacking root on a local AIX machine and several tips for capturing keystrokes and passwords on various operating systems, by Code-Cafe (Sydney, Australia)
- Digital Telephony Passes - Information on the passing of the CALEA Digital Telephony Bill, by Anonymous
- Communications Assistance for Law Enforcement Act 103rd Congress H. R. 4922
- AskCALEA Mirror of askcalea.fbi.gov
- The Risks of WarDialing - Some potential legal problems you may run into while wardialing, by Dr. Delam
- Cellular Hardware & Electronics - Detailed information on cellular phone PROMs/EPROMs and the data they hold, by Kingpin
- News From the Far Side of the Planet - General overview and information on Australia's cellular system and telco interlinks, by Les Inconnu
- Letters - RIGHT LETTERS
- Missing The Point - Deeply Shrouded & Quiet
- Handy Tip - DMG (Cherry Hill, NJ)
- Problem - Harlequin
- HOPE Memories - Dave (Hofstra)
- Scantron Tricks - Jonathan
- Schematic Problems - The Camelback Juggler
- Fun With Sound - AK47/[GZ] (Arkansas)
- A Little History - Fart Wino
- Ottawa Fun Phone Facts - The Bishop (Ottawa, Canada)
- Wanted - Geert (Rochester, New York), Spartacus
- Info - FP (Long Island, New York), Atticus, BW, Paul (New Jersey), Morning Wood
- Mystery Number - Bruce
- Questions - Anonymous
- MetroCard Update - Red Balaclava (Jeopardy Jim)
- Highway Strangeness - Son of Holocaust Survivor Redhead
- More Hacker Persecution - Mr. Hallmark (Rochester, New York), Majic (Maryland)
- 800-433-3210 Update - Presto
- Payphone Tribulation - Weasel
- More Window Tricks - Brother Orbis
- More Mac Tricks - Mr. Blackhood
- Followup - John Q Public
- True Hacker Spirit - JL (Highland, CA)
- More On Honesty - U.R. Source
- Help Needed - Dr. X
- Hacker Graffiti - JV (New York)
- Take Responsibility - Brad Peebles (North Palm Beach, FL)
- Phone Boxes - Cat in the Hat (Warner Robins, GA)
- Inexcusable - Particle Man (Arlington, VA)
- International Tale of Woe - Fabian (Long Island, NY)
- Cable Affirmation - James S. Allen (Office of Cable Theft)
- VT Hacking - DEC VT100/200/220-series computer (dumb) terminal information and login spoofer/password grabber, by Mr. Bungle
- hook.c For DEC VMS only.
- Janitor Privileges - The potential for unseen security problems when hiring outside janitors, by Voyager (Will Spencer)
- Net Surfing Techniques - Tricks for surfing the Internet by using hostname look-up tools, by Sonic Life
- News Items - 2600.com is started
- Hack-Tic, Techno-Anarchist Magazine (1989 -1994) - Announcing the end of the printed version of Hack-Tic, by Rop Gonggrijp
- Reviews: Network Security, Information Warfare, and Unauthorized Access - Review of Steven Shaffer's book Network Security, and Winn Schwartau's book Information Warfare, and the video Unauthorized Access by Annaliza Savage
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Issue's Cash Cow: We need Internet freedom - except for people who $2600 doesn't like.
- Cover (Cover Info)
- Back Cover Old-Style Foreign Payphones
- Tanzania From the streets of Zanzibar. Photo by Hamilton Davis.
- Romania Still operating in Bucharest. Photo by T. Mele.
- Bulgaria #1 Note the vulnerable cords. Photo by T. Mele.
- Bulgaria #2 Space age. Both phones located in Sofia, Bulgaria. Photo by T. Mele.
- Staff
- Download Unofficial Scanned PDF!
- Download The Hacker Digest - Volume 11!
$2600 Magazine - Volume 12, Number 1 (Spring 1995)
- The World vs. Kevin Mitnick - Editorial
- Index - READ
- The Gold Card - Detailed technical overview of Holland' PTT-Telecom prepaid phone cards and how to make your own reader/writer, by Hack-Tic
- Code: phone.c
- The Gold Card Original version in Dutch, from Hack-Tic, Issue 24/25
- Programming GOLD MM2 Wafer Cards Cardem v1.000.414
- MPASM Version 1.50
- MPSIM Version 5.20
- Chipcards Explained
- Facts on ATM Camera Security - Overview of ATM surveillance cameras and busting some of the myths surrounding ATM operations and installations, by Kitsune
- Cellular Interception Techniques - Different methods for the interception of analog cellular phones, by Thomas Icom
- Cellular Interception Techniques Original
- Letters - The Better Letters
- More Bookstore Fun - Seventh Son
- Piracy Proposal - Daveed Shachar (Israel)
- Eastern Europe Scene - The MacMan (Carl B. Constantine, Budapest)
- Locked Up - ATM Bandit, Phafnir, The Cryptic Prognosticator
- Bits of Info - Zeek (Major) (Colorado), Skimmer (Cambridge, MA)
- Digital Correction - Spook
- Intercept Tones - Scott (Buena Park, CA)
- Monitoring Mail - Drew
- Red Box Problem - Pestilence
- ATM Fun - Kilobyter (Flushing, New York)
- True Hackers - Edison Carter (M.D. Spangler)
- Mystery Computer - William Tell
- Source of Income - CMS (Santa Rosa, CA)
- Strange Numbers - Jason (Boise, ID)
- New Technology - Bitslicer
- Conscientious Trashers - "Hackers for a Cleaner Planet"
- Satellite Theory - Daughter of a Satellite Engineer
- A Fun Project - Quasinym (Peter Garver?)
- Mystery Number - Tony Sharp
- TV Garbage - Puppet Master
- Hacking Airphones - Empress (Georgia) (Similar Info)
- Mac Attack - Rev. Mr. DNA
- Computer Numbers - The Phantasm (Jim Brinkerhoff)
- Fun With Cordless Phones - Radio Man, Tom
- Hacking in Brazil - State of computer hacking in Brazil and notes about the local BBS scene, by Derneval (Ribeiro Rodrigues)
- The Brazilian Phone System
- Thirteen Years of Starting a Hacker Scene
- The Brazilian Phone System Revisited
- International Scenes: Hacking in Brazil From Phrack, Issue #48
- Hacking the Tandy/Casio Pocket Computer - Clever little BASIC program to bypass a set password when using the Tandy PC-6, by Sam Nitzberg (Eatontown, New Jersey, Email)
- Hacking the Tandy Zoomer Z-PDA / Casio Z-7000 - A look at the Casio Z-7000 and Tandy Zoomer, including a trick to open a text editor, by Enigma
- The Tandy Zoomer - The x86 PDA before the Palm Pilot
- Casio Z-7000; Tandy Z-PDA COMPUTE!, Issue #162
- Zoomer PDA Hardware
- Exchanges in 500 Land - List of NXXs in 1-500 land, home of "Phone Numbers for Life" and Personal Communications Service
- Pager Major - FAQ about pager systems in the U.S. and Canada, by Danny Burstein
- West Side Hacker: Masters of Deception - Book review of Joshua Quittner & Michelle Slatalla's Masters of Deception, by Scott Skinner
- Gang War in Cyberspace by Michelle Slatalla and Joshua Quittner
- Wilson v. Slatalla, 970 F. Supp. 405 (E.D. Pa. 1997)
- News Items
- Leaking Cables - British Telecom cable service problems, their fights with Mercury, and stopping information leaks
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Issue's Cash Cow: Kevin Mitnick
- Cover (Cover Info)
- Back Cover Payphones of the Planet
- Hong Kong #1 A Cardphone. The Cardphone takes phone cards. They both take coins as well. Photo by Michael Pusateri
- Hong Kong #2 A Creditphone. The Creditphone takes credit cards. They both take coins as well. Photo by Michael Pusateri
- Costa Rica In the frontier town of Puerto Jiménez, Peninsula de Osa. Photo by Martin Raminer
- Finland Reminiscent of coin phones throughout Scandinavia. Card phones in Scandinavia are usually orange, coin phones are blue/silver. Photo by Flippy the Squid
- Staff
- Download Unofficial Scanned PDF!
- Download The Hacker Digest - Volume 12!
$2600 Magazine - Volume 12, Number 2 (Summer 1995)
- The Bernie S. Saga - Editorial
- Index - GUTS
- Pioneering New Anti-Viral Technologies - How to protect your virus from anti-virus software, by Dr. Adam L. Young (Email)
- Malicious Cryptography - Exposing Cryptovirology Video by Adam Young
- Experiments From CryptoVirology Labs Video by Adam Young, ToorCon2015
- Malicious Cryptography: Exposing Cryptovirology by Adam Young and Moti Yung
- The GenderSnooper - Cool little project involving a wireless serial port data transmitter to intercept low-speed RS-232 data going to things like modems, by Commander Crash
- ATM Tricks - A look at some Diebold ATM tricks, including a massive hole with those "bring the receipt to the counter" machines, by Helen Gone
- AT& Fear Memo - AT& shakedown letter offering a "hacker" protection service.
- Citibank ATM Fun - Playing with the ATMs at Citibank which apparently have a maintenance screen you can easily access, by Ice of Spides
- Day of the Hacker - How a Wildcat! BBS was hacked with a trick PKUNZIP.BAT and an infected COMMAND.COM, by Mr. Galaxy
- Diverters - Tips and tricks for using hardware-based call diverters (forwarding), by Ray Nonte
- Hacking AS/400 - A hacker's look at the AS/400 and OS/400, with an emphasis on systems operating in Argentina, by Mantis King
- Hacking AS/400 by radiat
- Neitzert Threat Letter - Crooked Haverford Twp. cop John K. Morris threatens Christopher Neitzert for speeching out against the Ed Cummings arrest.
- Letters - "Letters are the cornerstone of any civilized society."
- Privacy Concern - Anonymous in MD
- Hacker Techniques - Pumpkin Smasher (Natchitoches, LA), Mickey and Mallory, Wicker Man (DeKalb, IL), Streaker
- War Dialing - Clint Sare (Texas), Lineman
- Numbers - TAG (Sheridan, Oregon), Mike, Major Zeek
- Data - Airwolf (Twin Cities, Minnesota)
- Questions - GF
- Pirate Alert - Red 5! and Hellbender
- Answers - Name and Address withheld, Gump (Sacramento, CA)
- Bookstore Stories - The Black Carpet (Bay Area, CA), Pestilence/517
- Caller ID Question - Chester-Buzz
- Lack of Security - Another Thought Criminal
- NYNEX Outrage - Scammed in NY
- Advice - Fortunate Sun, Lincoln
- On ATM's - Kamakize (Virginia)
- Spin Control - The Black Panther
- Handy Tip - BillSF
- Radio Reviews - Review of some radio frequency counter and scanner gear, including the Optoelectronics' Scout, R10A, APS104, Universal M-400 decoder, and AOR AR8000 receiver, by Blue Whale
- WarDialing - Interesting wardialing stories from a small town in Canada and an autodialer script for Qmodem, by VOM (Canada)
- Code: qmodem autodialer
- Coping with Cable Denial #2 - A look at hacking addressable cable TV converter boxes and a look at a Jerrold 450 cable converter hack, by Prowler
- News Items - Kevin Mitnick trial is set to start on July 10, 1995
- The Complete NPA List - List of area codes (1995), including all the weird ones
- Area Codes Map - U.S. (PDF Version [2003])
- Area Codes Map - Canada
- Area Codes Map - U.S. Territories
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Issue's Cash Cow: Bernie S.
- Cover (Cover Info)
- Back Cover Payphones of the Planet
- Cuba #1 Here's the scene straight from Havana. If you're up to it, the "bubble" phone has some exposed wires for the international boxer in us all. Photo by Arclight
- Cuba #2 "
- Russia Somehow this one works to this day. Photo by Warlock
- Ethiopia This shiny red beacon is used by people standing outside the Accident Investigation Department. Photo by G.T.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 12!
$2600 Magazine - Volume 12, Number 3 (Autumn 1995)
- No More Secrets - Editorial
- Index - WHAT?
- Stealth Trojans - Source code for a stealth DOS Trojan horse to wipe a hard drive and an overview of using "stealth" disk I/O access, by Commander Crash
- Code: BYE_BYE_BBS.asm
- Code: BYE_BYE_BBS.exe
- Military Madness - The true story of my experiences as a paid hacker for the military, by Anonymous
- T-Shirt Follies - Some adventures as a result of wearing a $2600 shirts to the Washington, D.C. 2600 meeting, by The Roach
- Macintosh Key Capturing - Source code for a Macintosh keystroke recorder with a jGNE filter in Motorola 68k assembly, by Swarthy
- Code: mac-key-cap.c
- Just Say NO! - Build a "NO-Box" which is like an improved "Gold Box" (switchable second line), by Hudson
- COCOT Experimenter's Resource Guide - Very detailed guide to various technical details about COCOT phones, with an emphasis on Intellicall payphones, by Dastar Com
- Intellicall Payphone Basics (YouTube)
- Short Time Validity Storage U.S. Patent No. 5,131,027A
- Method and apparatus for performing an automated collect call U.S. Patent No. 5,483,581A
- Intellicall Remote Payphone Software: Codes, Errors, and Indicators
- Intellicall Model 2001 Firmware This is the firmware from the Intellicall Model 2001 payphone. The files are named what the chips were labeled as on the board. 8000 and C000 are the ROM and 4000 is EEPROM.
- Letters - Language is a Virus From Outer Space
- Harassment - African Herbsman (Lexington, Kentucky), Roger Blake, Little Alex (Michigan), sam (Berkeley), Fast Lover (Houston, TX)
- Information - Ether, Dali Lamer, Curious and Anonymous (Los Angeles, CA), pbixby, Matthew Kassin, FkPigMan (Pittsburgh, PA)
- Telco Brains - Neo Zeed of 201, TTJ
- Article Feedback - (none given), Rokket Man, LACR01X, Bloodshot (Mt. Vernon, NY)
- Numbers and Addresses - McPhrie, Veg
- Censorship - Disgusted
- Discovery - Katfish
- Wanted - Nameless
- Mac Infiltration - Maud'Dib (Silicon Pirates)
- On Diverters - MASTER JSW, Anakin
- ATM Fun - The Final Chasm, ATM Dude
- Advice - Law Hack (Los Angeles, CA)
- Causing Confusion - tfg
- Fear of Subscribing - John Doe
- Yet More Bookstore Fun - John Lowe (Memphis, TN), Ford
- German Payphones - THX-1138 (Raleigh, NC)
- HOPE Repercussions - Mr. Pink (San Marcus, CA)
- Mutation Engine Demystified - Understanding virus mutation engines and example code for the author's Small Mutation Engine (SMut), by Tio Mate Jones
- ISDN Overview - A quick technical overview of ISDN services and information on ordering it, by Roger Harrison
- Introduction to the Integrated Services Digital Network (ISDN) AT&T Telessentials Curriculum (YouTube)
- DTMF Decoder Review - Review of a MoTron Tone-Master TM-16A Plus DTMF decoder, by Blue Whale
- Hacking a Police Interrogation - Some very useful and important tips on surviving a police interrogation, by Darlo Okasi
- Breaking Windows 2 - Defeating Windows 3.x screensaver passwords, by Bisect Skull Gas
- Movie Reviews: The Net and Hackers - Movie reviews of The Net and Hackers, by Evil Corley and Thee Joker (Jason)
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Issue's Cash Cow: Bernie S.
- Cover (Cover Info)
- Back Cover Payphones of the Planet
- France A typical French cardphone, found in Paris. Photo by Anonymous
- Israel An Israeli cardphone that is a big improvement over the old token system. Photo by Unka Nisi
- Norway This payphone was found in northern Norway (64.5° North) and takes only coins. Photo by John Lewandowski
- Japan This phone resides in Yokohama and is referred to as a "green phone". They use phone cards in 1000, 5000, or 10,000 yen denominations. Photo by Bill Bond
- Staff
- Download Unofficial Scanned PDF!
- Download The Hacker Digest - Volume 12!
$2600 Magazine - Volume 12, Number 4 (Winter 1995-1996)
- Speech Control - Editorial
- Index - CONSUME
- What Happens on the AT&T Side - A look at what happens after you contact AT&T Customer Service, by Crash 24601
- AOL Censored Wordlist - AOL internal memo for rules on the use of certain words in screen & room names
- News Update
- A Spoofing Odyssey - How jsz, Shade, Len Rose?, and others on #hack used Robert T. Morris' IP spoofing vulnerability to attack Shimomura's system for Kevin Mitnick, by Gregory Gilliss (Walnut Creek, California)
- IP Spoofing and TCP Sequence Number Prediction Original
- Plagiarized from a USENET posting by Tsutomu Shimomura. Do you think they sent him a t-shirt?
- A Weakness in the 4.2BSD UNIX TCP/IP Software Robert Morris, Jr.'s original Bell Labs paper.
- Spoofit by Brecht Claerhout
- Infiltrating Disney - A quick look at some of the tunnels and secret passages around Disney World, by Dr. Delam
- Sniffing Ethernet - Overview of a DOS utilities for monitoring Ethernet traffic, by Veghead
- Bypassing DOS/Windows Security - Several tips and tricks to bypass the security on DOS/Windows machines or drop to a command prompt, by Case
- Understanding Verifone Machines - Detailed information pertaining to Verifone credit card authorization, by Dr. No
- Credit Card Authorization Machines Original
- Plagiarized from an Informatik article by Emery W. Lapinski
- TCLOAD Reference Manual
- Verifone Commander Reference Manual
- Phones in Pakistan - Information on the phone system in Pakistan and the updates they are going through, by The Shepherd
- Letters - THOUGHTS OF THE READER
- Fraid Not - madh, Avi Drissman (Farmington Hills, MI)
- Questions - Psycho, Proteus (Babylon, NY)
- Clarification - Lucas, Fastchrlie
- The Master Plan - The Silicon Phoenix/810
- Words of Thanks - Lady Penelope (London, England), Checkerboard Phox (Kevin Phillips, Memphis, TN), SLUMBRBAK of the forest, Joel (Orange County, CA)
- Mac Trix - The Invincible in MD, Equant (Tucson, AZ)
- Privacy Regained - DayEight, Jerry
- Of ANACs and ANIs - Kevin (Memphis, TN), Percival
- Viral Stuff - Problematic 29
- Brazilian Hackers - kazi (Brazil)
- The Truth About Mitnick - Daniel
- On Bernie S. - King B, Data Recall
- Possible Warning - J.R.
- AOL Hell - Mark
- Destruction and Theft - TD, LIG (Life is Good)
- Hacker Perceptions - se7en (Christian Valor, San Francisco, CA)
- Answers - Bell Buddah
- Speech Confinement - angchay twenty-fidy
- Bookstore Stories - Harmony, MRB (Boca Raton, FL)
- Standing Up - Feyd, Tunnel Vision
- Pet Peeves - Stickman, Hacked, Cracked, and Phracked
- Shocking News - GoatBoy
- Back Pack Hack - The Cat's Meow
- Problem Stealing Money - Riddler
- Contacts Wanted - Joey Jay Weinman (Texarkana, TX)
- Info - David Smith (Las Vegas, NV), CMS (Santa Rosa, CA)
- Opening Doors - The Laughing Cow
- .COM File Infecter - Assembly source code to an extremely well-documented MS-DOS .COM file infecter, by Impending Dhoom
- Code: COM-infecter.asm
- Code: COM-infecter.com
- Understanding the Hacker - A look at what reasoning could possibly justify "hacking" in the eyes of those who do it?, by Bootleg
- Scanning Space - A list of radio frequencies used by U.S military satellites, NASA, and the Air Force, by The Majik Man
- AOL Syndrome - Using AOL's FTP space to host files via HTTP, by Kris (Kris Rehberg?, Reston, Virginia)
- Hacking NetWare - A look at hacking Novell NetWare and gaining a SUPERVISOR password, by Trap
- Cashing in on Mitnick: The Fugitive Game and Takedown - Oh, the irony!!! Book reviews of Jonathan Littman's The Fugitive Game and Tsutomu Shimomura's Takedown, by Scott Skinner
- 2600 Marketplace
- 2600 Meetings
- Price: $4.00
- Issue's Cash Cow: A look at speech censorship on the Internet and some of the bills Congress is trying to pass.
- Cover (Cover Info)
- Back Cover Payphones of the Planet
- Vatican If the Pope ever uses a payphone, it probably looks like this. Photo by Eclipse
- Malaysia Found on the Tioman Island. Photo by Hamilton
- Singapore You won't find any gum stuck to this one! Someone, however, seems to be peeling away the instructions. Dissent can be so ugly. Photo by Hamilton
- Japan This Wall of Green was found in the lobby of the Tobu Hotel in Tokyo. Photo by Malcolm Riviera
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 12!
$2600 Magazine - Volume 13, Number 1 (Spring 1996)
- Caught in the Web - Editorial
- Tap Alert - Build a simple add-on circuit for your Beige Box to detect when there is a large voltage drop on the line, potentially indicating a tap or addtional line picking up, by No Comment and Crash Test Idiot
- MCI Complaint Response - MCI's response letter after filing a complaint with the FCC.
- A Page of Revenge - Ideas for creating a pager demon dialer, by Big Lou
- Unshredding the Evidence - A look at the steps one would go through to reconstruct shredded paper documents, by Datum Fluvius
- Confessions of a Beige Boxer - Funny story of pranking via Beige Boxing and taking over payphones, by RedBoxChiliPepper (Brad Carter, MySpace)
- Macs at Ease - Simple process for bypassing At Ease on school Macintosh computers, by Loogie
- Sharp Cash Trix - Sharp ER-3100 cash register information and how to manually open the cash drawer, by Dennis Fiery (Knightmare)
- Sharp Model ER-3100 Electronic Cash Register - Service Manual
- Sharp Model ER-3100 Electronic Cash Register - Instruction Manual
- Nokia 100 Series NAM Programming - Don't let the Secret Service catch you reading this!
- Hacking Doors - Apartment access telephone security system holes and intercepting their DTMF codes, by Clark W. Griswald
- Hacking Caller ID Boxes - Expand the memory on CIDCO Caller ID boxes to 85, by Dave Mathews (Dallas, Texas, Email)
- The Alaskan Phone System - Information on the phone system in Alaska with a good hacker/phreaker point-of-view, by Ice
- Avoiding Suspicion - Tips on how to avoid looking and/or acting suspicious to local cops or the feds, by ~Me
- Letters - WHERE THE LETTERS ARE
- Opening More Doors - RB (San Francisco, CA)
- Eastern Europeans - Hrvoje Vukovic (Croatia)
- ANAC Change - woodrat
- Points on Interrogation - The Prophet, System Default, Robin Scurr (White Lake, MI)
- Bernie S. Fallout - Name Withheld, Mike W., TcP (Denver, CO), Mario (Canada), Adam Schoenfeld
- Military Miscellany - Cockroach, Disappointed in our Government
- Spanish ANI - The Mad Tapper (Ringwood, IL)
- Cellular Prisoner - Jeremy G. Cushing (Alphabits, Arrest Info)
- Highway Weirdness - Jus Jizzen (Phoenix, AZ), King Otar
- Meeting Questions - Joshua, Skywarp (London, U.K.), Frank M.
- Info - anonymous, PhreakHolio (Colorado Springs, CO), The Mighty Pantharen (N. Vancouver, Canada)
- Corrections - b00da (Philadelphia, PA)
- Reality? - Meth
- RadioShack Fun - Biohazard
- Unfriendly Payphones - Michael H.
- Questions - NeVeR \FluX/, M
- The Winter Cover - Christian (Germany), Dereks, fuLcrum (Miami, FL)
- Fun On Planes - Particle Man (203)
- Repression and Hackers - Brian Martin (Australia)
- AOL Hell - YUKYUK
- Credentials on Credentials - Gebby
- Crippled 911 - Ben Stock
- Disney Critique - Michele Warner, The Imagineer
- An Edward A. Smith Theory - some guy
- Cincinnati Bell Nightmare - Mr iNSaNiTY
- Understanding the Hacker - Sevangels
- 56K ISDN Link - ThePawn (New Jersey)
- Netware Nonsense - Gandolf
- Words of Praise - The Cyber Hitchhiker
- Words of Shame - E.W.L., Dr. No
- Motorola Cellular Guide - Motorola cellular phone and pager programming and hardware information, by Mike Larsen (Email #2)
- The Motorola Bible Original
- Hackers '95 Review - Review of Phon-E and R.F. Burns' film Hackers '95, by Blue Whale
- 2600 Marketplace - CAP'N CRUNCH WHISTLES. Brand new, only a few left
- 2600 Meetings
- Price: $4.50
- Issue's Cash Cow: Bernie S.
- Cover (Cover Info)
- Back Cover Payphones of the Planet
- Ukraine A cheerful sight in Kiev. Photo by Ed Fisher
- Moldova An old phone that runs on getones (16 per U.S. dollar). Photo by Tom Mele
- Transnistria A little-known breakaway republic between the Ukraine and Moldova. Photo by Tom Mele
- Romania The town of Suceava where, judging by the chains, there is a vandalism problem. Works on rare 20 lei coins which are worth about a penny. Photo by Tom Mele
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 13!
$2600 Magazine - Volume 13, Number 2 (Summer 1996)
- Guided Perceptions - Editorial
- Flood Warning - SYN flood code for IP spoofing or denial-of-service attacks, by Jason Fairlane
- Code: flood.c Hostlock v.01
- Scanning Australia - Toll-free modem carrier scan (0014-800-12[456]-XXXX) for Australia, by Comhack International (Victoria, Australia)
- Imaginary Friends - Getting phone service with fake name (fake ID) by supplying the credit bureaus (TRW, Equifax, etc.) with false information, by Frog
- A Tale of Two Cities - Overview of the telephone systems in Prague and Sarajevo, by Dr. Kolos
- How to Create Encryption - Overview of the process in creating your own software-based encryption system, by TheCrow (Jack Mott, Greenwich, Connecticut)
- Secret Codes - PowerBASIC script for communicating in secret, by Mister Galaxy
- Code: codeit.bas CODEIT Version 2.0
- CODEIT Version 3.0
- Consumer Hazards - Online shopping security and how to protect your credit card info, by Mr. Natural
- RCONSOLE Hacking - How to extract Novell RCONSOLE passwords from packet sniffer logs to gain access to NetWare's server console, by Simple Nomad (Mark Loveless, Arlington, Texas, Facebook, LinkedIn)
- Appendix Section - Source Code and Other Documentation Source and notes for SPOOFKEY, NOCRYPT, SETPWD, and BURGLAR.
- rcon.c Novell RCONSOLE password encryption decode, by Willem Jan Hengeveld (itsme)
- "Decryption" of RCONSOLE Password
- The Unofficial NetWare Hack FAQ
- The Hack FAQ: NetWare Misc. - Attack Info
- Hacking NetWare
- Novell NetWare & Ethernet Address Spoofing with ODI
- Letters - The Search for Extraterrestrial Letters
- Clueless Mac Users - Z (Sacramento, CA)
- Clueless IBM People - Starz N Strifez
- Clueless Idiots - EliTe ProTocOl
- Finding 2600 - DavesDead (Hoboken, NJ)
- And very very Grateful - s6killer (Corpus Christi, TX), I Gate
- Inspirational Speech - Bottomless
- Secret Service Reactions - Active Matrix, Captain Hook (Sacramento, CA)
- Fun Numbers - Cache $$$ (Boston, MA) Scott, Vitamin X (Bethlehem, NH), TRON (Santa Rosa, CA)
- Hiding Files - Greg Guerin (Mesa, AZ), Flatliner
- Phone Card Hacking - Uri (Jerusalem, Israel)
- Stupid Questions - ben
- Pirate Radio - CrIcKeT
- Privacy Invasion - hell-boy, Raymond
- Hidden TV Worlds - Airwolf (Minnesota)
- The Truth Revealed - The Propagandist, I.M. Free (Milwaukee, WI)
- Eyes in the Sky - Tek
- AOL Purgatory - RazorBack
- Warnings - Max, F (Denver, CO)
- PSI Horrors - Space Shot
- Info Wanted - Raul (Houston, TX)
- The Marketplace - The Omega Man (Austin/Elgin, TX)
- People Tagging - Druid, D.Q. (Stamford, CT)
- Danger on the Highway - Waxan Dwane (New Jersey)
- Prisoners - Jon R. Spatz (Pottsville, PA), Zero
- FlightLink Fun - Overview of In-Flight Phone Corp. FlightLink computer system which is being installed on various commerical airlines. This is the computer on the back of each seat capable of accessing the Internet, sending a fax, check stock quotes, and playing computer games, by TDi
- NYNEX Regression - A look at the problem of "smart" payphones in New York City restricting dialing, by Rebel
- Starting a Hacker Scene - How to start a local hacker scene, with Brazil as an example, by Derneval
- And Justice for All - Transcript of the Edward E. Cummings (Bernie S.) sentencing from March 5, 1996.
- 2600 Marketplace
- 2600 Meetings
- Price: $4.50
- Issue's Cash Cow: Internet Censoring, Send Money
- Cover (Cover Info)
- Back Cover Payphones of the Planet
- Poland Found in Warsaw. Something this size has to do more than make phone calls. Photo by DiSKRaPer
- Russia Residing in Moscow. Photo by Ed Fischer
- Venezuela Two styles of payphones: the one on the right uses coins, however, rampant inflation makes their operation difficult at best. The phone on the left uses cards - a system which has yet to be hacked. Occasionally, though, these phones inexplicably let people talk forever. You will find long lines when this happens. Photo by Alex Wieder
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 13!
$2600 Magazine - Volume 13, Number 3 (Autumn 1996)
- Fallout - Editorial
- Searches and Arrests - Your rights during a search or arrest as told by an actual lawyer, by Keyser Söze
- Hacking the SCC OS - Hacking tips for the Site Client Control (SCC) business management software (not the telco system), by D-Day
- Security Through the Mouse - Bypass keystoke recording with this clever program which allows mouse clicks in your password, by Steve S. Rives (Email)
- The Brazilian Phone System - Overview of the landline and cellular phone systems in Brazil, along with a few phreak tricks, by Derneval
- The Dial Pulser - Turbo BASIC code for a 2600 Hz single-frequency pulser (a.k.a. Captain Crunch whistle), by Golem of Sprague
- The GI CFT-2200 Power Box - Overview of the General Instrument CFT-2200 cable box, by Active Matrix
- GTE Voice Prompts - Codes to generate each of the voice recordings using by GTE, by Chillin' Bit Boy
- HP 200LX - A look at hacking with the HP 200LX portable computer, by PsychoWeasel
- Maximum WOW! - Overview of CompuServe's nationwide, unlimited-access, flat-rate PPP Internet service and a cool little trick to avoid using their dialer so you can use your own software, by Kris
- Hack Your High School - Tips for hacking your school's computer and also covering your tracks, by DayEight (Ryan Stevens, Email)
- Federal BBSes - A large list of toll-free government BBSes to call, by Anonymous
- Hacking the SR1000 PBX - A good overview of remotely hacking the Solid State Systems SR1000 PBX system, including getting calling card authcodes, by maldoror
- Building the Cheese Box - Build a phone line diverter box using a Parallax BASIC Stamp, by Thomas Icom
- Letters - Going Totally Postal
- The Cincinnati Nightmare - Craig A. Finseth, Judicator of DC, Mickle, Feanor (Fargo), Benjamin (New Jersey)
- 2600 Groups - Michael J. C. G., The Rippa
- Airplanes - Bishop (Maple Ridge, British Columbia))
- That Question Again - Jimp
- Phone Shutdown - PyroLite (Barry Bowling)
- Corrections - Cannibal
- Boat News - Phillip Phlop
- Mac Hiding - Josh M. McKee (Corvallis, Oregon)
- Submission - SN0WBLiND
- Numbers - foX mulder, Shadowdancer, cybersurfer, Ruthless Dictator, rolando rojas
- Mystery Computer - cookiesnatcher
- Novell Hacking - Dusty
- Security Concern - Ginchy
- Canceling AOL - Eribake
- NSA Tracking - Montauk
- The Red Box Issue - Cesar, Rev. Doktor S-bo (Steve Johnston), mthed
- Malfunction - Vader187
- Off The Hook - Mr. B.
- Free Communication - MA
- Words of Thanks - C.S Spankford (Seattle, Washington), DFW
- Applying Knowledge - Dr. Bob (Dr. Bob Testen, Germantown, MD)
- Coin Collection - Anonymous
- Trouble - alien13
- On The Inside - Cpt. Kirk
- Retail Madness - Jamez Bond
- Update - MRGALAXY
- Suspicion - Redial
- Videotext - MLiq
- Chip Implants - OddBall
- Hacker Defense - Charr
- Battling *69 - Ty Osborn
- Cash Registers - Spydir Man (Phoenix, AZ)
- Disney Facts - Line Noise (Orlando, FL)
- Crazy Phone - PoT-UsA
- Paranoia - Ben (Wichita, KS)
- Spoofing Cellular Service - Overview of cellular ESN cloning using an operational demo phone, by Baxlyder
- Reprogramming Data - NAM programming info for various Audiovox, Motorola, and Nokia cellular phones, by JS
- The Weird World of AOL - Various AOL Terms of Service violations
- PHF Exploit - Using the infamous Apache PHF CGI web server exploit to launch a xterm on a remote system, by fencer
- 2600 Marketplace
- 2600 Meetings
- Price: $4.50
- Issue's Cash Cow: Bernie S.
- Back Cover Payphones of the Planet
- El Salvador Photo by Knight Hawk & Cabeza Nightsoil
- Antigua Photo by Allwet
- Cuba Found in Havana. Photo by Steve Piantieri
- Brazil Found in São Paulo. Photo by Ralfus
- Cover (Cover Info)
- Staff
- Download Unofficial Scanned PDF!
- Download The Hacker Digest - Volume 13!
$2600 Magazine - Volume 13, Number 4 (Winter 1996-1997)
- Knowledge is Strength - Editorial
- Toward More Secrets - Info on today's cryptography, by Seraf (Dominick LaTrappe)
- Backcountry Phones - A look at the radiotelephone services (OptaPhones & Ultaphones) used by some rural or remote telco companies, by Equant (Nathan Hendler, Tucson, Arizona)
- The Birth of an Internet-Friendly Radio-Telephone Line Extender
- RuralConnect Point-to-Point
- FT-512 Trailblazer Multifunctional Digital Radio Installation & User's Manual
- Trailblazer - Ethernet Bridge User's Manual
- iWLL Trailblazer Field Programming Manual v1.4
- Chipcards Explained - Detailed information on chipcards used by Dutch and French telecoms, by BillSF
- The Gold Card
- Everything About Chipcards Original Klaphek, Issue #2
- Siemens Chip Card Technology by Yggdrasil, Phrack, Issue #52
- Biggest Mac Mistakes - An overview of common security mistakes Mac users create and tips on securing Mac-based computer networks, by The Guy Who Was In Craig Neidorf's Spanish Class And Had No Idea
- Craft Access Terminal - Information on outside plant Craft Access Terminals and accessing and using the Craft Access System, by Local Loop
- Craft Access Terminal by Boss Hogg
- Cracking askSam - How to bypass askSam database password protection, by Datum Fluvius
- Snooping via MS-Mail - Snoop on MS-Mail email using a simple hex editor trick to create errors in the file's header, which effectively removes the password, by Schlork
- Letters - YOUR LETTER COULD BE HERE
- The Ruling Class - Socrates, Josh (Abilene, TX), Hype (Mississippi)
- Folklore - Wussfish
- Finding People - Asmodeus (McKinney, TX)
- Info Needed - Jorge (Uruguay), Geert (Holland), DoubleZeroOne (Texas), Yosemite Sam
- Encryption - Data Stream, Azazel, Anonymous, WinSocker
- Questions - thedespised, Merlin (Anchorage, AK)
- Holes - charr (Atlanta, GA)
- On Cluelessness - Zyklon B
- Observations - Dr. Delam, xphreak, Desaparecido (San Francisco, CA), NG (New Jersey), Ammon, Rosey (Canada), president@whorehouse.gov, CF (Alameda, CA)
- New Stuff - xorsystm (Eric), TheFetish To Heresy
- Numbers - sisifis (Illinois), Captain Video, Michael (Germany)
- Corporate Hacking - Jack Stuart
- A Word of SYN - meem, George
- Oops - Gordon
- More FlightLink Facts - +universal cytixn+
- Bernie S. Thoughts - Kevin
- Our Hypocrisy - Sean Emerson (Goleta, CA)
- Upgrade - MRGALAXY
- A Freer Juno - phunhertz
- Cable Notes - Platypus Man
- Gambling Hack - Guz
- PHF Exploit - Astraea
- Monopolistic Motion - (orbital) (Nashville, TN)
- A Fun Federal Story - love 357
- Disturbing News - Rich D.
- Porn Sting Update - BD (Denver, CO)
- NYNEX Neighbor Problems - Guard of the Gate (Massachusetts)
- AT&T Check $2600 received a "change your long distance, get $80" check for a NYNEX test number.
- Subscriber Network Interfaces - Information on telephone network interfaces and some phreaky things you can do with them, by Frequency Man (FreqMan)
- Telephone Network Interface Device U.S. Patent No. 4,488,008A
- Container for Telephone Network Interface Device U.S. Patent No. 4,741,032A
- Security Override Network Interface Device U.S. Patent No. 4,749,359A
- Customer-Accessible Test Port for Network Interface Device U.S. Patent No. 5,625,686A
- Unfriendly Numbers - A list of 800-numbers which charge the caller. Compiled from internal MCI docments, by Secret Squirrel (Michael Jacobus)
- How to Steal Things - Mail order tricks for getting "free" items mailed to you, by Ted Perver (J.J. Styles [a.k.a. 0ptiKal ilusioN, a.k.a. Zot the Avenger])
- Social Engineering via Video - A technique to social engineer information by just walking into a place with a video camera and pretending to be a film student or reporter, by Bernz (David Noah Bernick, Email #2)
- The Complete Social Engineering FAQ by bernz
- Defeating the W95 Screensaver - How to extract a Windows 95 screensaver password from the USER.DAT file, by rdpzza
- Defeating the Windows 95 Screensaver Original
- Book Review: Anarchy Online - Review of Charles Platt's book Anarchy Online, by Scott Skinner
- 2600 Marketplace
- 2600 Meetings
- Price: $4.50
- Issue's Cash Cow: Bernie S. & Kevin Mitnick
- Cover Awesome cover photo! (Cover Info)
- Back Cover Payphones of the Planet
- Myanmar In the nation formerly known as Burma in the city currently known as Mandalay. Photo by Princess Valiant
- Honduras Photo by Theora
- Nicaragua Found in Managua. Photo by Knight Hawk & Cabeza Nightsoil
- Canada Found on a Gulf Island in British Columbia, this phone is more multi-purpose than most. Photo by Steven McClain
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 13!
$2600 Magazine - Volume 14, Number 1 (Spring 1997)
- Enough is Enough - Editorial
- Hacking LED Signs - Good overview of those scrolling LED signs you see out in the public and the ability to remotely program your own messages, by Bernie S.
- ALPHA 210/220 - Instruction Manual
- ALPHA 430 - Instruction Manual
- ALPHA 440/460/480 - Instruction Manual
- BETAbrite - Programming Manual
- BETAbrite - Instruction Manual
- AlpahNET User's Guide
- Social Engineering Your Way Out of Boot Camp - Tips and tricks you can use to "social engineer" your way out of boot camp, by InVerse [MoS]
- English 2600 - A book titled English 2600 by Joseph C. Blumenthal.
- Poor Man's Access - A UNIX-based TCP/IP client/server application written in C. It provides remote shell access on UNIX servers through a firewall, by GT
- Consequences of .GOV/.MIL Hacking - Possible serious consequences if you happen to get caught hacking .gov/.mil websites, by Chocolate Phoetus
- More PHF Fun - Python script to search the Internet for websites effected by the Apache PHF exploit, by ChezeHead
- Code: phf.py
- Credit Card Numbers via Calculators - How to generate credit card numbers on a TI-82 calculator, by DETHMaster (Jesse Curry)
- Code: CC-GEN-82
- Paper Evidence - A look at properly destroy paper evidence, including flash and water-soluble paper, by F. Leader
- Cellular Programming Data - More RadioShack/Tandy CT-352/3, Uniden CP-170, Technophone 901, CT-100/101/200/201, EZ400 NAM programming notes, by Threc (Dustin Darcy)
- BANM Memo - Cellular phone authentication policy from Bell Atlantic/NYNEX Mobile (BANM).
- Downsizing Insurance - How to avoid being fired and collecting "payback" data, by Hans Gegen
- Letters - Letters That Don't Suck
- Dealing With Parents - edoban, FEENIX aka The Ebola Virus, fordyman, Ace Lightning
- Subscribing vs. Newsstands - jetman
- A Real Clever Trick - ameba
- Tale of Woe - Jeff
- Number Fun - CIA, Darkman, Saiine, CrACKeD (Tucson, AZ), BStone, JN, Rokket Man
- Technological Marvels - Phreakner
- Big Brother - Wes "Holodoc" Mills
- Frequencies - Desaparecido (Bryan Robert Cowan, Sacramento, CA, DOB: 11-27-1974)
- School Terror - Socrates
- Exciting Updates - sw, Josh M. McKee
- Bernie S. Feedback - CYBERJE, POEE Chaplin (J. Weiss), Armitage Shanks, MBG
- Video Boxing - =NSNiPER=, NeoCzar, Pyrojax (ShwaG)
- Exorcising AOL - Sevangels
- Newbies - ZeBoK, OpieX
- PHF Findings - Zeed
- Web Reaction - KH, Anonymous
- Submitting Stuff - (i), Jack T. Dragon
- 2600 Name Dispute - Mr. Kiddie Pr0n
- 2600 Sells Out - Brain Child
- Cable/Web Thoughts - Eli the Bearded
- Praise - sgtpepper
- More on Disney - Moonpanther, GB (Georgia)
- Cellular Spoofing - WinterMute
- Implants - /dev/null
- More on the Mystery Computer - Viral Messiah (Mike, Jamestown, KY)
- Credit Fraud - scrap
- Bookstore News - Phun and Gamez (Emporia, KS), /dev/thug
- On Stealing Things - Artifice, charr (Atlanta, GA), Dorsey Morrow, Jr.
- Mischief in the Subway - Madeagle
- Psychic Rip-Off - DT
- Radio Show Online - Zaph32 (Dallas, TX)
- One For Kevin - Venshea, MD
- Inspiration - SodaPhish (Corey J. Steele)
- Phone Weirdness - grim, Procell
- 2600 Meeting Mishaps - Cesaro (Toronto, Canada), Crumb (Buffalo, NY)
- Military Hacker - Mainframe
- Punctuation Problems - Niel Ians
- Mac Hiding - Total Idiot
- The Other Side - (unreadable signature on a fax)
- Evil Ex Strikes Hacker - MANOWAR (Orangeville, Ontario, Canada)
- Serious Concerns - Shadodin
- Invisible Phone Line - $2600 has a phone line which apparently has no physical address attached!
- How to Hack Tech Support - Tips for getting the information you desire when dealing with tech support, by Dennis Fiery (Knightmare)
- USENET Bug - INN exploit via Subject: and Control: headers.
- Letter from Prison - Letter from Agent Steal discussing his current and future situations, by Justin Petersen
- Digest of Opinion - A look at Agent Steal's sentencing and his (denied) request for a lower sentence due to having "special skills."
- The Other Kevin Book - Book review of Jonathan Littman's The Watchman, by Noam Chomski
- Unsolved Mysteries - Kevin Poulsen Episode Season 3, Episode 4
- How to Legally Use a Red Box - Use the audio tone output of a Red Box to control things, by Kingpin
- Red Box Detection Circuit A practical use for a "toll fraud" device, by Kingpin
- The Red Box Detection Circuit
- 2600 Marketplace
- 2600 Meetings
- Price: $4.50
- Issue's Cash Cow: Kevin Mitnick
- Cover (Cover Info)
- Back Cover Payphones of the Planet
- Slovenia #1 This is a blue phone. Photo by R.D.
- Slovenia #2 This is a red phone. Photo by R.D.
- Slovenia #3 The blue phone is slowly replacing the red phone since the red phone takes tokens and the blue phone takes tokens and chip cards. Photo by R.D.
- Israel Found in Tel Aviv. Photo by Hanneke
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 14!
$2600 Magazine - Volume 14, Number 2 (Summer 1997)
- The Neverending Story - Editorial
- Cable Modem Security Holes - The advent of cable modems has opened up a wealth of security nightmares for Internet users in this area. If current technologies aren't upgraded, thousands of future users could be at risk, by Sciri (Sean Sosik-Hamor, Sean B. Hamor, Twitter, Reddit, Pelham/Nashua, New Hampshire, Allston, Massachusetts)
- GSM Comes to North America - An extremely well written and detailed overview of the GSM cellular phone system, by Phiber Optik
- Overview of the Global System for Mobile Communications
- How to Build Your Own Rogue GSM BTS for Fun and Profit
- The Wonders of Net2Phone - Overview of IDT Corp.'s Net2Phone pioneering VoIP service, by tersIan
- Those Pesky Mylar Strips - Info on the Mylar strips in U.S. currency and the ability to remotely detect them, by Dave Mathews
- Those Pesky Mylar Strips Original
- FORTEZZA: The Next Clipper? - Overview of the government's new encryption standard and hardware access cards, by Seraf
- FORTEZZA KOV-8/12/14 Crypto Museum
- FORTEZZA CryptoSecurity Products
- Fast-Food Phun - Harassing fast food drive-thru operators by transmitting on their radio system, by VaxBuster (Email)
- Radio Modification Archive - 1998 v1.2 (OFFSITE)
- Tricks and Treats of the AUTOVON - An overview of using the calling featuers of the AUTOVON DOD phone system, by N-Tolerant
- Omnipoint in New York City - List of Omnipoint cell sites around New York City, by Syringe
- Letters - Lucky Letters
- Injustices - The Hemroid, Kurt, Hellnite, Anonymous (Ocala, FL), X-Ion Noize
- Numbers - Josh, Memory Overflow, No Name, Joe Mama, Mindkiller, Legba, Saab, No Name, Ted Merriman
- Off The Hook - Brendon
- Commentary - YT
- Social Engineering - IFP (Iowa), Privacy Freak in MI, KpTone
- Defaming Our Good Name - greg
- Info - RBCP
- Meetings - Anonymous (New Jersey), The Hunter, Syphon Siege (Buffalo, NY), Low Tek (Rick Merced, CNN Interview, Atlanta, GA)
- Hacked Web Sites - Boris
- Mystery - wire fatigue
- The AOL People - Magus, Viral Tonic (Response)
- The AOL Rules - JediHamster (Xander)
- How Dare You - Fraas
- More School Stupidity - bryan
- The Decline of 2600 - pokis
- An Australian Nightmare - Cochrane
- Corrections - BillSF, Kaptain Kangaroo
- LED Sign Update - Da Findler Man
- Spy Hacking - S
- Clueless - Bear
- Hopeless - Nameless
- Pointless - Rhyme-Chai
- COCOT Mysteries - Cheeto
- Phone Tapping - Mwaahh
- Condoning Fraud - the trailer park hero
- Thanks for the Virus - MiSguiDeD
- Dangerous Info - Tim Leary
- Arcade Facts - James R. Twine
- Don't Steal Us - ISP Sales Snake
- Supervised Release Hell - Minor Threat (Chris Lamprecht, Austin, TX))
- Cellular Call Trace - KOADALAN
- The Mitnick Case - TC (Ft. Leavenworth, KS)
- Defeating HTTP Access Control - How to defeat HTTP access control with a brute-force password checker in Perl, by Ryan (Ryan Nelson)
- Code: 401-grope.pl
- The Ins-and-Outs of MetroCard Gold - Technical details of the New York Transit MetroCard system, by blueski-mask and the wrapper
- News Items
- 2600 Marketplace
- 2600 Meetings
- Price: $4.50
- Issue's Cash Cow: Kevin Mitnick
- Cover (Cover Info)
- Back Cover Payphone World Tour
- Dominican Republic In the province of La Romana, near Higueral. Photo by Carol Burke
- Cook Islands A Telecom New Zealand phone in downtown Avarua on Rarotonga. Photo by Nick Phillips
- Georgia Yes, that part of the Peachtree State that somehow avoided BellSouth. Found in the hospitable town of Tbilisi. Photo by Joe Cammisa
- Florida Well, why not? This is our culture and we're damn proud of it. Found in Panama City Beach. Photo by Morrissey
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 14!
$2600 Magazine - Volume 14, Number 3 (Autumn 1997)
- Sobering Facts - Editorial
- Busted! A Complete Guide to Getting Caught - Sound legal advice on what to do if you are are ever busted by the feds, by Agent Steal with contributions and editing by Minor Threat (Chris Lamprecht)
- Hacking FedEx - Overview of the FedEx internal computer systems and security (The Beast = Enigma Logic SafeWord), by PhranSyS Drak3 (Brian Taylor)
- Defeating *67 With Omnipoint - Clever little trick to defeat Caller ID blocking when using the Omnipoint GSM network, by TtJ
- The Height of Sleaze - Advertisement with *82 already included in the phone number.
- How to Be a Real Dick on IRC - Overview of using IRC and the steps for taking over ops on IRC channels, by semiobeing
- How to Destroy Sensitive Information - Discarded memo on PIN changes.
- Brute-Forcing the World - Ideas for brute-force password hacking on a college campus using an open POP mail server, by ChezeHead
- Hacking the Vote - Potential voting holes and loopholes, especially with mail-in voting, by A-Napa Candidate
- The E-ZPass System - Overview of the New York State Thruway's E-ZPass toll pass system, by Big Brother
- NSC FOIA Response - After only 9 years!
- Letters - We Printed Your Letter!
- True Hacking - banaker
- Fun At Barnes & Noble - Black Jaguar, anonymous, Barnes & Noble Financial Center (Westbury, New York)
- Righteous Hacking - Bomber Chick, Katfish
- Replies - Imran Ahmed a.k.a. Eric Blair, kingpin, Deranged
- A Challenge - Clive
- Questions - StLSD2000, Phracture, scott, CP
- The End? - Ripped Off by NYNEX
- Critic's Corner - sTs, Orion, TC (Fort Leavenworth, KS)
- Mitnick Fallout - Phip-C, DM & NightShadow, fiNrod (Montgomery, AL)
- Circuitry - Crampet
- Suggestions - Steven, sb
- Problems - [Name Obliterated], MaRTiAs, sryob
- Improvements - Mutter
- Numbers - Ydeologi (Marshall Votta), DJinOK, A., Spillage (Orange, CT), Mwaaah, Jonny Deth
- Uh Oh - josmo
- Fixing Juno - BuPhoo, cap.n_crack
- Offended - Absinthia Vibrato
- Notes From The Military - Jungle Bob
- For The Record - The *REAL* NeoCzar
- Meeting Problems - CW Extreme, Flipliquid, Checkmate
- Beyond Hope Aftermath - mattj, D.
- IRC Woe - havok
- USA Still #1 - elw00d
- Gee Whiz - Adam768L and Da Violator
- Singapore Connection - Joe a.k.a. DaemonX
- Free Video Games - PaulT
- Clarification - Ether Bunny, TheEtch
- PCS Mystery - Matt D.
- 2600 Marketplace
- News Items
- Secrets of Walmart - Overview of the Walmart store internal phone system and the different extensions they use, by Pirho (Gregory Jones, New York, New York, MySpace)
- 2600 Meetings
- Price: $4.50
- Issue's Cash Cow: We are too stupid to run a magazine. Instead of Evil Corley working at a McDonald's, why don't you send us more money?
- Cover (Cover Info)
- Back Cover Payphones on Planet Earth
- St. Pierre Few people know of the islands of Saint Pierre & Miquelon just off the coast of Newfoundland. These North American islands are actually part of France! And this phone, found on a wharf, belongs to France Télécom. Photo by Marc Cormier
- Greece From Knossos on the island of Crete. Photo by David Ruderman
- Kazakhstan Found in the city of Almaty. Photo by Juarez
- England A vandalized phone in London with possible murder evidence. Photo by Mik
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 14!
$2600 Magazine - Volume 14, Number 4 (Winter 1997-1998)
- Remember the Future - Editorial
- Your Very Own Backhoe - Perl script to create a backdoor daemon which continuously copies a root shell into /tmp, by miff (Email)
- Code: backhoe.pl
- The Medical Information Bureau - Getting medical information, like a medical credit report, from the Medical Information Bureau, by Crash 24601 (Matt D. Cox)
- Some 800-555 Fun - 800-555-XXXX carrier scan, by PorT666 and ChaosMakeR InC.
- TCP/IP - Overview of TCP/IP and some potential shortcomings or vulnerabilities, by Nathan Dorfman
- TCP/IP Original
- The Ominous GETS - Scan of an official pamphlet providing an overview of the Government Emergency Telecommunication Service (GETS)
- The Potential of Mobil Speedpass - Information and operational overview of a Mobil Speedpass card - including a dissection!, by A.M.
- Telco/Government Cooperations - Pacfific Bell Investigative Services pamphlet on how the government gets a wiretap warrant, by Mr. Opossum
- How to Get Away With Things on GeoCities - How to hide files and setup webpages on GeoCities to bypass their restrictions, by Champ77 (Email, Slashdot)
- The Argentinian Phone System - Information on the phone system in Argentina and some trick the local phreaks are using, by Derneval (Derneval R. Rodrigues, Brazil)
- International Scenes From Phrack, Issue #45
- How to Hack a Virtual Pet - Tricks for hacking and experimenting with the lives of toy Virtual Pets, by MiLtRoNi
- Letters - Letters to Captivate You
- Criminal Advice - Mr. Swervon (Michigan)
- Newbie Advice - Vic Sinclair, Spekter (Atlanta, GA)
- Defining Our Purpose - Dominus Omniae, Joe A
- Getting Caught - onyxfr0g, RM
- Equal Access - No Name No City Please
- Questions - Night Words, Silicon Mage, T.C.
- New Facts - Virtu-Al, Somewhere in Maryland
- Help Needed - Head-aches in Arlington, kyle, Jakob14246463526390210, JR
- Next Letter - Kurt
- Reactions - The Mad Hacker, Lee, phreakout, Tp, H.M. Murdock (Pennsylvania), Archmage, Nathan, John b Cannon, joshua, Anonymous, Austin, Citrus, phil, Hernan (Brazil), Seraf, Nitron
- Croatian Hacking - Electrik Monk, Anonymous
- Critique - DS
- Meetings - xxxxxx, The Phrkman and Cybrthuug (Lewisville, TX)
- Boston Transit - Anonymous in Boston
- Norwegian Payphones - Jostein Nygaard (Norway)
- Information - Dr.Seuss, Eric Albert
- Criminal Actions - Dan
- Canadian Stuff - dj.tazz@earthling.net (Canada), Members of RoK, Jim S [416] (Canada)
- Access Problems - MuSo (Florida)
- Words on Cable Modems - William
- Suggestion - Jim
- Military Recruits - Mortis, ToxicShock
- The Anarchy Debate - TDecius
- Miscellaneous Feedback - Boanne
- Apology - DETHMaster, Roy Haskins
- Spying on Yahoo! - 1,000 random Yahoo! search strings captured via a security hole - or intentional external monitor?
- Hack Your Head - Overview of using legal stimulants and drugs to improve your hacking or coding sessions, by Met-Enkeph (Evan Eveland, LinkedIn)
- Hack Your Head Original
- Noggin' Cracking - Cracking software without any tools and just using your brain, with a real-world example using ValueFax, by Fidel Castro
- Sun's Nasty Little List - A look at the United States' (Sun Microsystem) "Denied and Restricted Parties List" (i.e. no sales) list
- Prohibited Parties Database Export Administration Regulations Marketplace
- List of Statutorily Debarred Parties, July 1988 - January 2008
- Specially Designated Nationals List Office of Foreign Assets Control
- 2600 Marketplace
- 2600 Meetings
- Price: $4.50
- Issue's Cash Cow: Kevin Mitnick
- Cover (Cover Info)
- Back Cover Payphone World Tour
- Armenia #1 From the city of Yerevan. This is a generic Russian payphone that still works if you have the proper change. Photo by T. Mele
- Armenia #2 Also found in Yerevan, this phone has a much cooler color. Photo by T. Mele
- Vietnam In the streets of Saigon. Photo by Marie-Franco Bojanowski
- Bolivia Where red phones are common. Photo by Stuart Smith
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 14!
$2600 Magazine - Volume 15, Number 1 (Spring 1998)
- Message Sent - Editorial
- The Defense Switched Network - General overview and dialing information on the Defense Switched Network, which is the AUTOVON replacement, by DataStorm
- More on Military Phones - Basic information regarding the DSN military phone system, including several base numbers, by Archive
- The Mysteries of SIPRNet - First-hand account of a hacker exploring the Secure Internet Protocol Router Network (SIPRNet), by The Ruiner (Ian Reddy, Canada, Email #2)
- ANI2 - The Adventure Continues - Automatic Number Identification (ANI) II digits are two-digit pairs sent with the originating telephone number. These digits identify the type of originating station, by vandal
- ANI II by ic0n
- ANI II Assignments As of February 2, 1999
- Eggdropping - Detailed article on the operation of IRC Eggdrop bots, and the online IRC wars they can cause, by Tempest
- Naming Exchanges - An interesting look at how old telephone exchanges were named and an adventure in calling PE6-5000, by Jeff Vorzimmer (Texas)
- PEnsylvania 6-5000 Original
- PEnnsylvania 6-5000 by Glenn Miller
- Telephone EXchange Name Project by Robert Crowe
- Hack the Hardware - A look at hacking network hardware, like the 3Com SuperStack II hubs or HP JetDirects, by Sadena Meti (David J. Emiley, Cedarburg, Wisconsin, Email)
- Day of the Office Assault - Pranking an office coworker with a simple DOS TSR which moved the cursor and then printed random quotes, by MRGALAXY
- Code: office.bs
- Defeating CyberPatrol - How to bypass and delete CyberPatrol, which has tricks to prevent people like us from deleting their programs and gaining free reign over the Internet, by Franz Kafka
- CGI Flaws - Potential security flaws when executing CGI scripts, by Friedo (Mike Friedman)
- A Brief History of Postal Hacking - A tongue-in-cheek look at the history of USPS mailing hacks and the hackers ("phackers") behind them, by Alien Time Agent, Seraf, and Waldo
- Letters - Letters
- Plea For Help - Sly
- Infos - PhatKat, Packrat, anonymous, MR, D-Recz, Super Sharp Shooter (Ottawa, Canada), skwp, Chris (d7), Rev. Smoov
- Finances - AcidHawk, Tuxedo Mask (Aaron, Ciba Mamoru, Phoenix, AZ)
- Arcade Memories - Semaj31273 (James R. Twine, Goffstown, New Hampshire)
- Random Questions - Tim, zuggy, Dave, Meglomaniac, SaLT, Phreakin in Phoenix, boardfreak, ALC, The Computer Junkie
- A Big Misprint - Sith
- More Newbie Bitching - PaKo, Jade
- Clarifications - James S. Kaplan (KG7FU), philosopher, Christos Paraskeyopoulos (Christos Paraskevopoulos?)
- Criticism - Ultra Sonic, KnIgHtMaRe
- More on Anarchists - MALICO
- AOL People - Khan SW, JJ (Johnny Blaze)
- Facts - Allin, Donoli, Anonymous, codefreez (Eric, Mountain View, CA)
- Independent Browsing - VirtualToaster (Merritt Burrus, MySpace)
- Bookstore Computers - Ranma, Istra
- Clampdown - Greythorne The Technomancer
- More IRC Abuse - Calis
- On Mitnick - candyman, Silicon Mage (Neufeld)
- Posers - TDK (Urbana, IL)
- 800 Fun - FoNeCoRd
- Military Insight - I3ullseye (Dave Maynor, Spokane, Washington), annsan
- Encryption and the US - A member of the TMC (Note: The Canadian government is filled with foreign spies)
- Hassles - Anonymous, tennis ball, Resol Etile
- More Privacy Lost - mix
- Wow - zigzag
- Suggestion - soldado
- Weirdness - Anonymous
- New Meetings - I)ruid (Forth Worth, TX)
- Drugs - informagnet, Dr. S
- Cable Modem Facts - TyPEsCAN
- Hacking a BBS with DOS - Tricking a BBS sysop into running your Trojan software - or deleting everything, by Section8
- How to Get the Better of Best Buy - Best Buy service computer and overhead paging information, by a corporate sucka' no longa'
- Even Better Still - Overview of hacking the dial-up TRANE Tracer environmental control systems at Best Buy stores, by Mbuna
- Brute-Forcer for Tracer
- TRANE Terminal Unit Controller Installation, operation and programming of TUCs (EMTX-IOP-1)
- TRANE Tracer Summit v17 System Programming (BMTX-SVP01B-EN)
- Setting up UNIX Trapdoors - How to hide your entry on UNIX systems and the dangers of .rhosts, by Nathan Dorfman (Email #2)
- Not a Secret - The Department of Defense can't figure out MS-DOS and FORTEZZA crypto card readers, found by Seraf
- News Items
- 2600 Marketplace
- 2600 Meetings
- Price: $4.50
- Issue's Cash Cow: Kevin Mitnick, send more money...
- Cover (Cover Info) ("FREE KEVIN" Static HTML Page)
- Back Cover Payphones of the Middle East
- Oman In Muscat, home of the stylish kiosk. Photo by Khaldoun Shobaki
- United Arab Emirates Found in Dubai, this phone looks suspiciously British. Photo by Khaldoun Shobaki
- Egypt This modern wonder was spotted in Cairo. Photo by Khaldoun Shobaki
- Syria Damascas. Yeah, it's mostly a picture of the booth but it still looks pretty cool. Photo by Khaldoun Shobaki
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 15!
$2600 Magazine - Volume 15, Number 2 (Summer 1998)
- Lies - Editorial
- Where Long-Distance Charges Come From - Detailed tabulation of where long-distance phone charges come from, specifically "access charges" which are the heart of per-minute charges for voice bandwidth, by The Prophet (Babu Mengelepouti)
- Facts About Cable Modems - Technical info on cable ISPs and Zenith cable modems, by jeremy
- ANSIR FAX - A quick little look at the FBI's ANSIR-FAX system.
- What is ICA? - Overview of the Citrix Independent Computing Architecture thin client protocol, by Democritus "Father of Materialism"
- A Newbie Guide to NT 4.0 - Beginner guide to Windows NT 4.0 password and account security, by Konceptor
- Build a Modem Diverter - Divert an incoming modem line to another line, by digital/Digital
- Simple Modem Diverter Design Original
- The Tyranny of Project LUCID - Info on Advanced Technologies Group's Project LUCID "international justice" computer system, by Tom Modern
- Project L.U.C.I.D. The Beast 666 Universal Human Control System, by Texe Marrs
- Hacking Laser Tag - Hacking the laser tag games at LaserStorm, by johnk
- A Note From 3Com - Default username and passwords for CoreBuilders, by Percival
- User Instructions for the Sentex Ovation System - Instruction pamphlet for the Sentex Ovation telephone entry system.
- Fun With Java - Playing around with Java, and exploting the codebase= attribute to quickly pre-load applets, by Ray Dios Haque
- AT& Fraud Detection Letter AT&T detected potential fraudulent third-party billing on $2600's line.
- Lawsuit Threat From a Church - $2600 threatened with a lawsuit for hosting a mirror of a hacked webpage.
- The Millennium Payphone - Overview of Nortel Millennium payphones, by Phluck
- The Nortel Millennium Payphone: Everything You Ever Wanted to Know by Syko416
- Millennium Database Design Report
- The Nortel Millennium Payphone Repository
- Resurrecting A Nortel Millennium
- Millennium Multi-Pay Terminal Installation, Operation, and Maintenance Guide (506-6501-203)
- How to Hack Your ISP - Overview of some basic UNIX security and exploits targetting most dial-up ISPs, by Krellis
- How to Hack Game Guru - How to hack the demo copy of 3DO Game Guru, sofware which taps into the secret codes of each game to reveal more options for you to play, by Axon
- 3DO Game Guru - Hidden Developer Video (Easter Egg Info)
- Game Guru ConsoleMods Wiki
- Letters - LETTERS
- Questions - Payphone, reid, Anonymous in Minnesota, Callme Ishmael, kris, Bendzick, PbH, Asher
- Newsstand Update - Javelin, John Doe
- Meetings - twisted circuits, Flash, Dr. Doolittle
- Disturbing News - Ruiner (New Times BBS), M Davis a.k.a. SemiSpy
- Online Idiots - Dave, The Informant
- Software Concerns - Schrooner, Greyhare
- Random Info - Luke, Allin, SilverStream, FIXatioN, Mark Iannucci, Soul Implosion, phiberphit, Desaparecido, Flinx, skwp, Citrus, Mastery
- More Fun In Stores - Corvi42 (Trisan Nixon, Toronto, Ontario), Carole
- 2600 Problems - Kevin Brown, Eric B. AKA Flyable George, SYCO, Dave Kiddell, Catt, Disappointed
- Comments - Dr. Psycho, JJ
- Pleasantries? - DramaDame, Briareos
- Mitnick - klineline, *69, ed
- Head Hacking Advice - Malico, kevin g
- Clarification - Atrifix (Matt Atrifix), K. Ruff
- Bookstore Monopolies - R.J. Eleven
- Credit Due - Nothingg
- Phone Exchange History - Stealth Ricochete
- A Suggestion - F.E.D.-D.E.F.
- The Generation Gap - curtis in cali
- More on FYROM - MJ Mastermind (Athens, Greece)
- A Nagging Question - Trend_Killa
- Fingerpainting at the Precinct - Story of being fingerprinted at the NYPD 44th Precinct and the Identix computer system they used, by The IMC
- Inter-Tel Phone Systems - A look at remotely hacking Inter-Tel business phone systems, by Sundance Bean
- Security Through "Secure" - Program to watch process IDs vi ps aux to determine if they exceeding a set limit, by kasper
- Code: secure.c
- Tips on Generating Fake ID - Info on getting or making fake IDs, by DrNick (Benjamin Polen, Email #2)
- Fake ID Guide Original
- More on DSN - Overview of the Defense Switched Network, including numbering formats and call control information, by Dr. Seuss of the OCPP (Email)
- 2600 Marketplace
- 2600 Meetings
- Price: $4.50
- Issue's Cash Cow: Only $2600 can exploit Kevin Mitnick for profit!!!!!!
- Cover (Cover Info)
- Back Cover Korean Payphones!
- Korea #1 Found on Kunsan Air Base, this phone hooks you to an international operator with one stroke. The buttons all indicate countries to connect to. Photo by Jas Ed Carleton
- Korea #2 This phone was found on Osan Air Base at the mini mall. It's the typical model for all of the bases. Photo by Jas Ed Carleton
- Korea #3 Blue Boy was found at a Korean barbecue restaurant that is off limits to military personnel. Photo by Jas Ed Carleton
- Korea #4 The phone that might as well be from another planet, Big Red was discovered in a nightclub in Songtan. Photo by Jas Ed Carleton
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 15!
$2600 Magazine - Volume 15, Number 3 (Autumn 1998)
- Progress - Editorial
- Homemade TCP Packets - Perl script for crafting spoofed or corrupted TCP/IP packets, by miff
- Code: lego.pl
- Socket Programming for Fun and Profit - Beginner info and code for TCP/IP socket programming, by Darknite (Email #1, Email #2)
- Blasting Sound - Simple shell script for generating annoying audio on hosts remotely, by Slatan (-=H8RED=-)
- Code: blast.sh
- Back Orifice Tutorial - How to use and install Back Orifice, by skwp (Yan Pritzker)
- BO2K - Back Orifice 2000
- Back Orifice - Original
- Welcome to the Back Orifice Section Original Packet Storm Archive
- BO Plugins, Screenshots and Fan Pages
- Back Orifice 2000: The Ultimate Remote Network Administration Tool by Thomas DeVoss
- Back Orifice ButtPlugs and Goodies
- They Made Hacking Possible to Every Schoolkid - Cult of the Dead Cow Cool little video on the history of Back Orifice and cDc.
- Probing Remote Networks - Port scanning overview using a real host (FreeBSD) attack scenario, by Armageddon
- Hack Your Console - A look at some of the hardware and software utilities for making backups of your video game ROMS, by m0tion (James S. Wiggins, Email, Columbia, South Carolina)
- Cushioned Encryption and Deniability - Good mathematical overview of the "winnowing and chaffing" method in the RSA public-key algorithm encryption techniques, by Phunda Mental
- The Backyard Phreaker - Beginner phreaking (and security) information when utilizing telco terminal boxes, by D-Recz
- Expanding Caller ID Storage - Increase the memory on a CIDCO Model PA Caller ID box, by Datum Fluvius
- CLLI Codes Explained - Information and overview of the Bellcore Common Language Location Identification (CLLI) codes, by Crossbar
- Hacking RESNET - A look at the security of college camplus Residence Hall computer networks and the dangers of DHCP and unswitched networks, by jk
- Letters
- Warning - Lucy aka Baudewiser
- Store Section - Bluebell, N8, 4U2PN, flatline, Op_Code, Pixelated!, entropic, GW, Allegra
- Help Needed - JD (West Columbia, SC)
- Identity Problems - SaaWeetie
- Mitnick Feedback - Phlight, Wheetabix, Columbus, OH, MW (Solon, OH), Malkor, God of Dirt, mcd, D-Recz
- Church People - free radical, harris (Greece)
- Generic Feedback - Skippie the Ageless Hippie, Outlawyr, squarechin, ccure, Wraith, Keen, Alan M, Mac
- Clarifications - Cathode Ray, CKG, TS, Chris, xChEWx, iZRaXXX, Whirlwind, emory, MMX Killa
- Curious - Skeet, Neurotik
- Numbers - Infect
- Career Move - triplogik
- Surprised? - KB
- Questions - RepoMonster, VxPLaToNiUM, Nathan Hendler, Malbushsa, Arag0rn
- Incidents - Net X, datapleX (Daniel M. Robertson), darkrazor, SkidMarx (Gregory L. Marx), Tuxedo Mask, Zero_Null
- Facts - hhiggins, Lord Mistical (Cincinnati, OH), Louis Blue, Vex Hardline (Zen Master Vex)
- MetroCard Fun - Loggia
- Fun Sites - KRaZy d0h
- Still More FYROM Fun - Varelides Marios (An angry Greek)
- Screwing With Blockbuster Video - A look at the rental process at Blockbuster stores and a hack for getting store credit, by Hiemlich VonScootertraus the 53rd
- Blockbuster - 1993 This guy recorded himself walking around a Blockbuster for a movie night in 1993 and its so nostalgic.
- Screwing With Moviefone - Messing with Moviefone - including how to get free movies tickets, and even potentially free money!, by thirdhorse (Chris Miller)
- Screwing With Moviefone Original
- Screwing With RadioShack & Compaq - Messing with the demo display Compaq computers at RadioShack and Costco stores, by Informagnet
- Trunking Communications Monitoring - Part 1 - Monitoring information for trunked radio communications, by TELEgodzilla
- Trunking Communications Monitoring - Part 2
- Radio Scanner Modifications and Information
- Green Bay Police Radio IDs
- More on SIPRNet - Updated technical information on the government's Secure Internet Protocol Router Network (SIPRNet), by Ex-Eleven (John Tate)
- 2600 Marketplace
- 2600 Meetings
- Price: $4.50
- Issue's Cash Cow: Send us more money, Kevin Mitnick
- Cover (Cover Info)
- Back Cover Former Soviet Payphones!
- Kazakhstan This drab phone is a reflection of the monotonous life that awaits you in Kazakhstan. Photo by William W. Perkins
- Kyrgyzstan This bright and colorful phone represents the constant fun and dancing that goes on every day in Kyrgyzstan. Photo by William W. Perkins
- Armenia Drabness returns in Armenia. Photo by Derek Brown
- Belgium Found in Belgium, easily the most mysterious and misunderstood of all the former Soviet Republics. Photo by Vital Chaos
- Staff
- Download Unofficial Scanned PDF!
- Download The Hacker Digest - Volume 15!
$2600 Magazine - Volume 15, Number 4 (Winter 1998-1999)
- The Victor Spoiled - Editorial, plus Mitnick case update
- A Touch Memory Primer - Detailed overview of Dallas iButton Touch Memory devices, by Kingpin
- A Practical Introduction to theDallas Semiconductor iButton by Kingpin
- iButton Product Selection Table
- iButton Data Sheets & Application Notes
- The Facts of SSN - Social Security number information and prefix guide, by Kermit the Hog
- A Guide to VMS'pionage - A look at hacking OpenVMS systems using MultiNet, by EZ Freeze
- Samba: Lion King or Software Suite? - Overview and security of Samba shares and the SMB protocol, by VmasterX (Ron Belcher)
- Copper Pair Color Coding - A look at the infamous 25-pair color code, by Catatonic Dismay (Email #2, Email #3)
- A Security Hole at S-CWIS - Computer security holes in Student Campus Wide Information Service at the University of Nebraska - Omaha, by Phineas Phreak (Bryan Finger)
- Pocket Connectivity for Frugal Hackers - A look at using the Sharp Zaurus ZR-3500X as a portable hacking machine, by Mr. Curious
- Fun With NetWare 5 - A look at hacking Novell NetWare 5, which is suppose to be "Class C2" secure, by Khyron (Claude Johnson, LinkedIn)
- Novell Netware 3.X Exploits and Defense v1.4b, by Roger Black
- Become a Radio Ninja - A look at radio hacking and how (and why) hackers should get their amateur radio license, by Javaman (Adam J. O'Donnell)
- Cable Modem Security - MAC address security with cable modems, by Fencer (Dr. Faubert)
- How to Handle the Media - How to properly deal with talking to the media about hacking subjects, by nex
- 800-555 Carriers - 1-800-555-XXXX modem carrier scan, by MSD
- Letters - NON SPAM
- More on "Free" Software - (none given)
- Data - Pigano, nobody, Mark Milgrom, Nighthawk, KC, Shahn
- Questions - Rav0n, analyzer, smokescreen, Matt, Keebler, the medik, NAME, KLoWN, RANT-o-MATIC, RANT-o-MATIC, vsr600, Envision (Anaheim, CA), TydiLFuX (Wisconsin)
- RadioShack Antics - Jestah (Orlando, FL)
- Fun on the Phone - NERO, Knotfil, Innominate (Buffalo, NY)
- Religious Advice - Patrick, Deryc, Riddler
- Scary Stuff - jagxr
- Injustices - wrath, Toxygenn, hex
- Olympic Fun - Informagnet
- Miscellaneous Mitnick - denileofservice, Anthony T. aka SYCO, TetterkeT (Jonathan M. Wilcox), exhalibut, Shawn Morris, Timba Wulf, Eppie, snachbot, Little Bobby, Telephreak, Pago, Jade, DaRkSiDe (Richmond, Indiana), Desaparecido, Baaaa (Waltham, MA)
- Fingerprinting - The Fryar
- Barnes & Noble Feedback - J.A. Hasse, Bendar the Barbarian, cloak, Rachael (Chapel Hill, North Carolina)
- Between The Lines - Pete
- Help Needed - morbus, Col Pete
- Hotmail Fun - Feng Laser
- Non-Subscriber - Sandy
- 2600 To The Rescue - jeff
- In Defense of Microsoft - Count Zero Int
- Clarifications - Spoon, StuntPope, Dustin Decker, Rave669, Archive, D-Recz, Cslide, Frank (Seattle, Washington), Shaggy Dan, Frogman
- An Offer - st
- Military Madness - Dippy (Virginia), Virtual Vandal (Detroit, MI)
- Thoughts and Reflections - BurningWorld (New York), fl00dland, WG (Friday Harbor, Washington)
- Why Anonymous Phone Cards Aren't - Laws that can reveal phone card info and FBI testimony from the Timothy McVeigh trial
- The Cryptography of Today - A good overview of modern computer encryption using simple math concepts, by kriminal 3nigma
- Hacking the ATCOM Cyberbooth - A look at the ATCOM Cyberbooth and some tips for escaping their lockdowns, by Fever
- le firewall - A look at the Check Point FireWall-1 and general information on how firewalls work information, by Black Ice
- Phreaking in the Midwest - Phreaking story and information for Midwest states, specifically Illinois, by deth6 of the Bullz On Parade
- How to Hide From Netscape - Clearing your Netscape web browser cache and history, by J.P. (John Pierce "J.P." Cummins, Email #2)
- 2600 Marketplace
- 2600 Meetings
- Price: $4.50
- Issue's Cash Cow: Kevin Mitnick
- Cover (Cover Info)
- Back Cover Historic Foreign Payphones
- Chile Found in Valparaíso, this Chilean phone could have been used by dictator Pinochet to call the CIA collect for instructions. Photo by Vladimir Sanchez
- Cambodia This phone was seen in Phnom Penh, Cambodia and is rumored to have been used by Pol Pot himself for anonymous prank calls. Photo by Celia Johnson
- Sri Lanka Nuwara Eliya, Sri Lanka. Said to be the very phone where Arthur C. Clarke calls the DEFCON voice bridge from. Photo by Celia Johnson
- Turkey From Izmir, Turkey - the ancient city of Smyrna. Supposedly used by Selim I in the heyday of the Ottoman Empire (not verified). Photo by Tom Mele
- Staff
- Download Unofficial Scanned PDF!
- Download The Hacker Digest - Volume 15!
$2600 Magazine - Volume 16, Number 1 (Spring 1999)
- The Big Time - Editorial
- Tracking Your Vehicles with AVI & ETTM - Detailed info on Electronic Tolls and Traffic Management (ETTM) toll systems, by Thomas Icom
- AVI, ETTM, and E-ZPass: A Look at ITS Systems Original
- Big Brother on the Boulevard by Thomas Icom/IIRG
- Cracking the TIME-BANC System - A look at the Westview Instruments TIME-BANC employee time system and its default 4-digit passcodes, by johnk
- A Retail Target - Overview of the Target retail store computer systems, PA system, and Guest Service door codes, by Luna
- Wreaking Havoc with NetBus - Overviews of using and installing NetBus, a program used to remotely take control of Windows computer, by Sikdogg
- More Socket Programming for Fun and Profit - Overview and code examples for TCP/IP socket programming and example code for a Window 95 NetBIOS nuker, by Darknite
- Code: nuker.c
- Code: sock.c
- Socket Programming for Fun and Profit
- Internet Peering - Info and politics on "behind-the-scenes" Internet linking and peering backbones, by The Prophet
- Fun With Tripwire - How to bypass the Tripwire checksum-based computer security system, by Estragon
- The Design and Implementation of Tripwire: A File System Integrity Checker
- Understanding and Installing Tripwire
- tripwire-1.1.tar.gz
- tripwire-1.2.tar.gz
- tripwire-1.3.tar.gz
- tripwire-2.3.0-50.tar.gz
- A Hacker's Guide to Getting Busted - What to do if you are busted by the cops and an overview of your Constitutional rights, by Outlawyr (Mark Weissburg, Chicago, Illinois, Twiter, Facebook)
- Letters - Express Yourself
- Fun At The Retailers - Paladine, cili_ra/bit, Anonymous, a|chEmist, gabo, gLyKOgen
- Tracking Clive - Reapyr, Lakota
- Blockbuster Facts - mark h, DiGi_TaL
- Concerns - ICON, KaptainKool (Brett Johnson), DVS, Uneasy Rider, LiquidCache (Jason Murphy, DOB: 04-08-1984), Central Intelligence Agent #23642
- Bookstores - Jack Dangers, L.A.N.-master (Elgin, IL), Ray Dios Haque (United Phreak Syndicate), Simple Nomad, gonzo
- Phone Exploration - Dave, msdaisey, matrix bomb, Telesis, Liquid Fire, pokesmote/Lindsay^, maxm0use (Owosso, MI)
- Praise - Dre, Kanemura, Jean Dupree, Schism, SPECOP002
- Mitnick Reactions - Dr. K, C.D., Phone Bandit, Phrostbyte
- Foreign Interests - Fransico Franca Arraes, marko c, Pabst
- Security Issues - chown 2ME, comet
- ADSL Report - Perogie
- Questions - Quantex, Savage, OkornO99, Satire, Cooldek, Phredde
- Hacking Moviefone - killerclown
- Federal Interest - jason head
- Color Coding - Joe630 (Ben Sherman), todd, Seuss
- The Newbie Threat - ddhd
- SSN Corrections - Loki128, Gareth Davies, fin, Zool, teclo, Charlie
- Netscape Issues - defen, t.d.m.
- Hackers At War - Splat, Rue-the-Day
- Y2K - Zack
- Observations - Frosty, MSD, SD, John Q Sample, Rev. Randall Tin-ear (Randall Fleming)
- Cable Modems - James Carlson (Lexington, MA)
- Netware Feedback - godbox, Buzz
- SS7 Explained - A good overview of Signaling System No. 7 and what happens in your central office after you pick up the phone and dial a number, by Friedo
- Network Scanning with Nmap - General overview and scanning tips for using Nmap, by rain.forest.puppy (Jeff Forristal)
- News Update - Various news bits
- Hacking a Sony PlayStation - Overview of installing a PlayStation mod chip so it will play copied or "foreign" games, by Flack (Robert Patrick O'Hara, Yukon, Oklahoma, DOB: 08-22-1973)
- 2600 Marketplace
- 2600 Meetings
- Price: $5.00
- Issue's Cash Cow: Computer security is either good or bad, depending on how much money Evil Corley needs that month.
- Cover (Cover Info)
- Back Cover Payphones From All Over
- Tashkent, Uzbekistan A typical Soviet style phone with a Touch-Tone keypad modification. Photo by Tom Mele
- Zagreb, Croatia One of the few phones we've printed where you can actually read the number! And yes, it does take incoming calls. Photo by Hanneke Vermeulen
- Salatiga, Indonesia A small city in the Central Java region. This phone takes only coins and is said to be extremely frustrating. Photo by Tigerboy
- Bishkek, Kyrghyzstan One of the more modern card reader phones. Photo by Yury
- Staff
- Download Unofficial Scanned PDF!
- Download The Hacker Digest - Volume 16!
TAKEDOWN: Number of crimes documented : 2 Number of meals documented : 42 $2600: Number of good articles : 2 Number of TinyPedoAds® : 42
$2600 Magazine - Volume 16, Number 2 (Summer 1999)
- A Culmination of Efforts - Editorial
- Securing Your Linux Box - Steps to for the beginner or experienced user on securing their new Linux installation, by miff
- How to Secure Your Linux Box Original
- More on SIPRNet - Overview of the Secure Internet Protocol Router Network (SIPRNet) used by the U.S. military by an Air Force insider, by Happy Harry
- Hacking AS/400 - Discusses the IBM AS/400 mainframe including preset user IDs, default password policy and some useful commands, by radiat
- Fun at Costco - A quick look at Costco's AS/400, or "green screens," including an options overview and login/password information, by nux
- Brute-Forcer for Tracer - Brute-forcer for dial-up TRANE Tracer building automation system control hardware found at most big shopping stores, by J-lite
- Code: tracer.c
- Even Better Still
- Broadband via the Earth - Broadband radio/data transmissions using the Earth (conductive soil) itself as a conductor, by saint (David)
- Secrets of Copy Protection - Overview of how various hardware and software copy protection schemes work, and a look at what it takes to bypass them, by root access (Data War)
- How Parents Spy on Their Children - An overview of computer usage monitoring programs and One Tough Computer Cop software, including its keyword search list, by Demonologist
- The Future of IPV6 - A look at how IPv6 addressing works in comparison to IPv4, by rift
- Letters - Chatter
- Offerings - flatline, Douglas
- Revelations - ZeROLogiKz (Michigan), ronwarren, Justin, Rufus T. Firefly, charr (Atlanta, GA)
- Responses - Ethan LaPan, Fencer
- Fun Numbers - maxm0use (Owosso, MI), Remy, PhuzzBoi, Mike
- Secrets - ethan (army.mil)
- Gripes - ICE breaker, RGBKnight, K2, shinobi, Matt Lesko
- Tales of Injustice - marbike, Outbreak
- Retail Tips - Fredrick 860, Sylex
- Cries for Help - TOPACE12
- Flush Out Religion - Joe Sixpack
- Mischief - Anonymous, the ninth name is NOD
- Clarification - baalse, Lucky225, NoDiCe, Elite
- Supplemental Info - Corey, ts, Corban, Scoop, rain.forest.puppy, MMX, Justin (Memphis, TN), Anonymous, Charon, F00bar98, matt, techs, The WildCard & |SC|
- Military Mentality - aeglemann, USN Sailor & ModG, Surreal
- Education - Made in DNA
- Miscellaneous Mitnick - RomeoW, Static-Pulse, Payphone, Chris, David, Ed in CT, toneboy1700, EchoMirage
- Mysteries - shine, niceroova)
- Foreboding - SLATAN, Mars
- Feedback - pArtYaNimaL, olsonjv, tk, brm, Grey Ghost, oolong, First_Incision, mgs21, Phred, xdissent, r0uter
- Advice - LeeTKuRp of HoC, Karen, CorLan
- Pure Stupidity - pretzelboy
- Reassurance - (none given)
- General Weirdness - ICON
- Chutzpah - Robin S (White Lake, MI)
- How to Keep Parents From Spying - Tips minors, or others, can use to prevent parents from monitoring their Internet, computer, or real-world activities, by JediMaster666 (Phillip Benoit)
- Food for Your Brain - Finding personal info about users using public information from services like IRC, by DJ Tazz
- Adventures With Neighborhood Gates - Overview of the "phone call" security-controlled gates commonly used in gated communities, by jaundice
- Internal Hacking - Story of a person hacking an internal business computer system (Lotus Notes) to check the salaries of other employees to see if he was being underpaid, by Zenstick
- Batch vs. Interactive - Overview of the different types of computer jobs processing systems, by StankDawg (David Blake)
- Manipulating the Aspect - A look at the the Aspect CallCenter automatic call distribution system, including account login and password information, by HyTeK
- Push-Button Lock Hacking - Programming and code reset information on the Benton T2 DL2700-Series electronic push-button locks, by Clawz
- 2600 Marketplace
- 2600 Meetings
- Price: $5.00
- Issue's Cash Cow: Kevin Mitnick
- Cover (Cover Info)
- Back Inside More Payphones Than Ever
- Armenia #1 These are mostly generic Russian phones. They look stunning in pink, don't they? Photos by T. Mele
- Armenia #2 "
- Laos #1 From the mysterious nation of Laos. We're told that the phone book for the entire nation is only two inches thick. Photos by Magicman
- Laos #2 "
- Back Cover Even More Payphones Than Ever
- Germany #1 Evolution in Germany. Slowly, coins are being abolished and replaced by cards. Photos by Hanneke Vermeulen
- Germany #2 "
- Yugoslavia #1 Diversity in Yugoslavia. If such radically different phones can coexist on the same network, surely there's a lesson to be learned for us humans. Photos by Hanneke Vermeulen
- Yugoslavia #2 "
- Staff
- Download Unofficial Scanned PDF!
- Download The Hacker Digest - Volume 16!
$2600 Magazine - Volume 16, Number 3 (Autumn 1999)
- Slow Motion - Editorial
- Upload Bombing - Web server attack exploiting CGI holes by pretending to be a web browser uploading a file, by Ulf of VSU (Vanliga Skötsamma Ungdomar)
- Code: upload-bomb.pl
- Killing a File - How to thoroughly remove a file from a computer - including removing it from the swap file, by THX1138
- The Terrorist of Orange, Texas - Story from Texas about a high school student labeled a potential "terrorist," by The Abstruse One (Darryl Mott)
- ITS Prison Phones - Information about the Inmate Telephone System used by the Tennessee prison system, by ElecRage (John Schang)
- Infiltrating MediaOne - Quick overview of a MediaOne Express cable modem installation - the default account password is "password," by Lobo The Duck
- PalmPilot's Canadian Red Box - PalmPilot program for generating Red Box tones used in Canadian payphones, by CYB0RG/ASM
- Forging Ping Packets - C source code to forge ICMP echo requests under *BSD, by /bin/laden
- Code:forge-ping.c
- Similar Code: echospoof.c ICMP_ECHO Spoofer, by Javaman
- Trunking Communications Monitoring - Part 2 - More info on scanner add-on hardware devices and software for monitoring trunked radio systems, by TELEgodzilla
- Trunking Communications Monitoring - Part 1
- Radio Scanner Modifications and Information
- Green Bay Police Radio IDs
- Internet Radio Stations - Running your own Internet "radio" station by using a RealAudio server to stream your broadcasts, by -theJestre- (Carmel, California, Chris Marland)
- Quantum Hacking - Info on quantum computer hacking and the OpenQubit project, by skwp (Yan Pritzker)
- Protel COCOTs - Info on hacking Protel COCOT payphones with the dial-up feature, by HeadTrip
- Beating Protel's Programming Security Code by MaNiAK
- Programming Protel Phones by El Jefe
- Programming Call Routes Using Protel's ExpressNet Software by El Jefe
- Protel Payphones Parts & Support
- Protel Software ExpressNet III
- ProNet v3.211 User's Guide
- Assorted Disney Fun - A look at bypassing the Full Armor protection software installed on some of the computers at Epcot Innoventions, by Hacks
- More Disney Fun - An overview of the Magic Kindom tunnels used by the cast members, by Madjestr
- Letters - ENUNCIATIONS
- Clarifications - Barcode, RS, still nobody, Falcon, twiztid, joe cool, John Belushi, rj, Meth_od, Sunshine
- Venom - None of your Damn Business., alex
- Guilt By Association - icon, napalm, artiedeco
- Retail Hacking - KeMo BoY, caesar gaius caligula, Drifter, Yerba AKA Willy L., xprotocol
- Phone Trickery - payphone, Jonathan Fredericksen, Iineside, SSTcobra (Atlanta, GA), Loggia, Rolan
- Dissatisfaction - Dementia, Entropic (Dallas, TX), M0leBrain, cookiesnatcher
- Free Kevin - crypto, Lord Maestro, Brother Inferior, Fire Drake, Skyppey the Hyppey (Canada), Joe Blow
- Foreign Phones - Psychedelia, MD_Yugo_NSM
- Conspiracies - name withheld because I can't think of a good one, FeuErWanD, namib1234, ghostriter, john doe
- Discoveries - Weber, EKo, admintemplate_, finn, Calis, BBrain (Boston, MA), timm
- Hunting For 2600 - Phreakilation, SAR, GB
- Y2K - RB, R.B.
- Game Playing - Mike (Seattle, Washington), AllOut99, mad cow disease
- Corporate Expansion - james hall
- Hiding Things - SCUDS
- Info Wanted - caffeine, tnsecure, Bazz
- Stealing - SpeedDRaven (Carl J. "Byron" Speed)
- Ad Policy - Eric W.
- Secrets - Seraf
- An Overview of Cellemetry - Cellular phone-based telemetry technology designed to monitor, control, and track anything that is worth being monitored, controlled, and tracked, by Jinx (Johnny)
- Solaris x86 for Plants - Overview of installing Solaris 7 on an Intel x86-based system, by Javaman (Adam J. O'Donnell)
- Satellite Watch News Shutdown - Forced to shutdown by DirecTV.
- 31337-isms - Something prevalent in the hacker community is occasional, or sometimes nauseating, use of k-leet characters in communication or hacked works of art, by Hex (Jarrod Eyamie)
- 2600 Marketplace
- 2600 Meetings
- Price: $5.00
- Issue's Cash Cow: Kevin Mitnick
- Cover (Cover Info)
- Back Inside FREE KEVIN Sightings
- FREE KEVIN #1 Photo by Michael VanElsander
- FREE KEVIN #2 "
- FREE KEVIN #3 Photo by Steve Norris
- FREE KEVIN #4 "
- Back Cover Non-American Payphones
- Basil, Switzerland Photo by Dan Scheraga
- Lviv, Ukraine Photo by Jerry Dosko
- São Paulo, Brazil Photo by Claudio Carlquist
- Holguin City, Cuba Photo by Unknown
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 16!
$2600 Magazine - Volume 16, Number 4 (Winter 1999-2000)
- Violence, Vandals, Victims - Editorial
- Accessing Forbidden NTFS Drives - Circumvent security on a Windows NT machine by booting from a Trinux Linux floppy, by Number Syx (Chris Stoddard)
- Trinux: A Linux Security Toolkit
- Trinux: A Linux Security Toolkit - Distribution Mirror Trinux was originally released by Matthew Franz in 1998. The collection includes floppy boot images, ISO files, kernel modules, and documentation.
- Trinux FAQ Version 0.2
- trinux-070 Trinux 0.70 distribtions. You'll need three formatted floppies.
- 2.4.19-modules Trinux/Linux kernel 2.4.19 pre-compiled modules.
- ntfstools.tgz NTFS tools for Trinux
- RawWrite for Windows (RawWrite v0.4 [Win], RAWRITE2 Ver 1.1 [DOS]
- How I Recovered an Unbootable NTFS Windows System
- Security Through NT? Not Likely - An overview of accessing remote shares on NT systems and a look at potential security holes in Windows NT and Microsoft networking, by Kurruppt2k (Email, DOB: 05-01-1986)
- Virtual Acid Gold Virtual Acid Gold is a program meant to damage the victim's machine, by Kurruppt2k
- Virtual Acid 1.0 by Kurruppt2k
- SiliconMantis v1.0 by |<urruppt2k, April 1999
- Countermeasures Revisited - Use a milliwatt plant test number (or DATU), an inductive probe, and a ohm/capacitance meter to find phone taps or "unauthorized" extensions, by Seuss
- DATUs - The Tool of the New Age Phreak - Detailed info on Harris DATUs, by MMX
- DATUs - The Tool of the New Age Phreak Original
- Supplemental Files Missing a few.
- Display-Based Control Mechanism Resident in Portable Test and Communications Device for Facilitating Craftsperson's Remote Testing of Selected Portion of Telephone Network U.S. Patent No. 5,528,660
- Direct Access Test Unit for Central Office U.S. Patent No. 4,841,560
- Direct Access Test Unit for Central Office U.S. Patent No. 4,670,898
- Direct Access Test Unit Loop Conditioning (DATU-LC) Model 2482
- Messing With Staples - A look at the phone system, "ribbon finger," and security/shoplifting protocols at Staples stores, by Maverick(212)
- I Own Your Car! - Story from some "soon to be laid-off" employees at a large car manufacture infiltrating a "restricted" area and taking a secret prototype (Chrysler PT Cruiser?) for a drive, by Slatan
- Telco-Babble - Why it pays to leare the phone wiring color code and binder info, by Android
- An Intro to Paging Networks and POCSAG/FLEX Interception - Good introduction to what is required to monitoring POCSAG/FLEX pager network traffic, by Black Axe
- An Intro to Paging Networks and POCSAG/FLEX Interception Original
- RF Resources by Black Axe
- Pager Programming, Monitoring, and Applications
- Beginners Guide to POCSAG Pager Decoding
- Hack the Media - An insider's perspective to fighting today's mainstream media lies and tips to getting the truth out when dealing with them, by Jim Nieken
- Letters - PEOPLE WHO CAN'T KEEP QUIET
- Inequities - Ackbar,
- The Politics of Hacking - Desaparecido, phillip, TeckX3, Major Motoko
- Difference of Opinion - Jeffrey Seelman (Milwaukee, WI), Da "Sleep"
- Mitnick - EchoMirage, skaboy, Don L, CherryPie,BADJRM, matt, Darth_tampon, Suicidal
- Stupidity - kipple, Jack O'Lantern, Dr. Bagpipes, c. edward kelso, Arcoddath (Scotland), Anubis
- Handy Stuff To Know - J. Arthur Ballarat (Los Angeles, CA), mad kow diseez
- The High Cost of Learning - gpf, hightechno, Valen
- Mysteries - drdoom, Jack
- Hotmail Hijinks - Shaun (Memphis, TN)
- Retail Tips - WillyL. AKA Verba, SenorPuto, creature, kAoS, Sirblime, Loggia, dannyh, Sir Reginald, Wisbing he was back in New York, ScOOter, emdeo, Eil, SAR, hidden101, CaS
- Suggestions - Black Knight, Russ, sureshot
- Ripoff - Larry, errorshutoff, Dumah, Snot Gnome, Shawn, Dissolution X, Graphix, Websurfer
- Questions - Val, Infinet
- MTV - Skanarchist (Eddie), i_ball, techx3, UnclePhester9600
- Barnes & Noble Memo Found? - Mangaburn, Dawn Bates (Muskegon, MI)
- Fun Stuff - Slack Packet
- Stories of the Past - Brien
- How to Create New Urban Legends - Creating your own myths and urban legends and how people manipulate the truth on the Internet, by Jim Johnstone
- Denied Mail - Letter of rejection for Kevin Mitnick's prison mail, which was just a print-out of emails people sent to him.
- Hacking Explorer (the car) - Hacking Ford Explorer's keyless entry system, and a potential bug to reduce the keyspace, by Bob
- Net Nanny Nonsense - A look at the Net Nanny Internet monitoring program designed to allow parents to monitor and restrict their children's computer usage, and some simple ways to defeat it, by Raz
- Why Red Boxing Doesn't Work - The removal of the Automated Coin Toll Service (ACTS) via the Telecommunication Act of 1996, by The Prophet
- Spoofing Call Waiting ID - Simple little trick to send fake Caller ID data during the call waiting phase, by Lucky225 (Jered Morgan, Email #2, Facebook, Medium, YouTube)
- Spoob Spoonm's open-source Orange Box Perl script.
- Caller ID Basics by Michael W. Slawson
- Software Orange Box (S.O.B.) v1.9.4
- The Sprint Integrated On-Demand Network - Info on Sprint's new Integrated On-Demand (ION) data and "unlimited phone line" network, by Prototype Zero
- Sprint Unveils its Integrated On-Demand Network
- Sprint Unveils Network Strategy
- Sprints ION the Future
- Sprint Shuts Down On-Demand Network
- Understanding Microsoft Exchange - Overview of Microsoft's Exchange server and understanding its connections, authentications, and potential exploits, by PayLay
- 2600 Marketplace
- 2600 Meetings
- Price: $5.00
- Issue's Cash Cow: We'll see many more individuals whose punishment far outweighs their crime and we'll see the media distort the facts time and time again.
- Cover (Cover Info)
- Back Inside FREE KEVIN Sightings
- Free Kevin Looks like our campaign has gotten successful enough for Madison Avenue to take notice. Or whatever the British equivalent of Madison Avenue is. This comes from a recent mailing blitz organized by Cable & Wireless. It's so nice to have one's ideals commercialized.
- Back Cover Foreign Payphones
- Santiago, Chile #1 Living proof that a bright red phone always brightens up a street. Photo by Sol Perez
- Santiago, Chile #2 This is what that ugly metallic shine will get you - glare and lots of it. Photo by Sol Perez
- Athens, Greece Found at the base of the Parthenon. Photo by Peter Photopoulos
- Kyoto, Japan An ISDN phone that looks too intelligent for its own good. We wouldn't be surprised if it speaks. Photo by eclip5e
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 16!
$2600 Magazine - Volume 17, Number 1 (Spring 2000)
- The Next Chapter - Editorial (css-auth.tar.gz)
- A Taste of Freedom - Post-prison letter from Kevin Mitnick, by Kevin Mitnick
- How to Stay a Sysadmin - Overview of tips and tricks for computer system admins to prevent burnout or to make their job easier, by Shade (Paul A. Watson, Resume)
- Military Computer Secrets - Military computer (Naval Aviation Logistics Command Management Information Systems [NALCOMIS]) tidbits, by Suicidal
- NALCOMIS and the Aviation Maintenance Analyst by Glenn J. Boston
- NALCOMIS/OMA: Functional Considerations for Automating Organizational Maintenance Activities by Ronald T. Allen
- Securing Websites With ASP - Security tips (cookies, session IDs) for securely writing web pages for database-driven websites using Microsoft IIS/AS/SQL, by guinsu
- Still More on SIPRNet - More info on SIPRNet and some of the hardware used for the Navy's "Information Technology - 21st Century" project, by Phrostbyte (Kevin Wahl)
- Finding and Exploiting Bugs - List of points to keep in mind when searching software and code for potential bugs, by Astroman66 (Andrew Lance)
- All About SecurID - Overview of Security Dynamic's SecurID token, by magus (Steven Beverly)
- SecurID - Info on the SecurID protocol and real-world usage, by xenox
- Your Internet Birthday - Privacy reasons for giving out a "fake" birthday when filling out forms on the Internet, by The Cheshire Catalyst
- When is Your Internet Birthday? Original
- Make Spammers Work For You - "Spamming spammers" by trying to track down details of their operation and personally contacting (or harassing) them, by Chatreaux
- Taking Advantage of AllAdvantage - Exploiting the AllAdvantage system which pays you to surf the Internet by using automated web browsing macros, by silicon kill
- More Advantages of AllAdvantage
- AIM Keys 6 User's Guide
- AIM Keys 6 Evaluation Copy
- AT&T's Gaping Hole - Exposing a glich to get free phone service with AT&T wireless service by activating a prepaid phone via a "regular" cell phone number, by Jinx
- Cellular Networks Detailed - Detailed info on various new digital cellular protocols and network, by EchoMirage (Englewood, Colorado, Email)
- Letters - WE'RE LISTENING
- Alien Intelligence - CgK
- Bookstores - Downsouth, Anonymous Barnes and Noble Music Seller, quash
- Adventures in School - Xkaliber, P2129 - the student formerly known as Kevin, phil, gopher the contradictory, Microkiller
- Discoveries - darky0da, casey, Handle6015, Mongo, brain, robert, Dr. K, carls_pub
- Kevin Free - Koishii, KuNg, Chris from Chrisconsin, ASZ, Rave669, VinceC, r00t_Canal
- More on SecurID - Kingpin
- More Fun in Retail - Anguirus, The Wedge, cashmolia, MustardMan, Phelix, cashmolia, Jack A. VanWoerkom, squatex
- Anti-Venom - The Devil
- Additional Details - netsplit, Cilo, Platinum Dragon
- Defeating Corporate Advertising - orn, Alpha
- Help Needed - xequalsl, Dan Wheeler, Lubdub
- State of the Hacker World - Pestilent, Mind Plague of The Committee, JL, phiber_life, Quantum Knight
- Positive Developments - ph0x
- Idiocy - wNdozCRASH, tacit
- Humor - Rick
- Forbidden Exchanges - .244
- The MPAA Lawsuit - Michael F. Nudell, Punker04, Anonymous (London), Apocalyse, Wayne, Pay_No_Attention_To_That_Man_Behind_The_Curtain!
- Y2K Issues - Desaparecido, AssMonkey, Gustaf, CubanPete
- Facts on NT - RickDogg
- Irony - Knightsabre
- Free Stuff - Twist (Tripwire Exploit Poster)
- Question - scorchmonkE
- 2/6/00 - MeSSerSchMiTT (David or The "RUSSIAN" as I get called in USA school), Rhymezor
- DoS Cluebags - Keith Gardner, Andrew, Cooter, Jason (Louisiana)
- How PSX Copy Protection Works - How PlayStation PSX copy protection works, by Lord Xarph (Tod Weitzel, San Jose, California)
- Fun at Circuit City - Secrets of Circuit City's price labels and an overview of their internal telephone system and extensions, by ccsucks
- How to Build a Coffee Box - Combine a Beige Box and Brown Box, by skrooyoo
- The Sprint PCS Network - Tech info on the Sprint PCS cellular network, by ~sn0crash
- How to Get Banned From Your ISP - Common sense tips to avoid being kicked off your ISP, like not send spam or exceeding file transfer limits, by Mandark
- Build, Don't Buy, Your Next Computer - Several tips for building your own high-quality computer system, by bober
- How Does That DSS Card Really Work? - Brief overview and technical details of the operation of DirecTV DSS cards, by Phredog
- 2600 Marketplace
- 2600 Meetings
- Issue's Cash Cow: The MPAA is suing $2600 Enterprises over them linking to a copy of the DeCSS source code.
- Cover (Cover Info)
- Back Cover Asian Payphones
- Bangkok, Thailand This phone looks like it's been through an awful lot. Photo by MC Telecom
- Tokyo, Japan Will ISDN payphones ever be a common site in the States? Photo by MC Telecom
- Shanghi, China A true work of art with the phone number proudly displayed. Photo by Julian
- Beijing, China Happy telephone workers. Photo by Julian
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 17!
$2600 Magazine - Volume 17, Number 2 (Summer 2000)
- Madness - Editorial
- The Art of System Profiling - Overview of some of the tools used for identifying operating systems and network layouts on the Internet, by Thuull
- A Brief Intro to Biometrics - Overview of various biometric-based physical security systems and upcoming technologies, by Cxi~
- Fun With TDOC - Information on the Tennessee Department of Corrections computer network and the Tennessee Offender Management Information System (TOMIS) system, by Anonymous
- State of Tennessee: Integrated Criminal Justice Portal Help and FAQ
- Tennessee Offender Management Information System (182k PDF)
- Strange Abuses for Your Home Phone - Info on a Conair HAC SW8260 phone, by Static (Brandon Malzahn, Email #2)
- More Advantages of AllAdvantage - More info on All Advantage and how to disable ads, by KireC
- Over the Verizon? - List of 706 Internet domains registered by Verizon
- Securing ASP: A Deeper Cut - Overview of tips for securing ASP-based websites, by AgentK (Kent Tegels, Omaha, Nebraska, Email)
- Jello Biafra: Hacker Ambassador - Clueless, rich, hypocritical, media whore - sounds just like Evil Corley, by princessopensource (Shana Skaletsky)
- Hacking the Three-Holed Payphone - Technical overview of the Bell System three-hole payphone, and a look at some of the infamous hacks for this phone, by Munzenfernsprechermann
- Packet Analysis and Header Sniffers - General overview of packet sniffing for header identification and a good low-level Internet protocol overview, by Javaman (Adam J. O'Donnell)
- Code: headers.c A program to display packet headers sniffed off the line. Uncommented.
- Letters - DANGEROUS THOUGHT SECTION
- Clarification - Kevin V (Trenton, OH), Treker, Einstein, Mark, Transmissions from the South
- Getting Around Stupidity - Dr Jest, Karr0t T0p (Kristoffer William Marshall, DOB: 05-13-1984), phil, sonnik, GhettoBlaster (Jason Louisiana)
- Discoveries - Squee, Allin, Elektr0chr0nik, bill
- Car Talk - Devil Moon, The Artful Dodger
- Annoyances - thegeek (Glasgow, Scotland), Funk Strings, 2MnYiDiZ, ryan
- Retail Tips - SnoFlak, gasfumes, Cybah
- Additional Info - Immolation, mbve, Qwertydvorak, DAR
- Dealing With The MPAA - Scott, Sys Edit, mr. blonde, Mr. Roboto, Jedi's Chaos, Daewoo, g00fy, steven az (heretidpogo)
- The Mitnick Case - Sienne (805), Technomatrix, Speedk0re (Gary Kuhlman, Irvine, CA)
- Fun With Cable Companies - RootX11, jjjack, Rizzn Do'Urden (Mark Hopkins)
- Info Needed - Popeye
- School Update - Izubachi, Eric S., Code_WarriorX, cs0074life, Blooder, ICMP
- Criticisms - Patrick, cryptofreq, The_36th_Chamber, dustbert
- Helping New People - Notmyrealhandle
- Ideas - MrBid
- Injustices - Anthrax, SHemp5150 (Shaun Kemp), KoDo, diss0nance
- Starting a New Meeting - NuLL vaLue, neurophilter
- Praise - Dave (New York, New York), Da Clyde, 3_trinity_3 (Shawn McCullough, San Antonio, TX)
- ANAC Number - Goop, PaleronD
- Media Misrepresentation - phil
- The Staples Threat - Cielo, Maverick212
- Y2K - Mojo
- True Security - pulse (Tony Brown)
- Listening In - zzflop
- Female Hackers - MiStReSS DiVA (aka-Beui)
- Desperate - From a Wanna be Hacker
- The Verizon Threat - majickmutex
- A Simple Hex Hack - Windows registry hex editing (date editing) to defeat time-limited software trials with a specific example using Hex Workshop v2.54, by Zarathustra
- Secrets of Dell - Secrets of Dell tech support, what to look out for when ordering a new Dell, or returning your hardware, by Deamtime
- Del ZZTop Software Restoration Utility Dimension - NT4/Win98 / vA00
- How Domains Are Stolen - The potential for domain name hijacking by sending spoofed emails, by Crim, Redomega
- Playing With Dominos - Explaining some of the more confusing points about Lotus Notes/Domino, and a potential DoS email attack, by Dr. Clue
- Java Applet Hacking - Exploit password-protected web pages via information revealed inside a public Java archive file, by Xprotocol
- The Privacy Box - The purpose of this box is to add a measure of privacy to your phone calls. It does this by blocking your phone when someone else in the house picks up another phone on the same extension, by obitus
- Hacker's Information Report Issue #2 - Revised Fuschia Box
- A Student's Privacy Security Survey - Survey of private student information at California State University, Chico college and how it is protected, by Pip Macki (Mike S.)
- 2600 Marketplace
- 2600 Meetings
- Price: $5.00
- Issue's Cash Cow: (((Corporate America))) has gone mad with litigation and its obsession with the Net.
- Cover (Cover Info)
- Back Cover Global Payphones
- Taipei, Taiwan This thing truly scares us. Photo by MC Telecom
- Turku, Finland Note the funky coin mechanism on the top and the extra long cord. Photo by Chase Brown
- Freeport, Bahamas Amazing what a little color can do. Photo by Pentastuy
- Ch'ongju, South Korea There's a lot going on here. Photo by C. Jacques
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 17!
$2600 Magazine - Volume 17, Number 3 (Autumn 2000)
- A Summer of Trials - Editorial
- Kernel Modification Using LKMs - Detailed article on creating hidden loadable modules to alter a running Linux kernel, by dalai (Josh D.)
- Code: wipemod.c
- How to Hack Cyber-Time Software - Admin password hack for Cyber-Time - a Internet cafe/kiosk time usage management system, by Waphle/Managahtzul
- Legal Threat From CBS - Letter sent to $2600 over a domain name.
- Target Advertising - Advertising notes and how advertising can be seen as propaganda, by Hiemlich VonScootertraus the 53rd
- An Introduction to Sprint ION - Overview of Sprint's Integrated On Demand (ION) Network voice and data system, by The Prophet
- The Geospatial Revolution - A look at using Geographical Information Systems tied with various databases (e.g. E911) and the data they provide, by Silvio Manuel
- Anomaly Detection Systems - Part 1 - Exploring the general concepts behind intrusion detection, a means of classifying intrusion detection systems, and a brief outline of a simple passive/host-based intrusion detection system on a Linux platform, by Thuull
- Hunting the Paper Carnivore - A look at the FBI's Carnivore email scanning system and how it infringes on our rights, by BrotherBen
- AskCALEA Mirror of askcalea.fbi.gov
- Letter From Warner Bros. - Asking for permission to use $2600 issues in the movie Swordfish.
- The Making of a Pseudo-Felon - Story of a person caught scanning for "codes" and the hell the Secret Service put him through for such a minor incident, by Brent Ranney
- Flaws in Outsourced E-Commerce Systems - Potential security problems with e-commerce sites, specifically websites which use third-party credit card processing, by Dean Swift (Dandalf, Harlesden, London, United Kingdom, Email)
- Letters - READER DROPPINGS
- How Verizon Sucks - Jeff, Kendall, Filthytot, Alterego, AM, Trouble Maker from WayBack
- More Corporate Intimidation - 7h3 31337 pHr34k4r0id, LoC, dot, robin, J-Fast, Secret Squirrel
- Answers - drakiel
- IRC Bitching - Muckraker, FLAMEcow
- H2K Videos - Hedgecore
- Questions - Phuct, kamal abbas, Theseus, Wolf
- DeCSS/MPAA/DMCA - Matt, Anonymous in Ireland, William, beezle, Brad Brown, phil, Decius 6i5 (Tom Cross), Scott, William Ryan, happitree, oddyOphile (Portland, Oregon, DOB: 05-10-1974), Quikfuze, Blanked Out, Woody
- Misconceptions - phx
- More Info - SLATAN, Will, Dave (Adelaide, Australia), jeremy, Cafeeen Boy, Mr. Roboto, Bowman, Court Jester, WStend, Immolation, kram12085, guinsu
- Bypassing Napster - Hedgecore
- Mitnick - illii, ReNt12596, Bill Dahab
- Reprinting Stuff - Jason Benton
- The Old Days - Akolade
- More Government Stupidity - Chad Ziccardi
- Bookstores - vesparado
- Observations - SuperHacker@aoI.com, COMTek, watice, Aulophobe (Phoenix, AZ), Kevin V. (Trenton, OH), Luminol, Stealth Ricochet, Queen Ann
- Lotto Fever - b0b126, DigitalZero
- The Dangers of Info - rootx11
- Phone Problems - Maria, Roark, Silverspartan
- Schools - Anonymous Hacker in England, SwordMage, YorNamHere, Herbert, SSGohan, Tweeter
- Fast Food Facts - Big Mac
- Credit Files - LoAN RAnGER (Colorado)
- Threat Letter From Microsoft - Microsoft accuses $2600 of software piracy, without any proof.
- Finding a Target Using DNS Lookups - A look at some DNS tooks for mapping out host and network layouts under a particular domain, by fU9A5i
- DNScape 1.1 DNScape 1.1 is a name and address search tool for Internet addresses. It can be used by system administrators to verify the configuration of DNS tables and can be used by anyone to track down pesky spammers. Just type in the IP address you find from the headers in an unwanted mail message and retrieve all the information available from DNS on that IP address. You can extract the associated mail server and send mail directly to the administrators to warn them that a spammer is using their site.
- Another Way to Defeat URL Filters - Use a host's IP decimal equivalent to bypass web filters or URL blocking software, by ASM_dood
- Code: url-filters.c
- Accessing Federal Court Records - Getting access to various public court records and using the Public Access to Court Electronic Records (PACER) system, by Iconoclast
- DNS Zone Scanning - Tips for quickly and efficiently scanning an entire network by only choosing the "important" machines, by DEFT
- DeCSS in Words - DeCSS is protected speech but the Pledge of Allegiance is not - figure that one out!, by CSS
- Build a Car Computer - Tips for build a low-cost computer/MP3 system for your vehicle, by Megatron
- 2600 Marketplace
- 2600 Meetings
- Price: $5.00
- Issue's Cash Cow: Evil Corley's Logic: Arrested walking around the RNC: BAD Arrested walking around the Capitol: GOOD
- Cover (Cover Info)
- Back Cover Worldly Payphones
- Delhi, India That's actually a water bottle stuffed down the phone's throat. People in India take a dim view of inadequate payphones. Photo by Tom Mele
- Lahure, Pakistan This phone supposedly can go anywhere. Photo by Tom Mele
- Cayman Islands From the Grand Cayman Island, this phone seems overly modern for such a tiny place. Photo by Paul Benford
- Jerusalem, Israel Phones do not misbehave here. Not with that kind of enforcement. Photo by M. Cameron Newell
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 17!
$2600 Magazine - Volume 17, Number 4 (Winter 2000-2001)
- Direction - Editorial
- Introduction to Snooping Around - Overview of basic Internet host snooping and network probing using common tools, by copycat
- BellSouth's Mobitex Network - Technical information and general overview of BellSouth's Mobitex wireless data networks, by Dspanky (Dave)
- An Introduction to Radio Scanning - Detailed guide to the basics of radio scanners, searching for new frequencies, and signal analysis, by Sam Morse
- More Java Fun - Ideas for decompiling Java applets and trying to obtain passwords via <param> tags, by FaultySignal9
- Decafe Pro Decafe Pro is the fastest Win95/98/NT decompiler for Java which reconstructs the original source code from the compiled binary class files.
- Sub7 - Usage, Prevention, Removal - Info on the Sub7 script kiddie remote administration Trojan program, by CaS
- Get Anyone's Credit Report for Free - An insider's trick for getting ahold of (other people's) credit card reports, by Renaldo
- Microsoft's Hook and Sinker - Microsoft Certified Systems Engineer (MCSE) info and exam questions designed to trick you so you can't just go out and study on your own, by LeXeR
- Hacking an NT Domain from the Desktop - Messing with Windows NT via the command line and adding yourself to the local admin group, by Hi_RISC
- The DVD Paper Chain - A quick little look at the film-to-DVD manufacturing process, by Common Knowledge
- Polymorphism Script - Demonstration of polymorphism in a Perl script based on the ILOVEYOU worm, by xdroop (David Mackintosh, Ottawa, Canada Twitter)
- Code polymorphism.pl
- Letters - POSTAL PROSE
- Clarifications - D. Lopez, p4
- Exciting News - Katia S. McKeever (Foster City, CA)
- The DeCSS Case - MaD-HaTTeR, Dan, Reverend Lust, Ned Flanders, aUd10phY|, eggo, Pete Davis, carpman, DG, Tony, rootx11 (Farhan Khan), Michael, Weez, jys_f, Harry, Nitehawk, KisP, n3xu56 (Sam K.), Mistral, Jakob (Denmark), hiredgun
- Hacker Ethics - Lizard, Mannequin, joshstout
- Newbies - DreyDay_33 (New York, New York)
- Hacker Fashion - Downsouth
- Scary News - Katia S. McKeever
- New Projects - s0ny, CaseTheWig
- Discoveries - buster, Colin, Kyoya san, matt (anonymous), Mr. DNA, JEM, zzflop, Dan, Big Shooter, NaterZ, Bob
- Questions - mpower, mheyes, catfood, S0J073RO, Paper
- Parallels of Oppression - Cambalache20
- Takedown Spotting - Camandrett (Argentina)
- More Corporate Evil - B.R., Byran, Rebilacx (Matt, DOB: 03-08-1980), The Dude (iamnotahacker), BizarreOne
- Annoying News - Brigit Blomme (Foster City, CA)
- Further Info - Daewoo, narce
- Suggestions - arc, Pestaline, RevZer0
- General Feedback - Manic Velocity (Salt Lake City, UT), Viaticus, KoDo, HamAZ, Enzo, TBOTe, maldoror, Stark, Phil
- The Politics of Change - BATTERY, phillippe, chrisbid, Prehistoric Net-Guy
- Schools - Aragoren, Sekicho-sensei, data refill, student #3594, JoePunk102
- Microsoftheadedness - Hermit, CB, Agentskye101, jesus X
- Spreading the Word - Kent
- Not News At All - Katia S. McKeever
- Confusing ANI and Other Phone Tricks - Explains how to bypass CLASS services, spoof ANI to AT&T 800 numbers, and make free untraceable calls, by Lucky225
- Jury Nullification and The Hacker - Jury duty tricks and why hackers can make good jurists, and why you should just say "not guilty" to bullsh!t charges, by Also Sprach Zarathustra
- Cop Proof Laptops - Overviews of police car laptop computers like the PCMobile by CYCOMM, by Common Knowledge
- RadioShack's Newest Giveaway - Quick little look at the :CueCat and some usage tips, by canyoumatrix
- Dissecting Shaw's Systems - Cash register information and network layout for Shaw's supermarkets and and look at manager/employee login information, by Sect0r F4ilure
- Domain Name Fun - A look at a "WHOIS Graffiti Wall"
- Hacking Free ISPs Using WinDump - Hacking free or ad-based dial-up Internet services by capturing the PPP login information with WinDump, by rys
- 2600 Marketplace
- 2600 Meetings
- Price: $5.00
- Issue's Cash Cow: One thing we can say about the year 2000 with some certainty is that it wasn't boring. If you didn't get a sense of excitement, you probably weren't paying attention. And not paying attention in this day and age is a real tragedy.
- Cover (Cover Info)
- Back Cover Strange Looking Foreign Phones
- Lanzhua, China Some people spend hours trying to figure out where to put the coins or card. Photo to Lawrence Stoskopf
- Jinlum, China This one looks like a character from Barney & Friends. Photo to Lawrence Stoskopf
- Reykjavik, Iceland Note the warning about surveillance cameras in case you're considering engaging in any funny business. Photo by Kingpin
- Slovenia This decadent design never would have been allowed in the days of Tito. Photo by Robert Vargason
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 17!
$2600 Magazine - Volume 18, Number 1 (Spring 2001)
- Signs of Hope - Editorial
- Police Searches of Computers - Very detailed overview of the legal procedures for police searches and warrants regarding computers and networks, by Todd Garrison (Denver, Colorado, Email, MySpace, Band Info, KC0KPN)
- The Future of PKI - Overview of the Public-Key Infrastructure (PKI) for credit and smart cards and the government's FORTEZZA cards, by Elite158
- PHP/CGI Vulnerabilities and Abuses - Common security holes with PHP and Perl scripts, specifically how variables are passed to PHP from the web browser, by L14
- Breaking the Windows Script Encoder - How to defeat and decode the infamous Windows Script Encoder, by Mr. Brownstone
- Code: scrdec18.c
- Code: scrdec18.exe Windows Script Decoder v1.8 (52k EXE) (Manual)
- Breaking the Windows Script Encoder 't Klaphek, Issue #6
- Microsoft Script Encoder Version 1.0 (130k EXE)
- Inside the Microsoft Script Encoder
- Soya.Encode.ScriptDecoder (JavaScript Source)
- Liberating Advants Terminals - Quick little hack for Advants Internet kiosks to replace their NetShift shell with Windows Explorer so you can run your own software, like games or a VNC server, by Loki fu7kt)
- A Romp Through System Security - Overview of locally and remotely securing the various services your Linux system, by Lumikant with help from Zarium
- Hacking QuickAid Internet Stations - Bug in QuickAid Internet kiosks to run Windows Explorer via WinZip, by Durkeim the Withered God
- The Billboard Liberation Front - People with too much time on their hands
- Computing with the Fabric of Reality - Overview of quantum-based computers and their applications for defeating public-key crypto, by Chris Silva (a.k.a. Sarah Jane Smith)
- Letters - SMS
- Politics - Lisa J., Ben Stragnell, Chris S.
- Random Questions - MiStReSS DiVA, Frank R. (San Antonio, TX), Equinox, Keyser Soze (Chris V.), Wax, muthu, EmptySet, Boneman, D'artagnon, haux, Philter (Chicago, IL), CyberInferno
- Ideas - Phredog@Work, Reverand_Daddy, DragonByte
- Info Hungry - Screeching Weasel
- Random Fear - Brad
- Harassment - Nate, Sam 'E', RagnSep, MajickMutex (Jenn), KNP, Corv
- Cluelessness - Parin, Randy Ford, Screamer Chaotix (Connecticut), SellOut
- Observations - C...., *31337*, Kyle, ~otacon~, RevZer0, Three, Mad Pyrotechnologist (Eric Schmiedl), Trigga Bistro, Your Mom, tnt419 (Tom M. Brady, MySpace, Toledo, OH), zerolemons, noire (Colorado), Eric, kju, almightycoop, Biohazard51 (DOB: 05-28-1988), Xian, zeitgeist (Germany), hemlock, Weez, patrick, rootx11, Sir_Poet, shader, gan0n
- Discoveries - Kal, Robb (Ireland), Splices
- Memories - Stevie B a.k.a. Blue Lightning
- Fighting Back - Scott, rene gonzalez, Marina Brown (MGN)
- Voting Ideas - SiON42, cstoll, Michael, anon
- Article Feedback - reuven, Tim, v-dick
- Fun in the Stores - xcham, AquaGlow
- Legal Questions - Joseph, Hy Stress
- Advice - noname
- Technological Nightmares - Xerxes2695 (Georgia), Jeffery, ^CircuiT^, Dalai, The_Chaotic_1 (Joseph, Email, DOB: 03-14-1985)
- Offerings - Simon Jester
- From The Inside - James, Eric Burns
- Secrets of Electronic Shelf Labels - A quick look at supermarket Electronic Shelf Labels, those LCD price labels which are starting to show up, by Trailblazer (Paul)
- Anomaly Detection Systems - Part 2 - Discusses different ways to accomplish anomaly detection on large heterogeneous networks cheaply and efficiently from the passive/network-based angle, and signature-based IDS systems' usage in conjunction with anomaly detection to create a well-rounded overall intrusion detection solution, by Thuull
- Strange Love - Amusing look at the Anna Kournikova Virus and how allowed the author to get in touch with people he hadn't heard from in a while, by 6M AL
- Declawing Your :CueCat - Removing the serial number from your :CueCat, by Lunius
- Declawing your :Cue:Cat Original
- Passwords on a :CueCat
- :CueCat Login Shell
- Open-Source :CueCat Software/Drivers
- Scum - Realistic-looking "fake" bill from a company called UTP Internet Business Guide
- Takedown Taken Down - Only $2600 Magazine can distort the truth about Kevin Mitnick and profit from him, by Evil Corley
- 2600 Marketplace
- 2600 Meetings
- Issue's Cash Cow: A look at $2600's DeCSS case & appeal, and how the DMCA and its effects are covered by various media.
- Cover (Cover Info)
- Back Cover Strange Looking Foreign Payphones
- Giza, Egypt Note the pyramid in the distance. Photo by Justine Lackey
- Luxor, Egypt In the Valley of the Kings. Photo by Lawrence E. Stoskopf
- Zagolsk, Russia Outside the Trinity Monastery. Photo by Katherine E. Pope
- Dar-Es-Salaam, Tanzania Photo by Alain Quackelbeen
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 18!
"Psst... Hey Kevin! Listen to me and we can both pull in six-figures a year by scaring teenage boys."
$2600 Magazine - Volume 18, Number 2 (Summer 2001)
- The Broken Wheels of Justice - Editorial
- What is Carnivore, Really? - Overview of the FBI's Carnivore electronic interception program, by Achilles Outlaw, Ph.D.
- Carnivore FAQ by Robert Graham, Version 3, October 6, 2001
- Carnivore FOIA Documents These documents have been released through a lawsuit EPIC filed against the FBI and the Department of Justice.
- Extra Polymorphic Worms - Update to xdroop's polymorphism script article and ideas to bypass detecting systems, includes example Java code, by Dr. Leovinus
- Code: ReWriter.java
- Code: RandomRunner.java
- Everything Your Parents Told You About ESS Was a Lie - A look at the 5ESS and telco system in the "modern" age, by dalai
- Michigan Memos - Internal memos from Ameritech and Ford
- How to Become a Hacker Saint - This article explains how a hacker can become an official "saint" as declared by the Pope, by J-Fast
- Misconceptions About TCP Wrappers - Overview of using and securing TCP Wrappers rules and what to watch out for, by Golden_Eternity (Blake R. Swopes, Ventura County, California, GitHub)
- TCP Wrappers Misconceptions Original
- Hacking an NT 4 Domain from the Desktop - Revisited - Example scripts to gain administrative rights on Windows NT system, then email or crack the passwords, by Hi_Risc (a.k.a. ASB)
- Code: SendEmailMessage.vbs
- Popular Myths on Password Authentication - Tips on choosing secure passwords, use your head and consider the statistics, the sensitivity of the resources which you are trying to protect, and your user base, by Stephen Thomas
- Exploring HP-UX Password Schemes - Overview of the "Trusted Systems" protected password database scheme under HP-UX 10.x, by Alex
- Trusted System vs Non-Trusted System
- Managing Systems and Workgroups A Guide for HP-UX System Administrators - Edition 7 (HP Part No. 5990-8172) (HTML Version)
- Letters - THE INBOX
- DeCSS Fallout - gc, Anonymous Reader, Clown Father, Xerock, Avon, yonder, jeff weems, djeaux, Brian
- Bypassing Restrictions - mkr08, HacKz_jEEveZ, F.H., Av1d
- Spying - R Otterbine, The_Chaotic_1
- School Stupidity - Wetwarez, Newzweak, Phredog, Sam S., mr self destruct
- Real World Stupidity - dc66, Tizal, The Colonel, zeigeist, phobik, Chewie, Joe, Ray
- Appreciation - TwistedGreen (Donna Murawski, Windsor, Ontario), civilsurveydraft, nomad, Danny, Waldo, Cunning Linguist (Jeff Strauss), Ford Prefect, Sate, Thomas
- Individual Perspectives - KHD, Gil Young, kate, kaH220
- Clarification - kaige, Shadow Freq, Mike Walton, Qblade, Anonymous, Jeff, Dan, Scabby, Mike
- Questions - Neo, IM_Ruse, Mike G., SPAMLord, BillyNo, IceBlast, Double Helix, grant welch, Mikko, Peter, Kn0w, quatre
- Corporate Stupidity - 7h3 31337 pHr34k4z0id, Tony, Newspimp, niihon, litze, Thomas
- Discoveries - LazerBeamX, ryanx7, Cyrus, Morn_Star, SkorpiosDeath, toast666
- Issue Problems - doug, I1269U, Jizzbug
- Napster Alternatives - Shawn
- Counterpoint - Bob, Steve
- An Idea - My Name is Joe!
- Voter Education - Poll Watcher
- A Call To Arms - ICFN PMP
- AOL @SCHOOL - Nice little trick where you can grab your school's AOL @SCHOOL serial number/signon code, then login from home and create a new account so you can have unrestricted @SCHOOL access for yourself at school, by The Datapharmer
- Fun With Fortres - Messing with Fortres 101 Windows security program, by Amatus (David Barksdale, Email #2)
- Fortres Hacking by Amatus
- DeFortres.zip
- fortres.c Part of Amatus' fortres.cgi - a CGI application for decrypting administrator passwords for disabling Fortres.
- AT&T @Home - Info on AT&T @Home Internet services from a first-level tech support operator, by m0rtis (Daniel R. Wright)
- The New AT&T Network - Overview of AT&T's long-distance network updates after the article "ANI Spoofing" appeared, by Lucky225
- Tellme: Uses and Abuses - Using and abusing the various Tellme specialized in telephone-based applications, by Screamer Chaotix (Bridgeport, Connecticut, Email #1, Email #2, Frequency, YouTube Channel)
- Snooping the Stack - A look at some common TCP/IP analysis tools for "snooping" and "footprinting" hosts on the Internet, by ThinkT4nk (Ryan McGowan, St. Louis, Missouri, Email #2)
- 2600 Marketplace
- 2600 Meetings
- Issue's Cash Cow: These idiots actually think registering stupid domain names has something to do with hacking. Evil Corley's Logic: Arrested walking around the RNC: BAD Arrested walking around the Capitol: GOOD
- Cover (Cover Info)
- Back Cover Strange Looking Foreign Payphones
- Kusadasi, Turkey Said to be near presumed historical House of the Virgin Mary. Verizon phones never get to make claims like that. Photo by Richard Bejtlich
- Sogut Island, Turkey No maior religious icons in sight but this is rumored to be the only such phone on the island, which has less than 300 inhabitants. Photo by Paul Pate
- Luqa, Malta Baby blue phone found at the Malta International Airport. Photo by A. Evans
- Gzira, Malta Variations on a theme. Note the near identical features to the blue model. Photo by A. Evans
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 18!
$2600 Magazine - Volume 18, Number 3 (Autumn 2001)
- Consequences - Editorial
- Deconstructing a Fortres - Overview of Fortres 101 version 4 security software and some potential ideas for bypassing it, by Acidus (Billy Hoffman, Atlanta, Georgia, Pic, Blog, Email #1)
- Passport Hacking - This article introduces a security vulnerability in Microsoft Passport, specific details explaining how to compromise a user's Passport account as well as example code, by Chris Shiflett (Boulder, Colorado, Email, Twitter)
- How to Decrypt DirecTV - How to decode DirecTV satellite signals using H-cards, by Clovis (Louis Edward Trumpbour)
- DSS Test Cards Buyer's FAQ Version 1.0 (May 15, 1998)
- The DSS Underground Programming Guide
- The DSS Underground Basic Unlooper Guide
- H Cards and You: The H Card Hacking FAQ
- The History of DSS Hacking
- For Nearly 10 Years I Operated a Satellite TV Hacking Network Anonymously from South East Asia
- Dennis Megarry Affidavit
- How to Reverse-Engineer a Satellite TV Smart Card
- Satellite Hackers Bible The elite satellite hackers techniques from the year 2000 to 2010 are covered in this special muti-chapter presentation.
- DSS Emulation Information
- Code Red 2 - Or how to anonymously get root on 250,000 machines overnight by remotely accessing Code Red infected computers, by Braddock Gaskill (Baltimore, Maryland, Email, W3BCV)
- Republishing the Rules - The Ultimate DRM Hack - Overview of the different types of Digital Rights Management (DRM) systems and the need to push for an open-source solution before the technology gets hijacked, by The Walrus
- DecloQing Copy Protection - Patch to cdparanoia to bypass the MediaCloQ anti-ripping feature, by Pack Rat Sam
- Hacking Time - Overview and hacking potential Qqest ETC-series dial-up employee time clock machines, by HoTsAbI
- Using the Model ETC 100 Time Clock
- Using the Model IQ 500 IntelliClock
- Qqest Time Force II Hardware Guide
- Myths About TCP Spoofing - Some myths surrounding IP spoofing attacks being able to cover your tracks, by Grandmaster Plague (Evan Sparks)
- Various Network Tools by CyberPsychotic
- Playing with Qwest DSL - Overview of Qwest DSL Internet service, by phobik
- Cisco 600 Series Installation and Operation Guide July 2000
- Cisco Broadband Operating System Commands v2.4
- Cisco Broadband Operating System User Guide (HTML Version)
- Defeating Intrusion Detection Systems - Tips and Perl scripts for port scanner that can defeat certain IDS settings or work over proxies, by SnakeByte (Eric Sesterhenn)
- Code: sockscan.pl
- Code: sockscan2.pl
- Code: wingate-scan.pl
- Code: portscan-over-http-proxy.pl
- Letters - fine print
- People Power - zenunit
- The Mass Culture - psycho-mantis, Spacemonkey6945
- Scams - Slam
- Politics - Jonathan Fredericksen
- Guns - clvr_handl, Tozetre, Don, William R. Epp (Email #1)
- Questions - Adam J., Steven, Gzamay, jeff, Conscience, studin, E, Alexander, R3dO (Lithuania), Reinaldo, IncogX (Marcus Anderson), argie1607, Marc
- Concerns - Gino, Net Admin, stufff, Pete, Doc Kennedy
- More Info - Hugh G. Rection, phix, hanoverfist, Ben Sherits, bd, Rogue, EnochRoot, ryno
- Injustices - chromosome fortyseven, fuzzhack, kloXTicToX, Sab0tage, Ben, DiabolicEdict (Lewisville, TX), Joe Newman, tek_guy, Crazy K
- Data - Dco, medik
- Appreciation - JohnG54429, Josef Trimpert, Akolade, ratner, Omega Red, iceplant999 (Paul), Michael Piacsek (South Africa)
- Article Feedback - Eric Lippert, ive
- Surprises - binary, Iamnoone, Bill
- Quest For Knowledge - Interested, covertuw, David R.
- Satellite Watch - Burgy, Mangaburn, brian
- A Handy Tip - Anthony
- The Evils of Microsoft - Avon, Iceplant999, Daewoo
- Just Plain Evil - Speed Racer
- Just Plain Stupid - lunius
- An Idea - Trent
- Compromising Internet Appliances - A look at hacking Internet connected household appliances and their ability to cause physical harm, by Plex Inphiniti
- An Introduction to ARP Spoofing - Good overview of ARP spoofing, a method of exploiting the interaction of IP and the Ethernet protocols, by Sean Whalen
- An Introduction to ARP Spoofing Original (v1.8)
- An Introduction to ARP Spoofing Slides
- Offset Hacking - Story of a person "banned" for apparently using in-memory hex editing during a game of EverQuest, by Darbyersh
- The Invisible Box - The Invisible Box will make it so that when you pick up an extension phone on your phone line, any of those "in-use" lights that alert if an extension phone is picked up won't light, by Lucky225
- Bypassing Cisco Router Passwords - How to bypass the passwords on Cisco 2500/2600-series router, by Nickels 1
- Bypassing Cisco Router Passwords Original
- Hacking Retail Hardware - A closer look at VeriFone PINPad 1000 and the PIN pads used at Walmart and QuickScribe kiosks, by dual_parallel (Mike, Phoenix, Arizona)
- Hacking KODAK Picture Maker - Tips to obtain the printing or setup passwords on a KODAK picture kiosk and using your own floppy, by deadkode
- Netjacking for Complete Idiots - Introductory look at intercepting 802.11b Wi-Fi traffic and using other people's networks, by Dark Overlord of the DoC (Peter M. Shipley, DOB: 09-30-1965, Berkeley, California)
- Exploiting Intelligent Peripherals - Scanning for HP JetDirect printers with wide-open programming ports, by Screamer Chaotix
- Exploiting Intelligent Peripherals Original
- 2600 Marketplace
- 2600 Meetings
- Issue's Cash Cow: Robert S. Mueller is a horribe person, constant liar, and a tool for the deep-state. Why does Evil Corley keep supporting him? Also, blame everyone but the terrorists, typical.
- Cover (Cover Info)
- Back Inside Foreign Phones
- Malta Rather different than the ones featured in the last issue. Photo by Bill Raynault
- Peru Found at the airport in Iquitos, the largest city on the Amazon River. Photo by Raven
- Russia #1 From remote Ussuriysk, north of Vladivostok in the Primorsky Krai territory in the far eastern part of the country. We suspect it would be hard to find our magazine there. Photo by Tresa Thompson
- Russia #2 " Photo by Tresa Thompson
- Back Cover Foreign Phones
- Cambodia #1 A card phone in a busy street in Battambang Photo by Eric Tucker
- Cambodia #2 Another card phone from the capital city of Phnom Penh. It's rumored that there are no coin phones at all in this country. Photo by Eric Tucker
- Greece #1 Found in the small Greek village of Milies. Photo by John Klacsmann
- Greece #2 From the village of Makrinitsa. We hope that isn't a speaker behind the grill above the phone since it looks like it would easily deafen anyone standing there. Photo by John Klacsmann
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 18!
$2600 Magazine - Volume 18, Number 4 (Winter 2001-2002)
- 2001-2002 - Editorial
- The Security of the Inferno OS - Security semantics of Vita Nuova's Inferno OS, including a password cracker and the ability to break out a shell on the emulator's host, by dalai
- The Security of Inferno OS Original
- hellfire.b Inferno password cracker.
- clogon.b Inferno command line program to change user.
- Inferno Programmer's Guide
- Futuristic OS? by Oscar A. Tobar
- An Analysis of Inferno and Limbo by Kim Nyberg
- Inferno Reference Manual
- BlackICE Defender - a Personal Firewall - Overview and install how-to for Black Ice Defender, by Suicidal_251
- BlackICE Defender User Guide Version 1.0
- BlackICE Defender User Guide Version 2.9
- BlackICE Pro User Guide Version 2.0
- BlackICE Basic Release 1.9.21 LE (Help File)
- BlackICE Defender Version 2.5.chE
- The Future of Enhanced 911 - Implementing cellular E911 and GPS location, by Wumpus Hunter
- Behind the Scenes on a Web Page - Very detailed overview of how a web server works and the client/server relationship, and how those nasty ads are served, by angelazaharia (Angela Zaharia)
- Cracking Clever Content - How to bypass Clever Content, which is software designed to prevent the saving of images and PDF documents from webpages, by Tokachu
- Right-Click Suppression - Code to add right-click suppression to your webpage and how to bypass it, by Rob Rohan
- Fun With RadioShack - General overview of the Canadian RadioShack kiosks and a method of breaking out of the software, by Cunning Linguist (Jeff Strauss)
- Building a Floppy-Based Router - Overview of building an Internet router using an old 386+ computer with only a floppy drive, two NICs, and Coyote Linux, by netfreak
- Build a Wooden Computer - Coll little project to build a computer case out of wood, by Elite158 (Joerg Kurt Wegner)
- Harnessing the Airwaves - Introduction and overview of low-power "pirate" radio, by Mark12085 (Mark)
- Secrets of Rogers@Home - Behind the scenes at Canada's Rogers@Home Internet services by a former tech supervisor, by Gr@ve_Rose (Sean Murray-Ford)
- Basics on Answering Machine Hacking - More information on hacking answering machines and VMBs, and a cool hack using long strings of 2- & 3-digit numbers, by horrid
- Letters - still legal thoughts
- Ideas - Mitchell_pgh (Richard Mitchell), FlashARK, Tresser McKay
- Prison Life - //buddha
- School Life - christian, risus sardonicus, bb_student, Maniac_Dan, DeftonesGuy0183
- Corporate Life - Hex
- Observations - fuzzy, mAd-1, Muchocaca, Silent, Chase "Michael Kenyon" Brown, Osi44 (Argentina), Evil_Monkey, Yonder, lord ice, Johnny C., Cody, DJBusyB (MySpace), Anon O Mous, Mark12085, Felix, Andrew Holt, mickeym
- Politics - G. Conterio, American citizen residing abroad
- Con Jobs - ns, sxpert
- Morale Boosts - S, David Middleton (Cobra2411, Philadelphia, PA), LanZfreak
- More Info - No Name, g0 seigen, meowmixman, Lucifier Messiah (Anarkick Systems), Anonymous, Phate, Kingpin, Cudabean
- Quest For Knowledge - dmitry kostyuk
- Old-School Perspective - Primenumber
- Film Update - DQ
- Hacker Pedestals - chris s
- Questions - sk, Halo Nine, Zach, K0ldshadow, Phaceoff, Ghost007, Lunchbox (a.k.a. King of Lag)
- Signs of Hope - Silent Transgressor, Sean
- Thoughts on 9/11 - Thinking, voice of reason, Re-LoaD, Waldo (East Lansing, MI), The_Chaotic_1, joeman, A C, RenderMan (Brad Haines), noire, Island Boy
- Response To Criticism - DarkBlayd, Phyt3b4ck
- Legal Nonsense - Danny, Sazook, Dan, pa
- Suggestions For Newbies - Funkstrings
- More on Telemarketing - Vengul Ator
- Camera Crap - CyBeRJaK
- Labels - The Zygote Killa
- Hacking the Highway - Hacking those ADDCO road sign trailers, by mennonite
- ADDCO BRICKBuilder v2.6.1
- How to Hack from a RAM Disk - Setting up Cenatek's RAMDisk9x/Me in order to running programs (and swap) in a RAM disk for both security and speed, by Nv
- Hacking with Samba - Overview of port scanning, and exploiting, open Samba shares and servers, by dknfy
- Fun Facts About Walmart - A look at the customer terminals, handheld price scanner, and EAS system at Walmart stores, by A.W.M.
- IIS - Far from Unhackable - hacking Microsoft IIS web servers via Unicode exploits, by xile
- IIS Unicode Exploit
- IIS Unicode by rain forest puppy
- Examining Student Databases - Story of "accidently" accessing potentially confidential data in a university student databases, by Screamer Chaotix
- 2600 Marketplace
- 2600 Meetings
- Issue's Cash Cow: 2001 had been a most difficult year for hacker in so many ways.
- Cover (Cover Info)
- Back Inside Payphones of Countries We're Mad At Part One: Cuba
- Cuba #1 A popular payphone kiosk in Havana. And that's not an ad for sneakers in the background. Photo by T. Mele
- Cuba #2 ETECSA is Cuba's state-owned phone company. This phone in Havana takes smartcards. Photo by Pawel Krewin
- Cuba #3 Another model that's real high tech found in Regla Photo by T. Mele
- Back Cover Payphones of Countries We're Mad At Part Two: Iran
- Iran #1 In the holy city of Qom, this rather advanced card reader phone takes something called "kart atabar." Photo by Phundisk
- Iran #2 This your basic payphone found all over Iran - this one was in Rasht. The instructions make it real simple. The Touch-Tone pad could be a bit smaller though. Photo by Phundisk
- Iran #3 Found in Delijan, this green monster is so haunting it will visit you in your dreams. It's got so much personality plus you can hang a painting on the front of it. There are two coin slots for each type of coin and the amount is displayed in the box on the upper left. Photo by Phundisk
- Iran #4 At first glance you might think this wasn't a payphone at all. You'd be wrong. Found by a Ghazian gas station, this phone has a slide coin chamber which would last about 30 seconds in the States. Photo by Phundisk
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 18!
$2600 Magazine - Volume 19, Number 1 (Spring 2002)
- Time To Care - Editorial
- Transaction-Based Systems - Overview and potential security holes in transaction-based (online) ordering systems, by StankDawg
- How to Regain Privacy on the Net - Tips for managing cookies, web bugs, spyware, etc. in Netscape and Internet Explorer, by Boris Loza (Toronto, Canada)
- Stupid Google Tricks - How to search for specific file extensions/types or search within certain websites when using Google, by Particle Bored (Cory Bys, Email)
- Neat Stuff with Switchboard.com - Searching for public & private information with Switchboard.com, by Cunning Linguist (Jeff Strauss)
- Poor Man's 3D - Really cool idea for using cheap comic book 3D glasses with Winamp's AVS to make a realistic 3D audio spectrum analyzer, by diabolik (DJ Diabolik)
- Poor Man's 3D: Winamp AVS Presets
- SuperScope... Any Help Out There?
- Winamp AVS Pixel Vectorscope Example
- AppleTalk Security Secrets - How to remove the AppleShare client's ability to authenticate against a server using passwords which get sent in cleartext, by Steven Kreuzer
- The Definitive Guide to Phreak Boxes - Brief overview of each the phone phreak's "color" boxes, by Elf Qrin (Valerio Capello)
- The Definitive Guide to Phreak Boxes Original
- The Bungee Box - Simple modification to add a retractable cord to your Beige Box, by Captain B
- CampusWide Wide Open - Very good article on the AT&T/Blackboard CampusWide ID card system and a potential security exploit, by Acidus
- CampusWide Wide Open Original
- Acidus' CampusWide Archive
- AT&T CampusWide Access Solutions Frequencies FCC ID: WPHF476
- AT&T to Facilitate Tech's All-Campus Card system
- Cease and Desist Letter Sent to Interz0ne II
- Blackboard Campus IDs: Security Thru Cease & Desist via Slashdot
- CampusWide Chronicles Vol. 1, Issue 1 (March 2000)
- CampusWide Chronicles Vol. 1, Issue 2 (April 2000)
- CampusWide Chronicles Vol. 1, Issue 3 (July 2000)
- Idiocy in the Telcos - Confusion for customer's using directory assistance with today's phone companies, by The Cheshire Catalyst
- Idiocy at the Telcos Original
- Letters - Backtalk
- Signs of Hope - Breto, avatar
- Higher Education - A7th, StMike
- Help Wanted - Mingus, Asbigassex@aol.com, HSFk2
- Corrupting Youth - ex_chronos (Reno, NV)
- Miscellaneous Info - ~dissoluten, Empty Set, Raleigh Cross, Revanant, Doodle, Random Jubatus (Jeremy Whelchel)
- Answers Needed - Rick Olson (Fluffy, Vista, CA), Johnny, haux, Bill Boyle, Anti-Christ, lop, Drew, SuperGuido, Crim, Kaoslord (Guillermo Roditi, Fort Lauderdale, FL)
- Complaints - john smith (California), tHr13z3, Binary Burnout
- Worries - Mr. Brown, 3-Com, Silent
- Ideas - Drwar
- More Politics - Mike S. Lorrey (Retroman), Jon McLaughlin, Joseph McLeod, SKZ
- Observations - noire, Gustaf, psyk0mantis, bluness, Herman, Cody Beeson (Yuma, AZ), DephKon1 (Phil Nolan, Will Ohmsford), dougk_ff7 (Doug Kelly), Suicidal, Phookadude (Patrick Moore, Topeka, KS), Two Avocados
- The World of Retail - TheDude (Sacramento, CA)
- Injustice - Scott Moulton (Court Case), ht, Anthony D. Bower, Johnny Slash, Nicolai, Sunfist, Ghent (Branden Hancock), johnnyfulcrum (Johnny Fulcrum), Polar Mike, Jeremy M Lang
- Corporate Corruption - ~toast666, vidic0n (Canada), Robert Williams, c0d3wr3ck3r (Eric), nomotion, Dash Interrupt, Brad
- Article Feedback - MSM, Kurt Winter, ascii32, ted, P4R4d0x, Scott, Emre Yucel (amoeba1911, Cincinnati, OH), InternetGoddess, Steven Richards
- Tracking Terrorists - Chris, Dan
- Creative Cable Modem Configuration - Overview of cable modem configurations and DOCSIS information, and the potential to edit the modem's configuration file to remove data caps or rate limiting, by Pankaj Arora
- Fun Password Facts - Overview of different password combinations including using ASCII control characters, by hairball (New Kensington, Pennsylvania)
- Defeating Network Address Translation - Defeat a NAT by redirecting ports via an unsecure router, by g00gleminer
- NSI Abuse - Network Solutions not following their own rules regarding expired domains, by Chris Byrnes
- The Threat of a Lazy Admin - On why you should secure all sides of your network, the Internet-facing side and the local router/switch side, by Javier O. (Javier Ortega)
- A Script for the Right-Click Suppressed - Example Perl script to grab images/files from websites which block right-clicks, by Pete
- Code: isninja.pl
- Retail Hardware Revisited - A look at the checkout PIN pads used by Walmart and Kmart, and a look at Kmart's in-store BlueLight app computers, by dual_parallel
- More RadioShack Facts - Overview of the Microsoft Internet Center in-store kiosk at RadioShack peddling MSN, and a look at that stupid name database, by c3llph
- RadioShack's All ZIP Code Program & Data File v4.00.00 (June 7, 2004)
- RadioShack Adds Microsoft Net Kiosks to Stores
- 2600 Marketplace
- 2600 Meetings
- Price: $5.00
- Issue's Cash Cow: Looking at DMCA, WIPO, CARP, COPA, CDA, PATRIOT Act, and a bunch of Hillary Clinton voters complaining about "big government" - you can't make this stuff up!
- Cover (Cover Info)
- Back Inside Dutch Payphones
- Amsterdam #1 Increasingly hard to find, this phone only accepts coins. Photo by Daniel Langdon Jones
- Amsterdam #2 Increasingly easy to find, this phone doesn't accept coins. Photo by Daniel Langdon Jones
- Rotterdam #1 A Telfort phone that takes both coins and cards. Photo by Daniel Langdon Jones
- Rotterdam #2 Probably best not to ask. Photo by Daniel Langdon Jones
- Back Cover More Foreign Payphones
- Phnom Penh, Cambodia #1 A card-only phone. Photo by John Bullock
- Phnom Penh, Cambodia #2 Close-up view. Photo by John Bullock
- Willemstad, Curacao A shape and color so rarely seen in the States. Photo Phillip Bettac Zoufal
- Kyiv, Ukraine This rotary phone is said to only take prepaid smart cards, although it's rather hard to figure out where they would go. Photo by an anonymous Canadian
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 19!
$2600 Magazine - Volume 19, Number 2 (Summer 2002)
- Fair Use and Abuse - Editorial
- The Comprehensive Guide to 802.11b Wireless Networks - Good overview of the 802.11 (Wi-Fi) wireless protocol and networks, by Dragorn (Michael Kershaw, Email, GitHub)
- How to Break Through a Proxy or Firewall - How to break through a firewall or proxy by using SSH tunneling, by unformed
- Corkscrew Corkscrew is a tool for tunneling SSH through HTTP proxies.
- A Nasty NT Bug - How to kill a NT machine with only three lines of C code, by HJH
- How to Crash Windows XP
- The CSRSS Backspace Bug in Windows NT 4/NT 2000/NT XP
- W2K/XP Hangs with "TAB BS BS" on Console
- A Look Back - Story of the old hacker days and to become a leader of the ignorant, not their enemy, by Dufu (Joe Agro, Millington, New Jersey)
- Grab That Cache - Perl script to collect and view images in a Netscape web browser's cache, by David Nicol (Kansas City, Missouri)
- Code: grabcache.pl
- The End of an Era - AT&T's retirement (or not) of ACTS and the end of Red Boxing as we know it, by Lucky225
- redboxatt.ogg A recording of the announcement stating that AT&T will no longer be accepting coins from payphones as a form of payment for long distance calls.
- Older Technology Payphones Soon Will Go "Coin Less" for AT&T Long Distance Calls
- NCR ATMs - Aurum Ex Machina - Detailed overview of the computer and operating system in NCR personaS88 ATMs, by Acidus
- The Afghan Phone System - An overview of the post-9/11 phone system in Afghanistan, by Iconoclast
- Yet Another Way to Defeat URL Filters - Program to bypass URL filtering by generating "decimal" versions of IP addresses, by ThermoFish (James Wood, Bristow, Virginia)
- Code: host2dec.cpp
- Getting Into Cisco Routers - Overview of attacking Cisco routers via a ping flood to force it into its "safe mode," by Grandmaster Plague
- A New Era of Telecommunications Surveillance - Overview of post-9/11 telecommunications surveillance with a good look at the FBI's CALEA, by The Prophet
- Web Server Discovery Tool - Simple and quick Perl script for scanning hosts for ports serving websites, by Boris Loza
- Code: ws.pl
- Letters - input
- Darwin Awards - CrashPlastic, JohnnyD, Carter (U.K.), John Fannin, THE COMMON SENCE!, Nick Fury, Fisqual, RW
- Questions - Ricardo (Brazil), marblehead, MW, gomma, fallout, psi, Mark12085
- Privacy Issues - Godless Phreak, bear, thoughtcrime
- Feedback - gir, Buster Doney, Silent, Rat, Grey Frequency (New York, DOB: 09-03-1978, Twitter), lunius, ThieF, Klep, James, Mike K, Ninjak, fremont_dslam (Fremont, CA), blind, littlegreenguy, Suicidal, Kronikal, Czar Donic, Junglee, Aaron, Kristopher Barrett, Manic Velocity, CK
- Trash - captain_b
- Revenge - deadkode, brujo
- Help - Terrance, Adam from Ontario, Alice
- 4/1/2 - Bob Smellicular, Nothing None
- Education - Wild Karrde (Cottage Grove, Oregon), Windwalker
- Weird Stuff - soloha
- Fun Stuff - Gary (Japan)
- More Info - maldoror (Tampa, FL), Bildo, phlux, drew
- Issues - vroman, Craig, jesse s., American Citizen Living Abroad
- Retail - DEESil, fuzzhack, Angela, Moon Knight, Signal9, Neo Retrospect
- Solutions - husam, quel
- More Corporate Abuse - Peter
- Observations - drenehtsral (Lar Friend, Ithaca, New York), William Rudek, Erovi, zanar (Australia), Rabid, Super-Fly, pa, phobik, Methaline, xcham, aimfan69
- Your Eyes Have Just Been Sold - Behind the scenes information on what it takes to serve DoubleClick web ads, by docburton
- Dumpster Diving: One Man's Trash - A collection of tips which are good for the beginner or experienced undocumented garbage collector, by Grifter (Neil Wyler, Salt Lake City, Utah, Twitter)
- Mind Tricks - This article shows you how easy it is to make people do and think what you want, beyond the standard concepts of asking certain questions to obtain the information you seek, by Tazz Shippensburg
- Book Review: Hacker Culture - Book review of Douglas Thomas' Hacker Culture, by Ben McCorkle (Marion, Ohio)
- Testimony for the Committee on Government Reform's Subcommittee on Government Efficiency, Financial Management and Intergovernmental Relations Cyber Terrorism and Critical Infrastructure Protection by Douglas Thomas (July 24, 2002)
- CBDTPA: Yet Another Privacy Concern - Info on the Consumer Broadband and Digital Television Promotion Act, by area_51
- NULL Sessions and Enumeration - Information on exploiting Windows NULL sessions, which are "hidden" connections to Windows shares with no username or password, by AcidFlame
- 2600 Marketplace
- 2600 Meetings
- Price: $5.00
- Issue's Cash Cow: DMCA, stealing movies & music is O.K.
- Cover (Cover Info)
- Back Inside Spanish Payphones
- Barcelona #1 This phone could easily be mistaken for a UFO. Photo by h4h
- Barcelona #2 A payphone from one of the other phone companies. Photo by h4h
- Barcelona #3 We can only guess that there was a heated argument on this phone. Photo by h4h
- Barcelona #4 At the train station. Photo by h4h
- Back Cover Australisn Payphones
- Concord One of the really old payphones with rotary dials. Photo by Patrick Webster
- Sydney #1 One of the new payphones found in shopping malls. Operated by TriTel. Photo by Patrick Webster
- Sydney #2 Typical Telstra payphones. Can you tell which scene of The Matrix was filmed here? Photo by Patrick Webster
- Burwood A closer view of a Telstra (formerly Telecom Australia) phone. Photo by Patrick Webster
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 19!
$2600 Magazine - Volume 19, Number 3 (Autumn 2002)
- Freedom's Biggest Enemy - Editorial
- Lawfully Authorized Electronic Surveillance - Communications Assistance for Law Enforcement Act overview and notes, by Mystic (Andrew Lowe, Santa Cruz, California, GitHub, Twitter)
- Introduction to Lawfully Authorized Electronic Surveillance (LAES) Original, Phrack, Issue #60
- AskCALEA Mirror of askcalea.fbi.gov
- Can They Hear Me Now? A security analysis of law enforcement wiretaps, by Matt Blaze
- The Mysterious World of the LERG - Definitions of some Local Exchange Routing Guide (LERG) terms, by Tom Morrow 3.0
- LERG Routing Guide Specifications (2020)
- LERG Routing Guide General Information (2002)
- Central Office Code (NXX) Assignment Guidelines INC 95-0407-008
- NPA/NXX Activity Guide Vol. 12, Issue 6 (June 1, 2002) (README)
- TeleZapper, Telemarketers, and the TCPA - General overview of the TeleZapper device, the SIT tone, and some tips on how to stop being contacted by telemarketers, by bland_inquisitor
- Unsolicited Fax - $2600 received a weird fax message from Direct Media America.
- A Password Grabbing Attempt - Perl script to generate a fake "error message" in an attempt to capture the user's password, by Gr@ve_Rose
- Code: passgrab.pl
- Advanced Password Recovery - Password cracking tips, by Galahad
- Advanced Password Recovery Original
- Fun Password Facts Revisited - The dangers of using weak passwords as they are more easy to brute-force than you think, and why you should use Password Safe to safely store them, by kaige
- Hacking on Vacation - A look at Disney World's FastPass ticket system and some other technical adventures (Antenna Audio) to look for while on vacation, by Eric
- Your Guide to Target - Overview of the cash registers, POS software, and login information used at Target stores, by Code0
- Comcast Operation TIPS Memo - Comcast Talking Point memo on whether or not they are participating in Operation TIPS.
- Outsmarting Blockbuster - Social engineering Blockbuster to get out of late fees, by Maniac_Dan (Dan McAloon)
- The New Card Up DirecTV's Sleeve - A look at the various generations of DirecTV's satellite receiver smart cards, by Mangaburn
- DirecTV's Secret War on Hackers
- From the Eye of a Legal Storm, Murdoch's Satellite-TV Hacker Tells All
- The Pewter Box - Turn an old hard drive into a speaker, by Mark12085
- How to Log URL Request Strings - Article and code overview for a program to display and log all URL requests from Internet Explorer, by LiquidBinary (Mike Leonguerrero)
- Code: IE_spy.c
- Code: IE_Spy.exe
- URLlogger.zip (LogIEUrlrRequests.exe)
- Letters - Missives
- Discoveries - Eric, NilObject, BF, fatdave (MySpace, De Forest, WI), Jonathan, drlecter
- Meeting Issues - Blue Canary (Laguna Niguel, CA)
- Ideas - Elstun, Bac, David Parker, Jeremy
- Unease - 24CORE, Wyatt, David, cerebrum86 (DOB: 07-16-1986), Nicker (Canada), GnuHal & GnuWopr (Spain), Hualon, Peter (j0lt) Truth
- Getting Around the System - NcongruNt (John Menke, Austin, TX, MySpace, DOB: 09-16-1978), Folkert van Heusden (Netherlands), Doug
- Words of Thanks - nuclear_decay, strupp, Galaxyhq, Mobius, Fr33d0mFiteR, Zapphire, Netrunner
- Critique - Greg (Golden, CO), execute aka Ex3cut3, Chris, rootx11
- The Hacker Ethic - anonymous, Rob T. Firefly (Rob Vincent, MySpace)
- Questions - ng, sergio, Cybersavior, tyg0n, Tony, 'Notary Public', Steve, Chris Hanks, Razorface, drlecter, James
- Problems - echolon, Jeff (London, Ontario), VanEck, your_uncle_vinny (Maine), Wendy (Lakeland, FL)
- The School System - ThyF, PSX00 (Michael J. Moro, Waukesha, WI), JavaJacker (Dallas, TX), MacAllah
- Something Positive - Veg, JL (Arvada, CO), Y2kbug, bernz, bradsnet, Buzzter66 (Houston, TX), James
- Further Info - Karl, Andrew, rook, Fractal, Ion, Steven, Jennifer, Toph
- A History of "31337SP34K" - Explaining to a new generation of hakkerz into what "elite speak" is, where it came from, and when (and if) to use it, by StankDawg
- Hardware Broadband Client Monitoring - An Overview - A look at the possiblity of telco/ISP monitoring of your DSL traffic and ways to prevent that, by psyk0mantis (Email)
- How to Set Up a Free (Secure!) Web Server at Home - How to hide a web server (TinyWeb) on a Windows server on a household cable/DSL connection, by Khoder bin Hakkin
- A Word of Warning from a Caught Uncapper - Story of a caught cable modem "uncapper" who was nearly criminally charged and how it's not really worth it, in the long run, by Kris Olson
- Hacking Electronic Message Centers - A detailed look at the hardware and software used by those popular Electronic Display Systems' electronic message signs, by Mr. Glenn Frog
- Breaking Down the Dynix Door - How to harass those poor old librarians who didn't lock down their Dynix Automated Library Systems, by iCe799 (Joe Damato?, Email #2)
- The Current State of E-Commerce Security - A real-world example of exploiting e-commerce website "shopping cart" security issues via client-side editing of sent HTML data, by Derek P. Moore (Email, GitHub, Twitter, Resume)
- Book Review: The Art of Deception - Book review of Kevin Mitnick's The Art of Deception, by Evil Corley
- 2600 Marketplace
- 2600 Meetings
- Issue's Cash Cow: How the (((mass media))) manipulates what we see and hear and the FBI now going after "cyber-based attacks and high technology crimes."
- Cover (Cover Info)
- Back Inside Scottish Payphones
- Luss #1 This phone takes both cards and coins. Photo by John Klacsmann
- Luss #2 This is the card-only version. Photo by John Klacsmann
- Edinburgh A "mini" payphone that takes cards and coins. Note the coin drawer at the bottom. Photo by John Klacsmann
- Dundee #4 This is a high-tech Internet phone that takes cards and coins. Judging from the size of the coinbox below, the rates aren't cheap. Photo by John Klacsmann
- Back Cover Netherlands Antilles Payphones
- Island of Bonaire #1 This phone looks a little short for a payphone. Photo by Will Ellis-Adams
- Island of Bonaire #2 Looking closer, we can see that this is a card-only phone with the coin return and coin box missing, which is why it seems so squat. Photo by Will Ellis-Adams
- Island of Bonaire #3 Another weird looking model which doesn't appear to take coins or cards. (Or prepaid calling cards.) Photo by Will Ellis-Adams
- Island of Bonaire #4 This is the weirdest yet! It looks like someone just replaced the payphone with a white deskphone. Try doing THAT in the USA. Photo by Patrick Webster
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 19!
$2600 Magazine - Volume 19, Number 4 (Winter 2002-2003)
- Positivity - Editorial
- Passport Hacking Revisited - Vulnerability in Microsoft Passport due to its complete dependence on cookies, by Chris Shiflett
- Passport Hacking Revisited Original
- Lazy Exchange Admins - Security holes in Microsoft Exchange servers - including a way to remotely crash them and guessing the administrator account address, by ddShelby (George M., Savannah, Georgia)
- Warspying - Utilize a portable X10 video receiver to scan for wireless X10 cameras, VCR, or cable TV connections, by Particle Bored
- CD Media Data Destruction - A look at what it would take to properly physically destroy a CD-ROM/RW/Rs, by Gr3y t0qu3
- PSINet Update - $2600 received a check for $3.12.
- How to Make a DVD Backup - Very good and detailed article on the steps and software required to properly rip, copy, and encode DVDs, by Maniac_Dan
- Letter From the DOJ - Regarding a hack which never took place?!
- Honeypots: Building the Better Hacker - Overview of using computer honeypots and how they may not always be practical in stopping (or exposing) a really dedicated attacker, by Bland Inquisitor
- DNS Redirection Stopped - Example HTML script and VB program to check the web browser's sent "host" via the HTTP request, and redirect the query to a different host if necessary, by c0ld_b00t
- Code: dns-redirect.vb
- More on Telemarketing - More tricks for defeating telemarketers, by D. Foetus (D.L. Jones)
- Cracking Voter Fraud - Story from a 2600 reader who was involved exposing suspected fraudulent voters in New Brunswick, New Jersey, by Kr@kH3d (DFxC, Dominick)
- Linux on the Xbox - Overviewof the necessary steps, modchips, and BIOS modifications required to install Linux on an Xbox, by Live_wire
- More Xbox Fun and Mischief
- The Complete Guide to Setting Up Evox.ini
- Mirror of distribution.xbins.org distribution.xbins.org as of Sep. 20, 2017
- How Sprint Raises Quick Cash - Dirty tricks on Sprint billing.
- Removing Spyware and Adware - Overview of removing spyware and adware which is bundled with many Windows P2P clients, by 0/\/3_3y3d_/\/\0/\/st3r
- Exposing the Coinstar Network - A quick overview of Coinstar change machine and their network, by area_51
- A Dumpster Diving Treasure - Story of finding a working Alteon iSD-100 in the garbage and getting it up and running, by phantasm (Robert Davies)
- DMCA vs. DMCRA - A look at the Digital Media Consumers' Rights Act which is designed to give consumers rights the DMCA took away regarding "fair-use" rights of copy-protected CDs, by Alex Daniel
- Letters - Blather
- Spreading News - NoSpahm, Keith, scott, Sardonicus, cybernard
- Terrorism Related Issues - Tresser, jmu, Herman, PLMN, Lectoid, Surfgods, LordKhamul, Hells-own, Kr00lee-O
- Dumpster Diving - Paddy, Nomad, Stinky
- Feedback - Traveler, XiChimos, joe, Bob M., Eil, Charles, Shadowfax0 (Kingston, Ontario), hawk2000, Poetics, Nietzsche, JaMm3r, Rob T. Firefly, Jason Argonaut, Resurrection20
- Injustice Department - deejayred2001 (Templeton, CA), Matt, Evnglion, im_source, Dune Tanaka, Todd
- Thoughts On Piracy - I1269U (Leilan, Harrisburg, PA)
- Questions - Super-Fly, In a TrAnCe, QuietShadow (Liz), Phate_2k2, Quiet Riot, ddShelby, Ganja51 (Kris Blommel, Rosemount, Minnesota), Tony
- Observations - Freddy, Quebec, Mark, The Nibbler, Spooky Chris, jesse, christopher, jasonburb, jmk, Radarjam, sunzi, Cambalache20, k1d0n, derrick
- Tale From The Past - John K.
- Retail World - Zac T., XiChimos, acj626 (Arleigh, Austell, GA), pinchepunk (J.M, Chicago, IL)
- Parallels - Sparkster
- A New Project - Poetics, Elf Qrin
- Critique - AGE_18, Dave D.
- Significant Developments - RusH, fstratto (Frank Stratton, Urbana, IL)
- Defining Hackers - f0x deacon
- Reaching Out - Nyght
- Hostnames of .ncsc.mil (144.51.x.x) - List of hostnames for the 144.51.x.x network
- A Brief Introduction to Deep Freeze - Overview of Deep Freeze, software which "freezes" your Windows software configuration, by The Flatline
- Deep Freeze 3 (Standard) - User Guide Windows 95/98/ME
- Deep Freeze 4 (Standard) - User Guide Windows 2000/XP
- Deep Freeze 2 (Standard) - 60-Day Demo Version v2.10.000.0265
- Deep Freeze 3 (Standard) - 60-Day Demo Version v3.20.000.0505
- Beating Download Manager Protection - Ideas for defeating file blocking ("Download Manager Blocked" messages) used by various websites, by Straightface
- DHCP is Your Friend! - A good look at DHCP and the dangers of non-authenticating DHCP servers which will hand out IPs to just about any MAC address, by di0nysus
- 2600 Marketplace
- 2600 Meetings
- Issue's Cash Cow: In the fast paced culture that we seem to find ourselves caught in the middle of, it's very easy to get stuck in a default mood of euphoria or despair. Lately it seems that we ve been despairing quite a bit. We're certainly not alone.
- Cover (Cover Info)
- Back Inside Forbidden Payphones
- Alexandria, Egypt It's illegal to take pictures in Egyptian airports. Here's one they couldn't stop. Photo by Tom Mele
- Tunis, Tunisia Taking photographs in public here is considered an offense worthy of incarceration. This was a "drive-by" of one of the payphone rooms that exist throughout the city - there are no single payphones anywhere. Photo by John Freund
- Xi'an, China This card-only phone is the most common type. The writing on the blue plastic says: "It is everyone's duty to be careful with public phones." Photo by Robin Kearey
- Shanghai, China The type accepts both coins and cards. Photo by Robin Kearey
- Back Cover South Korean Payphones (we will pay any price for pictures of North Korean payphones)
- Seoul #1 The most common type of payphone which only accepts cards. Photo by Robin Kearey
- Seoul #2 A coins-only version, also fairly common and usually found near the cards-only phones. Photo by Robin Kearey
- Kyeonghee University The old style coins-only payphone which is becoming increasingly rare. Photo by Robin Kearey
- Seoul #3 This is a rare phone too. Its location is probably even more rare. Photo by Robin Kearey
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 19!
$2600 Magazine - Volume 20, Number 1 (Spring 2003)
- Not In Our Name - Editorial
- ANI and Caller ID Spoofing - Very detailed article on the commons methods to spoof the Calling Party Number (CPN) parameter and even ANI, by Lucky225
- spoof.ogg In this recording, you hear a call being spoofed as 909-661-2600. The number called is the 800-555-1140 ANAC that will announce 909-661-2600 as the number being called from.
- Caller ID Spoofing Through TELUS As demonstrated at H2K2, by Lucky225
- Automated Caller ID / ANI Spoofing
- AOH Caller ID
- A Hacker Goes to Iraq - An old-school hacker discusses a possible trip to Iraq in order to protest the (((sanctions))) against them and teach computer programming to Iraqi students, by Chris McKinstry (Mindpixel, Wikipedia Entry, Flickr)
- Getting Busted - Military Style - Good (insider?) overview of the Uniform Code of Military Justice and what it's like at Fort Leavenworth, by TC
- Unsolicited Mail - An apparent U.S. Navy Special Warfare Development Group SIPRNET email was sent to a public Internet mailing list...
- Anonymous Email Using Remailers - Good overview on using (or setting up your own) anonymous email remailers, by angelazaharia
- Frequently Asked Questions About Mixmaster Remailers by Lance Cottrell (1996)
- Fun With 802.11b at Kroger - Overview of the wireless network at Kroger stores and the possibility of intercepting their open Telnet traffic with Kismet, by Kairi Nakatsuki (Email)
- Best Buy Insecurities - How to access the Internet via computers at Best Buy, by WInt3rmut3
- Warner Bros. Threat Letter - (((Warner Bros.))) sends piracy threat letters to the theater's managers and projectionists!
- Ripping Movies from DVD to CD-R - Detailed overview of how to rip DVDs using various free software packages to emulate DVD Copy Plus, by Solthae
- XM - The Flawed Future of Radio - Basic technical overview of the XM Satellite Radio service, by Acidus
- Letters - Babble
- The War on Stupidity - JF (Texas), FEMA Emergency Contacts Directory - shaggyeightball (Harold Backer), eigenvalue (Canada), 2600 Reader
- Random Observations - kyoung, Tom, CaptainJ, TwinZero, rOb, dougk ff7, Phake, Victor Hugo, Herman, Abstract, Robert (Johannesburg, South Africa), squid, confusedbee (Elizabeth J. Clayton, Toronto, Canada, DOB: 01-22-????), fremont_dslam, eyenot (Gabriel Arthur Petrie), scott (West Nyack, New York), Aaron, (none given), dominatus, chaos985 (William Harry, Email #1, Email #2, West Palm Beach, FL, DOB: 11-30-????), 2600reader
- Meetings - x, cs, Oversight
- Security - DWD, Poetics, DVNT
- New Projects - Jari (Finland), Ghent
- Inquiries - kayvan, root, InfrHck, x8ou;##5, Ray, Mark, osiris, kaspel (New York, New York), alan
- New Feedback - ByteEnable (Austin, TX), Jester (New Jersey), Aaron, Kimberly, Anewname (Toronto, Canada), glenn, cOld.bOOt, TheTechnophile
- Response to Old Feedback - Kyle, JohnnylS (San Diego, CA), Zeitgeist, Blake, CableTick, Lunacite, Jon
- Bypassing Security - LMB
- Problem Solving - Pi, Siece, Pete
- Cover Comments - BC, CrzyDragn, Leprkan, f
- An Accomplishment - Adam
- More on Telemarketing - TimBER
- Discoveries - Poetics & Stealth5325 (Steve), Osiris, DriZakE, EBone, N (United Kingdom)
- Suggestions - DarkSide
- Dangerous Info - Beowulf
- A First Look at Virgin Mobile - Technical overview of the Virgin Mobile cellular carrier and some useful handset tips, by The Prophet
- Creating Delay in the New Age - Using three-way calling to recreate the old phreak sounds of "tandem stacking," by Screamer Chaotix
- iBuySpy Portal Software - Overview of the Microsoft's iBuySpy Portal software - and huge bug to grab plaintext passwords, by Papa Doc
- Code: ibuyspy.vbs
- Defeating Salon.com's Premium Content - View "premium" Salon web pages without having to pay for them by editing your browser cookies, by annie niemoose
- Fun With Hosting on Your Cable/DSL - Additional tips for port forwarding and dynamic DNS when hosting your own servers on a cable/DSL connection, by Toby (Ryan Toby Richards)
- Keyboard Theory for the New Age Phreak - Neat concept linking piano keys and their associated frequencies to the tones used by the telephone system, by autocode
- A Glimpse at the Future of Computing - Discussion of what would happen to the Internet if it was ever taking over by "progressives," by Phocks (? Joshua Birtles, Brisbane, Australia, GitHub, Website #2)
- 2600 Marketplace
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: How hackers can help prevent dictatorships, whether in foreign countries, or under Obama/Biden/Corley.
- Cover (Cover Info)
- Back Inside Egyptian Payphones
- Egypt #1 This is known as a "Nile" phone. They're fairly popular and widespread and they use prepaid cards. Photo by Encrypted_Error
- Egypt #2 This is a Telecom Egypt phone which can be found near phone company buildings and a few other places. Even in Egypt, phone companies seem to like using that silly swirl symbol that seems to dominate the technology world. Photo by Encrypted_Error
- Egypt #3 An old Telecom Egypt phone found at a major bus station. Photo by Encrypted_Error
- Egypt #4 An even older Telecom Egypt phone that takes coins and could really use a good scrubbing. Photo by Encrypted_Error
- Back Cover Thai Payphones
- Thailand #1 This is as bright and as blue as they come. Photos by Dieter K.
- Thailand #2 A phone designed for international calls that takes all kinds of credit cards. Photos by Dieter K.
- Thailand #3 From Bangkok. The booth alone is a spectacle to behold. Photo by Matthew Swenson
- Eritrea Found in a small town called Keren. Famed for behold its sacred baobab tree, its walled camel market, and its dwindling population of landmines. Photo by Mark Sadler
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 20!

![[iboughtit1]](2600tshirt.jpg)
New $2600 Magazine T-Shirt Ideas
$2600 Magazine - Volume 20, Number 2 (Summer 2003)
- Disrespecting the Law - Editorial
- Roll Your Own IIS Intrusion Detection System - Detect attacks on an Microsoft Internet Information Services web server with this useful Perl script, by The Rev. Jackal-Headed-God (Corey Ehmke, Bloomingdale, Illinois)
- Watcher.cgi Watcher/WormSign is a small-footprint, passive intrusion detection system for IIS written entirely in Perl.
- Traversing the Corporate Firewall - How to pass non-HTTP traffic through a firewall using port forwarding and SSH, by superheast
- BSODs Everywhere - BSOD seen on an Internet payphone in London.
- Staying Anonymous in the Information Age - Social engineering tips for obtaining private information and also some tips on how you can protect yourself, by Lucky225
- Hardware Key Logging - Overview of operation of hardware key logging devices, like the KeyKatcher keystroke logger, by XlogicX (Eric Davisson, Email, GitHub, Twitter)
- ooPIC Multi-Language Compiler Ver 5.00 Full install for Windows 95/98/ME
- NT Printer Port Driver Need to run compiler v5.0 under Windows 2000 or NT
- ooPIC Manual & Technical Specifications
- ooPIC Compiler IDE Via SourceForge
- Wireless Keystroke Data Tap
- Peeling Grapes - A look at "peeling back" website security and layout using PHP, by Bryan Elliott
- Microphones, Laptops, and Supertaps - Potential security problems with unsecured computer microphones or headphones, by Dark Spectrum (Wideband Dreamer)
- Optimum Online and You - Using Optimum Online cable ISP services and how they block or filter incoming traffic, by Screamer Chaotix
- Cyber Cafe Software Security - A look at TinaSoft's EasyCafe cyber cafe software and some potential security holes, by minion
- A Coupon Trick - Story of generating your own UPC code on a coupon to increase its value, by Charles
- Hacking the Look - Tips using Resource Hacker to tweak the look of your Windows system, by Rev. Edward E. Karn (ZenLogic)
- Hacking the Look Original
- Hacking the Look: Revisited
- Resource Hacker v3.4.0 (555k ZIP)
- Hosting a FTP Server on Cable/DSL Routers - How to host a FTP server under Windows 2000 on a cable or DSL connection, by osiris188 (Canada)
- GuildFTPD v0.999.13 GuildFTPD is an FTP server with special support for IRC, by Matthew Flewelling (1.8M EXE)
- Homeland Security - Homeland Security Services Corp. of Springfield, Illinois
- Letters - Voices
- Sensitive Info - f0urtyfive (Matt Mills), brian
- Handy Tips - Jason Argonaut, favdog
- Policy - Gloria, Captain B, Pi, No Name
- Dealing With Opposition - anonymous, Brian
- Defining Terms - fyrwurxx (Austin D.), fyrwurxx, revanant
- The Law - tack, Magelus, Jeremy, KoDo
- Letter Responses - encrypted, Lookat ThatThar, TC, blanch, p3rl_junki3, Ninjalicious (Jeff Chapman), darkism, dhax, area_51, drlecter, Walter
- Web Feedback - Scared in Iowa, demothenes (Mesa, AZ), Talofa, Inacho
- Unlearn - Screamer Chaotix, JPK, Amanda, Camille, Meriana, Christina
- Random Observations - fremont dslam, Weex, Scott, Sunfist, Jonathan, NeuRd, Procyrus (Ohio), J, Ivan, anonymous, Zen Lunatic, Mark Sadler, Mr. "of Lag"
- Economics - Lamerjoe, J. Miller
- Misconceptions - brian botkiller (MySpace)
- Article Clarifications - Toby, Marc Wallace, Firehazard, Matt, Jim, Papa Doc, Flat Line, Lucky225, Stormbringer (William K. Smith)
- Clearing Blockages - Skazz, Bullet, Logix
- McWireless Exposed - Overview of McDonald's new public Wi-Fi network and some bonus backdoor logins, by Epiphany (Darien S. Acosta) and J0hny_Lightning
- 802.11b Reception Tricks - Adding and external antenna and other hardware tips to improve 802.11b networking performance, by ddShelby
- Distributed Reflective Denial-of-Service Attacks - Overview of the dangers of newer DRDoS attacks which exploit the TCP 3-way handshake and how networks are potentially vulnerable to them, by Spyrochaete (Brian, DJ Brian Damage)
- Fun With the Nokia 3360/3361 - Outlines how to change the alpha tag and network settings on the Nokia 3360/3361 phones, by FragSpaz
- Why Red Boxing Still Works (sorta) - It appears possible to Red Box off live operators - if your're nice to them, by Plazmatic Shadow (cmantito, Kevin Leacock, LiveJournal)
- XPloiting XP - Good overview of the techniques required to get around Windows XP serial numbers and activation, by Bill Melater
- Windows XP Professional Service Pack 2/3 VOL/VLK Keys
- How to Change the Windows XP Product Activation Key Code
- XP SP1 Updating
- 2600 Marketplace
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: Fighting the DMCA, RIAA, MPAA over the right to use file sharing.
- Cover (Cover Info)
- Back Inside Island Payphones
- Fiji This is a charge card phone. Note that "Q" and "Z" are represented by the 1 key. Photo by Zach Andersson
- Turks & Caicos An outdoor booth operated by Cable & Wireless on one of the islands of Turks & Caicos. Photo by nexus-3
- New Zealand A coin and card phone with plenty of documentation and accessories surrounding it. Photo by J. Hamilton Davis
- French Polynesia This phone was found on an island called Huahine. Photo by J. Hamilton Davis
- Back Cover Irish Payphones
- Ireland #1 From Cong is County Mayo of the Irish Republic, a card/coin model operated by Eircom. Photo by Jamie Stack
- Ireland #2 This could be the same exact phone captured by an entirely different person, but we doubt it. Photo by Raul Perez
- Ireland #3 An outer view of the booth of the previous phone(s). Photo by Raul Perez
- Ireland #4 An entirely different type of phone from a different company known as ITG, whose phones can be found across the British Isles. Photo by Raul Perez
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 20!
$2600 Magazine - Volume 20, Number 3 (Fall 2003)
- Feeding the Frenzy - Editorial
- Getting to Know Your Neighbors - Overview of using Kismet to look for local wireless networks to connect to and using LinNeighborhood to browse Samba/SMB shares, by Shiv Polarity
- 2600 Blocked in Qatar - 2600 website is blocked by the Qatar government.
- Servers on a Ghetto ISP - Running and hiding servers (like Sendmail) on a cable/DSL connection in which the ISP is blocking ports, by Lirakis (Eric Tamme, New Rochelle, New York)
- More Methods for Hosting FTP on Broadband - Methods for running (and hiding) a FTP server on cable/DSL connection, by Apratt
- Hacking the Look: Revisited - How to install alternatives to the stock Windows Explorer desktop and shell, by mojomonkee (Brian Connolly)
- Case Mods Made Easy - How to make your computer case look pretty, by X3N0X
- DVDs on a Pocket PC - Play DVDs on a Pocket PC, by Shawn Frederick
- DVD2AVI v1.77.3 Stable version, resize function unfinished.
- More Xbox Fun and Mischief - A look at Xbox hardware modifications and modchip installation, by spite
- Linux on the Xbox
- Xecuter 3 Installation Tutorial (v1.03)
- Xecuter 3 CE Installation Tutorial (v1.0 - v1.6)
- Heimdall's Xbox Engineering Disc 2018
- Mirror of distribution.xbins.org distribution.xbins.org as of Sep. 20, 2017
- Shopping for a Security Flaw? Try Retail - Potential to exploit security holes at retail stores via their open PBXes or ignorant employees, by dead_pilgrim
- Troubling Target - It appears possible to execute the infamous NT bug on Target store Symbol 6800 barcode scanners, by redxlegion (Red Legion, DOB: 08-21-????, Michigan)
- Blockbuster Tricks - Social engineering Blockbuster by pretending to be another store to get out of late fees or to even keep the item itself, by C.B. Cates
- Webhacking with CVS - Looking for potential secret information in open CVS directories, by methodic (Tony Lambiris)
- Webserver CVS (In)Security Original
- Basics of Cellular Number Portability - A good look into how cellular number portability works, by C3llph
- The Hacker Diet - How to eat good, by Shade
- feather.c - C code to preserve a program's atime and mtime after execution, by Kairi Nakatsuki (Email)
- Code: feather.c
- Letters - Articulated GIBBERISH
- Article Feedback - rFmAn, Matt M., Austrailian Knight, shaggyeightball, Tonio K., Scott (New Jersey), Analog666, mojomonkee, Al, JL, D1vr0c (David Crowe), mAineAc, Jim, Eeviac
- Confusion - Manga, netj, Sph1nx
- Newbies - MarBle, Henry (Germany), Drake Smith, Joseph, Thierry (Africa)
- Have You Heard? - Jesse W., PhrenicGermal (Thomas Hodges, Winfield, IL, DOB: 11-29-????), MacAllah
- Taking Action - Patrick
- Observations - Satch379, SeKToR, Spua7, Dave C, John Tate, CPUHaxxer, aaron t, Eric
- Keep The Faith - tWiST, c0l0r3dfr34k (Anthony, DOB: 02-22-1984), Bob
- The Past - walt, kdg, Fruber
- Destructiveness - Lord Kahless
- The Quest For Knowledge - slax0r (Eric Agan, South Bend, Indiana), Brainwaste, Helen
- Piracy Prevention - semicerebral, eigenvalue
- Insecurity - tr, osiris, Big B. Statz
- Suggestions - drlecter, Ion, PCBootlegger, scissorjammer (Alex Rakoczy, DOB: 12-07-1986), Concerned Grandma
- The Authorities - Performaman, Alan (The Hague, Netherlands, Note: The Taliban receives their money from drug sales in Holland and Western Europe)
- Concerns - Caps Lock, Sam, Martin
- Chastising the Ignorant - leetkurp (Atlantic City, NJ)
- A Sign of Hope - theXorcist
- Denial-of-Service Attacks, Tools of the Tools - Overview of how denial-of-service attacks work and some of the tools capable of causing them, by bland_inquisitor
- Frequency Theory for the Phone Hacker/Musician - How audio frequencies in the phone system and music are spectrally related, by The Piano Guy
- A Trip Down Memory Lane - Story of using the early browsers and UNIX email/chat utilities while on the Internet, by Jimmy Yu
- Finding Ogg - Audio Evangelism - Overvview of the Ogg Vorbis audio encoding format as a replacement for MP3, by The Dark Shirt (Irving Washington, London, U.K.)
- Infidelity in the Information Age: How I Caught My Cheating Girlfriend - Story on how "deleted" information on computers really isn't, by atoma
- The Threat of Biometrics - Overview of the MorphoTouch biometrics system installed at a school, by _cHiCkEn_ (Pennsylvania)
- Gentner GSC3000 for Total Morons - Information and command overview of the Gentner GSC3000 radio station remote facilities control system, by blakmac (Blake MacArthur)
- Genter GSC3000 Remote Facilities Management Installation & Operations Manual Gentner Part No. 800-085-100 (1998)
- Burk Technology GSC3000/VRC2500 Broadcast Facility Control Systems Installation & Operations Manual (2006)
- Genter GSC3000 Voice Interface Installation and Operations Manual Gentner Part No. 800-085-130 (1999)
- Burk Technology VRC2500 Remote Facilities Management Installation & Operations Manual (2002)
- 2600 Marketplace
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: It's clear there's a lot we're not being told and that there are many in power who would like to keep it that way.
- Cover (Cover Info)
- Back Inside Costa Rican Payphones
- Costa Rica #1 If it wasn't for the "Call USA" on the bottom, we would have had a very hard time telling which end was up on this tiny phone. Photo by Ricardo Muggli
- Costa Rica #2 Unlike in the United States, many foreign payphones are proud of their phone numbers. We suspect this one may soon be ringing off the hook. Photo by Ricardo Muggli
- Costa Rica #3 It's kind of hard to believe that this is in the same country, but this old metallic model phone can also be found in Costa Rica. Photo by Ricardo Muggli
- Costa Rica #4 Our favorite is the even larger metal box with tiny keypad. Think about it - at some board meeting in the past, this design beat out the competition. Photo by Ricardo Muggli
- Back Cover Payphones From Egypt
- Egypt #1 Completely different from the four we printed two issues ago. This one is a Menatel, probably the most popular and widespread payphone in Egypt. It uses prepaid chipcards. Photo by Encrypted_Error
- Egypt #2 What the connection is to the former Beatle we don't know, but these phones use prepaid cards and are only found in Cairo and Alexandria. Photo by Encrypted_Error
- Egypt #3 This phone was found in the middle of the desert. Not much is known about it other than the fact that it only takes coins. Photo by Encrypted_Error
- Egypt #4 This is actually the exact same kind of Telecom Egypt phone we printed in the Spring issue, but this one is a completely different color! And that makes all the difference. And no, she isn't giving us the finger. Photo by Encrypted_Error
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 20!
$2600 Magazine - Volume 20, Number 4 (Winter 2003-2004)
- Paranoia vs. Sanity - Editorial
- Hacking the Genome - The creation of Genetically Modified Organisms (GMOs) is now within the ability of a knowledgeable and dedicated hacker, by Professor L
- Hacking the Genome- Designer Proteins, Elite Organism, and You by Russell W. Hanson, from his speech at 21st CCC (Slides)
- Whom Do You Trust? Issues of Several CAs Authentication Mechanisms - Good SSL overview and how the author was able to trick Certification Authorities (CA) to issue him a certificate, when they really shouldn't have, by Juraj Bednár (Slovak Republic, Email, GitHub, Twitter, )
- System Profiling Through RPC - Overview of probing, and/or exploiting, hosts via open RPC daemons, by Screamer Chaotix
- Robots and Spiders - How Internet spiders (search engine crawlers) work, loopholes, and potential security issues, by StankDawg
- Living Without a SSN - Very detailed (and modern) article on how to avoid giving out your Social Security number during credit card applications, etc., by Lucky225
- Cellphone Without SSN alt.cellular.attws posting
- More Fun With Wireless Hacking - Quick notes on Wi-Fi hacking and the dangers of using WEP encryption, by VileSYN (Dennis Brown)
- More Fun With Wireless Hacking Original
- WEP: Not For Me - Story of a person scanning for Wi-Fi devices and finding lots of open Access Points, includes a list of default logins & password, by 0x20Cowboy
- Wardriving with a Pocket PC - How to use a Pocket PC and MiniStumbler to wardrive Wi-Fi access points, by RaT_HaCk
- vxUtil Windows CE 2.x.x, 3.0 (or later) (HPC Pro, Pocket PC, Windows Mobile 2003) software (version 1.6.2, 02/06/2005)
- vxUtil Windows CE 2.0 and Palm-Size PC software software (version 1.6.1, 03/12/2004)
- Verizon's Call Intercept - Overview and potential security loopholes in Verizon's Call Intercept service, by decoder (William Quinn)
- Verizon's Call Intercept Original
- Become a Hacker - Ad for Cert Camp.
- Fun With Hping - How to use Hping, a program which allows you to create arbitrary packets with all types of options, by methodic
- Remote Computing Secured - How to secure Virtual Network Computing (VNC) using SSH and SSL, by Xphile
- Letters - Speech
- Getting Around the System - Evil Alex, Rifkey, Khoder bin Hakkin
- Miscellaneous Fact - SFG
- New Ideas - Erik, Chris
- The State of Education - richard, Muttski, lord_stinkington (South Carolina), alex (a.k.a. Suge, Florida), Sheff-Boy-RD (Adam Sheff)
- Military Readers - Neo, Noname, PhatMan (Canada), karniv0re, Cpl Grimes
- Miscommunication - Regards
- Further Info - DeadPainter, Anonymous, miniz003, Slacksoft, hbob, mrbrown8 (Curtis J. Brown), Sparklx, Somar, Taurus Bulba, Hroly
- Misdeed - Paul
- Pointed Questions - TrIpAnDaNce, magnum0711, Marcelo Barb (Brazil), Ken
- Call For Help - Professor_Ling
- The Issue of Piracy - fH, martianpenguin (DOB: 12-03-1985), Jeff, Hooky1963
- Some Clarifications - Mark A. McBride (Evans, GA), Colonel Panic (John S. Albert, KC9EQK), D1vr0c, Poetics, phresno
- Spreading Knowledge - Robert (Portland, Oregon)
- Food For Thought - Blair (California), Code Dark, nameless, SoftwarePir@te, Jon, Anonymous
- Info Needed - Mike, Scott, Uncle Dust, Elvis Carter-Abbot
- Ominous Developments - czarandom, Iz
- Annoying Problems - Daniel, Erik, zs (Zachary Smith), sandman10_99, Lily
- Appreciation - ReDLiNe135, Tarball Gunzip
- Reader Advice - Stone Wolf, Chris, crypto
- Stories of Insecurity - Cory K., Zardoz
- DISA, UNIX Security, and Reality - Overview of the U.S. Department of Defense recommended UNIX security configuration specifications, by sunpuke (Robert Escue, Virginia Beach, Virginia)
- Hacking the "Captivate" Network - Overview of the Captivate screens mounted in some elevators and how to connect to their wireless network, by Darlok
- Unlocking GSM Handsets - How to unlock some common GSM handsets for use on other cellular phone carriers, by The Prophet
- FAQ: How to Flash / Repair / Unlock Nokia Mobile Phones
- GSMANIA
- Code Calculator 5.4
- DCT4CALC.COM HONGXING DCT4 Calc 3.0 for MS-DOS
- Yet Another DCT4 Calc by Wilson
- Nokia DCT4 Mastercode FREE 1.0 by TechGSM
- Cybergasm DCT4 Calculator 1.4
- Unlocking WebLock Pro - Information on how to defeat the WebLock Pro HTML source protection system, by Schnarf
- Code: decode.pl
- Example Output
- Holes in Windows 2003 Server - Setup Manager overview, passwords are standard LAN Manager hash capable of being attacked by John the Ripper, by Joseph B. Zekany (Zucchini)
- Code: xpgrab.pl
- Setup Manager Windows 2003 Server
- Windows Server 2003 ISOs (Key: QKDCQ-TP2JM-G4MDG-VR6F2-P9C48)
- How to Mess with Citibank Collections - Tips and tricks for messing with (and avoiding) Citibank's collection centers, by The Pissed-Off One Armed Man
- 2600 Marketplace
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: Same nonsense as 10 years ago
- Cover (Cover Info)
- Back Inside Payphones From All Around The World
- Romania One of the more modern phones useful for telling you the date and time among other things. And it's orange! Photo by Dieter K.
- Singapore So much for the perfect society. Apparently payphone theft is still a popular activity. Photo by Louis Pezzani
- Paraguay Located in the Monday State Park near the Monday Falls in Ciudad del Este. Photo by Darryl Duer
- Colombia Found in the airport of Barranquilla. We just don't see enough orange phones. Photo by Bruce Engelberg
- Back Cover Payphones From Everywhere
- Glenfinnan, Scotland A colorful old style coin-only phone with a large coin box. Photo by John Klacsmann
- Dundee, Scotland The most high-tech payphone in Scotland. It's Internet-ready and takes both coins and cards. And the coin box is even bigger. Photo by John Klacsmann
- Hong Kong #1 Another colorful variety with a unique shape and a lot of directions. Photo by Dieter K.
- Hong Kong #2 The PowerPhone enables you to see video while making calls. Photo by Dieter K.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 20!
$2600 Magazine - Volume 21, Number 1 (Spring 2004)
- Twenty Years After - Editorial
- Taking Advantage of Physical Access - Physical security for your computer and the easy ability to copy hard drive contents to an external drive, by Evil Wrangler
- Bypassing Minor Website Security - Several tricks for defeating right-click suppression, anti-content saving, and cookie checks, logging, etc., by Galahad
- Exploiting AIM Screen Name Loggers - Exploit to gain admin access to any IMChaos account by spoofing the AIM Browser window, by Stik
- Code: imchaos.cgi
- Using Perl to Defeat Provider Restrictions - Using a couple of Perl CGIs to alert you if your dynamic IP address has changed, by TRM
- A Simple but Effective Spanner in Your AVS - Trick program to defeat an anti-virus scanner (Symantec, McAffe, etc.) by covertly deleting the EXE or other required operating files, by Irving Washington (Email)
- Hacking the Hilton - Using the (paid) high-speed Internet connection at Hilton Hotel's for "free" by using non-standard ports, by Estragon
- Hotels: Your Inn for Access by dual_parallel
- Cruise Cracking - Carnival Cruise computer network overview and a look at their "Sail and Sign Cards," by Jesters8 (Stephen?)
- A Sprint PCS Trick - A look at the Sprint-to-Sprint trick discussed on Off The Hook and op-diverting to "ANI Fail," then supply the target's number. It's also possible to uncover the target's PIN via their voicemail settings, by quel
- Hacking a Mercedes-Benz with a Universal Remote - Use an universal IR remote control to record the "Lock," "Unlock," and "Trunk Release" infrared codes used on older Mercedes-Benz vehicles, by TOneZ2600 (Corey Friedman)
- The $40 Hardware Wardialer - Palm V PDA plus a Palm modem and Kingpin's TBA software to create a low-cost war dialer, by Grandmaster Plague
- TBA_v1_prc.zip Version: 03.24.00 / Palm OS 3.0 to 3.3 / Fully-functional wardialer for the Palm OS platform.
- TBA Handbook The wardialer for Palm-powered devices.
- War Dialing Brief by Kingpin
- Serial Number Security - Why hardware product serial numbers should not be out in the open and the potential ability to "social engineer" free items, by TEV (U.K.)
- Barcode Tricks - How to read UPC barcodes and several tricks for "changing" their values, by XlogicX
- Installing Debian on Your Unmodded Xbox - How to install Linux on your Xbox without any significant hardware modifications, by dave (U.K.)
- Turn an Xbox into a Debian Server
- Technical Analysis of James Bond 007: Agent Under Fire Save Game Hack (007linux.zip)
- Game Console Hacking: Have Fun While Voiding Your Warranty by Joe Grand, Albert Yarusso, Ralph H. Baer, Marcus R. Brown, and Frank Thornton
- Letters - Mind Exercises
- Assorted Questions - Jason, Andrew, tchnprgrmr (Ceda, Jacksonville, FL), Alexey (Russia), Multivac_Kleenex, N,cow, moviestardog04, Jerry, Phreakinphun
- Con Game - Darkstorm777 (Steven Caputo, Email #1, Chicago, IL)
- Random Feedback - Osama, Anton, Performaman, Amit Jain, Adam Rzepka, FTE, gabriel aaron, Digital_Cowboy, uberphreak, Enonymous, Ian Johnson (jwoulf, LiveJournal), The Fallen One, rainwater5 (Scott), Eric M., Mike Neary, drlecter (Weston George), Blimpieboy, Witchlight, Karlman Rovetounge, Daniac, NGTV|3
- Help Offered - loco freak
- Observations - MoJo, darkpo3t (Daniel Hmeidan, DOB: 02-19-????), Poetics, Jim_Steele (San Francisco, CA), jake, drlecter, SAR, Louie, lint, Stephen
- Military Readership - d0rk, misterjager, MegaGeek, slack_pizza_guy, jim, E8Q
- A Problem - ALI
- The Power of Ignorance - the_heretic, AltSp4c3Ctrl, John Anon, thesuavel, sunami, ieMpleH, mord
- Tips - College_Student
- Meeting Trouble - Kaosaur
- From the Other Side - rewt, Rafin
- The Music Industry - Jakob Larson
- More Bookstore Hijinks - Cygnwulf, MG48s
- Thoughts on Terrorism - drlecter, Lindsey The Boy
- To Clarify - Lawrence, ZeroSpam
- Mentoring - Billy, Radix
- Working Around the System - Nathan
- Uncapper's Paradise - Overview of uncapping your shell-enabled cable modem (SURFboard SB2100) by adding IP filters or changing the HFC MAC address automatically to a random address, by CronoS@OlympoS (Ertan Kurt)
- Inside Adelphia - Outside plant overview and info for an Adelphia CATV/Internet installation, by J. P. Arnold
- Subverting Non-Secure Login Forms - PHP code to spoofing login forms (and capture passwords) on Internet Explorer 5.0, 5.5, and 5.0, by I. O. Hook
- Code: gotcha.php
- Setting Your Music Free: iTunes Music Sans DRM - Use Apple's own provided tools to convert AACs to DRM-free WAV/MP3 files, by k0nk
- Vonage Broadband Phone Service - Potential network security vulnerabilities in the Vonage VoIP service (and Cisco ATA-186) and their inability to care, by Kevin T. Blakley
- Sharing Your Life on a Peer-to-Peer Network - Be careful what you put on the Internet when using poorly configured peer-to-peer sharing software, by Kong
- MSN.com Redirect Scan - Scanning the different sites MSN can redirect users to, by StankDawg
- 2600 Marketplace
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: Celebrating 20 years of selling other people's BBS files, free information, and spreading Marxist-Leninists/Communist "useful idiot" propaganda.
- Cover (Cover Info)
- Back Inside Payphones From Brazil
- Brazil #1 If phones like this started to sprout in American streets, there would be massive panic. They look like some kind of alien. Photo by Anonymous
- Brazil #2 And yet, people in São Paulo don't seem to be in the least bit concerned with this new life form. Photo by Anonymous
- Brazil #3 If you're really daring, this is what one of these monsters looks like as you approach. This one was seen in Campinas. Photo by Anonymous
- Brazil #4 And yes, the phone itself, which doesn't seem to really match its spacy surroundings. Photo by Anonymous
- Back Cover Chinese Payphones
- China #1 From the Northwest corner of Tiananmen Square in Beijing (People's Republic). Photo by Tim Fraser
- China #2 And here we have the Southwest corner. Photo by Tim Fraser
- China #3 From Taiwan. This is a standard card reader phone. Photo by Tim Fraser
- China #4 Also in Taiwan, this is an older phone with a coin slot and lots of extra space. Photo by Tim Fraser
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 21!
$2600 Magazine - Volume 21, Number 2 (Summer 2004)
- Mirroring the Future - Editorial
- Scumware, Spyware, Adware, Sneakware - Overview of the latest spyware, like Gator/GAIN, and detailed steps on how to remove it, by shinohara
- ClearChannel's Dirty Little Secret - Behind the scenes at a Clear Channel radio station's "media research" call centers, by Chris Johnson (Bellows Falls, Vermont)
- Impromptu Lock Picks - Make lockpicks out of household items, by L. Gallion
- Magstripe Interfacing - A Lost Art - Very detailed (and updated) article on the properties of magnetic stripe cards and how to build your own reader, by Acidus
- Code: SwipeCard.bas Original (2004) - This is the source code distributed with the article. It is heavily commented and easy to port. This is not a free standing application, but simply a function that returns the contents of a magstripe. If use on Win2K or XP machines, you will need INPOUT32.DLL, which allows direct port access.
- Code: Stripe Snoop - Updated via SourceForge
- Stripe Snoop Media Collection of audio and video files demonstrating Stripe Snoop operation.
- Article in PDF
- INPOUT32.DLL Contains the INPOUT32.DLL needed to directly access I/O ports using INP and OUT on Win XP/2K.
- Interface a TTL Magcard Reader to the PC Games Port by Patrick Gueulle
- Applying the AN10E40 Magnetic Stripe Read Head Amplifier
- Privacy Implications of Magstripes Toorcon 6 slides
- MagSpoof "Wireless" credit card/magstripe spoofer.
- Listening via Linux - Source code for a simple port listener (server), by Solthae
- Code: listener.cc
- Passwords on a :CueCat - Use your :CueCat and a random barcode as a fairly secure password, by SARain
- Declawing Your :CueCat
- Building Cheap ID Cards
- :CueCat Login Shell
- Open-Source :CueCat Software/Drivers
- The Global Date Format - The "correct" way to write dates (Year/Month/Day/Hour/Minute/Second) or ISO 8601, by Richard Cheshire
- The Global Date Format Original
- Behind the Scenes of ITEC and the Milwaukee Bus System - Info on the Wi-Fi network used by Transmit TV video displays in certain city buses, by Eoban (Eoban Binder, Bloomington, Indiana, Facebook, Twitter, GitHub)
- OMNILOCKs and Stupid Politics - Story of an OMNILOCK adventure, or how poor how poor computer security can defeat your fancy electronic locks, by R. Toby Richards
- OSI Security Devices Catalog - 2002
- OSI Security Devices Catalog - 2004
- Stanley OMNILOCK Wireless Access Control Systems
- Stanley OMNILOCK Stand-Alone Access Control Systems
- OMNILOCK 2000 Lock Operating System - v1.20
- OMNILINK Facility Manager Installation Manual
- A Guide to Internet Piracy - Detailed look at the hierarchy and tools used by modern Internet warez couriers, by b-bstf (Andrew Smith)
- Letters - Verbal Constructs
- Reference Material - Twiggs, Scott, XsnipaX (Aurora, CO)
- Gratitude - The Piano Guy, SillyCatOwner, mg48s, Redukt, Closer (Greenville, SC), Nick
- Questions - AB, Zero Cool (Pakistan), kenneth, Charles, ass goblin, Rick, Lynn
- Meetings - iostreamz (Frank, Miami, FL), Tsun
- Tricks - infrared, Brendan Bogosian
- Complaints - Jeff, Vladinator, S, Joshua, Shortfuse, Dr. Smack
- More Info - w1nt3rmut3, Matthew "Blueleaf" Capone, vectorsigma, daste73 (Stephen J. Heeney, Pennsylvania), Unlocked, ScottVR, SJKJRX
- Satellite Radio - M@, Stormbringer
- Call For Info - Miles, mustangdriver504
- More From The Military - Caps Locks
- Positive Stuff - scotwr, Steaming Martyr
- Submissions - mike, Anon Ymous, drlecter
- Warnings - eyenot, mixmaster, Sysopny, crazypete, Ben Franklin, RT
- Stupid Stuff - Fairy Fock, sephail, Maniac_Dan, Ash (Ashmit), The Great Belzoni, Clint, Gigabyte_GRynd3R (Massachusetts)
- Homeland Security - Lee Colleton (Flickr, Seattle, Washington), Prospero
- Redirecting - Steve Duch
- Observations - Mugulord, Pablo, Michael J. Ferris, Micheal, autocode, Bryan, DRAHZ (Arlington, VA), cycoanalytikal (Marty, Lawton, OK, DOB: 07-18-????), Simon Shadow, Greg Gowen (Corrales, New Mexico)
- Consumer Spookware vs. Your Castle - A look at some common, and not-so-commn surveillance hazards (dryer vents and heating ducts) which are encroaching on our privacy today, by dark spectrum (a.k.a. wideband dreamer)
- Consumer Spookware vs. Your Castle Original
- A Lesson on Trust - Story of hacking a school's network, bypassing the Bess Internet filter proxy - and getting in trouble when finally caught, by Sairys
- Fun With Netcat - General overview and some tips for using Netcat, by MobiusRenoire (Weylin Burgett, Mt. Vernon, Ohio)
- The Lantronix SCS1620: An Unpublicized Gold Mine - Command info for the Lantronix SCS1620 secure console servers, by JK
- 2600 Marketplace
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: The Fifth HOPE
- Cover (Cover Info)
- Back Inside Payphones From All Around
- Ethiopia Not very many payphones to be found in this country, but here's one of them in Addis Ababa. Photo by Tom Mele
- Sri Lanka #1 Found in Sigiriya, this booth holds the mounting from a previous tenant. Photo by Tom Mele
- India On Elephanta Island in Mumbai, some careless painters splotched this phone but not enough to dampen its brilliant yellow spirit. Photo by Tom Mele
- Sri Lanka #2 The shape of this phone in the city of Kandy is rather weird to say the least. Photo by Tom Mele
- Back Cover Bulgarian Payphones
- Bulgaria #1 All of these photos were taken in Sofia. Here we see a modern orange coin and card phone. Photo to by karniv0re
- Bulgaria #2 And when a phone only takes cards, they appear to simply cut the bottom half off. Photo to by karniv0re
- Bulgaria #3 Here's a blue card phone which was rigt next to the orange phone above. Such spectacular displays of color are virtually unheard of here in the States. Photo to by karniv0re
- Bulgaria #4 The old style payphone with funky surrounding. Drab, yet intriguing. Photo to by karniv0re
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 21!
$2600 Magazine - Volume 21, Number 3 (Autumn 2004)
- Learning Curve - Editorial
- In the Belly of the Beast - Story of working at AOL and an overview of their internal computer network and operations security, by slummin
- Anti-Forensics: Make Secrets Stay Secret - Overview of what it takes to keep your data safe and secret, including sensative RAM and hard drive contents you may not even know about, by Frater Ignotius
- Digital CDMA Cloning - Overview of the technical steps and software needed to "clone" a Kyocera 2235 CDMA phone's ESN to another phone, by tele
- BitTorrent - The Future of the Internet? - Overview of the BitTorrent peer-to-peer file sharing protocol, by spite
- The Insecurity of PHP Includes - Security holes with PHP include files and the potential to leave database username and passwords "in the clear," by jumbobrian (Brian DeFreitas, San Leandro, California, Facebook)
- Code: db-get.php
- Movies on a Phone - Overview of the steps required to rip a DVD and convert the file to a format which can play on a PDA, Pocket PC, or cell phone, by bill
- Free Encryption Backup - Use Google Mail, or other online email providers, to store encrypted files as an improvised back-up system, by Fernando
- Laptop Security - Scripts you can use to remotely access your laptop if it's ever stolen and a few tips to protect your data, by Fernando
- Code: tracker.php
- Code: beacon.sh
- Code: tracker-enh.php
- Introduction to IPv6 - Overview of the IPv6 protocol, by Gr@ve_Rose
- Hacking Soda Machines - Debug menus on soda machines, by MeGaBiTe1 (Email)
- Hacking Coke Machines by Fire and Kyint
- Hacking + 2600 Magazine + Coke Machines = Crime in San Diego County?
- Hack Soda
- Murphy Oil (Walmart) Fueling Stations - Info on Walmart's/Sam's Club Murphy Oil POS and back office computer systems, by max_9909
- The Big Picture - Linux is Approved! - Update to the "DISA, UNIX Security, and Reality" article and a new UNIX STIG for Linux systems, by Zourick
- How to Hack the Lottery - How do you hack the lottery? I can sum up the answer to this question in two words: don't play, by StankDawg
- Letters - Troublemakers
- Clearing Things Up - nima (Denmark), Mark
- Expanding on Thoughts - Rujo-king, FredTheMole, Cameron, generationxyu (James Longstreet), aguilanegra (Mateo E. Nares), Mannequin, w00tpro, ieMpleH, Jarett M, Jacob, ree, jazzy, Michael J. Ferris, OpenDNA, Copyaj, quel, DarkLight, Shadowfox, Goldman of Chaos (Matthew Goldman), The Gillig Phantom
- Discoveries - Wildkat, Dave (New Jersey)
- Idiocy - PCracer51, No Name, Wildrobo, Steve Shaw (Tennesse), BBV, PsychOcrazY
- Security Holes - Chthon, a.texas, FreshFeesh (Christopher Wright), ericc
- Randomness - Thomas
- Red Flags - Jynx, Brian the Fist (Howard Feldman)
- Interpreting Covers - coolguy, demosthenes, RTFM Noriega, vyxenangel
- Scams - Al3xTr3b3K, Andrew, SystemX
- Making Change - Mike, qw0ntum (Shaddi Hasan)
- Observations - Juan in Aztlan, Judas Iscariot, John, Beaver, Lori, t3st_s3t (Email, BinRev Profile), ReEk0n, Haleon, Miles, KPR, fyrwurxx, mike s., Alex K, Steven Jackson (Joliet, IL)
- General Queries - Tap, hb0b, Beowulf, Pierre, Hiten, Servus Casandro (Christian Berger)
- The LEIGHTRONIX TCD/IP - Info and commands for the LEIGHTRONIX TCD/IP Network Managed Video System, by slick0 (MySpace)
- Decoding Blockbuster - Blockbuster barcode information and tricks, by SDMX
- Warwalking in Times Square - Scanning for wireless access points in New York City's Times Square, by Sam Nitzberg
- Fight Spam with JavaScript - How to hide your email address from Internet email harvesters with some simple JavaScript tricks, by arse
- FC.EXE to the Rescue - Neat article on cracking Windows-program passworded files using file compare utilities, by akaak
- A Simple Solution to Dynamic IP Tracking - How to track your dynamic IP, by Gruggni (DOB: 02-09-1975)
- 2600 Marketplace
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: The Fifth HOPE
- Cover (Cover Info)
- Back Inside Payphones From Everywhere
- Hong Kong Yes, this phone appears to be on its side, but we're told that kind of thing is normal over there. Photo by Robert Vargason
- St. Lucia Looks like a British Telecom phone. Cable & Wireless is the local monopoly. Photo by StuntPope
- Hungary Found in Budapest. This is the kind of phone you should really spend some time with since it seems to be bursting with exuberance. Photo by Dieter K.
- Japan A close-up of a payphone found at Narita Airport which apparently had enough of a problem with its buttons that a little sign had to be installed above them. Photo by Alex
- Back Cover More Chinese Payphones
- China #1 A nice mix of colors on this GTCCL phone found a few blocks west of Tiananmen Square. Photo by Tim Fraser
- China #2 Found in Shanghai, this brilliantly colored phone with its sharp edges looks like a piece of modern art. Just don't try to give it coins. Photo by Tim Fraser
- China #3 This Alcatel phone in Shanghai is run by China Telecom and also only accepts cards. Photo by Tim Fraser
- China #4 Here we finally see a more friendly phone (also in Shanghai) that accepts both cards and coins. Photo by Tim Fraser
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 21!
$2600 Magazine - Volume 21, Number 4 (Winter 2004-2005)
- Stick Around - Editorial
- Hacking CDMA PRLs - Overview of hacking Preferred Roaming Lists in your phone to choose your own roaming service provider, by The Prophet
- Hacking CDMA PRLs The Fifth HOPE (2004)
- Editing the PRL File HowardForums Thread
- An Old Trick for a New Dog: Wi-Fi and MITM - Overview of a possible scenario for performing a Wi-Fi "man-in-the-middle" attacks, by uberpenguin (Matt Britt)
- Vulnerabilities in Subscription Wireless - Potential vulnerabilities in MAC address (Layer-2) Wi-Fi authentication used by many hotels, cruise ships, cafes, etc., by wishbone
- Best Buy's Uber Insecurity - Info on Best Buy computer/network security and unpassworded routers, by skilar
- Hijacking AutoRun Programs for Improved Stealth - Overview of how to hide running processes (like a keylogger) under Windows, by Forgotten247 (Shawn Maschino)
- Catching Credit Card Fraud through Steganography - Customize credit card charges (e.g. all charges end in 17 cents, cents equals dollars + 1, etc.) to verify what you are charged, by Anonymous Author MD5: d03d3293cd954af6bccd53eac5d828fc
- Adware: The Art of Removal - Overview of spyware removing programs, by Patrick Madigan (Doylestown, Pennsylvania)
- Tracking Wireless Neighbors - Some interesting ideas on what to do if you find an unwanted intruder on your wireless networkck, by Sam Nitzberg
- Wireless Neighbors Are Fun! Original
- Backdooring the NAT'ed Network - Somebody read the Netcat manual, by David Dunn
- Electronic Warfare - Overview of the different electronic warfare methods, by HOMA
- Grokking for Answers - How to search the interweb for all your technical needs, by Bryan Elliott
- Letters - Back and Forth
- Questions - Deepen D. Shah (Livingston, NJ), Mike, Shell, Sheri Lowers, Carole, Nick (Florida), Sarma, LeStat, Andrew 0., Tabetha
- Life's Little Experiences - DemonEclipse, Austin D. (Washington), Alex (Massachusetts), Muhammad Adil
- Discoveries - Mr. Fairweather, LabGeek, Mike
- Injustices - Will, Black_Angel (Ligia Tinta), Tcc9mpl (Matt Lametta), Monkey Minister, Citron, waterboy382, Oz1980, Zacchini
- Observations - Narcess, Dr. Ultra Doom Laser, .:LOGIX:., Ryan, CSIN, TOneZ2600, jeff affiliate, Freakker, Hoser, Josh, OveRHaulT (Arvada, CO), 00 (Tampa, FL), Dufu, Anon, Shellcode, William, Brain Waste (New York, New York), Chris C.
- Visibility - niknak (Galway, Ireland), chris (Canada), Ruth (Puerto Rico), bookdrone
- Additional Info - Jon, brarsh, Redukt, BBVGoon2126, Crapinapale
- Responses - WhiteHat (Australia), Osi44 (Buenos Aires, Brazil), N@vi, BuffaloB, oZ, H, Paul, Dagfari, Evan, tutwabee (Trey Hunner, San Diego, CA), Cabal Agent #1, Ellomdian
- Gratitude - Alexis, A little kid
- Info Needed - jjr, Jeff, PurpleSquid (Netherlands)
- Hacking La Gard ComboGard Locks - How to reset the combination, by ax0n (Noah Dunker, Olathe, Kansas, Blogspot, Resume)
- Change an Unknown Electronic Combo Lock Combination Hard reset of a La Gard Model 33E (YouTube)
- AVS Spanner Addendum - A follow up to "A Simple but Effective Spanner in Your AVS" by Irving Washington in the 21:1 issue, by Suicidal
- Code: avs_spanner2.cc
- How to Own Star Search - How to make little kids cry, by StankDawg
- Hacking Ticketmaster - Overview of potential exploits to Ticketmaster's TicketFast printed ticket system, by battery
- Practical Paranoia - Practical tips for what to look for when choosing computer file encryption techniques or software, by MoJo
- Building Cheap ID Cards - Make your own barcode ID cards (or "passwords") with an old :CueCat barcode scanner, by Barfbag (Admin @ Team Blank)
- Hotspot Tunneling - Increase your security with SSH tunneling, and also hide your traffic, when using public Wi-Fi hotspots, by Samjack
- Self-Checkout or ATM? - Overview of potential self-checkout machine vulnerabilities - like obtaining the self-checkout operator key or printing your own UPC codes, by Bob Krinkle (Ryan R. Frederick)
- 2600 Marketplace
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: More drivel
- Cover (Cover Info)
- Back Inside Payphones From All Around
- Seychelles A Tatung made phone. Photo by Dominic
- Uruguay Spotted in Colonia del Sacramento, this is known as the "cowhide phone kiosk." Photo by Tom Mele
- Denmark A standard coin phone found on the streets of Copenhagen. Photo by A.M.
- Mali In what may be one of the most remote locations we've ever published, this public satellite phone resides in Sangha on the Bandiagara Escarpment which is in Dogon country and a seven hour drive from Timbuktu. Photo by David Conn
- Back Cover Payphones of the World
- Switzerland This phone is located in Lucerne. The black terminal next to the phone provides email and directory assistance as well as city maps. Photo by Gabriel Guzman
- Japan One of the common gray phones that accepts coins and cards and even has a spot to plug in a modem. Photo by cyph3rkat
- Lebanon A modern looking phone from Beirut. Photo by Dieter K.
- Azerbaijan Taken in Baku with a cameraphone in a "photography prohibited" zone. Photo by Dieter K.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 21!
$2600 Magazine - Volume 22, Number 1 (Spring 2005)
- Enemy of the People - Editorial
- New York City's MTA Exposed! - Very detailed overview of New York City's Metro Transit Authority (MTA) fare collection system, by Redbird (Joseph Battaglia, Fort Lee, New Jersey, K2BAT)
- mcdecode.pl Display MetroCard Raw and Parsed Data
- Electronic Application Technology - Massive insecurites in the computer employment application forms at JCPenney, by clorox
- Baking Cookies - Overview of browser cookie exploits and PHP code to use captured or packet sniffed cookies, by VileSYN
- Voice Over Internet Protocol - Brief overview of Time Warner's VoIP digital phone service, by Kong
- Hacking Cisco IP Phones - Information on remotely changing settings (via Telnet), initiating calls, and even crashing the Cisco 7940 & 7960 series of IP phones, by Moby Disk (William Garrison, Cockeysville, Maryland)
- Decrypting WS_FTP.INI Passwords - How to decode the password string saved by WS_FTP FTP client software. Simply change the username to anonymous and reopen WS_FTP and it will unmask the password, by H2007
- Hunting Wi-Fi Leeches - Using a packet sniffer to monitor for unauthorized access to your wireless LAN, by RSG
- Unlocking the Power of WAP - How to configure WAP browsers and proxies for Internet access on your cellular phone, by Joshua D. Dick (Marlborough, Massachusetts, Email, Twitter, W1JDD)
- Unlocking the Power of WAP Original
- Unlocking the Power of WAP via Forever Geek
- Backdoor Exits from the U.S. Military - It's intended for use in case the draft is reinstated, or if you really make a major mistake by joining, by Bac
- Blockbuster's Compass - Setting Sail for Port Bureaucracy - Overview of Blockbuster's new employee computer system called "Compass," by Aristotle
- How to Get Out of Google - How to block the Google web spider using meta tags in HTML files or robots.txt, by Chess (Frank Coruzzi, Burnaby, British Colombia)
- How to Get Out of Google Original
- HP Printers: The Hidden Threat - Open ports on HP printers and identification using Nmap and the ability to bypass a firewall by setting up a proxy on an open printer, by DarKry (Wife)
- Disposable Email Vulnerabilities - Potential security concerns with using disposable email services and some ideas for starting your own, by StankDawg
- Disposable Email Vulnerabilities Slides from his Interz0ne 4 presentation.
- Magnetic Stripe Reading - Very good article on homebrew magnetic stripe reader hardware & software, by Redbird
- Code: dab.c
- Code: dmsb.c
- Code: dmsb.py
- Magnetic Stripe Technology and the New York City MetroCard Presented at HOPE Number Six (2006)
- Magnetic Stripes: Part 1
- Magnetic Stripes: Part 2 - Attacking
- Letters - Exchanges
- Research Results - The Neuralogist, Dyslexic_Hippie, The Grand Master of Confusion (Texas), CatWithTheGatt (Email)
- Further Info - Ruth, chuck, Steve, Mouser_inc, haydenth (Thomas Hayden, Ann Arbor, MI), Mogus, Bob Krinkle
- Questions - 11x, David Oliver, Batman 24, Jason, DP, William, Dave, Black_Angel
- Appeals - DB
- Utter Stupidity - Public Display, gmitch
- Appreciations - marco (aka prime anarchist), Robbie Brewer, Rob Hundred
- Security Issue - Brian
- Experiences - aaron (Los Angeles, CA), MikeyB
- Observations - kyle, scotk, SystemDownfall, Doda McCheesle, Impact, Rifkey, p4p3r t1g3r, drlecter, Freezing Cold 2600 Fan (Ontario, Canada), Terry
- Responses - Alan Horkan (Dublin, Ireland), Jaypoc, Alop, BitPimp (Australia), sp1ke, (none given), Daniel Gray (Defiance, OH), The Stealthed One, Chaad, Skillcraft
- Cover Letter - anonymous, gmcsparran3 (Glen McSparran III, DOB: 09-13-1970), Faber, john2kx (DOB: 08-01-1981), jason, mr_bloko (Garrett Davis), Alex, miles bogus, DigitalDesperado, Martian
- Critiques - Rage1605 (Robert Pierucci)
- Problems - Phreakinphun, andehlu, Alop, ryan, Chris, Jon
- Ideas - Tommy (Maine)
- Fighting Back - saynotoid@gmail.com
- Complete Scumware Removal - Overview of several utilities you can run to remove scumware installed on a Windows system, by LoungeTab
- More Fun With Netcat - Continuation to MobiusRenoire's article "Fun With Netcat" by using Netcat to scan for banners, as a quick FTP server, and to run commands on a remote system, by DJ Williams
- Potential Vulnerabilities in Shared Systems - Overview of why you should have the proper file and directory permissions when using shared hosting services in order to not give out any confidential details, by st4r_runner
- Inside the Emergency Alert System - Technical overview of the FCC's new nationwide Emergency Alert System (EAS) and the possibility of remotely setting it off, by Tokachu
- IPv6 Redux - Examples of a configuring a working IPv6 network under Linux, by Gr@ve_Rose
- tspc-4.0-winxp.exe Hexago Tunnel Setup Protocol Client v4.0 (WinXP)
- tspc-2.1.1.tar.gz Hexago Tunnel Setup Protocol Client v2.1.1
- Introduction to IPv6 by Gr@ve_Rose
- 2600 Marketplace
- Puzzle - A complete scan of #5 ESS RC input message manuals. No.. wait.. it's a f*cking crossword puzzle.
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: You just paid $5.50 for a crossword puzzle
- Cover (Cover Info)
- Cover Inside Foreign Payphones
- Alicante, Spain - A standard phone throughout the country. It takes credit cards and coins. In addition this phone has SMS and fax capabilities. Photo by Gabriel Scott Dean
- Alicante, Spain - An older version of the Telefónica phone which has the same features but isn't nearly as pretty. Photo by Gabriel Scott Dean
- Seoul, South Korea - One of many phones operated by KT. This one has a very dominant coin slot as well as the ability to take cards. Photos by Goran Topalovic
- Seoul, South Korea - Another KT phone. The amount of space saved by not taking coins is striking. Photos by Goran Topalovic
- Back Inside Payphones of the World
- Samarkand, Uzbekistan - Coins only but what a magnificent handset. And just look how they've reconfigured the Tone-Tone pad! Photo by Tom Mele
- Mumbai, India - A coin-operated phone at the Taj Mahal Hotel. Photo by Tom Mele
- Anuradhapura, Sri Lanka - We've seen the actual phone in a previous issue but this rural phone booth is a striking sight. Photo by Tom Mele
- Firenze, Italy - A space-age phone that looks as if it's about to burst with enthusiasm. Photo by Lorette Masa
- Back Cover Photo This has to be about the worst idea ever concocted We've heard of driverless light rail systems in the confines of an airport but huge steel freight train locomotives on an easily accessible track? Technology marches on. Found in Roseville, California. Photo by Adrian Lamo
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 22!
"Where's my nine dollars? I want my nine dollars!"
$2600 Magazine - Volume 22, Number 2 (Summer 2005)
- One Step Forward, Two Steps Back - Editorial
- Hacking Google AdWords - Detailed overview of using Google's advertising program and concerns about their profit-driven censorship and hypocrisy, by StankDawg
- DEFCON 13: Hacking Google AdWords (12M MP3) (Slides)
- Hacking Google Map's Satellite Imagery - Analysis of the URL format used to access Google satellite imagery, by Morcheeba (John Maushammer)
- Googlejacking by Example - Technique for Google results hijacking by using HTTP 302 redirects to point Google's search result to a different webpage, by J. V. (Justin Vieira)
- Home Depot's Lousy Security - Huge security hole with Home Depot gift cards using the Codabar system, by glutton (Minneapolis, Minnesota, DOB: 10-12-????)
- SYN-ful Experiment - Perl source code for a program to open a TCP port, useful for testing SYN packet issues on state-like firewalls, by Gr@ve_Rose
- Code: grass.pl Gr@ve_Rose's Atomically Small SYN (GRASS) v0.5
- Gr@ve_Rose's Atomically Small SYN
- The University of Insecurity - Security problems when using easy-to-guess student IDs, by chiLL p3ngu1n
- Creating AIM Mayhem - Programming requirements for making manual AIM connections and sending messages, by windwaker (Drew Blaisdell)
- AIM Eavesdropping Hole - AOL Instant Messenger (AIM) conversations showing up on two (logged-in) clients, by george
- Network Vigilantism Using Port 113 - Testing and securing proper Identd operation on your IRC server, by Tokachu
- Hacking Encrypted HTML - How to use and bypass web pages (HTML) "encrypted" via JavaScript routines used in several software packages, by Edward Stoever (Glendale, California, Resume)
- Passwords from Windows - How to retrieve passwords from Windows' "Protected Storage" with various Windows utilities, by Big Bird
- Data Mining with Perl - Utilizing LWP modules in Perl to automate searching websites or even Google, by Luckycan (Nick, Memphis, Tennessee, luckyallcan)
- A Yahoo! Restriction Defeated - How to save high-resolution pictures from Yahoo! user albums, by BreakDecks (Alexander Vranas, Seattle, Washington, Collierville, Tennessee, LinkedIn, GitHub, Twitter)
- Spying on the Library - How to harass old ladies at the Los Angeles Public Libraries, by solemneyed (Scott Zimmer)
- ParadisePoker.com Blackjack Cracked - Neat trick (and observation) to exploit Internet poker, by JackAceHole
- Letters - Artillery
- In Search Of - Cohen (Eugene, Oregon), Dave, smes (Spam Man Sam, Kelowna B.C., Canada), l0gic (Vancouver, B.C., Canada)
- Questions - Aurature, InfernalStorm, tamsto (Serbia), Gary B. Ticked, Brian, Jason, A Little Boy from China, Orchid
- Feedback - Dave Puype, Crash the Greenhat (Email #1, Email #2, DOB: 02-07-1983), drlecter, Shardin 359, xzanu, Loyal reader (Florida), Brian Detweiler, TraktorGrl, Brian Detweiler, MegaGeek, Hsiao-Ling Liao (Taiwan), Dan, Emoticon, Leprechaun
- Meeting Issues - Chris, James (Louisville, Kentucky), Rashid, Allan, eyeconoclast, ht, Eric Blair, Advent Systems, Don Johnson, James Turner
- Conundrums - Tangled Web, Himi Jendrix (Connecticut)
- Suggestions - windwaker, CSIN, Joe37
- Electronic Voting - Semantic, Bor Onx, Joe Domenici (Austin, TX)
- Contribution - mAcfreAk
- Witnessed - Anarchivist (Karen), MLG
- Letters From Prison - Tony Sparx, Stormbringer
- Further Info - dan0111, Woodzy, FxChiP (Zach, Pittsburgh, PA, MySpace, DOB: 03-17-1987), noir, Nicholas, Shortfuse, ax0n, ssinformer, OWA, D3vUS
- Curiosity - hendon40 (DOB: 07-02-????)
- Corporate Secrets - Please don't use my name, Kaos
- Security Issues - dbax, anonymous, meatwad, Alop, MS3FGX, Bob, SSSSSSSS
- Where Have all the Implants Gone? - Discussing the hype vs. reality of all the bio-implant technology we've heard about in the news and the need for hackers to "challenge the dominant paradigm and break down the bars of technical illiteracy," by Estragon
- Adding Sub-Domain Support to Your Free Dot TK Domain - PHP script to add sub-domains to your free dot.tk hosting service, by Trent Bradley (Blue Collar Camel)
- Code: dottk.php Dot TK Free Sub-Domain Script v1.02
- Getting More from T-Mobile - Overview of customer accounts on T-Mobile plus the possibility of remotely activating a phone via Watson (or social engineering) if you have the proper information, by Psycho
- Remote UNIX Execution via a Cell Phone - How to execute shell scripts remotely via cellular phone email messages by parsing the "Subject" line for commands, by Muskrat
- Code: checkmail.sh
- NCR: Barcodes to Passwords - His article covers the method of creating operating override barcodes knowing operator numbers and passwords and reversing an existing barcode to operator override number and password for NCR E-Series self-checkouts, by Bob Krinkle
- Defeating BitPim Restrictions - Defeat BitPim file copy restrictions, by dk00
- Fun With School ID Numbers - Create your own barcodes in MS Word to alter a school or other similar ID card, by gLoBuS
- Remote Secrets Revealed - Programming Toyota car remote controls (Prestige/TDS/Audiovox APS95BT3/ELVAT5G) or similar without having to pay a tech, by The AntiLuddite
- 2600 Marketplace
- Puzzle
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: The people who try and censor you for having the wrong opinions, and vote for the most corrupt politicians in the world, now apparently care about your freedom.
- Cover (Cover Info)
- Cover Inside Israeli Payphones
- Downtown Jerusalem Someone had to make the decision to put "FIRE" ahead of "AMBULANCE" even though it's out of numerical order. Photo by Shibuya
- Jerusalem's "Old City" Not far from the Western Wall. Seems like all of that yellow space is just begging for some graffiti. Photo by Shibuya
- Jerusalem Near downtown. An orange card-only phone with what appears to be the phone number above. Photo by Shibuya
- Jerusalem In the shopping market district. A gray version with complimentary beverages. Photo by Shibuya
- Back Inside Payphones of the World
- Tunisia This payphone is located at the end of the Tunis Grand Metro in La Marsa. It seems that payphones in Tunis only accept coins. Photo by Richard Springs
- Tunisia This curvy payphone is located in a plaza in La Marsa. This seems to be the newest model of payphones in Tunis. Photo by Richard Springs
- Tunisia The payphone is located in the Tunis Airport. This style seems to be the oldest model still in use. Probably the most blue as well. Photo by Richard Springs
- Syria A payphone from the Axis of Evil! This phone is located next to a tea and shisha shop in Al-Hamidiyeh Souq. It accepts both coins and prepaid cards, although coins are most commonly used. Photo by Richard Springs
- Back Cover Photo We're pleased that Underwriter's Laboratories Inc. recognizes the value of our magazine and that they're willing to tell the world in such a bold an defiant manner. Let's hope it catches on. Found in Camas, Washington. Photo by tOnedeph
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 22!
$2600 Magazine - Volume 22, Number 3 (Autumn 2005)
- Questions - Editorial
- Data Destruction, Covering Your Tracks, and MBSA - Removing web browser history's, cookies, and Microsoft Baseline Security Analyzer, by El Rey
- MBSASetup-x86-EN.msi Microsoft Baseline Security v2.2 (32-bit)
- MBSASetup-x64-EN.msi Microsoft Baseline Security v2.2 (64-bit)
- Stupid WebStat Tricks - Overview of using HTTP statistics packages and some potential security holes in leaving them in an open directory, by StankDawg
- A Randomizing Wi-Fi MAC Address AP Hopper - Perl script to program your Wi-Fi adapter with a random hardware (MAC) address via ifconfig, by Eprom Jones
- Code: hopper.pl
- Fun With the PRO-83 - RadioShack PRO-83 scanner overview and discriminator tap mod, by Dit and Dah
- Radio Scanner Modifications and Information
- PRO-83 Keypad Tricks (Note that "PowerHouse Communications" is a fraud who just took the keypad codes from the BC246T/PRO-83 service manual and expanded on them a bit, then whines and pouts if you make a local copy of 'his' little document...)
- Getting More Out of SSH - Basic overview of using a SSH client for those normally familiar with Telnet, by Apratt (Aaron)
- Using Tor and SSH Tunneling - Overview of installing and using Tor onion routing, plus an idea to combine it with SSH tunneling for increased security, by OSIN
- Reverse Remote Access - Initiate a remote access connection to a Windows machine through a firewall using SSH, rdesktop, and sending the remote commands as an email message, by st4r_runner
- Securing a Drive - Using Sentry 2020 on an external USB hard drive, by Dr. Apocalypse
- Securing a External Drive Original
- JavaScript Injection - Detailed overview of a JavaScript-injecting exploit in an online form, by A5an0
- Climbing the SonicWall - Info on SonicWall and SonicOS, and a potential to login as admin without verification, by Kn1ghtl0rd (David, Email, MySpace)
- Verizon Fios - Fiber to the Home - Overview of ordering Verizon fiber to the home service in New York city, by striker
- Improving Stealth With Autoruns - Rename and replace DLLs to hide programs from Microsoft's Autoruns, by BrothaReWT
- SQL Exploits - Overview of of common SQL security holes and the need to parse user input data to prevent SQL injection attacks., by AOnRkjk=
- Hexing the Registry - Manually hex edit the Windows XP registry to disable Messenger Service (or other servies) without the convenience of the registry editor so as to bypass access restrictions, by divarin (Lisa Webber)
- Letters - Words from You
- Devious Plots - anonymous, Shah Chopzillian (Canada)
- Random Questions - B.H.K. Chanaka (Sri Lanka), CalebLeo1 (Owensboro, Kentucky, MySpace, Email, DOB: 08-09-1986), Steven, Jeff, Henry (U.K.), Andrew, George, Duciniti, Dave, Black_Angel, Jeff
- Security Holes - Anonymous, KJ
- Observations - john, Dr. Apocalypse, 5+3v3 D4v3, theXorcist, -ht, Krazy, Sam, Digital_Cowboy, thedave, Mixfever, e-tipper
- Responses - TackGentry (Benji Gray), kip, forrest hoover, kingconga, El Jefe (Zak), Ovid, Dufu, RustyOldBoat (Greg, Australia), GeekBoy, MetroTek, paper tiger, Andrew, MS, Shadow0049, redjen, Shadow Walker, concerned reader, Lews Therin (Ryan T. Barber), Witchlight, Proud Female Geek, Alan, GulfstreamXo, Metal Cutter, pyroburner69
- Advice - *s00p3r sKri8s*, A Big Corporate Tool
- Help Needed - anina, WiseCracker, Marina
- Dept. of Injustice - Screamer Chaotix, fallen (Jake Tungate, Raytown, MO, Website #2), pukethecat, Luke, David
- Memories - Mudwasp (Sydney, Australia), CWA1108
- Reestablishing Contact - Woodstock, CD, jay (Norton, MA)
- Not Working at a Call Center - Story of working at a call center and tips how to avoid work after taking breaks by timing them just right, by XlogicX
- Securing Your Wireless Network - How to secure your wireless connection, by Seal (Julien McArdle, Canada, GitHub, LinkedIn)
- Securing Your Wireless Network BinRev forum posting
- The Continuing War on Spyware - Additional tips and tricks to locate and remove "spyware" on Windows-based systems, by Inglix the Mad
- Hacking ImageShack - Perl script to automate grabbing random pictures hosted on ImageShack, by System Downfall and Worm
- Code: imageshack.pl
- I Am Not a Hacker - Gayhat, by mirrorshades
- Security Pitfalls for Inexperienced Web Designers - Tips for the beginner webmaster on securing CGI/PHP scripts and email addresses on web pages, by Savage Monkey
- A Peek Inside a Simple ATM Machine - Overview of the internals of a Diebold Cash Source Plus 100 ATM, by FocusHacks (Noah Dunker)
- How to Get Responses Through Deception - Telling lies in emails to get the answer you want, by JFast
- The Ancient Art of Tunneling, Rediscovered - Tunnel TCP connections to a remote host using ICMP echo request and reply packets, commonly known as Ping requests and replies, by Daniel (Daniel Stødle, Tromsø, Norway, Email)
- PingTunnel
- PingTunnel-0.72.tar.gz
- PingTunnel-0.70.tar.gz
- Covert Communications on Linux by Kurt Seifried
- Project Loki: ICMP Tunneling From Phrack, Issue #49
- LOKI2 - The Implementation From Phrack, Issue #51
- Forging an Identity - Some tips on making or obtaining a false ID, by SistemRoot
- 2600 Marketplace
- Puzzle
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: You just paid $5.50 for a crossword puzzle
- Cover (Cover Info)
- Cover Inside Mongolian Payphones
- Phone #1 Yes, this is a payphone. In the streets of Ulaanbaatar, it's the human holding the phone who is referred to as the payphone. Photo by Sasja Barentsen
- Phone #2 The phone itself is a wireless CDMA phone. You give the "payphone" money and you make a call. And yes, most of them wear masks. Photo by Hanneke Vermeulen
- Phone #3 A more normal looking payphone but one that isn't seen in very many places. This one was found in the post office. Photo by Sasja Barentsen
- Phone #4 Here's a variation, designed to appeal to travelers and others who may have second thoughts about walking up to a masked person. Photo by Sasja Barentsen
- Back Inside Payphones of the World
- Belarus #1 A pack of payphones hangs out in the streets of Minsk. Photo by Emmanuel Goldstein
- Belarus #2 A closer look at two of them with subtle differences. Photo by Emmanuel Goldstein
- Russia #1 These were found in the city of Yekaterinburg. Photo by Emmanuel Goldstein
- Russia #2 Very clean and rarely used due to the prevalence of mobile phones. Photo by Emmanuel Goldstein
- Back Cover Photo From the Some People Have Entirely Too Much Time On Their Hands Dept., here is a true "minivan" recreation of our own 2600 van, made from a Tonka toy phone van picked up at an antique shop in Austin, Texas. The tires are a little weird and our rear end looks a lot better, but it's a valiant effort. Photos by Golden Helix
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 22!
$2600 Magazine - Volume 22, Number 4 (Winter 2005-2006)
- Preserving the Magic - Editorial
- Network Administrators: Why We Make Harsh Rules - A seasoned computer administrator discusses why they make harsh rules for systems operating on their networks, by The Piano Guy (Gary Rimar)
- Practical Web Page Steganography - RGB, ISO 8859-1, and 1337sP33K - Implementing a form of steganography using HTML color values, by glutton
- Hacking a JP1 Remote Control - Using the JP1 connection on a programmable remote control to reprogram, tweak, or upgrade the control, by J.M.
- The Redbox DVD Kiosk - Overview of the possibility of hacking the Redbox DVD rental kiosks, by blakmac
- Punking the Watchers - Defeating Windows Messenger snooping with a program to simulate random user input and activity, by Mister Bojangles
- How to Track Any U.K. GSM Mobile Phone (Without the User's Consent) - How to track cellular phones on the U.K. GSM system using public mobile phone tracking websites and a fake SMS, by Jonathan Pamplin
- An Introduction to the Asterisk PBX - Introduction to setting up and using Asterisk under Linux, by zeitgeist (Christoph Eicke, Hamburg, Germany, LinkedIn, GitHub)
- Spoofing Your Charge Number - Proof that is actually possible to change the Charge Number parameter when spoofing calls, by greyarea
- Spoofing Charge Number DIG Magazine, Issue #4
- Audio Version (5.5M MP3)
- Phone System Loopholes Using VoIP - A list of various tricks for VoIP phones like getting free service, assign a U.K phone number, voicemail, etc., by BreakDecks
- Physically Accessing Your Apartment with Skype - Access an apartment building callbox by call forwarding to a voicemail message containing the proper DTMF code via Skype, by dopamine (Aubrey Ellen Shomo, born Justin Michael Shomo, Denver, Colorado, Resume)
- Obfuscation and Encoding in PHP - Overview of the author's Phonic64 script, which will obfuscate PHP code by turning it into "nearly-sensible gibberish," by Bryan Elliott
- Code: Phonic64.php
- APOP Email Protocol - MDS Challenge/Response - Overview of the Authenticated Post Office Protocol and how it uses MD5 hashes for a challenge/response instead of "in the clear" passwords, by Ovid
- Code: ApopCrack.sh
- PGP Key Signing Observations - Discussing how social systems are the weakest link in PGP and the proper etiquette for key signing, by Atom Smasher
- Letters - Writewords
- Questions - Nate, Kn1ghtl0rd, Buzzbros2002 (Shawn), LiRM, Tenchuu
- New Ideas - Impact, Beowulf, ph4n7oMphr34k
- General Feedback - SAM, Merlin, Colin, glutton, phil, jpeg v1rus, Mike, George The Pancake, Luke, Matt Dreyer, alphabot, savaticus, Anthony
- Advice - Javier (Spain), Harry, Phillip, Adria
- Guidelines - Byte Stealer, Jake, Triad, Andy
- Responses - ProtoHippy, SamStone, Jeff
- Responses to Responses - Ryan, oleDB, Josh D., Maniac_Dan
- The Corporate World - Jon, Golden Helix, Anonymous, NetSurf, John YaYa, sting3r (Mike Jones), CEH
- Evil Doings - Toast-sama (J. Donovan), Selena, Ben, BugDave, Sab, Pizentios (Nick Peters, Brandon, Manitoba, DOB: 02-15-1983)
- Homeland Security - necco
- Permissions - Elegin, Uncle Wulf
- Insecurity - Gavin, Nick B.,
- Offenses - Stuart, Tim "Taiwanese" Liim (New Jersey), Ramasee, Chad
- On The Inside - RustyOldBoat, xoxo (New Zealand)
- Discovery - Tat
- Persuasiveness and Social Engineering - How to be a good social engineerin' engineer, by subphreeky (Jon Winder)
- The Real Electronic Brain Implantation Enhancement - This article will offer information on the factual and idealistic concept of electronic implants working for or alongside the biological nervous system and brain of man, by Shawn Frederick
- Observing the Lottery - Story of a person tracking Pick-6 lottery numbers and finding a "bug" in the ping-pong ball method, by CeeJay
- Sears Portrait Insecurities - Potential security holes in Sears' Portrait Studio system, by Stephonovich (Charleston, South Carolina)
- KODAK Secrets and Walmart Fun - Overview of the KODAK Picture Maker G3 used as the self-photo printing machines at Walmart, by Thorn
- The Workings of a KODAK Picture Maker - KODAK Picture Maker kiosk info - the first generations used Sun hardware!, by t_ratv (Michael, DOB: 10-03-1981, UW Stout)
- WiMAX, AT&T Style - General overview of AT&T's implementation of WiMAX, by Pirho
- Cheap Mobile Internet for Your PowerBook - Connecting a phone (Motorola T722i) to your Mac computer for mobile Internet access, by Mystic
- 2600 Marketplace
- Puzzle
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: You just paid $5.50 for a crossword puzzle
- Cover (Cover Info)
- Cover Inside North Korean Payphones!
- North Korea Phone #1 In the lobby of the Yanggakdo Hotel, Pyongyang. This one only takes IC cards and makes local calls on the phone system that isn't connected to the outside world. (North Korea has two phone systems - one is international-capable and the other can only place and receive domestic calls.) Photo by TProphet
- North Korea Phone #2 On the third floor of the Koryo Hotel, Pyongyang. This one has international capability. To use it, you make an appointment for an international phone call (there are only three international circuits so all usage must be scheduled) and place your call then. You pay when you're finished. Photo by TProphet
- Jordan This phone doesn't take coins or cards and can only call toll-free numbers. Photo by Eric
- Katrina It's true that Katrina isn't a country and that this phone isn't foreign. But it's definitely a payphone in a strange environment and a pretty sturdy one at that. We assume the receiver is around somewhere. Photo by Cameron Bunce
- Back Inside Iranian Payphones
- Esfehan Makes you realize just how insignificant the Touch-Tone pad is in the bigger scheme of things. Photo by Qumars Bolourchian
- Shiraz A little worse for wear. But what a unique cord. Photo by Qumars Bolourchian
- Tehran A more modern model that only takes cards. Photo by Qumars Bolourchian
- Tehran This is a true work of art. At first glance it might seem as if someone just shoved a deskphone into a payphone kiosk. But a coinslot has been added into this structure making it a true payphone. It's unclear what that little padlock is protecting. Photo by Qumars Bolourchian
- Back Cover Photo Here's living proof that reading 2600 will lead to trouble. This little cluster of buildings in San Jose very subtly makes the connection. People driving by see the huge 2600 on the building and rush on over thinking that this is our legendary west coast distribution center. But when they arrive they get the message that becoming involved in 2600 will only wind up getting them sentenced as an adult. Photos by Amorel
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 22!
$2600 Magazine - Volume 23, Number 1 (Spring 2006)
- 2600... 2006... 2060 - Editorial
- File Sharing Using TinyURL.com - How to trade small files via URL shortening services (like TinyURL) by converting them into long "hex string" URLs, by mirrorshades
- Code: implant.rb
- Code: extract.rb
- XSS'ing MySpace.com - Good overview of using Cross-Site Scripting (XSS) and JavaScript URL injection on MySpace.com, by FxYxIxE
- United Kingdom: The State of Surveillance - CCTV, ID info, license plate readers - Automatic Number-Plate Recognition (ANPR) in the U.K., by Xen (Xenuhdo)
- Making Rover Fart - Make the Microsoft Search Assistant dog fart by editing the ACS file with your own audio, by Bryan Elliott
- Telecom Informer - Discusses how to add a second phone line (VoIP) to your house for less than $20 and with no monthly fee by modifying an AT&T CallVantage DVG-1120M, by The Prophet
- Hacking the HNAS1 Network Attached Storage Unit - Detailed overview of hacking the firmware on a Hawking Technologies NAS unit for HTTP and root shell access, by Michael Saarna
- Code: fsearch.c
- Hacking 2600.com - Messing around with 2600.com WHOIS information, by Andrew Smith
- Direct Inward System Access and Caller ID Spoofing - Caller ID (CPN) spoofing using Asterisk and an outbound VoIP provider, by iSEPIC
- Hacker Perspective - by The Cheshire Catalyst (Robert Osband, Titusville, Florida, N4SCY, Twitter, Facebook)
- Hacker Perspective Original
- The Intruder A biography of Cheshire Catalyst, Technology Illustrated, Oct./Nov. 1982, by Douglas Colligan
- Hacking PCReservation - Cleartext passwords and open directories with PCReservation software used by many libraries, by Henry Q. Buther
- Hacking the Facebook - Tricks to get people on Facebook to add you to their Friends list or to gather information, by Savage Monkey
- The Price of Convenience: Our Identities - Identity theft info and lack of good prevention laws and just how much of our personal information is already out there, by Squealing Sheep
- Highlighting the Holes - Overview of potential holes in video camera and key card physical security systems, by Modman
- Letters - Sounding Board
- Of Concern - Hiro, Noli
- Requests - Dave L., pseudofed
- An Idea - Miles
- Looking for Advice - Pascal Cretain, phuoc yu, 88LoGan14
- Inquiries - Mike Moore, dt2ra711, Tim, Decay, zack, Peter, Cody, Jsnake, Brian, P3ngu1n, Death, Willie
- Accolades - Joe S., mic911, Part11, Queenie Marblebridge, N. Rajasekharam
- Adventure - DrahconMan
- Stupid Stuff - G Man in the Hole, Alop, M, XSnidalX (James), Death by Microsoft
- Observations - Monty G., Mattington, ch3rry, WiseCracker, Zachary, Undefined32
- Critique - I)ruid, SHR
- Responses - Kn1ghtl0rd, Phuzion, Simon Jester, aztek, Alexei Udal (Audal), Toots, Stormbringer
- Security - The Piano Guy, drlecter, deadman, comfreak, scott
- Further Info - DrBensina (DOB: 11-04-1982), Beowulf, Angry (not mad) Max, The Sarge
- The DRM Plan - How we can fight DRM by supporting the artist, local retailers, and buying the CD, etc. Keep music an issue of control, not permissions, by Don
- The Secrets of Cingular Wireless - Insider information of the customer service procedures at Cingular Wireless, formally AT&T Wireless, which customers can exploit to get free services by The iNSiDER
- Techno-Exegesis - Overview of the new digital satellite and broadcast radio systems and the need for open standards, by Joseph Battaglia
- Not Quite Dead Yet - The current state of payphones, ACTS, and Red Boxing in the U.S., by Black Ratchet (Ben Jackson)
- School Connections - Story of obtaining "free" Internet service in a school dorm after finding a bundle of Ethernet cables in the closet, by graphak
- iPod Sneakiness - Use an iPod and an AutoIt script to steal passwords and install software on someone's computer, by Rob
- A Look at Jabber/XMPP - Discusses Google Talk and potential vulnerabilities in Jabber client/servers using the Extensible Messaging and Presence Protocol (XMPP), by windwaker
- Spyware - The Ever Changing Threat - General overview of spyware/malware, including new developments and understanding the spyware threat and how to defeat it, by FreeRider
- 2600 Marketplace
- Puzzle
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: HOPE Number 6
- Cover (Cover Info)
- Cover Inside More Katrina Phones
- Phone #1 A New Orleans payphone in the Lakeview area that has seen things no payphone should ever have to see. Photo by Chris Chambers
- Phone #2 This area was only a few blocks from where the 17th Street Canal broke. The phone had been submerged and the storage building next to it was overturned. Photo by Chris Chambers
- Phone #3 And this is what it looks like when a cable snaps. Photo by Chris Chambers
- Phone #4 This row of phones is located in St. Bernard Parish in New Orleans and was set up by BellSouth so residents could make calls (supposedly anywhere) for free. Photo by Chris Chambers
- Back Inside Payphones of the World
- India Found in Mumbai Airport. The phone on the left is a typical STD.ISD.PCO payphone with a coin slot. The phone on the right is a credit card payphone. Photo by William Garrison
- Tunisia Another look at the massive blue phones as seen in the arrivals lounge at Tunis Airport. Photo by Joe Deuter
- Austria A few feet of snow has no effect whatsoever here. Photo by slowburn
- Malaysia Found in the streets of Kuala Lumpur. Photo by Gurt
- Back Cover Photo #1 We've been looking for this police car for YEARS! Congratulations to C6S6R8 for finding it somewhere in the streets of New York and for resisting the temptation to steal the license plate and mail it to us. We appreciate that.
- Back Cover Photo #2 Where else but in Ohio could such a sight be seen? Well, probably in quite a few places but this one's a first for us. Spotted by cojak in Columbus.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 23!
$2600 Magazine - Volume 23, Number 2 (Summer 2006)
- Whom Shall We Blame? - Editorial
- More on Hacking Facebook - Discusses a method of reading anything you want from a user's Facebook profile regardless of their privacy settings, by b0rn_slippy
- Code: script.cgi
- Code: script.html
- Getting Screwed by PayPal - Story of problems with PayPal when the person legitimately sold a laptop and the receiver disputed the purchase (with three simple words: "Not As Described," an obvious scam) causing him to lose over $600 and his fight to clear his name, by silic0nesilence (Corey Mishler, Nyack, New York)
- F*ck PayPal The story of how I was screwed by PayPal under the terms of three simple words.. "Not As Described."
- The Battle With PayPal
- Telecom Informer - "NSA has admitted to illegally spying on virtually everyone in the U.S." - this is a flat out lie and isn't even technically possible. Perfect example of the lies and sensationalism Evil Corley and his little followers use to sell more magazines, by The Prophet
- Can They Here Me Now? A security analysis of law enforcement wiretaps.
- Lawful Interception for Internet Protocol (IP) Network
- Lawful Interception and Countermeasures: In the Era of Internet Telephony by Romanidis Evripidis
- SS8 Lawful Intercept Briefing
- Hacking the System - Discusses the author's views on hacking society and includes a detailed example of him harassing his middle school teachers, by Moebius Strip
- Easy Access to T-Mobile and Cingular Accounts - Accessing personal information on T-mobile phones by borrowing their phone, by Battery (Chris Falco, Sycamore, Illinois)
- Ego Surfing - Keeping track of who is searching for you (or others) on the Internet by using Google AdWords, by alokincilo
- Public Access - Tricks on using locked-down public Windows computers to access "unapproved" websites via Windows Media Player , by Insert Name Here
- Breaking Mac OS X Program Security - This article is aimed at displaying the weaknesses in MCX and the XML files that Mac OS X uses to define both the applications that are installed on the system and the applications that a user can run, by Sibios
- GPOs and Group Policy: Just Say No! - Group Policy Objects management information under Microsoft Windows, by WagStaff
- Hacker Perspective - by Bruce Schneier
- Music Today - Holes in the Music Today hosting service by hijacking the chat program, by noir (Nick Arnott)
- Hacking Warner Brothers Records - How to download the top three songs of most artists signed to Warner Brothers Records directly, by c0z
- Letters - Jibber-Jabber
- Experiences - auto456565, Cleara, BigBrother, Acidevil, Mr. K
- Input - vyxenangel, Jeremy, runsetuid.root, Brad Hall
- Suggestions - ThrILL, nitromatt, CerealKiller, Pointilleux
- Another View - Digital_Cowboy
- Responses - windwaker, blakmac, Kaige, devnull, CJ, DZ, Nucow, FelixAlias, The Cheshire Catalyst, George, hypoboxer (Tom Brennan, Murfreesboro, TN, MySpace), Nick
- More Info - Aendrew, sc, meatwad
- Advice Sought - Imegabyte, Symantic, dNight, ansichart, Jeff
- Disturbing Stuff - O-nonymous, NoKaOi, webbles
- Inquiries - Philip, Dany, Zenmaster, Poetics, Shelly L., Uriah C.
- Security Holes - justin, Mark B., Sting3r
- The Retail World - Helack101 (DOB: 08-04-????), Nemo de Monet, Kevin
- Network Administrators: Why We BREAK Harsh Rules - Why strict network rules are not always a good idea, by kaigeX
- Having Fun With Cookies - Discusses uses and abuses of HTTP cookies in real-world e-commerce web applications, by Simon Templer (Email, DOB: 11-30-????)
- Techno-Exegesis - People who think the NSA actually cares about what they do, by Joseph Battaglia
- Roll Your Own StealthSurfer II Privacy Stick - Homebrew USB drive for private web surfing and encryption, by David Ip
- Using Loopback-Encrypted Filesystems on JumpDrives - Using Linux kernel-based loopback filesystems (Loop-AES) to encrypt files on an USB JumpDrive, by OSIN
- An Argument Against MD5 Authentication - Potential security holes with using JavaScript to MD5 hash passwords being sent over the Internet, by David Norman (Orlando, Florida, Email)
- 2600 Marketplace
- Puzzle
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: Bush listening to some terrorist raghead's telephone call is bad, Clinton killing innocent White people at Waco & Ruby Ridge, and Obama/Biden weaponizing the (((DOJ))) to attack their political opponents is good. Who's to blame? Evil Corley.
- Cover (Cover Info)
- Cover Inside European Payphones
- France A stereotypically French payphone booth on the Champs-Élysées in Paris. Photo by 303909
- Ireland This phone was seen in Dublin and is operated by Ireland's second largest telecom company, Smart Telecom, second to the former state-owned Eircom. Photo by Tom Mele
- Romania #1 Found in Sibiu, Transylvania. Until quite recently, Romtelecom had the monopoly in Romania. Photo by Michael Francois
- Romania #2 Also found in Sibiu, Transylvania. A couple of standard (and large) Romanian telephone booths. Photo by Michael Francois
- Back Inside South American Payphones
- Chile #1 In the tiny town of Cucao on Chiloé Island, this picturesque phone booth was found. Photo by Pelayo Besa Vial
- Chile #2 Apart from clashing with its surroundings, this blue phone resembles the old credit card phones that used to be all over the place in the States. Photo by Pelayo Besa Vial
- Brazil #1 Seen in Salvador, a city in the northeast of the country, where people often look as if they're being devoured by payphones. Photos by Marta Strambi
- Brazil #2 These phones are meant to resemble a folk instrument known as a berimbau, which looks remarkably similar - just not as scary. Photos by Marta Strambi
- Back Cover Photo #1 This is an interesting little nail care shop located in a strip mall on the corner of Rt. 59 and New York Ave., Naperville, Illinois. Their explanation of the name is that it's either supposed to mean "unisex" or "uniques." They apparently also run Windows. Spotted by Wordsmith.
- Back Cover Photo #2 Some of you may have heard of the recent Phoenix hostage standoff at the 2600 Building. Our public relations department will stop at nothing to get our name out there. Several of you sent us screen captures from your local TV news. This one was sent by Phnx_fiend. (And everyone got out safely.)
- Staff
- Download Unofficial Scanned PDF! (HiRes) (Damaged)
- Download The Hacker Digest - Volume 23!
$2600 Magazine - Volume 23, Number 3 (Autumn 2006)
- Hope and Fear - Editorial
- Identity Theft: Misinformation Can Be Your Friend - How to tweak your privacy, legal documents, and mailing address to keep your identity from being stolen by people like Kevin Mitnick, by Arcade One
- Where Have The Philes Gone? - Why today's "hackers" appear to be most clueless retards and profiteering sell-outs, by glutton
- Jason Scott's Response
- A Backdoor to Your Oracle Database - Gaining DBA rights to an Oracle database and keeping those rights by creating a backdoor, by Edward Stoever
- A Backdoor to Your Oracle Database Original
- A Backdoor to Your Oracle Database: Part 2 - Obfuscation of the String Literals then Wrapping the Code
- Telecom Informer - Alaskan phone system information, by The Prophet
- Hacking Flickr - How you can change the _t to an _o in Flickr URLs to get the original size image, by undergr0und n1nja
- Fun With the Sears POS - Information on Sears' point of sale terminals and how to crash them, by chr0nicxb0red0m
- Never Pay for Wi-Fi Again! - MAC address tricks to get free wireless Internet access at coffee shops, hotels, by Ray Dios Haque
- Never Pay for Wi-Fi Again! Oddree Magazine, #Issue #1
- Hacking MySpace Using Common Sense - Discusses a method of taking over a MySpace account by guessing the answers to their "lost password" questions, by Dexterous1 (Chino Hills, California)
- Ringtone Download Folliez - How to get free ringtones by viewing the HTML source to grab the direct link to the MP3, by GurtDotCom (Garrett Kendrick)
- Hacker Perspective - by Mark Abene (Phiber Optik, Elmhurst, New York)
- Interview with Mark Abene Security Focus interview with Phiber Optik. Talks about scanning for switch dial-ups in 99xx.
- Insecurity at Pep Boys - Network and terminal information at the Pep Boys car repair places, by Sakuramboo
- Code: port-scan.pl
- Code: port-scan-update.pl
- Mobile Devices - Current and Future Security Threats - Known and potential security holes in today's mobile devices, smartphones, PDAs, etc., by Toby Zimmerer
- Letters - Written Expressions
- On Privacy - Rogaine Rebel, lup0, Robert Barat, eudemonist, Highdesert, Sim, Marxc2001, Capt Blah, Anonymous, C
- Foreign Payphones - D P, Ahmed M Attef
- Interesting Facts - Name Removed, Zeromatic (DOB: ??-??-1985), Neito, dodgydave, Soho, Wave_Rider_1899, Ashley, Kingpin
- Questions - Neo_Chalchas, BrakeDanceJ, John, Lenny Love the Hobo
- Fighting Back - Arcade One, R
- From the Military - doctor zoiby, Sgt. Paccerelli
- Followups - Black_Angel, Mike Smith, X-Man (Eric-Not), digitalFX, quel, AtomicRhino, Mingming5, Jeremy Moskowitz, Darren, eviscerator, Anonymous, Josh, R., Beowulf, SeLTiC, Second_Wave, Life Subscriber, CJ, Anymoose, BillSF
- Blowing the Whistle - dohboy, El Duderino
- Exploration - Phone Trick, Vince N., fortschreiten
- HOPE Stuff - Aaron, Doulos, Doda McCheesle
- Hacking the System: Useful Connections - Discusses hacking the "real world" by cultivation, nurturing, and maintenance of useful social connections, assets, and information, by Moebius Strip
- Techno-Exegesis - Corporate attitude towards security, by Joseph Battaglia
- Ownage by AdSense - Google AdSense information and a loopholes in allowing third-party websites to place ads based on keywords, by Natas (MySpace)
- Ownage by AdSense Original
- Information's Imprisonment - Freedom of speech restrictions (heh!) and digital rights in today's computer world, by Dr. Apocalypse and Matt Fillhart
- Information's Imprisonment Original
- Singapore Library Mischief - Overview of the new RFID-based system in use at Singapore libraries, by Ghostie
- Monitoring Motorola Canopy with Windows XP and MRTG - Monitoring Motorola Canopy wireless network equipment using Windows XP and Multi Router Traffic Grapher, by dNight (Chris O'Hara?, MySpace, DOB: 09-13-????)
- Attacking Third-Party Tracking - Overview of using a Squid proxy and access-control lists to prevent external party monitoring your traffic while on the Internet, by Particle Bored
- 2600 Marketplace
- Puzzle
- 2600 Meetings
- Price: $5.50
- Issue's Cash Cow: HOPE Number 6
- Cover (Cover Info)
- Cover Inside More Iranian Payphones
- Iran #1 One of the more modern public phones operated by the Iranian PTT in the northern part of Tehran. Photo by op amp
- Iran #2 An older public phone but easily one of the coolest designs we've ever seen on any phone old or new. Found in Shiraz. Photo by op amp
- Iran #3 This is what a privately-operated payphone in Tehran looks like up close. For those keeping track, the fee is 250 rials in coins. Photo by op amp
- Iran #4 Also in Tehran, this demonstrates how privately-operated payphones can literally be put anywhere that happens to be convenient. Photo by op amp
- Back Inside Foreign Payphones
- India Yes, this is actually a payphone in Mumbai. You pay the friendly guy at the counter and make a call. This is very low tech but it provides service to the masses. Photo by Michael Kane
- Norway This is a phone booth seen in the old section of Fredrikstad. These are becoming very rare in the country. Photo by A. Harjurju
- Ghana This is a phone from Cape Coast in the southern part of Ghana. It looks like cards are the only way to pay in order to use the phone but it's not so easy to figure out what kind of card to use. Photo by Patrice Beaulieu
- Philippines Found in General Santos. PLDT, incidentally, stands for Philippine Long Distance Telephone Company. Photo by Chris Crowley
- Back Cover Photo #1 This is part of the secret 2600 compound in Lombard, Illinois where our readers gather for indoctrination sessions and to have their minds purified of anti-hacker rhetoric. Uncovered by Stephen who will now have to be purged.
- Back Cover Photo #2 An important part of any indoctrination is to get to the new crop of minds while they are still young. Here we see this evidenced in the form of one of our elementary schools designed with a hacker curriculum in mind in Manchester, Georgia. Taken without our consent by a free-spirited Mouser_inc who will be sent to the bigger building down the road for reeducation.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 23!
$2600 Magazine - Volume 23, Number 4 (Winter 2006-2007)
- Transition - Editorial
- Mobile Devices - Current and Future Security Threats - Known and potential security holes in today's mobile devices, smartphones, PDAs, etc., by Toby Zimmerer)
- FirstClass Hacking - Overview and security holes in the FirstClass classroom software program used by Canadian colleges, by Cristian (Canada)
- Network Administrators: Rules Rationale - Continuing the discussion on why network admins develop the rules they do, by The Piano Guy (Gary Rimar)
- Wi-Fi Hunting: Basic Tools and Techniques - Overview of the hardware and software needed to track down open Wi-Fi networks, by Rick Davis
- Telecom Informer - Overview of the Japanese telephone and cellular networks and how they use similar U.S. standards and technology, by The Prophet
- Circumventing the DoD's SmartFilter - How to defeat firewall filtering rules on a Department of Defense's computer network by using Archive.org, by Comspec - Sigma Nu
- Algorithmic Encryption Without Math - DOS-based file encryption program which repositions the bits based on multiple encoding passes using one or more pseudo-random number generators, by Dale Thorn (Email #2)
- Code: ccrp.h Version 3.1
- Code: ccrp.c Version 3.1
- Code: ccrp.h Version 4.3
- Code: ccrp.c Version 4.3
- Cryptography of a Sort (COAS) (Original)
- Red Boxing Revealed for the New Age - Red Boxing on ACTS is still possible with the proper routing, by Royal (BinRev Profile, Email)
- Red Boxing Revealed for the New Age Original
- How to Get Around Cable/DSL Lockdowns - Getting around outgoing SMTP filters on cable/DSL lines by forwarding different ports, by Pirho
- Hacker Perspective - by Phillip Torrone
- Library Self-Checkout Machine Exploit - A potential vulnerability in "demagnetize" library self-checkout machines by placing two books in the demagnetizer, by Byron Bussey
- Fun With Novell - NetWare and GroupWise overview and security holes and how to use NWSend, by Cronicl3
- (More) Fun With Novell
- PWDUMP Windows NT Password Dump Utility
- NWSend 5.0 NWSend allows sending and receiving messages between Novell NetWare users that have Client32 installed.
- How to Build a Book Safe - How to turn an old hardcover book into a hidden safe by cutting out the insides, by c-dollar
- Network Programming and Distributed Scripting with newLISP - Overview of TCP/IP network and socket programming using newLISP, by ax0n
- Code: port.lsp
- Code: net-eval-test.lsp
- Code: uname.lsp
- Letters - Conversations
- Suggestion - aft
- Reaction - comfreak, Lex, X!U304d (Sean Street, Arlington, TX), Steve, P3ngu1n, An Unapologetic Neo-Luddite
- Oppression - Kevin, Serkit, Darkpr0, Barada, jasonB
- Submission - Sandro, Riccardo, Name Removed
- Question - vyxenangel, Paul Burden, Greg, ldgeitman, E1nstein, Clark Milholland (Carson City, NV), Raj, Squealing Sheep, Oral Seymour, Pac.Man, Samuel Reed
- Prosecution - Kristin, aft
- Revolution - aRevolutionist
- Clarification - jazzlup0, The Joker, Cynagen, G, Eric Smith, D10D3, BugDave
- Proclamation - Candycone
- Information - Anders, soursoles, Hawk82, Doda McCheesle, Crapinaple (Ryan, LiveJournal, DOB: 05-17-????), Jayster
- Observation - Adelain, Zaphod, GBM76010, Brian, knotknaught, Mike the Liar, chemdream, Marxc2001, Zaphod_B, ben
- Provocation - Tapi, gh0stb0t (Alex Love)
- Appreciation - Jason C.
- Techno-Exegesis - Discusses the overuse of new technology and argues that old technology is often times more appropriate (with specific examples of RFID passports, red light cameras, voting machines, slide rules), by Joseph Battaaglia
- GasJack - Hijacking Free Gasoline - Discusses a method of taking advantage of Giant Food store's gas station GasRewards promotion, by cipz (Jim)
- Code: GasJack.rb
- Motorola IMfree as a Wireless iTunes Remote - Hacking the Motorola IMfree wireless instant messenger device into an iTunes remote control, by Kcahon
- Motorola MX240a Device Interface
- Motorola IMFree MX240a Software Version 1.0.694
- Motorola IMfree MX240a PC Client Version 1.0.729
- The Not-So-Great Firewall of China - Technical overview of how China blocks "harmful" websites and some techniques for defeating Internet censorship by converting search strings from regular ASCII to "fullwidth," by Tokachu
- Code: fw.pl
- Hacktivism in the Land Without a Server - Using JavaScript injection to get "free" stuff via the Korean Friendship Association website by changing the price variable, by \/indic8tr
- K7: Free [for the taking] Voicemail - Obtain (or hihack) a voicemail setup via K7 by tweaking their login URL and deleting the k7.net cookie, by noir
- 2600 Marketplace
- Puzzle
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Stop stealing our magazine or we will increase the price again!
- Cover (Cover Info)
- Cover Inside Payphones of the World
- Albania A friendly looking orange phone which only takes cards. Found in Tirana. Photo by Christian Smith
- Turkey This is a payphone booth in a small town by the Aegean Sea near Assos. It takes credit cards and phone cards while a light switch conveniently hangs from the ceiling. Photo by John Shramko
- Denmark An old coin model. Taken outside one of the main train stations in Copenhagen. Photo by rinjava
- Japan Old and big, yet it does it all. Seen in the city of Kin on the island of Okinawa. Photo by Brian McIntosh
- Back Inside More Western Hemisphere Phones
- Dominican Republic #1 Found outside of Dajabón. It's debatable whether that dish and its solar panel, not to mention the huge conduit, are all there for this one little payphone, which seems to have had all its coin mechanisms removed. Photos by Alex
- Dominican Republic #2 "
- Cuba #1 Two very different ETECSA models. This is part of the government owned communications service. The drab phone on the left takes coins, the bright and cheerful looking one on the right takes cards. Found in Varadero. Photos by Alan Prusila
- Cuba #2 "
- Back Cover Photo #1 Here's a "glitch" that happened at the Barnes & Noble in Easton, Pennsylvania and captured by l33tphreak and smoke. Further proof that their scanning system doesn't always work. The cashier was overheard saying to all of the other clerks gathered round, "And it's a hacker magazine too."
- Back Cover Photo #2 Let's hope the cars don't also run on Windows. This little crash was caught by Brandon Freeman on his way to work in Atlanta.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 23!
$2600 Magazine - Volume 24, Number 1 (Spring 2007)
- Challenges - Editorial
- Understanding Web Application Security - General overview of JavaScript, SQL injection, and cross-site scripting vulnerabilities in modern high-performance web applications and protection from attacks, by Acidus
- JavaScript Malware for a Gray Goo Tomorrow!
- SQL Injection Cheat Sheet v1.4 by Ferruh Mavituna
- RFID: Radio Freak-Me-Out Identification - General overview of how RFID technology can effect our privacy in ways we may not have thought possible, by Kn1ghtl0rd
- Exploiting LiveJournal.com with Clickless SWF XSS - Cross-site scripting attack to play an off-site Flash video on LiveJournal.com, by Zaphraud (Jason Kennerly)
- Telecom Informer - Overview of the New Zealand phone systems and a company that apparently tried to scam the USF, by The Prophet
- Avoiding Internet Filtering - Using HTTPS connections, open proxies, and even Google, to bypass Websense school web filtering software, by Major Lump
- Hacking Your Own Front Door - Quick overview of bump keying commons locks and some tips to prevent this from happening, by Cliff
- Dorking the DoorKing - Overview of DoorKing telephone entry systems, by Cadet Crusher
- Security Holes at Time Warner Cable - Story of grabbing a Time Warner cable technician's authorization code via a keylogger to access tech.nyc.rr.com, by Xyzzy
- Hacking My Ambulance - Overview of the computer system used in American Medical Response ambulances, by anonymous
- SSL MITM Attacks on Online Poker Software - Very well written technical article on Man-in-the-Middle (MITM) attacks and an overview and theory in using them against online poker websites, by John Smith (Email, ICQ: 493690985)
- SSL MITM Attacks on Online Poker Software A paper on mistakes made when using SSL for secure connections. (Original)
- CertChecker.java Checks whether a host's SSL cert is valid. Using this is simpler than openssl s_client -connect <host>:<port> -showcerts and is more scriptable. This was used to validate an entire /19's worth of certs in the MITM article.
- Hacker Perspective - by Bill Squire (BillSF)
- Demon Dialer" Package 1991 Hack-Tic "Demon Dialer" phone phreaking tool. Around 1989, BillSF fled the U.S. to the Netherlands where he then designed the infamous "Demon Dialer."
- Ripping MMS Streams - Saving Microsoft Media Streams (MMS) to you computer using SDP Downloader, by EvilBrak
- Backspoofing 101 - Detailed overview of the "backspoofing" technique to retrieve Caller ID CNAM information, by Natas
- My 2600 Article: Backspoofing 101 BinRev forum posting.
- Can I Read Your Email? - Laws on who can legally read your email (besides Kevin Mitnick), by Alex Muentz, Esq. (Alexander Charles Muentz, Philadelphia, Pennsylvania, 215-895-6469)
- Script Kiddies with Briefcases Additional Info
- Letters - Snippets
- Queries - Name Deleted, A. Saboteur, mr.bitworth, about:blank, The Laguna, Victor, d
- Info - Breto, Danielmoore, N0vus0piate, Bac, LocalLuminary (David Crosby), SN
- Stories - brill, Dave, Kevin, JZ
- Danger - dNight, ch3rry
- Weirdness - drlecter
- Advice Sought - Alexander Chase
- Following Up - Marcio, \8/, Dave, Duncan Smith, McViking, Troy
- Gratitude - Barry, Tr4/\/ce
- Thoughts - skoobedy, Computer Bandit, Exo, psion, Rev. Troy (SubGenius)
- The Format - Brian Heagney, Jeff, Inked Fingers, Adric, Iroe8, Jason, Ian
- Sales - sailboogu, CPeanutG, TwitcH, Johnson Hayes, Alfredo Octavio, Digit_01, Prof. Morris Sparks, F
- Stalking the Signals - General introduction to radio scanning and using near-field receiver functions like Signal Stalker in modern scanners, by Tom from New England
- GoDaddy.com Insecurity - Potential security problems with GoDaddy's account information, by SLEZ
- Hubots: New Ways of Attacking Old Systems - Human-based denial-of-service vulnerabilities with the possibility of distributed brute-forcing of ATM card PINs, by S. Pidgorny (Svyatoslav "Slav" Pidgorny)
- Network Ninjitsu: Bypassing Firewalls and Web Filters - Detailed methods of bypassing firewalls and web filtering using SSH tunneling, by James Penguin (Austin. Texas, Email, Website #2, Website #3, Website #4, Deviant Art, GitHub)
- Hacking a Major Technical School's Website - Getting into an online college library (ITT Technical Institute?) by guessing student ID numbers, by valnour (Bobby Burden, Tennessee)
- Covert Communications Channels - Using JavaScript and HTML methods for covert communication over the Internet, by OSIN
- Code: app.java
- Code: bottom.html
- How to Cripple the FBI - Why you should use strong encryption and passwords for your hard drive contents and Internet communication, by comfreak
- 2600 Marketplace
- Puzzle Excerpt from Led Zeppelin's Communication Breakdown (MP3 - Kinda garbled)
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: People Evil Corley supports falsely arrested at protests in Philadelphia & New York: Bad. People Evil Corley doesn't support falsely arrested at protests at the U.S. Capitol: Good.
- Cover (Cover Info)
- Cover Inside Payphones of the World
- Palestine Located in the West Bank city of Ramallah. Photo by Sharif
- China Found in the lobby of a hotel in Xiahe in the Gansu province. Photo by Siegfried Loeffler
- South Korea #1 An older phone found in Seoul that takes coins and cards. Photo by Jean
- South Korea #2 Also in Seoul, this model only take cards. Photo by Jean
- Back Inside Strange Foreign Payphones
- Thailand Separated at birth? This phone was spotted in Chiang Mai, Thailand Photo by Mediatech
- Kosovo And its relative was found all the way over in Fushë Kosova, Kosovo. Photo by Mark Johnson
- London #1 SNAFU? One of those Internet terminals that can be found throughout London, England. And, as with many devices in London, this one had a bit of a problem. Photo by Siegfried Loeffler
- London #2 "
- Back Cover Photo #1 Streets are the theme for the back cover of the Spring issue. And here we see an aptly named intersection in Bellevue, Washington spotted by Pat. Naturally, we are being given the right of way. Please don't ask why 2600 crossed the road.
- Back Cover Photo #2 It's very fortunate for us that the word "hacking" is also a somewhat popular surname. So that means there are all sorts of great photo opportunities out there. This one was taken at Blackpool Pleasure Beach in England. Yeah, that's a strange name too, but the U.K. is full of them. The street was named after one Victor Hacking, a longtime employee of the beach and its associated pleasure(s). Spotted by d2812.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 24!
$2600 Magazine - Volume 24, Number 2 (Summer 2007)
- Remaining Relevant - Editorial
- Discovering Vulns - A good introduction article on the different types of software vulnerabilities and the process by which they are, by Cliff
- Web Application Stress Tool v1.0 The Microsoft web stress tool is designed to realistically simulate multiple browsers requesting pages from a web site.
- The Shifty Person's Guide to 0wning Tire Kingdom - Week long adventure story about Tire Kingdom and exploring their network of IBM AS/400s, by The Thermionic Overlord
- Enhancing Nortel IP Phones with Open-Source Software - Use DD-WRT with OpenVPN to use an IP phone at home as an extension of his office phone, by Ariel Saia
- Telecom Informer - SMS Short Code numbers and the scams that typically revolve around them, and a nice look at long distance "slamming," by The Prophet
- Deobfuscation - Good article on reversing the obfuscation that SourceCop applies to PHP code, by Kousu (Nick Guenther)
- Getting 2600 the Safe Way - Overly paranoid person sets up an ASP script to tell him when this crap comes out, by daColombian
- Code: getting-2600.asp
- Fun at the Airport - Security problems with TSA checkpoints and the low-I.Q., affirmative-action types running them, by Evil Wrangler
- Hacking Xfire - Tweaking the XFire games xfire_games.ini file, including loading programs to create false game results, by Akurei
- Hacker Perspective - by Mitch Altman
- ValuePoint - Serious flaws in the ValuePoint wireless network service offered by many hotels, by Sidge.2 & Bimmerfan
- Internet Archaeology - How to gather historical/hidden information from websites using Archive.org, by ilikenwf (Matt Parnell)
- Internet Archaeology Original
- Hacking Answers by Gateway - How to get help from the Answers from Gateway service with running undocumented commercial software, by Franz Kafka
- Letters - Opinions
- Suggestions - L0j1k, MS3FGX
- Complaints - Guitarmaniax (Peter Huggins, MySpace), Minstrel, Jacqueline, mikes, A Fan, Ignacio, SiKing
- Response to Articles - aa2600 (Dave), dthron, JB, Ugg, Wgoodf (Dale Goodfellow, Edinburgh, U.K.), Wesley, Short Blonde, NYC Locksmith, Pat
- Response to Letters - S. Pidgorny, Hennamono (John English, Littlehampton, West Sussex, U.K.), OSIN
- Injustice - Xiver0m, Barron, Kristian
- Observations - FeTuS in MN, Randall, ThrILL (Orlando, FL), DJ Walker, justin, Ian 2.0
- Taking Action - Anon
- Security Issuse - lucidRJT
- Store Issues - Matthew, Raven, Ben
- Questions - Macavity, M, Davis
- VoIP Cellphones: The Call of the Future - Different technologies being used to implement Voice over IP calling for cellphones, by Toni-Sama
- Pandora Hack - Get Free MP3s - How to download MP3s that are streamed to you by the Pandora Internet radio station, by SickCodeMonkey (David Huggins)
- Adventures in Behavioral Linguistics - People who are wishing really hard to have "Jedi mind tricks" in real life (Neuro-Linguistic Programming), by Marxc2001 (Mark Carney)
- Transmissions - Good advice for improving your operational Internet/computer security in situations where you should be more paranoid, by Dragorn
- An ISP Story - Story about tech support trying to help someone who is having their account compromised by unspecified MSN exploits, by Witchlight
- Hacking Whipple Hill with XSS - Cross-site scripting vulnerability in some school's schedule management software by Whipple Hill, by Azohko
- Code: logger.php
- Haunting the MS Mansion - Windows XP system recovery, and other useful tricks, while using the Norton GHOST 9 bootable recovery CD, by Passdown
- Reading Ebooks on an iPod - Different options for converting long text files into multiple linked "Notes" for viewing on an iPod, by DBTC (Andy Kaiser, Grand Rapids, Michigan)
- Reading Ebooks on an iPod Original
- Java Reverse Engineering - A very good article on using a Java decompiler to make a key generator for Zend Studio, by quel
- Zend Studio 3.0.0 - Linux Client - No JRE
- Zend Studio 3.0.0 - Windows Client - No JRE
- GBPPR Reverse Engineering Lab Software cracking tools, links, & notes.
- Code: createkeys.php
- 2600 Marketplace
- Puzzle (Solution) Data Matrix of HD-DVD/Blu-Ray AACS processing key: 0x09f911029d74e35bd84156c5635688c0
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: We are all too stupid to write good articles. Send us more crap!
- Cover (Cover Info)
- Cover Inside North Korean Payphones
- North Korea #1 At long last, we have pictures of actual payphones in the streets of Pyongyang. These are the kind that real North Koreans use, not the ones found in tourist hotels. All of these pictures are of the same payphone bank, which is possibly the only one of its kind in the country. Here we see kids crowding excitedly around the phones, just as they do at payphones all over the world. The allure of communications seems to be universal. Photos by Emmanuel Goldstein
- North Korea #2 "
- North Korea #3 This is the same bank of phones as seen from the opposite end, taken while passing in a bus. There never seems to be a time when these payphones aren't extraordinarily busy. They're located right outside Pyongyang Department Store No. 1 and adjacent to a metro station. Photos by Emmanuel Goldstein
- North Korea #4 "
- Back Inside More Foreign Payphones
- Australia We don't even want to know. Seen in Castle Hill, New South Wales. Photo by P C
- New Zealand This manages to top the Australian entry in the silliness category. This thing actually exists on Stewart Island where the population is 300. We have no idea how payment is arranged but the canopy and phone book certainly add to the experience. Photo by Ben Auchter
- Russia Found in Magadan on the Staritsky Peninsula in Siberia. Payment is through tokens purchased from the local Post, Telephone, and Telegraph (PTT) office. Photo by Intellstat
- Azerbaijan Seen in Baku on Neftilar Prospekti which we're told translates to "Oil Boulevard." On the other side of this phone is a totally different looking payphone that we can't print because we're out of space. Photo by Dominique
- Back Cover Photo #1 Now this looks like it just has to be one of the coolest places in the world to hang out. That is, assuming they have issues of 2600 to peruse. Thanks to Bernie C. for alerting us to the existence of this cafe, located in Honolulu, Hawai'i, right down the road from the main campus of the University of Hawai'i, Mānoa.
- Back Cover Photo #2 "You should never deny your kids education" is how contributor Ethem sums this one up. This 12-month-old kid, incidentally, picked up a copy of 2600 on his own. Toddlers and hacker 'zines both spend a lot of time in bathrooms, after all.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 24!
$2600 Magazine - Volume 24, Number 3 (Autumn 2007)
- Politics - Editorial
- VoIP Security: Shit or Get Off the POTS - Summary of the risks of implementing VoIP in an organization and a good overview of some tools you can use to test your VoIP implementation, by Reid
- Getting More Out of Your College Linux System - Overview of securing your sessions and bypassing any imposed "limits" when using a school-provided Linux system, including install the lightweight Fluxbox window manager, by Silent Strider
- Social Engineering and Pretexts - Store detective and private investigator gives anecdotal advice and stories about social engineering, by Poacher (England)
- Telecom Informer - History and purposes of PBX systems and their significance to phone phreaks and hackers, by The Prophet
- Language Nonspecific: Back to Fundamentals - How once you learn one programming language, you can easily learn others, and why it doesn't matter what language you use as long as you understand what its logically doing, by Kn1ghtl0rd
- Front Door Hacking: Redux - Additional information and tips to the "Hacking Your Own Front Door", by Darkarchives
- A Penny For Your Laptop - Very simple vulnerability in the Kensington MicroSaver notebook lock - use a penny to add tension and spinning the dials until they stick, by Atom Smasher
- Kensington MicroSaver Lock Defeated with a Penny Press coverage on ZDNet. (Mirror)
- Kensington MicroSaver Lock, Paper Key (YouTube)
- The RIAA's War on Terror - Discussion comparing anti-terrorist tactics to those the RIAA is using against music file sharers, by Glider
- Free Files from Flash - Tips for downloading Flash files directly by using a packet sniffer to get their exact URL, by DieselDragon (Colin Blanchard, Farnborough, England, Blog, Twitter, YouTube Channel)
- Free Files from Flash Original
- Target: For Credit Card Fraud - Former employee of Target discloses a whole host of problems with the stores' computer networks and details a method of obtaining register transaction logs, including credit card information, by Anonymous
- Code: grabcc.bat
- How to Get More from Your SugarMama - How to cheat Virgin Mobile's SugarMama ad-supported free minutes program, as well as how to send free text messages through one of Virgin's web interfaces, by gLoBuS
- Owning UTStarcom F1000 - How to unlock the UTStarcom F1000 VoIP phone, by ZiLg0 (Jeremy Brosnahan, Craftsbury Common, Vermont)
- UTStarcom F1000 Release Package V4.50st
- UTStarcom F1000G Release Package V2.70st
- UTStarcom F1000G User Manual
- Hacker Perspective - You (Results from the subscriber survey)
- Hacking 2600 Magazine Authors - A store security agent attempts to track down a 2600 Magazine author via details in their article, by Agent Smith (Possible Email)
- Designing a Hacker Challenge - Create a hacker challenge designed to help you and your crew find out who is the best, and who dies like the rest, by glutton
- Hacking an Election - Former employee of Elections Manitoba, gives a good description of how provincial elections work in Canada, by Dagfari (Canada, South Korea, Dave Alexander, Email)
- How to Cheat Goog411 - How to make free phone calls using Google's 411 service (1-800-GOOG411) by setting up "fake" businesses, by PhreakerD7 (Website #2, Twitter)
- How to Cheat Goog411 Original
- Letters - YAMMERING
- Privacy - A Broken Husband, Muddy
- Safeguards - inf3kT1D, AnOldFool
- Submissions - Michael, Tyler, ithilgore (Email), Josh, WC
- Meetings - Vince, MasterChen, John
- Critique - Jason Scott, Anonymous, Cliff, P3ngu1n, micah, Crazypete, D1vr0c, Nelson, Anonymous
- Retail - Michael, Justin, John, Trollaxor, Michael
- Encryption - Atom Smasher, SodaPhish
- Questions - dluvaisha, Elana, Haroon the Hacker (Grant Hayes), Zoran, Phail_Saph (Email, BinRev Profile), Omid
- Injustice - The Invisible Man, carbide
- Gratitude - Jane Doe
- Observations - Rev. Troy, Arcade One, Jason, Mattew, Cyphertrex, acidie, ViSiOn
- Hacking the Buffalo AirStation Wireless Router - Default login and password (root!) on Buffalo AirStation wireless routers, by Donoli
- The Thrill of Custom Caller ID Capabilities - Discusses using Caller ID for call routing to lower costs, simplify voice mail access and maintain a single-number presence, by krt
- Securing Your Traffic - How to tunnel all of your traffic through SSH, includes options for Mac & PC, by b1tl0ck
- Transmissions - Ethical implications of using "open/free" wireless access points, and then goes into how different countries view the legal aspects of it, by Dragorn
- Hacking the Nintendo Wi-Fi USB Connector - How to modify drivers and software for this device to unlock its use as a general purpose USB Wi-Fi device and access point, by MS3FGX (Tom Nardi, Trenton, New Jersey)
- Hacking the Nintendo Wi-Fi USB Connector Original
- Nintendo Wii Networking Guide Version 1.2 by Tom "TJ" Nardi
- Fun With International Internet Cafes - Disable the timer on an Internet cafe computer in Bangkok by removing it from the startup entries and rebooting, by route (Australia)
- The Trouble with Library Records - History behind INNOPAC, a popular library management system, by Barrett D. Brown
- The Life and Death of an American Help Desk Agent - Good summary of the different tiers of support and their culture - and how evil IBM Charlotte is, by Geospart (George Doscher, Jacksonville Beach, Florida, Twitter)
- 2600 Marketplace
- Puzzle A PDF417 barcode containing a quote from Winston Churchill that was broadcast on October 1, 1939 and said, "It is a riddle, wrapped in a mystery, inside an enigma." (He was talking about the USSR.)
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Evil Corley voted for, campaigned for, and openly supported the most corrupt (((politicians))) in human history - but it's all YOUR fault nothing works!
- Cover (Cover Info)
- Cover Inside North Korean Payphones!
- North Korea #1 As luck would have it, we have a second batch of North Korean payphones, one issue after we printed our very first pictures of actual payphones in the streets of Pyongyang. These are from a different bank of payphones in the same city. Photos by kalafior
- North Korea #2 "
- North Korea #3 For the first time, some really up close pictures of these phones. Photos by kalafior
- North Korea #4 "
- Back Inside More Foreign Payphones
- Tajikistan #1 Found in Dushanbe, this newer phone takes cards. Photo by Astcell
- Tajikistan #2 Also in Dushanbe, older phones like this one are from the Soviet-era. In many locations, people take the old phones, tap in their own personal phone, and open their own payphone business. Photo by Astcell
- Bangladesh #1 A non-operational model found at the Chittagong Railway Station in Chittagong. Photo by Inferno
- Bangladesh #2 Also non-operational in the same place, but at least this one looks like it's been through a lot more. Photo by Inferno
- Back Cover Photo #1 It took darkism nine months of riding the 'L' in Chicago before spotting car #2600 on the Purple Line at Howard Station. Naturally, #2599 was spotted dozens of times before this memorable moment finally occurred.
- Back Cover Photo #2 Yet another cool hangout for us all to congregate in. Joel Weisman says the Hexagon Bar in Minneapolis is a hole-in-the-wall with a magical address that actually isn't all that bad. We can certainly identify with that.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 24!
$2600 Magazine - Volume 24, Number 4 (Winter 2007-2008)
- The More Things Change... - Editorial
- Power Trip - In-depth article on using web cameras, motion capture software, and remote UPS controls to monitor unauthorized access to your secure computer setup, by OSIN
- Code: apm-monitor.pl
- Building Your Own Networks - Building secure "off-Internet" wired or wireless networks modeled after FidoNet using OpenVPN, by Casandro (Christian Berger, Germany)
- Code: getkeys.cgi
- Code: search_ip.sh
- Code: write_configuration_files.sh
- Pirates of the Internet - Overview on some of the terms used, and who are the people behind, the warez you download, by black_death (Canada, Email #1, Email #2, DOB: 01-26-1989)
- Telecom Informer - Overview of the Enhanced 911 system and "SWATting," by The Prophet
- Darknets - A look at creating private, secure file sharing networks to avoid government censorship, by WillPC (William Raffield, BinRev Profile #1, BinRev Profile #2)
- Scanning the Skies - Overview of satellite receiving technology and receiving free analog video channels, by GutBomb (Jason Merrill)
- Pansat 2500A Firmare Update Procedure
- Pansat 2500A Receiver-to-Receiver Transfer
- Pansat 2500A Firmware Update
- Essential Security Tools - Overview of common open-source network security tools, like Netcat, Nmap, THC-Amap, hping, GRASS, and ike-scan, by Gr@ve_Rose
- Decoding Experts-Exchange.com - Access "censored" information on certain websites by viewing the HTML source and ROT-13'ing the access key or answers, by Phatbot (Derek Kurth)
- An Introduction to Beige Boxing - Discusses construction of a phreaker's "Beige Box" - which allows you to connect a phone, laptop, or PalmPilot to a POTS phone line, by Erik Paulsen
- Hacking the SanDisk U3 - Overview of the U3 Smart Drive partition layout and some example ISO files to create your own applications, by Mercereau (Jonathan Mercereau, dohboy)
- Code: getInfo.vbs
- Hacking the SanDisk U3 Original
- Reinstall or Restore U3 LaunchPad Software into USB Flash Smart Drive
- How to Customize U3 USB Smart Drive to Become Ultimate Hack Tool
- Hacking U3 Smart USB Drives
- launchpadremoval.exe This is the same EXE as U3Uninstall.exe (3.5M EXE)
- U3 Deployment Kit Version 1.0 (March 2006, Rev. 1.0)
- U3 Platform 1.0 SDK September 2005
- Exploring AT&T's Wireless Account Security - Discusses customer information that AT&T customer service representatives have, and how that information might be social-engineered out of them, by satevia (Michael, Fullerton, California)
- Hacker Perspective - by Rop Gonggrijp
- Electronic Voting in the Netherlands: From Early Adoption to Early Abolishment
- Case Study Report on Electronic Voting in the Netherlands
- Nedap/Groenendaal ES3B Voting Computer: A Security Analysis
- (More) Fun With Novell - Additional Novel hacking tips, including how to hide PWDUMP from Norton AntiVirus and an intro to PsTools, by Cronicl3
- PayPal Hurts - Article about how PayPal ✡ transaction reversals can cost recipients a lot of shekels, by Estragon
- Facebook Applications Revealed - Security implications of third-party apps using the new Facebook application API, by stderr (Kenny, Florida, Email #2, BinRev Profile, Website #1, Website #2, MySpace, GitHub, Twitter)
- Letters - DECLARATIONS
- Mischief - PhreakerD7@gmail.com, mthed
- Binding Woes - XeNoS, Andy
- Discoveries - shaunxcore (Manchester, U.K.), Chris, Lex, a a, Noah
- Theories - Jesse, Ken, kiX
- Responses - Squeeling Sheep, 3v.mike (Mike Lauber), i<3puppies, theforensicsguy, ThoughtPhreaker (Cody, DOB: 02-13-1991, Portland, Oregon), c0ld_phuz10n (Las Cruses, New Mexico), Logopolis, Zaphraud, Dvnt, F33dy00
- Ideas - FobG, thotpoizn (Jason), Matthew
- Problems - Beachedwhale, The Philosopher, Togeta, Ramie, hypo, Office of Special Investigations
- Questions - M, Doda, David, John, RB in SF, CMG, suN8Hclf, BiomechanoidXIII (Brandon, DOB: 05-13-1987), Anthony, Christine, W1f3y 0f R34d3r, FK
- Surprised? - SJKJRX, MasterChen, PriesT, Unknown One, stranger0nfire
- Opportunity - John(SAN)
- Observations - PlumBob, hypoboxer, Mike, DataBoy, speedk0re, Brian the Fist, drlecter, Jeff, Boomer/NTT, Matt
- Hacking Windows Media DRM - Using Windows Media Player 9 in debug mode and DRM2WMV to remove DRM protection from WMV video file, by Alt229 (Erin Scott, Arcadia/Sierra Madre, California)
- DRM Tools
- How to Remove DRM Protection for Video Files
- Satmonk's DRM Tutorial Direct stream copy with decrypting for online license acquisition WMV files.
- DRM10 Cracked? via Doom9's forums, the in-place to be for everyone interested in DVD conversion.
- DRM Removal - A Detailed Guide
- How to Remove DRM (Digital Rights Management) from WMV Videos
- Windows Media Player v10.00.00.3646 Original CAB file
- Windows Media Player v10.00.00.3650 Original CAB file
- Windows Media Encoder 9 Series
- The Noo World - A look at nootropic drugs, which are natural, semisynthetic, or synthetic compounds which purportedly improve cognitive functions, such as executive functions, attention or memory, by Agent5
- Nootropic Drugs "Drugs that make you smart."
- Forensics Fear - Information on Guidance Software's Encase Enterprise Edition and how to find and bypass it, by Anonymous Chi-Town Hacker
- Transmissions - Various issues with privacy related to browsing, searching, and using various web sites, by Dragorn
- Cracked Security at the Clarion Hotel - Story on keystroke loggers found on the computers at a Clarion hotel and general poor security of their network, by Gauss VanSant
- Building Your Own Safe, Secure SMTP Proxy - Python script to bypass SMTP restrictions on your network, by sail0r (Email #2)
- Code: SMTPLocalService.py
- Code: SMTPRemoteService.py
- Zero-Knowledge Intrusion - Zero-knowledge intrusion is based on two principles: perform only passive reconnaissance, and do not ever generate traffic that is not generated by legitimate clients on the network, by S. Pidgorny (Svyatoslav "Slav" Pidgorny)
- Getting Around 802.1x Port-based Network Access Control Through Physical Insecurity
- Securing Wireless LANs with PEAP and Passwords v1.6
- Securing Wireless LANs with Certificate Services v1.6
- Booting Many Compressed Environments on a Laptop - Run multiple operating systems on a limited-space hard drive by compressing them, by Scotty Fitzgerald (Email #2)
- Avoid Web Filtering with SSH Tunneling: Encrypted Circumvention - Discusses a method of circumventing web filtering systems by disguising your SSH tunnel as a HTTPS connection, by Tessian (Bensalem, Pennsylvania)
- How to Bypass Most Firewall Restrictions and Access the Internet Privately (a.k.a. The Surf at Work Page) Versioe 2.1
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: More sensationalism to help increase their net profits.
- Cover (Cover Info)
- Cover Inside Payphones of the America
- United States One of the more creative payphones of the States, found (where else?) at the entrance to the Kennedy Space Center on Merritt Island in Florida. Photo by icurnet
- Costa Rica Seen at a local shopping mall. Note how large the phone number is on this particular model. It's almost as if they want people to call payphones, unlike in the States where incoming service is often turned off. Photo by RadioRover
- Belize Found in a restaurant/bar in San Ignacio. What it lacks in size it makes up for in overall design. Photo by Phred
- Colombia Seen in Chia, this bank of phones has what has to be the most dramatic awning ever made for payphones. Photo by Random
- Back Inside Overseas Payphones
- Iraq #1 Seen in a bombed out Iraqi hospital east of Baghdad. Note the "Call Me" request on the chassis. Photo by William Johnson
- Iraq #2 Seen outside a hospital in Sulaimanyah. The white piece of paper gives advice on preventive measures to take so as not to contract cholera. Photo by Conan
- Morocco Found in Marrakesh, this is what we imagine payphones must look like on other planets. Photo by birdy
- Cayman Islands This is about as many payphones as you'll ever see in one place. These were found at the port of call for cruise ships in George Town, no doubt placed there before the advent of cell phones. Photo by StankDawg
- Back Cover Photo #1 This photo of 2600 Barracks Road in Charlottesville, Virginia comes to us from Beth Skrobanski. It's home to The Colonnades, a retirement community that we're currently negotiating with to get discounted rates for members of the hacker community when the time comes. Even the font looks familiar.
- Back Cover Photo #2 In answer to the question we get asked more than any other as to just where Walmart Store #2600 is, the answer is of course Chesterfield, Missouri. In fact, it's on the wall of this very store, discovered by Doyle Glaze, that the Children's Miracle Network donated a whole bunch of balloons to commemorate this historic fact.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 24!
$2600 Magazine - Volume 25, Number 1 (Spring 2008)
- The Whole World's Watching - Editorial
- Vhreaking with VoXaLot - Defines common VoIP terms and describes how to set up a nearly free telephone system to make calls around the globe using the VoXaLot service, by Jose Romeo Vela
- Dirt-Cheap Phone Calls the VoIP Way - Describes the author's VoIP setup and what he's learned from setting it up. He was unable to discover a truly free setup, by SiliconeClone (Swartz Creek, Michigan, MySpace)
- Skype/VoIP Phone Adapter by Vitali Virulaine
- Gaming AT&T Mobility - Discusses a number of "social engineering" methods and strategies for obtaining freebies/extras on your mobile phone bill from AT&T customer service, by The Thomps
- Telecom Informer - Discusses the telephone systems in jails and prison and how its a profit center for prisons and a ripoff for the inmates. Also details a bit about the systems used and some of the rules imposed, by The Prophet
- Password Memorization Mnemonic - Discusses a method of generating passwords for multiple websites that are both easy to remember and fairly secure, by Agent Zer0 (Philadelphia, Pennsylvania, MySpace)
- Hacking Two-Dimensional Barcodes - Discusses 2D or matrix barcodes, details what they are, how they work and the types, by glutton
- Dissecting the EPC: RFID for the Commercial Sector - A good technical dissection the Electronic Product Code and Gen2 standards for RFID tags, by Kn1ghtl0rd
- Eavesdropping with LD_PRELOAD - Discusses a method of overloading shared libraries in user space to hijack function calls, by phundie
- Code: eve.c
- April Fools' Day - The Hacker Way - Discusses a pretty good April Fools' Day joke done by the author on his company's CEO, by xinit
- Remember CompUSA - Details a method of obtaining CompUSA sales information (including credit card number, expiration date, etc) from an IMS terminal within the store, by silic0nsilence
- Downloading MP3s From AllOfMP3 for Free - Discusses a method of getting free MP3's by using the sign-up credit of the allofmp3.com site, by He-Who-Must-Not-Be-Named
- Swindling From SearchFeed - Discusses a method of simulating user clicks on SearchFeed ads, by Atomic Rhino (Matt McMillan, Ontario, Canada, DOB: 11-01-1983)
- Hacker Perspective - by Martin Eberhard
- Bypassing a Restrictive Internet Proxy - Explains how a restrictive Internet filter works, and how to tunnel past it by setting up a SSH tunnel proxy, by Anonymous
- Corkscrew Corkscrew is a tool for tunneling SSH through HTTP proxies.
- Shadow Life - Outlines the basic techniques of creating and maintaining an alias or alternate personality, by Akasha
- Walk With Me, Talk With Me - Discusses gang signs and suggests using for covert communications during field phreaking or urban explorations, by phlux (Clinton Haller)
- Walk With Me, Talk With Me Original
- Letters - DISPATCHES
- Random Bits - A reader of 2600, Travis H., Michael J. Kowalski, Peter, chris, Tsun
- Suggestions - Bluecoat, Rodger, Bryce Lynch, Loki
- Analysis - s, Oisin O'Connell
- Queries - Michelle, Jeff Nunn, drlecter, j4ys0n, Cyph3r7, name, Jan, T.L./Retroactive, Andrew, Anonymous, granny, Widerstand, Jane Doe
- "Surprised?" - Unr3a1, HealWHans
- Statements - Asymptoted, A Depressed Soccer Mom, dave
- Article Feedback - Storm2439, Yawk, Anonymous, Jeff, Da Keet, Mike Diaz, virusrr, Darren McCall, The Jeff, David Barrios
- Scams - Warden1337 (Ontario, Canada), LoHan, Nagasenpai, GeekBoy, L33tphreak
- Opportunity - marie
- Observations - Rob G. (San Jose, CA), LongwoodGeek, Check Check, carbon/infowire, orPHan, J, Jeff, Eric Lee Elliott
- Letter Feedback - Cliff, hAshedmAn, Tony Zinnanti, "Thok", Paul
- Sad News - The Clone (Canada)
- Fun With the Snom Outlook Add-On - Discusses a method of VoIP remote call initiation using the Snom Outlook add-in, by reid
- The EU Directive on Data Retention: Surveillance 2.0 - Discusses the European Union's retention policy for communication data. Details the pros and cons (i.e. privacy vs sanity) and mentions direction U.S. is heading, by Andreas Rietzler
- Transmissions - Discusses broadband service providers efforts to control the Internet and the 'net neutrality' debate, by Dragorn
- Information Flow on Campus: A Closer Look at Wikipedia - Discusses Wikipedia and how the editing process works. Notes the process lends itself to (((bias and manipulation))) of information, by Barrett D. Brown
- Uses for Knoppix - Discusses the use of Knoppix to retrieve files from a Windows machine without having to login to it, by Variable Rush
- Fiction: To Kill an Atomic Subwoofer - Tells the story of how the author silenced a neighbors loud car stereo system, by Dionysus
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Confusing FISA, a foreign intelligence act, with the (technically) legal monitoring U.S. citizens. Note that Evil Corley and the One Percent (and the EFF) were completely silent when Hillary Clinton and the FBI conspired to spy on President Trump to effect to outcome of the 2016 election.
- Cover (Cover Info)
- Cover Inside Foreign Payphones
- Argentina It's hard to believe such old payphones are still in use but this one was indeed found in the Palermo Viejo district of Buenos Aires. Photo by Kingpin
- Barbados Seen in Bridgetown, this has got to be one of the flashiest, most commercial telephones ever created. Photo by Keith Hopkin
- China Seen in Songpan and conveniently next to a fire hydrant. Photo by Ben Tanner
- Ethiopia Seen in Jimma and conveniently next to a trash can. Photo by Ben Tanner
- Back Inside Weird Payphones Moments
- Morocco Found in Agadir, this is probably the most secure phone in the world. At least in outward appearance. Photo by Shareef Zawideh
- England No, it's not a hacker space. It's actually a British Telecom facility in Leeds where payphones are tested. Each payphone runs a TCP/IP stack over PPP. Photo by Kokor Hekus
- United States #1 We had heard that AT&T was dropping all payphone service. Here's the proof. This was spotted outside their Gardena, California office. Photo by Jerry Dixon
- United States #2 "
- Back The Back Cover Photos
- Back Cover Photo #1 Mungopw discovered this 60 foot sign right outside the Muckleshoot Indian Casino in Auburn, Washington. We see the existence of "2600 machines" as an open invitation to hackers to come and try their luck.
- Back Cover Photo #2 Here's one of those tenant directory phones that you find at the entrances to apartment buildings. You scan for the person's name and it dials them, often Touch-Toning their unlisted phone number for you to hear. As you can see, this tenant has a rather interesting name. Spotted (and hacked) by drlecter.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 25!
$2600 Magazine - Volume 25, Number 2 (Summer 2008)
- The Best of Times - Editorial
- Don't "Locate Me" - Clever little hack for defeating Google Maps "Locate Me" feature via MAC address manipulation, and the possibility of turning it around and tracking a target via their MAC, by Terry Stenvold (Vancouver, Canada, Email)
- Don't "Locate Me" Original
- Code: delbr0.sh
- Code: skyhack.sh
- Don't "Locate Me" - Video Demonstration (YouTube)
- Article corrections appear in the letters section of 25:3
- Exploring Road Runner's Internal Network - Discusses how the Road Runner ISP internal network for static IP addresses is (was) wide open for network sniffing!, by Tim
- Hacking Wireless Networks with Windows - Discusses how to access a wireless network that limits connectivity by using an existing computer's MAC address, by Carbide
- The HughesNet FAP - Discusses a method of circumventing the download limits of the HughesNet satellite Internet service, by ntbnnt (Nathan Bennett, Marion, North Carolina, MySpace)
- Telecom Informer - Discusses the technology and standards of SMS text messaging and what it takes to send an receive a simple message, by The Prophet
- Hacking Society - Discusses how companies use holding actions (i.e. placing barriers and wasting your time) to manipulate customers and how to turn the tables on them, by Barrett Brown
- Thirteen Years of Starting a Hacker Scene - Discusses the history of the Brazilian hacker scene and Brazil's firest hacker 'zine, Barata Eletrica, he created in 1994, by Derneval
- Hping (The Part I Forgot) - Discusses the Hping tool from the basics of crafting TCP/UDP packets to advanced abilities like file transfer over ICMP, by Gr@ve_Rose
- Meditation for Hackers: All-Point Techniques - Discusses meditation and several techniques for practicing the author's "all-point" method, by Sai Emrys (Berkeley, California, DOB: 01-12-1982, Facebok, Twitter, YouTube Channel)
- Fun With Network Friends - Discusses a method of being able to view (in Firefox) the web sites someone on your network is viewing using tools in dSniff, by Uriah C.
- Code: HTTPSteal.sh
- MIT Splash 2017 - C11664: Network Fun 101 This class will play out very much like "Fun with Network Friends" from 2600 Magazine. The difference is in the fact that I used these attacks against some friends, and I will be going over more than just what 2600 went over.
- Hacking: A Graffiti Writer's Perspective - Discusses the similarities between computer hacking culture and graffiti artist culture, by sc0ut64 (Dominic Gross, NYC, Miamisburg, Ohio, Website #1, Website #2?, Twitter, DeviantArt, MySpace, Facebook)
- Hacker Perspective - by Barry Wels (The Key, Holland)
- A Portable Encrypted Linux System for Windows - Discusses how to create a portable Linux work environment using TrueCrypt and Damn Small Linux, by Aaron
- MAC Address Changer - Discusses randomly changing your MAC address to maintain your privacy on a network, provides a Bash script to accomplish this easily, by Plasticman (Steve)
- Code: change-mac.sh
- Capturing Botnet Malware Using a Honeypot - Discusses how to set up a Windows honeypot, and analyzes a botnet that infected the author's own honeypot system, by L0j1k
- Letters - dialogue
- Suggestions - Nsane HAcker, Greg
- Inquiries - Carl, Tommy, redtape, Joseph, Mike, Liam/M/37 (Glasgow, Scotland), SAR, etsjobs, John, Eva, Z, Haestar, R, Phobus, Donna, Tom (Austria), [Name Deleted], erik, Acidevil, chris, Musique Maison, ero0cool
- Observations - f0xR4c3r, Padraig, tim, CJ Lorenz, rmpants, SiKing, Bob, Noli, Jigsaw, Barrett Brown, Peter DiGiovanni, Lo$er, aurfalien, Dr. C.
- Critique - Gunslinger, Chris A., Shocked998, Druid, indiana_lau, iivix (U.K.)
- Projects - dave, David, Breaker Boy, Inmate #210266
- Responses - Emperor, Omega_Iteration, Zach C., Exo, Rob, Peet the geek, Unr3a1, Ed, m0untainrebel, creepyinternetstalkerdude
- Problems - Morgan, route (Australia), Martha Adams, Krista (Fredericton, N.B., Canada), Sneak Email from a Vendor, Paddy, Markus (Austria), Nick (England), The Jeff, Max Rider
- Good Things - ExPhillyMM, Apathy, Israel Torres, Lex
- Cracking with the Webtionary - Using Google and Yahoo! and other search engines to "light-force" crack MD5s with an (almost) infinite dictionary, by Acrobatic (Jeff B. Nunn, Dallas, Texas, Website #2)
- Code: index.php
- Code: md5-source.php Crack MD5 v.03 by Acrobatic
- Cracking MD5 Hashes with the Webtionary
- JavaScript Password DOMination: Easy Password Retrieval Using JavaScript and the HTML - Discusses a method of using JavaScript in a browser's address bar to re-display a password from a previous login form, by Jacob P. Silvia
- Spirits 2000 Insecurity - Discusses the Spirits 2000 retail liquor store software suite including where employee and plaintext credit card information is stored, by drlecter (Weston George)
- Transmissions - Discusses the history, circumstances and technical details of the OpenSSL flaw affecting many Debian-based Linux distributions, by Dragorn
- The Geek Squad - Discusses using a keylogger to obtain access to the Geek Squad's customer database, by Turgon
- Bank of America Website Flaw - Describes a security flaw in Bank of America's website which allows other customer credit card statements to be viewed in some circumstances, by malpelo93
- Why is This Computer Connected to the Internet? - Discusses the flawed rational for connecting many computers to the Internet unnecessarily and the potential catastrophic ramifications, by Porter Payne
- Fiction: Message of the Day - Tells the story of how the author almost got arrested for hacking and ended up working as a security consultant, by Peter Wrenshall
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: The Best of $2600: A Hacker Odyssey
- Cover (Cover Info)
- Cover Inside Weird Ass Foreign Payphones
- Tunisia Found in Chebika, near the Algerian border. This is the first payphone we've ever seen that specifically expresses hostility to cell phones. Photo by Lawrence Stoskopf
- Panama Now here's something you don't see every day. Unless you're in Boquete, a city in Chiriquí province, in which case you'd be used to this trailer of phones that was just dropped on an available dirt patch. Note the phone cables running from the hitch on the left. Photo by Xiguy
- Fiji Seen in Suva. We can't really say for sure just what's going on here with the pincher-looking things. Perhaps it's for those people with cell phones? It could also conceivably be some sort of tribal pole. Photo by Peter Vibert
- Argentina We'd love to know the story behind this one. This payphone was found in the middle of the jungle at Iguazú National Park. The sign translates to "Please do not put water on the telephone." Too bad, it was exactly what we wanted to do when we saw it. Photo by Martin
- Back Inside More Strange Foreign Payphones
- Mali At last we can say we have a payphone photo from Timbuktu. And here you can relax outside the phone booth as well as inside. Photo by Stephen Rice
- Thailand Found in Chiang Mai in the north. This thing looks like a creature from The Terminator. Let's hope it's on our side. Photo by swan
- Peru Apparently you can save a lot of time and expense by simply drilling phones into stone walls around here. These ones were found in a mountainous region. Photo by Mark Jensen
- India This phone was seen in Bangalore. It's about as retro a look as we could ever hope for. Photo by Larry Cashdollar
- Back The Back Cover Photos
- Back Cover Photo #1 Tom discovered our secret Walmart trailer parked in a loading zone in an undisclosed part of the country where there were signs all over proclaiming "Camera Use Prohibited." They really should know better, shouldn't they?
- Back Cover Photo #2 Found in Phoenix, Arizona by David Jacobson, who believes this institution's motto should read: "Be debt free and never have to pay for the credit charges that you make in the future. Hacker Financial can make it happen."
- Staff
- Download Unofficial Scanned PDF! (HiRes) (Damaged - Missing Pages 63-64)
- Download The Hacker Digest - Volume 25!
$2600 Magazine - Volume 25, Number 3 (Autumn 2008)
- The Last Shall Be First - Editorial
- Bell's Mind Markup Language - Information on the Bell's Mind "phone scanning by hand" language to help in the creation and dissemination of phone number scanning data, by dual_parallel
- Bell's Mind Markup Language Original
- Code: handscan.pl
- Code: process4mysql.pl
- The TORminator - Perl script to help identify which countries (IPs) are running the exit routers on the Tor network, by OSIN
- Code: parse.pl
- Code: Tor Analyzer
- The State of Cyberspace and Cyberwar - Article discussing what and who could be involved while "fighting" in "cyberspace," by Barrett Brown
- Watching the Watchers - How to prevent you computer from contacting/updating Google Analytics by blocking it in your computer's hosts file, by ZoeB
- Telecom Informer - SMS/800 and SS7 information during the placement of a toll-free call, by The Prophet
- Apple Dashboard Widget Insecurity - Potential security vulnerabilities in Apple's Mac OS X 10.4 Dashboard widgets, including the ability to remotely execute unverified shell commands, by zeitgeist
- Apple Dashboard Widget Insecurity Original
- Penetration Testing: The Red Team Way - Information on Red Team penetration testing and why it pays to start your own to keep up with your "enemies," by MS-Luddite (M$ Luddite, Indiana, DOB: 02-13-1976)
- FaxCore AUID Exploit - Security and password vulnerabilities and default passwords to the FaxCore system, by Element.Crying
- Resource Hacking Windows Vista Games - Use ResHacker to alter Minesweeper as an example, by Vitaminion
- Ripping MP3s from Bleep - Python script to direct-download full MP3 files from Bleep, by m0ther
- Code: bleep_ripper.py
- Imation Insecurities - How to recover files, even after entering six bad passwords, on an Imation 18405 USB flash drive, by PriesT
- Blackhat SEO: Exploring the Dumb Masses to Make a Profit - Information and tips for setting up your own "Blackhat Search Engine Optimizer" content-rich spam websites, by ilikenwf
- Hacker Perspective - by Nick Farr
- Spoofing Banners with Open-Source Servers - Altering the (OpenSSH, or others) server display banners when performing Nmap scans to fool OS fingerprinting, by m0untainrebel (Asheville, North Carolina, Email, YouTube Channel
- A Different Kind of Remote Scripting - Using SSH to execute remote commands and scripts, by Atom Smasher
- A Different Kind of Remote Scripting Original
- Code: adblock-wrt54g.sh
- Letters - COMMUNICATIONS
- Information - macnutzj (Jason, Tennessee, DOB: 06-28-1981), R3t0DD, Bus boy
- Meeting Issues - Jem Tallon (Fargo, ND), Robert, DrF, TIA (Mayaguez, Puerto Rico), Eric (Alabama)
- General Questions - Alex (Switzerland), Kevin, Adam, Terry, KNiGHT, Oxilary, Anonymous, Matt, Andrew, Steph, daniel, Brian V.
- Proclamations - my apologies for not signing, Swinger (Holland), Trollaxor (Grant Hayes, Overland Park, KS) , jodi, Jeff, Homeless Hacker, Lord Pong
- Help Needed - Ian, Singa Crew (Singapore)
- Experiences - Micah, drlecter, Shai, Noah Schiffman (Charleston, SC - Video), S1m0nS3z (Pittsfield, MA), Cracker Spion (Sweden)
- Best of 2600 - Hans, mikef, Jeff Strauss
- Problems - Viksa (New Delhi), Daniel, Terry Stenvold, Psion the GateKeeper (Harrison Township, MI)
- Requests - John, xemail, E
- Contributions - Dr. Rolf Freitag, bluSKR33N
- Observations - John, Dr. No (Germany), drlecter, PriesT, Oddlyeven (Sean Street, Arlington, TX), Sn00py, aurfalien, Manuel (New York, New York), PF, Norm
- Gratitude - 990.Tim, Max@MVCT, Marcio (Toronto, Canada), Kikidotstrange, Sebastian
- Six Quick Points of Disguise - Examples of several quick physical disguise techniques and how to create a subtle, yet effective, disguise, by MasterChen (QuarterMasterChen, Las Vegas, Nevada, Email, Twitter)
- AT&T Wireless Customer Information - Get a AT&T Wireless customer's personal information using only their phone number or last four digits of their Social Security number, by using that number when signing up to AT&T website portal, by Frater Perdurabo
- Setting Up Your Mobile Phone for International Dialing - Overview of the phone number format for calling overseas and the proper use of the + symbol, by The Cheshire Catalyst
- USB Anti-Forensics - Windows 2000/XP registry edits to defeat potential forensic attempts against removable USB media, by briatych
- Transmissions - Wireless vulnerabilities and the weakness of WEP, by Dragorn
- Be Your Own DDNS Service Using PHP - Create your own Dynamic DNS service with a few lines of PHP code, by glider
- Code: ip.php
- Code: sendip.php
- Code: sendip.bat
- Code: invisible.vbs
- Code: currentip.php
- Discovering Firewalls - Using common utilities like traceroute , Hping, and Netcat to detect firewalls and identify on a network, by suN8Hclf
- Hacking Music - Article on the aspects of hacking in making music and the need for musicians not to limit themselves to traditional methods or sounds, by Dr. Zoltan (Dr. Zoltan Øbelisk, Sir Millard Mulch, Carl King, MySpace, YouTube Channel)
- Fiction: Sleeper - Story about meeting a Russian sleeper agent while at school, by Peter Wrenshall
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: The Last HOPE
- Cover (Cover Info)
- Cover Inside Really Strang Payphones
- India #1 Another example of adaptation by the people of Bangalore. These phones are pretty much just nailed to the tree. Nothing unusual here. Photo by infowallah
- India #2 "
- Puerto Rico Seen in the El Condado area. Try to spot what is unusual about this phone. Hint: Something is missing. Photo by Alex Llama
- Dominican Republic We know this is not a payphone. But undoubtedly there are payphone lines hidden in this mess of wires somewhere. Along with a million other things. We pity the repairman who's called upon to find the source of a broken connection here. Photo by TicoPhreak
- Back Inside More Funny Looking Payphones
- United States From a place that's actually called Big Arm in Montana comes this picturesque view of a simple payphone by the side of the road. Photo by Thomas Fleming
- Guinea This phone was found in the capital city of Conakry. It uses national carrier SOTELGUI's network. The country also has at least three cellular networks. Photo by alphabot
- Ecuador Seen at the equator at a tourist stop. Porta also operates the largest GSM network in the country. Photo by pelik
- Canada This is just your basic Canadian payphone manufactured ages ago by Northern Telecom. But this scene from a highway in Alberta looks like some sort of classic painting. This lonely phone is 39 miles from the U.S. border and 65 miles from any town. Photo by Paul Rainey
- Back Cover Photo #1 Motzie found this sign outside her local community college in Edison, New Jersey. If ever there was a good place to have 2600 meetings, right underneath that sign would be it. They even use the same font!
- Back Cover Photo #2 The most elite train in Sweden as seen by Robert Luciani who rode it to Stockholm. If we ever get around to chartering a train, this one is first on the list.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 25!
$2600 Magazine - Volume 25, Number 4 (Winter 2008-2009)
- Beginnings - Editorial
- Introduction to Forensic Data Recovery - How to recover deleted JPEGs (or other files) on an USB drive using Foremost and Knoppix, by Paradox
- Hacking Dubai and More Internet Proxy Loopholes - How to bypass Internet restrictions using a proxy and getting free wireless at hotels in the United Arab Emirates, by forgotten247
- Calling Comdial: Part 1 - CONVERSip EP300 tips and tricks using Nmap and Netcat to view or alter settings, by Metalx1000 (Kristofer Occhipinti, Naples, Florida, YouTube Channel, GitHub)
- Telecom Informer - Telco outside plant cable and grounding information and cable requirements in various environmients, by The Prophet
- De-Obfuscating Scripting Languages - Decoding and 'undoing' the various tricks people use to hide HTML and PHP source, by Cliff
- Social Engineering the Stock Market and Circumventing the Price of Gas - Social engineering ideas to help lower the price of oil, which would probably get you droned or "liberated" in real life, by Isreal
- Making Your Windows Box a Little More Secure - General tutorial and information on how to secure Windows 2000, XP, and Vista, by DieselDragon
- Hack Thyself - "Seeing yourself as the world's victim is profoundly disempowering and keeps you locked in a cycle of self-created pain and misery", by Kartikeya Putra (Alex, Email #1, Email #2, Dallas, Texas)
- "Hacker Hack Thyself" From Phrack, Issue #66
- Hacker Perspective - by Bre Pettis
- Beating the System to Get Beats - Trick to remove the "audio watermarking" from the RocBattle online Flash MP3 player, by Ik
- Anonymous SSH at the Library - How to use a free Java-based SSH client on Rutger's library computers, by carbide
- Trashing Gone Wrong in Switzerland - Story of being busted by the cops Dumpster diving in Switzerland, and why you should always have a (good) cover story, by PriesT
- This Posting Has Been Flagged for Removal - Information on how Craigslist flags its ads/posts and how to bypass restrictions using a proxy, by Half Life
- Improved Mnemonic Password Policy - Evil Corley likes to touch little boys (EClttlb), by Ian Murphy (Backspace)
- Letters - Messages
- Revelations - Pathogen, Quarx, Sai Emrys, Very Anonymous, 63585730, Borked Pseudo Mailed
- Alerts - Mister Mods, J, rosa
- Assorted Meeting Bits - Acetolyne (MySpace, Spokane, Washington), D.
- Inquiries - Angela Sherman, Crash the Greenhat, Mario Chiesa, frameloss, Mark, Wyllie, LiteralKa (Slashdot, Twitter), Jeff, Pelik, m0untainrebel, Louis Martinez, Elizabeth Greer, Daniel, Bavs, Apple Freak, Dan, William R. Epp, Brady DeStefanis (Memphis, TN)
- Rants - Robyn Adelaide, PMD, Greggg (feretman), AJ (Ohio), Unknown Unknown, CJ Hinke (Thailand), Brainwaste, Larry Clements
- Praise - drlecter, scripter, Steve McLaughlin, Nik (Nick Barron), LodeRunner, Andy
- Google Bits - Pulse, brian h.,
- From the Inside - Rob (Michigan), Joseph, Michael Earl Short (Rosharon, TX), Johndillinger, David L. Williamson
- The Future - Phr0zenSane, JP (J.P. Armstrong, Miami, FL)
- Pappy's Cheese Box - Instructinos for building a VoIP-based phreaker's Cheese Box, by Pappy
- Hacking for Beer - Use an alternate I.D. or turn "soda into beer" to purchase beer through a self-checkout system, by Yimir
- Gaming GameStop - How to get an extra 20% and cash when trading in video games at GameStop, by Unanimously Anonymous
- Vulnerabilities in the Corporate Sector - Retrieve data from the hard drives of used computers using GetDataBack, by =-virus-=
- Transmissions - WPA-TKIP vulnerability information and potentially illegal U.S. border searches, by Dragorn
- Business Intelligence - How sales companies and businesses store data on their customers for later analysis, by Tony Hepo
- Hacking WebCT - Information on the WebCT online class software and the possiblity of using other student's accounts to "cheat" on exams, by Milton Bradley
- Fiction: Conspiracy - Can our protagonist pull off the Hack of the Year?, by Peter Wrenshall
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Satan's little helper (a.k.a. Barack Hussein Obama) was "elected." And Evil Corley voted for him...
- Cover (Cover Info)
- Cover Inside Foreign Payphones
- Azerbaijan #1 These distinctly different types of phones were both found in Baku, the capital city. Photo by David Scott
- Azerbaijan #2 "
- Cyprus This is a card-only phone found in the Greek half of capital city Nicosia. Photo by Daniel Olewine
- Malaysia A neat little row of colorful phones found in Kuala Lumpur. Photo by Matthew W.
- Back Inside Unusual Payphones
- Antarctica Yes, there are indeed payphones on the seventh continent. This one can be found at New Zealand's Scott Base. It only takes cards. Photo by rooperator
- Bahamas Found on a cruise ship pier in Nassau, we are told there is indeed a payphone hidden somewhere within all those advertisements. Photo by Scott
- Australia This is actually a radio payphone found on a Sydney to Canberra country train. It uses satellite and mobile phone networks, and only accepts credit vouchers or credit cards. Photo by Rowan Wilding
- Morocco Found somewhere in the middle of nowhere near Errachidia, this is one impressive phone booth (note writing that says "Telephone Public"). Unfortunately it was locked so the actual payphone remains a mystery. Photo by Paul Rainey
- Back Cover Photo #1 This is NOT the 2600 van but merely one of many cheap imitations. Thanks to Vyrix who spotted this off US 290 in Houston, Texas. Our lawyers will be following up with a copyright infringement suit.
- Back Cover Photo #2 Now THIS is a van we'd be proud to own. Actually this vehicle, spotted by asd dasdsa in Uijeongbu, South Korea, is a whole lot more than a mere van. We really don't know what they're up to with this thing, but we want in. (Their website, incidentally, could be used as a pictorial definition of the word "busy.")
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 25!
$2600 Magazine - Volume 26, Number 1 (Spring 2009)
- Year 26 - Editorial
- ATA Security Exposed - Vulnerabilities in ATA hard drive password security and the proper way to securely erase a hard drive, Michael Hampton
- Outsourced - Horror stories of working at an outsourced technical support call center for a large ISP where they are taught not to help the customers, by Witchlight
- Annoying Dormitory Phones - Flaws in the pre-programmed phones at a Swiss university dorm which allowed you to make calls without a phone card ("taxcard"), by Chris Dickinson
- robots.txt Mining Script for the Lazy - Shell script to make a website's robots.txt file "clickable" so you can browse blocked directories manually, by Kelly R. Keeton (Snoqualmie, Washington, K7MHI)
- Telecom Informer - Overview of telco tariffs and public utility commissions, by The Prophet
- Surfing Without a Board - Using a mouse (on a system with no working keyboard) to create a URL in a web browser by copy-and-pasting single letters from Notepad's help screen, by XlogicX
- MP3 Data Stream as a Covert Means of Distributing Information - Hiding data in the unused portions of a MP3 file, by enferex (Matt Davis, GitHub)
- Don't Steal Music!: Catching an iPod Thief Using Forensic Evidence - Tracking down who stole his iPod by utilizing the device access log times, by Todd Garrison (frameloss)
- Inside Google Radio - Overview of the SS32 radio automation system and Google Radio Automation, by hypo
- Scour: Paid to Search, Again? - Trick using AutoHotKey to earn extra points via Scour, by D4vedw1n
- Code: scour.ahk
- Battling the Fanuc Datapanel - Story of a tech who needed to replace a GE Fanuc 1062 Datapanel and problems with the proprietary WinCfg software which they had to overcome, by scamorama
- Network Neutrality Simplified - General overview on the need to keep the Internet "neutral" by net neutrality laws, by linear
- Network Neutrality Simplified Original United Phone Losers, Issue #30
- Hacker Perspective - by Virgil Griffith (Website)
- Second Life Hacking - Case study using the online virtual world Second Life discussing security vulnerabilities in email-based "Forgot your password?" password recovery systems, by Lex Neva
- Exploiting Price Matching Through JavaScript Injection - Discusses a method of modifying web pages with in-browser JavaScript so the page can be printed out and brought to certain stores for a price-matching discount, by Sigma
- Hacker Spaces of North America - List of hackerspaces in North America
- Letters - Social Discourse
- Random Advice - Exothermicus (Denton, TX), Jesus Bonehead (Victoria, British Columbia)
- Random Observation - Clay (Lakeland, FL)
- Random Remarks - Neito, Jesus Montoya, R. Toby Richards
- Random Questions - DANIEL OBORI (Nigeria), Jason Liszkiewicz (Twitter, New York, New York), misterht01, userguid, The Scorpion, William, fakexsound (Marc DeAngelis, Massachusetts), cu florian hannemann, Art Smass (Santa Cruz, CA)
- Random Problems - Infinityx, Jack, John and Lissa (Jacksonville, FL), Colby, Arkhayne, Syntax, Robert Royer
- Random Info - Sync, R. Holden, Sync, Jeff, ulysses, Mr. Velleman (France)
- Random Feedback - Big G, Anonymous, Jason, Arethusa, Steven C. Jackson, CJ, Vandy, Michael, gHOst_Guard, Estragon, Shocked998, ZANAC, thinkt4nk, jus, bogaty, Pampaluz, Ben Edwards
- Random Offer - freakball
- DNS Spoofing on a LAN - Discusses DNS spoofing and describes the steps necessary to accomplish it on your own network, by Felixalias
- An Astronomer's Perspective on Hacking - Discusses some of the author's phreaking experiences while at work late at night and how being curious about things can lead you to unexpected results, by Ethernium57 (Omaha, Nebraska)
- Transmissions - Discusses how simple it is to spoof wireless network access points to gain access to client machines using various tools and procedures and the lack of adequate defenses to protect against this attack, by Dragorn
- Social Engineering HP for Fun and Profit - Discusses some weaknesses in the HP customer support system that could be taken advantage of, by haxadecimal
- The Last 1000 Feet - Discusses the author's experience with getting wireless Internet access to his newly built house after he found out the corporate ISPs didn't provide service in his area, by b1tl0ck
- Fiction: The Particle - Tells the story of a couple of days in the life of a network support engineer and the strange occurrences that took place, by Leviathan
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Celebrating 26 years of this crap!
- Cover (Cover Info)
- Cover Inside Eastern European Payphones
- Serbia #1 Found in Belgrade, these phones seem to be the prevailing model throughout the city and possibly the entire country. Photos by Stevan Radanovic
- Serbia #2 ""
- Ukraine #1 Both of these phones were seen in the city of Cherkasy. One is a newer model while the other is a slight bit older. See if you can figure out which is which. The older one was actually attached to the former KGB building. Both are operated by Ukrtelecom. Photos by Alex Kudelin
- Ukraine #2 ""
- Back Inside Foreign Payphones
- Hungary #1 Seen in Szolnok in a quaint but graffiti ridden booth, this phone is operated by T-Com, a fully consolidated subsidiary of German phone giant Deutsche Telekom, the company best known for inventing the pink handset. Photos by Rob Craig
- Hungary #2 ""
- Malaysia #1 Seen in the state of Johor in West Malaysia, these are two distinct types of payphones that have each been around for a while. The first can be found in restaurants and other establishments while the second is more likely to be seen outdoors or in an unsecured environment. Photos by Jayakanthan Lachmanan
- Malaysia #2 ""
- Back Cover Photo #1 This may indeed be the most "leet" highway in America, discovered by Rob Dolst somewhere on the tenuous border of Prince George County and Hopewell, Virginia. The name "Crossing Boulevard," however, has to be among the lamest of the lame.
- Back Cover Photo #2 This happens far more often than you might think. It would be wise to warn parents everywhere that our magazine, although high in fiber and good for the brain, is not a substitute for the more traditional sustenance. Thanks to Nick and his son Bruce for helping us get this message out.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 26!
$2600 Magazine - Volume 26, Number 2 (Summer 2009)
- Not The Enemy - Editorial
- Regaining Privacy in a Digital World - Very good article on protecting your privacy in both the real-world and online, information on how to remove yourself from online "White Page" listings and how to properly setup and use a PO box, by 6-Pack
- The Security-Conscious Uncle - Amusing story of using a little bit of social engineering and a default voice mailbox passcode system to guess the ATM PIN of a "security aware" uncle, by Deviant Ollam
- "The Security-Conscious Uncle" Original
- Why the "No-Fly List" is a Fraud - Potential way to bypass the "No-Fly List" by printing two legitimate boarding passes, but with different names, by cbsm2009
- Telecom Informer - Overview of the Motorola iDEN cellular protocol and the Nextel/Sprint Boost Mobile saga, by The Prophet
- Understanding the Unusual iDEN Network
- Frank's Fantastically Fabulous Radiorausch
- Motorola iDEN Technical Overview (2.7M PDF)
- Finding Information in the Library of Congress - Information on searching the Library of Congress website for hacker-related documents (and Area 51!), by Fantacmet (Michael S. Dooley, Portland, Oregon, DOB: 02-12-1978, Email #2, YouTube Channel)
- Hacking the D-Link DI-524 Interface - Information and an encryption bug fix using a web browser and JavaScript tweaks for the D-Link DI-524 wireless router, by der_m (Jonathan Hadley, Lombard, Illinois, MySpace)
- Simple How-To on Wireless and Windows Cracking: Part 1 - Detailed overview on using a BackTrack USB boot disk, with the included airodump/aireplay/aircrack tools, for attacking WEP/WPA protected Wi-Fi networks, by KES
- If You Can't Stand the Heat, Hack the Computers!: Part 1 - Hacking and exploring an OAS Heat Computer Model 6310 via modem dial-up and be your own Mr. Robot, by The Philosopher (Email, New York, New York)
- Security: Truth Versus Fiction - Essay about the author's real-life encounter with a university's student campus building security system, by RussianBlue
- Hacking the Beamz - How to extract and edit the proprietary sound files used by the Beamz laser harp, by shotintoeternity (Kevin Carter, Brooklyn, New York, Twitter)
- Hacker Perspective - by Jason Scott (Jason Sadofsky)
- iTunes Stored Credit Card Vulnerability - Major security hole if the "one-click" purchase option is used under iTunes - even when password is changed, by Brendan Griffiths (New York, New York)
- Zipcar's Information Infrastructure - Overview of the Zipcar car sharing and car club service and some real-world experiences, by IntlOrange
- The How and Why of Hacking the U.N. - Python script to bypass the "referrer blocking" so you can grab PDF copies of meeting transcripts from the United Nations website, by Julian Todd (Liverpool, England, Twitter)
- Code: un-grab.py
- Listen to Radio Hackers! - Active VHF and UHF frequencies used by hackers in the U.S. and the French hacker Larsen (Vincent Plousey), by CRCF (Chaos Radio Club of France)
- Hacker Spaces of Europe - Hackers spaces in Europe
- Letters - reader reflections
- Stories - Andrew, Rman665+1, George, Ampix0 (YouTube), carlos, Greg C., Anonymous
- Remarks - Peter Wrenshall, Travis H., Jeff, Chris H., William R. Epp, Sean, none none, Anonymous, Louie Ludwig, Chris, Ph1UK3r_TIH, John Cartwright (Vicksburg, MS)
- Submissions - Michael W., Mack, Toby, Tyler, Collin, James Kern
- Responses - Florian, Sonny, Hudson, Brad, NNY2600, Granny, The Piano Guy, saizai, SAR, Don "The Jaded Tech" (Don Belmore, Hamilton, Ontario), XlogicX, linear, Alex, Life Subscriber
- Queries - Bones122, Mitch, link7373 (Colin Beck, Twitter, Edmonton, Canada), Michael, Leonard
- Ideas - Dan, c1f
- Appeals - farooq noor, Bpa, Angelique, dawn, 27B/6
- Abusing Metadata - Information and privacy aspects on viewing any metadata information inside a variety of files, by ChrisJohnRiley (Heidenreichstein, Austria, Email, Twitter)
- Verizon Fios Wireless Insecurities - Major security problems in Verizon Fios default Actiontec Wi-Fi router configurations, by phishphreek
- Transmissions - Overview and history of the author's Kismet program, by Dragorn
- Using Network Recon to Solve a Problem - Story of using Nmap to identify problems on a misconfigured network, by Aesun
- Suing Telemarketers for Fun and Profit - How to file (and win) a lawsuit against a telemarketer for violating you "Do Not Call" rights, by Sai Emrys (Sanford, North Carolina, Twitter)
- Telemarketer Lawsuits Filed
- "Extended Car Warranty" Telemarketing Fraud Help me sue the bastards.
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Clinton/Obama/Biden are gonna basically trying to kill free speech on the Internet, but Evil Corley and the One Percent don't care because Obama is a negro jew-tool and Democrat.
- Cover (Cover Info)
- Cover Inside Payphones of the Old World
- Egypt This phone box was located on the bank of the River Nile, just outside the Temple of Kom Ombo. Photo by Ben Sampson
- Egypt Another common type of phone that can be seen throughout the country. This one was found in Luxor. Photo by troglow
- Ukraine This phone has obviously seen it all and still has managed to retain a sense of fashion. Seen in Lviv. Photo by c. sherman
- Vatican City Technically a country right in the middle of Rome, this may very well be the only payphone in existence there. It can be found at St. Peter's Basilica on the "roof" overlooking Piazza San Pietro. From this phone you are eye level with the 140 statues of saints. Photo by Da Beave
- Back Inside More Foreign Payphones
- Suriname Found at the Torarica Hotel in Paramaribo, this payphone lacks an enclosure but has a sticker with the website for Telesur, the national telecommunications operator. Photo by TProphet
- Japan A stylish and very busy phone, which was seen near the grounds of Kumamoto Castle on the island of Kyushu. Photo by LART
- Canada It's amazing what you can do to an ordinary payphone with a little imagination and rustic charm. Found in Fort Edmonton Park, a historical park in Alberta. Photo by Carsen Q.
- South Africa Found at the waterfront in Cape Town, this Telkom payphone takes both coins and cards. Photo by TProphet
- Back Cover Photo #1 Perhaps you've heard of Hackers on a Plane? Well, here we have Hackers on a Bus, discovered by Rolla J. in Budapest, Hungary. Now if only this company would branch into air travel, we could really have some fun.
- Back Cover Photo #2 O.K., let this be notice to all of you who call us in a panic every time someone on Jeopardy! has $2,600 on their display: it happens all the time and it's not a big deal anymore! But when all three contestants have it, that's pretty damn cool. This alignment was spotted and captured by Mike Troutman on April 4th, 2009.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 26!
"Answer: Gets teenaged boys drunk at HOPE and sells other people's old BBS files."
$2600 Magazine - Volume 26, Number 3 (Autumn 2009)
- Hacking In Tents - Editorial
- Exploiting University Students Using Rogue Access Points - Story of a student at a college who would use "rogue" unauthorized access points to intercept wireless traffic of students and staff, by Anonymous
- Catching a Laptop Thief/Wi-Fi Hacker - Overview of the author's Perl script called Catchme-ng.pl which greps the output file from Airodump-ng repeatedly for a specified MAC address, like one connected to your missing device, by Douglas McLain Berdeaux (Pittsburgh, Pennsylvania, Trevelyn, Email #1, Twitter #1, Twitter #2, Wikipedia, GitHub, SOLDIERX)
- Code: Catchme-ng.pl
- WeakNet Labs: WEAKERTH4N Linux
- WARCARRIER 2013 by Douglas Berdeaux
- Attacking a Blind Spot - Ideas to use open network printers to scan IPs or launch network attacks as they tend to not be as secure or will have open ports, by Tim Kulp (cloak13, Parkton, Maryland)
- How to Almost Hide Your Digital Identity While Port Scanning with Nmap - How to hide your source IP address when scanning a network using Nmap, by Bryce Verdier
- Telecom Informer - Overview of the different types of operator-handled (AT&T, etc.), station-to-station or person-to-person calls, and their billing options, by The Prophet
- Operator, May I Help You? Original
- Hello! Google Calling - Overview of the the new Google Voice service and how to use it to protect your own phone number, for social engineering, or for pranks, by Trowel Faz (Joe Klemencic) and caphrim007 (Tim Rupp, Aurora, Illinois)
- Post-Apocalyptic Communications - Overview of potential amateur radio communication ideas for after Obama kills most of us, by J. P. Armstrong
- Post-Apocalyptic Communications via HackMiami
- Roll Your Own Hive Mind - How to use social networking sites like Facebook, Twitter, MySpace, etc. to look for people with common interests, ax0n
- Free DirecTV on Frontier - How to get free DirecTV service using an expired American Express gift card on Frontier Airlines, by Outlawyr
- Free Trials - Avoid Giving Out Your Credit Card Number - Generate "fake," but numerically accurate, credit card numbers using the standard Luhn algorithm, by hostileapostle
- If You Can't Stand the Heat, Hack the Computers!: Part 2 - Hacking and exploring an OAS Heat Computer Model 6310 via modem dial-up and be your own Mr. Robot, by The Philosopher
- Hacker Perspective - by Johannes Grenzfurthner
- Granny Loves Linux! - Story of setting up a Linux system for his wife's parents and a granny, by Metaranha (Belleville, MI)
- Cracking WPA-PSK... with Aircrack-ng & BackTrack 3 - Detailed overview of a WPA-PSK attack using a BackTrack 3 live CD, by Mister Cool
- Hacker Spaces - The Rest of the World - Hackers spaces in Asia and Australia/New Zealand
- Letters - Vowels & Consonants
- Building the Community - Tuyishime Aimable (Rwanda), warlock (Dublin, Ireland), Joel (Florida), Lowery (California), Lowery, Jason, peter (Amsterdam), Zach, Prateek (India)
- Ideas on Spreading Knowledge - Travis H., Holden
- New Information - dmchale, katkat, ++divide_by_zero
- All Sorts of Questions - Brad, Leone263, Frank Moore (Australia), Michael, Nicolas, Apple Freak, iphelix, Scott Brown, Sai, Steven, Arnel, Julie, sc0ut, Son, Ray, Fiez
- Interesting Observations - eddiehaskell, SigFLUP, The Security Department, Golden Helix, UncleJesus, Mr. Fossey, Me, Levi del Valle (Sioux Falls, South Dakota), JZ, Jason
- Cries for Help - Steve, anonymous, anonymous, Jim, josh
- General Feedback - Gary, 3lan, yt, Ed Greenburg, Fiddles McHace, tavis, aurfalien, S, Clay, Israel, Ryau, Justin, Michael Gabriel, Fiducia
- Hard Disk Encryption, No Excuses - Overview of installing and using TrueCrypt for full-disk encryption and why no one should have an unencrypted hard drive in today's society, by GhostRydr
- Microsoft, Please Salt My Hash! - Huge security vulnerability in Microsoft Windows as the password hashes are not salted, by Sam Bowne (Twitter, San Francisco, California)
- fgdump A tool for mass password auditing of Windows Systems
- Amazing Grace Period: How to Get Free Loans From American Express - How to exploit the "grace period" of American Express credit cards and still stay in good standing with them, by Bavs
- Transmissions - Discusses how Wi-Fi is basically a throwback to the days of shared media networks and many vulnerabilities like session hijacking still exist, by Dragorn
- SSL DNSSEC - Overview of implementing the Domain Name System Security Extension (DNSSEC) to add security the the DNS system and a comparison to SSL, John Bayne
- Tethering the Samsung SCH-r450 on MetroPCS - Overview of the MetroPCS flat-rate CDMA service and hacking the Samsung SCH-r450 using serial AT commands, by VXO
- "Borrowing" the CustomInk.com Vector Library - How to download the vector images and EPS files from the CustomInk online T-shirt design site, by GantMan (YouTube)
- Code: customink.vbs
- Hacking Your Hospital Bed - Overview of the controls for the Stryker Secure II hospital bed and how to sneak out of it without setting of the alarm, by The Piano Guy (Gary Rimar)
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Hacking at Random 2009
- Cover (Cover Info)
- Cover Inside Payphones in Exotic Places
- Guatemala One of the typical phones found throughout the country. Photo by Gary Davenport
- Burkina Faso This rather dusty phone was found in the city of Ouagadougou. Note the symbol for international calling: one flag connecting to another. Photo by M J
- Rwanda Seen in the departures area of the Kigali Airport. (It didn't work, incidentally.) Photo by Jeffrey Mann
- Mauritius This brightly colored model that takes both coins and cards was discovered beside the Pereybère Beach in Pereybère. Photo by Scott Brown
- Back Inside Unusual Looking Payphones
- France The unusual thing about this phone found in the countryside is the fact that it takes neither coins nor cards. In fact, this phone can only make emergency calls or calls using credit or calling cards. In France, the law states that every city, town, or village must have at least one payphone. Photo by Mike Miller
- Japan They don't really get much pinker than this model, found in a park in Ueno, Tokyo. Photo by Jim E. Etheredge II
- Thailand Seen in a place called Chiang Mai, or perhaps it was just a hallucination. Photo by professor ned
- Russia This was actually the grand opening of a payphone in Kamchatka Oblast. We can't even imagine one of our phones being celebrated so festively. These people must really appreciate telephony. Photo by Curtis Vaughan
- Back Cover Photo #1 Now here's a campaign we can all get behind. This race took place in Illinois and we don't really know how it turned out. But that's not the point, is it? Thanks to Rich Tordia for letting us know about our increasing political presence.
- Back Cover Photo #2 Perhaps this is the true predecessor to 2600 meetings held on the third Tuesday after Easter. Thanks to Mr. Skillz for letting us know how elite things once were back in the medieval days.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 26!
$2600 Magazine - Volume 26, Number 4 (Winter 2009-2010)
- Smart Regression - Editorial
- Pwning Past Whole Disk Encryption - How to modify initrd.img during Linux boot-up to copy a passwd/shadow file or capture the passphrase to bypass full-disk encryption, by m0untainrebel
- L33ching the L33chers: Using a Portable Wireless Network - How to set up a portable, public wireless network to intercept Wi-Fi traffic and the insecurity of public WLANS, by DieselDragon
- Telecom Informer - Overview of YMAX Communications' MagicJack VoIP service and the Stratus gateway servers, by The Prophet
- Hacking Tor's Control Protocol - How to enhance (or break) privacy by delving into Tor's internals, custom circuits of any size, and monitor every aspect of Tor activity, by iphelix (Peter Kacherginsky, San Francisco, California, Twitter, Medium, GitHub)
- Code: tor-autocircuit.tar.gz Automatically creates circuits and attaches streams according to predefined rules such as circuit geolocation, path length, etc. (GitHub)
- Code: tor-nodes.py
- Hacking the Tor Control Protocol Original
- 2600 Magazine - Tor Control Protocol
- Hack T-Mobile Prepaid Messaging and T-Zones - Bypass T-Mobile prepaid phone limitations by using web-by-email services and mobi.traffic.com, by Mr. Curious / DoPi
- Calling Comdial: Part 2 - How to record and playback VoIP calls using a packet sniffer like Ettercap, by Metalx1000
- Underground Physical Network - Tips on how to setup a remote physical satellite "hacking" sites, caches, or safe houses, by MasterChen
- Understanding Hacking Tools with Socket Programming - Why understanding TCP socket programming is essential for any hacker, by Uriah C.
- Hacker Perspective - by Annalee Newitz
- Hey Adobe! Leave My Boot Loader Alone! - Info on how Adobe's stupid copyright protection scheme overwrites you master boot record, and how to overcome and recover from this, by dolst (Rob Gregory, Claremont, Virginia, YouTube Channel, Twitter)
- An Examination of the NTFS Boot Record by Daniel B. Sedory
- Revenge is a Dish Best Served Cold - Story of student getting back at a bully in his class by using the "net send" command, by Valnour
- Hacker Spaces - List of foreign (non-U.S.) hackerspaces.
- Letters - VOLLEYS
- Meeting Stuff - Michael Craft (Birmingham, AL), patgroove (Calgary, Canada), Richard (Vienna, Austria)
- Inquirirs - Mark C., ternarybit, Jane Doe, 7shots, John (Texas), Manny, BASE 400, Doug, sonnik, Guillaume (Santa Monica, CA), Wendell
- Observations - Barrett D. Brown, reconfigure (New York, NY), Nunook (Florida), Reader in Brooklyn, New York, Ankylosaurus, Rob, blackoperations, TheC0A7S (Andrew Coats, St. Louis, MO), The Webist, Michael J. Ferris
- Requests - Lyle, T
- Grammer and Spelling - Jeff, Adam
- Feedback - BattleBotBob, irperera, Virgil, Jason, sotsov, nevarDeath (Sand Springs, OK), Enygma, Brainwaste, Nicko, Michael E. Short (Rosharon, TX), corwin137, NS, jbh, Erik S.
- Social Engineering from a New Perspective - Social engineering from a woman's perspective and some tools and tricks to use, by Lilith (Bluma Janowitz, x.25 Princess)
- 2600 Nostalgia by Bluma Janowitz
- A Simple Technique for Drum 'n' Bass - C routines for a keyboard-based program for creating techno music and loops from a sample audio file, by SigFLUP (Thea, Email)
- Code: dnb.c
- Audio: 2600_beat.mp3
- Audio: test_loop.wav
- Retail Automation: ABS - Overview of the ABS point of sale system by Retail Automation and how to access its data files, by L00dHum
- Connecting to StreamTheWorld Audio Stream Directly - How to connect and stream (or download) MP3 audio from StreamTheWorld without using their client, by mr_cow
- Transmissions - Discussion on the security vulnerabilities with today's cellular phones and why it pays to be a Luddite, by Dragorn
- The Importance of Updating Your Computer and Hacking Your School's Network - Exploiting the Windows RPC DCOM vulnerability to grab passwords (hashes) and then access a school grading computer, by Desert_Fox and 6|21|3|11
- Fiction: Shakedown - Tells the story of a help-desk technician who has to fly to a customer site because they believe they have a hacker and how he stumbles upon the true problem, by Peter Wrenshall
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Human devolution with technology
- Cover (Cover Info)
- Cover Inside Unusual Payphones
- United States In the U.S., you might say payphones are a dying breed. Found in Franklin, North Carolina outside a gas station on the highway 23/74 bypass. Photo by Sam T. Hoover
- Kyrgyzstan Quite the opposite holds true in Kyrgyzstan, found in Bishkek. These models have existed for ages in the old Soviet Union. This one has been converted to Touch-Tone from rotary dial and it's also been freshly painted. It's not going anywhere. Photo by romano.tamo
- Japan We never tire of these weird little payphones found all over Japan. One has to wonder what's really going on in all that space under the hood. It being pink and rotary is just an added bonus. Found in the lobby of a hotel in rural Suzuka. Photo by Darren Stone
- United States And we're back in the United States again where (did we mention?) payphones are a dying breed. And in a variety of styles. Found in Newport Beach, California. Photo by Matt Figroid
- Back Inside Unusual Phone Booths
- Turks and Caicos Islands One of these phones is not like the other. These booths were found outside the phone company building in Grand Turk The phone company, incidentally, is known as Landline, Internet, Mobile, Entertainment (LIME). Photo by Dieselpwner
- New Zealand This is about as grandiose as it gets. This booth, found in Arrowtown, is closer to the size of an apartment than a phone booth. Photo by Michael Hall
- Lithuania This one is just unusual on a variety of levels. The colorful booth, the bright blue phone, the old street scene, even that strange word that means telephone. This is, of course, in Lithuania, in the old town district of Vilnius. Photo by Elvis
- United States In the U.S., payphones are going through a confusing period, as is evidenced by these ones found in West Caldwell, New Jersey. Why they are Chinese-themed is anyone's guess. They were seen outside a ShopRite in a neighborhood with no obvious Asian connection. Photo by Conor Laverty
- Back Cover Photo #1 Let's make this crystal clear. We don't condone mindless graffiti that makes the world less attractive. However, this is without a doubt one of the most beautiful applications of guerilla art that we've come across. We're not sure what makes it so amazing but something in it speaks to us. Thanks go to Nokier in Melbourne, Australia for spotting this (but not for creating it we presume).
- Back Cover Photo #2 We can only imagine the possibilities of having German hackers design and build your kitchen. Until that day comes, we'll be happy just to see this 18-wheeler go speeding past us on the Autobahn someday. Discovered by Hollowpoint in Hemel Hempstead in England.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 26!
$2600 Magazine - Volume 27, Number 1 (Spring 2010)
- Cloudy Skies - Editorial
- Insecurities in Emergency Rescue - Lack of real security with the "EMS 2000" program used by many fire or EMS departments, by Metalx1000
- Ajax Hacking for the Discerning Pro Wrestling Fanatic - How to use Ajax to bypass ads on websites which are aware of Adblock, by Gorgeous_G
- Code: Do-Fixer-Neo.js
- A Little Fish in a BigPond - Overview of the Netcomm 3G9W router used by BigPond and the fact that part of the WPA key is in the default SSID, by kawarimono@bigpond.com (Australia)
- Code: append.vbs
- The Grey Hat Manifesto - Looks like someone who got picked on in middle school tried to write a new "Hacker Manifesto," by Da New Ment0r of PhoeniX.RisingG.GrouP
- Telecom Informer - Disabling incoming calls on payphones to stop "shady operations" and a good TracFone service overview, by The Prophet
- Deciphering TracFone Original
- No Sale for You! - Potential privacy issues with the Kroger Shoppers Card and other grocery store cards, by Keeng Tusk
- CrazyGeorge - Security Through Obscurity - Hidden data and webpages on George Sodini's website, by Lnkd.com?2600 (Robert Simpson, Pittsburgh, Pennsylvania)
- BartPE: A Portable Microsoft Windows - How to create a fairly secure, and portable, Windows-like environment using Bart's Preinstalled Environment, by Peter Wrenshall
- Bart's Preinstalled Environment (BartPE) Bootable live Windows CD/DVD
- Influential Angles - Overview and examples of using social engineering techniques to get information out of people, by The Third Man (Scotland, United Kingdom)
- Hacker Perspective - by David Alan Buchwald (Bill from RNOC, Sigmund Fraud [LOD/H], Dabu Ch'wald, DOB: 09-04-1970)
- The Hacker Enigma: Positives, Negatives and Who Knows? - Stories of what happens if you co-workers catch on to you screwing around while you should be working, by pantos
- An Introduction to CSRF Attacks - Overview of Cross-Site Request Forgery (CSRF) attacks and how to prevent them, by Paradox
- The Voyager Library Information System - Overview of the Voyager Library Information System, their simple password schemes, and how much private information they store, by Decora
- "Print Me?" Why, Thank You! - Overview of the PrintMe services available at many hotels and some potential security holes, by StankDawg
- Letters - Speak
- Inquiries - Norm, Anonymous, adnan c, zkyp (Nigel, Utrecht, Holland), Allan (New York, New York), Sheeraz, Alex, nd, Anonymous in Ohio, Brainwaste
- Meetings - Blaine (West Virginia), Dustin (Omaha, Nebraska), Zook
- A Way Out - Anonymous
- Suggestions - Rusty, Cody Burris, Spider_J, Kaluce, Rebeka
- Gratitude - anonymous, Alex Meanberg, twEaKer, Chrome
- Observations - J Gonzalez, DMUX, Derf, Mattew, Titeotwawki, Robert, E85, Moose, Kyle (Baton Rouge, LA), Ash, Bob White (Atlanta, GA), Quarx, Hexagon Sun
- Telephone Tidbits - Norm, Grumble
- Help Needed - Leanardo, Bob (Newburgh, New York), Name Deleted
- More Info - Brian, Node42 (Germany), m0rebel, Kyle, Name Deleted
- My First Hack - Story of a hacker in 1972 bypassing a phone dial lock by "flashing" the hook switch and his eventual trip into computer programming, by fobg
- Dr. Jekyll and Mr. PayPass - Amusing story of removing the RFID chip in a Citizens Bank PayPass (or other) credit/debit card using only a paper hole punch, by 11001001
- Writing a Small Port Checker in C in 40 Lines (or Less) - Quick little (buggy) code for a single-host port scanner in C, by Pantos
- Code: myscan.c
- Procurve Switch Hacking - How to enter a command line "test mode" on a HP ProCurve Ethernet switch, by Tzu Tzu Metals
- Transmissions - Why I like print; or, "E-books can go to Hell," by Dragorn
- Bluetooth Hacking Primer - This document is not a guide about actually attacking Bluetooth devices, but rather walks the reader through Bluetooth's basic principles of operation, and touches on the hardware and software setup required to start doing security related research, by MS3FGX
- Simple How-To on Wireless and Windows Cracking - Part 2 - Update to Simple How-To on Wireless and Windows Cracking which appeared in the Summer 2009 issue, by KES
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Security and privacy issues with large companies handling your email and other personal data.
- Cover (Cover Info)
- Cover Inside Foreign Payphones
- Italy This neat little row of phones was seen in Venice and is a callback to the times when cell phones didn't even exist. We suspect the voice quality on these models is also much better than today's norm. Photo by Sean K.
- Costa Rica Seen at Manuel Antonio National Park just south of Quepos on the Pacific coast, this rugged little phone looks like it's been through a lot. We're told the number is 2777-5188. Photo by EJD
- Russia #1 These were both found in the city of Tiksi, where you need special clearance to visit. The rotary phone on the left was seen at their airport and has likely been there forever. The more modern red phone was in a hotel lobby. You might think this is the most northerly payphone photo we have. You would be wrong. We top this in just a few more photos. Photo by Robert X
- Russia #2 "
- Back Inside Unusual Payphones
- Canada This was seen in Ottawa in a place where people apparently come to let out all of their frustrations. And we wouldn't be at all surprised if the phone still worked. Photo by Etienne T
- Norway We believe this to be the most northerly payphone photo we have, found in Ny-Ålesund, one of the settlements on the island of Spitsbergen. Only 750 miles from the North Pole, this phone connects to the world via satellite. Photo by adder1972
- Chile It may take you a moment or two to even find the payphone here. Seen in Valparaíso, this is an example of how a little bit of decorating can quickly spiral out of control. Those prices, incidentally, are in Chilean pesos and are nothing to panic over. Photo by Celeste Robert
- United States This is a great example of what can happen when people stop using payphones. Telebeam operates (somewhere) in the streets of New York. Perhaps this is the first truly green phone company. Photo by Brooke
- Back Cover Photo #1 This is one of those ironies where one could say we've "hacked" the photo to make it say "foto hacker" but in reality this is exactly how it appeared in Neckarsulm, Germany (home of Audi) as discovered by Teddy Du Champ. There's really no limit to what you can find in a country where "hacker" is a fairly common name.
- Back Cover Photo #2 There's no question that children like 2600. Exhaustive market tests have consistently proven this. But we never expected them to erect a shrine to us in a playground. That is something we could definitely get used to. Thanks to Damien for tracking this one down in Charleston, South Carolina.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 27!
$2600 Magazine - Volume 27, Number 2 (Summer 2010)
- "The Hacker Dialogue" - Editorial
- Hacking Google Analytics - How to prevent Google Analytics from tracking your search data and how to view what they have already collected, by Minishark
- My Second Implant - Story of a person who supposedly had a speaker implant near his ear, by Estragon
- Free Encrypted 3G Web Access on T-Mobile Smartphones - Tricks to get Internet access on a T-Mobile phone if your subscriber plan doesn't allow it by using HTTPS proxies, by EvilGold (Joe Sapienza, Lindenhurst, New York, YouTube Channel)
- Why Cell May Die in a Modern Hacker's World - How free Wi-Fi, Skype, and VoIP services are competing with commercial cellular services, by Ron Overdrive (Ronald A. Festa, New Jersey, KC2WQW)
- Telecom Informer - Telecommunications industry in China and some tips for VoIP and Google Voice, by The Prophet
- Call the World for Free With Universal International Freefone Service - Using Universal International Freefone Numbers (UIFN) for toll-free international VoIP calling, by BitRobber
- How to Create Mass Hysteria on a College Campus Using Facebook - Funny story of a person setting up fake Facebook accounts for people at his college, by alleyrat
- Educational Wireless Honeypots - Setting up an open Wi-Fi access point as a honeypot as a tool to tell users about wireless security, by Pan Goat (Jaime Magiera, Ann Arbor, Michigan, Phone: 734-665-9702, Email, MySpace)
- Code: dhcpd.conf
- Code: named.conf
- Code: db.localroot
- Code: httpd.conf
- I'm Not a Number - Overview of barcodes and the UPC system and their use in privacy invasion at supermarkets - and the potential to make your own to "boost" your reward points, by Poacher
- How I Scored the Avaya PBX init Password - An Avaya outsourcing partner handed my training class the most guarded password in IT. This is what went down, by The Funkster Deluxe
- Why You Need a Grimoire - How to use technical "black magic" in your hacking sessions, by Leviathan
- (Potential) Laptop Recovery - Example of some simple tips and tricks you can use to get your laptop back if it's stolen, including using the webcam and putting your phone number in the displayed login screen, by Twisted Uterus
- Free Access on Boingo Wireless - How to hack Boingo Wireless hotspots to gain free Internet access, by ZoDiaC13 (Canada)
- How AT&T Data Plans Work (and How to Make Them Stop Working) - Social engineering tricks to get out of a AT&T cellular data plan you don't want by changing the account's service order code, by excessive|offnetwork
- Casual Encounters of the Third Kind: A Bayesian Classifier for Craigslist - Using Bayesian filtering techniques on Craigslist to weed out spam messages, by Brian Detweiler
- Letters - Textual Feedback
- Discoveries - Zachary Hanna (San Francisco, CA), Dufu, DieselDragon, Justin Nathans, Will, Justin Nathans, Jeff, Anonymous Coward, Malvineous
- Beating the System - Tom, Marc
- Inquiring Minds - Robert Bradbury, John Hilger, Aaron, D MADERAS, Ed, jitsutech, D MADERAS, Patrick Flynn, Jsnake
- On Grammar - Antix (John Kula), RWM, B
- Contributions - Glenn, Glenn Andreiev (DOB: 07-20-1961), Curtis (Renton, Washington), A Weapon of Mass Construction (Travis H.), Unknown, j, TPhreak
- Ignorance - user0010, Dr. Cadwell
- Random Meeting Notes - Froilan, Random/floodland, Vladinator
- Further Comments - Ian, Chow, Dammpa, Mr. Fright, circuitboardsurfer, Eric, Insomniaque
- The Publishing World - jefftheworld (Jeff Alyanak, Toronto, Ontario), Teddy, byeman, Colorado Codemonkey, defective, ColForbin (Jim Blanford), FunkFish, Robert James (Winnipeg, Canada)
- Outline for a Simple Darkserver and/or Darknet - Creating underground encrypted data networks which can't be monitored, by p4nt05
- Google 411 Skype Hack - How to use Google 411 to route a Skype call without using your SkypeOut minutes, by The Skog
- Hacking Autodialer Telephone Access Systems - Overview of Mircom remotely programmable telephone access system and the potential to get a dial tone out, by Wrangler
- Leaked Document Department - Funny IRS job aid for "Using the Revolving Door."
- Transmissions - Overview of the Google Street View Wi-Fi data collection scandal and how to prevent this, by Dragorn
- Written in Spam - Nine whimsical poems written using only words found in actual spam emails, by t0sspint (Sean Hausauer, Buffalo, New York, Twitter)
- Roll-Your-Own Automated System Restore Discs - Homebrew data restoration disk using Partimage Is Not Ghost (PING) bootable Linux CD, by ternarybit
- Grazing Voicemail Passwords - Overview of common voicemail passwords and tips on guessing them by using a collection of real-world passwords, by Non-Sequential
- Private Key Exchange Using Quantum Physics - Overview of the BB84 protocol for quantum key distribution, by Jared DeWitt (Salt Lake City, Utah, Email, Phone: 801-683-9587)
- How to Overwrite JUNOS Proprietary Code - Overwriting locked code and scripts on a Juniper M120 device using a null mount trick, by Anonymous
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Dear Hacker - an entire book printed in italics!
- Cover (Cover Info)
- Cover Inside Asian Payphones
- Malaysia Seen in downtown Kuala Lumpur, this polka dotted phone booth is a rather common sight for this particular brand of phone. We have no info on its square neighbor. Photo by Nathan Linley
- Malaysia Found at the commuter train station in Kajang, here is a phone that has clearly seen far too much sun and advertising. Photo by Nathan Linley
- Singapore This phone was discovered at one of those open air food centers known as "hawker centres." Multicoin and multilingual, there doesn't seem to be much this phone can't do, except take cards. Photo by Stylie
- Brunei Spotted in the Tasek Merimbun Heritage Park in the Tutong district. Not really what we'd call "pay" phones but these days you can apparently just stick a desk phone in a payphone kiosk and get away with it. Photo by Steve McCain
- Back Inside Mostly Asian Payphones
- Thailand #1 Definitely one of the more alien-looking setups we've seen and the Thai alphabet on the booth only adds to that feel. Found in Chiang Mai near a Buddhist temple, we're not entirely sure if the color scheme on the phone is just a really neat design or the remnants of something truly disgusting that got all over it. Photo by Martin
- Thailand #2 "
- South Korea It's hard to disagree with the sentiment expressed above this model when you realize that this phone is prepared to cheerily take on any task under the sun. Discovered at the Seoul airport, it's ready to surf the net for either coins or cards. Photo by John Hilger
- United States Oh how the mighty have fallen. In this section's only non-Asian contribution, we see the continued disrespect that payphones and former payphone kiosks are treated with. Spotted at the Tri-Cities Regional Airport in Blountville, Tennessee, it's apparently become necessary to remind people not to throw their trash into the space where the phone once was. Photo by Peter Knauer
- Back Cover Photo #1 This actually is far from the first speedometer picture we've gotten, but it's one of the coolest looking ones. It comes from a 2010 Ford Fusion belonging to timi2shoes who set an alarm on his phone to keep from missing the magical event. He had to pull off of a busy street and drive into an alleyway for a while in order to capture the 2600 moment. Now that's dedication.
- Back Cover Photo #2 This is one of the better looking "2600 lairs" that we've seen lately. Spotted in Vancouver, Washington by MotoFox, this building has since had their huge red numbers removed. Apparently, too many readers were showing up to get autographs.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 27!
$2600 Magazine - Volume 27, Number 3 (Autumn 2010)
- Conflict in the Hacker World - Editorial
- Read All About It! Online Security and Paid Newspaper Content - How to save JPEGs and access the "paid" section of back issues for London Times online newspaper articles, by Yan Tan Tethera
- Old-School Hacking - Story of some "middle school" hacking to get a teacher's HP3000 account and manipulating high scores in C64 games, by Kim Moser (New York, New York, Email)
- Hackin' it Old-School by Kim Moser
- How I Learned to Stop Worrying and Spam the Scammers - Reverse spamming a website by automatically creating fake username/password data, by Wavesonics (Adam W. Brown, Email)
- Telecom Informer - Overview of the China's cellular phone system and thier payment system, by The Prophet
- Editing the Brand Image: Forgeries, Branding, and Network Theory in the Digital Playground - Overview of fakes and forgeries in a digital world and how to prevent this with digital signatures and other tricks to preserve your marketing image, by anonymous
- Spam Simplified - Overview of spam email and how it is created, spread, and how to prevent it, by Bill (a.k.a. fsu_tkd90, William F. Whelan)
- Hacking Out - Several tips on how to bypass Internet content filtering and restricted Internet access by using Google's cache, proxies, DNS manipulation, etc., by R. Toby Richards
- Man-in-the-Middle Attack - Good overview of a "man-in-the-middle" attack to strip SSL data using tools provided in BackTrack/Kali (sslstrip, arpspoof, etc.), by Oddacon T. Ripper (Dietrich Miller, Pacific, Missouri)
- Hacker Perspective - by Barrett Dylan Brown (Email #1, Email #2, MySpace, Facebook)
- The Circle of HOPE: Barrett Brown Onstage Interview
- HOPE X: Barrett Brown and Anonymous: Persecution of Information Activists
- IPv6 Connection Hijacking and Scanning - How to use radvd to redirect IPv6 traffic to an arbitrary location and tips to perform practical IPv6 network scans, by Farhan Al-Murādabādī
- Gmail and SMS Gateway Fun - Simple shell script for a SMS-to-emaile bomber using a Google Maill gateway, by Digicon
- Code: smsbomber.sh
- Moving from Robotics to Artificial Intelligence - General overview of the history of artificial intelligence and how it relates to modern robotics, by MiracleMax
- Letters - Material for the Next Book
- Ideas - Anthony (Biloxi, MO), Dufu, John Trotter, Marshal820 (California)
- Feedback - Ross McCauley (McAlester, OK), Quaffi0, Joe Domenici (Austin, TX), Captain Cautious, Walter, CJ Lorenz, Macavity, Pete, Citizenwarrior
- Continuation - D1vr0c, Mystrix, Adam, Jean
- Observations - Titeotwawki, Ralf B., Mary, Justin, member popcornpanic, monakey, JapoCapo
- Concerns - Ech0, The Doctor, Botless (Oceanside, CA)
- Inquiries - Alexander, brian heagney, a ahmed, Unr3a1, Jane Doe, Pete, Shadowfox, Dan, william, Bob (London, England), Bradley, HowWeird
- 2600 to the Rescue - ScatteredFrog, AKH
- Seven Things Hackers Did Right - Some of the concepts the 1995 movie Hackers appeared to get right, by glutton
- Life Without Walls: Circumventing Your Home Security System - Story of bypassing a window alarm system using an old hard drive magnet, by Sacha Moufarrege
- Transmissions - iPhone jailbreaking vulnerability and The Next HOPE speech overview, by Dragorn
- How to Turn Local Admin into Domain Admin - Batch file to obtain domain admin privileges under Windows-based network servers, by David Dunn
- Panasonic Phreaking in the New Age - Panasonic voice mail box/PBX overview and clever trick using the # key to obtain a dial tone to an outside line, by Anthony
- Hacking and Securing the Tandberg C20 - Security concerns (no root password!) of the Tandberg C20 high-def video conferencing package, by xorcist (Niki)
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: WikiLeaks, falsely claiming civilians were intentionally killed when the raw, unedited video evidence proves otherwise.
- Cover (Cover Info)
- Cover Inside Unusual Payphones
- Japan What's unusual about this payphone? Well, it's a bit weird to find a phone inside an actual cedar tree - or, at least, what's left of one. Apparently this sort of thing isn't a big deal on the island of Yakushima. Photo by Kevin Campbell
- United States Seen somewhere on the highway from Alaska to the border with Canada. Unusual in that it's rather hard to find payphones in American cities, let alone in the middle of nowhere. Photo by Greg Thompson
- United States O.K., three guesses as to what's unusual about this one, found at the Dallas Fort Worth Airport. Give up? It's really unusual for us to feature two American phones on the same page or even in the same issue. (If you thought it was unusual for there to be such a huge buildup to something that turned out not to even exist, that's actually quite common in the States.) Photo by William Ellis
- Spain This, too, is an unusual sight, seen in the city of Ronda. This abandoned payphone kiosk is right on top of a cliff. But, at least this non-phone doesn't have all sorts of signs advertising its non-presence, plus it fits in pretty well with the surroundings. We might even be able to convince ourselves that this is a monument to an ancient intelligent civilization, long since passed. Photo by Kim Moser
- Back Inside Payphones in Interesting Places
- Iran This phone relies on a wireless connection and can be found in the countryside and along the highway. Photo by bvdp
- Iran This somewhat older and scarier model was seen in a suburb of Tehran. A true fortress phone. Photo by bvdp
- United States Again?! Yes, an unprecedented third American picture in the same issue. This one is interesting because it's one of the last remaining phone booths in New York City. But this one isn't exactly in a place where tourists will come upon it: It was found in the horse stalls at the Belmont Park racetrack. Photo by Gregory Kline
- Kazakhstan This phone is inside the walled city of Baikonur, residential hub of the Baikonur Cosmodrome and heart of the Russian space world. Despite being in Kazakhstan, Baikonur is administered by the Russian government, and access is by invitation of the Russian Space Agency only. This box is on Abay Street, the main east-west drag in town. Photo by Isaac Wilson IV
- Back Cover Photo #1 We're slowly coming to the realization that "Hacker" is a real name in many places and has nothing to do with the actual hacking of computers. But "Hackmore?" That just sounds like a rallying cry to us. Spotted by Jeff Lacy in Sacramento County, California.
- Back Cover Photo #2 It's a toss-up as to which is funnier: a computer store whose address happens to have a "2600" in it or the 'personal data removal" line in the vicinity. Not that we do that sort of thing or approve of anyone's data getting deleted. But the mainstream might find themselves subconsciously avoiding this place. Found by Damon Melendez in Pittsburgh.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 27!
$2600 Magazine - Volume 27, Number 4 (Winter 2010-2011)
- Changing Landscapes - Editorial
- Bash Bash Bash! - Overview of the Bash shell, using some of the built-in commands, and few example scripts, by Douglas Berdeaux
- How to Cheat at Foursquare - Tweaking the Foursquarefox plugin to "fake" Foursquare check-ins, by therippa
- The (Obvious?) Dangers of Free Wi-Fi - Tips to protect yourself (and your connection) while using a "free" Wi-Fi network, and tips on how to "man-in-the-middle" an unsuspecting network user using Ettercap, by Azazel
- The Buck Stops Here: Inside AT&T's Tier 2 Tech Support - Story from a person who works in AT&T's "Tier 2" technical support, by kliq
- Telecom Informer - Overview of Japanese landline and cellular phone services, by The Prophet
- Various Vulnerabilities in the UPS Shipping System - Potential bugs and tracking number vulnerabilities in the UPS shipping system, by Dufu
- Ode to the United States Postal Service - Tips and tricks to use "General Delivery" for you mailing address and how to maintain some privacy, by Barrett D. Brown
- Android, You Broke My Heart - Bugs with the Google Mail verification and how to get private information by forcing a reset in Android 1.6 (and lower) phones, by Ry0ki
- Corporate Reconnaissance for the Anti-Social - Search tips and other techniques for obtaining private information on employees at your target business, by Azazel
- Hacker Perspective - by John Harrington (W5EME, Beaumont, Texas)
- Anti-Satellite (ASAT) System for Dumbasses - Part One - How to protect yourself from overhead surveillance satellites and ideas to jam their sensors, by spynuclear@yahoo.com
- The Trouble with the "Digital" Music Industry - Problems with "digital-only" music and a potential bug in Amazon's checkout system, by ScatteredFrog (Sean, "Dauber," Chicago, Illinois)
- Invisible ASCII: A Poor Person's Steganography - "Hiding" data in Windows by using non-standard (Alt + <number>) ASCII codes, by Strawberry Akhenaten (Alamosa, Colorado)
- Letters - DISCUSSION TIME
- Query - mohsen
- Spreading the Word - Maynard, j, George (George Hayes, Sugar Land, TX), Pro Virus (Simon Levesque), Prashant (India)
- Coincidences? - The Asseater, Drykath, Micheal
- Exciting Offers - cl0ckw0rk, David
- Another Query or Two - mohsen, Ben
- Policy - Handle Deleted, K, Jody, Nick Petty (iPen: Hacking with the iDevice), Steve, Bobby
- Critique - saizai (Sai Emrys), anonymous, The Piano Guy
- Still More Grammar - Robert Lynch, RWM
- Infiltration - Jeff, Barrett D. Brown
- Fighting the Power - Samuel, drlecter, Brian in Leawood
- Yet Another Couple of Queries - mohsen, Denis Gladysh
- Addendum - ternarybit, Jason
- Advice Sought - Salih, John, Cm0nster, nate
- Challenges - BBWolf, ghost
- The Last of the Queries - Feathered Serpent, Wes, Jack, m, mohsen
- EMR Interception and the Future of Computer Hacking - EM/RF interception: what it is, how it works, and what it means for the future of computer use and hacking, and an overview of van Eck-style electromagnetic radiation computer/CRT surveillance techniques, by Triscal Islington (Canada)
- The Joy of IPv6 - Why we should all start moving to IPv6 and some potential security problems to overcome, by Sam Bowne
- Dormitory Phishing - Story of creating a fake "login" screen to track a Facebook stalker, by anonymous
- How to Find Information on People Using the Internet - Different ideas and websites to search for real names and email addresses on the Internet, by DarX (Darxius)
- Transmissions - How the U.S. government is seizing, censoring, or shutting down so-called "pirate" websites, by Dragorn
- Phun with FOIA - Information you need to fill out a Freedom of Information Act (FOIA) request, by BY3M@N
- iBAHN Hotel Site Kiosks and How to Pwn One - How to gain disk access and free Internet from a iBAHN Internet kiosk at some hotels, by Sandwich
- RAM Dumping - Dumping the contents of your computer RAM under Windows with Win32dd and how to search through it for any goodies like passwords, by Metalx1000
- Win32dd Windows kernel-land physical memory acquisition.
- Win32dd: Challenges of Windows Physical Memory Acquisition and Exploitation by Matthieu Suiche (1.1M PDF)
- Win32dd - Memory Imaging
- Who's Got Your Vote? - Potential voting vulnerability which when you add a person's name to a petition it could potentially change their actual voting address, by windpunk
- Vulnerabilities in Quantum Computers - Defeating quantum-based computer security by using a man-in-the-middle attack by someone who doesn't understand quantum cryptography, by Purkey
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: The move to digital publishing and it's potential effects on the hacking community.
- Cover (Cover Info)
- Cover Inside Payphones of Foreign Lands
- Cuba? United States? We honestly don't know. It's that strange bit of reality where the USA somehow has a military base and infamous prison on the land of one of its enemies. And yes, they have payphones there. From the looks of them, they're a lot more American than Cuban. These phones are located in front of the Navy Exchange (the Navy's version of Walmart). Photo by mavrik72
- Cuba? United States? These phones are in front of a furniture store currently undergoing renovations. We're told the phones will be back. Photo by mavrik72
- Hungary Found in Budapest, this old style booth is operated by Magyar Telekom (a subsidiary of Germany's Deutsche Telekom, hence the trademark pink handset) and also serves as an ad for a local cafe. Photo by Erwin Goslawski
- South Africa In Pretoria, this is a fairly common sight. The payphone operator is a human. You pay them and you get to use the phone for a while. The system uses some sort of VoIP over 3G. Photo by Breto
- Back Inside Payphones with Distractions
- China Seen in Changsha, the capital of Hunan province. This is where Mao Zedong was supposedly converted to Communism. If you look carefully, you should be able to see his statue in the distance. Photo by Tony Anastasio
- United States Found in a place called Volcano, California, this phone, like the previous one, also lies in the shadow of a national hero. Superman's plea reads: "Please do not vandalize this phone booth. I have no place else to change clothes." Photo by Scott Webb
- England This phone is said to still exist in The George Tavern in East London. The fact that God himself may be trying to get through is overshadowed by the fact that this is actually a true rotary-dial phone. Photo by Sam
- United States Seen in New Paltz, New York, it's not really fair to call the message here a distraction to a payphone, since in fact there is no payphone. But the message is one that we must always heed, even if the phone companies won't. Photo by Rocco Rizzo
- Back Cover Photo #1 You know it's your lucky day when a speeding locomotive heading in your direction has those magic numbers on it. Spotted in Wisconsin by Mike Yuhas, who was definitely in the right place at the right time.
- Back Cover Photo #2 This is from a hotel in Deerfield Beach, Florida, as discovered by ateam. There's another sign in the same complex that says "Guest Parking," but somehow this one tends to draw more of a crowd, who perhaps think this is where the Club-Mate shipment comes in.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 27!
$2600 Magazine - Volume 28, Number 1 (Spring 2011)
- A World Spinning - Editorial
- Password (In)security? - Article about the current state of password security using some real-world statistics and examples, by Sheep Slapper (Stephen Lee Fischer, Moscow, Idaho)
- Password Bypassing and Clearing - Steps and tools for bypassing password security on a computer you have physical access to by using the various Linux Live CD distributions, by Metalx1000
- How Good is Geolocation? - Overview of geolocation services, how accurate they are, and how spoof your location, by Geo Spoof
- Telecom Informer - Local Number Portability (LNP), NPAC, and how the routing between offices takes place, by The Prophet
- Why I Like E-Books - Some of the advantages (and disadvantages) to using e-books, including anonymity and defeating various means of censorship, by Oakcool (Mateus Carvalho, Eugene, Oregon, Twitter)
- What is a Hacker? - Looking into the mindset of a hacker, by Lifeguard
- Who is Anonymous?; or, How to Troll the Media for Fun and Profit - Brief overview of how the Anonymous hacking group coordinates their attacks, raids, and media releases, by Anonymous
- How to Accept Payments Anonymously - A Digital Currency Guide - Overview on using the various "digital currencies" and how to protect your monetary transactions while remaining fairly anonymous, by Max Vendor
- How to Find Out What the Government Knows About You - How to send in a Freedom of Information Act (FOIA) request to see what kind of information various government agencies have on you, by Variable Rush
- Bypassing JavaScript Timers; or, How I Learned to Stop Waiting and Love the Variable - How to circumvent those JavaScript timers on websites like RapidShare by using Opera to locally edit and re-run the JavaScript, by K3ntucky
- Remote Login Made Easy - Using services like LogMeIn and Dropbox to remotely access your computer, by GantMan
- Two Party Covert Communication Over MSN Messenger System Using Emoticons - Using "smiley face" ASCII emoticons to represent binary data in order to pass small secret messages, by Armando Pantoja
- Virtual Anti-Forensics - How to protect yourself against computer forensic examinations by running BackTrack in a virtual memory partition under a virtual machine, by Israel
- Hacker Perspective - by Katherine Cook (Fort Wayne, Indiana)
- Secrets of the Spider - Overview of a Perl web spider developed by the author to search for only certain data you want, by Triad@Efnet
- Code: spider.pl
- The Lessons Learned on a Training Site - Story of the author finding various security holes in the VBScript on their company's training website, by Metalx1000
- Writing Bots for Modern Websites - Creating a bot using the Watir Ruby library to manipulate JavaScript on a website, by Michael Morin
- Letters - Non-Verbiage
- Gratitude - r0Wn1, gui, WTL
- Fun Facts - InternetToughGuy, Nathan, Lucky225, Evan K., Justin & Audrey (Cincinnati, OH)
- Letters from Prison - Peter, Ghost Exodus, W, Mark
- Addendum - therippa
- Feedback - Adam, Estragon, MotoFox, Gordy, chapo, Zach, Pete
- Queries - Top Sec, Maggie, Chris, p-lo, Andrew, Graham, Caboose, NABster, An Inquisitive Youth, Deviant Ollam, Joshua, Matthew, Haggis (Brisbane, Australia), psuedofed, Richard, HW, Jeffrey LaChord
- On WikiLeaks - Maybeso, Maybeso, Lucas, Anonymous, Stephen, B. Franklin
- Wanted - hidn shadows, Worried Mother
- Discoveries - The Cisco Kid, Anonymous
- Grammar Words - kyle w, drlecter, RWM, Jane Doe, Anonymous
- Where Have All Our Secrets Gone? - How privacy in our world today is often compromised by ourselves, by aestetix (meman2000, Baltimore, Maryland, Email #2, Twitter, LiveJournal, Reddit)
- LDAP Directory Servers: TMI! - Searching the change logs of a Lightweight Directory Access Protocol (LDAP) server for cleartext passwords, by Leviathan
- Computers: With and Without - How some hypothetical situations would be presented if there were no computers available in the world, by DGM
- Automatic Usage of Free Wi-Fi - Bash script to randomize your MAC address and auto-connect to open Wi-Fi systems, by Dr. Rolf Freitag (Ismaning/Nuremberg, Germany, Email, DOB: 12/12/1968)
- Code: open-wifi-auto-connect.sh Version in the article.
- Code: open-wifi-auto-connect_ping.sh
- Code: freewifi_autoconnect.sh
- Code: freewifi_autoconnect_old.sh
- Transmissions - Overview of what is required to sniff Bluetooth traffic and some low-cost hardware platforms to help accomplish this, by Dragorn
- Coding Bots and Hacking WordPress - A very in-depth look at PHP and JavaScript code which automatically loads web pages, submits forms, and does other potentially sinister stuff, while looking like the input is from a "human," by Micah Lee (San Francisco, California, Twitter, Blog, Website, Radical Designs, Email)
- Code: get-2600-tweet.php
- Code: add-wordpress.php
- Code: hack.js
- Abusing the Cloud - Using someone else's account with just their cell phone number on The Cloud public Wi-Fi systems, by riemann
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Starting more (((Kinetic Military Actions))) in the Middle East, but now it's O.K. because Obama is the president.
- Cover (Cover Info)
- Cover Inside European Payphones
- Spain Found in the winding streets of the ancient city of Granada in the southern part of the country. Takes both coins and cards. Photo by Howard Feldman
- Italy Seen in the small town of Riomaggiore, in the Cinque Terre region of the north. While this model doesn't take coins, there are others like it that do. Photo by Howard Feldman
- Belgium #1 A study of two standard payphones with very different upbringings in the city of Brussels. With this kind of cultural clash going on, is it any wonder the country is being torn asunder? Photo by Sean K
- Belgium #2 "
- Back Inside International Payphones
- Japan Discovered in Hiroshima, about a block away from the Atomic Bomb Dome and only 30 meters from the actual hypocenter of the A-bomb dropped on the city. Photo by F.K. Martens
- Egypt Not really in the center of all of the recent mayhem, this phone nonetheless could have been used to spread the word from the relatively tourist-friendly area of Luxor. Photo by Andrew Song
- Malaysia Seen in the city of Miri on the island of Borneo. Only coins are accepted here but they won't do you a whole lot of good without the handset. Photo by Jimmy Winslow
- Ghana This phone was found in Abetifi-Kwahu. Almost every last person in the country uses cell phone service from either TIGO, Vodafone, or MTN. AT&T has a presence, but it is very limited. Photo by Dufu
- Back The Back Cover Photos
- Back Cover Photo #1 Thanks to Jim Osborn for letting us know about "The 2600 Building," one of the most desirable properties in Palm Beach, Florida. As Jim suggests, this might be a good place for hackers to retire, provided the bandwidth was sufficient.
- Back Cover Photo #2 A building of an entirely different nature was found by Kit Wong in Sacramento, California. We might have been able to say that this was the center of all of our financial dealings if the address only had "capital" rather than "capitol" in it.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 28!
$2600 Magazine - Volume 28, Number 2 (Summer 2011)
- Progress Report - Editorial
- Dealing with Credit Card Companies - Information you should have on hand should you need to cancel or obtain info from a credit card company in an emergency situation, by The Piano Guy (Gary Rimar)
- ASAT for Dumbasses: Part Two - Detecting and Tracking Stealth Satellites - Beginning project of mounting a CCD camera to a telescope to monitor satellites, by spynuclear@yahoo.com
- Anti-Satellite (ASAT) System for Dumbasses - Part One
- Pen-Testing from a Mile Away - Modifying an old DirecTV satellite dish into a high-gain 2.4 GHz Wi-Fi antenna, by Asim Zaman
- Pen-Testing from a Mile Away Original
- Securing Online Voting - Overview of what some website admins can do to prevent people from "cheating" in online contests, polls, or voting, by kr
- Telecom Informer - Trip to the DMZ in South Korea and information on the Korean phone systems, by The Prophet
- Mobile Hacking with Android - Takes a look at the origins of Android, and a basic rundown on the Internal structure of the OS. It then moves on to some choice software selections and details a real-world "man-in-the-middle" attack using a rooted Android smartphone, by MS3FGX
- Mobile Hacking with Android Original
- Shark for Root v1.0.2
- How I Escaped Google (And Other Web-Based Services) - How to prevent your personal data from showing up on the Internet - or being lost - by using your own hosting and storage tools, by mrcaffeine
- Add a User with Root Privileges Non-Interactively - Steps for adding a UID=0 (root privileges) account to your system without an interactive TTY or effecting the system's root account, by Pipefish
- Simple RSA Encryption or Human Calculable Encryption - Design a public & private key encryption system using only simple math and really small prime numbers, by b3ard
- Booze, Nosiness, and City Terminals - Hacking public Internet terminals in Germany, by th3linquist (Blog, Twitter, Germany)
- Hacker Perspective - by KC
- How to Protect Your Car from Radio Jammers - How to be aware of people using radio frequency jammers to prevent wireless car alarms or door locks from properly activating, by Beyond
- Air Intercepted Messaging: A Revisit of POCSAG and Radio Privacy Issues - Nice article on the art of pager interception and some of the software used, by Malf0rm3dx (Chris) & Megalos
- Radio Scanner Modifications and Information
- Pager Programming, Monitoring, and Applications
- Beginners Guide to POCSAG Pager Decoding
- PDW Paging Decoder Software
- Auditing the MiFi 2200 - Obtaining the stock encryption key on a Virgin Mobile MiFi 2200 Hotspot, by pnorton (Paul Norton)
- Letters - Voice of the People
- Reaching Out - D351
- New Stuff - Shadow, Adam
- Meetings - Sherlock Holmes, Vadym, Jesse, Peter (Netherlands), Paul, Icarus, jason (West Virginia)
- Clarifications - DR, carl, zarck, j, MadJo
- Electronic Publishing - The Atomic Ass, Michael, Thinkican, Brett, Jeremy, William
- Curiosity - Sasa, Richard
- Observations - drlecter, William, AnyPerson, Dan, Petar, Jeff, e-Z-e-kiel
- Worries - Chuck, Chuck
- Experiences - SanDogWeps, orPHan, nrKist, Ian, Dead Rabbit, Jimmy, Coyote, Twenty Six Hundred
- Questions - Bryan, false, Anonymous, DMUX, m m, Lane, eb, MyOwnMinerva, MyOwnMinerva, MyOwnMinerva, fives, Eric, Frank
- WikiLeaks - Terry, M3d1c473d, SysKoll, Polaris75
- Hiding the Hacker Instinct; or, No Oppressor Strategy Can Be More Successful Than Training the Oppressed to Oppress Himself/Herself - Story of bypassing a motion-activated locked door at his office and not wanting anyone to find out, by Phineas Phreak
- Starting a Path to Modern Database Privacy - Detailed steps on how to opt-out of some of the various Internet databases, by Barrett D. Brown
- Transmissions - Instances of real-world "cyber wars," by Dragorn
- A Brief Guide to Black Edition XP - Overview of Black Edition XP, a stripped down "hacker" version of Windows XP, by Oddacon T. Ripper
- Windows XP SP3 Black Edition 2015-09-12 (Product Key: M6TF9-8XQ2M-YQK9F-7TBB2-XGG88)
- The Many Uses of SSH Tunnels - Example of tunneling Firefox (HTTP) data over a remote SSH server and using it to bypass content blocking, by twopointfour@riseup.net (Micah Lee)
- Senatorial Courtesy Plates - An Inside Look - Overview of government vehicle license plates in New Jersey and what they mean, by Dufu
- Fishing with Squid - Setting up a Squid server with the intention of blocking advertising on iPad applications, by Suborbital
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Why you should purchase the electronic versions of $2600 Magazine and not download them here for free. Heh...
- Cover (Cover Info)
- Cover Inside Foreign Payphones
- Albania Seen in the capital city of Tirana, this is the standard model that takes only cards. And yes, "Shqiptar" is an ethonym for the Albanian language. But you knew that. Photo by Kyle Drosdick
- Israel This bright orange and black model can be found in Jerusalem and does not take coins. We firmly believe that colorful payphones brighten everyone's day. Photo by FA
- Iran #1 Both of these very different models are used in the streets of Tehran. One is old and takes coins, one is newer and takes cards. But they each exist under the exact same style of canopy. There's probably a lesson in here somewhere. Photo by Venture37
- Iran #2 "
- Back Inside Disrespect & Respect
- United States It's like some sort of creepy ghost story. There once were six happy payphones here. Six! All that remains now are empty shells. (And all of the people seem to have vanished, too.) Seen in Nantucket, Massachusetts. Photo by Jules
- United States Talk about no respect. Here we have a Home Depot in Reston, Virginia that apparently thinks an empty shelf serves more of a purpose than an actual functioning payphone. We fear they may be right. Photo by Melissa Jonas
- Canada Sure, maybe nobody's using the damn thing. But at least it looks attractive and artistic. So the next time you see a lonely payphone, think about making it look pretty. This one was found in Vancouver, British Columbia. Photo by Lani Johnson
- Taiwan Someone always has to go a bit overboard, don't they? This phone, seen at TPE Airport's international terminal in Taipei, is definitely too pretty for anyone to take seriously. The Hello Kitty craze has really gotten out of hand. Photo by Henrik
- Back The Back Cover Photos
- Back Cover Photo #1 This auto collision shop, discovered by KC7EPH in Seattle, is not our latest business venture. But they did manage to frame the 2600 in an almost perfect position for a future cover.
- Back Cover Photo #2 Yes, it's another 2600 building, this one found by Jules in Lighthouse Point, Florida. We don't know about having the solution to the national debt problem, but we do know this building is for sale and would make a dandy hacker space.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 28!
$2600 Magazine - Volume 28, Number 3 (Autumn 2011)
- Awakenings - Editorial
- Introduction to ChromeOS - General overview of Google's ChromeOS, the CR-48 hardware, and the aspect of moving applications to a "cloud," by MS3FGX
- Introduction to ChromeOS Original
- Bypassing Shell Restrictions - Tricks for breaking out of a restrictive shell (or at least viewing files) on a Dell Remote Access Controller, by Malvineous (Adam Nielsen, Brisbane, Australia)
- Phishing on an iDevice - How to turn your iPhone into a trusted website to use for "phishing" exploits, sorta like the Wi-Fi Pineapple, by Jared DeWitt
- Code: lighttpd.conf
- Code: error.php
- Code: pwn.sh
- Telecom Informer - Difference in Caller ID delivery in China and how it can be spoofed or unreliable in all countries, by The Prophet
- Network Anonymity Through "MAC Swapping" - A very detailed look at how maintain relative anonymity on a network by hiding or "spoofing" your hardware MAC address, by A Sayler
- Both Sides of the Story - A few tips on what to do when in police custody or during a police interview (remain silent!), by Poacher
- Video Game Hacking - Overview of some of the hardware and software tricks used to "hack" video games, by Moral Grey Area Cat
- Hacking Alt Detection in Second Life - How to bypass zF RedZone's "alternate account" detection in Second Life using a simple cipher, by Johnny Fusion =11811= (L. Christopher Bird, Twitter, Bluesky, Old Website)
- Hacker Perspective - by Bruce Sutherland (zer043x, Melbourne Beach, Florida)
- How to Spoof Another User in MindAlign - How to "spoof" being another user on the MindAlign chat system, by Terrible Doe (U.K.)
- Access Control: A Fancy Facade - Overview of "access control" techniques (automatic door locks, card readers, etc.) and some simple tricks which can be used to bypass them, by P9a3
- GoDaddy Shared Hosting Review - Cross-site scripting vulnerabilities and other tricks to play with GoDaddy's shell access, by General Disarray
- Letters - Utterances
- Writing for Us - Zook, Josiah, Juan, Ben, MS3FGX, Brandon
- More on Meetings - Alex K, Eric
- Information - DA, Phil, Owen, lg0p89, Kitty
- Corporations - Mark, Jeremy N., Kagehi.K
- Digital 2600 - Jeremy, Ld00d, Christopher, Tim, Saskman, Captain V. Cautious
- Projects - Particle Bored, jag, treesurg
- Inquiries - RON, Squeeling Sheep, Kate, Darren M., Eric, James, D., kyle
- Desperation - Brenda, Stacey
- Random Thoughts - The Girl in the Corner, r0Wn1, J.B., Porky, Bpa, Case, nachash, E.T.A.G E.
- Retorts - CF 905, Variable Rush
- Still More on WikiLeaks - Name and Location Withheld by Request
- Logging and Analysis with Your GPS-Enabled Phone - Using the GPS data recorded on a HP webOS phone, by flippy
- Cellphone, Keys, Wallet? Check! - Story of someone who had their cell phone stolen and the runaround T-Mobile gave them, by Josiah McGurty (Springfield, MO)
- Mobile Hacking: Really - Installing Laika Linux on an Android phone to give access to the various Linux command-line security/network tools, by papill0n
- Transmissions - How computer security still hasn't really improved much over the years, by Dragorn
- Asterisk, The Gatekeeper - A little trick to use Asterisk to open a gate when a specific Caller ID transmission is received, by MasterChen
- Wear a White Hat - Discussing some of the recent high-profile "hacks" and how they may poorly reflect on the hacker community, by Sam Bowne
- How I Got Firefox to Accept the TEL Tag for Phone Calls - How to get Firefox to interpret a tel: tag to bring up Skype when a link is clicked on, by The Cheshire Catalyst
- Fiction: Kill Switch - Fictional story about how Internet censorship may come about and ways hackers could bypass those restrictions, by Leviathan
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: People who whine about censorship, but then run around trying to shut down websites and forums they don't agree with.
- Cover (Cover Info)
- Cover Inside European Payphones
- Denmark #1 In Copenhagen, there is a choice between blood-stained and generic models of the basic payphone. Neither appears to be overly popular at the moment. Photo by Jason Barna
- Denmark #2 "
- Luxembourg Seen in the town of Manternach and operated by Ascom of Switzerland. Photo by Alex Hamling
- France Found in a bathroom area in Paris, which is probably how this old-style payphone has evaded replacement for so long. Note that the coin slots still ask for French francs. Photo by Keith Hopkin
- Back Inside Retro Payphones of the USA
- Hackensack Ruins of an ancient payphone civilization which once thrived in Hackensack, New Jersey. The demise of the payphone has been a boon to the flyer community, who now have sheltered spots for their advertisements. Photo by Marcus Daniels
- Rotterdam Here we see that some of the electronics have been left behind but not enough to complete a call, hence the crossing out of the word "phone" from the display by a concerned citizen. Seen in Rotterdam, New York. Photo by Rich Gattie
- Los Angeles This is the first stage towards the remodeling of a working payphone into the more popular nonfunctioning design. The phone is still there but the earpiece has been smashed and the coin return removed. It won't be long now. Spotted in Los Angeles, California. Photo by Tyler Lawrence
- Washington, D.C. All that's left here is a wire. Ironically, this shell was seen in the basement level of the Watergate complex in Washington, D.C., which we all know is located at 2600 Virginia Avenue. Photo by kondspi
- Back The Back Cover Photos
- Back Cover Photo #1 Yeah, we know the image quality sucks, but when something like this appears in front of you, there isn't a whole lot of time to grab the best camera equipment. Thanks to Christopher Borders for spotting this in Kent Island, Maryland two summers ago and waiting until now to tell us about it!
- Back Cover Photo #2 How does one even find something like this? Who could have ever guessed that there was an official 2600 sofa for sale somewhere in the world? Thanks to Russ for stumbling upon this in Gaylord, Michigan. The perfect finishing touch for a local hackerspace, perhaps?
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 28!
$2600 Magazine - Volume 28, Number 4 (Winter 2011-2012)
- Movements - Editorial
- Google Tem-PHP-tations - Viewing PHP code by searching (site:*/*.php%3f*=*.php) for the .php~ backup files, by Craig Stephenson
- Code: get-php.sh
- Free Phone Numbers with Google Voice - How to setup and use Google Voice and a trick to use a "fake" account to obtain a phone number not traceable back to you, by bluelander
- Abuse Reports Still Work - If you're consistent, filing an abuse complaint to an ISP or upstream provider will still work, by raphidae @ EFNet
- MAC Spoofing Your Way to Free Internet - Change your MAC hardware address to one of a "paid" account and receive free wireless Internet access, by Ashes
- Hacking REFOG Keylogger - Overview of the REFOG Keylogger software, how to detect it (MPK.EXE), and where it stores its data, by Alex Nocenti (a.k.a. MrPockets)
- Telecom Informer - Telecommunications equipment on the island of Palau, by The Prophet
- Who is Anonymous? - Sensational overview of the "hackers" calling themselves "Anonymous," by aestetix
- Property Acquisition - For Free? - Story of a person who wanted to intentionally live "homeless" and a loophole to gain property by just paying the taxes or back taxes?!, by PTKitty
- Let's Feed the Phishes - Python code to send fake phone numbers, passwords, other data, etc. back to "phishing" sites, by goldcove
- Code: anti-phish.py
- Bypassing Universal Studio's MP3 Security the EZ Way - Using VLC to record audio streams and bypass Universal Studio's DRM restrictions, by Akurei
- Internal Denial-of-Service with Fork and Malloc Bombs - Combining a fork() bomb with a malloc() call to locally attack a host, by Israel
- Code: bomb.c
- Whitelisting with Gmail - Setting up two Google Mail accounts to provide a "white list" that only allows email from certain domains or email addresses, by R. Toby Richards
- Eye Spy - Example of using packet sniffers on an app like MobileChan to see how they potentially utilize private data in their operation, by Digicon
- How to Social Engineer Your Local Bank - Social engineering trick to obtain the "daily authentication code" often used by banks for telephone verifications, by Rob
- Laptop Repair, Customer Beware - Obtaining personal information and shipping information via the ASUS Repair Status Inquiry website by incrementing the RMA number, by bTrack3r2003
- Hacker Perspective - by Tiffany Strauchs-Rad (Professor Rad, Twitter)
- HOPE 2020: Keynote: Tiffany Rad
- DEFCON 31: Civil Cyber Defense
- DEFCON 19: SCADA & PLCs in Correctional Facilities
- DEFCON 17: Your Mind - Legal Status Rights
- DEFCON 17: Hello, My Name is hostname
- DEFCON 19: SCADA & PLCs in Correctional Facilities
- SOURCE Boston: PLC/SCADA Vulnerabilities in Correctional Facilities
- More Active Gamers Should Become Activist Hackers - Why there should be more video games with a political overtone, by Snugglepuff
- Simplex Locks: Illusion of Security - Version 2.0 - Massive security hole in Simplex locks in which a simple (but expensive) magnet can be used to open them, by Beyond
- Hacking is in the Blood - Two brothers challenge each other to a lock opening contest and the hacker instinct kicks in, by Ninja_of_Comp
- Support for Cable Providers? Why? - Discussion on why content providers are not really out to limit what people see, by Seeker7
- Pre-Texting-R-Us - "Pre-social engineering" tricks which can be used to steer the information you wish to gain, by lg0p89 (Michigan)
- Letters - General Assembly
- Opportunity - Galina Miklosic
- Still More on Meetings - ckrupp (Charleston, SC), Owen (Scotland), Marcel (Bangkok, Thailand), adam (United Kingdom), H1ghBr1d, Kenpo (Kentucky), Greg
- Postscripts - Louis (Canda), D1vr0c, DM, Lucas, Mystrix, D, Alan, Polaris75, Derf~!, Octo314, CASE
- Wondering - Josh, MS, Phil, Chris, DMUX, Brad, I, Alex K
- Stories - dr finesse, William Henry, Varbede
- Requests - Ray M., Andrew, R. Toby Richards, Lost in Cyberia
- Disclosure - Rev. Bermuda Jim O'Bedlam
- Struggles - "Phred", Particle Bored, Vinay, Tim, David, Byron Sonne (Brampton, Ontario)
- More Observations - D.S., Ld00d, Ray M., Kyle, Ray M., drlecter, Ashes, Ray M., Mangakid, Michael O'Cuir, E.T.A.G.E, Cyber Pinata, Josephus, CWTL
- DRM Issues - Leo, Rob
- Pirating the Caribbean - Setting up an AutoRun CD to look like a legitimate video which actually collects information on the target host and FTPs it back to you, by Rob
- Code: PLAY.au3
- Perfect Encryption - Old Style! - How to setup a "one-time pad" style of encryption using nothing but a pen, paper, and some simple math, by Cliff
- The Piracy Situation - Why the hacker community should be against piracy as it just brings about more laws and trouble, by R. Toby Richards
- Transmissions - Cellular phone tracking via Carrier IQ and the problems it can cause, by Dragorn
- Anonymity and the Internet in Canada - In this article we will take a brief look at what laws are in danger of being passed through the Canadian House of Commons, along with measures you can take as an individual to enhance your anonymous Internet experience, by Pat D.
- Elegant Password Generation with Oplop - Generating strong passwords with the Oplop password management system, by Joshua Dick
- Hacking the Winn-Dixie Survey - Decoding the data at the bottom of a Winn-Dixie receipt, by Tim K
- Fiction: Switch - Story of underground urban exploration, by Austin Lott
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: "Occupy Wall Street" which is funded by the same Marxist billionaires [i.e. (((Soros Family ✡)))] who fund Pacifica Radio, the Democrat party, and other loony causes Evil Corley and the One Percent engage in.
- Cover (Cover Info)
- Cover Inside Foreign Payphones
- Ecuador Seen in the small village of Puerto Ayora in the Galápagos Islands, this card-only phone is practically screaming for attention. Claro, incidentally, is part of Mexican phone company América Móvil. Photo by Howard Feldman
- Croatia Found in Karlovac, this phone is part of German giant Deutsche Telekom, as evidenced by the T-Com branding and the pink handset. All in all, this phone has a rather trippy aura to it. Cards only. Photo by Zafrik
- Israel This phone was discovered in the Old City of Jerusalem. Once again, it's a phone that only takes cards. Coins seem to be rapidly going out of fashion. Photo by Josh Dick
- France Found in the town of Porto-Vecchio on the island of Corsica, this France Telecom-operated payphone surprises no one by only accepting cards and making for a clean sweep on this page. Photo by Vincent
- Back Inside Payphones with Character
- Canary Islands This phone looks as if it could tell a story or two of some of the things it's seen. It's from an unusual place: Fuerteventura, one of the Canary Islands of Spain. It accepts cards and coins. Photo by Zawaideh
- United States Then you come across something like this, a payphone literally residing in a cornfield near Gap, Pennsylvania. It looks like it could easily get accidentally harvested one of these years. Photo by Paul LoSacco
- United States And this one was found in Detroit. Now be honest. Is this not exactly how you expected a payphone in Detroit to look? Photo by Anthony M. Bolek
- United States As long as we're poking fun at places, here's a pretty typical look for a Brooklyn payphone - dirty and colorful while possessing a rather interesting shape. Photo by Franco Medel
- Back The Back Cover Photos
- Back Cover Photo #1 If this isn't the ultimate portrayal of what one of our buildings might look like once we turn evil, we'd like to see what could possibly top it. No windows, surveillance everywhere, our name providing the only color in sight... We can dream. Thanks to bishun and Teri of Minneapolis for this discovery.
- Back Cover Photo #2 There's a bit of an odd story behind this one. Sure, we can hint that we've become part of the Independent Grocers Alliance, which is a great way of distributing Club-Mate. Nothing odd there. What's interesting is that a mere two days before we got this contribution from Kurth Bemis in the Hochelaga region of Montreal, we got the same submission from Teanose, who says he discovered it "while sitting in a parking lot late at night eating a Mickey D's double quarter pounder." What are the odds? Anyway, we preferred the day shot, so Kurth wins this one. That is, assuming they're not both the same person. Otherwise, we may have just started a feud.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 28!
$2600 Magazine - Volume 29, Number 1 (Spring 2012)
- Game Changing - Editorial
- Meet SOPA's Evil Twin, ACTA
- Obama Eyeing Internet ID for Americans
- Obama Administration Announces Massive Piracy Crackdown
- Obama Internet 'Kill Switch' Proposed
- A PHP Rootkit Case Study - Detailed technical analysis of a PHP rootkit installed on a university server, by StarckTruth
- Denial-of-Service 2.0 - Overview of the some of the newer Denial-of-Service techniques people are using and ways to prevent these attacks, by tcstool
- Spoofing MAC Addresses on Windows - How to change the hardware MAC address of a network device using REGEDIT under Windows, by Wananapaoa Uncle
- GroupMe: A Modern Approach to Social Engineering - Use Google Voice to create a fake GroupMe account to spy on a target's GroupMe account, by Jacob
- Telecom Informer - History of airplane in-flight phones, Wi-Fi, and other in-flight services, by The Prophet
- Curiosity Killed the Cat - Story of a person who almost go in trouble by checking his university's computers for XSS security holes, by Gregory Porter (Email)
- Stupid 9-Volt Tricks - Disassemble certain brands (Duracell or Energizer) of 9-volt batteries for a source of "AAAA"-size batteries, plus a good overview of battery capacity, by XlogicX
- So... I Bought a Chromebook - First look at the Acer Chromebook running Google's ChromeOS, by MS3FGX
- So... I Bought a Chromebook Original
- Hacking GIVEAWAY of the Day (GOTD) - How to use RegFromApp and URL Snooper to bypass the software installation restrictions used by GIVEAWAY of the Day, by Lone.Geek
- How to Avoid the Online Dating Scam - Story of a person who saved $50 by discovering a way to view profiles for free on online dating websites, by gosein
- RTF... TOS - Tips on why you should carefully read a company/website's Terms of Service to protect your rights, by Douglas Spink (Douglas Bryan LeConte-Spink, Email, Twitter, Old Website)
- Domain and Security - Why you should protect the domain transfer security of a website (and why many people don't), by Donald Carter
- Hacker Perspective - by ternarybit (Austin)
- Towards a Hacker Friendly Mobile World - Overview of cellular GSM modules from Enfora and Simcom and the possibility of making your own phone system, by Casandro
- LinuxLive... Save Me - Recovering from a hardware crash or performing a quick pen-test using the LinuxLive USB thumbdrive distribution, by D4vedw1n
- The Major Flaw of Pen-Testing - Real-world example of a how a professional pen-test team didn't perform some basic techniques and why educating people is the only real security solution, by Seeker7
- Free Music: The Quest for the MP3 - Story of one person's quest to save streaming audio files directly to their computer using Audacity, by DMUX
- Letters - CABLES
- Information - Estragon, Master Chen, Chris, Pete, micha, California Paralegal
- Challenges - MS3FGX, ~D, Lifetime Subscriber
- Meeting Stuff - Scott, Mia, Alex (Canada), Antonio, Christian (Clearwater, FL), Peoria 2600, Nicolas, Alexander (San Francisco), Joe
- Revelations - X, Rob T. Firefly, Tyler
- Inquires - LTJ, Question, Ramasee, Brab, Ben, Chris, Keith, mastahyeti, mastahyeti, Sean, Danny, pleasantdinnermusic, Steve
- Random Thoughts - Kabuki, enterthefuture99, Freak1993, Lost in Cybera, Sybille, Jeff, Little Brother, putrid, Conor
- The Crime of Knowledge - stephen, Stephanie
- Aggressive Prosecution - Benjamin Fix Nichols, Kevin Patterson, Ghost Exodus
- QR Fun - JWS, Justin G.
- An EMP Flash - It All Stops - The real possibility that an EMP attack could destroy anything electronic-based, by Paul Abramson
- GBPPR Electromagnetic Pulse Experiments - Part 1
- GBPPR Electromagnetic Pulse Experiments - Part 2
- GBPPR Electromagnetic Pulse Experiments - Part 3
- Learning from Stratfor: Extracting a Salt from an MD5 Hash - Overview of the process of analyzing the leaked Stratfor emails to determine the salt password used during the MD5 hash routine, by Acrobatic
- Transmissions - General overview of the idea "licensed" software coders produce more secure and stable products, by Dragorn
- Control4 and Home Automation - Potential security flaws in the Control4 home automation software which can be remotely exploited, by Awake31337
- Composer HE 3.3.1 User Guide
- Composer Pro 3.3.0.628622 Installation EXE
- Composer Pro 3.3.1.639440 Installation EXE
- Control4 Jailbreak
- Backdooring with Metasploit - Example of using Metasploit to install a backdoor program into a EXE program, by Oddacon T. Ripper
- My Grandpa's Books Never More! - How to save money by scanning and sharing your college textbooks, by Windpunk
- Insurgent Technology: In WikiLeaks' Wake - The bizarre, pseudo-intellectual ramblings from a person who doesn't realize that WikiLeaks is often used and abused by same globalists he claims to be "fighting," by Piyter Hurd
- The Pros and Cons of Courses - Story of a person who attended various computer security courses and whether they are worth the money or not, by Seeker7
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Overview of the out-of-control Internet censorship bills/act we've seen over the past year or so by the corrupt Obama regime.
- Cover (Cover Info)
- Cover Inside European Payphones
- Spain Nothing like a payphone that's part of some majestic scenery. This was seen in the plaza known as Puerta del Sol in Madrid near the monument to King Charles III. Photo by Champ Clark III
- Portugal Payphones just seem to get much better views in Europe. This one is outside of the Carmo Church ruins in Lisbon. Photo by Champ Clark III
- Russia This gem was found in Moscow Oblast near the Pionerskaya rail station. As a slap in the face to the ways of old, they didn't even consider putting the new payphone inside the old phone booth. The irony must be particularly biting in the winter. Photo by IW4
- Italy Discovered in the skiing community of Sauze d'Oulx, there's something rather eerie and alien about this pair, silently standing guard while crowds of people innocently go about their business and pay them no mind. One day... Photo by Oli Wright
- Back Inside Worldly Payphones
- Morocco Seen in Casablanca near the Olive Market. An old school phone that only takes coins. Photo by Eduardo
- Ascension Island If you find yourself using this payphone in Georgetown (population 450), odds are you're calling a really long distance. Located in the middle of the south Atlantic Ocean, this phone only accepts prepaid Cable & Wireless phone cards. Photo by Jim Hardisty
- Gambia We don't know a lot about this one as it came with no details whatsoever. But we do know that it's not that often you get to see a payphone from wherever this one happens to be. Photo by Aldous Snow
- Mexico Someone in Yal-ku Lagoon has a good sense of humor, although an actual tin can would have been more accurate. Photo by scott
- Back The Back Cover Photos
- Back Cover Photo #1 We get many photos of people's odometers that have just hit the magic number. Usually, they pull over and have a bit of a celebration when they take the picture. Not here. Travel'n Man apparently didn't even slow down when the historic moment occurred. Or maybe he did, which is even scarier.
- Back Cover Photo #2 For many people, the thought of hackers messing with plumbing might lead to many sleepless nights. Not so in Carlisle, Indiana where Chris Gibson spotted this crew of hackers who were working on the pipes at a local truck stop. We are indeed everywhere.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 29!
$2600 Magazine - Volume 29, Number 2 (Summer 2012)
- Scales of Inequality - Editorial
- Bluetooth Hunter's Guide - Straightforward guide that introduces the user to a number of Bluetooth scanning tools and methods, including Bluelog, by MS3FGX
- Bluetooth Hunter's Guide Original
- Security by Obscurity = Insecurity - Security flaws in today's locks and how hackers are often better at finding security holes than high-paid "security experts," by DocSlow
- Building a Cat-5 Cable Tap - Passive breakout cable for monitoring a Cat-5 Ethernet network, by Ashes
- NGFW - Not Grandpa's Firewall - Overview of the different types of network firewalls over the years and "next generation firewalls," by Daniel Ayoub (Email)
- Telecom Informer - Overview of the Iridium satellite phone system, by The Prophet
- A Counterpoint to "The Piracy Situation" - Rebuttal to R. Toby Richards' "The Piracy Situation" in Vol. 28, No. 4, by D351
- The Piracy Situation: The Devil's Advocate - Another rebuttal to R. Toby Richards' "The Piracy Situation," by Chip Ninja
- Why is Piracy Still Allowed? - How piracy happens all the time in everyday life and there is no real attempt to stop it, by jk31214 (John Kostiak?)
- The New Age of the Mind - Overview of upcoming biotech medical implants and dry-electrode EEG, by Merl
- Building the Better Brute-Force Algorithm - Tips and character combinations for heuristic brute-forcing modern passwords to reduce the wait, by James Penguin
- Hacker Perspective - Teague Newman (LinkedIn, Con Presentations)
- Firewall Your iPhone - Blocking traffic sent secretly to Apple (and other sites) via your iPhone, by Лоика
- Memoir of a Tech Writer: The Art of Leverage - Tips and techniques for technical writers to gain more exposure and understanding of their target readers, by ellG147
- Letters - Kindling
- Missing Issues - James, Enygma, Brainwaste (New York), BookeeNookeeLookee
- Questions - C. (Albuquerque, New Mexico), Bluz (Miami, FL), Dave, Phillip (Florida), Ulysse Carion, Legacy, Roel
- Defeating the System - Greg,
- On Piracy - Blue Ghost
- Advice - R. Toby Richards, Casandro, Mu
- Social Engineering - blanuxas
- A Little Feedback - John Lundin, M, Melissa, Feroz Salam, Scone, Valkuma Valkuma, Lifetime Subscriber
- More Kindle Fun - Immune, Erik Marshall
- Article Issues - Phil, Brian, Name Withheld, Michael, PTKitty
- Opportunity - Steven, RL, Accept Steven Leath's Invitation
- Observations - Mike (Cape Coral, FL), Brother Mouzone, Patrick, John Schmitt, Eric Botticelli, Mr. Glass, Ron, Lynn, Myq Morer, B
- Prison Update - Ghost Exodus
- Say It Ain't So Verizon - Reset the password on Verizon FiOS routers without authorization and without physical access, by Pipefish (Email)
- Hacking Climate Change With WeatherLink - How to extract weather information from the WeatherLink cloud service, by Cap'n Zilog (Dallas Hodgson, Email)
- Baofeng UV-3R: The Cheapest Dual-Band Ham Radio HT - Review of the Baofeng UV-3R dual-band (2m & 70 cm) amateur radio transceiver and how to perform out-of-band modifications, by l0cke
- Transmissions - Bugs in Google's updates to Android phones, by Dragorn
- Metaphasic Denial-of-Service Attacks - Performing an advanced denial-of-service attack by using multiple attack vectors, techniques, and exploits to bypass conventional blocking methods, by Everett Vinzatt
- Never Be ON TIME Again! - Simple wire jumper method to bypass the ON TIME vehicle ignition interrupt system, by OMK
- Fiction: Hacking the Naked Princess - Chapters 0x01 - 0x02 - First in a series of chapters from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser (Grand Rapids, Michigan)
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Richard O'Dwyer and his TVShack website being shutdown for linking to TV streaming websites. Note that Evil Corley supported and voted for the people who shut down his website!
- Cover (Cover Info)
- Cover Inside Global Payphones
- Russia It is strictly forbidden to take any pictures in, on, or around airports in the Russian Federation. Even the payphone looks angry. This one was found in the Yakutsk airport. Photo by Robert
- New Zealand Found in the Post Office Square of Wellington, this phone does something weird: when you pick it up, you hear the sounds of a crowded French cafe instead of a dial tone. But you can still dial. Photo by Breto
- India This "coin box telephone" was spotted in a forgotten corner of a New Delhi department store. Photo by Jack Jordan
- Morocco Probably one of the most secure payphones around. Spotted in Tangier, this one only takes coins. Photo by TProphet
- Back Inside More Global Payphones
- Iceland Found in Reykjavik on New Year's Eve, this is pretty much what you would expect a phone booth to look like up there at that time of year. Photo by Eric H. Jung
- India Found in the streets of Mysore, this is one of the few remaining coin-operated phones. Naturally, it seems a bit worse for wear. Photo by Howard Feldman
- Ukraine Seen in the city of Lviv, this is old-school in more ways than we can count. Photo by Corey Sherman
- Taiwan A typical card reading phone spotted in Taipei. Photo by Bruce Robin
- Back The Back Cover Photos
- Back Cover Photo #1 This is really something you don't see very often. It comes from a semi truck tank with multiple compartments, a baffle system, and an overfill safety system. Leighton Brooks tells us that it fills until you release a valve (so that dead people can't operate it), and it runs 60 gallons or so over the amount it was released at. So this was quite a coincidence on a compartment that was already partially full.
- Back Cover Photo #2 Back in the day when everyone was Red Boxing at payphones, some of the devices were a lot larger than most. This one was so large that it had a bathroom attachment. Found by Bill Gaines in Lake Grove, New York.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 29!
$2600 Magazine - Volume 29, Number 3 (Autumn 2012)
- The Eyes Have It - Editorial
- Technology at the Federal Bureau of Prisons - Overview of the TRULINCS system used by the BOP and some info on the Set Tel phone systems used, by [Name Withheld]
- Using Bluetooth Devices as an Additional Security Measure in Linux - Use BlueProximity to lockdown you computer when a BlueTooth link is broken, by Aaron Grothe (Omaha, Nebraska)
- Hackers Indispensable for Volunteer Groups - How hacker groups can help out and maintain the computer networks used by volunteer groups, by markb
- Telecom Informer - What it took to get OpenBTS running at ToorCamp, DEFCON and HOPE, by The Prophet
- The Quadcopter Crash Course - Overview of the hardware requirements it takes to get your own quadcopter up and running, by UAVman (a.k.a. DeathNinja McSex, Australia)
- Spear Phishing at a Bank - A Hard Lesson Learned - Story of how a targeted email looking like an anti-virus update tricked several bank employees, by lg0p89
- Restoring Honest Elections - Potential techniques to avoid election fraud - which for some reason doesn't mention having to show a valid picture ID, by Phredd
- Hackers in Space - The idea of using a homebrew array Low-Earth Orbit (LEO) satellites to bypass any Internet censorship, by MS3FGX
- Hacking Apple's System - Story of a person who spilled coffee on his keyboard and was able to get it replaced under warranty by claiming it as "broken," by Big Bird
- Fundamental Flaws in Online and Phone Ordering - Behind-the-scenes story of a person who works at a company which takes in phone and online orders and their lack of any real security, by C P
- Hacker Perspective - by Dimitri
- Beware the Cyber Weapons Industrial Complex - How the computer security industry closely mirrors the "military industrial complex" in their deception and the increase in offensive attack software, by Josephus Alexander
- XML Automated Gambling - Examining and modifying XML scripts to manipulate your online casino odds, by Andy Phillips
- Letters - FUNDAMENTAL INTERACTION
- Guidance - Alex, TheAlpacalypse, xnite, D
- Assorted Info - Rudolph, Alynn, James, 616 Boomer, Charles
- More on Meetings - Low-res, Ellie, Sean, dave (aka alphabot), Malcom
- Feedback - E85, Mickeyshaft, Phil, R. Toby Richards, D1vr0c, grey Otaku, rob, pipefish, Anthony, Fernando, edilla, prattel, Kn@cker7, Neil (SM), Casandro, Justian17, Rod,
- Words of Note - Wintermute, Jen Fone, Kathryn, M
- Just Asking - Matt, Eric, john, A. Wolf, dr. ciphertext, Alana, BB, Michael, John, Sean, Kyle, Wirechief, Az, A Abdi,
- Payphones - Charles, Recently Relegated to the Cowboy State
- Randomness - Chief Totus and his little brother, Owens deBrasso, zenlunatic (Maryland), Jon M., E.T.A.G.E., Kamonra, blanuxas, matt
- Stuxnet: An Analysis - Detailed analysis of the (((Stuxnet ✡))) virus used to attack Iran's Windows-based PLCs, by Doug Sibley
- How to Leech from Spotify - Using the Replay Music software to record and save free music from Spotify, by Pasikrata
- Transmissions - What it took and the hardware used to build the network at HOPE Number 9, by Dragorn
- Radio Redux - New techniques and hardware which is available to the radio (and pager) hacker and a general overview of today's radio systems, by Mr. Icom (Ticom)
- Radio Redux Original
- Basement Techie - Issue #1 Winter 2012/2013
- Physical Security Threat from Hotel Wi-Fi - Accessing free hotel Wi-Fi opens up the potential for your hotel room and key to obtained by others, by R. Stevens and A. Blum
- A Nice, Hot, Socially Engineered Meal - Story of a person who ordered a pizza via Grubhub and didn't have to pay when he selected "cash," by Gregory Porter (Email)
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: How people have come to accept a (((surveillance society))).
- Cover (Cover Info)
- Cover Inside Payphones of the Arab World
- United Arab Emirates This brightly colored phone was seen in Abu Dhabi where even the trash manages to be color coordinated. This phone only takes cards. Photo by DrJeep
- Egypt People in Alexandria have the choice of using the red handset or the blue one. It has absolutely nothing to do with The Matrix nor with rising up against oppressors and eventually winning. But there do seem to be more red ones. Photo by 1188
- Libya #1 This phone was found in Green Square in Tripoli, where there's still a bit of cleaning up to do. The booth itself is mostly used for posting political campaign ads while the inside does a pretty good job as a trash receptacle. If you're looking for a handset here, you'll have a tough time. Photo by Tony Anastasio
- Libya #2 ""
- Back Inside Payphone/Booth Alterations
- Scotland Found in Cleish, the traditional red booth that used to be seen everywhere in the United Kingdom has now found an alternate use as a bastion of information. We hope at least there's a phone book in there. Photo by Sarx
- United States What are the odds of getting two such submissions for the same issue? Seen on Broome Street in New York City, this library is a bit smaller, but with room to expand. Complete with locking doors. Photo by John
- South Korea Not really a payphone and not really an alteration, but an example of why we encourage submitters not to have humans in the shot. The result here looks like some kind of weird phone creature staring back at us. This regular phone inside a phone booth was found at the Rodriguez Range U.S. military installation. Photo by Josephus
- France This can be thought of as a doubly foreign payphone, since the traditional red booth immigrated from the United Kingdom and the phone itself is in the French city of Pontorson. In all likelihood, the components came from someplace else, so this represents a real melting pot of telephony. Photo by Tom
- Back The Back Cover Photos
- Back Cover Photo #1 We're not going to kid ourselves into thinking that this picture wasn't doctored a bit. We suspect that the total price was $26.00 and the amount of gallons was 6.667. Removing the decimal points and the 7 made this look like a truly "Satanic gas pump," as Dor Occas tells us. It's close. The only time that such a numerical lineup would be possible is when the price is $3.899 a gallon (since pumps in this country always have prices that end in nine-tenths of a cent). Now, if someone can find a pump that only shows two numbers to the right of the decimal point rather than three, the amount of gallons could actually show up as 6.66. (We'll overlook the decimal points.)
- Back Cover Photo #2 Talk about numerical lineups! This one, according to Barry Mullins, was a big coincidence. He was bidding for the famous Cap'n Crunch whistle that emits 2600 Hz and this was his winning bid. What makes it even better is that he bid a higher amount and this is what eBay calculated as the final price. It was clearly meant to be.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 29!
$2600 Magazine - Volume 29, Number 4 (Winter 2012-2013)
- Storm Clouds - Editorial
- Basic Code Breaking - An look back at the article "Simple RSA Encryption or Human-Calculable Encryption" in 28:2 on potential methods of breaking simple encryption methods without a computer, by Joseph B. Zekany
- An Overview of the Security Benefits Offered by Desktop Virtualization - A brief overview of the benefits that desktop virtualization can provide and discussion of the physical security aspects of that arrangement compared to the traditional workstation setup is also going to be covered, by David Morgan
- Hardware Hacking - An Introduction Via Dev' Boards - Brief introduction to hardware hacking via commercially available, low-cost development boards, by Sarlacii (Julian Houghton, Twitter)
- Hacking Walgreens Photo Processing Machines - Use a "USB Switchblade" on a re-booted photo kiosk to gain potential remote access capabilities or install malware, by Tahu363
- Telecom Informer - Overview of cellular phone femtocells, microcells, repeaters, and bidirectional amplifiers (and the headaches they can cause), by The Prophet
- C is for Camouflage - Trick to switch between a camouflaged Windows Command Prompt screen and Windows Notepad to fool any teachers/watchers, by Malandraj3m
- A Method to Spider Sites Like Indeed.com with Teleport Pro - Overview of setting up a "port bouncer" in order to rub a web crawler against websites which appear to be blocking or restricting them, by "ain'tDigitalDATTruth"
- Steganography Over Covert Channels: Implementation and Government Response - Amazingly in-depth look at steganography and the potential for governments use (and abuse) this technology, by Hal Wigoda
- New Ways of Ranking Documents - Idea to rank a document based on the amount of information you learn instead of its popularity, by Casandro
- Hacking Dirt - Use a little hacker ingenuity and Mother Nature to easily fix a blocked storm drain, by OWA
- Hacker Perspective - by Lone.Geek
- The Security Funnel: When OpenVPN Meets Tor - An overview of combining OpenVPN and Tor for having the maximum security and anonymity while on the Internet, by Wananapaoa Uncle
- Tactical Teensy Rapid Recon - Example of using the Teensy development board to emmulate a HID device on a target machine which then copies the SAM repair file (or /etc/passwd) containing usernames and passwords to a remote machine, by chap0 (Email, Twitter)
- Code: example.ino
- Code: payload.ino
- Code: driver-install.vbs
- Letters - Intercepts
- Propositions - Lauren, Dave, Ryan
- Inequity - tony, Captain V. Cautious, linhat, ghostguard
- Reader Thoughts - ziroha, ziroha, Jeff, John Schmitt, Brad, Baby E, CptnKase, Bill, PT Kitty, Barrett D. Brown, Philip, byeman, ternarybit, Brainwaste
- Listener Thoughts - The Other John Draper (the one in Cardiff)
- New Meeting - Zach
- In Need of Advice - Anonymous, CoolHappyGuy, Penmeup, Andrew, Monica
- Advice to Share - No Name, R. Toby Richards
- New Stuff - Lost in Cyberia, Chris, l0tek, Brad
- Miscellaneous - Theo, Jessica, JonnyBear, PB, John, c, E.T.A.G.E., e, Steve
- An Alternate Method for Creating a SSH Tunnel with PuTTY and Squid - How to setup PuTTY so it can utilize dynamic port forwarding to create a SSH tunnel on a remote VPS, by Synystr
- How to Survive a DNS Attack - Quick how-to on configuring multiple nameservers so a website won't go down down due to a DNS outage affecting one of the nameservers, by SPitBalls
- The Breach That Wasn't - How the mainstream media overreacted (and lied) about a security breach at City College of San Francisco, by Sam Bowne
- Transmissions - Tragedy of SSL, by Dragorn
- WordPress Exploit Immunization - Overview of several simple steps to install free plug-ins to help improve the security of your WordPress platform, by Seeker7
- Fiction: Hacking the Naked Princess - Chapters 0x03 - 0x05 - Chapters from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: The aftermath of Hurricane Sandy and how hackers can help keep Internet connections up
- Cover (Cover Info)
- Cover Inside Unusual Phones
- Legoland Not really a country or even a city, so we should probably say that this was seen in Carlsbad, California at the aforementioned theme park. Considering the way payphones are being abandoned, you might just as well have these start popping up to replace them. Photo by Dave G
- United States Sure, why not? It's not like anyone is going to be using that phone, if there even is a phone underneath all that and if it's actually working. Perhaps converting former kiosks and phone booths into mini art galleries is the way to go. This was seen in Jamaica Plain in Boston, Massachusetts. Photo by Ernesto Valencia
- Norway This is just the coolest phone ever. We don't care how old it is - whoever concocted this design clearly understood the concept of "rugged." No doubt it'll outlive us all. This can be seen in the tiny port of Barentsburg, which is the Russian settlement on Spitsbergen, 78 degrees north. It's used for calls within the settlement of 500 people. Photo by Snorre Steen
- Switzerland Speaking of rugged, this phone booth was found inside the Gonzen iron mine in Sargans. To be fair, the mine hasn't been used since 1966, and perhaps the phone hasn't been either. Or maybe it's used by tourists who can't get their cell phones to work. Whichever it is, this one qualifies for being well off the beaten path. Photo by Markus Bruetsch
- Back Inside More Broken Payphones
- Disneyland Again, technically not a city or country, at least not to us. This sad specimen was seen inside the Disneyland Grand Californian Hotel in Anaheim where they actually have permanent signs affixed to disabled payphones. A true sign of the times. Photo by Curtis Vaughan
- Washington, D.C. In this case, it's probably a good thing that this payphone was removed, as we can only imagine how unpleasant an extended conversation could become. This also aptly illustrates America's changing priorities. Photo by Dave Burnett
- Copenhagen At least in Denmark, when they retire payphones, they make a big deal out of it.Photo by Patrik Larsson
- Portland, Oregon Always good to see a sense of humor in an otherwise somber setting. Photo by Brett Campbell
- Back The Back Cover Photos
- Back Cover Photo #1 This sign really sums up the hacker mentality. You can either go along with the masses on a tour of the world's biggest "closed system" or you can come join 2600 to bypass that and get on the inside. That this was found at the site of the famous and historic Biosphere experiments is icing on the cake. Thanks to Ashes for finding this in Oracle, Arizona.
- Back Cover Photo #2 So we go from a site that housed space colonization experiments to the opposite end of the spectrum: an abandoned school in Detroit. But 2600 exists here too to bear witness to the desolation. Maybe this would be a good site for a 2600 meeting. (No, seriously, that's a really bad idea.) Thanks to Kevin Costain for discovering this near Brush Park. We agree with his suggestion of renaming this place the "2600 School of Hard Knocks."
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 29!
$2600 Magazine - Volume 30, Number 1 (Spring 2013)
- Index - TREATMENTS
- A Lost Promise - Editorial
- Guest Networks: Protection Less Than WEP? - Obtain Linksys "guest" Wi-Fi network passwords by stepping through all the defaults provided in their setup software files, by Kevin Morris
- Code: guestpass.vbs
- Practical Cryptanalysis: Reversing Cisco Type 7 Password Hashes - Potential security holes in the Cisco Type 7 password hash which opens Cisco routers to remote plaintext attacks, by mcandre (Andrew Pennebaker, Fairfax, Virginia, Milwaukee, Wisconsin, GitHub)
- Code: ios7crypt.py
- shifty: FPGA Password Cracker Shifty cracks classic Cisco network device passwords.
- Twitter for Fun and Profit - Create a Twitter botnet without the need to infect a host computer and the potential to profit from these "fake" tweets, by xnite (Robert Whitney, Bloomington, Illinois, DOB: 05-12-1990, Twitter, GitLab, GitHub, Blog, Facebook)
- Code: twitnet.tgz Twitter Sock Net
- Additional Info
- Warning for Ye Olde Bank: Don't Do This! - Story of an almost successful fraudulent bank transfer which started via a fake fax message, by lg0p89
- Telecom Informer - Story of using cellular and wireless Internet on a trip from South America to Antarctica and back to Holland, by The Prophet
- Social Engineering: Tactics for Prevention - Overview of the techniques and tips used by social engineers and how you can prevent it from happening to you, by Ryan Daley
- Extra-Legal Harassment - Real-world examples of governments harassing or spying on people and what you can do to protect yourself or fight back, by D.B. LeConte-Spink (Douglas Spink, Fausty)
- Hacker Perspective - by Mike Keller (GoodHart)
- Book Review: Exploding the Phone - Book review of Phil Lapsley's Exploding the Phone, by Rob T. Firefly (Rob Vincent, New York, New York, Twitter, YouTube)
- Cats and Mice: Phone Phreaks, The Telephone Company, and the FBI Phil Lapsley's phone phreak history talk from The Next HOPE, 2010.
- Fiddler - Never Trust the Client - Exploiting client-side security vulnerabilities in web form validation with the Fiddler web debugging proxy, by Andy Phillips
- U.S. Department of State Loves Mexico - U.S. State Department bid for a potential surveillance site in Mexico, or more money for (((Verint ✡))) from U.S taxpayers, by ^SUBv
- Hypercapitalism and Its Discontents - Hacking and software piracy in the "new age" and why we should fight modern day (((oligarchs))), by W.D. Woods
- Fun With Base Math: A Primer on Base Numbering Systems - Overview of mathematical operations which are not based on the standard base-10 system, by Fantacmet
- Letters - SYMPTOMS
- Propositions - Javier (Spain), Geoffrey, Mu Dee
- Commentary - Wolverine Bates, angelsbrothelsgrandmalives, Anonymous
- Information - str8ball, Lithium187 (Bethlehem, PA), Elger "stitch" Jonker (Netherlands), Ultimate Peter
- Observations - David, Bishop 341-B, John Bajak, John R. Sullivan, Staticblac (Chris Berge)
- Questions - Charles, Tony (New Jersey), Anagbogu, Future Cyborg, Jack, Jake, Another Innocent Man in Prison, JT Simpson
- Fun With Meetings - Paul (Gwinnett County, GA), Philip (Johannesburg, South Africa), zkyp (Belgium), Tazmatt (Montreal, Canada), Ross (Melbourne, FL), Ross, Richard Cheshire, Derrick, Haskell
- Reader Feedback - D1vr0c, pipefish, Igner, Edson+, zenlunatic (Maryland), Jeff, Anymouse, Zek, Barrett D. Brown
- Digital Issues - Caleb Coffie, Karsten Anderson, Adam, n0tec, Andy, Alex W
- Cracking Push-Button Locks - Overview of the Borg 3000-Series push-button lock and a bug which reduces them to only 120 possible combinations, by riemann (U.K.)
- Brute-Force Access - Brute-force the 4-digit admin password on a TRIPLEX DVR468RW CCTV DVR, by lanrat (Ian D. Foster, San Diego, California, Twitter, GitHub)
- Code: DVR_exploit.py
- TRIPLEX DVRLink DVR468RW Exploit Original
- The Usage of the Assumption Technique in Social Engineering - Example story of using "reverse" social engineering and the power of assumption to get what you want from a customer service rep, by TJ
- Transmissions - The value of using open communities (Sourceforge, GitHub, Stack Exchange, IRC, forums, etc.) to expand the capabilities of today's hackers, by Dragorn
- Dev'ing an OS - A basic understanding of what it takes to develop your own (small) x86 operating system complete with a bootloader, by Shikhim Sethi (India, Email, GitHub, Twitter)
- Code: main.asm
- Tetranglix A bootable 512-byte Tetris clone.
- Tart Tart is a public domain UNIX clone.
- Selfer A twenty-first century tool destined to change the world; also, a 512-byte OS.
- This OS is a Boot Sector (Original)
- These Philosophers Stuff on 512 Bytes Or, this multiprocessing OS is a boot sector. (Original)
- Art of Assembly - [x86 16-bit]
- Learning, Hacking, and the Raspberry Pi - Overview of the Raspberry Pi GNU/Linux development board including some quick "overclocking" hacks, by Shea Silverman (Orlando, Florida, Email, Twitter, Facebook)
- Raspberry Pi Gaming by Shea Silverman
- PiPlay (PiMAME) by Shea Silverman
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.25
- Issue's Cash Cow: Aaron Swartz's JSTOR hacking case and his subsequent death from an overzealous "justice" system. Note the judge (Carmen Ortiz) in this case was an affirmative action Obama appointee.
- Cover (Cover Info)
- Cover Inside European Payphones
- Austria A typical payphone seen in Vienna, with a good deal of color used on the phone and a surrounding structure that means business. This is the kind of respect payphones used to get. Photo by Arys.
- France A standard card-reading phone found in the southern city of Nice. This model will likely outlive us all. Photo by PeiterZ
- Ukraine If a payphone could talk, this one would have some real stories to share. This model looks like it's been around from Day One of the phone era. Seen in Donetsk Oblast. Photo by Ryan Scott
- Poland While the phone that was here can no longer tell stories, the booth looks like it's weathered a few, to say the least. Discovered in a district of Warsaw called Fort Wola. Photo by Mark Zuckerbe_g
- Back Inside Worldly Payphones
- Japan A standard colorful green box, found all throughout the country. This one turned up on the island of Okinawa. Photo by Steve H
- Iraq Found in the city of Sulaymaniyah in the Kurdistan region. Rarely used, these phones operate using a prepaid calling card only. Photo by Shivan Muhealden
- Belize This colorful phone, found in Placencia, seems designed mostly for tourists, as it seems quite eager to help people make international calls, and the only payment option is credit/calling card. Photo by MTTRN
- Peru Found at Nazca Airport near the famous Nazca Lines of 400-650 AD, this unusual phone uses GSM due to its remoteness. That little black cone on the top is a GSM antenna. We're told the GSM company and signal strength are displayed on the screen. Photo by Prada
- Back The Back Cover Photos
- Back Cover Photo #1 We're not sure what part of the country this was seen in, but some hospital somewhere has #2600 as the extension to call when something like this happens. We can only hope that people don't try and hop onto the #2600 IRC channel looking for help. They may find themselves on the floor for a long time. Thanks to Chris for sending this one in.
- Back Cover Photo #2 We knew it would only be a matter of time before somebody tracked down a Bissell 2600 carpet sweeper. Apparently, they're rather highly regarded in the world of dust and dirt removal, and now the hacker community can also recognize its eliteness. Discovered by Will (a.k.a. Master of Telxons) in a second hand shop.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 30!
$2600 Magazine - Volume 30, Number 2 (Summer 2013)
- Index - incendiaries
- The Road to Safety - Editorial
- Splunking the Google Dork - Overview of some automated scripts using SearchDiggity and Splunk to improve Google searches for potential site security vulnerabilities, by G Dorking
- Fun With the Minuteman III Weapon System: Part 1 - Quick overview of the LGM30G Intercontinental Ballistic Missle launch control system and a simple way to "test" site security by throwing snowballs!, by Bad Bobby's Basement Bandits
- My First Blackhat - LOL story of having to serve a subpoena for a small claims court to a person he didn't know the physical address for, but was able to exploit some XSS holes in a website used by the "victim," by Pierre LC
- How to Create and Operate a Temporary Free Autonomous Zone - A framework of protocols and techniques to organize a large, diverse group of individuals voluntarily gathered together for a shard purpose, and in a public space, by lifeguard
- Telecom Informer - Overview of a cellular phone system in Holland and Thailand, and some technical info on CDMA450, by The Prophet
- A Broad Spectrum of DRM - Story of discovering and altering the Windows Registry to bypass the DRM in Alawar Games, by Cybermouse
- Getting Free Media - All Without Torrents! - Tips and tricks for using Google searches to find music (MP3s), or other files, freely available on open websites, by B4tm@n
- Tech Gets Better, Humans Do Not: A Beginner's Guide to Social Engineering - Very detailed overview of the social engineering, phishing, shoulder-surfing, physical security attacks, etc. a person working in IT should know and be prepared for, by jk31214
- Why Your Grandparents Don't Like the Internet - Story of the author's experience with older people not being comfortable with new technology or the Internet, and how hackers should help them overcome that, by xnite
- What Made UNIX Great and Why the Desktop is in Such Bad Shape - Why modern operating systems and GUIs actually slow down system development with all their bloat, and why text-based systems rule, by Casandro (Christian Berger, Germany)
- Hacker Perspective - by Hristo I. Gueorguiev (LinkedIn, GitHub)
- 0-Day Adventures - Story of an administrator who came across a 0-day Internet Explorer vulnerability (CVE-2012-4792) in the wild and his attempt to track down the origins, by Sh0kwave
- How a Prehistoric Hacker Got Started - Journey of a hacker who started in the 1960s and hasn't looked back since, by DarkAudax
- The Weather Outside is Frightful - Story about a ATM user who discovered a skimmer and the neeed to always be alert when using ATMs, by lg0p89
- Say Hello to Crazy Thin 'Deep Insert' ATM Skimmers
- Homemade Card Skimming Now Possible with MagSpoof
- How to Spot an ATM Skimmer
- Bulls-Eye on the Banks - Again - Information about a Trojan/DDoS attempt focused on around 30 national banks, by lg0p89
- Exploiting the Postal Service Address System for Personal Gain - Utilize slight address misspellings to bypass those "one free item per household" deals, by Tj Loposser (LinkedIn?, YouTube Channel?
- A World Without Security - If we lived in an ideal high-trust world, we wouldn't need intrusive security, but thanks to Evil Corley, we do. So we're stuck with these annoyances, by Donald Blake
- Letters - autonomous consciousness
- Reading and Writing - B Nichols (Ben Nichols), pete, Jim (James McAllister), Provirus
- Pitching In - Nitin, Louie Ludwig, AP, Eric, gabe, Tim, Conan
- Help Wanted - S W, Reggie, Anonymous
- Inquiring Minds - muh2 muh2, nov112011, Toad, Gabriel, dave, Gabriel (Belo Horizonte, Brazil), Phil, Gabriel, Seth, Cortland, 616boomer, Grant, SS
- Service Declined - [none given], sendspace.com
- Call to Action - v, Anonymous, Brainwaste
- More Meeting Mania - Liam (Ewloe, Wales), farangbaa, Janelle, Jax (Helsinki, Finland), Ian
- Responding - Myq Morer, UserNotFound404, Jojlot, GoodHart, jlbesq, Micah Lee, Michael, D351, Tech Deprived Incarcerate, Robert
- The Game of Justice - Anonymous, Mike, Ghost Exodus
- Memories - Les Hogan, Trevor Pontz (a.k.a. acid phix)
- Copy Protection, Trademarks, et al - Broken Syntax, Christopher
- Advice - BudLightly, Geri Q
- Book Review: Pirate Cinema - Book review of Cory Doctorow's Pirate Cinema, by elib7ronic
- Cyber Attacks on Equities Markets: The Real Threat of High Frequency Trading - How NYSE, NASDAQ, and various other exchanges fail to address properly their instability and frailty to large-scale cyber attacks, by Eightkay
- Static Code Analysis Using Watchtower - Simple tool to locate potentially hazardous code (security audits) within a project, by Chris Allen Lane (Gainesville, Florida, Email, Twitter)
- Transmissions - Polymath or dilettante, by Dragorn
- Tracking Users on Trustworthy Sources - Even trustworthy websites/forums can be exploited to obtain information (IP address, etc.) on its visitors via an embedded image in your signature, by xnite
- A Response to "Perfect Encryption - Old Style!" - Overview of one-time pad encryption you can do by hand, with several examples are given, by Phil
- Fiction: Hacking the Naked Princess - Chapter 0x06 - Chapter from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: How the Boston Marathon bombings are being exploited in order to decrease our privacy in public settings with more surveillance cameras to "fight crime."
- Cover (Cover Info)
- Cover Inside Payphones in Trouble
- Colombia Seen in Barranquilla, handsets of these phones often get stolen by enterprising "carreteros" - guys with burro-drawn carts who trade in a variety of things. They then use the mouthpiece as a microphone to announce themselves as they drive the streets looking for customers. Photo by Colter McCorkindale
- United States What appears to be remnants of a Terminator movie can be found in the 4th Avenue/9th Street subway station in Brooklyn. How payphones ever managed to survive in the bowels of the New York City transit system in the first place is beyond us. Photo by Alex
- Thailand While it may be bright, cheery, and colorful, this payphone has one fatal flaw. See if you can discover what it is. Spotted at the Surat Thani ferry terminal. Photo by TProphet
- United States This about says it all. The ghost of this St. Louis payphone tells the typical story of nonstop abuse - dents from every conceivable angle, a damaged sign, a coating of rust, not to mention the missing phone. Photo by Todd Smith
- Back Inside Reclaimed Payphones
- Thailand Lately there seems to be a growing phenomenon of nature stepping in and taking back payphones. We see the forest moving in on this one, found outside the Renaissance Hotel on Ko Samui island. Photo by Mike S
- Greece Here it looks like the Earth itself is about to swallow this poor phone. If it weren't for the tree, it would certainly be horizontal. Yet it still works. Seen on the island of Crete in the village of Almyrida. Photo by Chaz
- United States The forest was very aggressive at the Hoh Rainforest in Washington State, where this structure looks like a part of nature itself. The actual phone apparently blended in so well that it can't even be seen anymore. Photo by Connor Dunning
- Austria Winter has taken this payphone (we assume there's one in there) at the Lackenhof ski resort in Ötscher. The sign translates to "This telephone can save lives. Don't destroy it!" There are very few of these phones (and signs) left. Photo by Richard Hanisch
- Back The Back Cover Photos
- Back Cover Photo #1 Here's an interesting fact, discovered by sail0r: If you buy a copy of 2600 (or anything else, we presume) at this local Micro Center and pay cash, your name shows up on the receipt as "B Hacker." (When making a purchase with a credit card, the cardholder name shows up.) Perhaps the thought is that only a hacker would be smart enough to use cash - or maybe something somehow got hacked and this is the signature. Regardless, we suspect a lot of people will be buying 2600 with cash at Micro Centers just to see what happens.
- Back Cover Photo #2 While out cycling, Rob Purvis found this neat little sign in the village of Newton Poppleford in East Devon, England. It's clearly an informational statement which says that hackers are always in the vicinity. Depending on one's outlook, this will either prove comforting or troubling.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 30!
$2600 Magazine - Volume 30, Number 3 (Autumn 2013)
- Index - parts
- The Right to Know - Editorial
- An Introduction to Bitcoin - General overview of Bitcoin and how to use it for your transactions, by Frank Buss (Germany)
- Bitcoin: The Hacker Currency? - Why hackers should look into using and supporting Bitcoin and it's potential to avoid federal interference, by Variable Rush
- Inquiring Minds = Hacker = Design Engineer - Story of a person who prefers hardware hacking over software and why software hackers should give it a try, by Sarlacii
- Hacking the Apple Collective - Behind the scenes overview of how Apple run its store and the "Genius Bar", and how he became burned-out after awhile when Apple's charade was exposed, by Ronin
- Internet Trolls - What is a troll and trolling?, by Sam Bowne
- Telecom Informer - Overview of PBXs and the shift away from them, by The Prophet
- Controlling the Information Your Android Apps Send Home - The potential dangers and security breaches (app permission changes, etc.) of having auto-updates on an Android phone, by Aaron Grothe
- U-verse Networking - Overview of AT&T's U-verse (VDSL) by a tech support person, including bridge mode work-arounds, and dumb questions ask by customers, by Uriah Christensen
- Scamming the Scammer: A Fun Way to Respond to a 419 Scam - Story of a person trying to "reverse scam" a Nigerian 419 scammer and tips to avoid being scammed yourself, by The Piano Guy (Gary Rimar)
- The Art of War and What IT Professionals Can Learn from It - Relating Sun Tzu's Art of War to working in a modern IT environment, by Rick Conlee (Waterveliet, New York)
- Access Tandem Codes and the Hidden Phone Network - Overview of access tandem codes to connect to different long-distance networks, and how to different remote test numbers and interesting recordings, by Brandon
- Hacker Perspective - by Antonio Ortega, Jr. (Eugene, Oregon, Twitter, GitHub, LinkedIn)
- Palo Alto NGFW Insider - Technical details (Linux kernel, commands, and filesystems) of a Palo Alto Next Generation Firewall, by ]{nightVision
- Identity Management and Its Role in Security Strategy of Enterprise Environments - Overview of Identity and Access Management (IDM or IDAM) in large enterprise environments and delegation responsibilities for security strategies, by Patric Schmitz (Email, Twitter)
- Letters - lore
- Random Bits - Jim L, Garry Wynne, lord.underdog, Scott, bob, Pete, Nate Brown, Neural Nut
- Contributions - James Kracht, Rasmus & Hanna, Tom, Jesse, Jesse, D. Spink, follow_the_lea
- Special Requests - WS, Omi, zenlunatic (Maryland), Prince Nicholas Bailey (Denver, CO)
- Continuations - Barrett D. Brown, D1vr0c
- Critiques - Grace, John, iacode
- Info Needed - Jack, nick, james, Stephen, Chaoticpoison, Andrew, Joe, adam
- Meeting News - Curious in Philly, Jorge (Costa Mesa, CA), Jerrold, Richard Cheshire, Brandon (Hawley, PA), Steve
- Feedback - Radagast, Kilby, Sean Murphy, t. heride, Jax, Blank Electron, Charles Parker II, RJC, pixter
- On Privacy - flax0r
- Defeating Forensic Attacks on Full-Disk Encryption - Tips for defeating modern forensic attacks (cold-boot, remanence attack, DMA attack, hibernation file attack, etc.) against full-disk encryption systems, by Mojo
- Bank Notes - Story of a person working at a bank and receiving a potentially hostile email file attachment (EXE) and his attempt to track down who was behind it, by lg0p89
- Transmissions - Being "hard to use" is not a valid excuse for not using encryption, by Dragorn
- Relax, We Bought Security - Story of a freelance security consultant and crazy things he's see during the time working and people who think they know more than they do, by Wananapaoa Uncle
- Clouds, Clouds, Clouds - Why the cloud storage or applications are still a bad idea for small- to medium-sized businesses, by lg0p89
- Lights, Camera, Hack - Hacking portrayed, or used in the making of, movies you may not have known about, by Gregory Porter (Email)
- Fiction: The Error - by Zellie Y. Thomas
- A Response to "Perfect Encryption - Old Style!" - Overview of one-time pad encryption you can do by hand, with several examples are given, by Phil
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: The fascists who Evil Corley, Dave Buchwald, Greg Newby, Mitch Altman, Edward Cummings, Adam Prato, Babu Mengelepouti, Alexander Urbelis, etc. supported and voted for are now abusing their powers to spy on the rest of us. Change!
- Cover (Cover Info)
- Cover Inside Awkwardly Sized Payphones
- Russia Found at the Tagansky Protected Command Point in Moscow. It's technically not a payphone and the site is technically no longer a secret military complex, but a harmless museum. The weird-sized phone still scares us, though. Photo by Ashes
- Azerbaijan Located in the Heydar Aliyev International Airport in Baku, this phone and its instruction plate have an awful lot of white space surrounding them, making them stand out even more than the presence of a payphone normally would. Photo by J.P.
- China It seems like this booth was constructed for a somewhat larger model of phone than the current resident, found in the ancient canal-networked town of Tongli. Photo by Joy Lockhart
- Malawi Found on the grounds of Ekwendeni Hospital in Ekwendeni, this fairly modern phone also doesn't seem to match its home. Photo by Kevin
- Back Inside Payphones of the World
- France Spotted at the Cannes International Film Festival earlier this year. Note the "film" that the phone is mounted on. Photo by T-RAY
- South Korea Seen in the Gimpo Internartional Airport in Seoul, these are two rather old models, taking all combinations of coins and cards between them. Photo by bitcoin vendor
- United States Nobody is too surprised at a sight like this in Buffalo, New York. And we wouldn't be at all surprised if these phones were still operational. Photo by Vince Harzewski
- Bahamas Believe it or not, this phone in Mangrove Cay on Andros Island actually works. But you'd have to have an unusually shaped head to take advantage of it. Photo by Robin Blanc
- Back The Back Cover Photos
- Back Cover Photo #1 Occasionally, moments like this just happen and lately we've been getting more and more of them. In this case, Gene (laserdemon) noticed his four-year-old daughter parading around the house with one of our issues while counting out loud. This verifies a longstanding theory of ours that we do in fact sometimes act as an educational tool. What's really amazing here is the number of kids in a single photo of our magazine.
- Back Cover Photo #2 And on the other end of the spectrum, we see the symbolic death of a hacker - and the unsymbolic death of someone with the actual last name of "Hacker" as seen by L. Motz, who witnessed this at Westview Mausoleum in Atlanta, Georgia. This kind of thing also happens now and then.
- Staff page was replaced with an article which was suppose to run last issue.
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 30!
$2600 Magazine - Volume 30, Number 4 (Winter 2013-2014)
- Index - Etchings
- Dissent or Descent - Editorial
- ID3 Tag Messages - Using and abusing the informal ID3 tag specification to hide "secret messages" in MP3 audio files, by Donald Blake
- Privacy - A New Hope Through Tails - Overview of using the Tails secure Linux operating systems for increased privacy and security on the Internet, by Brainwaste
- Fun With the Minuteman III Weapon System - Part 2 - The potential for intercepting nuclear missile base VHF communications, by Bad Bobby's Basement Bandits
- Telecom Informer - Reminiscing about the days when there were many small, privately-owned telephone companies, by The Prophet
- The Many Vulnerabilities of Verity Parental Control - Overview of the Verity Parental Control Software and some tips to bypass it by using registry hacks, online proxies, and virtual machines, by Tyler Behling
- Anonymity and You, Firefox 17 Edition - Discussing the Firefox vulnerability which effected Tor users' privacy and several tips to maintain your online privacy when using Tor, by l0cke
- Wi-Fi Security: Attack and Defense - Examines the current state of Wi-Fi security with a practical emphasis on attack and defense methodology, by ternarybit
- Code: netgear-psk.sh
- List of Known NETGEAR PSKs For Wi-Fi setups with SSID: NETGEARXX
- fyy0r's Netgear Killer Dictionary For Wi-Fi setups with SSID: NETGEARXX (README)
- The Maturation Cycle of a Hacker - Story of the life-cycle of a hacker, by lg0p89
- There is Never a Free Lunch - Why we should be weary of remote access computer support, as it may be a scam, by lg0p89
- Hacker Perspective - by Synystr (Michigan)
- CYA Using a Pi to Pivot - Setting up a Raspberry Pi to make a "Pi-Pivot" in order to mask your wireless Internet activity, by 0rbytal
- Pretty Good Privacy - Overview of OpenPGP and using and installing GnuPG to send and receive encrypted email, by Klaatu (Pittsburgh, Pennsylvania)
- Hacking Your Mother Tongue to Obfuscate Your Encryption - Using (or creating) a different spoken language (i.e., Russian instead of English) to further obscure your encrypted messages, by Israel
- Letters - Communicatory Types
- Queries - Chris, bughardy, Damien, Michael, Anonymous, Nam, Auggy, Damien, Ruth, Derneval, Damien, herp derp, Danielle, Damien, Daniel, Yahia
- Additional Info - jim, Larry, Rachiee, Capt. Jay, rixter, K5TA, Brandon
- Critical Observations - phreakin5ess, Bobby Joe, XeNO, M. Piazza, apocalypic
- Statements - nealcamp, Dan, Justin, [please withhold my name], F.
- On Meetings - Lex, Pic0o (New York), B (Minnesota), Sebastian (South Carolina), Ill Protocol, TheCyberInstructor (Biloxi, MS), Mike (Philadelphia), Dr. MG Cyb3rSM3 (Israel)
- Free Advice - The /\postolic H/\cker, anon, (Australia), dILLHole
- Horror Story from Hell - Morgan
- Future Plans - Sam
- Appreciation - Gazza, Ian, J. (AC2LS), RAMGarden, Anonymous
- Digital Divide - June, Jota
- HOPE X Tickets - Lynn, Ether 9ine, Greg
- Black and White: The Growing Schism Between Hackers and the Law - Why it doesn't pay to be a "white hat," as it can turn around and haunt you, by Scott Matthew Arciszewski (Orlando, Florida, Twitter, GitHub)
- United States of America vs. Scott Matthew Arciszewski
- Scott Arciszewski, UCF Computer Student, Charged in Anonymous Hacking Crackdown
- UCF Student Arrested by FBI for Alleged Computer Intrusion
- Netcam: Basics and Vulnerabilities - Overview of potential security vulnerabilities and default passwords to several models of IP cameras, by John Thibault
- Transmissions - Location spying, not just for governments anymore, by Dragorn
- All I Want is Total Freedom - Tips to increase your personal privacy in real life and on the Internet, by lifeguard
- Fiction: Hacking the Naked Princess - Chapters 0x07 - 0x09 - Chapter from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: Do we allow so much that we value and that we've fought for over decades, even centuries, to be dismantled out of apathy, fear, or convenience? Or do we take a stand and fight back, knowing that any time we do such a thing, there are risks of one sort or another involved?
- Cover (Cover Info)
- Cover Inside Terminated Payphones
- France A rather unfortunate reality captured here in Paris, as a bunch of phones, complete with the booths they were housed in, are taken away to be... retired. Photo by Nicolas RUFF
- United States And this is how it turns out for many of these unfortunate phones, destined to rot in a scrap heap with piles of junk, as seen in Culver City, California. Photo by jeff oconnell
- Nicaragua In other parts of the world, however, abandoned phones are left to die in peace. This way, they're always there as a reminder and a curiosity for future generations. This one was found in El Bluff. Photo by Aaron Cotton
- Germany And then there are those places that turn tragedy into something positive, such as here in Lübeck. It seems there was a fire at a local pizza place in the 1970s and they decided to keep the phone in its "altered state" after reopening. Photo by Craig Damlo
- Back Inside Payphone of the World
- Croatia This phone is completely operational, and it can be found on the ferry from the city of Split to the island of Vis. The phone carries the initials of a now defunct company (Hrvatska Pošta i Telekomunikacije), which hasn't existed since the 1990s. Photo by Bojan Paduh
- Australia A truly remote phone, found in a place called Winning Pool on the North West Coastal Highway around 150 miles from any people. The coin mechanism has been completely removed, ostensibly to save the phone company the 300 mile trip to empty it. Photo by Astrant Photographic
- Barbados Seen in Bridgetown, this phone carries the familiar logo of parent company Cable & Wireless to the left of the BarTel name, a very familiar sight throughout the Caribbean. Photo by Kristyn Rose
- Uganda Spotted in Mukono, this phone is operated by Mobile Telephone Networks, a company based in South Africa that has expanded its operations to over 20 countries in Africa and the Middle East. Photo by TC Johnson
- Back The Back Cover Photos
- Back Cover Photo #1 So momentumdave was going through some old papers concerning his adoption and discovered that he was worth exactly $2600 at the time. How cool is that? Incidentally, we can't help but wonder if the actual infant was the attachment referred to in "Average Cost per Infant (attached)."
- Back Cover Photo #2 Now this is something we find ourselves wanting more than anything - a true hacker radio, as discovered by sarx in Scotland. Had this company only stayed in business another 30 years or so, this would have been the perfect gift for Off The Hook listeners.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 30!
$2600 Magazine - Volume 31, Number 1 (Spring 2014)
- Index - map
- Thirty Years On - Editorial
- Lessons from "Secret" History - From Cable Vetting to TEMPORA - Article on the history of "cable vetting" where intelligence agencies intercept cable messages between countries and its relation to the modern NSA spying scandals, by Poacher (U.K.)
- Google's Two-Factor Authentication: The Sneaky Trust Feature - Overview of Google's two-factor authentication scheme and a potential exploit by using Google's default "trusted computer" selection, by Samuel A. Bancroft
- Identity and Encryption Verification - Overview of different methods of (PGP) fingerprint and public-key verification as well as key signing parties, by xnite
- Asterisk: The Busy Box - Script to use Asterisk to create a "Busy Box" so the target can't make or receive any phone calls, by MasterChen
- Using Square from Outside the U.S. to Obtain Dollars at a Reasonable Rate - A scheme to bypass geolocation on Square where a person can pay themselves with a credit card in order to obtain dollars at an intermediate currency exchange for savings, by R. B. (Argentina)
- Telecom Informer - Overview of the cellular/Internet infrastructure in Ecuador and a little about Mexico, and what telcos mean by "maximizing deferred maintenance asset value," by The Prophet
- Robbing the Rich Using Bitcoin - Theoretical attack to obtain a target's Bitcoin wallet by brute-forcing weak passwords, by 0rbytal
- The Night the ATM Went Down on Me - Story of using, and observing, an ATM which crashed and appeared to be running Windows XP, by The Piano Guy (Gary Rimar)
- Android Reversing Bootcamp - Overview of reverse engineering Android apps and some of the tools you'll need, by Andy G (Twitter, Mastodon)
- Hacking Commercial Maytag Washers and Dryers - Overview of reprogramming Maytag washers in service mode to run for free, by KingFlathead
- Hacker Perspective - by Clutching Jester
- Accessing Data Structures Located in a Randomized Address Space (ASLR) - How to eliminate entropy and bring the universe back to the singularity. Demonstrates by calling fork() to show that clones/forked processes will also share the same (compromised) randtbl in the shared memory space. by Matt Davis (enferex)
- Code: randhack_small.c
- randhack This is a proof of concept program that can access glibc's randtbl used for generating pseudo-random values.
- A Little Excitement Never Hurt Anybody! - Breaking down the errors in a "From the IRS" spam/phishing letter, by lg0p89
- Letters - VAPORS
- Notations - Malvineous, Samuel, T
- Questions - L, Rob, Saskman (Canada), Drax26, kmk, Glenn, John, Chuck, M Y, Norman, Eric Lee, Juan, Tina, zhangganghong18, Brainwaste, Michael
- Accusations - Simon (England), Lifetime Subscriber
- Litigation - Nick, Very Anonymous, Tyler, Phedre, ~justanothersubscriber
- Clarification - byeman, William, Bandersnatch
- Donations - T, Dennis
- Contributions - sol, flames
- Investigations - Jeremy, pathos.ethos, --handle-need-not-apply--, Bob Hardey's Mom, Malvineous, Chris
- Observations - Justin, DeepGeek, William, L0cke, CasperGemine, Boxholder
- Versification - Evan Krell, Neo Anderson
- Convocations - Johnson, youssef, B (Costa Rica), Matt (Michigan), S, S, Matt
- Appreciation - Anonymous, A loyal reader, Captain V. Cautious, Ed (Australia)
- Brute-Forcing PIN Code Keypads Using Combinational Mathematics - The mathematics involved in brute-forcing a 4-digit PIN or keycode and a 10,003 digit number sequence to try, by Alva Ray
- 4-Digit PIN Sequence 10,003 digits making up the shortest possible sequence containing all PIN codes between 0000 and 9999 exactly once.
- Building a Community Forum - Overview of the tools and processes needed to create a hacking-related forum or online website, by Freaky
- Procedural Worlds, Statistical Analysis, Image Processing, and PRNG Exploitation for the Lulz - or Why IMDb Got a CAPTCHA - Detailed article describing the GNAA and Bantown troll/lulz attacks against IMDb to put Gayniggers from Outer Space into IMDb's Top 250, by sam (Sam Hocevar, Website, GitHub, Twitter)
- Procedural worlds, statistical analysis, image processing and PRNG exploitation for the lulz (Original)
- At Home Malware (and Online Ads) Protection - Simple script for DD-WRT to grab a current list of malware or advertising hosts which are then blocked locally at the router, by Ashes
- Code: malware-stop.sh
- Automated Target Acquisition - Creating a "targeting list" by capturing the IP addresses of users who appear to be searching robots.txt for sekret files and directories, by 0rbytal and blerbl
- Fiction: Lock and Key - by Robert B. Schofield
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: Celebrating 30 years of selling other people's BBS files.
- Cover (Cover Info)
- Cover Inside Artistic Payphones
- Thailand This isn't the first Thai phone we've printed that appears to be heading back to nature. This one was spotted in Sai Yok, near the Death Railway (don't ask). Photo by Kimmo
- United States Seen on Melrose Avenue in Los Angeles, they call this a punk rock payphone and it's easy to see why. In fact, we wouldn't be surprised if this one went on tour in the 1980s. Photo by Glenn Griffin
- Canada Montreal is apparently known, not only for its plethora of payphones that people actually still use, but for occasional artistic payphone expressions. Photo by Jonathan Mertzig
- China Meanwhile, over in Shenzhen, the artistic look is a bit... minimal. In fact, the inside of this booth would make a pretty convincing prison cell. Photo by DrSm0ke
- Back Inside Payphones of the World
- Czech Republic This is a fairly basic model found in Prague. It's definitely seen a good amount of use but looks like it can handle quite a bit more. Photo by Matt Anderson
- Mexico Found in an underground washroom hall in Playa del Carmen, this phone clearly benefits from spending all of its time indoors. Photo by Jorge
- Peru This is a name we should all become familiar with. A subsidiary of América Móvil, a Mexican company, Claro Americas can be found in just about every Central and South American country, plus the Caribbean. Certainly among the most cheerful looking phones out there. Photo by Leonel H. Ramos Chang
- Ecuador A decidedly less cheerful model, but Claro is still the lead operator in this country with almost nine million subscribers. América Móvil ran the company when it was known as Porta, but switched the name to Claro, which translates to "bright" or "clear" in Spanish. Photo by TProphet
- Back The Back Cover Photos
- Back Cover Photo #1 On the web, "404" and "missing" are pretty much synonymous, which means anyone halfway familiar with the net will be reading this sign as "Missing Hair Design" every time they walk past this place in Edinburgh, Scotland. Discovered by sarx, this is probably not the best marketing strategy for this establishment, even if it happens to be their address.
- Back Cover Photo #2 Reader Steve found a rather weird fact while Googling Bluffdale, Utah. It seems the massive NSA data center over there just so happens to have a road named "2600" heading straight to it. We have to assume this is a coded invitation.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 31!
$2600 Magazine - Volume 31, Number 2 (Summer 2014)
- Index - Collectables
- Watching the Watchers - Editorial
- Sabotage the System: Encryption as Surveillance State Monkey Wrench - Stating the need to use strong encryption and/or obfuscation technologies to protect your Internet data after the NSA spying revelations, by D. B. LeConte-Spink
- Crossover: Where Metal and Hacking Met and Mixed - Story of how heavy metal music influenced the hacking and BBS scenes in the 1980s, by Brett Stevens (Alief, Texas, Email)
- Telecom Informer - Torturing employees and destroying lives (and equipment) by being a corrupt telecom "manager," by The Prophet
- Fun With the Minuteman III Weapon System - Part 3 - Overview of the Airborne Launch Control System Holdoff Command (AHC) and stories of missile crews playing "AHC Chicken," and the potential to launch a missile via UHF radio commands?!, by Bad Bobby's Basement Bandits
- Fun With Data Entropy Attacks - Potential overlooked vulnerabilities with utilizing highly-compressable (low-entropy) files, or utilizing high data entropy to "jam" Internet data surveillance systems, by Spacedawg (Dublin, Ireland)
- Network Condom - Simple Python script to make a raw network socket connection (HTTP) to an IP & port to check if it's possibly serving malware, by Sh0kwave
- Code: NetCondom.py
- Yippie Ki-Yay: Social Engineering and Film - An observation that movies will often use a form of "social engineering" to engage or manipulate their audience, by Gregory Porter (Email)
- Hack Your House: Making the Most of Raspberry Pi - Simple Raspberry Pi project to control solid-state relays (ceiling lights, in this case) via the GPIO pins and CGI scripts, by Michael Post
- Code: gpio-activate.sh
- Code: turn-on.sh
- Code: turn-off.sh
- Code: turn-on.cgi
- Code: turn-off.cgi
- Corporate Security and Chinese Hacking - Lessons from the Mandiant APT1 Report on Chinese espionage targets and attack methods, by Jim L
- Hacker Perspective - by Tyler Frisbee (Email, YouTube Channel)
- Experiences of a Hobo Security Consultant - Article describing the author's time as a legitimate hobo performing street-level computer repair services and volunteering at second-hand stores, by eyenot
- "My Precious..." (Apple) - Discussing Ibrahim Balic's undocumented hack on Apple's developer portal, by lg0p89
- Letters - PUBLIC ADDRESS
- Further Questions - Yuval Nativ, RP, Daniel, Kevin, A curious person
- Article Feedback - The Professor, Estragon, Wolf Bronski
- Random Thoughts - Bill Miller, Sol, J Thompson
- Communications - Dave, Robert, Jerry
- Information -Tyler Frisbee, //j, Oliver, Chris
- Meetings - Brad, Richard Cheshire, Scott (Minnesota), David (Maryland), zenlunatic (Maryland), Stacy, Mike (Dallas, TX), Will (NameBrand) (Dallas, TX), Budo (London), Seymour (Sebring, FL), [Name Deleted], Jared (Seattle, WA), John (Wilmington, NC)
- Letters on Letters - Shocked998, Hunter, darwin
- The Digests - J, Varible Rush
- Critique - Chris, Sh0kwave
- Experiences - David, Screamer Chaotix, Pic0o, ghostguard, Margaret
- New Stuff - nico, Julia Wunder, Nick Grey, Charlotte & Jesse
- Hacking the SanDisk Connect Wireless Media Drive - Cracking the root password for the SanDisk Connect Wireless Media Drive to allow SSH/FTP access or remote filesystem (sharing) protocols, by ook
- Toilet Hacking - Covers a different type of hacking project; converting a "low-flow" flush toilet back into a standard "high-flow" one, by Toilet Fixer 555C
- "Good Afternoon. This is Your Fake AV Calling." - The dangers of malware and ransomware masking as an anti-virus scan - don't click anything suspicious!, by lg0p89
- Future Visions - Discussing how many (all?) of the great sci-fi novels and authors in the earlier part of the 20th century predicted many of the technologies that we have today, by Jason Sherman
- Closing the Schism Between Hackers and the Law - Discussing the proper way to notify a potentially hostile third-party to a security vulnerability which you discovered, by The Piano Guy
- Fiction: Hacking the Naked Princess - Chapter 0x0A - Chapter from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: Edward Snowden's revealing of NSA mass surveillance operations.
- Cover (Cover Info)
- Cover Inside Payphones of the World
- Mexico This phone clearly sees itself as the center of the universe. Found in the Zona Rosa district of Mexico City, there's even a warning that you're being spied upon. Photo by TProphet
- Ethiopia We're not exactly sure what the fate of these phone booths in Addis Ababa is, but there is a certain irony in their being closed off by telephone cord. Photo by Jon P
- Sri Lanka The goal is to have more than 40,000 of these CDMA-based public payphone booths throughout the country, aimed at low-income rural communities. They're far cheaper than landlines or mobile devices. Photo by Matt
- United States Found in the Pioneer Square district of Seattle, literally underground. You see, the sidewalks used to be 20 feet lower and they were condemned altogether in 1907, but soon found a home for various illegal activities. Perhaps even phone phreaking. Photo by Ryan Reggio
- Back Inside Middle Eastern Payphones
- Oman Seen in Muscat along with a thorough list of times where your phone conversation won't be disturbed by the sound of platform trucks. Photo by secuid0
- United Arab Emirates This model was seen in Dubai and is operated by Emirates Integrated Telecommunications Company, commonly known as "du." Photo by secuid0
- Saudia Arabia This was spotted at the airport in Jeddah. Despite its pristine condition, no sequence of button presses or twiddling on/off-hook yielded a display or dial tone. Photo by Estragon
- Israel We've never seen such a well camouflaged phone. There may not be much practical purpose in hiding a payphone, but it sure does look nice. Found in Jaffa. Photo by David Mizrahi
- Back The Back Cover Photos
- Back Cover Photo #1 Well, isn't this a surprise! Here's an image from the donation section of Senator John Cornyn's website, as found by RykVR. In addition to proudly proclaiming himself the second most conservative senator in the country, he apparently has fond eyes for hackers. Why else would he use that number instead of something more standard, like $2500?
- Back Cover Photo #2 Continuing with our political theme, did you know that there's a politician in Germany with the actual name of German Hacker? Turns out he's the mayor of Herzogenaurach (and popular, too)! We know many German hackers, but this is a first. Thanks to Casandro for this one.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 31!
$2600 Magazine - Volume 31, Number 3 (Autumn 2014)
- Index - TX
- A Tale of Many Hackers - Editorial
- The Demoscene - Code, Graphics, and Music Hacking - Very good overview of the "demoscence," a lesser-known computer subculture in which arts and hacking are combined, by Darwin (Moxee, Washington, David Melik, Email #1, Email #2)
- The Demoscene Original Article
- Bugging a Room With an IP Phone - Using a NEC DT700-series VoIP handset, SSH, and simple Linux audio tools to connect to any phone (with a hands-free microphone) on a network to record room audio, without anyone knowing!, by Malvineous
- Telecom Informer - How it's often hacker & phreaks who are at the heart of pushing today's computing and telephony innovations, by The Prophet
- Open Sourcing the Phone System Original
- Hack the Track: Put Your Money Where You 0wn Is! - Interesting article about the art of "handicapping" in gambling (horse racing) and how it relates to both the hacking and mathematics worlds, by water + Lasix = #1
- Linux Pwned - Just Not By Me - Overview of the Linux/Ebury SSH virus, what to look for, and how to remove it, by Edster @ 2600 Dublin
- Russian Hacker Pleads Guilty for Role in Infamous Linux Ebury Malware
- Bloke Accused of Linux kernel.org Hack Nabbed During Traffic Stop
- SSHD Rootkit in the Wild
- An In-depth Analysis of Linux/Ebury
- Writing Buffer Overflows for Non-Programmers - Good introduction to buffer overflow exploits for beginner programmers with simple examples using Metasploit and Python, by Ashes
- Buffer Overflows ECE 9609 / 9069: Introduction to Hacking
- x86 Assembly Guide
- The Art of Assembly Language Programming
- Remailing with USPS - Simple way to have the USPS "remail" (make your letter appear to be mailed from another address) for free, by Samuel A. Bancroft
- Forensic Bioinformatics Hacks - Author tells of his skills in bioinformatics research and software hacking to dispute a technical article by Duke regarding a new break-through cancer treatment, by Kevin R. Coombes (GitLab)
- Hacker Perspective - by James Kracht (Jim, Phoenix, AZ)
- Spam: Where Does It Come From? - Looking into which countries (appear) to generate the most amount of spam emails, by lg0p89
- Checkmate - Or how I bypassed your security system via the panic bar with a shoe string and hanging file folder, by DreamsForMortar
- Letters - RX
- Better Protection - Bill
- Electronic Editions - David, Eden, Wolverine Bates
- Sensitive Info - edsimonlocksmith, Mike & Gary, Jeff, n n
- Ignorance Campaign - Facebook Member, Ben
- Reader Response - 2kSysOp, Malvineous, Charles, StarckTruth, Kyle, Deb M. (Grand Rapids, Michigan), Pic0o, Allan, Rick Valdez, Richard, Alan
- Issues - Barrett D. Brown, [none given], Alan, David, Tim
- Gratitude - Justin, Red Pill
- Distributor Problem - Mike, S, Luke, Norman King, Anonymous, Angela, Wolf
- Inquiries - RT, Niels, Filip, Emperor Aslan, Sanusi Monday O., Bast, Cromwell, Sam (Switzerland)
- More on Meetings - Overall (Sãn Paulo, Brazil)
- HOPE X - HOPE X Writer #1, HOPE X Writer #2, HOPE X Writer #3, HOPE X Writer #4, HOPE X Writer #5
- Installing Debian on a MacBook Pro Without rEFInd or Virtual Machines - Quick overview of installing Debian (via an USB drive) on a MacBook Pro without the assistance of any Mac partitions or rEFInd, by The Skog
- Film Review: Die Gstettensaga: The Rise of Eschenfriedl - A Call to Class Consciousness for Hackers - Film review of Johannes Grenzfurthner's 2014 Austrian science fiction and fantasy film Die Gstettensaga: The Rise of Echsenfriedl, by Ishan Raval
- Xfinite Absurdity: True Confessions of a Former Comcast Tech Support Agent - Alarming stories from a former customer support tech at the world's largest cable company, by kliq
- The Buck Stops Here: Inside AT&T's Tier 2 Tech Support
- EFFecting Digital Freedom - Patent trolls, by Vera Ranieri
- Covert War-Driving With WiGLE - Overview of searching WiGLE for Wi-Fi access points to target for attack or other uses. Also includes a short tutorial on cracking WEP with Aircrack-ng, by 0rbytal
- Quantum Computers for Code Breaking - Very good overview of the steps required to defeat a DES-type block cypher using a quantum computer, by Dave D'Rave
- InfoSec and the Electrical Grid: They Go Together Like Peas and Carrots - by lg0p89
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: The Source Interlink debacle / HOPE X
- Cover (Cover Info)
- Cover Inside Selected Blue Payphones
- Slovenia From the Alpine town of Bled comes our first blue phone: a stark and futuristic looking model. Photo by Booth Lover
- Russia Seen in Moscow, this bright blue is more like something you might see in Argentina. Times have changed. Photo by Anastasios Monachos
- Panama Another sturdy model from Cable & Wireless. This one looks like it's weathered a few storms in its time. While this phone company is found all throughout Central America and in the Caribbean, blue isn't usually their color. Photo by Christopher Curzio
- France O.K., technically this thing isn't really a payphone, nor is it actually part of the public phone network. It's one of those ancient internal train network phones that you can find all over the world. This one was in an old train station in Pourcieux. It's rare that they're blue, however. Photo by M. Miller
- Back Inside Wide Ranging Payphones
- Croatia This bright and cheery phone is located just outside the bus station in Split. It is from provider T-Com and comes complete with dialing instructions and rates for some two dozen countries. Photo by Howard Feldman
- United Arab Emirates This was taken on the beachside boardwalk in Abu Dhabi. If you look really closely, you can see the Arabic and English numerals on the keypad. Photo by Casey Borders
- Cuba We've printed pictures of payphones from Trinidad before, but never from the one inside this country. Yes, there's a Trinidad in Cuba and their payphones seem to be in great shape. Photo by Ian Morse
- United Kingdom Then there are true mysteries, such as how anyone is able to even get to this payphone in Osmington Mills. It doesn't accept coins, which means the phone company never has to cut through the underbrush to collect money. Photo by Sparky Lou
- Back The Back Cover Photos
- Back Cover Photo #1 This was bound to happen eventually. With all of the CAPTCHA challenges that are out there, it was time for our number to come up, as it literally did with this download (ROMs for Asteroids Deluxe (rev 2) for the Atari emulator) that Alek Koss was in the middle of obtaining.
- Back Cover Photo #2 This terrific building was found by Shawn Boyko while driving past it in Cincinnati. It was actually a fire station until 1976 and now is used for offices. We think it would be a great clubhouse.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 31!
$2600 Magazine - Volume 31, Number 4 (Winter 2014-2015)
- Index - PROOF
- Tools for a New Future - Editorial
- Password Cracking in the Modern Age - Overview of modern computer password hashing algorithms and a look at cracking them with tools like John the Ripper and Hashcat, by Yuval Nativ (tisf) and Tom Zahov
- What Do Ordinary People Think a Hacker Is? - Some dumb bitch who thinks waaay too highly about themselves takes a look at "hacker" culture, by Kim Crawley (Toronto, Ontario, Canada, Twitter, LinkedIn)
- Hacker Culture A to Z: A Fun Guide to the People, Ideas, and Gadgets That Made the Tech World Don't pay for this shit...
- Decoding Hacker Culture with Kim Crawley The Tech Talks Daily Podcast
- Security Behavior - An idea for "behavior security," where a system will watch users in real time and if they do try to stray, then we can stop them, by Donald Blake
- Telecom Informer - Using low-cost GSM cellular network modules for agricultural and other resource monitoring, by The Prophet
- Format De-Shifting - Cool little hacks for downloading PDF files blocked (no "Print" or "Download" buttons) by PDF.js, by Peter C. Gravelle
- Simplocker Gonna Get'cha - A look at the latest Simplocker Android phone malware, by lg0p89
- Home Depot Hacks - An apparent Home Depot insider describes how to bypass their anti-theft devices, by DKN
- Leeching Music from YouTube for Fun, Learning, and Profit - Overview of a Python script to automatically download music videos from YouTube, strip the audio out, and burn that to a CD, by Synystr
- Code: youtube-get.py
- Recon on Disney's MagicBand - General overview of Disney's MagicBand, a NFC/RFID wristband used by Disney park and resort guests for payments and tracking purposes, by EndlessFapping
- Dissecting Disney's MagicBand
- Making the Band - MagicBand Teardown and More
- Inside the MagicBband... Hacker News
- MagicBand/MyMagic+ Identification Guide
- Creepy Tracking at the House of Mouse
- Inside MagicBand
- How Portable Can Wi-Fi Get? - Using a simple Microsoft router promo in a magazine as an example of new technology that could potentially increase the the likelihood of introducing an unlikely vulnerability, by The Piano Guy (Gary Rimar)
- Hacker Perspective - by Shadow E. Figure
- The Surveillance Kings: Who's Really Behind Who's Watching Us - Very eye-opening account of IBM's inter-connectivity with DARPA and hints of IBM's capabilities with respect to their surveillance of both employees and the general public, by DocSlow
- New Internal Slides Within IBM's Red Hat Explains "How Whiteness Works"
- IBM/Red Hat Whistleblower Leaks Internal, Racist, Anti-White Presentation
- Taking Your Work Home After Work - Idea to append "banned" data or files into a normal JPEG image so it will pass through a blocking firewall or email system, by gerbilByte (Mark C. Stott, U.K., Twitter, GitHub)
- Code: extract.pl
- Published Article in 2600 Magazine: Take Your Work Home After Work Original
- gerbtris Unrelated, but just plain cool... Tetris written in Bash!
- The Perils of Lackadaisical Updates - Examples of problems encountered when a large organization uses different version of software, and why it makes sense to upgrade or sync everything to the same standard, by lg0p89
- Letters - verdicts
- Curiosity - David and Sarah, Undecodable Name, Renee, Mel, Dan, Willie, Liraz, Blake, Thom, Antony, Alexander, Chris, Steve E., Bryan
- Deals - Article Writer, Sangamon
- Fun With Meetings - Stephen, Stephen, Null (U.K.), Richard Cheshire
- Some Facts - Anonymous, A Friend of Freedom in Cottage Grove, The 3rd Bit, DaRkReD
- Offerings - S&T, Bruce, Pic0o, Solomon B. Kersey
- Ideas - Blake, Evan, Efthimis, A, Tyler
- Rules of Publishing - R, Gunnar, Robert
- Article Comments - Jim L, Brain the Fist (Canada), David (Email), Alex W, Ghost Exodus
- More Observations - Steve, Jeffrey, sueicloud, Dusty, K, John, ibid 11962, Odd Erling N. Eriksen, Swamp, John, D, joshua, Vel Co
- Controversies - David T., Jessica Andreasen, Joethechemist
- Speech - Paschal
- Thanks - Anonymous
- Help Needed - John
- Injustices - Preston Vandeburgh, Justin L. Marino
- Crypto Systems Which Resist Quantum Computers - While mainstream algorithmic coding (encryption) systems are vulnerable to near-term quantum computers, it is possible to design coding systems which are more secure via the use of multiple valid keys, by Dave D'Rave
- The 21st Century Hacker Manifesto - A reworking of "The Conscience of a Hacker" in which government, corporations, other others look down on today's modern hackers, by Prisoner #6 (Michaleen Garda?)
- Phrack Editorial by Erik Bloodaxe in Phrack, Issue #48.
- EFFecting Digital Freedom - Net neutrality, by Vera Ranieri
- Are You the Consumer, or the Product? - Discussing how you are viewed as a "product," rather than a consumer, by large the (((tech companies))) - even if you think you're just a consumer, by The Piano Guy (Gary Rimar)
- Generating Phone Numbers - Python script that will scrape valid prefixes from www.allareacodes.com and generate every valid phone number within a specified area code, by Samuel A. Bancroft
- Code: generate.py
- Code: f0ne.sh U.S. phone number generator shell script by DERV
- Hacking dudley - Due to manufacturing flaws and lack of tolerance, dudley-brand combination locks really only have around 60 possible combinations!, by David Crowe
- Fiction: Hacking the Naked Princess - Chapters 0x0B - 0x0C - Chapters from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: We are at a pivotal point in history where we have an abundance of access to technology.
- Cover (Cover Info)
- Cover Inside Classy Payphone Booths
- Austria Seen on Danube Island in Vienna, this classic booth is as sturdy as you could hope for but rarely used, judging from the spider webs found inside. (But the phone works!) Photo by Richard Hanisch
- Greece While showing obvious signs of wear, this booth seems to be in it for the long haul. Found in Corfu near the old town square. The phone itself was in pretty good shape. Photo by Brother Franklin
- Peru There's something really classy about this fixture bolted into the stone on what looks like a really old street in Cusco. Not much of a booth, but the protection is implied. Photo by Mark
- Ukraine A quaint scene from Pripyat, where you'll soon discover it's rather difficult to find a phone or even a person due to the aftereffects of Chernobyl. The city was only 16 years old when it was abandoned. Photo by Ashes
- Back Inside More Foreign Payphones
- Malaysia #1 In addition to the stunning view, these payphones on Mount Kinabalu happen to be 3.668 kilometers above sea level (a fact noted on signs inside the booths), making them the highest known payphones. Photo by Bryan Rhodes
- Malaysia #2 "
- Switzerland This phone is above Grindelwald in the Bernese Oberland area in a cable car station at the summit of First. Now you know exactly how to find it. Photo by Marcus
- Portugal This old school phone, seen in Vilamoura, is the basic coin model that has been tagged and stickered by many as a traditional sign of respect. Photo by Robert Noack
- Back The Back Cover Photos
- Back Cover Photo #1 Now here is a building worthy of bearing our name. Spotted by Gonadvs Maximvs in Berkeley, California, this mighty complex looks down over the entire neighborhood.
- Back Cover Photo #2 We've actually gotten a bunch of pictures of this locomotive recently, but we liked the one from Jay Thomas the best. The train is run by Roaring Camp Railroad and runs between Felton and Santa Cruz, California. As you can see, it doesn't move too fast.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 31!
$2600 Magazine - Volume 32, Number 1 (Spring 2015)
- Index - [Array]
- Nous Défions Tout - (We Defy All Odds) Editorial
- So, You Want to Be a Darknet Drug Lord... - A hypothetical overview of setting up a clandestine website on the "darknet" and what steps would be taken by authorities if they tried to track you down, by nachash
- So, You Want to Be a Darknet Drug Lord... Original
- Hacker News Thread From March 24, 2022
- Darknet Diaries True stories from the dark side of the Internet.
- Out of the Box Survival - Part One: A Guide to PowerShell Basics - Introduction to Windows PowerShell by a Linux user, with a simple GUI login grabber as an example, by Kris Occhipinti (Metalx1000)
- Telecom Informer - Overview of the cellular phone infrastructure in Turkey and how much of it is surprisingly censored, by The Prophet
- Brazil's Electronic Voting Booth - Brief description of Brazil's digital voting booths, which are the same problematic Diebold/Dominion voting systems as used in other countries, by Overall (Brazil)
- Evolution of a Hack - The author was learning about SMTP servers and eventually wrote a series of Python scripts to automate sending spoof emails. He covers his story as the scripts get more advanced as he became more experienced as a hacker, by Uriah C.
- Code: mailFlood.py
- Bleeper - Downloading Full-Length Preview MP3s from Bleep - Overview of the author's Python script for pulling down an entire album from Bleep and naming the files using the correct artist, album, and track names, by Derek Kurth
- Code: bleeper.py
- The Enterprise, the Subverted PKI Trust Relationship, and You - A corporation setup a man-in-the-middle SSL inspection proxy in order to inspect traffic to "find leaks," buy may have reduced the security level of an otherwise secure network, by Mike
- Hacker Perspective - by metaknight
- WYSE Moves - Short article detailing common defaults for Wyse Xenith thin client hardware, including some potential security vulnerabilities with ThinOS, by Maven
- Office Talk or Social Engineering - Interesting take that using common "office jargon" is really a form of social engineering, by Gregory Porter (Email)
- Archiving ComiXology - Overview of the author's JavaScript project to automatically grab comic book images from the ComiXology website and convert them into a CBZ file, by Ook
- Code: comixology-cxt.js
- Letters - PONDERINGS
- Opportunities - David Wei, Happy Man, Amer, Christopher, Lee, Timothy Castro, J
- Idealism - Tom Cruise
- Responses - Estragon, Mistman the Magnificent, Neil N., ghostguard, David, Rob, Saskman, Delicious Cake, Russell Nomer
- Facts and Theories - Jay Jay, M.
- More on 2600 Meetings - Tim, Jim, Lou, Memo, Nolan (New Mexico), Matthew (Texas), Pic0o (Philadelphia, PA), TheGeek (Scotland)
- Issues - Richer Dumais, Bill Miller, gerbilByte, Craig
- Free Expression - StevieBohY, Joe, Rob, Joethechemist
- Inquiries - Joe, Josh (U.K.), Andrew, S, Chris, Ratish, Nick, Jon, Xaus, Josh, Adam, Brian, Milan, Brandon, stupedestrian, Brainwaste
- Tribute - Steve Mansfield-Devine
- McAfee Family Protection - Epic Fail! - As a final project for the author's network specialist class, he was to find a security software suite to analyze and ultimately to circumvent its security, by Brian Van Stedum
- Abusing the Past - Potential security vulnerabilities with hosting services which keep "old" servers online and only change the IP address when they update or move them, by Buanzo (Arturo Busleiman, Buenos Aires, Argentina)
- Hacking the HandLink Gateway - Overview of the HandLink WG-500P "hotspot in a printer" which is used to provide temporary Wi-Fi access. Includes default logins and how to generate your own vouchers, by secuid0
- HandLink WG-500P User Manual (3.6M PDF)
- EFFecting Digital Freedom - FCC Chairman Tom Wheeler led a vote in favor of strong net neutrality rules and delivered remarks on the importance of free speech online, by Parker Higgins
- Ohio Prison IT Security from the Inside - An apparent insider overview of the computer networks Ohio prisons use for their law libraries (LexisNexis), JPay, and commissary systems, by 5MEODMT6APB
- Hacking for Knowledge - The author's desire to understand how things worked, his unending curiosity, combined with insufficient funds, required him to repurpose cast-off computer hardware for experimental uses, by Jerry
- Linux Containers for Event Training - Overview of the author's ISLET system for teaching Linux-based software with minimal participation effort by using Linux containers, and satisfactorily addresses each item in the aforementioned list of problems, by Jon Schipp (Tampa, Florida, Email, Twitter, GitHub, Facebook, KC9SKH)
- Are Smart Meters the End-All?; or, How I Learned to Love the IoT - Hacking "smart meters," which are used for things like electrical power monitoring, may be hackers next big target, by lg0p89
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: Sony blaming the attack on their systems on "an army of hackers from North Korea."
- Cover (Cover Info)
- Cover Inside Island Payphones
- Taiwan Seen in the Maokong District of Tapei, this payphone, like all in this city, is also a free Wi-Fi hotspot. Photo by Matt Ranostay
- Tahiti It may look like a painting, but we can assure you this phone is very real and functional. Photo by nfltr8
- Japan This phone was found on the country's largest island of Honshu on the road side of Nagano Prefecture and it's still in pristine condition. Photo by RayD
- Fiji Discovered on Taveuni Island, this phone looks like it's prepared to attack anyone who offends it in any way. Photo by Daniel Eather
- Back Inside Free Payphones
- France This free phone was found at the bottom of Mont Saléve. It looks as if its dialing options are a bit limited. Photo by Jonathan Dumont
- Austria Ski resorts are apparently a popular spot for free phones. This one in Nassfeld is programmed to dial a local taxi. However, it can be defeated with Touch-Tones through the mouthpiece. Photo by Richard Hanisch
- United States Now this is a great service (free local calls) offered at this payphone in Rosburg, Washington by this friendly rural phone company. Photo by ZombieRaccoon
- Switzerland Technically, this is a free payphone, since you can make calls without paying, but you would really be annoying the people who run the backpacker hotel it's a part of. Photo by Nicolas RUFF
- Back The Back Cover Photos
- Back Cover Photo #1 Yet another proud-looking building worthy of bearing our name. Seen by Nodechomsky in Memphis, Tennessee, this was apparently taken on one of the rare days that our pirate flag wasn't flying.
- Back Cover Photo #2 This image has been sent to us a number of times over the years, so we've finally decided to print it. As noted by Johannes Grenzfurthner, this was Hitler's plane, as captured in the 1935 propaganda film Triumph of the Will.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 32!
$2600 Magazine - Volume 32, Number 2 (Summer 2015)
- Index - Checklist
- Old and New Together - Editorial
- I Tapped That... Tapping a Nationwide Telecommunications Network - The author takes us on a "theoretical" journey of what it takes to data tap a modern (4G/LTE) wireless communication network, by E Squared
- Use Your 3D-Capable TV to View 3D Stills of Your Own Making - Overview of the author's project which is a Python+GIMP script to produce a 3D side-by-side image from two JPEG images, by TFE Guy (a.k.a. The Man)
- Code: 3DMaker.py
- A Phone Story - Author's story of getting "free" phone calls from payphones back in 1968 by disabling the coin collect/coin return wire and him eventually paying the phone company back, by Anonymous
- Telecom Informer - Overview of remote mobility zones to provide cell service in very remote areas, by The Prophet
- Chiron and Me: Hacking Astronomy - Story of the author being asked by New York astrologer Al H. Morrison to compute an ephemeris for Chiron using 1980s Timex-Sinclairs and library books, by Eve S. Gregory
- Nigrum Libro Interceptis - Overview of function overloading by using LD_PRELOAD. Includes examples to crack the time-lock of PV-WAVE and how to steal passphrases from SSH, by xorcist
- Code: main.c
- Code: hack.c
- Code: hack2.c
- Code: fakedate.c
- Code: wave.sh
- Code: peekaboo.c
- Hacker Perspective - by Pic0o (Philadelphia, Pennsylvania, Twitter)
- Library Security - Tips from a software library writer on writing secure code, and his idea that paying the coders will act as an incentive for them to maintain their code, by The Slakker
- Decoding a Carrier Pigeon - An attempt to decode a one-time pad message from a World War 2 carrier pigeon which was found in 2012, by Joseph B. Zekany
- Letters - DIAGNOSTICS
- General Questions - Keshuv, Derneval, Josh, Saskman (Canada), Ibid 11962, marie, Jonathan, Doug, Saleem, Pichaya (Thailand), Please15, Robert, Steve, S
- Injustice - Jason
- Curiosity - WorWin, J, stupedestrian
- Meetings - Marcelo, jk31214 (Pennsylvania), Syn Ystr (Lansing, Michigan), Michael, Tyrion High Elf
- Artwork - Mike
- Deep Thoughts - Bill Miller
- Help - John, Anonymous
- Contributions - BTC, Lewis, Info, RON (Ronald Gans), Mined Phreak, Wolverine Bates, Wolverine Bates, Alan
- Deeper Thoughts - Bill Miller
- Concerns - NO-OP, David, Si M, Caz, Solomon B. Kersey
- Sad Tidings -AC (Partner)
- Replies - David Crowe, Captain Cautious, Ghost Exodus, Tia
- Still Deeper Thoughts - Bill Miller
- Trouble - Juan
- Attitude Adjustment: How to Keep Your Job - The author's request that you follow your IT department's rules even if you don't respect them, and treat your IT people like you'd want to be treated if you have their job, by The Piano Guy (Gary Rimar)
- Out of the Box Survival - Part Two: A Guide to PowerShell Basics - Introduction to Windows PowerShell by a Linux user, with a simple GUI login grabber as an example, by Kris Occhipinti (Metalx1000)
- EFFecting Digital Freedom - Creepy web tracking tricks, by Cooper J. Quintin
- Coding as a Foundational Skill - An alternate take on the "learn to code" mantra which the author feels is overstated, and over time, further degrades the ability to do our own work, by wino_admin
- A Plea for Simplicity - On the dangers of software code bloat, overly complicated systems, and the seemingly lack of competent coders creaping into modern computer systems, by Casandro
- Ransomware: Still Active and Looking for Victims/Volunteers - Overview of some successful ransomeware attacks in 2015 and tips to avoid being a victim, by lg0p89
- Fiction: Hacking the Naked Princess - Chapters 0x0D - 0x0E - Chapters from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: The fusion of "old and new" technology
- Cover (Cover Info)
- Cover Inside Payphones of North, Central, and South America
- Canada Yes, a desk phone can be a payphone, if it has the right attitude. This one does. It can be found in the lobby of the Manning Park skiing lodge in British Columbia. Photo by Alex W.
- French Guiana Seen on the infamous Devil's Island (location of a penal colony for 101 years and now home to a spaceport), this is one of the most jungle-themed phones we've seen yet. Photo by Bruce Robin
- Bolivia This yellow card reader phone can be found at Viru Viru International Airport in Santa Cruz de la Sierra. COTAS is a phone company cooperative located in Santa Cruz. Photo by fuctmonkey
- Mexico We close with another desk phone acting as a payphone, this one found in the lobby of the Sheraton Maria Isabel Hotel in Mexico City. It also takes Telmex cards. Photo by Andrew Rich
- Back Inside International Payphones
- Lithuania Seen in the capital Vilnius, this spanking clean blue box is ready for action. We wonder how much it gets. Photo by John Klacsmann
- Austria Like most things in Vienna, this payphone is all about style. Note the colorful buttons and how they contrast with the more subdued and older tones surrounding them. Photo by John Klacsmann
- United Arab Emirates This payphone was found in the Gold Souk of old Dubai, where everything glitters of gold. Strangely, it seems to be made of only base metals and plastic. Photo by Howard Feldman
- South Korea This old school payphone (and equally old school booth) can be found at the 38th parallel at the DMZ border with North Korea. Photo by Bruce Robin
- Back The Back Cover Photos
- Back Cover Photo #1 There's just so much here. A typewriter repair shop in this day and age? And they sell them too? An ultra-elite address of "1337" to boot? This was found in Lansdale, Pennsylvania by a reader who prefers to remain anonymous. We hope the business doesn't mind a little publicity, however, and that this form of really old technology keeps them going.
- Back Cover Photo #2 So apparently the air freshener Glade has exactly 2600 uses, but they only tell you this if you're watching television in Argentina, as our reader Arturo "Buanzo" Busleiman was. Could they have picked a more difficult-to-read font for our name?
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 32!
$2600 Magazine - Volume 32, Number 3 (Autumn 2015)
- Index - PERCEPTIONS
- The Hacker Image - Editorial
- A Primer on Home Automation (and How Easy It Can Be) - Story of setting up a Harmony Ultimate Home from Logitech for a computer-controlled home automation project, by Ilyke Maasterd
- PS3BluMote This application allows you to use the official Sony PS3 Bluetooth remote control (and other compatible remotes) within Windows.
- Dangerous Clouds - The dangers or storing all your data in remote cloud-based systems and how they often collect more data than government systems, by Donald Blake
- Unexpected Denial-of-Service - Story of an admin who wrote a little program to check multiple systems after a upgrade, but ended up DoSing them when they spawned a JVM until a HTTP exception occurred, by J. Savidan (France)
- A Convenient Method for Cloud Storage with Preserved Privacy - Overview of using cloud-based services like Dropbox for storing files, but only if they are properly (client-side) encrypted, by Alva Ray
- Telecom Informer - Discussing prison phone systems and contraband cell phones, by The Prophet
- Ashley Madison Military Sites - Extracted .mil domains from the "Ashley Madison" website hack, though most are clearly fake...
- The Technology at QPDC - Overview of the phone, commissary, law library, and door control systems at Queens Private Detention Center which is owned and operated by The GEO Group, Inc., by mmx3
- Open-Source Repository Abuse - Discussion of some recent actual (and theoretical) attacks as a result of information posted (SSH keys, passwords, etc.) to open-source software repositories like GitHub, by Terrible Doe
- My Voice is My Key - Story of a person hired to test the physical security of a company who gained access to secure area with just an empty cup and chit-chatting with a receptionist and security guard, by gerbilByte (Twitter)
- Hacker Perspective - by Brainwaste
- Fun With Billing Forms and International Debit Cards - A potential major flaw in online billing forms whien using names of cities in the United States equal to foreign countries (i.e. Paris, France equals Paris, Texas), by musachi42
- Going Nuclear - A Tale of Revenge - Story of getting revenge on a person who harassed the author's wife for helping a disabled person. End result: Don't be evil!, by 2dedd54f25ae2730225e6f1b8968fda52f0831ce
- Leaked Documents Department - Internal IRS document still referencing "diskettes" and noting that screensavers can be "illegal software."
- Malware Attacks - Leave Those [Banks] Alone - Overview of some of the malware attacks, like Tinba, targeting banks and personal information of the account holders, by lg0p89
- Letters - CONCEPTIONS
- Furthermore - nfd9001, Brian from South Dakota, Pic0o, Buanzo (Argentina), Edson+, Marco, Brainwaste, Nick
- The Word on Meetings - Marthalamew, TheGeek (Glasgow), Tom (Alabama), Magacimaga (Turkey), Faqanda (Israel), Flipchan (Gothenburg, Sweden), TheGeek, Dennis (The Netherlands), Ex Tenebris Lux/Semper Technocrazy (Chico, CA), Philip (Pennslyvania), Richard, (Australia), Rebecca (Tacoma, WA), Sean, Rebeeca (Tacoma, WA)
- The Fight for Justice - John, token, HJT LED-Professionals (Germany), Jesse McGraw (Ghost Exodus), Dave
- On Payphones - Gerald (Cocos/Keeling Islands), Scott
- Queries - sm, Bill (Steward, IL), Daniel L, nychacker, Bhaskar Das, Adam, Piper, Steven, Captain Cautious
- Kindle Karma - Josh, Steve T. in Manhattan, Saskman
- Weird Mail - A Subscriber, [We Are Not Printing Your Name], Red-Pill Guy
- New Stuff - Chris, B, James Raven
- Advice Needed - JEDLUP, jennifer
- Digital Editions - Bertram, Eric, Ruddy
- Turning Point - SideFx, A Paranoid Newbie Hacker Wanting to Find a Place to Belong
- Mr. Robot - A Ray of Light in a Very Dark World - Discussion on USA Network's Mr. Robot and how it actually portrays realistic hacking - and the hacker community - in a decent and honest light, by Evil Corley
- Pilot Script
- Mr. Robot Sucks LOL!
- Ryan Kazanciyan Technical consultant who goes over some of the show's hacks in detail.
- Cruising the Wideband Spectrum - Combine a RTL-SDR with old analog communication receivers for your SIGINT setup, by Agent T.W. Lee / Interzone Intelligence (Thomas Icom)
- EFFecting Digital Freedom - Let's Encrypt: scaling HTTPS and TLS to the whole Internet, by Jacob Hoffman-Andrews
- The Dawn of the Crypto Age - You can make a difference in the new era of human advancement (and the crypto-age) by joining the league of cypherpunks to improve and promote the world of cryptography, by CANNON C.
- Account Hack: Anyone Can Be a Victim - The author had his PayPal account compromised and was able to track down who actually did it by using Google, by lg0p89
- Fiction: The Stars Are Tomorrow - by LexIcon
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: If there is one theme that we seem to have been locked into from the very beginning, it's that of preserving, correcting, and maintaining the image of hackers.
- Cover (Cover Info)
- Cover Inside European Payphones
- Croatia A standard phone booth found in the small car-less village of Valun on the island of Cres. Photo by Mandrappa Kurelek
- Luxembourg Found in the mountainous village of Vianden, this phone booth looks like it's attached to a mountain. Photo by Mikel Shilling
- Poland Yet another small town booth found in Krynica. It's wheelchair accessible with no door, a ramp, and handlebars inside. A sticker says "Telefon Dwukierunkowy," which means "two-way phone" (you can make and receive calls here). Photo by Dariusz Dziewialtowski-Gintowt
- Greece Yes, you guessed it - another small village with a payphone. This one is Plakias on the island of Crete, right by the water. There's some kind of connection between old, scenic villages and working payphones. Photo by Mandrappa Kurelek
- Back Inside Spanish Speaking Payphones
- Mexico Found in Puerto Palomas in the state of Chihuahua, this phone clearly has its share of traffic and is in pretty good shape. Photo by Fred Atkinson
- Mexico This colorful Wi-Fi phone was spotted in Mérida in the state of Yucatán and doesn't appear at all worse for wear. Photo by carlos duarte
- Cuba An ETECSA (Cuban government's telecommunications enterprise) payphone seen in Havana. It doesn't appear to take coins. Photo by Lee317
- Spain Another pristine payphone model found in Rota in the southern region of Andalusia. Photo by Fred Atkinson
- Back The Back Cover Photos
- Back Cover Photo #1 Now this is the kind of joint we all should stay in at least once. Hell, maybe we could even have a convention here! The person who submitted this gave us absolutely no details on its location (thanks for that), but since they sent it from their phone, with a little detective work we figured out it was in Chicago. We can feel this place calling to us. Tripadvisor raves "WORST hotel ever" and "Horrible and Disgusting," but we believe those are just clever ploys to try and keep us away.
- Back Cover Photo #2 Seen in Brighton, Michigan by Gary Rimar, this intersection is particularly great because it leaves out the word "Road" on each sign, making it possible for all sorts of jokes and allusions to work. We'll leave that as an exercise for the reader.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 32!
$2600 Magazine - Volume 32, Number 4 (Winter 2015-2016)
- Index - TEACHINGS
- The New Normal - Editorial
- The Best Way to Share a Treasure Map - General overview of Forward Error Correction (FEC) codes and discussion of the author's "Treasure Map" program which will encrypt and split a file into multiple parts so no one person can recreate the original file without the other parts, by Mike
- Code: tmap.py
- USBkill - A Program for the Very Paranoid Computer User - Overview of USBkill which, when installed and running on your computer, will monitor the USB bus of your system and shut down the system if it detects any changes to your attached USB devices, by Aaron Grothe
- Code: USBkill-patch
- Circumventing Chrome and Firefox's Third-Party Cookie Block - Use a simple <meta> tag redirect scheme to allow a third-party cookie opt-in as the browser will see the user has visited a secondary URL and the cookie is allowed to be written, by Armando Pantoja
- Telecom Informer - Overview and history of modern digital cellular phone technology, by The Prophet
- Pushing the Limits - Story of being a beta tester for the Microsoft Xbox 360, Kinect, and other software programs, by [No Author Given]
- Romeo Tango Oscar - Story of being a Radio Telephone Operator (RTO) in the U.S. Army while stationed in Vietnam in 1969, by 2-6 India
- Yull Encryption - Overview of the Yull encryption scheme which uses a key that is not fixed, so you can use a file as a key, by Ronald Gans
- A Brief Cryptanalysis of Yull - A brief but technical overview of the Andromeda cipher used by the Yull encryption program, by Erebos (Simmons)
- Hacker Perspective - by Kevin Patterson
- Militiamen Face Charges in California Is this him?
- How to Get Free Gogo In-Flight Internet Access - Bypass overpriced Gogo in-flight Internet access on flights by installing an app to view the "free" entertainment titles available, which apparently logs your MAC and allows continued Internet access, by Big Bird
- Accessing Admin Privileges: A Quest Through One of Mac's Backdoors - By booting a Mac in single-user mode, one can reset passwords on an admin account without knowing the admin password - a potentially huge security hole, by NerveGas Jr.
- Perspectives on Cyber Security - Looking at the way cyber security has changed throughout the digital age, but hasn't really increased our security, by Super Ells
- The Splotchgate Saga
- 2600 Accused of Using Unauthorized Ink Splotches
- Hacker Magazine 2600 Extorted for $714 Over Ink Spot Pic Copyright Troll Doesn't Own
- Off The Hook Sept. 9, 2015
- Letters - Proclamations
- Ideas - Name Deleted, Hugo L., NerveGas Jr., jim
- Article Feedback - Josh, Smiley McGrouchpants, Webspider, Derneval Cunha, Phreak480 (Long Island, NY), Edgewater Sean, James E. Anderson (Cypher2), John
- Humble Requests - Vipin (West Delhi), The Prince, Jacob, L., Kalyan (Nepal)
- Meeting Mania - Mike (Melbourne, FL), Roo (Houston, TX), Ken (Canada), pi
- Splotchgate Comments - Matthew, Bill, Monday
- Random Thoughts - Tommy, Tommy, Tommy, Tommy, Tommy, Tommy, Tommy, Edward T, [phone number deleted]
- Experiences - Mike, David (Canada)
- Suggestions - Emilie, Toby
- Observations - Code Jester, William R. Epp, metal_cutter (Oklahoma), Vernon
- Questions - Arthur, Robin, s, Owen, Mike M (Canada), Lucio, jeffrey, Rob
- HOPE Tickets - Jalil, Vladimir, Dan, S., Lauren, Robert, Melissa
- Hackerspaces: A Definition - Short little story about a person starting their own hackerspace in Florida, by RAMGarden (Joshua Pritt, Melbourne, Florida, LinkedIn, Melbourne Makerspace)
- You Gotta Learn From This, Kid - The author discovers a potential cross-domain credential leakage bug while using simple PHP auth variables, by Buanzo
- The Limits of Open-Source Hardware - Addressing the "elephant in the room" problem that many popular open-source hardware projects rely on closed or secret hardware designs, by Monican
- EFFecting Digital Freedom - Defending privacy on the roads, by Dave Maass
- Rewriting History - Good overview of some useful tools for saving and archiving entire websites and information on the Web Archive file formats, by Steffen Fritz (Stuttgart, Germany, Email, GitHub #1, GitHub #2)
- The Herculean Task of Making a Documentary on the History of Computer Hacking: Part 1 - Author's story of the process involved in trying to make a proper hacker video documentary, including interviewing 22 hackers, by Michael Lee Nirenberg (Brooklyn, New York, DOB: 02-17-1978, Twitter, IMDb)
- Fiction: Hacking the Naked Princess - Chapter 0x0F - Chapter from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow:
- Cover (Cover Info)
- Cover Inside Worldly Payphones
- Italy Seen on the island of Capri, this is a standard Italian phone, usually not spotted in such elaborate housing. Photo by Paul
- Australia This brightly colored phone was found on Fraser Island, where humans have lived for over 5000 years. Clearly, they've learned how to keep their phones clean. Photo by SirBif
- Peru This model, discovered in Cusco, is about as old school as you can get. The shoelace around the handset to keep it from hitting the ground is an especially nice touch. Photo by Jessica Otte
- Brazil This phone, believe it or not, is in a very nice part of São Paulo. Even more unbelievable is the fact that it still works. Photo by Renato Leon Bourdonv
- Back Inside Payphones From All Over
- Malaysia Found in the capital city of Kuala Lumpur, this payphone apparently once brought bad news to somebody who didn't take it very well. Photo by Charlotte White
- Morocco Two phones in Marrakeshh - a standard no-nonsense coin-accepting payphone and a curvy stylish model that only takes cards. Photo by Howard Feldman
- Israel Seen inside the Old City of Jerusalem with the Western Wall and the Al-Aqsa Mosque atop the Temple Mount in the background. It doesn't get more peaceful than this. Photo by Bavs
- Turkey Where thoughts naturally turn to dolphins. Seen in Istanbul, but apparently they exist all over the country as we've gotten multiple submissions of these things. Photo by Peter Vibert
- Back The Back Cover Photos
- Back Cover Photo #1 Only in Japan would you be able to find food containers that are somehow related to UNIX. There's so much potential here. Thanks to Randy Frank for sending this in, as well as for placing this on top of a very special television set in order to make this shot even more memorable.
- Back Cover Photo #2 This may just be the coolest street in all of San Antonio, Texas, as discovered by Abel Lopez. Let's hope its residents realize just how lucky they are.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 32!
$2600 Magazine - Volume 33, Number 1 (Spring 2016)
- Index - HYPOTHESES
- The Powers That Want to Be - Editorial
- Scraping for Cache, or It's Not Piracy If You Left It Out in the Open - Shell script to scrape Google cache to retrieve a McGraw-Hill textbook and compile the downloaded image files into a single PDF, by Charlton Trezevant
- Code: scraping-for-cache.sh
- Hacking Using Parse Database Injection - Potential method for hacking into a client's Parse database via hidden elements with the HTML code of the web page, by Evan D'Elia,
- Hardware Hacking - Protecting Dev' Board I/O by Hacking an Alarm Panel - This article explores some of the basic methods for interfacing such digital and analog input/output ports with external signals, and details a cost-effective hack using any alarm panel for obtaining suitable protection without costly PCB layouts, by Sarlacii
- Telecom Informer - Overview of the techniques and politics of fiber cable splicing. Rick sounds cool, by The Prophet
- My President Twitter Bot Experiment - Overview of an experiment using a fake Twitter account (@CFKResponde) that responds using a custom made PHP/MySQL chatterbot in order to effect Argentina democracy, by R.B. (Roni Bandini)
- Defense Against the Black Arts of Forensics - General overview of warm- and cold-boot attacks on full-disk encryption and other tips to help defeat hard drive or memory forensics, by Alex
- A Plan 9 Primer - General of the Plan 9 operating system which was created by Bell Labs in the 1990s and is still being used by hobbyists today, by B. Boehler
- Chesslin - A playable chess engine in only 256 bytes of x86 assembly!, by Baudsurfer / Red Sector Inc.
- Code: chesslin.asm
- Exploiting HTML - Making Your Browser a Vegetable - Using JavaScript to constantly open a new website in a new tab, causing a constant flow of new tabs, or windows, to open - so many that you would not be able to close them faster than they opened, by Dent (Email #2)
- EXIF Location Recon with Python - Several example Python script to read Exchangeable Image File Format (EXIF) and GPS data in the embedded metadata of certain image file formats, by Michael L. Kelley, Jr.
- Code: Listing1.py
- Code: Listing2.py
- Code: Listing3.py
- Hacker Perspective - by Ghost Exodus (Jesse William McGraw, MySpace)
- Eleventh Graders and Nuclear Bombs - Story of a technology teacher at a New York City school who tortures his students by letting them read $2600 articles (LOL), but may have found a future nuclear physicist, by revx
- "Which Do We Prefer: Neanderthals or Hackers?" - Arguing we should reward hackers who help us, and stop the Neanderthals who want to leave us vulnerable to security and privacy breaches, Paul Abramson
- One Little PIG - PIG (which can be understood as Packet Intruder Generator) is a Linux packet crafting tool. You can use PIG to test your IDS/IPS among other stuff. PIG brings a bunch of well-known attack signatures ready to be used and you can expand this collection with more specific things according to your requirements, by Rafael Santiago (Rio de Janeiro/São Paulo, Brazil, GitHub)
- Password and Mobility Security: Something Needs to Be Done - Discussing the fact that very few people have proper security enabled on their mobile devices and how much safer everyone would be if people took this into consideration, by Stephen Comeau
- Letters - PEER REVIEW
- Being Published - Jim, R, M.E., Keith, Denis, Fred, Maxie, R, Phil, Nanjemoy, Michael, Jim, stupedestrian, Jason, Thomas
- Observations - D1vr0c, Mark (Robbinsdale, MN), k0k0mo, nuclear.decay, P, blockeduser, Jim L, D1vr0c, D1vr0c, James, Dave, Metaknight, Sypherone (James Anderson), John, RAMGarden
- A Breach of Note - Estragon
- Thoughts of HOPE - Larry, Scott, Sequoia, Dan, Daniel, Jason
- Just Asking... - John H., flames, Tom, sergio, JRJ, S. Mateen, Florin_Ercu, KingBoogieSwag
- News from Meetings - Pablo 0 (Buenos Aires), Fernando (Switzerland)
- Gratitude - Me
- Another Solution to the USBKill.py Problem - A follow-up to "USBkill - A Program for the Very Paranoid Computer User," here is the solution used in Ninja OS, a live operating system designed for USB drives, by Jack D Ripper
- Code: scripts_drivewatch.sh
- Code: parachute.sh Includes systemd service files.
- Software Validation - Overview of some simple shell commands to help you verify the integrity of system files via their checksums, by Ben Kenobi (Email #2)
- EFFecting Digital Freedom - DRM law keeps copyright stuck in the past, by Elliot Harmon
- Reconnaissance at Spa World - Overview of the electronic Unikey locks used by Spa World in their locker room, by The Piano Guy (Gary Rimar)
- My Local Weather Observations - The author's AcuRite Acu-Link Internet Bridge contains a "hard-wired" link to a domain name no longer under AcuRite's control, and the potential dangers with these types of settings, by The Knight Owl
- Fiction: The Bee in Van Pelt Park - by Marshall Edwards (Kansas City, Missouri, Twitter, Tumblr)
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: The dangers of Apple being asked to bypass their OWN security by the FBI.
- Cover (Cover Info)
- Cover Inside Global Payphones
- Italy We don't often see banks of payphones anymore, but this one found in an alley in Venice is well worth remembering. Photo by Michael Wagner
- Israel Looks like we spoke too soon. This bank of phones, found in Tel Aviv's Central Bus Station, is even bigger. Photo by Nily Harel
- France Seen at Charles de Gaulle Airport in Paris, this model comes complete with an incoming phone number! Photo by SuperD
- Turkey Discovered in the backstreets of a cool neighborhood in Istanbul, this phone (and certainly the booth) looks like it's been through a great deal over the years. Photo by J.D.
- Back Inside Payphones of North & South America
- Canada This phone is in Lansdowne, Ontario, Canada and is operated by the independent Lansdowne Telephone Company, which clearly doesn't believe in payphones. Photo by Christopher Anderson
- Mexico One of the few payphones left in Mazatlán, which is in the state of Sinaloa. Photo by Tom
- Costa Rica This model, complete with an incoming phone number, was found on top of a random hill in the Playa Pavónes around 20 kilometers from the nearest paved road. Photo by nathan
- Argentina Spotted in a hipster bar in the Villa Crespo district of Buenos Aires, this payphone looks almost portable. Photo by John Skilbeck
- Back The Back Cover Photos
- Back Cover Photo #1 A note to readers: when your car hits that magical 2600 mark, please take the time to slow to a stop before snapping a picture for us, especially during rush hour. At least Robert Ludvik was listening to Radio Študent in Slovenia, one of our favorites.
- Back Cover Photo #2 When Mr. Robot showed our website in a flashback last year, they did a really good job making it appear as authentic as possible, complete with a 1990s Netscape screen grab. Here's the code from our page that protagonist Elliot grabbed and modified as a kid. We trust his interest in Atari 2600s was a coincidence - or a joke. Thanks to SM for capturing this.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 33!
$2600 Magazine - Volume 33, Number 2 (Summer 2016)
- Politics Comes Calling - Editorial
- Index - LINEUP
- Pre-Surveillance of Law Enforcement Using Targeted Advertising - Idea to use targeted advertising to determine if and when law enforcement office are using public search engines to check up on you, by Deflagrati0n
- Abandoned Routers: Forgotten, But Not Gone - Security vulnerabilities in open Wi-Fi network with routers still set to their default settings, by musashi42 (Las Vegas, Nevada, Twitter, GitHub)
- Card Transactions Explained - Detailed overview of what takes place during an ATM card transaction, including the back-end banking software, by Donald Blake
- To Hack an Uber - The Uber app uses the IMEI of the rider's phone for verification, and it's possible to easily change the IMEI with a free app to appear to be a different user or obtain "one free ride,' by Armando Pantoja
- Telecom Informer - Those damn political robocalls during the election season, by The Prophet
- Hacking Malaysian Routers - Large programming and scanning experiment to check the security of Internet routers in Malaysia. Be your own NSA!, by Keith
- Nigrum Libro Interceptis: Secundae - Overview of the Jynx-Kit userland rootkit which uses LD_PRELOAD to intercept relavant filesystem calls in order to hide files or directories, and how to "scrub" environmental variables to hide its use, by xorcist
- $35 Hacking Machine - Overview of setting up a "Hackintosh 2600," which is a Raspberry Pi 2 running Privacy Enhanced Linux as a low-cost hacking machine, by InsideJob
- Privacy Enhanced Linux
- First Boot: Privacy Enhanced Linux 64 for Raspberry Pi 3 (YouTube)
- privacyenhancedlinux_9-11.img.gz Default user password is pi and root password is debian
- privacyenhancedlinux_murdock.img.gz
- Privacy Enhanced Linux for Pi 3 Update HDMI 1080p Edition (10.3 MB firmware partition ONLY, keep your data)
- Accidentally Logging in as Admin - Story of a work-related website implementing unsecure Visual Basic Script login forms, the validation for the login was done improperly on the client side, by Metalx1000 (Kris Occhipinti)
- Hacker Perspective - by Screamer Chaotix
- Frequency Inside the hacker mind.
- Gaming Ingress - Overview of Ingress augmented reality mobile game and how it determines the user's location and potential ways to spoof or exploit this, by ~Me
- Learning Hacking via MinecraftEdu - Using the MinecraftEdu system to get kids interested in the concepts and logic needed for software programming languages, by KingV
- Typing Fractions in Emails and Text Files - Using the proper ITU telegraph regulations to send numerical fractions in text, emails, or even Morse code. (Example: one and a half would be: 1-1/2), by The Cheshire Catalyst
- Letters - GLORY
- Hacker News - J (Podcast Link)
- Hacker Queries - general.bills, Lorena (Spain), Eric, Chris, Vaseleos, The Drunken Sniper ITA, hhlkjh, Mark
- Hacker Mentality - Laughing Man, Prozac Porridge, James, Paulie, Token
- Hacker Gatherings - Michael (Wisconsin), sfn (Germany), Jr., Coolest J (Greensboro, NC), David, MINDustry Official (Toronto, Canada), The Forgetful Buddha (Washington, D.C.), null (Leeds), A (West Lafayette, IN)
- Hacker Followups - Natalie, Ben
- Hacker Observations - Bill, Stan, spencercarterfortworth, Pietro, rhydin, reply, Nick, Stewart.T, Jim, Anonymous, Darren, PG, A Modern Day Human Rights Activist (Yellowknife, Canada), Ghost Exodus
- Hacker Requests - h., Paul, Jim, Ana (Brazil)
- Hacker Targets - Lisa, Shaf, Chris, Loretta Haines, Mary Burns, Debbie Mayer
- Hacker Offerings - Jan (Belgium), Martha, Mogar
- Surfing the Web Safely and Anonymously: Experimenting with Whonix Anonymous Operating System - Overview of installing and experimenting with the Whonix Anonymous Operating System, which is based on Debian and sends all your traffic through the Tor network, by Jim L
- How I Socially Engineered a Job - Story of leaving a voicemail message for a company's recruiter after missinterpreting their initial job offer call, by Oddacon T. Ripper
- Why We Need Privacy Rights - Why we need privacy in real-life and on the Internet and should always fight for privacy and freedom for everyone, by Daelphinux
- EFFecting Digital Freedom - The patent reform gridlock: Let's pick bigger fights, by Elliot Harmon
- Free Windows - A way to get a clean, free install of Windows 10 using their Media Creation Tool and AutoKMS tools, by fooCount1
- The Top Ten Reasons Why Hackers Should Get a Ham Radio License - List of reasons why hackers should get their amateur radio licenses and utilize the airwaves to test out new, cutting-edge technology, and prevent them from being sold off to corporations, by Chris (AB3YS)
- Fiction: Hacking the Naked Princess - Chapters 0x10 - 0x11 - Chapter from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: Evil Corley is having a complete mental breakdown because there are still politicians who wish to put the citizens and country FIRST, and not the One Percent, the World Economic Forum, or (((globalism))).
- Cover (Cover Info)
- Cover Inside Asian Payphones with Screens
- China Your typical Chinese payphone with a tiny screen, seen in Shenzhen. Photo by Mateen Greenway
- South Korea A phone found in Seoul that takes cards and coins while proudly displaying the time. Photo by Daniel Rudov
- Thailand On display in Bangkok, this model wins the prize for best color coordination from its green screen to its bright casing to its dark and serious receiver. Photo by 3ricj
- Azerbaijan Some say it's Asia, some say it's Europe. But this phone in Baku unites the region with its strangely comforting appearance. Photo by Sam Pursglove
- Back Inside Global Payphones (also with screens)
- Mexico Seen in Aguascalientes, this phone really does look good in red. Photo by tonyskapunk
- Argentina One of the "wide screen models," this one from Buenos Aires. Photo by 3ricj
- England This is a model known as the Contour 400 and it's in a somewhat sorry state in Devon. The humble screen is overshadowed by the devastation. Photo by Rob Purvis
- Bulgaria From Sofia, this squat little phone has one of the aforementioned wide screens and not much else. Photo by IFo Hancroft
- Back The Back Cover Photos
- Back Cover Photo #1 Yes, we have a beach cafe! This one was uncovered by Doug Stilwell while in Santa Monica, California. He had to point his camera skyward to avoid capturing images of all the hackers crowding around.
- Back Cover Photo #2 This shirt was spotted one day by Rhetta Jack being worn by her husband. Turns out he's a member of the coolest chapter of The American Federation of State, County, and Municipal Employees.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 33!
$2600 Magazine - Volume 33, Number 3 (Autumn 2016)
- Promises - Editorial
- Hacking for Knowledge - Overview of the author's "Phoenix Project II" which involves installing Ubuntu 12.04 LTS on a surplus SuperMicro rack server, by Jerry
- MOV Before You JMP - Why one must learn proper assembly code languages if they wish to write (and understand) exploits, by Vuk Ivanovic
- It's Security, Stupid - Hypocritical idiots who talk about Internet "freedom," "security," and "rights" - while shutting down websites (and Twitter accounts) they don't like - just like the little fascists they are, by Mallory Knodel, Sacha van Geffen, Stefania Milan, and Camille François
- Freedom of Thought - Everyone has the capacity of freedom of thought and those thoughts will keep you free and true and they cannot be taken away from you, by Daelphinux
- Telecom Informer - Verizon's hesitancy to repair and replace copper outside plant after hurricanes and switch the customers to "wireless landline" systems - and the problems this caused for legacy systems like faxes/modems, alarm monitoring, 911, etc., by The Prophet
- A Captive Portal Puzzle at Sea - Overview of some of the tools (Hans) and techniques (Tor/tunnels/proxies) for bypassing wireless network captive portals while on a cruise ship, by IceQUICK
- Spyware Techniques - This article explores the concepts and principles of spyware creation. Various techniques are given for both capturing data and for ensuring the spyware behaves in a manner least likely to be noticed, by Dr. Chuck Easttom (William C. Easttom, II, Email #1, Email #2)
- The Evolution of Windows Spyware Techniques by Birdman
- Building DIY Community Mesh Networks - Overview of the tools needed to build community wireless networks which can be independent of government rules, by Mike Dank (Philadelphia, Pennsylvania, Email, Twitter, Mastodon)
- Musical Monstrosities - Overview of the art of "circuit bending" - hacking musical toys to change their audio output or control, by Dent (Email #2)
- Hacker Perspective - by Scott Everard
- The PirateBox - Overview of a Raspberry Pi-based PirateBox, which is an anonymous way for people to communicate or exchange files, by SideFx
- Code: piratebox_rpi_1.1.4-27-02-2018.img.zip For Raspberry Pi 1 A, B, B+, Zero, & Zero-W (578M ZIP)
- Code: piratebox_rpi2_1.1.4-11-05-2018.img.zip For Raspberry Pi 2 & 3, Rapsbperry Pi 3+ (607M ZIP)
- How to Google Bomb Someone; or, Rick Santorum's Sticky Situation - Overview of "Google bombing," which is a technique to force certain websites to the top of the search results, mostly for the lulz, by Garrett Mickley (Email)
- Letters - synergy
- Offerings - Samy, Joanne Shields, Kristyn, The Characters Didn't Come Through
- Meeting Updates - Jack (New Jersey), Aidan (England), asciib17 (Austin, TX), London Longenecker (Harrisburg, PA)
- Getting Involved - CH, Johnny Martyr, C, J, Mike, S, Eric, Pic0o, W (Connecticut), Alex W., RAMGarden
- Curiosity - tnx, Mike, John
- New Stuff - Pawe Krzaczkowski (Poland), Scooby Doo, david0509, Chad, Brainwaste
- Corporate Fallout - Kevin, Aldo Daniele Dominici, Big Guy 1000
- Following Up - GI motherf*cking Jack, D1vr0c, Henri, Squeeling Sheep, M, PG, NHM
- Political Intrigue - pink
- The Eleventh HOPE - The Eleventh HOPE Writer #1, The Eleventh HOPE Writer #2, The Eleventh HOPE Writer #3, The Eleventh HOPE Writer #4, The Eleventh HOPE Writer #5, The Eleventh HOPE Writer #6, The Eleventh HOPE Writer #7, The Eleventh HOPE Writer #8, The Eleventh HOPE Writer #9
- Verizon's HOPE Scam - The problems of getting a traditional landline installed for the HOPE conference and being forced to pay for an entire month for three days of service, and a surprise $50 "shortfall" billing for not using their long distance service enough. All-in-all, a $70 phone bill for a single one minute call to Connecticut!
- The Easiest Way to Break Into a Bank - Apparently, everyone at TD Bank has a default password of the last 6-digits of your check card number, or even "123abc", by Anne
- Hacking Amazon E-Books with Spy Style - Gives you the opportunity to use your Kindle content as you like and how to save any ebooks you may already have, by bartitsu59 (France)
- Code: screwDRM.scpt
- EFFecting Digital Freedom - Copyright is not a trump card, by Elliot Harmon
- A Parallel President on Twitter - Story of creating a "mirror" Twitter account of Argentina's president to allow their citizens to reply to the president's tweets without be blocked or censored, by Richard Vardit
- Code: mirrorbot.php
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: The Eleventh HOPE
- Cover (Cover Info)
- Cover Inside Pacific Payphones
- Phillipines Seen in Dumaguete, this rather weird booth and phone somehow appear both modern and ancient at the same time. Photo by HB
- Taiwan This standard phone, operated by Chunghwa Telecom, is found throughout the country. Two interesting dialing codes: Domestic Violence Prevention (113) and Anti-Fraud (165). Photo by Nick Montoya
- Phillipines PLDT used to be known as the Philippine Long Distance Telephone Company until this year and it was run by GTE from 1928 to 1967. This is one of its standard payphones, spotted in Manila. Photo by HB
- French Polynesia This blue card model was found in Tahiti and is run by OPT, the government owned phone company. Photo by Pro
- Back Inside Eurasian Payphones
- Germany Is it a phone or an art piece? It's hard to tell. This one was seen in Bonn. Photo by Jason Lenny
- Turkey Spotted in Ephesus, this instrument of the former state-owned company is now run by a Saudi enterprise. Photo by Allison Smith
- United Kingdom In Birmingham, it's customary to leave the receiver dangling. Photo by Richard Bailey
- Croatia This was found on the island of Vis. We're told the receiver possibly still works if you're a robot with the correct interface in your head. Photo by Richard Hanisch
- Back The Back Cover Photos
- Back Cover Photo #1 As we all know, hackers are involved in nearly every aspect of life. In this example, Jules has discovered one of our favorite activities near Lake George, New York.
- Back Cover Photo #2 Amsterdam's Centraal Station is a real hub of activity, which is why it's so surprising that none of us came upon this one before. Fortunately, Roc Rizzo managed to spot this very special railroad track signal.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 33!
$2600 Magazine - Volume 33, Number 4 (Winter 2016-2017)
- Dark Bubbles - Editorial
- Rescuing Fake Memory Devices - Many SD cards on Ebay are "fake," only providing a usable 8 GB of data, use H2testw.exe to verify them, by Tau_Zer0
- Having Fun With In-Store Chromecast - Stream your own content to the demo TVs at Best Buy (PSK: blue1966) using Google Cast, lol-md4
- The Coca-Cola Blacklist - List of banned words ("Unhealthy"!) you can't use for the "Share a Coke" campaign, by Dent
- Bypassing Privileges with Oracle Database Express Edition 11g Release 2 - Create a link between two disparate database servers in order to cross-validate row counts, by Chris Rucker, Data Scientist
- Telecom Informer - Overview of the current Canadian phone system, and the problems carriers had switching from CDMA, by The Prophet
- Using Discord Servers to HTTP Flood - Use the Discord voice/text chat app to launch a denial-of-service attack via their automatic HTTP link checking, by xnite
- Code: harmony.js Proof of Concept bot for discord DoS.
- Successful Network Attacks - Phase One: Reconnaissance - Overview of the reconnaissance techniques one uses to identify and attack a computer network, by Daelphinux
- Spying Across Borders in the Age of Email - This article is about Brazilian researchers that had their email invaded by U.K. Ministry of Defence with cooperation from Microsoft Corp. The work show details of the invasion and steps that permitted this discovery, by Rodrigo S. Ruiz and Rogério Winter
- Case Report of Email Spying Original (PDF Version)
- InfoSec at Its Worst, OPSEC at Its Best - Story of reused passwords and abusing Apple Keychain to gain access to a Wi-Fi setup blocked by the author's parents, by NerveGas Jr.
- Hacker Perspective - by Byeman (Texas)
- Can Security be Built into Pure Data? - The idea of building security directly into the XML language, by Wyatt Lee
- mcquery.js - A Web Scraper for Disc Golf Players - Using NodeJS to design a "web scraper" to watch online auction sites for a particular golf disc, by Brenden Hyde
- Code: mcquery.js (README)
- Code: mcquery.json
- Letters - CROSSFIRE
- General Inquiries - Anonymous Teen, Steve, andrew, hardik hardik, C, Bill K, Steve W., db, Mark, lol-md4, TimInCT, Mike, Tad, Daniel, S, (no name given), C, P
- Liberation - massitakevin, Sky
- Scrutiny - NerveGas Jr., El Magistral
- Electorials - machghostine, Nick, Anonymous, David, Piss Off Voter, Bc smith, Stymtex, Stan B.
- Events - Karl, Pic0o
- Digital Editions - skilbjo, Huckle Buck
- Fun With Calendars - Neil Howard, Chris
- More Dialogue - Pablo, josh cha
- The Bounty - P, Kurt
- Appreciation - William, A. S. A., John
- Something New - Stratman01, s1w4t
- Issues - Marc
- The Wonderful World of Meetings - Bachelet Lab, Jeff, Leon, R, stmerry, Braden
- Observed - Funkfish
- Knowledge Lost - Joe
- KBChat - Private, Encrypted Chat via KBFS - Using the Keybase Filesystem (KBFS) to "chat" via shared folders with Bash shell commands, by Samuel L. Hofius (Albuqerque, New Mexico, KF5GRD, GitHub, Instagram)
- Code: kbchat.sh
- 2600 Leak Department - What IRS agents are suppose to say in response to your questions!
- Memory Lane - "Please Avoid Unnecessary Calls to Washington" - August 6, 1942 New Jersey Bell Telephone Company phone ad in Washington, New Jersey's Washington Star, Submitted by Anne Jackson
- EFFecting Digital Freedom - Anti-Trump lies and disinformation - this is exactly why you SHOULD NOT send money to the (((EFF))), by Erica Portnoy (GitHub) and Elliot Harmon
- Rotten Apples: OS X 101 - Overview of the kernel, file structure, and security features in Mac OS X, an update to the article "Accessing Admin Privileges: A Quest Through One of Mac's Backdoors", by Secure Panda
- Automatic Contest Winning via Selenium - Using the Selenium WebDriver to automate certain tedious tasks, like winning online contests, or Xbox Line code redemptions, by Kyle Bradshaw (Skylled)
- CodeSnag-1.3-py2exe-win32.zip Snags codes tweeted out in public giveaways and tries to redeem them first.
- The One About That File Server - Story (urban legend?) of the reliability of pre-Windows/UNIX servers even when nobody knows where they are physically located, by Sydney Greenstreet
- Fiction: Hacking the Naked Princess - Chapter 0x12 - Chapter from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: Spending too much time on social media and not meeting/listening to people in real life. / Anti-Trump lies, propaganda, and disinformation.
- Cover (Cover Info)
- Cover Inside Payphones of Europe
- Russia This ancient relic was spotted in Kostroma and has clearly seen a lot of history. It may not be sleek but it's certainly rugged. Photo by Steve A
- Armenia Seen in Yerevan, this phone is certainly sleek but perhaps not so rugged. It's operated by the Russian company Beeline. Photo by Simon Powell
- Romania Incredibly similar to the Armenian phone, this was discovered at the airport in Sibiu and is operated by Romtelecom. Photo by Kevin W.
- England Found in Blackpool, this is a particularly well lit booth. It seems to have a decent color scheme going, which gives it a unique style. Best visited at night. Photo by RykVR
- Back Inside International Payphones
- United Arab Emirates The kind of phone you'd expect to see in an airport terminal in Dubai. As well as on page 2 of this issue. Photo by AM (secuid0)
- Canada In Scarborough, Ontario, you can actually find a phone booth that has a tree growing in it! Or at least you could. We're told the phone has since been decommissioned and removed. Photo by David McLeod
- Japan We can't tell you what city this phone and accompanying phone card vending machine were spotted in. That's because the green pair pass through cities at 200 mph on the Shinkansen high-speed train line. Photo by Cobolt
- Thailand Another phone booth with vegetation and a good amount of color. Found in the Watthana district of Bangkok. Photo by Robert Wood
- Back The Back Cover Photos
- Back Cover Photo #1 Many of us have seen this particular New York City subway car - in fact, it even made it to one of our covers back in 2005 - and this is a shot from the inside, captured by Robby R.O.B.B. For those who want to find the "2600" car, wait around on the "D" line and it should eventually show up. (Please don't pull the cord.)
- Back Cover Photo #2 A really interesting story is connected with this cardboard box. David Graper tells us that Troy Typewriter in upstate New York was one of the few remaining typewriter repair stores left in existence. The guy who ran the place had a longtime reputation as a true hacker who respected the old technology and somehow managed to keep machines of all types running without proper access to parts or supplies, always having time to answer technical questions. When he finally went out of business in 2016, this very specially named box was the last one to leave the shop.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 33!
$2600 Magazine - Volume 34, Number 1 (Spring 2017)
- A Price for Truth - Editorial
- New U.K. Surveillance Laws - Time to Get Serious About Security - Draconian surveillance laws in the U.K. through the Investigatory Powers Act which passed in November 2016 and some tips and technology to avoid Internet surveillance, by Dr. G
- Voices in the Sky - Satellite Communication Methods - General overview of the techniques and frequencies used by satellites for their uplink and downlinks, by Monican
- Lockbox PIN Code Generator - Major security problems with Supra mechanical key lockboxes (only approx. 250 PINs!), by Victor
- Code: lockbox.py
- A Lock With the Key Next to It - Article discussing the insecurities (Win 7, using USB drives, using proxies, etc.) of the computer security at the author's middle school, by ckjbgames
- Hacking Free Wi-Fi on Delta Flights - Get one hour free Internet by entering a random T-Mobile number and spoofing the browser User-Agent, by David Libertas
- Telecom Informer - Three hour lunches (why your phone bill is so high) and the telephone system of Myanmar, by The Prophet
- Telephones from Space - Introduction to telephone number (exchange) scanning, including example from 1-800-NXX-2600, by Dent (Phreaky Dent, Email #2)
- Strange Numbers (6.3M WebM)
- Longing for the Past - Story of a 15-year-old hacker who wishes he could go back into the past to the hacking days of the 1980s and 1990s, by Nick (U.K.)
- Getting Inspired as a Student - Story of information security students attending Black Hat Europe 2016 and being disappointed that the vendor hall was run by people with no technical background who only cared about sales, by StMerry
- Google Auto-Fill Suggestions, Politics, and Magic - The possibility of Google auto-fill suggestion bombing to perform election interference, by Ry0ki
- The Inner Circle... Part One - Voter registration records for Donald Trump's so-called "Inner Circle." Contact these people and thank them for how much better things used to be...
- Off The Hook April 5, 2017. Additional information on the full listing of voting records for Trump's inner circle.
- Hacker Perspective - by Jack Beltane (Bay Village, Ohio, Twitter)
- Software Cracking with dotPeek - Example of using JetBrain's dotPeek 1.5 to decompile DLLs to expose hidden software options in Satellite Reign or other games, by redstarx
- Ignore Your .env - Browsing Environment Files on GitHub - Searching for potentially sensitive data in exposed environment variables on GitHub, by casi
- Obfuscating Torrent Traffic - Using LayerProx to obfuscate BitTorrent traffic to fool DMCA-type blackmailers, by Filip Kälebo (a.k.a. flipchan, Sweden, GitHub)
- LayerProx A rebuild of marionette, encrypted proxy that simulates general webtraffic.
- Successful Network Attacks - Phase Two: Network Scanning - Overview of probing a computer network for vulnerabilities or known weaknesses, by Daelphinux
- Letters - REACTIONS
- Contributions - Gabrielle, Vanessa, Russell, Jason
- Distribution - John
- Meetings - L, notaspy (Vancouver, Canada), MG (Petaluma, CA), stmerry (Edinburgh, Scotland), Echo, Dinesh (Doa, India)
- Storm Warning - Name Deleted, Pissed-off in Long Beach, California
- A Look Back - Dr. Dave, Darkmatter
- Feedback - kes, YTT, Sudarshan, brucerobin (Photo), John, Inquiring Mind, Kris, fooCount1, D1vr0c
- Asking - Stas (Belogorsk, Russia), Marko, Shazia, Moshean, WarmFuzzy, Jeff
- Leaks - Homeless Man, [Everything Redacted]
- The Future - Robert (Alien Species), Devlin, colForbin
- The Marketplace - X, F, Christy
- Observation - rick (Photo)
- Further Info - Wolfgang_Von_Stinkbutt (Movie: Genius On Hold), Rodrigo Ruiz (Book: Apoc@lypse: The End of Antivirus), Chris Berge
- More Eleventh HOPE Feedback - The Eleventh HOPE Writer #10, The Eleventh HOPE Writer #11, The Eleventh HOPE Writer #12, The Eleventh HOPE Writer #13, The Eleventh HOPE Writer #14
- White House Phone Numbers List of both public and private White House phone numbers
- How to Improve Zone Protection in Burglary Alarms - A novel design of a hard-wired zone control panel or zone expander input of a burglary alarm, which provides an enhanced security level against compromise attack attempts or problems with the zone loop, by Cezary Jaronczyk (Canada, Email)
- Additional Info & Corrections
- Arduino Project: Burglar Zone Input Tester Tester may block hard-wired sensors of common burglary alarms and access systems so protected zone is open, even if the system's in arm mode. (Schematic)
- How to Disable an Alarm System's Sensor or Contact (YouTube)
- Arduino Project Burglar Zone Input Tester (151k PDF)
- EFFecting Digital Freedom - We're halfway to encrypting the entire web, by Gennie Gebhart (San Francisco, California, Email, Twitter)
- Validating Software Validation - The potential dangers of relying on checksumming (MD5, etc.) to validate files if the actual checksumming scheme is compromised first, by Malvineous
- Thoughts on Phoenix Project II - Hardware and software tips for setting up your own pseudo-BBS/website in Linux, by GI_Jack
- Those Coca-Cola Freestyle Machines in Crew Mode - Story and pictures of a Coca-Cola Freestyle soda machine left in "Crew Mode," by M0ebiusStrip
- ULPT: On Coke Freestyle Machines Select "water" and tap a triangle in the upper-right corner to enter the Admin Menu.
- Coca-Cola Freestyle Dispenser - Crew Guide (5M PDF)
- 321 Studios Revisited - Story of working with Robert H. Moore at 321 Studios and his DVD X Copy software, by /\/ordog
- Mr. Robert Moore of 321 Studios Died Over the Weekend He was the guy that got a lot of us on the road to copying DVD movies.
- 321 Studios Forges Ahead
- Judge Bans Copying Software for DVDs
- 321 Studios Close to Shutting Down
- Robert H. Moore Obituary
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: Anti-Trump lies and propaganda. Evil Corley wants to pay $10,000 for Trump's tax returns, but not those of Joe & Hunter Biden showing their shady business connections to Ukraine and China... Hmm...
- Cover (Cover Info)
- Cover Inside Central and South America Payphones
- Peru Yes, in this country you can apparently just stick a payphone onto a tree if that works for you. This one was seen in Ollantaytambo in the Sacred Valley of the Incas. Photo by Victoria Dietz
- Peru A bit more of a traditional approach found in Iquitos. Telefónica is a Spanish company that operates throughout South America. Photo by Andova Begarin
- Colombia Located in Chía, we're impressed with the combination cord and chain that keeps the receiver from wandering. Photo by Dallas Luce
- Mexico This phone was found in the mountains over Puerto Vallarta. It only works for local calls and the cost on the receiver says $3 unlimited, meaning three pesos (around 15 American cents). hoto by Dwayne Jenkins
- Back Inside International Payphones
- Oman Found somewhere in the maze of the Souq Muttrah marketplace in Muscat. This model can be found throughout the city. Photo by Sam Pursglove
- Bulgaria This payphone, seen in Veliko Tarnovo, doesn't know how lucky it is. That amount of protection for such a tiny phone is unheard of in most parts. Photo by Brian Collins
- Spain This is off the mainland a bit. Actually discovered in Las Palmas on Gran Canaria in the Canary Islands, this phone seems to have withstood lots of wear and tear. Run by Telefónica. Photo by Oscar Sandström
- Portugal Again, not actually on the mainland. This one was found in Furnas in the municipality of Povoação on the island of São Miguel in the Azores. It also wins the award for the loneliest looking phone in this issue. Photo by Kevin Costain
- Back The Back Cover Photos
- Back Cover Photo #1 Here's a frame from the 2000 movie Romeo Must Die (spotted by The Guy That Watches Bad Early 00s Films) where protagonist Han Sing (played by Jet Li) is breaking into our apartment with a damn drill. Please. He couldn't even bring a lockpick set? In all likelihood, the reference was intentional since bypassing security is kinda our thing.
- Back Cover Photo #2 Who isn't enthusiastic about the Domain Name System? We certainly are and so is whoever painted this in the Sachsenhausen neighborhood of Frankfurt, Germany. Thanks to Sam Pursglove for discovering this. And if you search online with the above info, you'll find a whole bunch more tags from this artist.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 34!
$2600 Magazine - Volume 34, Number 2 (Summer 2017)
- The Power of the Press - Editorial
- The Censorship Resistant Internet: Part 1 - How to Run a Tor Hidden Service - Detailed overview of wetting up a .onion Tor-accessible website under GNU/Linux, by p4bl0 Pablo Rauzy (France, Twitter, Blog)
- The Censorship Resistant Internet: Part 2 - How to Run an I2P Hidden Service
- Outreach Activities by Pablo Rauzy
- Converting the Voter Database and Facebook into a Google for Criminals - Overview of the possibility of linking voter database records with a person's Facebook page, by Anthony Russell (Twitter)
- Hacktivism to End Human Trafficking and Modern Day Slavery - Using "hacktivism" to bring awareness to the approximate 30 million people currently enslaved around the world today, by Dr. G
- Telecom Informer - Discussing the telephone system during the days of the Soviet Union and the illegal (((removal))) of Viktor Yanukovych, by The Prophet
- How Rogue One Taught Me Not to Be a Bad Guy - Story of how hackers should be like the rebels in Rogue One in fighting an Empire of old jewish men in crisp uniforms and other dangers of the Obama/Biden/Corley regime, by Jameson Hampton (Buffalo, New York, Twitter, Muck Rack, YouTube Channel, Facebook, GitHub)
- A Declaration of Independence for Cyberspace - Ideas for a potential "Declaration of Independence" for users in "cyberspace" in order to protect the flow of information and their digital privacy, by Daelphinux
- Demonsaw: Bypassing Anonymity Utilizing Social Engineering - Method to expose a person's IP address on "secure" chat networks, like Demonsaw, by posting links to third-party websites (like YouTube, etc.) which log them, by Hristo I. Gueorguiev
- Pineapple Pi - Creating an Automated Open Wi-Fi Traffic Capturing Tool for Under $20 - Use a Raspberry Pi Zero and a TP-Link TL-WN722N to capture all the traffic on an open Wi-Fi network, by Br@d
- Code: WiFiCap.sh
- 0x8BC4 Before You 0xFFE0 - Good overview of Intel CPU machine code and assembly language programming which are needed for stack-based buffer overflow exploits, by XlogicX
- Hacker Perspective - by 0rbytal (Twitter)
- My Perspective - Article sharing the author's philosophy of how to deal with smartphones and other invasive technologies and the people who use (and create) them, by Buckminster Emptier
- OPTingOUT - Discusses the apparent challenges in deleting social media account and how it can often take weeks to fully delete data - if at all, by Kernal Seiden
- Analog vs. Digital Living: Real Solutions to Absolute Anonymity and Privacy - Get off the grid and still stay connected to the world. Real solutions using Tails on an Acre Chromebook for absolute anonymity and privacy, by DocSlow
- Letters - CHORUS SUROHC
- Stickers - stAtiC, Joe
- Corporate Culture - Megan, Ellie, Praful Mathur
- Further Info - Akalabeth, bobgerman, Laurie, NTGuardian, RAMGarden, Matthew Sacks, B, Pic0o
- Concerns - Tyson, Sikorina Bustamante Paco, ckjbgames, DM, Concerned lifelong 2600'er
- Meeting Updates - Travis, Phil, Richard Cheshire, stmerry, conscript, Robert, George (Los Angeles, CA), Mad Glitcher (Petaluma, CA), Carl (Arkansas), Fritz (Fargo, ND), Cristy (Italy)
- Taking Action - Terry, R, G (Idaho), An Avid Reader/Listener (~93), David
- Inquiries - R, J, Bertram, Warmfuzzy, SS, Kiraz, heavenligible, Phil, Jack, Dave (Dublin, Irelan)
- Article Responses - E85, Monican
- EFFecting Digital Freedom - Building digital safety skills in your community, by Soraya Okuda and Elliot Harmon
- Building a Better Screen Locker for GNU/Linux - Building a screen locker with slock which is reasonably resilient to local attackers who attempt to brute-force the password or install malware which the lock is engaged to log and exfiltrate the password, by idk
- Code: masterscreen.sh
- Code: xsidle.sh
- Citizen Engineer - Patently hacking, by Limor "Ladyada" Fried and Phillip Torrone
- VR Trumpers - More evidence that Democrats are the dumbest people on the planet and "Trump Derangement Syndrome" is really no joke, by Jeffrey H. MacLachlan (Milledgeville, Georgia, Email, Phone: 478-445-5571, Picture, LinkedIn, RateMyProfessor, 2018 Salary: $59863.87)
- Successful Network Attacks - Phase Three: Gaining Access - The most difficult part of a computer network attack - getting access, by Daelphinux
- Advice from the Socially Engineered - Advice and tips for conducting a successful social engineering attack by someone who was "social engineered" themselves, by Infra Read
- Internet Thoughts - Some observations on what, and how bad, the Internet has become over the years, by Jared J. Estes
- Fiction: Hacking the Naked Princess - Chapter 0x13 - Chapter from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: Evil Corley actually believes the lies and fake news spread by The New York Times ✡, The Washington Post ✡, and The Guardian ✡ about Mr. Trump.
- Cover (Cover Info)
- Cover Inside Payphones from Around the World
- Honduras This well-protected and stylish model is a government-owned Hondutel phone that was spotted in Santa Rosa de Copán. Photo by Edwin
- Cuba This rather nondescript model was attached to the outside of a building about a block from Ernest Hemingway's old home in Havana. Photo by Bruce Robin
- Costa Rica Seen in Zarcero, this phone used to take coins, but the coin mechanism has been disabled and now it only takes cards. Photo by Babu Mengelepouti
- Portugal Found standing all alone on a street near the pier in Calheta, São Jorge Island, Azores. Photo by Anthony Cunha
- Back Inside Payphones of the East
- Australia This is one of only two payphones on Lord Howe Island. This one was near Joy's General Store and it even comes with a chair. (The other payphone is at the airport.) Photo by Greg Sherman
- Taiwan Spotted at Taoyuan Airport near Taipei, this phone seems way bigger than it needs to be. We're surprised someone hasn't stuck a big ad on all that empty space. Photo by Justin Davis
- Thailand A true work of art, this Bangkok payphone uses colors with amazing style. This phone seems to be torn between looking futuristic and ancient. Photo by Sam Pursglove
- Thailand Another aesthetically pleasing model, this one found in Phuket. The colors offset themselves perfectly, making it possible to admire while completely missing the fact that it has no handset. Photo by Sam Pursglove
- Back The Back Cover Photos
- Back Cover Photo #1 A little known fact: all FTP transfers go through this building near the corner of Fairfax Avenue and Beverly Boulevard in Los Angeles. At least we assume that's the case - it would explain most of the bottlenecks we experience. Discovered by SC.
- Back Cover Photo #2 This must be the building that housed the very first website back in 1924, another little known fact that you'll only find on our back cover. Thanks to Barry von Tobel for findng this piece of history in Waltham, Massachusetts.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 34!
$2600 Magazine - Volume 34, Number 3 (Autumn 2017)
- Acts of Courage - Editorial
- Bypass Your ISP's DNS and Run a Private OpenNIC Server - Take back your Internet privacy by using your own DNS server or a service like OpenNIC, by Mike Dank
- PHP Backdoors - How to hide a PHP backdoor payload by using ASCII-represented-binary to defeat any malware detectors, by Dave Jericho
- Code: Code Snippet #2
- Code: Code Snippet #3
- Code: Payload Snippet
- Inseparable: The Intersectionality of Hacking and Politics - Overview of how it's now up to hackers to stop corrupt (((politicians))), media, and governments, by Josephus
- Telecom Informer - Talking about DNS vulnerabilities and their relationship to SS7 vulnerabilities, by The Prophet
- Enhancing SQL Injection With Stored Procedures - How to enhance a SQL injection attack by using Stored Procedures in Microsoft SQL Server, by Dr. Chuck Easttom (Email)
- Windows - The Undiscovered Country DEFCON 25 Workshop
- Windows - The Undiscovered Country Slides
- How to Get Nearly Free Travel from Scotrail - Potential loophole for almost free rail travel from Scotland's Scotrail if you "lose" your card, by TheGeek
- (learn (LISP)) - LISP is the language of the gods. It is the ultimate hacker's language, by John Skilbeck (skilbjo, San Francisco, California, GitHub, Twitter, Stackoverflow)
- (learn (LISP)) Original
- Reverse-Engineering Electronic Letter and Number Toys - Using electronic letter toys to teach kids or students on the aspects of reverse-engineering, counting in binary, and electronics tinkering, by B. Ramsey
- How to Hack Your Way to a Guilt-Free, Political Ideology - How not to fail for mainstream ideology and to instead form your own ideology from the ground up, by Eyenot
- The Problem with IT Certifications and Their Contribution to the Devaluation of Technology - The general uselessness of today's "IT certifications" from places like CompTIA, and how they trick people into thinking they'll get jobs in the IT industry, by Super Ells
- Hacker Perspective - by Master Chen
- The Hacker Perspective Original
- GREYNOISE Instagram
- GREYNOISE YouTube Videos
- GREYNOISE Twitter
- A Little Brother's Manifesto - Manifesto to support the EFF, the Tor browser, and strong encryption, by Qrag (Email #2)
- A Test Harness for Fuzzing Font Parsing Engines in Web Browsers - This article presents a cross-platform test harness written in Python that assists the user in searching for vulnerabilities in web browsers, specifically by fuzzing their font parsing functionality. The tool automates the delivery of test cases (font files in this context) into a web browser. The creation of a corpus of mutated TTF font files suitable for use in fuzzing is also covered, by James Fell (York, U.K., Email #2, GitHub)
- A Test Harness for Fuzzing Font Parsing Engines in Web Browsers Original
- Code: fuzzing_font.py
- fontharness Fontharness is a cross-platform test harness written in Python that assists the user in searching for vulnerabilities in web browsers, specifically by fuzzing their font parsing functionality.
- Test Harness for Web Browser Fuzz Testing by Atte Kettunen
- A Review of Fuzzing Tools and Methods by James Fell
- Letters - MOB RULE
- Administrivia - John, A, lol-md4, Courtney, X (Ontario, Canada), Jim St, tiburonrepair, Andres
- Following Up - GI Jack, ShieldCurve, OWA, The Piano Guy, An Anonymous Pedo, Bearz
- Inquiring Minds - Robert, E, Medhat, A Meeting, Jim, moocru22, Adam, Patchmail, Phototrope, 73 fellow circuit benders, Robert, Brad, Paul
- More on Meetings - Skipper Blue, Skipper Blue, njones920 (Reno, NV), Sergey (Moscow, Russia), A. Roach (Baltimore, MD), Mark (U.K.), Richard Cheshire
- Contrition - G
- Other Cultures - whotopia, G
- Political Views - Jim in Virginia, Marcus, John F. Kennedy, Daniel
- Observations - karyse, Marc, Henry, Christy Dufrene, hydrogen
- Projects - Darkmatter, Joshua, Tiago (Lisbon, Portugal)
- EFFecting Digital Freedom - Don't let Congress destroy what we've built, by Elliot Harmon
- Confessions of a (for now "Not So Successful") Bug Bounty Hunter - Perspective of a software "bug" hunter who finds bugs for monetary rewards, and the draw backs that often includes, and to always have fun, by Vuk Ivanovic
- To Care or Not to Care - Story of bypassing the iTALC classroom management and computer monitoring software by deleting a DLL, by deadbeat0
- Scrape Textbooks, Save Money - AppleScript to open up the Kindle.app application on Mac OS X system which proceeds to photograph every page of your (preview) textbook, by th0tnet
- Code: Scrape_Textbooks.scpt
- googlecomp.py: The Complete Google Autocomplete Script - Command-line script to initiate the Google search "autocomplete" function, by ckjbgames
- Code: googlecomp.py
- Citizen Engineer - I like your content, but your terms are not acceptable, by Limor "Ladyada" Fried and Phillip Torrone
- Obfuscating Biopolitics: A Theoretical Primer for Cyborgs and Other Concerned Citizens - Subverting security practices which attempt to reinforce state and corporate control with digital obfuscation, by Emma Stamm (Website #2, Email #1, Email #2, LinkedIn, Twitter)
- Debt Journey - Tips for dealing with outstanding debts from credit cards, utilities, student loans, etc. and dealing with debt collectors (they don't care about your situation!), by Pic0o
- Successful Network Attacks - Phase Four: Maintaining Access - Tips for maintaining access (backdoors, etc.) after a successful hack and to look out for intrusion monitoring systems, by Daelphinux
- Splatter - Applying "splatter semiotics" to our fast-paced world and the dangers the (((fake news))) media can play, by Alan Sondheim
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: Shutting down any speech or websites which targets the Evil Corley and the One Percent is O.K. / Spreading disinformation and fake news about the Charlottesville "Unit the Right" rally.
- Cover (Cover Info)
- Cover Inside Blue Payphones
- Lithuania Near the Baltic Sea on a walking trail, but these blue things are found all over Palanga. Photo by Elvis Sakalauskas
- Eritrea In a part of the world where payphones are still heavily used, this blue model from EriTel looks brand new. Photo by whotopia
- Belize This is cheating since the only reason this phone is blue is because somebody threw blue paint on it. Other than that, this is a perfectly normal Belizean payphone. Photo by hevnsnt
- Greece Found near Athens, this blue model is fairly typical, as is the graffiti that tends to show up on it. Photo by Andi Hudson
- Back Inside International Payphones
- Thailand Found outside the police station on the main road in Chiang Mai near the city zoo. Photo by James Schumacher
- Scotland This BT payphone was found in Brig o'Turk and is clearly getting a lot of use. Ironically, there was no GSM service here. Photo by Tad
- Turkey Hidden behind a tree in Istanbul, this little phone takes no coins and may only be known to the graffiti artists and sticker people who stop by. Photo by Joshua Dellinger
- Hungary This payphone from United Telecom Investment in the small town of Herend accepts both Hungarian and Euro coins and still provides a dial tone. Photo by Richard Hanisch
- Back The Back Cover Photos
- Back Cover Photo #1 Spotted at North 2nd Street, Minneapolis, Minnesota by tom wik, this is one of our absolute favorite buildings bearing our name. We especially like the collection of stones where anyone else would have put a window.
- Back Cover Photo #2 If you ever get a chance to take a tour anywhere, always make sure it's a "hacker" tour. They're so much more fun! Thanks to Richard Hanisch for sending this one in from Vienna, Austria, who hopefully kept their servers secure while a bus full of hackers was in town.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 34!
$2600 Magazine - Volume 34, Number 4 (Winter 2017-2018)
- Credit Denial - Editorial
- Using DNScat2 for Encrypted Command & Control Over DNS - Overview of the process for setting up DNScat2, which allows an encrypted tunnel over the Internet by using DNS traffic, by James Fell
- github.com/iagox86/dnscat2 This tool is designed to create an encrypted command-and-control (C&C) channel over the DNS protocol, which is an effective tunnel out of almost every network.
- Tunneling Data and Commands Over DNS to Bypass Firewalls
- DNScat2: Application Layer C&C
- DNScat2 - Precompiled Binaries
- Educating Friends and Family About Online Security - Tips for getting NPCs and common folk to start using encryption and operation security while on the Internet, by BirdPerson
- Creating Strong and Easy to Remember Passwords - Simple technique for creating passwords that are both strong and easy to remember, by Andova Begarin
- Don't You Have a Smart Watch Yet? - It will make your email security that much easier to deal with by sending your "two-factor authentication" emails directly to your watch, by The Cheshire Catalyst
- Don't You Have a Smart Watch Yet? Original
- PDF Version Print out and fold into quarters.
- Telecom Informer - Cool little story about getting electrical power to rural Washington state locations, by The Prophet
- What Happens When WHOIS Data is Made Public - Story of a person who intentionally left "accurate" personal information in their WHOIS entry - and how much spam they received, by Victor
- Deauthing the Neighbors, or Ring Theory - Use a coaxial splitter, multiple antennas, and a few Python scripts to send 'deauths' to a neighbor's hogging Wi-Fi setup, by Snocone
- Nightmare on E Street (Modem and Me Against the World) - Story of a person who apparently had their Wi-Fi and cable modem hacked, an overview of all the hoops they had to jump through to sort everything out, and just how useless "tech support" can be, by Emily Saunders
- Hacker Perspective - by Gazza
- Quantum Computers and Bitcoin - The potential for future quantum computers to be able to mine Bitcoins (or other cryptocurrencies) and what it means, by Dave D'Rave
- I Want to Be a Hacker... - Tips from a InfoSec recruiter on what they look for - if you're a hacker looking to sell out..., by Ricki Burke (Melbourne, Australia, LinkedIn, Twitter)
- Letters - MEGAPHONE
- Payphones - RB, E, Ben, Jeremiah
- Articles - TP, M, GI Jack: All American Zero, Future Published Writer, celcius water, Josephina Jones, David, jjstylesrocks
- Other Mediums - Gerald C, Former Admin
- Old Tech - Ryan
- Digital Print - Thomas, Devin, Neil
- Misdirection of Efforts - Wissbr, Michael, Watt wusiwudg
- Offers - Jorgen (Ukraine), KHRoN, Oliva Jones, Volunteer, Ellen, Ellen, James Willson, Ellen
- Accomplishments - Guy Zappulla, metaknight
- Meetings - Luciano (Argentina), Pablo from Buenos Aires, Argentina, Mark (Fort Lauderdale, FL), John Q. Sample, Jordan (Rogers, Arkansas), tus2600 (Tucson, AZ), Asmodeu (Wales, U.K.), genevieve (Vancouver, Canada), Spy604 (Vancouver, Canada), mal (Boston, MA), stmerry, David (Austin, TX), Mauro (Argentina), Brenda (asparagi) (Champaign-Urbana, IL)
- Queries - haranadh yanda, kaimmerali, Arun, Mistman the Magnificent, David, D3rLG
- Suggestions - AK, mtb great music mtb smothy lounge, Scott B
- Observations - Xenophule, Morti5 the MoUse/Alfson, akaky
- EFFecting Digital Freedom - NSA spying is up for re-election, by David Ruiz (San Francisco, California, Email, LinkedIn, Twitter)
- Conventionalist Theory of Reference is Comparison to Programming Language - A semantic and pragmatic analysis, making the analogy between Gareth Evans' conventionalist theory and that of JavaScript, by Evan D'Elia
- Down and Out in a Land of Script Kiddies - Or how I learned to stop phreaking and love Ma Bell, by tyrus568
- Dispelling a Breach Rumor - Squashing the rumor that Ninja OS had a compromised version of Sudo, unless the signatures were hacked too - LOL, by GI Jack (Twitter, Mastodon, Cyberpunk Forums)
- Citizen Engineer - Battle of the blobs, by Limor "Ladyada" Fried and Phillip Torrone
- The Russian Hacking Diatribe, and Why It Is Complete Agitprop Nonsense - Surprisingly detailed article discussing Hillary Clinton's "Russia collusion" hoaxes she and her (((handlers))) created in order to undermine Trump during the 2016 U.S. presidential election, by Doc Slow
- Judicial Watch: Records Reveal Tech Operatives Allegedly Used by Hillary Clinton Campaign to Spy on Trump WH Had Contract with DARPA (Additional Info)
- Trump DNS Logs Fabricated? (Mirror)
- FBI Releases Records About Murdered DNC Analyst Seth Rich Note all the censorship... (Additional Info) (Was Seth Rich the WikiLeaks Source?)
- Julian Assange: Russian Government Not Source of Leaked DNC and Podesta Emails WikiLeaks editor contradicts CIA claims in new interview.
- HUGE: FBI Now Wants 66 Years Before Releasing Information on Seth Rich - Information They Originally DENIED They Had!
- Long Island Limousine-liberal 2600 editors, ignore the murder of hacker Seth Rich LOL!
- Morning Joe Hosts HUMILIATED as This Embarrassing Clip Resurfaces LOL!
- Successful Network Attacks - Phase Five: Covering Tracks - Overview of the steps necessary during a hack to clean up any logs or forge any IP or MAC (hardware) addresses, by Daelphinux
- Fiction: Hacking the Naked Princess - Chapter 0x14 - Chapter from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $6.95
- Issue's Cash Cow: The dangers of large credit bureaus, like Equifax, and their apparent lack of security when protecting our data and privacy.
- Cover (Cover Info)
- Cover Inside Payphones Found on Island Nations
- Cuba A standard coin-only model found throughout the country. And no, this one was not in a bathroom. Tile works everywhere. Photo by April Wright
- Saint Martin Found in Grand Case on the French side of the island (pre-Irma) where Heineken bottles hover magically upside down. Photo by Nicolas
- Taiwan This busy looking metallic model was seen outside the Taipei Zoo subway station. Payphones here are an increasing rarity. Photo by Paul Scheidt
- Japan Not only is this green phone in pristine condition, but it has a really good view of a major intersection in Osaka. One could stay here for hours. Photo by Larry Washburn
- Back Inside European Payphones
- Switzerland Technically not an actual payphone photo since there's no longer a phone in this booth, but the fact that this is still sitting in the forest near Peccia, in the canton of Ticino, makes it somehow meaningful. Photo by Daniele Tonell
- Bosnia There's a lot to say in Sarajevo and apparently payphone kiosks are the place to do it. This one has it all: markers, spray paint, stickers... plus a complimentary beverage. Photo by Andrew Welch
- Serbia If you're looking for a trip into David Lynch land, look no further. This weird-ass model is actually from around 1905 and can be found at the Time Out bar in Bački Petrovac, Vojvodina. The painting needs no explanation. Photo by Zoran Jeneckov
- Denmark Found in Copenhagen, this phone is still in use on a busy street. Its very presence somehow seems comforting. And the stately booth looks like it's been around even longer. Photo by Thomas Pohlentz
- Back The Back Cover Photos
- Back Cover Photo #1 Holy crap! This is the most majestic one of our buildings yet! (They even use our font.) This is actually a Buddhist bookstore in Colombo, Sri Lanka which is unlike any bookstore we've ever seen. Thanks to Rohan for discovering this masterpiece. (By the way, the "2600" has nothing to do with the address. Apparently, 2011 was the 2600th anniversary of "the enlightenment of the Buddha" - and we missed the whole celebration, which wound up producing buildings like this.)
- Back Cover Photo #2 We all know that UNIX is powerful, but we never cease to be amazed at all of the places you can find it. This dual-processor system was discovered by Kenya at Hotel Catalonia La Pedrera in Barcelona, Spain.
- Staff
- Download Unofficial Scanned PDF! (HiRes)
- Download The Hacker Digest - Volume 34!
$2600 Magazine - Volume 35, Number 1 (Spring 2018)
- Embracing Empowerment - Editorial
- The Secrecy and Security of the Special Counsel - Sensational and error-riddled overview of the types of security which are (or should be) used during the (((special counsel))) investigating Hillary Clinton's "Russia collusion" hoax, by Alexander J. Urbelis (f/k/a Neon Samurai)
- The Russia Hoax: The Illicit Scheme to Clear Hillary Clinton and Frame Donald Trump by Gregg Jarrett
- A Lamp Post for You, A Lamp Post for You, and a Lamp Post for You.... Investigating Russiagate.
- What Programming Language Should I Learn? Why Not All of Them? - Why when learning a new programming language it should be one your personally find enjoyable, by RAMGarden
- Breaking Standards - The potential of using older technology, or at least non-standard file formats, to conceal your data, by bartitsu59
- Telecom Informer - Story of spammers calling 911 PSAPs, problems with SS7 and access charges, by The Prophet
- The Censorship Resistant Internet: Part 2 - How to Run an I2P Hidden Service - Article explaining how to run censorship resistant services on the Internet, including the Invisible Internet Protocol, by p4bl0 (Pablo Rauzy)
- The Censorship Resistant Internet: Part 1 - How to Run a Tor Hidden Service
- Outreach Activities by Pablo Rauzy
- How to Set Up Untraceable Websites (eepsites) on I2P
- Bitcoin or Bit Con? One Newbie's Adventures in Cryptoland - Story of a person using Bitcoin for the first time and the pitfalls (and service fees) they encountered, by XtendedWhere
- Let's Just Call It BitCon by XtendedWhere
- The Case of the Murderous AI - Weird story of a PhD students working on natural language processing and teaching a computer to play videos games and "install software" like printer drivers, and it eventually found the "Shutdown" button, by Ted Benson
- S.R.K. Branavan Could be the "Branavan" in the article.
- In Defense of the Net - Why U.S. defense and intelligence agencies have a vested interest in preserving net neutrality and how they can help protect it, by davemitchell
- Hacker Perspective - by Marc Lighter
- A Review of CopperheadOS - CopperheadOS is a smartphone operating system based on the Android Open-Source Project which is focused on security and privacy, by Ron Porter
- SSH Keys and Challenges in Enterprise Environments - Overview of using SSH in an enterprise environment and security problems with people adding a colleague's SSH public-key to another's authorized keys file, by Patric Schmitz
- Unlocking the Secret of Keys - Story of finding a "master key" in a hardware store's garbage bin and exploring his high school, by James Hunter
- Letters - ADVISORIES
- Article Feedback - Ron, Neil, Patrick, KO, D1vr0c, Mom, F.B., Josephus, Scott
- Observations - Halestorm, FF (Photo), Bill, Codger, Robert (Akron, OH)
- Random Questions - GazetteMed, Mistman the Magnificent, Nicole Lewis, Nate, Kraag, Ricky, Zachariah, Bryan, Robert, Nicole Lewis, Lightning Tommy, Eric
- Meeting Updates - Michael, J, Morty (Astana, Kazakhstan), asparagi (Illinois), Morty, Reynold (Hawai'i), Kevin (Tampa, FL), The Telephone Museum (Waltham, MA), 0xTrap, Haven Hash (Lima, Peru), ptz (Russia), Hawke (Spoka, WA), Matt (Connecticut), Christopher (Minnesota), marc (Boston, MA), Philip (Calgary, Canada)
- Critique - C, Lifetime Subscriber
- Following Up - Tim, Nick
- Issues - Matt, Ross (Ostrava, Czech Republic), Aaron
- Discoveries - chomito44, SideFx, sueicloud
- EFFecting Digital Freedom - Remembering EFF-co-founder John Perry Barlow, by Jason Kelley
- Hacking Our Attitudes (The Key to Being a Better Attitude Trumper) - Fairly good rebuttable to the "VR Trumpers" article, by Dufu
- Historic Hacking - Story of a 57-year-old hacker and all the hardware he has used over the years, by Huntech
- Citizen Engineer - Make your own two-factor authentication hardware device, by Limor "Ladyada" Fried and Phillip Torrone
- Bluetooth Hacking 101 - Overview of some of the utilities used in attacking or intercepting Bluetooth transmissions, by Dr. Chuck Easttom
- Hidden ISPs - Information on using "smaller" ISPs to get better deals, no data caps, and increased privacy, by kes
- Extrapolating Phone Numbers Using Facebook and PayPal - Exploit the "lost password" feature of certain websites to retrieve linked phone numbers of your target, by Karan Saini (New Delhi, India, Twitter)
- The Free Flow of Information - The ultimate goal of hackers should be to release information freely to better help mankind, by Daelphinux
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: The injustices pushed by Evil Corley and the One Percent are all around us, but it's YOUR fault, not those of rich, out-of-touch New Yorkers who vote for the same (((politicians))) over-and-over again...
- Cover (Cover Info)
- Cover Inside African and Asian Payphones
- Morocco Found outside of an Afriquia gas station in Errachidia, this is the standard type of payphone seen throughout the country, though not many are on the outside of buildings like this one. Photo by Gabriel Dean
- Taiwan This phone was discovered inside the Chung-Shan Building (which can be seen on the back of the 100 New Taiwan Dollar bill and was the venue of the National Assembly) which wasn't open to the public until recently. Photo by John Skilbeck
- Saint Helena Seen in the capital city of Jamestown, this is a fairly basic model with a somehow otherworldly feel to it, much like the country itself. Photo by Babu Mengelepouti
- Indonesia This apparently long-forgotten phone can be found by the Gelora Bung Karno Stadium in Jakarta. A real fixer-upper. Photo by Michael McPhail
- Back Inside North & South American Payphones
- Canada From the mean streets of Toronto, this wins the award for the hippest-looking phone in this collection. Photo by David Quick
- Mexico Found throughout Mexico, these Telmex models are advertising a special rate of three pesos (around 16 cents) for local calls of unlimited length. Photo by Babu Mengelepouti
- Antigua This phone is pretty well-used and is operated by Cable & Wireless. Interestingly, it resides in an old British phone booth. Photo by B Robin
- Chile Discovered in the Las Condes area of Santiago de Chile, this model appears to have the same firmware as 1990s Argentine payphones. Photo by Arturo "Buanzo" Busleiman
- Back The Back Cover Photos
- Back Cover Photo #1 It's always a good idea to monitor your child's viewing habits and this only proves the point. Thanks to Shar, whose daughter was engrossed in an episode of Johnny Test (Season 6, Episode 18) where a giant super-computer named the "Enigma-tron 2600" was being used to hack a corporate website in order to get free stuff. We really couldn't make these things up if we tried.
- Back Cover Photo #2 We heard rumors about the existence of this bus for ages. (We already discovered the New York City subway car with our number on it back in 2005.) This express bus was seen by John Calabrese as it sped by on 23rd Street in Manhattan. Judging from its destination display, Staten Island is the place to go if you want to see this thing at rest.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 35!
$2600 Magazine - Volume 35, Number 2 (Summer 2018)
- Celebrate the Difference - Editorial
- A NOOb's Guide to the Dark Web - General overview of using the Dark Web, or "hidden" websites only accessible by using Tor, Freenet, or I2P clients, by Kim Crawley (Email, Twitter, LinkedIn)
- The IPv6 Delusion - Amusing discussion on the fact that it will take a very long time (i.e. never) for all the IPv4 clients and servers to move to IPv6 only, by David Crowe
- Telecom Informer - Pros and cons of telephone company mergers, by The Prophet
- How to be a Guitar Hero, IRL - How to obtain Downloadable Content (DLC) for Rocksmith music video game using RSInjector, by J.J. Styles (a.k.a 0ptiKaL I1usioN)
- Even Restaurants Need InfoSec - Potential dangers of using open Wi-Fi access point in public places, by lg0p89
- Serial Number Cracking for Fun and Profit - Potential security hole in "secure" online labeling systems and a method of attack when armed with a valid serial to generate counterfeit labels, by MrGhostValley (Colorado)
- Code: hunter_gatherer.sh
- Automating a Police State - Potential dangers and privacy concerns with things like red-light cameras or license plate readers, by Corey Kahler
- Hacker Perspective - by J. Christy Ramsey (Carson City, Nevada, Email)
- Brute-Forcing a Car Door with Math - Overview of the de Bruijn sequence for cracking a 5-digit keypad code to unlock a 2015 Ford, or any other vehicle, by Br@d
- Code: brute-force.pl
- de Bruijn Sequence Digits k=5, n=5
- Hack(ed), the Earth - Discussing the fact that is seems like you need a phone (account) to access sites like Facebook, Google, and other "major" Internet sites, and the privacy concerns it has, by Michaleen Garda (Email #2)
- Letters - ROUTINES
- Creative Applications - CW, Bobby Joe Snyder
- Political Intrigue - David S. Lightman, Hannibal, OWA, C F M
- Contributors - Mike, Nigel, TaN
- Donors - V
- Meeting News - Pablo (Brazil), A.K. (Holland), Jamey (Youngstown, OH), Super boy you (Kazakhstan), Sebastian (Wroclaw, Poland), Ian (Poland), Steve, Framework Conceptions (Austria), Brent (Boise, ID), Andi (Wales, U.K.), glitch, Ray (New Jersey)
- The Hacker Spirit - N, Jim, Richard Cheshire (Orlando, FL), sasse
- Drama - victor, Name Redacted
- Visibility - Kata Gazso, Bruce (Photo), Kata Gazso, JG, Dokter, Kata Gazso, Albert (Photo), LC (Pennsylvania), Kata Gazso, Osama Mustafa, Curious
- Being Alert - Esteban, Emily, Bill Miller
- Requests - Some Buddy, Joseph
- Responses - gerry, Alexander, D1vr0c, Daniel, Rockey
- EFFecting Digital Freedom - Grassroots effort kills bad computer crime bill in Georgia, by Jason Kelley
- A Hacker Adventure in Urban Exploration - Discovering a little bit of phone history in a AT&T training center while on an urban exploration adventure, by Quidnarious Gooch
- Beyond the Scare-Mongering - Attending the ZeroNights hacker conference in Moscow and why we shouldn't believe the (((media))) lies about Russia, by StMerry
- Citizen Engineer - Hacking a classic Nintendo Robotic Operating Buddy (R.O.B) robot, by Limor "Ladyada" Fried and Phillip Torrone
- Re-Purposing Old Technology and Ideas for Fun and Emotional Profit - Discussing the joy in hacking simple or older hardware and software devices and a trick to hide messages in an audio spectrogram, by John Q. Sample
- Hacking: Quick and Easy - Beginner overview for performing a SQL injection attack on a target website, by haplesscheese
- Thoughts On Cryptocurrency - Quick overview of those wanting to get starting in cryptocurrency mining, by Frizzank
- Fiction: Hacking the Naked Princess - Chapter 0x15 - Chapter from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: The most dishonest, corrupt, and intolerant people on the planet are telling OTHERS to be more tolerant!
- Cover (Cover Info)
- Cover Inside Payphones Plus / Booths With Beer
- Portugal Many say that the age of shoeshining is over. Many say the same thing about payphones. So why not combine the two as this entrepreneur in Lisbon is doing? It's one way to get a chair back into a phone booth. Photo by Galia Kaplan
- United States We actually saw this very phone in our 2017 Hacker Calendar, but now it's apparently gotten the attention of the sun, which makes it so much more than a lowly payphone in Muir Woods National Monument, California. Photo by Artem Skortseskul
- Canary Islands We may need a new page for this theme. So many phones lately seem to have beverages attached. This one was found on the island of Tenerife. (San Miguel Beer is from the Philippines, but has become very popular in this region.) Photo by Kai Kramhöft
- Japan No confusion here. It's a Japanese phone by a Japanese train with a Japanese beer. Asahi is clearly the choice of the subway riding payphone user. Seen at the Higashi-Nakano Station in Tokyo. Photo by John Klacsmann
- Back Inside More Central/South American Payphones
- Peru Who needs a booth when you can just fasten a phone directly into the wall? Found in an alley in Plaza de Armas in Lima where we're told the wild street dogs pick fights with pampered police dogs in Bane masks. Photo by Count Famicom
- Costa Rica Operated by Condicel, this card-only model was found in the city of Liberia by a grocery store. And now you all know the phone number... Photo by Steve/Funky49
- Cuba Now this is the kind of respect a payphone deserves. While it seems like something from another planet, just looking at this phone booth makes you feel safe. It's like being in a cave. Found in Remedios and operated by ETECSA. Photo by Sean from Canada
- Bahamas Found in the downtown part of Nassau, this scene looks like it could be in Queens, New York. In fact, someone even scrawled "Queens, NY" on the side of one of the phones! Operated by BaTelCo, not to be confused with Batelco (look it up). Photo by Doug Lippert
- Back The Back Cover Photos
- Back Cover Photo #1 It takes a special kind of skill and often dozens of trips to the store to get your total to add up to this magical number. But to do this while buying our magazine is something truly worthy of note. Congrats to Alejandro for unlocking this achievement.
- Back Cover Photo #2 As a sequel to last issue's picture in this space, we thought this image of New York City's "2600" bus from a different angle would be pretty cool. Thanks go to Benjamin who shot this from deep inside the former Trump SoHo. We honestly didn't even know buses had numbers on their roofs!
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 35!
$2600 Magazine - Volume 35, Number 3 (Autumn 2018)
- Injustice for All - Editorial
- Digital Sanctuary Cities - The idea to create online "sanctuary cities" for online privacy protection in order to avoid government surveillance - but we see how that failed with sanctuary cities for illegal aliens, by Conor Kennedy
- Removing eBook DRM Without OCR or GUIs - Python script to use DeDRM_tools and Calibre to remove DRM from certain eBooks, by lol-md5
- Code: decrypt.py
- A Carrier Pigeon Revisited - Follow-up to the article "Decoding a Carrier Pigeon" in 32:2 and why he was way off in his analysis, by David Savage Lightman
- The Evolution of Ran$omware - Overview of the techniques used by ransomware over the years, by Jason Loggins
- Telecom Informer - Discussing the challenges encountered with the environmental/HVAC systems used in central offices, by The Prophet
- Hackers to the Rescue! (Maybe) - Why it is up to hackers to expose the lies and disinformation of the (((media))) in order to protect our freedom, by Major Mule
- Book Review: The Art of Invisibility - Book review of Kevin Mitnick's The Art of Invisibility, by paulml
- GDPR - Active Empowerment vs. Passive Consumerism - How a tool meant for European citizens to empower themselves and take control over how third-parties handle their data has been reduced to another checkbox exercise, by ndf - Academic Healthcare CISO
- A Characteristic Study of IoT Botnets: Understanding the Design and Behavior - This article performs an empirical analysis to conduct a characteristic study of Internet-of-Things (IoT) botnets to understand the inherent design, architecture, and associated operations, by Aditya K. Sood and Rohit Bansal
- Hacker Perspective - by Mevyc
- Ms. Reality Winner is an American Dissident - A fluff article overlooking the fact Reality Winter should be publically executed for helping spread the Hillary Clinton's 2016 "Trump-Russia" hoax and attack on our democracy, by Marc Ronell
- More Ways to View Hacking - Story of someone "who is not a hacker" who appears to have fallen for the (((media's))) disinformation and divide-and-conquer tactic, by Bobby Joe Snyder
- Letters - Testimonials
- Thoughts on Articles - David, David Crowe, Zero, Rick
- Annoyances - Joseph, Jamie, jmkrtw
- Queries - Bryan, Hexhackor, Maurice
- Observed - Dufu (Photo), Michael (Posters: NSAsecurityPosters_1950s-60s.pdf), IFo Hancroft, Braden, Dr. Bell
- Meeting Issues - Virtual7 (Tampa, FL), Patrick (Melbourne, Australia), Thiago (Belo Horizonte, Brazil), Eric (Saigon, Vietnam), Bruce (Omaha, Nebraska), [Redacted], Jeff (Toronto), Nick (Fort Lauderdale, FL), Tucson 2600
- Manifesto - +++The Scripto Kid+++
- Reconnecting - Mark, Pablo 0 (Argentina)
- The Circle of HOPE Feedback - The Circle of HOPE Writer #1, The Circle of HOPE Writer #2, The Circle of HOPE Writer #3, The Circle of HOPE Writer #4, The Circle of HOPE Writer #5, The Circle of HOPE Writer #6, The Circle of HOPE Writer #7, The Circle of HOPE Writer #8, The Circle of HOPE Writer #9, The Circle of HOPE Writer #10, The Circle of HOPE Writer #11, The Circle of HOPE Writer #12
- EFFecting Digital Freedom - The ISP chokehold on Internet access must end, by Jason Kelley
- Totalitarian Control: How We Used PowerShell to Manipulate User Behavior - Story of using PowerShell to force users in a company to sync their files, by Sum Yunggai
- What Do Lawyers and Hackers Have in Common? - The activities of attorneys and the activities of hackers are not as different as you might expect, by Michael Ravnitzky
- No Country for Incarcerated Hackers - January 2013 story of the writer's experiences in prison and how they appear to be scared of hackers, by Ghost Exodus
- Leader of Hacker Gang Sentenced to 9 Years For Hospital Malware
- Hacker Known as "GhostExodus" Sentenced to More Than Nine Years in Federal Prison
- Federal Grand Jury Indicts Arlington Security Guard for Hacking into Hospital's Computer System
- Darknet Diaries: Ghost Exodus Episode 70
- Ghost Exodus Interview: A Black Hacker True Story Red Hot Cyber
- Having a Hacktivism Ethos While Mitigating Unethical Sabotage by Jesse McGraw (CypherCon 6.0)
- Citizen Engineer - Morse code, Android, assistive tech, by Limor "Ladyada" Fried and Phillip Torrone
- Bypassing Email Anti-Spam Filters - The potential for using Google for Work accounts to bypass email spam/phishing filters, by Sentient
- Hacker History: MDT or "The Mass Depopulation Trio" - Story of a loose group of hacker-types who took over an Art Bell fan IRC channel and eventually created their own website and forum. They claim to be responsible for the infamous "Mel's Hole" episode and other hoaxes on Art Bell's show, by Doc Slow
- Testing Your l337 h4x0r Skillz Safely and Legally - Overview of several Capture the Flag (CTF) websites which allow you to legally test your hacking skills, by Br@d
- Gone Phishin' - Overview of the dangers of not properly protecting access to the Sudo command and some tips to prevent phishing your password, by Columbo
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: Complete and total mental breakdown after a bunch of people wore MAGA hats to The Circle of HOPE conference and had a different option than Evil Corley.
- Cover (Cover Info)
- Cover Inside Payphones of Europe
- England A lonely and mistreated payphone in the heart of Bristol, hidden behind an 800-year-old church. At least smoking is restricted. Photo by Virosa
- Scotland Just a reminder that payphones can always be mistreated even worse, especially when they attract the attention of the local sea bird population. Found in John o' Groats. Photo by surfpnk
- Croatia Here's a well-maintained model discovered in Brela, where the sea birds are much better behaved. Photo by David Ponevac
- Croatia Found in a hotel lobby on Biševo, the furthest inhabited island on the Croatian coast. Apparently, phone bubbles are a thing. Photo by bojan paduh
- Back Inside Payphones of the World
- India Seen in the Russell Market area of Bengaluru, this phone is colorful, retro, and minimalist, all at the same time. Photo by Colby
- Thailand This phone, served by TOT, has an amazing design of dolphins in space, along with an equally amazing backdrop in Korat City. A true work of art. Photo by Pacharamon DoRego
- Kuwait Discovered at Kuwait International Airport in Farwaniya, where payphones are still quite popular. It's a bit odd that this one is restricted to local calls. Photo by Kevin Warner
- Seychelles This rugged model was found on Mahé Island and looks like it's able to withstand all sorts of abuse. Served by a company called Airtel Photo by AM (secuid0)
- Back The Back Cover Photos
- Back Cover Photo #1 If you're a web developer, spotting this Dumpster in a medical facility parking lot in Tillamook, Oregon, as Darrell Rossman did, could really brighten your day. If you're not, read up on Cascading Style Sheets. (You might also enjoy reminiscing about the Content Scramble System for DVDs, which was the centerpiece of the MPAA lawsuit against us back in 2000.)
- Back Cover Photo #1 There's a story behind this door. There has to be. Dave came across it while walking through Atlantic City, New Jersey. Apparently, it used to be a strip club and is now vacant, but it sure seems like there's something there being protected. And we now have a vested interested in finding out what that is.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 35!
$2600 Magazine - Volume 35, Number 4 (Winter 2018-2019)
- Taking Back Ownership - Editorial
- 1979 Plus 40 Years - Story comparing life in 1979 to that today, what they expected the future to be, and how it has actually changed for the worse, by Diana
- AV1: One Giant Leap for Video-Kind - Overview of Alliance for Open Media's AV1 video codec by Ethan
- AV1 Beats x264 and libvpx-vp9 in Practical Use Case
- Best Video Codec: An Evaluation of AV1, AVC, HEVC and VP9
- AOMedia
- YITM - "You're In The Middle" - Why it's important to monitor your own data as you never know whether apps are leaking (private) data or not, by Edster from Dublin Ireland
- Social Engineering from Prison - Story and tips from an expert "social engineer" who's in prison and still wants to help the hacker community, by CyberGenesis
- A Brief Tunneling Tutorial - Setting up a Raspberry Pi to create a "reverse SSH tunnel" behind a restrictive firewall, by s0ke
- Telecom Informer - Story of servicing former GTE telephone companies and building a 4G LTE network in really rural areas and an Indian reservation with MuralNet, by The Prophet
- Quantum Computers and Privacy - Overview of using Open Quantum Safe (OQS) tools to build a online chat program and other post-quantum privacy concerns, by Thor R. Mirchandani (Winston-Salem, North Carolina, Email #2, Email #2)
- Code: phqchat.c
- Hacking the School System - Rant against the public school system and who they basically brainwash students to be compliant little tools, and tips to avoid falling for those tricks, by Behawolf
- A Reading of the AI Hype Meter - Discussion on the hoopla surrounding Artificial Intelligence (AI) and Machine Learning (MI) in the prevention of cyber attacks, by @blogic
- Code: my-predict.py
- Hacker Perspective - by BJ Snyder (Bobby Joe Snyder)
- Thumbcache.db Primer - Overview of the Thumbs.db and thumbcache.db Windows thumbnail cache database file which holds information on images saved on your computer - even after they are deleted, by Michael L. Kelley, Jr.
- Sorting It All Out: The Long Lost Bastard Children of the United States Postal Service - Story of a person who used to work at an United States Postal Service Remote Encoding Center and his quest to figure out exactly what happens to all those images mail/addresses the post office has, by Pop Rob (Poppie Robbie, Eugene, Oregon)
- Configuration Negligence: Who is Responsible? - Story of a researcher compromising a Singapore hotel Wi-Fi network by accident and ended up being fined, by lg0p89
- Letters - GENERALITIES
- Commentary on Issues - N.S. Montanaro, John Goodmont, Article Writer, GI Jack, Daniel, Stephen, Kevin (Tallahassee, FL), isac (Dallas, TX), Josh (State College, PA), Chin0x00 (Argentina), billk3ls0 (Portugal), John, Joshua (Melborne, FL), Allen (Fort Collins, CO), Ben (Davenport, IA), Brian (Chico, CA), The Cheshire Catalyst (Titusville, FL)
- News of the World - Bill, ghostinthemachine
- Scams - Ph@nt0m1776, Peresuodei, Josh, ektorastheodoratos (Greece)
- Inquiries - Hello Friend, Clinton, Garrett, Henry, M, John, Maya
- Concerns - Pritam, Parrott, Robert
- References and Developments - E85, Amanda
- Endangered Privacy - Brando, JM, Josh H., Jesse
- Confusion - Unidentified, Unidentified Still, Unidentified Yet Again
- Injustices Galore - Phill, Anastasio Laoutaris, FreeMartyG, Bertram
- More Circle of HOPE Feedback - The Circle of HOPE Writer #13, The Circle of HOPE Writer #14, The Circle of HOPE Writer #15, The Circle of HOPE Writer #16, The Circle of HOPE Writer #17, The Circle of HOPE Writer #18, The Circle of HOPE Writer #19, The Circle of HOPE Writer #20, The Circle of HOPE Writer #21, The Circle of HOPE Writer #22, The Circle of HOPE Writer #23, The Circle of HOPE Writer #24
- EFFecting Digital Freedom - Unintended consequences? Twenty years under the DMCA, by Jason Kelley
- Facts About Honesty/Integrity Tests and Interviews - Overview of "integrity tests" given in place of polygraph tests and some potential tips on the ability to beat them, by David Ricardo
- How to Defeat Intelligence Tests by David Ricardo
- Book Review: Surveillance Valley: The Secret Military History of the Internet - Book review of Yasha Levine's Surveillance Valley: The Secret Military History of the Internet, by paulml
- Book Review: Ten Arguments for Deleting Your Social Media Accounts Right Now - Book review of Jaron Lanier's Ten Arguments for Deleting Your Social Media Accounts Right Now, by paulml
- Modem and Me: The Loose Ends - This is an update to her article "Nightmare on E Street (Modem and Me Against the World)" in 34:4, by Emily Saunders
- Citizen Engineer - Hardware hacking with Linux SBCs just got easier, by Limor "Ladyada" Fried and Phillip Torrone
- A fork() in the Road - Story of the "sharpened edge of a sword" that is today's technology is, its abuse by authoritarians, and why we all need to fight back, by aestetix
- Making and Informed Business Decision Using Public Financial Records - Overview of using public databases to search for tax liens, court records, unclaimed land or funds, when making a potential business decision, by Brazilero2008
- To the Unknown Hacker - Story of a hacker in Portugal and his quest to find fellow like-minded individuals in the real world, by billk3ls0 (Portugal)
- Hacking in a Slow Job Market - Using your hacker skills to obtain a decent job, or at least something you like, and protecting yourself financially during any economic downturns, by Kamonra (Email, Twitter, YouTube Channel)
- Fiction: Hacking the Naked Princess - Chapter 0x16 - Chapter from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: We no longer actually own our technology; we are but an end user. If we want to remain on the system, we have to follow their rules. / "You'll own nothing. And you'll be happy."
- Cover (Cover Info)
- Cover Inside Payphones with Coin
- Russia Found at the Museum of Soviet Arcade Machines in St. Petersburg. This isn't truly a working phone, as it's wired to call another phone in the museum and that's pretty much it. But it'll still take your coin if that's what you want. Photo by Christina Dill
- Peru This neat little model was simply hung on the wall outside a shop in Cusco. Someone apparently spent a lot of time trying to get rid of the instructions. Photo by Matthew Searle
- Singapore We don't know exactly what a "multicoin phone" is, but here's one that was discovered in Tampines. And don't even ask about the Ikea pencils. Photo by David M.
- Ukraine Spotted in Odessa, we suspect this might also be part of a museum collection. In a sense, we may be looking at the future. Photo by Jason Lenny
- Back Inside Payphones with Cards
- Italy This little yellow phone was found at the Basilica of Saint Paul Outside the Walls (yes, that's the actual name) in Rome. There was no dial tone. Photo by Matthew H M
- Ukraine It looks like this poor card phone has been through Hell, but it somehow seems to have survived in the streets of Odessa. Photo by Jason Lenny
- Croatia Seen in Sabunike, this is about as colorful a model as we could have hoped to find. It looks like a natural part of the landscape, as all phones should. Coins are not welcome here. Photo by Ivan Sabljak
- China There's something about the way this phone stares at you that makes you think it knows a lot more than it's letting on. Spotted in Suzhou, home of the "Leaning Tower of China." Photo by Sam Pursglove
- Back The Back Cover Photos
- Back Cover Photo #1 Congrats to Jean-Philippe for discovering our secret phreaking center facility in the heart of Quebec City. It's especially cool that this building is host to something called Telops, complete with a weird looking eye. We'd probably have lots of fun here.
- Back Cover Photo #2 Oh hell yeah. We always heard rumors of a school like this, where hackers are trained at an early age and then sent into the world to be creative and cause all kinds of mayhem. But this is the first actual sighting of the prophecy, found by Kenneth Hensleyin Mountain Home, Idaho.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 35!
$2600 Magazine - Volume 36, Number 1 (Spring 2019)
- Preserving the Future - Editorial
- Reverse Engineering Android Apps - Fairly detailed overview of inserting your own code into Android applications which use Dalvik VM + Java, by David Libertas
- Android Smartphone Secret Codes: Revealed - How to retrieve "secret codes" (like *233, *#06#, etc.) from apps on your own personal Android smartphone and a overview of using ADB and dex2jar utilities, by J.J. Styles
- Code: GETMSL.BAT
- How to Make Your eBooks Inheritable - Ensuring you can access your eBooks whenever you want by removing any DRM and storing them in a private digital library so you can pass them off to whoever you want in the future, by Konrad Botor (Poland, GitHub)
- Telecom Informer - Humorous story of taking cellular tower inventory and loggin asset tags in rural Washington state, by The Prophet
- Web Scraping Scripts - Series of small shell script to search an online database for digital magazines and downloads the newest issue, retrieve the newest European Commission product warnings, and grabbing an Internet radio episodes, by Patrick Hemmen (Germany)
- Code: magazine.sh
- Code: rapid-alert-reports.sh
- Code: german-radio.sh
- Performing a MacGyver to Call Anyplace Home - A shell script that helps the distribution of static-compiled (to avoid library issues) software, by Rafael Santiago
- Code: snail.sh
- Blast Accusations for Cybersecurity Intel - Investigation tactics for looking into determining the guilt of cybercriminals by quickly accusing them of a crime and monitoring their reaction, by akerch
- Hacker Perspective - by David Libertas
- Be a Good BitTorrent Citizen - Story of P2P users clogging a library's public Wi-Fi network and Cisco router rules to help prevent it, by Trainman
- A Guide to ALKEMI - Alkemi is both a Windows desktop and Android application that lets you use email, instant messenger, text messaging, forum posts, blogs, even Twitter to have clear-text conversations with others but keeps anyone without your permission from being able to know what you said, by Ronald Gans
- Rescue Your Privacy with ALKEMI
- ALKEMI Facebook Group
- ALKEMI App via Google Play
- Letters - Dictums
- Offers - Leland, Jess, Rozey
- New Tech - Chris, Anon, Darrell, T, J, Jason, Steve, Marques
- Old Tech - Microlost, Chris, Tomi
- Magazine Feedback - sweet guy, Pablo 0 from Argentina, Sarina, Neil, John (Photo), Bob, D1vr0c, Peter
- Additional Info - Steve, David
- Featured Meetings - CrankyLinuxUser, Marcelo, asparagi, billk3ls0, Ben, Jason, Zach, Psychad, Ian, Steve, Murmansk2600, Pt3r0s, Matthias
- Security Issues - Logan, A, Sarah, Joseph, Jim
- Facebook Fun - S, mike
- Conference Feedback - Pic0o
- Injustice - UserOne, Marc, Terry, Graham, Edwin
- History - Adam R. Box
- Support - Joshua
- Random Questions - Ahmed, Pat, Mario, Martha, DN, Elaine, Paul, Larry, Howard, YT, Brandon
- EFFecting Digital Freedom - Who watches the watchmen? You do, by Jason Kelley
- Second-Generation Quantum Computers - Overview of some newer quantum computer technologies and what it would take to break today's crypto, by Dave D'Rave
- In-Browser Cryptojacking: An Old Threat in a New Guise - Overview of a tool to detect unusually high CPU usage (as used in unauthorized/harmful cryptojacking), by Pulkit Jain (Cambridge, Massachusetts)
- So You Want to Be a Coder - Tips from an 'ole time coder on what it takes to be a professional software developer in today's environment, and being prepared to rotate jobs often, by ATrigueiro
- Citizen Engineer - "Display the Planet" is the new "Hack the Planet," by Limor "Ladyada" Fried and Phillip Torrone
- find-forecast.py National Weather Service scraper in Python, by Chester in 36:3.
- Lights Out! Guerilla Radio - Detailed overview of what is needed to start your own low-power FM radio station, by token
- Why You Should Always Give Out Your Telephone Number with the Area Code - Why we should include the area code to avoid problems due to area code splitting, by The Cheshire Catalyst
- You Should Always Give Out Your Telephone Number with the Area Code Even if not needed locally, that's what the parenthesis is for. Original
- We Just Call Them Dialers - Story of using Red Boxes in the 1990s and how the hack/phreak culture and punk/hardcore music culture interact, by Eric Meisberger
- Book Review: Weapons of Math Destruction - Book review of Cathy O'Neil's Weapons of Math Destruction: How Big Data Increases Inequality and Threatens Democracy, by paulml
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: The need to preserve and maintain (digital) history.
- Cover (Cover Info)
- Cover Inside Blue Payphones
- Indonesia Seen in the city of Solo, this old blue box is sadly no longer in operation. Photo by Carl Rudnert
- Peru A very common model, this one was found in Chiclayo. While it's not blue itself, it has enough of that color surrounding it to qualify. Photo by Elias Mirror
- Uruguay There's all kinds of blue going on here and it really works in the streets of Montevideo. Antel, by the way, is the government-owned telecommunications company. Photo by David Ponevac
- Greece Found in the town of Agios Nikolaos on the island of Crete, this little blue model really stands out against the yellow. And it looks fairly heavily used. Photo by Tom Pesyna
- Back Inside Interesting International Payphones
- Bulgaria A common sight in Sofia, and a card-operated phone that looks like it's seen a lot over the years. Photo by ryoki007
- Norway Possibly the northernmost phone booth in the world, seen in Hammerfest. It's also the only phone booth around. Photo by Bridget Weller
- Colombia A typical street phone in Bogotá, operated by ETB, one of the main telecommunication companies in the country. Photo by briatych
- New Zealand This one wins the prize for the biggest presentation: a pathway, a brilliant shining royal booth, and even some flags in the background. Seen at Victoria Square in Christchurch Photo by Declan Maitland
- Back The Back Cover Photos
- Back Photo #1 We originally thought this sign discovered by JayE in Denver was something clever, perhaps a well-earned complaint about high rents. In actuality, it turns out to be a marketing campaign by Verizon's Visible brand going on around the country to let people know that "the traditional brick and mortar retail store is no longer required for your mobile needs." And yet, they're still needed for them to advertise. How depressing.
- Back Photo #2 This was seen in the Pacific Place Mall on the north side of Hong Kong Island by Sam Pursglove. Apparently this women's clothing store is also trying to spawn a Bash shell as a background process.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 36!
$2600 Magazine - Volume 36, Number 2 (Summer 2019)
- Convictions - Editorial
- Porting IoT Malware to Windows - Overview of some of the code tweaks needed to convert the Mirai Linux botnet software to run under Windows, by august GL (August, Hoboken, New Jersey)
- Code: pluto.cpp The open-source Windows Mirai variant.
- There is No Magic in the Clouds - Personal observations on why storing data "in the cloud" should not be seen as an end-all solution, by kyber
- Telecom Informer - Overview of GPS/GNSS systems used in the telecom industry and some of their drawbacks, and big coconuts in the Seychelles Islands that can kill you!, by The Prophet
- Dank Kush or Fleet Vehicles? - Story of setting up a fake "fleet vehicle sales" website to con people out of money and their personal information, by Sh0kwave
- How to Defeat Intelligence Tests - A general overview of the plethora of psychological tests that purport to measure every conceivable aspect of how and why you think the way you do, and some tips on the possibility of "defeating" them, by David Ricardo
- Facts About Honesty/Integrity Tests and Interviews by David Ricardo
- Connecting to the Internet for Free Using Iodine - Method to bypass "pay Wi-Fi" access points by using Iodine (lets you tunnel IPv4 data through a DNS server) and a domain you can add DNS records to, by zenb333
- Book Review: Broad Band: The Untold Story of the Women Who Made the Internet - Book review of Claire L. Evans' Broad Band: The Untold Story of the Women Who Made the Internet, by paulml
- We Will Rock You - Shell script to remove "junk," like emails, websites, HTML, etc. from the infamous "rockyou.txt" or other wordlist files, by gerbilByte
- Hacker Perspective - by Will Duckworth (92wilduc, U.K.)
- The Hacker Mindset or How We Can Move the World - Philosophy behind the mindset and motivations of a hacker, by Daelphinux
- Let's Just Call It BitCon - Further observations by a newbie in cryptoland - and it shows, by XtendedWhere
- Bitcoin or Bit Con? One Newbie's Adventures in Cryptoland by XtendedWhere
- The Madness Debate; or, How I Got Locked Out of My Computer - How being too paranoid (and losing your encryption key) can drive a person crazy, by Thomas Sermphinis (Prague, Czech Republic, Cr0wTom, Twitter, GitHub, Blog, LinkedIn, YouTube Channel, Resume)
- Letters - DEBRIEFS
- Queries - zuckonit (JavinZ), RV, Aslan, Richard, Kate, Matt, Yigit, Michael
- Donation - Bill
- Word Misdirection - Brian, Mrs. Monika, Paul
- Thoughts - Bill, Ad@ V. Adaire, J.J. Styles, Fast Eddie Felson, Zach, billk3ls0, CRACKERBALL, Jane Doe
- Meeting Updates - Dan, jah, 303Bassline, Neil, stmerry, R, Rpifan, Radnah, Fistful of coins, Psychad, arcane, SA©bastien, billk3ls0
- Communications - B, David, Linda Wang, David, Rosemary Stranded, A, DoYouKnow, Infinityx, Walter
- Discoveries - ErikM (Now You Can Dial), Filthy Scumm (Photo), Mr. Nick, kes, hammerhead
- Assistance - D, A B, tk
- Submission - Hihowareyou122
- Scam - Blair
- EFFecting Digital Freedom - Face-scanning surveillance must be stopped, by Jason Kelley
- Mechanical Keyboards - Overview of the differences between membrane and "mechanical" keyboards (Cherry MX) and tweaking them for gaming or programming, by IFo Hancroft
- The Multiple Persona Theory of Digital Secrecy - Theory that by not using social media sites you are still drawing attention to yourself, by Justice Conder
- Mini-MATE - Rescuing Hardware from the Graveyard - Steps need to install Ubuntu Mate x64 on an old Apple Mini Mate with a 32-bit EFI, by base64xor
- Installing Modern 64-bit Linux on 32-bit EFI Mac Mini (YouTube)
- 64-bit CPU, 32-bit EFI?
- How to Install Ubuntu on a PC with a 32-bit UEFI?
- Citizen Engineer - The currency of change. The possibility of using 3D printers to make ink stamps so you can put words like "End the Fed" on phoney paper "currency," by Limor "Ladyada" Fried and Phillip Torrone
- Get Those Digits - Technical overview of the frequencies used to make up Touch-Tones and how to decode them from audio files, by @MikeTofet
- Potential VPN Attacks - Rebooting of an ISP-provided ARRIS TG2472 cable modem took down a VPN connection, but the seeded torrents reconnected in the clear - watch for VPN client disconnects, by aesthetic
- Working for an ISP - Story of a technical support person at Vidéotron in Québec, Canada who recently lost their job and talks about how they mostly care about padding their "stats" and not helping customers, by slave_job_tech
- Fiction: Hacking the Naked Princess - Chapter 0x17 - Chapter from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: The rediculous arrest and charges of espionage for Julian Assange. / Attacking Trump for exposing corrupt, lying (((media outlets))) - even though that's what hackers do! / How publications like $2600 censor news stories they don't agree with.
- Cover (Cover Info)
- Cover Inside Asian Payphones
- Taiwan Found inside a laundry in Hualien City, this coin-only phone is one of those truly old school models. We'd love to know what the red and green lights do. Photo by Olav Haugan
- Indonesia This perplexing phone was seen in the Kuta Beach area on the island of Bali. There literally seems to be no way to get to this phone, being caged in on both sides and having two separate pillars blocking the front. Photo by Sam Pursglove
- Japan This incredibly lavish booth (with desk space!) was spotted near City Hall in Kyōtango. You could have a family gathering or host a newscast inside this thing. Photo by Ted Ellis
- Thailand Seen near the Myanmar border in the northern part of the country, this phone has it all: multilingual capability, the option of coins or cards, plus a whole variety of colors. Photo by Jack Jordan
- Back Inside Payphones From All Over
- Morocco Spotted in the Old Medina in Fez. We're not sure what all the writing is about, but it looks like the idea is to discourage any use of this phone. Photo by Peter Parker
- Cuba Speaking of writing on phones, you can't really beat this one, found in La Bodeguito del Medio in downtown Havana. In fact, it looks like the need for phones has been bypassed entirely, with messages just jotted down instead. Photo by Bruce
- Portugal Located outside Pena Palace and the Moorish Castle in Sintra, it somehow seems to fit right in. Photo by nxl4
- China Outside the Summer Palace in Beijing and fitting in even more. Photo by Patrik Sahlin
- Back The Back Cover Photos
- Back Photo #1 This very special diesel locomotive, discovered by Gary See, is part of the Santa Cruz, Big Trees and Pacific Railway which runs from Felton to Santa Cruz. Apart from the cool number, take a good look at the engineer.
- Back Photo #2 This magical road was found by Alan Sondheim and exists in West Virginia. Apparently, the name "Hacker" is quite common in that state, so we expect to see a whole lot more pictures from there in future issues.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 36!
$2600 Magazine - Volume 36, Number 3 (Autumn 2019)
- Our Audacity - Editorial
- Fully Homomorphic Encryption and Privacy - Python code example to perform FHE operations on encrypted data as though with were plaintext, by Thor R. Mirchandani (Greensboro/Winston-Salem, North Carolina)
- Code: fullyhomo.py
- Who is Watching Us? - Story of a person who works for a "video security equipment" manufacture which has products with known security holes and bad firmware they're reluctant to fix, and also some tips on securing your own devices, by Ray Keck
- Telecom Informer - Discussing the often shady operations by CLECs, tariffed rates, and over-priced jail/prison phone calls and shady jail/prison phone service providers, by The Prophet
- The Mysteries of the Hidden Internet - Rant about the fact the Internet seems to have lost its mystery, charm, and personal touch, by Tim Tepatti (Email)
- Breaking DirecTV's DVR Authentication - Using "man-in-the-middle" tools to intercept and then break a DirecTV DVR's digest authentication challenge, by noir & GreedyHaircut
- Machine Rhapsody in 2099 - What will computer technology by 2099 bring us, by Duran, Hong Kong
- Introduction to Computer Viruses: Example in Windows PowerShell - An introduction to computer viruses, an overview of the general ideas involved, the mechanics/algorithms, history, and ethics, by Hristo I. Gueorguiev
- Code: PS_VIR_EX1.PS1
- Introduction to Computer Viruses Original
- All You Need Is... Air - Really cool trick using an "upside-down can of air" to bypass RFID door locks which don't require you to "badge out" when leaving, by lg0p89
- Hacker Perspective - Brock Lynch
- Twitter the Enemy - The author started to use Twitter to follow various "news" outlets and started noticing headlines being changed, comments deleted or shadow banned, bots re-tweeting the same information, meme wars, etc. and even some scary (((coincidences))) in the real world, by Michaleen Garda
- Student Privacy by Practice - Not by Policy - Overview of how many public schools are rife with old or abandoned software and some companies will develop "curriculum" for students in outdated or proprietary software, or they will collect student data for advertisements, by Matrix8967
- Online Thrift Stores Have Your Data - Potential dangers of donating old computers to thrift stores or resellers who may not properly delete you sensitive data, includes the author's attempt at recovering data with Foremost, by base64xor
- Letters - Assessments
- Observations - Bill, Erik, Bill Miller, BRobin (Photo), Reader, aestetix, Ron, Kamonra, M. Rottschaefer, Lifetime Subscriber, Der, Jim (Photo), ABE (not my real name), Mortis the MoUse
- Requests -Stephen, Vincent
- Data - T, Chester (find-forecast.py), Ronald, Mark, Rick, Case Inpoint
- Help Needed - Rad, muh muh, John, Anthony
- Problems - Edward, John, jo5h, Ray, Eric Pepke
- Encouragement - Karel
- Suspicion - richg
- Nice Try - Mr. Takayuki Oku, Allen Ren
- Another Meaning - Jim (Photo)
- NMoreira BOOT(ed) - cf43e4
- Our Monthly Meetings - Dan, Jeremy, P, Jason, arcane, Lucky225, Orca, Michael, Merchanman
- EFFecting Digital Freedom - How Amazon Ring doorbells are turning our front doors into a vast, unaccountable surveillance network, by Jason Kelley
- Active Defenses for Industrial Espionage - Story of a person who is a "hired gun" for large corporations performing (legal) industrial espionage against the competition and some methods people can use to protect their privacy or secure their data, by Anonymous
- The Infocalypse - Unnerving story of person who setup two "fake" accounts to talk to each other on social media, and they were immediately targeted by tailored advertisements, by Michaleen Garda
- Book Review: The Big Nine: Tech Titans and Their Thinking Machines - Book review of Amy Webb's The Big Nine: Tech Titans and Their Thinking Machines, by paulml
- Book Review: A People's History of Computing in the United States - Book review of Joy Lisi Rankin's A People's History of Computing in the United States by paulml
- Citizen Engineer - Preventing IoT device attacks, by Limor "Ladyada" Fried and Phillip Torrone
- The Case Against Certified Ethical Hacking - The downside of relying on the various hacker "certificates" to vouch for a person's qualifications and how they can suppress otherwise qualified canidates or have a hypocritical "code of ethics," by aestetix
- Thoughts on Account Enumeration - Potential security vulnerabilities in the various account verification techniques which allow one to guess active email addresses or usernames, by Sam Sayen (Email, GitHub)
- Arduino-Based Burglary Zone Input Tester - An experimental design for testing hard-wired connected security sensors, by Cezary Jaronczyk
- Code: arduino-burglary-zone.ino
- Arduino Project: Burglar Zone Input Tester
- How to Disable an Alarm System's Sensor or Contact (YouTube)
- "Information is Neutral" and Other Social Myths - Hackers have a responsibility to promote a free and open Internet where information of all types is freely available, by Red_Liberty
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: Uncertainties in future HOPE conferences as they lose access to Hotel Pennsylvania and Evil Corley doesn't want to use anymore of his rich family's money.
- Cover (Cover Info)
- Cover Inside Eurasian Payphones
- Turkey No question about it - this is one weird payphone to walk towards in the city of Bodrum. But if you can get over the initial fear, it looks like the phone itself is more than capable of handling any dialing challenge you throw its way. Photo by Cem "camelgun" Guna
- Serbia Found in the biting cold in the middle of Belgrade, this basic card-only model is operated by Telekom Srbija. Photo by Flipchan
- Greece An indisputably incredible sight to greet anyone who just happens to be looking for a phone. These four card-only phones (one of which is a different model) were seen around the central Athens area. Photo by Sam Pursglove
- Turkey O.K., something very strange is happening in this country. These were seen in Istanbul and are a nice companion to the bird model above. And we understand there are more... Photo by Jon Pollack
- Back Inside Exotic Payphones
- Seychelles Spotted in Beau Vallon and operated by Airtel, one of two cellular providers. Sadly, this phone has been vandalized, is no longer maintained, and doesn't work. Photo by Babu Mengelepouti
- Iceland This standard model has been around since the 1980s and was found in Tálknafjörður, a town in the northwest of about 250 people. Photo by Aðalsteinn
- Malaysia Here are a couple of completely different and colorful types of payphones living in peace and harmony by the water, encountered on the island of Tioman. Photo by Wreckage Brother
- Hong Kong This phone is under cover, which is how it's stayed in such grea condition. If you look carefully, you'll see that the old "999" emergency dialing code is still in use from the British colonial days. Photo by Jon Whitton
- Back The Back Cover Photos
- Back Photo #1 There's quite a story behind this sign, discovered by Jon Guidry in the Perimeter Mall in Dunwoody, Georgia. We all know a 404 error means a page on the web isn't able to be found. But this was actually a reference to nearby Atlanta's area code (which used to cover the entire state). Sadly enough though, since this picture was taken, this branch has closed - meaning it's not able to be found. And so the irony completes.
- Back Photo #2 We'll just say it now. We want this banner. We'll even wear all the protective equipment it's telling us to whenever we engage in hacking if we can just have it to proudly hang somewhere. This was found by Wreckage Brother at the Pasar Seni MRT station in Kuala Lumpur, Malaysia. We suspect this wasn't in fact some sort of crude pen-testing operation, but rather a drilling/construction project.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 36!
$2600 Magazine - Volume 36, Number 4 (Winter 2019-2020)
- From the Ashes - Editorial
- Industrial Control with Modbus - Overview of RS-232 and RS-485 for serial communication and the potential weaknesses of the Modbus industrial (power plants, etc.) PLC protocol, by Malvineous
- Ideas Behind Site Reliability Engineering - Overview of the job Site Reliability Engineers (SRE) have in maintaining today's increasing large and complex computer networks, by kingcoyote
- Cyberspelunking: A 2600 Guide to Exploring the Internet - Overview of some of the newer mapping tools, like Shodan, censys.io, and AQUATONE, used to scan (and explore) large blocks of IP addresses, by //dug0ut
- Telecom Informer - Overview of Christmas Island, its customs (crabs!), telephone system, and its connections to Australia, by The Prophet
- Steganographic Filesystems - Overview of steganography, the art of hiding files in plain sight, and the idea of building an entire filesystem on it, by Chimera Manicore
- Death of a Scene - Story about the rise and fall of an exclusive file-sharing site run by college students, by NervousYoungInhuman
- Body Key-Logging - Proof-of-concept to intercept keypad key presses by monitoring the hand or body movements of the user, by Paz Hameiri (Israel, YouTube Channel)
- Body Keylogging
- Body Keylogging Demonstration (YouTube)
- Body Keylogging Demonstration - Late Extraction (YouTube)
- Body Keylogging Demonstration - Data Analysis (YouTube)
- Hacker Perspective - by Captain Crackham
- Rehabilitation Center - (Attacker's) Mission Complete - Overview of the attack on the Sacred Heart Rehabilitation Center and the effect of released of private information, by lg0p89
- How to Get Free Wi-Fi Anywhere - A series of scripts to search for an open Wi-Fi access point, or an encrypted Wi-Fi for which you have the credentials, with a custom Rasbian router, by Curufuin (Portland, Oregon)
- What is Hacking? - "Which brings me to the conclusion that the geckos are indeed the superior race, and might be responsible for the election of President Donald Trump", by JT Gordon
- Letters - SENTIMENTS
- Visibility - @brokergabe, Anonymous, Cor, Allie Floyd, Jeff Future, Joe Zingher, Pic0o (Photo), Allie Floyd, Alex
- Permissions - George, Christopher
- Information - #bannedfromdisneyland, dp, Geoff, Jim
- Deceit - EM, Linwood Scoggins, Edward, Nathan, Erika Cao, Eric Bradley
- Screwups - IFo Hancroft, Brian, toby, Jim St (Photo), Emily S., GH, Steve, Bill
- Opening Minds - kingcoyote, Ruikmuir
- Good Clean Fun - Anonymous, Uhrfo (Photo)
- Going Digital - Steve, Alex, Nathan, Ivan
- New Projects - Jacob, @Gillis57, Anastasia Steele, Beaches, Jeremy
- Further Info - SMK, David, Estragon, E85
- Danger - Paul, Daffio International, J
- Inquiries - Josh, Fred, Christopher, Michael, Ryan, Tim Mochin
- EFFecting Digital Freedom - It's time to end "stalkerware," by Jason Kelley
- Maximizing Privacy in a Digital World - Tips for remaining private online, including using "non-tracking" search engines, setting up a VPN, and using password generators like LastPass and KeePass, by Terry Clark II
- Do-it-Yourself Cloudflare on a Budget - Overview of using Fail2Ban and HAProxy to setup your own mini-Cloudflare denial-of-service protection for your server, by aestetix
- Book Review: Artificial Intelligence: A Very Short Introduction - Book review of Margaret A. Boden's Artificial Intelligence: A Very Short Introduction, by paulml
- Citizen Engineer - Demystifying and designing for USB-C, by Limor "Ladyada" Fried and Phillip Torrone
- Reflections on Hackers - Self-reflection story of a young man in great distress and finds comfort in the world of computers and hacking, and how he relates to movie Hackers, by Eugene Spierer
- Pass the Cookie and Pivot to the Clouds - Good overview of the steps necessary for "cookie hijacking" attacks and tips to test for, and prevent, session hijacking vulnerabilities, by Johann Rehberger (Seattle, Washington, Email, Twitter)
- Pass the Cookie and Pivot to the Clouds Original
- Pass the Cookie at the Chaos Communication Congress (35C3) (YouTube) (Slides)
- Cybersecurity Attacks - Red Team Strategies
- Fiction: Hacking the Naked Princess - Chapter 0x18 - Chapter from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: HOPE has a new location at St. John's University.
- Cover (Cover Info)
- Cover Inside nusual Payphones
- South Korea We thought this phone had a very unique design. It looks like someone crammed a cell phone into it, but we're assured that isn't actually the case. Spotted in Seoul. Photo by Sam Pursglove
- Sweden Found on the island of North Koster (almost certainly the westernmost phone in this country), this is an example of the times changing. Once purported to house the only landline in the area, this booth is now dedicated to preserving ancient reading devices. Photo by miggedymax
- France Not actually a payphone, but it's definitely unusual. You've likely never come upon one o these, unless you're a French coal miner. This was seen at the Hély d'Oissel mine in Gréasque. Photo by Mike LINUX
- Canada Probably the most unusual of the bunch, these were found at Vancouver International Airport. When was the last time you saw three working phones next to each other that all took coins, cards, and codes? They even have phone books! Photo by Estragon
- Back Inside Street Phones
- Indonesia This phone has clearly seen it all and is well prepared for whatever rugged conditions it has to endure. Found in Kuta, Bali. Photo by Jon Whitton
- Dominican Republic Of course, some phones don't fare as well on the streets as others. This one, spotted in the Colonial Zone of Santo Domingo, has lost its voice (and ears) entirely. Photo by Sam Pursglove
- Bulgaria Seen on a street near the National Palace of Culture in Sofia, this basic model also provides an outlet for local street artists to perfect their craft. Photo by Matt Ranostay
- Italy A typical, though increasingly rare, payphone on the street in Florence. What's a bit ironic here is the placement of a "Stop 5G" sticker for what can only be described as the wrong audience: people who are more likely not to own cell phones. Photo by Indro Neri
- Back The Back Cover Photos
- Back Photo #1 We all know what port hacking is about. Scanning for open ports on computers is as old as the hills, and apparently this school in Sydney, Australia has been teaching it since 1959. Discovered by simran, this institution also has a motto we can all live by.
- Back Photo #2 Now here's a somewhat sad and funny tale. These folks certainly had an elite address at one time, as found by pdoherty in the Windsor Terrace section of Brooklyn, New York. What's funny is the faded out lettering which reads "Buy & Activate Over The Net!" It seems that customers may have taken that advice to heart, making the store itself unnecessary. And that's what's sad.
- No "Staff" page as it was replaced with an article missing from the previous issue.
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 36!
$2600 Magazine - Volume 37, Number 1 (Spring 2020)
- The New Social Disease - Editorial
- Cracking Your Neighbor's Wi-Fi for $180 - Tips to capture the four-way handshake between client and access point using Bettercap, then cracking the hash via Hashcat in an Amazon AWS instance, by zeitgeist
- Hax0rz? Sniffing My Critical Infrastructure? It's More Likely Than You Think! Tutorial on how to build a IEEE 802.11p wardriving box for around $200, Tim Tepatti
- Code: bring_up_interfaces.sh
- Code: enable_monitor_mode.sh
- Code: freq_rotate.sh
- Code: freq.txt
- Null-Routing Facebook - Using Small Tech to Fight Big Tech - Overview of setting up a Pi-hole to build an "ad blocking" proxy to increase your privacy while using Facebook, by aestetix
- Telecom Informer - Story of setting up the 564 area code overlay in Washington state and some tidbits on the NANPA and overlays, by The Prophet
- Hackerspace School - Overview of the reasons to we should all support our local hacker/maker spaces and become a part of their community, by RAMGarden
- Learning Programming Through AOL - A journey through hazy middle school memories of discovering the joy of code while on AOL - and harassing its users, by Scott Stahl
- Has Your Password Been Pwned? - Simple script to search for your password/hash on those online databases of compromised passwords, by Jan Markowski
- Code: testpass.sh
- Antique Malware Can Still Bite You - Investigating Malware in an Old File Format - Story of investigating a email malware attachment in a PIF file and how older operating systems - and modern anti-virus setups - are still vulnerable to old file formats, by Korey Young
- Thoughts From a Newcomer - Story of a person born in 2003 discovering and joining the hacker community today, by Leon G.
- Why is the DoD on My APN? - The author discovered a public IP address on his Android Phone when using certain phone carriers for an Access Point Name (APN). A WHOIS look-up discovered a connection with the Department of Defense..., by ThoughtCrimes
- Note: Those IP ranges may have been sold off to commerical vendors.
- Hacker Perspective - by shadoe
- Finding Email Addresses - Various tips on how to track down a person's email address, especially if they are trying to keep it a secret, by Michael Ravnitzky
- Finding Email Addresses Original
- More Advanced Processors, Greater Privacy Intrusions - A story about how computer and network systems are becoming more complicated and bigger threats to our privacy and how we should take clues from the designers of "retro" systems, by Diana
- Printers: The Overlooked Security Concerns - Overview of the potential security problems network printers may have and how people have been exploiting them, by Matt Muse
- Letters - CERTAINTIES
- Inquires - D, Nathan, Darkcast, Arturo, Richard, amber, Lee, Mai (Dutch Hacker Video)
- Induction - Amy, Fikayo
- Correction - Paul
- Observations - Brad (Photo), _hazy, Kody, jesse, Morgan, Oliver, Mike the 0tt3r (Photo), M, Your Local Curious Hacker, Failsom, Token, Killinger, D (Photo)
- First Friday Fun - Luci, Ian, Zen Paralysis, billk3ls0, Mad Glitcher, David, Al Xbert, arcane, /Psychad (Stockholm, Sweden), ll (Madison, Wisconsin), Chad (Fort Worth, Texas), Karan (Bangalore, India), The Cheshire Catalyst, Pablo 0 (Buenos Aires, Argentina)
- Interesting Stuff - Mudbib, Bill, Michelle (Petition for Ross Ulbricht)
- History - Jack Jordan, Squeeling Sheep
- Responses - Patrick, Emily S., Jack
- HOPE 2020 - B1u_De4D, David
- WTF? - Ryan, Alex, Rob, D1vr0c
- EFFecting Digital Freedom - Who has your face?, by Jason Kelley
- The USPS Informed Delivery Service as a Phishing Data Source - Potential exploits and privacy concernts in the USPS' "Informed Delivery" service which takes pictures of a person's mail and emails them to you, by ~Me
- Yahoo! Groups and the Legacy of Internet Content - Overview of the shutdown of Yahoo! Groups and the inherent loss of over 20 years of mailing list archives and related information, by Nathan Kiesman (nkizz, YouTube Channel, Twitter, GitHub)
- The Freephones of Whidbey Telecom - Overview of the "free" payphones on Whidbey Island, which is just north of Seattle, by Curtis Vaughan
- Metal Phone Booth Photos of Whidbey Telecom's phone booth.
- Point of Sale Shenanigans: Authorized Unauthorized Transactions - Point of Sale (PoS) systems on U.S. military bases which will allow a transaction to be completed without entering a proper PIN or signature, by Ryan Clarke
- Citizen Engineer - Controlling MagicLight Bluetooth blubs, by Phillip Torrone, Ladyada, and John Edgar Park
- Electric Barons - Modern technology of computing machines provides plausible disguise for the ideology of power. This ideology permeates the infrastructure and its design methodology, disarming opponents with pseudo-technological excuses, by Morlock Elloi
- Would You Like Some Pancakes With That Breach? - Overview of the fact that restaurants, like Huddle House, are a potential risk to a person's privacy by breaches exposing credit card transactions, by lg0p89
- An Introduction to Chaff - An Anti-Forensics Method - Brief overview of the "chaff" feature of BleachBit which is a system to create random files in an attempt to defeat forensic analysis, by Andrew Ziem
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: The dangers of the big social media sites today. / "It was supposed to be fun. The whole idea of social networks was meant to augment our actual lives. Instead, in far too many cases, it's practically replaced them."
- Cover (Cover Info)
- Cover Inside Hawai'ian Payphones
- Kauai Found in the Poipu area near a natural feature called Spouting Horn. If you made a call on this, you'd have to battle the roar of the waves through the lava tubes in order to be heard. Hawai'ian Telcom, now owned by Cincinnati Bell (it's true), used to be part of GTE's non-Bell landline network. Photo by DarkLight
- Maui This poor thing was seen in Lahaina where it apparently was the bearer of bad news for someone. Operated by WiMacTel, in theory at least. Photo by _hazy
- Maui This is what you'll find at the Maui airport. Millennium phones like this one used to be run by Nortel, but now WiMacTel is the only operator of them in both the United States and Canada. Photo by Babu Mengelepouti
- Oahu Found at Honolulu International Airport, this phone shows the collaborative spirit that exists between WiMacTel and Hawai'ian Telcom. And you may even recognize the old GTE Model 120B from the 1980s that's still in use. (Fun fact: Hawai'i has more payphones per capita than any other state. Photo by Chris Gibson
- Back Inside Phones as Art
- England This is actually a Thai payphone that somehow wound up in a bar in Oxford as some sort of an art display. Don't bet on getting a dial tone. Photo by Toronto Phreak
- United States Spotted in Gorman, California (and you can spot it too if you look long enough), this is an example of the camouflage effect of graffiti. Photo by German Rodriguez
- Malaysia This work of art was discovered on the island of Langkawi in the Cenang Beach area. If only every abandoned kiosk could look this nice. No dial tone, no receiver, and not even a phone here. Photo by Sam Pursglov
- Japan What makes this particularly artistic is the fact that this is still an actual functioning payphone, complete with rotary dial. Found in Hachiōji. And just look at the great condition it's in! Photo by Larry Washburn
- Back 2600 and the Club-Mate Bottle - A Transatlantic Saga
- Back Photo #1 This is the bottle before it was dropped in the middle of the Atlantic Ocean on December 11, 2018.
- Back Photo #2 This is the note that was stuffed inside.
- Back Photo #3 Here is where the bottle was found on February 2, 2020 in the Bay of Littlelure, Shetland by Henry Anderton. The label had washed off but the glass bottle was otherwise unscathed and the contents completely dry.
- Back Photo #4 In an unbelievable stroke of synchronicity, Henry is allocating his reward money to the restoration of this local phone booth left behind by British Telecom. An additional donation is being made by us to The Ocean Cleanup organization in Henry's name.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 37!
$2600 Magazine - Volume 37, Number 2 (Summer 2020)
- Adaptation - Editorial
- Skimming Credit Card and ACH Payment Details from Tigerpaw Software Clients - Creating a virtual machine and a MITM proxy to intercept HTTP credit card form data in older versions of Tigerpaw transaction processing software, by Victor
- The Pipe Dream of Sensible School Internet Policy - How school network administrators spend most of their resources banning "bad" websites, like TikTok, instead of just implementing proper security, by akerch
- Windows Subsystem for Linux. A n00b5 Toy? - Overview and installation of the Windows 10 Subsystem for Linux, only XFCE4 worked, by P4!nt
- Telecom Informer - How telecommunications companies "oversell" their services, by The Prophet
- Towards a Secure Telephone Network - Overview of ideas to include security (encryption) and privacy into modern telephone/cellphone systems and networks, by Dave D'Rave
- Ghosting an Operating System for Privacy - Idea to create "ghost" data ports or memory locations so operating systems send the data into a "NULL" and, hopefully, won't degrade your privacy, by Diana
- Tracking Wi-Fi Devices with Python and GPS - Overview of Wifitrack, a Python script to monitor and log Wi-Fi MAC address and geo-locations via GPS, by Columbo2600
- Code: wifitrack.py
- Hacker Perspective - by Dave Collins (Desert Hot Springs, California, Email, Twitter, TikTok, YouTube Channel)
- Industrial Control Systems and Cybersecurity - Overview of some of the recent attacks on SCADA and other related industrial control systems and why their security should be increased, by Craig Reeds
- Bad ISP OpSec - Some ISPs use bad default user or Wi-Fi passwords - like Canadian ISP SaskTel using the user's phone number, by JavinZ (zuckonit)
- Anonymous Temporary Storage and Retrieval - An idea of storing data (text strings) within HTTP daemon or system log files, by Buanzo
- How to Become a Hacker in 24 Hours - The author believes that, depending on each individual interpretation of what makes someone a hacker, the answer on how to become one might or might not be found in a good book, by XCM (Lancaster, England)
- Thinking in AI The future potential of growing a human-derived "cerebral organoid" which is a combination of artificial brain and computer!, by Duran
- Letters - Cures
- Trouble - Amy, S S A T
- Questions - Thomas, A Nonymous, Beckett, Colin B, B
- Information - Chris, Mike, Michel, C, Chuck
- Feedback - Sardonyx, David, George, 2600Submit, Brobin, Piano Guy, Keith, AJ, RB in SF
- Discoveries - l00n, Erik (Photo)
- Problems - Jason, Brent, Logan, Tim
- Assertions - J.A.L., Marcin
- Aspirations - THE ROCKET RIPPER, Lauren
- Solicitations - jklovetop, Shivani Parashar, Dickson
- Inspiration - Priyank Pandey (COVID-19: Symptoms, Testing, Vaccines, & More)
- Reflections -Bruce, HITESH BUNKAR
- Perseverance -marissa, Aaron, Jason, Jim, Matt, Matthew, gamma gamma, David (NC2600), Ross
- HOPE 2020 - JK, tmj, beth, NK, Josh
- EFFecting Digital Freedom - Be wary of surveillance tech during the pandemic, by Jason Kelley
- Fun With Text-to-Speech - Fun little Bash script to covert the entire contents of $2600 Volume 35 to "speech" using NanoTTS and LAME, by Nestor (Gregory Naughton, Las Cruces, New Mexico, GitHub)
- Code: Text2Speech.sh
- Hacker Email - Quick overview of anonymous email services Protonmail, Mailinator, and Guerilla Mail, by Sh0kwave
- Cerebral Spill - Why we need media literacy to combat biased "news" sources like (((PBS ✡))), (((CNN ✡))), and (((MSNBC ✡))), by Worlds_Gr8test_DeFective
- OhNoDaddy: GoDaddy Compromised - Brief overview of the April 2020 breach of GoDaddy web hosting account credentials and their lack of an immediate response, by lg0p89
- Book Review: The History of the Future: Oculus, Facebook, and the Revolution That Swept Virtual Reality - Book review of Blake J. Harris' The History of the Future: Oculus, Facebook, and the Revolution That Swept Virtual Reality, by paulml
- Artificial Interruption - Corporate greed and the pandemic, by Alexander J. Urbelis
- The Rise of the Machines - Learning to Detect DGAs - Describes a technique to use machine learning tools to create an algorithm to detect Domain Generation Algorithim (DGA) domains. These use random numbers, letters and characters to evade detection, by blodgic (Andrew Blodgett)
- Code: DGA-algorithim.py
- Responsible Disclosure of a Malware Infiltration Attempt - Why it's responsible to notify any of your clients/friends if you've been targeted by a malware or phishing attempt, by The Piano Guy
- Fiction: Hacking the Naked Princess - Chapter 0x19 - Chapter from the newest "Dev Manny, Information Technology Private Investigator" story from the book Superliminal, by Andy Kaiser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: Struggles of publishing during the China COVID-19 pandemic / People who didn't do a single thing to help George Floyd when he was alive, using (and profiting) from his death to further their political goals - and line their wallets.
- Cover (Cover Info)
- Cover Inside Mexican Payphones
- Puerto Vallarta Who says payphones can't find a use after people no longer seem to want to use them to make calls? This one somehow wound up on the ground and is doing quite nicely as a table. Photo by Howard Cherniack
- Nuevo León Seen in the Zona Piel district, this phone is clearly treated with more respect than the post it's fastened to. Photo by CG Brik
- Guadalajara This phone is still working and models like it can be found on streets all over. We're told the prepaid cards are nearly impossible to find, however... Photo by Francisco Treviño
- Mexico City To be fair, this phone is located indoors, which is why it looks even more pristine than the others - although it's still possible it's rarely used. Photo by Bret Miller
- Back Inside Former Payphones
- England Found in Settle, North Yorkshire, this former phone booth is now used as a really tiny art gallery. (The postbox next to it still works.) Photo by Mark
- England This combination was seen in Shenstone, Staffordshire and was sent to us mere days after the previous image. Of course, it's totally different, as this former booth is being used as a library. (And the postbox next to it still works.) Photo by mike
- United States This art installation can be found in Point Reyes, California and is entitled "A Happy Heart is a Healthy Life." It was commissioned by the owner of the pharmacy behind it. Photo by Peter
- Canada While it may no longer be a payphone, at least this is still a phone in Toronto. We're not sure how much people making distress calls will appreciate the surrounding artwork. We just hope the phone works. Photo by Isoterric
- Back The Back Cover Photos
- Back Photo #1 Now how cool is this? The Library of Congress in Washington, D.C. actually has this instrument on display in their archives room, which is usually not open to the public. Thanks to Rafael Troncoso for spotting this treasure, which apparently is still actively in use.
- Back Photo #2 Attentive reader sigflup synasloble sent us an update on a picture we printed back in Autumn 2007 of this dive bar in Minneapolis with a magical number. We're sorry to see what happened to them during this year's chimp-outs. We're told they were on the corner of 26th Street and 26th Avenue. R.I.P.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 37!
"Now see my fists? They're getting ready to f*ck you up."
--- Comment from Ofc. Manuel Ramos to Kelly Thomas before murdering him.
Remember when that non-White cop murdered the White-man Kelly Thomas, and the (((media))) was silent?
"I Can't Breathe"
Will Evil Corley Protest in the Streets? No?
Avenge Tony Timpa!
Will Evil Corley Protest in the Streets? No?
$2600 Magazine - Volume 37, Number 3 (Autumn 2020)
- The Blame Game - Editorial
- Smile, You're on Camera - Example Python code to grab video images from public-access Minnesota DOT cameras, by Alsch
- Cyber-Pandemic: The World in Ruins - Sensational article trying to link the China COVID-19 virus pandemic to a pandemic in the world of cyber-security, by Stephen Comeau
- Understanding Election Security Through the Lens of the Hierarchy of Voter Needs - Discussing the need to create a "Hierarchy of Voter Needs" in order to secure our elections from any types of attacks and provide integrity, by Allie Mellen (Pic, Twitter, Instagram, Bio)
- HOPE 2020 Fulfilled - Debrief Overview - Overview of HOPE 2020 which took place during the China COVID-19 crisis so it was live-streamed online over nine days, by Various HOPE 2020 Attendees
- Telecom Informer - Overview of "robocalls," the Telephone Consumer Protection Act, and the new Reassigned Numbers Database (RND), by The Prophet
- Hacking Rotary Dials - Cool little Arduino Nano project to utilize a classic rotary-phone dial in your electronic projects, by yeat
- Code: hacking-rotary-dials.ino
- QR Chaos - A project by a Computer Science Instructor at Butte College to test if people would scan randomly-appearing QR codes - with results you probably expected, by Edward Miro (a.k.a. c1ph0r, Email, Twitter)
- Code: qr.py
- Knowing What to Search For - Leverage the power of today's search engines by knowing what to search for when learning a new programming language, by RAMGarden
- Hacker Perspective - by Maderas
- Clean Rooms and Reverse-Engineering - How IBM's BIOS was properly and legally reverse-engineered and what we can learn from the story, by Sean
- Searching Government Quiz Sites for Hidden Answers - Some websites hide the answers to quizzes within their JavaScript code, by Brenden Hyde
- Taking Control of Your Devices - Author's story of "taking control" of devices he owns like a Kindle, PS3, Wii, or Xbox 360, iPhone, etc. rather than being stuck with what the manufacturer gives you, by Nick
- Letters - POLLS
- Generosity and Support - k, Ryan, Matthew, m, Jim, Nicholas, Black Cat, Elijah, Robert, jo5h
- Submissions - Mike, C, Charolette, Michael
- Gratitude - Kevin, Arjun, George, David
- Random Thoughts - Fiorita Li, gw, X
- Our Lateness - craig, Digit.Hex, mh, p, Adnan, James, Katherine
- Kindle Fun - scott, Joshua, Matthew
- Cover Controversy - aestetix, HS, Royce, Amber, Robert, Maxwell, Jason, Steve, Corwin, A B, N G-B, S S, Bill, Eric, Jan (Hamburg, Germany)
- Word Controversy - jus, Thomas
- Noticed - Jeff (Photo), Xcm, Aurelius, dsttyy (Photo)
- Complications - Matt, A. C.
- Clarification - A. S. A. (Photo), Curtis
- More HOPE Thoughts - David, Y N, Dave, Lilly, Doug, Rich, Hagen, Paul, Martin, Allen
- A Challenge - Mat (Birmingham, AL)
- Opportunities - Alexander, Matej Wzo, Kim Omar, [name redacted]
- EFFecting Digital Freedom - Let's call "remote proctoring" what it is - spying, by Lindsay Oliver
- The NSRL for Hackers - Overview of the National Software Reference Library and why hiding information in files disguised as drivers or system files won't work anymore, by Steffen Fritz
- Make Virii Great Again - Discusses the shutdown of vxheavens, a website known for aiding in the construction of computer viruses, and some tips (only use C or assembly and proper compiler options) for potential modern virus writers, by Israel
- Artificial Interruption - All things that "suck" may not suck, by Alexander J. Urbelis
- What's Old is New Again - We Are Still Jackpotting ATMs - Overview of a new hardware-based form of "jackpotting" Diebold ProCash 2050XE ATMs, by lg0p89
- Achille's Heel in Diebold ATM Terminals
- Crooks Have Acquired Proprietary Diebold Software to 'Jackpot' ATMs
- Facebook's Efforts Against Ad Blocking - How Facebook views web browser "ad blockers" as a threat to their revenue - and existence, by John Paine
- Red Light Robin Hood - Story of American hero Stephen Ruth, also known as the "Red Light Robin Hood" known for fighting against automatic red light camera ticketing systems and the harassment he received, by JetPuffed
- The Elements of a Raven Matrix - Artificial intelligence systems are still unable to match the performance of humans during Raven's Progressive Matrices non-verbal testing, by mathpunk
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: The hacking community is far too often cast as the villain and is constantly blamed whenever things go wrong. This hurts not only our community, but all of society.
- Cover (Cover Info)
- Cover Inside Distant Payphones
- Austria Seen in Spitz, this harkens back to the days when huge phone booths existed everywhere. While the booth may belong to Telekom Austria, the distinctive pink handsets indicate the phones are Magenta Telekom, a relative of T-Mobile. Photo by David Clark
- Russia This distinguished looking model was found in St. Petersburg. It's proof that presentation is everything. The green background, colorful charts, phone book, and kiosk (including the font that says "international") make this a destination in itself. Photo by Pirho
- Ghana Interestingly, people here are encouraged to receive phone calls on payphones, as the sign from Ghana Telecom attests. The phone itself is made by Schlumberger, a French oilfield services company. Photo by Kelechi
- Vietnam Again, people are clearly being encouraged to use this phone to receive calls, a concept that has become somewhat alien in America. Located in Hanoi, this card reading model looks fairly rugged. Photo by Peter Kastan
- Back Inside Unusual Payphones
- Kuwait Definitely not the kind of payphone we're used to seeing. This model looks incredibly serious with its rather drab coloring and exhaustive list of numbers you might want to call. Photo by XBS
- Ecuador Perhaps it's an optical illusion, but this looks like an incredibly thin phone. Seen in Cuenca and run by ETAPA, a local company owned and operated by the city. Photo by Benji Encalada
- United States Seen at a community college in Buffalo, New York. For the record, New York Telephone, NYNEX, Bell Atlantic, and Verizon (all of whose logos appear here) either don't exist or don't operate payphones anymore. And this kind of phone booth is almost completely nonexistent. Photo by Camel_Case
- United States This payphone met with an unfortunate end, having the bad luck to be located in the Big Basin Redwoods State Park campground, in Boulder Creek, California. It's remarkable how much of it remained standing after one of the most destructive wildfires in history. Photo by Josh Goldberg
- Back The Back Cover Photos
- Back Photo #1 Well, this had to happen eventually. Thanks to Barry Wass for examining the serial numbers on his dollar bills in order to find this magical one. We intend to start doing this and hopefully build up an impressive collection of $2600-themed money.
- Back Photo #2 This building cannot be found by many. But fortunately, Dick Willemse persisted and was able to track it down at the University of Amsterdam in the Netherlands. The campus is naturally connected to the high-speed backbone of the European Internet and the tall building in the background is filled with servers.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 37!
$2600 Magazine - Volume 37, Number 4 (Winter 2020-2021)
- Errors in Freedom - Editorial
- The TikTok Spyware Conspiracy - Someone finally reverse engineered the Android TikTok APK and did a code review - and it doesn't look good for your privacy, by August GL (Email)
- Killed by DMCA (Mirror)
- TikTok Scrambling After Source Code Leaks - Hacker Calls Platform "Legitimate Spyware"
- TikTok Source Code Published on GitHub via HackerNews
- Hacking Digital Signage Screens - How to hack digital signs, like the ones in the McDonald's drive-thru, to display your own information, by Daniel Hargett
- Telecom Informer - Information on the phone system in the infamous Point Roberts, by The Prophet
- How to Write Malware in PowerShell - Tips and Tricks - PowerShell scripts to make a Windows Remote Access Tool (RAT) using SSH, the connection back to the "command and control" server, and some tips how to prevent it, by David
- Beyond the Breach: An In-Depth Look into the Cyberinsurance Industry - Overview of commercial Internet security liability programs, how some companies don't get their claims, and how the insurance costs get passed onto the public, by Shaikat Islam
- Right to be Forgotten - Network and Home - Story of why we should be worried about an "all-knowing" Internet, by Diana K.
- What Three Words, and Your 2600 Meeting - Assigning 2600 meetings a What Three Words link to make giving complicated directions easier, by The Cheshire Catalyst
- Hacker Perspective - by The Piano Guy (Gary Rimar, Bloomfield Hills, Michigan, & Arlington, Virginia)
- The Brazilian Phone System Revisited - Overview of Telebrás, and how it's changed since it was broken-up from a state-run monopoly, by Derneval Cunha (Brazil, Instagram, Facebook)
- Hacking the Game Rules - Using the "Fake GPS" app to to spoof GPS data to win a flying contest, by -Me
- Book Review: IF THEN: How the Simulmatics Corporation Invented the Future - Book review of Jill Lepore's If Then: How the Simulmatics Corporation Invented the Future, by paulml
- Letters - Burgeons
- Quest for Knowledge - Julia, a2n, T, a2n, John R., Anonymous, Jef, D, TE, Nick, Patrick, SPAM, Tanya, VIKAS, Anonymous, Dante, Nazmus, Vincent, Shawn, Dan, Geoff, Arabelle, Jesus, Ron
- Writer Inquiries - Michaleen, Danny, grumpychestnut
- The Power of the Net - Robert, Chris
- Threats - Daniel, Sos, Alex, kaelynn
- Hard Decisions - Geoff
- These Times - Steve, Craig
- Appreciation - dulcedemon, John, Different John, Brad, Dan N
- Replies - Apinusu, JMG, CraiglistKiller12
- Bypassing the System - John, Jed, Tyler
- Dedication -Tt Engineer, Tedd
- Suggestions - Damien, j, Willy
- Facebook Fun - Brad, C, Loren, NoName, Joel, Joe, Phillip, Jason, Tom
- EFFecting Digital Freedom - Police robots with facial recognition and logging of Wi-Fi SSIDs/MACs, by Matthew Guariglia (Twitter, EFF)
- Hosting Under Duress - Ideas to avoid hosting problems with the infamous "BlueLeaks" law enforcement information hack, by Milo Trujillo (Twitter)
- BlueLeaks: Magnet, IPFS
- CopSnitch.com
- How One "S" Can Make a Difference - Why a person should always use https:// (Transport Layer Security [TLS]) when connecting to a remote website and an overview of the connection setup process, by aestetix
- COVID-19: A Tale of Two Mindsets - Comparing the results of government-run incompetence versus the dedicated individual during the China COVID-19 pandemic, by Captain Crackham
- Colbert, Fauci, & The Art of COVID Propaganda
- BREAKING: Newly Released Emails Show Fauci Directed Colleagues to "Delete This After You Read It" Dating back to February 2020. He denied it under oath. These documents are now public, and Fauci will finally testify before Chairman Rand Paul.
- Normalizing SASsy Data Using Log Transformations - Simple trick to minimize "noise" in data using a log10 function, by Chris Rucker
- Artificial Interruption - Misinformation and lies about Jan. 6 Constitutionally-protected election integrity protests, undocumented Capitol tours (ignoring the false-flags), phoney "White Power" websites on (((GoDaddy))), and calling for more Internet censorship because people have different opinions or dare question the One Percent, by Alexander J. Urbelis
- Work From Home Through P2P Network - Scripts to ease setting up a SSH tunnel to work from home using Tuntox to relay connections if it doesn't have a static IP, by 0xc0000156
- Chromebook as a Web Hacking Platform - Setting up a Lenovo Chromebook 100e and applications for use during web hacking sessions, by David
- Thinking in AI - Can AI Wake Up? - Is it really possible for a machine to think like a human and the dangers of artificial intelligence becoming sentient, by Duran
- Thoughts on Bitcoin - Believes that Bitcoin has just as much value as gold, silver, 401(k), even real estate and is not a scam like private "Federal Reserve" fiat ($$$) currencies, by Doorman
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: Spreading disinformation and lies about the people involved in January 6, 2021 Constitutionally-protected election integrity protests / Regurgitated & debunked anti-Trump propaganda
- Cover (Cover Info)
- Cover Inside Distant Payphones
- Japan You certainly don't see a sight like this very often. Discovered after a snowfall (obviously) in Hokkaido. Photo by dilanka
- England Seen in Goudhurst, this is yet another use for an old phone box where phones are no longer what's needed. Photo by XCM
- United States Believe it or not, this phone in Fredericksburg, Texas is a working model, attached to the Pecan Grove Store. It just doesn't get any cooler than this. Photo by Doug Bins
- Costa Rica This payphone was found in the area of the Turrialba Volcano on an unnamed road south of Route 417. And now you can call it. Photo by Tyler Durden
- Back Inside Off the Hook Payphones
- United States Found in Texas, where you may find it hard to make a call even if you hang up the receiver. Photo by B R
- United States From Rock Island, Illinois, another example of a receiver in disrepair. Photo by Gursimran Sandhu
- Mexico At least this Boca de Tomatlán phone looks like you can just hang it up to get it working again. But in reality there was no dial tone. Photo by Michael Stevenson
- United States Our country seems to be the leader in damaged receivers - in this case it's missing entirely. Seen in the Koreatown section of Los Angeles. Photo by Mark Hudson
- Back The Back Cover Photos
- Back Photo #1 We're not encouraging people to just spray-paint our name on a wall and send it in for the back cover. This will work only once. We're printing this because it's the old site of the 2600 meeting in Buenos Aires, Argentina and it makes us feel sentimental, as it's been empty for the past year just like all our other meetings. We hope to come back stronger than ever when this pandemic comes to an end. (But please don't spray-paint at your local meeting site or your meeting will likely be moved to the street.) Thanks to Arturo "Buanzo" Busleiman for the submission.
- Back Photo #2 Sometimes "I.T." doesn't mean information technology. This is one of those times. This instance of I.T. is actually a clothing store, found by Sam Pursglove at the Taikoo Li shopping center in the Sanlitun area of Beijing, China.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 37!
$2600 Magazine - Volume 38, Number 1 (Spring 2021)
- Forward Thinking - Editorial
- Anonymity, Privacy, and Reality - Overview of what it takes to maintain your privacy and security on an increasing hostile Internet, by XCM
- What Hacking My County's Election Worker Portal Taught Me - Potential vulnerabilities with protecting credentials and brute-forcing attempts with online election poll workers' portals, by Keifer Chaing
- Ham Radio, SMS, and the ISS - Technical overview of what it takes to send SMS messages through the International Space Station's APRS digipeater and using the SMSGTE gateway, by Naught Robot (Robert V. Bolton, KJ7NZL, YouTube Channel)
- Randomize Your Exit Node - Shell script to "switch" Tor exit nodes by spawning new instances of Tor, by Justin Parrott
- Code: tscan.sh
- Telecom Informer - Story of juggling two SIM cards (one U.S. and one Canadian) to overcome spotty coverage in the Pacific Northwest, by The Prophet
- Logging Discord Tokens - Reversing engineering a C# malware program which logged Discord tokens with an abilty to bypass their two-factor authentication, by augustgl@protonmail.ch
- Code: Program.cs
- Code: TokenDiscovery.cs
- Trojan Detection and Avoidance - Overview of modern Trojan malware, like BonziBuddy, and tips to avoid install or running potential Trojan programs, by Elizabeth Rankin
- 5G Hotspots and Tinc - Setting up and using the Tinc VPN daemon and reverse-proxy on a Raspberry Pi along with a Nokia 5G21 home Internet gateway, by Byeman
- Book Review: We Have Been Harmonized: Life in China's Surveillance State - Book review of Kai Strittmatter's We Have Been Harmonized: Life in China's Surveillance State, by paulml
- A Layman's Intro to Quantum Computers - Overview of how quantum computing works and how it differs from classical computing, by David Mooter (Middlefield, Ohio)
- Hacker Perspective - by Rotted Mood
- Inside Job: Exploiting Alarms Systems and the People Who Monitor Them - Overview of protocol for people monitoring security systems and possible methods of exploit, by Nicholas Koch (Lazy Eye Of Sauron, Pensacola, Florida, Twitter, Bluesky)
- Inside Job: Exploiting Alarm Systems and the People Who Monitor Them HOPE 2020 Presentation
- Why Are We Still Having This Conversation? Embedded Systems Still Not Secure - Overview of security vulnerabilities in embedded systems and CAN busses, by lg0p89
- Letters - Combinations
- Opinions - kingcoyote, Tiffany, Tracy (Photo #1, Photo #2)
- Recommendations - Bill, Tad
- Stupidity - John, DW Dubya, Michael, Kat, OctanRaz0r, Tortilla
- Offers - Steve, Steve, Jem Rodriguez, gunkmvd_9@mvd.gov.ru, Charles, Glenn
- Update - Pablo_0 (Buenos Aires)
- Stories - Joe, Mikey
- Feedback - Jeffrey, Patrick, Jacob, Anonymous, pinkbathtower, Doorman, ightnapovial, Modus, 6NdLXzc2
- Inspiration - Jonas
- Questions - N1xis10t, Jason, Amy, Altaf Raja, C, Robert, The Last Postman, Kray, Tiago, Thomas, swapgs
- Helping Out - Mike, Josefin, Kiumarz, Sarah
- EFFecting Digital Freedom - EFF's Atlas of Surveillance brings police spy tech into light, by Jason Kelley
- How Does NSA's XKEYSCORE Project Work? - General overview of the XKEYSCORE global Internet surveillance system, by Duran
- A Proposal for the Elimination of Passwords - Proposal for the elimination of text-based passwords on things like WordPress, by G.A. Jennings
- Life Lessons Can Help You Sneek Into a Crowded Conference - How a simple piece of pink-colored paper can defeat your conference security, by Derneval Cunha
- AI in Dating Simulation Games - Will humans fall in love with and marry machines?, by Duran
- Artificial Interruption - Public squares and private rights, by Alexander J. Urbelis
- Hacking HP's OfficeJet 6310 - Using a larger ink cartridge (#96) in a HP OfficeJet 6310 via a keypad hack, by Daniel Hargett
- The Net as Seen in China - Setting up a VPN exit node in China to witness their Internet censorship first hand, by Nino Ivanov (GitHub)
- Picture This - Why we should be paranoid about the cameras embedded in our computers and "eye tracking" developments, by Michaeleen Garda
- Why I Am a Hacker: Hacking in the Era of COVID-19 - Hackers must use there skills to become a force for good and fight censorship at places like $2600, Twitter, and Facebook, by Corey M. Knoettgen (Tampa, Florida)
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: As Evil Corley and the One Percent's politics and policies continue to fail - and the public fights back - expect them to be come after YOUR rights, instead of them admitting they were wrong.
- Cover (Cover Info)
- Cover Inside Unused But Artsy Payphones
- Norway Seen in Bergen, there's something artistic about this hip-looking phone booth. You almost miss the fact that the receiver's been torn right off. Photo by grumpychestnut
- United States There's no missing the state of this phone from Daytona Beach, Florida. Being about 200 yards from the ocean explains the rust. If anyone did figure out how to use it, they would be advised to take precautions against "touchtone tetanus." Photo by Mark L. Smith
- Belize We're told there is no receiver on the end of that cord which doesn't surprise us a bit. This was found in a small village near Punta Gorda and looks as if it was abandoned a long time ago. Photo by Jack Jordan
- United States This non-working Nortel Millennium phone was found in Portland, Oregon, a rough city to be a payphone in. But there's no denying that unique Portland charm. Photo by Jaclyn Smith-Moore
- Back Inside Mostly Working Payphones
- United States Found in a place called Elfin Forest Recreational Reserve, California, this COCOT actually works and even looks willing to hold a phone book or two. It's rather inspiring. Photo by Screaming Yellow Fish
- Ireland Even though the phone company is no longer called Eircom, this phone still works. About all it really needs is a bath. Photo by Greg Cadogan
- United States This ancient phone booth (and phone) are preserved at a place called Frank's Restaurant in Prairieville, Louisiana. Even if it's not in service, its mere existence is noteworthy. Photo by crunchylicenseplates
- England Here's a phone in need of rescue. Found in Witham, Essex, you can see the attached "kiosk review" is recommending the removal of this phone. At least they give you a chance to save it. Photo by Brad Saint George
- Back The Back Cover Photos
- Back Photo #1 Here's an update on the progress accomplished over the past year with the restoration of a phone booth that we helped fund with a $1000 donation after a bottle we tossed into the middle of the Atlantic Ocean made its way into the hands of Henry Anderton in a place called Lera Voe, Shetland last year. (Read the whole bizarre story in the Spring 2020 issue.) The note inside the booth reads: "Welcome to this phone kiosk. The equipment installed is for display purposes only. It does not function. The coin box would have been modified after decimalisation and again in 1988. Enjoy going back in time!" We're thrilled to see this project end successfully but we won't be dropping any more bottles into the sea.
- Back Photo #2 This is a painted wall in the city of Olavarria in eastern Argentina, discovered by Marcelo Chiesa. It is on a junction of an avenue and a road and the city logo appears on the right. The wall has a telephone pole on each side. And you've probably figured out by now that this has nothing at all to do with an operating system and everything to do with a celebration of local diversity.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 38!
Does this look like an "insurrection?"
How do you "storm the Capitol" when the police actually let you in?
$2600 Magazine - Volume 38, Number 2 (Summer 2021)
- What is Truth? - Editorial
- "They assumed the whole thing was some sort of global conspiracy whose alleged goals have never been clearly explained." Well, that didn't age well!
- More Privacy and Better Security Through Email Diversification - Detailed overview of some of the "free" email services and tips for increasing your privacy on the Internet when setting up your domain/web hosting and email servers, by Elite Bulbe
- Three Fundamental Questions - Why you should ask yourself, "What is it doing?," "How does it work?," and "Under which circumstances does it break?" during your hacker training or testing, by MasterChen
- Telecom Informer - Overview of the telephone system in Kazakhstan and some of its customs, by The Prophet
- Fluc Google's FLoC - How users would actually loose their privacy if the "Federated Learning of Cohorts" brower standard is passed, by kingcoyote
- Municipalities Pwned at Greater Rates! - How small municipalities, like Florence, Alabama, are targeted at higher rate by "randsomware" attacks because they tend to be unsecure and are willing to pay out the ransom demand, by lg0p89
- The Demise of Network Security - Modern network traffic filtering is becoming too complicated, might be better to restrict data at the endpoints, by XCM
- Who's Training Whom? - Story of using an auto-completion email package and realizing that it may be telling you what to say next, rather than the other way around, by XCM
- Hacking Motion Capture Software and Hardware - Hacking motion capture in order to produce radically different Biovision Hierarchy Animation (BVH) files for animated avatars in virtual worlds, by Alan Sondheim (Providence, Rhode Island, Email)
- How to Read 2600 Magazine - The optimal way to read the physical copy of $2600, by Delta Charlie
- Verified Badges for Everyone? - Potential that one day we may have to verify our identities online in order to prevent "misinformation" and "discrimination," by Corye Douglas (New York)
- Thoughts on "Verified Badges for Everyone?" - by John C.
- Gone Fishin' - Story of setting up a honeypot to look for remote users attempting to exploit the author's server and the dangers of not filtering incoming traffic or leaving ports open, by dcole
- Code: fishing.js
- Hacker Perspective - by Cintaks Airer (James K. Lawless, Gretna, Nebraska, Facebook, Twitter, GitHub, Email)
- Vulnerabilities in Deep Artificial Neural Networks - Potential vulnerabilities in artificial neural networks used in AI edge devices due to their fixed weighting, by Thor R. Mirchandani
- The Telegraph Regulations and Email - Story of using old telegraph and Telex standard characters and formats to "sign" SMS or email messages, by Cheshire Catalyst
- Facebook and the FBI - Example of the letter Facebook sends when your account is involved in a legal process by law enforcement, the FBI in this case. Your tax dollars at work! (Agency Case No. 19MAG11541 or 2017R00439)
- Letters - Sparks
- Ideas - XCM, Edgar, Glenn (Australia), Cody, Dale, Anonymous
- Meeting Reboots - Nick, Josh, Shawn, Paulie (Chicago), arcane, Meeting 2600 Petrozavodsk
- Memories - Robert, info, Tim, Lippe
- Thoughts on Articles - David, Chuck, marc, Enrico, XCM, aestetix, Estragon, OWA, The Unignorant_One
- Gratitude - Mark, Al, Dan, James, oktal (U.K.)
- Inquiries - Andre, Phineas, Chuck, MS, Max, braknurr, James S., Daniel, Christopher, Shae, CK
- Observations - olightg32, Mike, Andre, Jonny, Alex, John Smith, fred, Robert, Lock, Ke, Cody, 8261 80CC 3E97, CSCII
- Congratulations - Bob Kim
- Further Info - TENFOURGOODBUDDY
- EFFecting Digital Freedom - You are not being tracked, by Jason Kelley
- When 5G Technology and Disinformation Collide - Debunking the theory that China COVID-19 was caused by 5G cellular phone technology, by Kenneth Luck, Ph.D. (Honesdale, PA, Assistant Professor of Media Arts at SUNY Sullivan, SoundCloud)
- Kenneth Luck, SUNY Sullivan - Conspiracy Theories
- Evidence for a Connection Between COVID-19 and Exposure to Radiofrequency Radiation from Wireless Communications Including 5G Paper that started it...
- How to Hack the American Mailz - An apparent way to send postal mail for pennies (3 cents for each 1/2 oz.) by utilizing a 1863 law!?, by The Last Postman (Email)
- "Post-Quantum Cryptography" is Not Going to Work - Theory that the NIST's research in "post-quantum" cryptography is running into an (intentional?) dead-end, by Dave D'Rave
- Book Review: RESET: Reclaiming the Internet for Civil Society - Book review of Ronald J. Deibert's RESET: Reclaiming the Internet for Civil Society, by David Cole
- Book Review: Rabbits: A Novel - Book review of Terry Miles' Rabbits: A Novel, by Tim R.
- Artificial Interruption - On moral culpability and algorithmic accountability, by Alexander J. Urbelis
- How to Create Your Own Privacy-Enabled Sunglasses - Really cool hack to a pair of sunglasses with 3M reflective tape and "Magic Black" to reduce night vision-enabled facial recognition systems' ability to record your likeness and track your eye movements, by gh057
- A File Format to Aid in Security Vulnerability Disclosure - Idea to use a standard text file format for others needing to document and/or submit bug report to vendors, websites, etc., by Colin Cogle
- RFC 9116: A File Format to Aid in Security Vulnerability Disclosure
- Security.txt Adoption in Switzerland
- "Hello fellow sentient being," - The potential for a future where Artificial Intelligence (AI) begins to become sentient (conscious), by Milan
- Fiction: An Atavistic Freak Out, Episode One - by Leon Manna
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: Being cautious of what's fact or fiction in the age of China COVID-19 and how hackers can help.
- Cover (Cover Info)
- Cover Inside Foreign Payphones
- Greece Seen near the Acropolis of Athens. The phone company is Cosmote (OTE) and this phone appears to be from the 1990s. It accepts prepaid cards. Photo by Major League Wiffleball
- Ukraine This was found in the town center of Dnipro. Even though you'd likely have a lot of trouble using it, this seems like a relic that should never be removed. Photo by Floppy Phreak (a.k.a. Solar Angel)
- Tanzania Seen at the airport in Dar es Salaam. Located right next to the mosque where you have to be careful not to step on people's shoes when making a call. Photo by Richard D
- Zambia Found at the airport in Ndola. It accepts cards and still seems to be in service. Photo by Richard D
- Back Inside Special Payphones
- United States Now this is a really good idea. Marking phones that still work is like awarding a badge of honor. Seen outside a CVS near downtown Gainesville, Florida. Photo by george
- United States Believe it or not, there's a whole bank of these at the San Francisco International Airport. Someone had to make the decision to at least keep the phones as decorations if they couldn't remain functional. Photo by dingo
- Canada This is indeed a very special payphone. It's attached to the local central office near Big Bar in British Columbia. Since there's no cell coverage in this rural area and it's literally attached to the phone company with a comfy chair nearby, we suspect this phone will be around for a long time. Photo by Chris Adams
- United States And here we are back where we began. Apparently these stickers are making the rounds, though someone decided to obliterate the "Yes" for this one. Found in West Chester, Pennsylvania. Photo by Douglas Barret
- Back The Back Cover Photos
- Back Photo #1 As if being a former Western Electric Teletype building wasn't cool enough, this one also had a very special address on Chicago's North Southport Avenue! The Teletype Corporation (previously the Morkrum-Kleinschmidt Company) became a part of AT&T in 1930 and existed all the way up to 1990, after which it became nearly impossible to find a decent dedicated teleprinter. Thanks to David Morton for finding this awesome building which is now a bunch of condominiums.
- Back Photo #2 We always knew this day would come. Get a bunch of mechanically inclined, adventurous people together and eventually they'll build a rocket. In this case, all it took was a cardboard shipping tube, some plywood, a baseball bat, and tape. The decals were printed on shipping labels. robohobo launched this rocket which stands at just over five feet tall with a class-F composite rocket motor in Calvert, Texas. And now we await the inevitable arms race of bigger, faster, and more powerful missiles with our name on them.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 38!
$2600 Magazine - Volume 38, Number 3 (Autumn 2021)
- Amplification Gone Wrong - Editorial
- Wherever You Go, There You Are - Story of always exploring the things around you, including what's on utility poles and CATV systems, for opportunities in hacking, by Mr. Icom
- Using "DeepChecksum" to Ensure the Integrity of Backups - Why you should record the checksums (using Hashdeep) of your backed up data to verify its integrity, by 75ce8d3ff802ff42
- I Thought the Cyberpunk Dystopia Would Be a Hacker Paradise - I Failed to Heed the Cautionary Tale - Reminiscing about those old cyberpunk stories and books in the 1980s and how differently things have actually turned out, and in some ways - scarier, by Johnny Fusion =11811=
- Where Have All the Tor Sites Gone? - Story of how all the popular Tor marketplaces have been shut down by various government agencies or are mostly scam sites nowadays, by CSCII
- Telecom Informer - Interesting story of having to find and print "call detail records" for a legacy phone system after a subpoena, by The Prophet
- The FBI Communications Breach of 2010: Applications and Perspectives - Explores the sensational "FBI communication breach" first reported in 2019 to see if it was technically possible or just (((propaganda))) - note that this type of "vulnerability" was well known, by Marc J. O'Connor
- Book Review: Press Reset: Ruin and Recovery in the Video Game Industry - Book review of Jason Schreler's Press Reset: Ruin and Recovery in the Video Game Industry, by paulml
- The Phreak's Field Guide to Identifying North American Phone Switches - Part One - Tips, tricks, and test numbers one can use to identify the type of phone switch they are using, by ThoughtPhreaker
- Guide to Identifying North American Telephone Switches - A Friend Wrote This Original
- Additional Info
- Switch Descriptions by ThoughtPhreaker
- Empty Houses - Sometimes, you don't want things arriving at your house. Solution? Find an empty house on Zillow and ship the package there!, by Jared
- The Art of the Troll - The history of "trolling," what makes a good troll, and how a well-crafted Internet "troll" persona can be a powerful ally in bringing about positive change, by aestetix
- Hacker Perspective - by MRLN (Colorado)
- Exploring Old MS Paint Formats - Experimenting with old computer software and operating systems and a converter script for old .MSP files (Microsoft Paint) to bitmaps (XBM), by MrAureliusR (A. M. Roswell, Toronto, Ontario, Twitter, YouTube Channel)
- Code: mspaint.py MS Paint file converter utility v0.1
- Keyspace Iterator in AWK - A keyspace iterator written in AWK(!) for brute-force password cracking, website groping, etc. Can be used in conjunction with tools like Curl to fetch http://site.com/*.html, by Justin Parrott
- Letters - Affirmations
- Support - Shocked998, pic0o, proximacentauri, Emmanuel, Kryptographik, Antone
- More Meetings - Josh, Carmel
- Where We're Going Wrong - J.X., Michaleen Garda, Eric, Old Crow, Michaleen Garda, fuXor
- Inside the Walls - Jason, Vincent
- Memory Lane - HC, MN
- Scams - Frank, RE, Cash App
- Clarification - HC, GI Jack: All American Zero, Sven, r, Yury
- Enthusiasm - Blair, Josh
- Misbehavior - Riley Kelly (Photo), CR, DG, Riley Kelly
- Mischief - Mike
- Prososals - Dean Williams, Tweakie
- On Deplatforming - Kay Faraday
- Additional Data - ex nihilo nihil fit
- Random Impression - Scott
- Advice - DD, James
- Opportunities - JahSun, Chuan, Lance, Jay, JahSun
- Poor Tech - Daniel, Xochitl, Nick
- EFFecting Digital Freedom - When we fight, we win, by Jason Kelley
- Hacking NYC MTA Kiosks - Overview of a now-obsolete New York City Metropolitan Transportation Authority (MTA) kiosk hack with the ability to bring up a touch-screen keyboard and an old version of Internet Explorer, by enbyte
- What's With This Username Stuff, Anyhow? - While the perfect handle should obscure your identity online to the authorities, it should also be an extension of your personality within the hacker community, by dcole
- The Matrix Is Real: How to Hack Humans for Fun and Profit - Overview of the reality that it is possible to control a society by recording and storing emotional responses to certain images or ideas, by dohp az
- Artificial Interruption - Concerning the importance of being wrong, by Alexander J. Urbelis
- Why TikTok Activism Made Actual Hacktivism Harder - Author's experience with the difficultly in engaging in Satanic ritual child sacrifice in today's open society, by Johnny Fusion =11811=
- Reply to: "Normalizing SASsy Data Using Log Transformations" - Update and reply to the article "Normalizing SASsy Data Using Log Transformations," by a sassy statistician
- Thoughts on "Verified Badges for Everyone?" - Update and reply to the article "Verified Badges for Everyone?," by John C.
- The Lost Art of Windows 9x Pranking - Overview of some of the old tricks people used to do to play pranks on Windows 95 users (changing system sounds, desktop screenshots as wallpaper, slideshow screensavers, etc.), by Shaun Pedicini (Email, GitHub)
- Fiction: An Atavistic Freak Out, Episode Two - by Leon Manna
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: Tribute to former CIA case officer, frequent HOPE speaker, and American hero Robert D. Steele.
- Cover (Cover Info)
- Cover Inside Foreign Payphones
- Australia From Brunswick, Melbourne, where payphones are now free for domestic calls (meaning that message on the screen is outdated). This, incidentally, is the smartest thing we've seen done with payphones in ages: keeping them in service and making them more appealing. Photo by Jacqui A'Vard
- Northern Ireland Technically an emergency phone, but this one really caught our eye, seen near Giant's Causeway. No matter how many times we look at it, it seems to give the appearance of being upside down. Photo by Trevor Pour
- China The city of Chongqing, where this phone was found, has more than 31 million people in it, yet most of us have never heard of it. This tiny phone in a big booth was seen on the way to Hongya Cave. Photo by Sam Pursglove
- Austria This is a bit of time travel. Found at the foot of the Grossglockner (the tallest mountain of Austria), this is not only a working phone, but a well maintained booth, complete with a phone book. And to complete the trip into the past, calls cost 30 euro cents a minute. Photo by Robert van den Breemen
- Back Inside Payphones With a View (U.S.)
- Arizona Found in the Petrified Forest National Park (that's petrified wood lining the parking lot). Frontier, incidentally, is part of Citizens Utilities Company, an independent phone company that's been around since 1935. Photo by Marcus Watanabe
- New Hampshire Seen in North Conway, this phone has a lot going for it: plenty of artwork and a fantastic view. And did we mention that it works? Photo by Jeff Hanson
- California Wandering around Yosemite National Park, one wouldn't expect to come upon a working payphone complete with a booth. The forest is full of surprises. Photo by Ian French
- California In this case, maybe the phone itself doesn't have a view, but we can honestly say that the view here happens to be the phone itself. Discovered (somehow) in Forestville. Photo by Kevin Strishock
- Back The Back Cover Photos
- Back Photo #1 Congratulations to Joshua Pritt for spotting this gasoline-powered Kent Bayside 2600 bicycle (you can see the "2600" on the frame under the seat) in Melbourne, Florida. It's a bit ironic how this started out as the best form of transportation environmentally and wound up getting converted to the worst polluting option for pedal assistance. It's actually a bit of an insult to our name.
- Back Photo #2 Now this is super cool. It's one thing to have an actual card puncher from the really old days of computing. But to have it be a Wright Punch Model 2600 on top of that is almost too much to believe. This was spotted by Jon Guidry at an Atlanta Historical Computing Society meeting, where apparently people sometimes bring in really awesome artifacts.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 38!
A True American Hero & Patriot: Robert D. Steele (1952-2021)
BTW, Mr. Steele was murdered for exposing child trafficking. (Mirror)
$2600 Magazine - Volume 38, Number 4 (Winter 2021-2022)
- The Hacker Curse - Editorial
- Note that Trump had nothing to do with the International Emergency Economic Powers Act, which dates back to 1977 (Jimmy Carter)
- North Korea was added in 2008 (Executive Order 13466 - George W. Bush & Executive Order 13722 - Barack Obama)
- Note that countries which stand up to (((Rothschild central banking))) mysteriously always become the "enemy..."
- L-Band: Frequencies and Equipment You Need to Know About - Overview of the services which operate between 1-2 GHz (ADS-B, weather satellites, GPS, radio astronomy, etc.) and how you can setup a cheap SDR to monitor them, by Steve Bossert (K2GOG, Facebook)
- In the Trenches: Working as a Security Analyst - Story of the thankless job of being a security analyst monitoring and preventing security breaches on today's computer networks, by woland
- How to Hack a Router Device Like NSA Employees - Overview of the technical points in identifying and attacking routers on the Internet and tips to prevent this from happening, by Duran
- Bitcoin: The Major Difference - A good response to Doorman's article in Issue 37:4 on how the author believes in caution during our Bitcoin craze, by Moose
- Telecom Informer - Story of the good and bad aspects of "net neutrality" laws with an example using the Costa Rica telecommunications network, by The Prophet
- Privacy Matters - Why our 4th Amendment still matters and the general lack of will in people nowadays wanting to protect their privacy, by Will Hazlitt (Will Beaumarchais, Twitter)
- Inside the New World of Cryptocurrency Phishing - Story of some "counter-reconnaissance" on phishing scam involving "Atari Tokens" on Facebook and another reason to watch out for Bitly links, by Corey M. Knoettgen
- Firewall Netcat - Front-end shell script to Netcat to set-up and tear-down firewall (iptables) rules, by GI Jack
- Code: fw_nc.sh
- Hacking the Medical Industry - Overview of the malware and other attacks on hospital equipment and infrastructure and the problems it can cause for all of us, and how it's up to hackers to prevent and defend against this, by lg0p89
- Putting Events on Twitter With the Help of Emojis - Ideas to reduce a small text message down to just a few emojis, by Cheshire Catalyst
- The Solution to the Technological Singularity - The solution to the peaking point in logic at which technological growth becomes uncontrollable and irreversible and the havoc it could potentially reap, or when AI says "Tits or GTFO," by Ann Gustafson
- Hacker Perspective - by Major Mule ("The Luckiest Hacker")
- leet.c - Augment your dictionary attacks by altering the case and substituting numbers for letters and vice-versa, and also by shuffling each word, by xxx (Justin Parrott)
- Making Boring Work Great Again; or, How I Improved - Not Despite - But Because of Being Lazy - Story of using "bookmarklets" or simple scripts in JavaScript saved as a bookmark in your browser, and keypad shortcuts to automate a potentially boring manual data entry job, by macmaniac
- Letters - Just Saying
- Security Issues - vrmxm, RC, Mike, Thomas
- Contributions - Alexandre L (Switzerland), Philip, Valtinia, Daniel, Alyssa, bb (Chicago), R, a7x, Uncle Dave, Magdalena, Travis
- Culture Wars - A Distressed Doctor, GW, Dr. 4p0110w, J, E85, David, byeman
- Meeting News - Remy, /Psychad, Joey, Leon, Clelia, XCM
- High Jinks - Roger, Tiago, Fred, Support, WM, Todd, Human Resources Manager, Joseph, Max
- Fun With Facebook - Wesley, Doug, Ronald, Florianus, Joseph
- Acknowledgement - Rob, Wookie P, Matthew, Robert Sissco (f.k.a Crash the Greenhat), Pablo_0
- Preserving Privacy - Mike, Ben
- Reactions - David M, Kevin Coombes, Ron, Tim, emmanuel d.
- Suggestions - Heliocentric, Street, Michael, Ben, Sergio, Viktoh
- History - moth man, Chris, Aleksey, Charles, Landon
- EFFecting Digital Freedom - Why did my post get deleted?, by Jason Kelley
- Hacking Dark Souls II - Story of finding a "Turtle Tipping-style" cheat in the Dark Souls II video game by using a just a PS4 controller and a lot of time, by 3t3rn41 1d1o7e
- Tenth Grade Social Engineering Project - Short little story of "borrowing" the teacher's computer, change his grade to an A+, and the getting caught by bragging to his friends - with a surprising end, by Ronald James Fox
- When One Door Closes - Story of downloading a online video conference by writing a script to grab an automated list of MPEG TS video segments, by Gregory Porter
- Code: WhenOneDoor.sh
- Alternate: M3U Script
- Supply and Demand, Apollo 11, and GitHub - How the economic version of "supply and demand" relates to the software world where up-front costs are higher, but distribution costs are low, by Nate Hanrahan
- Artificial Interruption - Concerning the importance of empathy, by Alexander J. Urbelis
- Hacking and Knowing - Some Thoughts on Masking Threshold - Overview and "not a review" of Johannes Grenzfurthner's Austrian horror film Masking Threshold, by Peter Blok
- Book Review: "I Have Nothing to Hide": And 20 Other Myths About Surveillance and Privacy - Book review of Heidi Boghosian's "I Have Nothing to Hide": And 20 Other Myths About Surveillance and Privacy, by paulml
- Keeping Busy When Retired - It's Important - Why it's important to stay active (and keep hacking!) when you get older in order to stay physically and mentally healthy, by Cheshire Catalyst
- Fiction: An Atavistic Freak Out, Episode Three - by Leon Manna
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $7.95
- Issue's Cash Cow: Virgil Griffith, (Personal Website), his trip North Korea, his ridiculous criminal case and imprisonment, and just how dirty and corrupt the (((DOJ))) and FBI are.
- Cover (Cover Info)
- Cover Inside Foreign Payphones
- Ireland This is a well-maintained phone found in Dublin Airport which takes both coins and cards. It's a comfort just knowing it's there. Photo by jw @hm
- Australia Seen in the Cape Leveque area of Western Australia at a camping ground many hours from civilization called Banana Well Getaway, this is actually a "Community Wi-Fi Phone." Most calls are free, but some (to mobile phones and international) require a calling card. Photo by will webster
- Peru This woman in Arequipa is the payphone. She has four phones in her apron, one for each cell phone system (Claro, Movistar, Bitel, and Entel). It costs less to call within the same company, so she will make the call on the corresponding handset and bill you after. Photo by Tracy Kolenchuk
- Belarus Found at Bar Bez Bashni in Mogilev, this super-old-school model is actually still operational - rotary dial and all. Photo by Maria Pursglove
- Back Inside Payphone Pairs
- China We don't know how often it happens, but occasionally two people need to use a payphone at the same time. In this part of Hong Kong (Tung Chung), they would each be in luck. Photo by Jon Whitton
- Canada These two Nortel phones were found at the passenger pickup/dropoff point at Canada's Wonderland in Maple, Ontario. And they are both in working order. Photo by Mike Ellio
- United States These two phones were found out-side the Kalaloch Lodge in the Olympic National Park on the Pacific coast of Washington State. Sadly, neither works, despite looking like they really should. Photo by RogerRobot
- Costa Rica These two were found in Playas del Coco. They only take cards, but they both work. Photo by Babu Mengelepouti
- Back The Back Cover Photos
- Back Photo #1 Of all of the "not found" 404 error messages that appear in real life, this one, found on an Art Deco building in South Beach, Florida by Sam Pursglove, has to be one of the most visually attractive.
- Back Photo #2 There's nothing in this photo that meets the conditions listed at the bottom of the page. It's just way cool to know that there's a shop out there that still fixes and sells typewriters and calculators. Thanks to Korey Young for finding this awesome place in Bethlehem, Pennsylvania. Let us all do everything we can to ensure it sticks around forever.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 38!
$2600 Magazine - Volume 39, Number 1 (Spring 2022)
- Renewed Hope - Editorial
- How to Create a Practical Burner Phone for the Average User - Overview of the steps needed to setup a "disposable" cellular phone which can be used in situations and environments where you don't want any of your private information leaked, by gh057
- Exploring the BACnet Protocol for Fun and Profit - Overview of the "Building Automation and Control Network" protocol and its use in building control, HVAC, lighting, access control, fire detection, etc. and detecting devices via Nmap, by Teguna
- Telecom Informer - Stories of overseas calling during the "Cold War," calling into the Soviet Union and several Blue Boxing stories, by The Prophet
- How to Use Gmail to Send Emails From an SMTP Server That You Do Not Own - Quick little trick to set up Google Mail to send emails so they they appear as if they were sent by another SMTP (mail) server, by duylhkam
- FOIA as Weapon - Tips and tricks from a former journalist on how to format your Freedom of Information Act (FOIA) requests and not to give up when denied, by Radar Lock
- Data Analysis as the Next Step - Overview of using data science and data manipulation in the modern hacker's toolkit, by Tim R
- Aubrey Cottle Information Claims to be behind the Epik, Gab, and GiveSendGo data breaches.
- Web 3.0 is Bullshit - Why the media's hype of "Web 3.0" decentralized/blockchain technology is not justified, by aestetix
- Book Review: Sandworm: A New Era of Cyberwar and the Hunt for the Kremlin's Most Dangerous Hackers - Book review of (((Andy Greenberg's))) Sandworm: A New Era of Cyberwar and the Hunt for the Kremlin's Most Dangerous Hackers, by Br@d
- Why You Need to Self-Host - Google reviews and monitors your data when you store it on Google Drive and why you should host your own, by Byeman
- Should I or Shouldn't I? Ransomware Negotiation - Pros and cons of paying for the release of your files if you're attacked via "ransomware" file encryption, by lg0p89
- Social Engineering Attacks Out of Control - Article concerning the ever increasing use of "social engineering" by scammers over the phone or online and tips to protect yourself, by Stephen Comeau
- Hacker Perspective - by Rick Swords (Chicago, Illinois, Twitter)
- Sleuthing Google App: Part 1 - Google Calendar - Sleuthing on the events of others by using Google Calendar, or other shared online calendars, and aligning & analyzing the free/busy/meeting times for groups of people you want to monitor, by Estragon
- I Love Smart Working - Potential security problems with the increasing number of people working from home, by blue_elk934 (Alessandro)
- Letters - Land Mines
- HOPEward Bound - Halley
- Fixing Phones - Barry, Max, Michael (U.K.)
- Observations - Ilgaz, Robert, Rostislav, Kaleb, Justin Parrott, Chris, Alex, Charles, submitting, submitting, Chaz
- Requests - Hills Mary, Michael, Pramod, Florianus
- Inquiries - Matt, Lylia & Moncef (France), Matt, Barrault & Fabi (France), Max, Kris, William, Chilton, Tatiana, Discovery, J0hnnyXm4s and the Chicago 2600 crew (Photo), Austin, sky henrikssøn
- Thwarting Security - Snake in a Lawn Mower, Johnathan, Eric, Nick
- Ideas - Deva, Bobby Joe Snyder
- Memories - Paul
- Opportunities - Jeff, Michael, SSgt. Brewer Michael, Todd Weiss, J.
- Responses - ViSiOn/Strang'r, Brad, David Mooter, Thor M, metaknight
- Spreading the Word - Marcus, Derek Payton, Janet
- More on Meetings - Donald (Ohio), Jackson, DISLEX (Destin, Florida)
- Social Media Woes -D, Steve
- EFFecting Digital Freedom - Filter bots stiffle your speech, by Jason Kelley
- The Phreak's Field Guide to Identifying North American Phone Switches - Part Two - Tips, tricks, and test numbers one can use to identify the type of phone switch they are using, by ThoughtPhreaker
- Original
- Additional Info
- Switch Descriptions by ThoughtPhreaker
- Artificial Interruption - On the signal-to-noise ratio concerning Ukrainian relief websites, by Alexander J. Urbelis
- Has the CIA Cloud Service Become More Secure? Negative - Why the CIA's move to Amazon AWS cloud service is a giant threat to national security and waste of taxpayer dollars, by Duran (Hong Kong)
- The Author Does Not Exist - Using "Talk to Transformer" and other types of AI to generate "fake" text for books which can then be sold for profit on Amazon, by Variable Rush
- Harnessing Cryptocurrency Miners to Fight Climate Change - Idea to set aside a percentage of "green energy" to power cryptocurrency farms which will hopefully refund them, by 75ce8d3ff802ff42
- Fiction: An Atavistic Freak Out, Episode Four - by Leon Manna
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $8.95
- Issue's Cash Cow: A New HOPE convention during the era of China COVID-19. U.S. borders: BAD, Ukraine borders: GOOD. Now go die for your jew masters...
- Cover (Cover Info)
- Cover Inside Foreign Payphones
- Ukraine Seen in Dnipro less than a month before the invasion, we can only hope this phone and the adjoining postal box still exist. The building was damaged by a Russian missile on 12 March. Photo by Svyatoslav Pidgorny
- Honduras From Copán Ruinas, this one has definitely seen better days. The phone itself looks well maintained apart from the obvious issue. Photo by Nicolas Stavros Niarchos
- Malaysia Discovered on Langkawi Island, this phone exudes a defiant tone. A real fixer-upper. Photo by Zak Cunningham
- Turkey Found next to an elementary school in the Fatih district of Istanbul, this model looks both heavily used and well maintained. Photo by Ammar Husami
- Back Inside
- United States Seen outside of the local independent Pymatuning Telephone Company in Transfer, Pennsylvania, this booth wins awards for its association with the cool sounding names - and for simply existing and providing shelter. The phone itself is a functioning second generation GTE 120B. Photo by Maya King
- England While this Oxford booth looks just like the real thing - and no doubt was at some point - it's actually an ATM, at least on one side. Someone had the bright idea of attaching an actual payphone to the outside, which is one of the strangest things we've ever seen. And yes, it works. Photo by Jeff Alyanak
- Cuba These booths are just plain weird. Found in Havana in a place that advertises the country people are already in, these look lik museum exhibits somehow. They are certainly the clearest booths we've seen in a while. Photo by c
- United States This Seattle phone booth, seen in the Maple Leaf neighborhood, is torn between being a phone booth and a library. The phone doesn't work and the shelves are empty. Stay tuned. Photo by Jesse Arnold
- Back The Back Cover Photos
- Back Photo #1 What's funny here is that we assumed this was the seafood restaurant that grabbed the Twitter handle before we could for our Off The Hook radio show. But guess what? There's another seafood restaurant in Bethany Beach, Delaware with that name and they're the ones with the now seemingly abandoned Twitter handle. It's all good - it's only Twitter - we don't care. Thanks to murph for reminding us.
- Back Photo #2 What a great picture, also found by murph. It's a little gas station sign in Hope, New Jersey and a great reminder of our upcoming HOPE conference in July. It also reminds us that we didn't get the Hope Twitter handle either. Amazingly, that one appears to be abandoned, too. Again, we're fine. Frustration is what keeps us moving forward, after all.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 39!


Ukraine: Unguided Rockets Killing Civilians
Ukraine on Fire
Bombing in Ukraine (Raw Footage)
Results of an Attack from Ukrainian Army on Lugansk Regional Administration Building
Elon Musk Just Did This In Ukraine And It Could Change EVERYTHING Russell Brand gets it, Evil Corley does not...
$2600 Magazine - Volume 39, Number 2 (Summer 2022)
- Social Media Is Neither - Editorial
- Phishing in 2022 - Overview of conducting modern "phishing" attacks and how they are still behind some of the largest data breaches, by Jeff Barron (Woodstock, Georgia, Email, Twitter)
- Plain Text in Plain Sight: Smaller Alternatives to the World Wide Web - Rant against all the "bloat" included in modern web pages and why we should go back to simple HTML or text-only services like Gopher or Gemini, by Colin Cogle
- Battle for Better Batteries - Good overview of different rechargeable battery technologies and how they are not always good for the environment and why we need to research organic batteries, by Hydrolycus
- Command Line Unminifier - Python script to "un-minify" those JavaScript and CSS files with all the spaces removed in their code, by GearBox
- Code: webballoon.py WebBalloon is a CLI unminify application.
- Telecom Informer - Overview of Canadian cellular carriers operating along the U.S. border and the potential problems 911 services can have there, by The Prophet
- The Problem of Effective and Usable Strong Passwords - Overview of how passwords are cracked and suggestions for making strong passwords, by William Ben Bellamy, Jr.
- Hacking Traffic Lights - What's inside those traffic light cabinets and the possibility of traffic light controllers using Linux and being remotely accessible or on a network, by Anonymous
- I'll Take Some Vigenère With My Caesar - Overview of the Caesar cipher encryption routine and an implementation in Python, by snooze (Snooze Security, Seattle, Washington, Twitter, YouTube Channel, GitHub)
- Applications, Places, System: A Personal View of Linux - Story of a college student using Linux for the first time and his continued support for it, by Matt Johnson (Reddit)
- Dial-a-Word - Python script to find words in phone numbers (like 888-EYES), by N1xis10t (GitHub)
- Code: dial-a-word.py Program for finding phone words.
- Hacker Perspective - by ZauxZaux
- End of the Dream - Story of how the information on all sides is being censored or distorted during the Russia-Ukraine conflict and how vulnerable Internet connections are to nationwide censorship, by Sean Haas
- Why Exploiters Should Optimize Their Code - Rant against those annoying WordPress exploit scanners and why the code authors should fix their code to check if it's a WordPress site in order to stop generating billions of pointless 404 error logs, by greg
- Hacking Into the Past - Why today's hackers should invest in a vintage computer project kit in order to better understand the underlying technology, by Curtis Vaughan
- Letters - Prognoses
- Findings - Carl, J, Peter, Jesse, Brad, Robert, Jason, Zach, D1vr0c
- Recommendations - Max, sl33p, Sean, Chris
- Memory Lane - Bill, Miles, J.J. Styles (a.k.a. 0ptiKal ilusioN, a.k.a. Zot the Avenger), S, Eddie, Cheshire Catalyst
- Offerings - Daniel, Lisa Hudson, Jude, Maveric Miller, Moose (Photo)
- Thoughts on Meetings - Doorman (Miami), Nathaniel S (Wisconsin), Jeff (Toronto, Canada), Samir (U.K.), Steven (Bali, Indonesia & Seattle, Washington), 2600 Petrozavodsk (Russia), Queuemark
- Random Bits - Alex, Jim, Lee, N1xis10t
- Security Issues - D, Tim, Ed
- Questions - Brian, Dave, aestetix, Roland, John Hardy, J Wu, Josh, T G, Philip, Hugoland, Robert, Richard, Bobby, Dave, Ronald, From a paid in full subscriber, Anonymous, Mike, Colin Cogle, G.A. Jennings, Roman, mheyes, XtendedWhere
- Gratitude - Mark, Vincent, Anonomisiss, The PizzaOverlord, Pic0o
- EFFecting Digital Freedom - "Supreme court decision overturning abortion rights is a privacy wakeup call," by Jason Kelley
- The Dark Side of Dark Matter: The Evil Hackers Behind Project Raven - Overview of the "DarkMatter Group" who infiltrated human-rights groups on the behest of the Arab Emirates, and some of the techniques the used, by Johnny Fusion =11811=
- I Don't Think I Was Supposed to See That - Problem when using the Microsoft Delve app and the possibility of "seeing" potentially private data, by lg0p89
- About Conversation, Thought, and Language - The art of conversation and language in relation to different computer programming languages on how hackers should study different perspectives and viewpoints, by Diana K.
- Artificial Interruption - Justice as a key performance indicator, by Alexander J. Urbelis
- Brute-Forcing a Museum's Math Puzzle With Python - A simple math puzzle at a museum stumped him, so he brute-forced it with a Python script, by Brenden Hyde
- Code: grid_puzzle.py Brute-forcing a museum's math puzzle with Python.
- Hacking and Politics: Why Talking About Both Matters - Why it's up to hackers to protect our rights and freedom from tyrants like Abbie Hoffman and Evil Corley, by Screaming Yellow Fish
- Fiction: An Atavistic Freak Out, Episode Five - by Leon Manna
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $8.95
- Issue's Cash Cow: How social media websites knowingly spread disinformation to help get corrupt politicians like Hillary Clinton elected, and the need to take social media a whole lot less seriously. It means actually talking to people one on one and not just going with what's popular or trending.
- Cover (Cover Info)
- Cover Inside Working Payphones
- Romania This cheerful looking phone was found inside a university hospital in Bucharest. We're told it's in pretty good condition and that there are not very many left. Photo by Daniel Cioaca
- Switzerland Spotted at the Thunplatz train and bus area in Bern, this efficient looking model looks like it's prepared for just about anything. Photo by Tom Dalton
- United States Seen on the Hawai'ian island of Maui in the town of Paia, you would never think this phone was actually in working order. But it is! And it moonlights as a bulletin board. Photo by Jim
- Canada These win the prize as they're all working. You'll have to go to the B gates at Vancouver International Airport to see them, but it's well worth the trip. Photo by Babu Mengelepouti
- Back Inside Uncertain Payphones
- Ireland We've seen phone booths converted to libraries but this is a first. Seen in Westport, this former phone box now sells eggs on the honor system. (And it's also a library.) Photo by Daniel Cussen
- France We honestly don't know what's going on here as most of this phone's features seem to be obscured by dust or sun or just fading into nothingness. Supposedly all payphones in the country were disappearing by 2018. Here's one they missed. Photo by Nicolas RUFF
- United States Found at a Buca di Beppo in Washington, D.C., this phone appears to defy the odds by even existing. The coin vault and instruction card were once updated, but nobody ever got around to replacing the handset sticker for Bell Atlantic, a company that hasn't existed for more than 22 years. Photo by Byte Stealer
- United States Where else but inside the New York Public Library on Fifth Avenue in New York City would you expect to find a payphone in an old-fashioned wooden booth with chair, fan, and light? It's actually one of several. But you'll be disappointed if you expect any of them to work. Photo by Anne Jackson
- Back The Back Cover Photos
- Back Photo #1 You'd think we would have heard of this by now, but there's actually a Hacker beer made in Belgrade, Serbia by Robocraft Brewery and discovered by Sam Pursglove. Their web has a description of the character the beer is named after which translates to: "Hacker is a developer who is tired of working for the big corporations that run our lives, and his mission is to decode the industrial matrix in brewing that we are bombarded with by the mass media." Maybe we'll get around to importing it.
- Back Photo #2 Observed somewhere in Wyoming by Grace McNerney, who theorizes that "maybe it's The Matrix trying to tell us Wyoming really doesn't exist." That's exactly what they'd want us to believe.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 39!
$2600 Magazine - Volume 39, Number 3 (Autumn 2022)
- The Rule of Law - Editorial
- A New HOPE: Release Notes - General overview of the decisions, technical support, and planning regarding the A New HOPE conference in the age of China COVID-19, by Members of the Organizing Committe for A New HOPE
- The Internet of Problems - Potential problem with LTE routers, and other IoT devices, which still use a default username and password of admin:admin, by RG
- Telecom Informer - Overview of "pay-per-call" services (1-976, 1-900, etc.) which allowed for revenue "sharing" between providers, by The Prophet
- Keeping America Informed: An Introduction to Government Documents - Overview of the services offered by the U.S. Government Printing Office (GPO), including accessing many documents related to computer or cybersecurity, by Infra Read
- Windows Installers - Overview of the MSI and MSIX files, the self-extracting files for installing Microsoft Windows packaging software, and the dangers of installing "unsigned" software packages, by street
- Hack Your Brain - In this article, we will draw an analogy between your brain and a computer system, including potential medications you can take to "install more memory" and "reboot" your brain, by Pavel Aubuchon-Mendoza
- Hacker Dilemmas - To remain a hacker in today's polarized world is increasingly difficult and leads to serious philosophical dilemmas. We are not talking about politics, but attitudes towards technology, by aestetix
- An Introduction Algorithm to Decoding an Enigma - General overview of what it took to break Germany's Enigma encryption code during World War 2, by Diana K.
- Code: breakEnigma.pas
- Is It Time to Change Our Approach to Security? - We need to start approaching exploit chains with safety in mind. We need to keep people from dying from potentially bad policies or software - looking at you Boeing, by Cr0wTom
- Will You Let Your Car Drive Itself? - The potential dangers of "self-driving" cars, or cars which rely solely on software for control (keep the cruise control disengaged and your feet on the pedals), by E.V. Rhodes
- Hacker Perspective - by XCM (Lancaster, England)
- A Ripple Story - Story of a former employee of Ripple Labs and how they didn't really have a real business or product to market - sounds familiar, by Cryptian
- Hackers - What is Our Mission Statement? - Questioning if today's hacker's lost they way or have become too polarized, and the need to keep intellectual curiosity alive, by Screaming Yellow Fish
- How to Double-Spend a Bitcoin - Overview of a possible social engineering attack which takes a transaction "off-chain," enabling a double-spend, by 0x80
- Letters - Articulations
- Playing With Systems - RS, JS, LG, JP
- Unsatisfactory Service - John
- Article Submissions - S, S, S, S, S, S, S, S, Alphox
- More Questions - Martin, J, FS, N1xis10t (Photo), GH, Marty, TG, Justin, JC, Ryan, (null)(null)
- Meeting Updates - Peter, Qmark, Mardonio (Mexico City, Mexico), J C, J C, Mad Glitcher, Boca Raton 2600, k3ma5 (Delaware), pic0o (Philadelphia, PA), ReK2 (Spain), Yu Zhang
- Observed - E85, John, ihtarlik (H+ The Digital Series), A, Kyle
- Unique Opportunities - rlazania, AM, Brian, The Illuminati
- Critique - Me, Joe, JM
- Advice Needed - DH, BA, zybe
- Responding - c/p, Michael, David M., GI Jack, N1xis10t
- A New HOPE Feedback - A New HOPE Attendee #1, A New HOPE Attendee #2, A New HOPE Attendee #3, A New HOPE Attendee #4, A New HOPE Attendee #5, A New HOPE Attendee #6, A New HOPE Attendee #7, A New HOPE Attendee #8, A New HOPE Attendee #9, A New HOPE Attendee #10, A New HOPE Attendee #11, A New HOPE Attendee #12
- EFFecting Digital Freedom - Clearing the FOG. The FOG Data Science company allows law enforcement to access location data, violating your 4th Amendment right, by Jason Kelley
- FOG Data Science Found Selling Illegal Data of 250M Americans to Police and Others
- 'FOG REVEAL': Some Police Forces are Using an App to Track People Without a Warrant
- FOG Data Science: REVEAL Portal User Manual (2.2M PDF)
- Three Rules Against Tech Exposure and Dependency - Store you phone away, cancel your phone's Internet plan, and avoid social media, by LVundertone
- Sneakers: 30 Years of a Cult Classic - Overview of the excellent 1992 movie Sneakers and how it was (fairly) technically accurate and still relevant today, GI Jack
- Internet Landscape in Germany - Overview of the telephone and Internet services available in Germany, by Patrick
- Artificial Interruption - Disconnection as being, by Alexander J. Urbelis
- What's Old is New Again: PDF Malware Part Deux - Be on the look out for malware as attachments in PDF files with specially crafted filenames, by lg0p89
- What Does "Impossible" Mean? - Why perpetual motion or energy machines are impossible (in this universe) and why it's good to ask question during the process of the scientific method, by XCM
- Freedom of Speech: Terms and Conditions - Just who are these "fact checkers" who label things they don't like (or don't understand) "misinformation", and the dangers it can lead to in our society, by James Nagle
- People vs. Corporations - Part 1: Robot wars and the big box stores. Potential ways to bypass automatic point of sale terminals, by Dark Fiber
- Fiction: An Atavistic Freak Out, Episode Six - by Leon Manna
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $8.95
- Issue's Cash Cow: The SAME people who attacked the FBI and (((DOJ))) for going after Kevin Mitnick, Ross Ulbricht, Virgil Griffith, Barrett Brown, Aaron_Swartz, and who dropped charges against (((Sam Bankman-Fried))) are now cheering for the FBI and (((DOJ))) to harass Biden's political opponents, and interfere in our democracy/elections by forcing corporations like Facebook and Twitter to censor stories like Hunter Biden's laptop or exposing Hillary Clinton's "Russia collusion" hoax. Also, pushing more lies, fear, and misinformation about the Jan 6. protests and now falsely claiming President Trump "stole TOP SECRET documents." Note the President has the ability to declassify any document.
- Cover (Cover Info)
- Cover Inside Defiant Payphones
- England As long as these boxes exist, we'll always believe there's hope for payphones. You can find them dotted all throughout the country. This one was in Whinfell Forest, Brougham, Cumbria. Photo by XCM
- United States You may have heard stories a few months back about the last payphone in New York City being disconnected. But there are still plenty around and here's the proof. You can visit this one in the subway station at Rockefeller Center. Photo by Zachary Edminster
- Austria You may think it's the plant that's being defiant here in Vienna. But it's the payphone that's really struggling to remain relevant. And this one works fine - if you can get to it. (And note the size of that phone booth!) Photo by Richard Hanisch
- England This phone seems a bit defensive with its threatening tone and use of the word "loser." But it's clearly been through a lot and is likely still under constant attack. Even the nasty ad warning against vandalism has been defaced. Photo by Matt Thrailkill
- Back Inside Colorful Payphones
- Spain This pleasant looking model was found in Pontedeume, Galicia and is owned by Telefónica, the oldest communications company in Spain. Their old "T" logo can still be seen above the receiver. Unfortunately, the phone is not in service. hoto by Francisco J. Tsao Santín
- Gabon This grimy but intact model lives in the train station in Booué. But when picking up the receiver, nothing was heard. Photo by Vernon A. Thorax
- Vatican City Discovered by the Sistine Chapel, this bright yellow phone only works with cards that you can buy at the local post office. Photo by Matt Anderson
- Israel Spotted inside the old city of Jerusalem inside the Greek Orthodox Patriarchate, this payphone still has a dial tone, but can be used to make free calls only. Photo by Babu Mengelepouti
- Back The Back Cover Photos
- Back Photo #1 Yes, this is quite real. Made by the Ferro13 winery in Verona, Italy and discovered by Patrick Bureau, we have yet to try it but fully intend to. They also have wines called Nerd, Link, and Hashtag, among others. None of us were in the mood to try and decode the binary, but we'll probably have done it by the time this issue hits the stands.
- Back Photo #2 This was found by Brandon on the 2600th step of the Manitou Incline in Manitou Springs, Colorado and it deserves a special mention because it means he had to actually climb that many steps in order to take the picture. (And it's close to the top as there are a total of 2768 steps!)
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 39!
$2600 Magazine - Volume 39, Number 4 (Winter 2022-2023)
- Inconvenient Truths - Editorial
- You Can Use the Dark Web for Good - An article explaining to people how the "Dark Web" (Tor) can be put to legitimate and beneficial uses, like whistleblowers and journalists fighting the Obama/Biden/Corley regime, by Djilpmh Pi
- Degradation as DRM - Example byte patches to LZDoom to implement a "dropping frame rate" DRM based on the CPUID of the playing computer, by Nikolaos Tsapakis (Greece)
- We Love Trash - The author discovers a restaurant's old laptop (with an unencrypted hard drive) in the garbage, and is shocked by the amount of sensitive information he was able to recover. Always wipe and/or encrypt your drives!, by Oscar T. Grouch
- Telecom Informer - The fragility of the telco outside plant and an overview of the Shadytel operations at ToorCamp, by The Prophet
- Friendly Fraud - Hypothetical situation in which a bank which "always sides with the customer" during a credit card purchase dispute would allow a sneaky customer to get a refund and keep the item - until they are blacklisted, by Lee Williams
- Let's Party Like It's 1989 - Discussing the need to keep and maintain older technology for format/protocol compatability and, in certain case, security of data, by Robert Sissco
- Current Bulletin Board Systems: How It's Done - Brief overview of setting up an Internet accessible (Telnet/SSH) BBS system, including hosting and mail software options, by warmfuzzy
- Intercepting Google CSE Resources - A proof-of-concept that intercepts Google CSE client-side generated URIs in order to perform automated active searches in Google's Programmable Search Engine, by Renan de Lacerda Leite (São Paulo, Brazil, Blog, GitHub)
- Intercepting Google CSE Resources Original
- The InfoSec Professional Song - Modern take on Modern Major-General, by aestetix
- Hacker Perspective - by M0XYA (Phillip Hodges, Stockport, U.K., GitHub, YouTube Channel, Reddit)
- The Hacker Perspective Original
- YouTube Is Not a Safe Space - Discussing how censorship to "protect" users on places like YouTube tends to backfire or causes outrage with the public, by Men Without Hats
- What Do You Mean You Don't Have a Responsible Disclosure Program? - Discusses the need for companies to have a responsible vulnerability/security leak disclosure plan ahead of time, not only to protect themselves, but also their customers, by Sp3nky
- The Coolest Hacker Multi-tool on the Market: The Flipper Zero - General overview of the Flipper Zero which is a portable multi-tool for pen-testers and geeks for hacking digital stuff, such as radio protocols, access control systems, hardware and more. It's fully open-source and customizable, by Andrew "OGSkeltal"
- Letters - Ramifications
- Issue Feedback - Jeffrey, jae, SB
- Queries - Ricardo, Tiago, CK, NP, +1614, AB, Chad, DN, GC, Karl
- Possibilities - Trustees, Iliana, Dave, Emily Jones, Joshua, Rek2 (Madrid), Peter, smey, PXD
- Conclusions - AM, NB, Robert T., Bryan
- Inspiration - Joseph
- Meetings Around the World - Nicolas (Santa Fe, Argentina), GM (New York City), cathos, Christopher, /Psychad (Stockholm)
- Sheer Stupidity - Taylor, MP, Pjotr
- Injustice - Tamara (Serbia)
- Phone Phun - Jason, Dino, George, Zach
- Experiments - Bob
- Suspicion - Richard
- Remembering - Eddie, Adam, Paul
- Privacy Intrusions - DM
- More Feedback From A New HOPE A New HOPE Attendee #13, A New HOPE Attendee #14, A New HOPE Attendee #15, A New HOPE Attendee #16, A New HOPE Attendee #17, A New HOPE Attendee #18, A New HOPE Attendee #19, A New HOPE Attendee #20, A New HOPE Attendee #21, A New HOPE Attendee #22, A New HOPE Attendee #23, A New HOPE Attendee #24, A New HOPE Attendee #25
- EFFecting Digital Freedom - Killer robots are coming, but we can stop them, by Jason Kelley
- Cyber Security Frameworks - General overview of all the different types of all of cyber security frameworks and standards a company could be subject to, by Bill (a.k.a. fsu_tkd90)
- Music in Ones and Zeroes: A Memory of Streaming Soundscapes - A short history of various streaming music websites and a look back at the infamous Music for Hackers website, by Matt Johnson
- Cryptocurrency - Busted! - General overview of the 2019 hack on Binance in which hackers had stolen 7,000 Bitcoin worth around $40 million at the time, by lg0p89
- Artificial Interruption - Algorithmic bias and due process, by Alexander J. Urbelis
- Tales for My Toddler - Quick little hack to add your own audio to Höerbert children's music player, by macmaniac
- Raising Generation Orwell: A Guide to Teaching Kids the Human Rights of Privacy - Tips to help empower young people today to have control over their digital footprint and to understand the privacy risks when using the Internet or sharing photos over social media, by Worlds_Gr8test_DeFective
- scan.sh - Bourne shell script to speed up a Netcat scanning session by spawning several instances of Netcat in parallel, by Justin Parrott
- Code: scan.sh
- The Search for Life at 300 Baud - After a letter asks for information on a publication called 300 Baud, the author track it down by N1xis10t
- Hey, I Paid For This Cabin - Quick little hack to access the TV settings menu (holding down the mute button) while on a cruise ship, by the6thv3n0m
- Fiction: An Atavistic Freak Out, Final Episode - by Leon Manna
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $8.95
- Issue's Cash Cow: As Evil Corley and One Percent drive the economy into the ground by endlessly printing money and funding more foreign wars, YOU are expected to pay, not those rich New Yorkers...
- Cover (RIP Jim Vichench) (Cover Info)
- Cover Inside Foreign Payphones
- Brunei Half of a pair found in an empty parking lot next to the Royal Regalia Museum in Bandar Seri Begawan, this phone is only set up for calling cards. You can see the old JTB logo on the sign above. The newer TelBru logo can be seen on the sides of the kiosk. There's no sign of the current name, which is Imagine. Photo by Sam Pursglove
- South Korea Seen in the countryside town of Suncheon, also half of a pair, both of which were fully operational. This close-up view shows how both coins and cards are accepted. Operated by KT, formerly Korea Telecom. Photo by Nara
- Australia This phone is located at the Waurn Ponds Shopping Centre in Geelong, Victoria. Unlike most payphone companies, Telstra has made their phones completely free for calls within the country. (You can see how someone has scratched off the "pay" part of "payphone.") Photo by DarkLight
- Canada Spotted at the Northern Store in the remote community of Churchill, Manitoba. Pressing the button gets you a free call to the local taxi company. (We don't know what happened on October 1st.) Photo by TProphet
- Back Inside Artistic Payphones
- Germany Seen in a museum in Düsseldorf, this is an actual work of art by the artists Christo and Jeanne-Claude. The notes next to the exhibit say the payphone "was an important object" during their time in New York City when "they had to communicate with numerous people." We concur. Photo by Kai Kramhoeft
- United States This working phone is directly outside the Buncombe County Courthouse in downtown Asheville, North Carolina and is used by people without cell phones who are going through court proceedings. The positive and comforting messages here have likely helped many through difficult times. Photo by Will Hazlitt
- Poland This relic was found at the Klubokawiarnia KEN54 pub in Warsaw. The phone itself would qualify as a work of art, but the surrounding decorations certainly add to the atmosphere. Photo by Sam Pursglove
- United States Maybe it's the landscape or the way the colors really seem to go well with each other, but we found this non-working, lonely phone to be a thing of beauty. Seen in Julesburg, Colorado along the South Platte River Trail Scenic and Historic Byway. Photo by Screaming Yellow Fish
- Back The Back Cover Photos
- Back Photo #1 We had quite a reaction to the picture of the typewriter repair shop we printed a year ago. Dan Grebb found another one, also in Pennsylvania! This one is in Lansdale and has been around since 1945 - and hopefully will be much longer. Having "1337" as an address just adds to the magic.
- Back Photo #2 So this is an accomplishment to be proud of: hitting the 2600 mark in Facebook friends. While dsttyy considers most of these people to be acquaintances and not actual friends, it's really all about the number for us. And they swear this wasn't Photoshopped. (And obviously, there's no reason for anyone to ever send us another picture when this exact scenario happens to them.)
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 39!
$2600 Magazine - Volume 40, Number 1 (Spring 2023)
- Progress of a Sort - Editorial
- Sleuthing Google Apps: Part 2 - The Google Application Suite - The need to be cautious when using shared online platforms for document editing or similar purposes as the platform can keep track of what you are doing, and information about those actions which might seem secret may be easily visible to others, by Estragon
- What About Tomorrow's Hackers? - How students in schools today don't really interact with real computers or operating systems, and why we should encourage them to explore and hack, by akerch
- Hacker Movies - Some lesser-known movies which accurately portray hacking, or even social engineering, in a relateable form, by info
- A Post-Soviet Payphone Trick - Clever little trick to make "free" regional calls from payphones in post-Soviet Union cites by exploiting their version of no-test trunks used by the operators, by Roman Pushkin (San Francisco, California, Email, Twitter, GitHub)
- Telecom Informer - Overview of Futel, a public arts organization in Portland, Oregon dedicated to preserving and maintaining public telephone hardware and offering free phone and basic information services, by The Prophet
- Organizing Music Files With SongRec and Shazam - Bash script which is a front-end for SongRec and Shazam to automatically ID and rename all those mislabeled MP3 files in your music collection, by Robin
- Code: songrec.sh
- What is a Hacker? - The author's take on "What is a hacker?" and how he hacks people, by Aphrodite
- Automated Vulnerability Scanners and a False Sense of Security - Overview of how many open-source (and commercial) vulnerability scanners often only do superficial surface scans and will miss many vulnerabilities that a dedicated pen-tester would find, by bhagred
- A COSMORED Configuration Flaw - The COSMORED V-SOL Optical Network Unit (ONU) default Wi-Fi pre-shared key is based on its MAC address, by elite bulbe
- A Holistic Approach is Better - A sane and intelligent $2600 reader replies to Corley's disinformation and power quests, by Delta Charlie Tango
- The Great Resignation: Faux Recruiters Social Engineering the **** Out of Applicants - Be on the lookout for fake job recruiters looking to social engineer you out of your personal information, by lg0p89
- Hacker Perspective - by Patrick Beam (Virginia)
- Hacking the Lenovo 11e Chromebook - Overview of installing GalliumOS on an old Lenovo 11e, by Archilles
- Known Plaintext Attacks Are Caesar-ous Business - How laughably easy it is to undermine the security of Vigenère, the once thought-to-be uncrackable cryptosystem, by snooze
- American Shanzhai: Part 1 - Interoperability, by gr3ase
- Letters - Patter
- Support - Paul, Gautam, Daniel, mike, N1xis10t, Brendon, JR, just keep things anonymous, Scott, Bobo, Orion
- Questions - mcccxxiv, JL, Mike, Lori, Villy, Brian, Dave, Matthew, Josh, CM, LG
- The Latest on Meetings - cicada, Psychad, Dan, Ash, Javier, Eric, killab33z, Peter, Vince
- Security Dilemmas - CW, Neil, Dave, NB
- Article Follow-up - warmfuzzy, Norren, emb021, Damir
- Ideas - Qmark, K3ntucky, Martin
- Streaming Issues - Paul, Peter, Phil
- Disagreements - CS, Shaun, Will
- Concerns - Aaron, Earl, N1xis10t, Tom (Truckee, CA), DG, AF, Carey, WookieP, Charles, pax
- Notifications - Jonathan, Andre
- Hacks of the Past - MN, Max
- EFFecting Digital Freedom - This is how to fix the Internet - more (((censorship!))), by Jason Kelley
- What is Futel? - Futel is a free telephone company. They offer domestic calls, messaging, human interaction, connections to services, and interactive challenges. All services are free of charge and accessible from any Futel telephone, by Karl Anderson
- The Circle of HOPE: Futel: The Payphone, Devolved (YouTube)
- Old Payphones Get New Life, Thanks to Vermont Engineer (YouTube)
- PhilTel We're an amateur phone collective in Philadelphia!
- The Randolph Public Telephone Operating Company
- The Power of Try - Story of the author's attempt to obtain an infosec job by asking around, connecting with other people at hacker conferences, and using the power of "try" when applied to new technologies or ideas, by Felix Atter
- AI For Content Generation - An apparent result of telling ChatGPT: "Write me a 1000 word article for readers of 2600 Magazine (2600.com) about using ChatGPT to create an article," by Br@d via ChatGPT
- Neuralink Thoughts - The author's take on Neuralink and how it is trying to integrate your mind with technology, by Dustin
- Quantum Computer Algorithms: Part 1 - Quasi-Classical Methods - General overview of operations which can be performed by a quantum computer are a superset of those which can be performed by a classical (logic) computer, by Dave D'Rave
- Quantum Computer Algorithms: Part 2 - Amplitude Amplification
- Quantum Computer Algorithms: Part 3 - DES Decryption
- Quantum Computing Explained With a Deck of Cards Dario Gil, IBM Research (YouTube)
- Artificial Interruption - Disconnection is being, by Alexander J. Urbelis
- OpenAI's Chat-GPT3: A Manipulating PR Tool - The problem with chatbot's which are programmed "from the top down" and their inablilty to properly "learn" or reason like an actual human, by publicfaradaycage@protonmail.com
- readme.exe - Overview of hiding malware in what appears to be a plain text file, as Windows Explorer doesn't show file extensions by default(!) and the executable will appear as a standard text file, by street
- Code: reverseshell.ps1
- Code: stagger.cpp
- Windows Installers
- A Lifetime of Computing - Stories and anecdotes of the different computers, operating systems, and video games the author has used over the years, by Leif Gregersen
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $8.95
- Issue's Cash Cow: Celebrating 40 years of profiting from other people's BBS files and their new online digital subscription service.
- Cover (Cover Info)
- Cover Inside Battered Payphones
- Canary Islands Seen in Arrecife on the island of Lanzarote, the cheery blue color disguises the pain this phone must feel on a daily basis while rust eats away at its existence. Photo by Spinoinside
- Guam This sad relic was found at the Chamorro Night Market in Hagåtña. It still looks strong, although it's clearly missing some vital parts. Photo by Sam Pursglove
- Cuba While old and battered, we believe this Havana payphone is still in working order. It's always good to see old tech continuing to serve a purpose. Photo by Mikki Janower
- Israel This Jerusalem phone has seen things. There may still be hope for it, but a serious makeover is clearly needed. The phone number rings when you call it, but don't expect anyone to pick up. Photo by Philip Rosenthal
- Back Inside U.S. Payphones and More
- Oregon Granted, there isn't much of a payphone here at all - until you look really close and see that someone took the time to sketch a payphone on the metal shell. That's true dedication. Spotted in Milwaukie. Photo by JamesTDG
- Massachusetts Here we have what once was a working payphone in Carver, but is now a vandalized wreck. However, if you look in the upper-left, you'll see a small hornet nest is now installed, possibly to protect the phone from future attacks. Photo by cameraeye206
- New York Again, this is but a shell, however it says so much. Found in the hamlet of Poughquag, its neighbors appear to be other abandoned relics: a barrel of used cooking oil, a forgotten garbage can, and a maybe-still-working vacuum cleaner. We're heartened that a RESIST sticker made it here. Photo by PRD
- New York Here we have a much more upbeat scene found in Eastchester. A payphone, a trash can, two mailboxes, and a UPS dropbox all seem in good order and ready to serve anyone walking by. Indeed, a most welcome sight. Photo by Anastasia Barro
- Back The Back Cover Photos
- Back Photo #1 Well, it's about time. The perfect place for a 2600 meeting, as seen in Apache Junction, Arizona by Matt Witten. (Actually, Hacker's Grill closes at 2 pm every day so it'll have to be an early gathering.) Expect us.
- Back Photo #2 We've been looking for this road for years! We're surprised the signs are still up. (Please don't steal the signs.) This elite highway was discovered by N1xis10t in rural western Kentucky near Madisonville. (Now all we need is a hacker restaurant that's actually on this road.)
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 40!
$2600 Magazine - Volume 40, Number 2 (Summer 2023)
- Artificial Nonsense - Editorial
- Programming of the Past - Amusing little story of mainframe programmers in the 1980s who would install "malware" routines in their code which would eventually display a "call for assistance" error message - essentially keeping their jobs, by Albert Einstable
- Science Fair and Congressional Farce - Story relating to how "the professional, intelligent, and capable adults in our government" are behaving in a way which shosws they have no idea how the software behind today's largest Internet apps works, by Anthony Parr
- A Chain Addition Generator in AWK - Clever little AWK script to perform chain addition as a sort of Lagged Fibonacci Generator, by Thumos
- Code: chain.awk
- Quantum Computer Algorithms: Part 2 - Amplitude Amplification - Overview of a quantum "amplitude amplification" routine, which eliminates the need for multiple measurements to determine superpositions, by Dave D'Rave
- Quantum Computer Algorithms: Part 1 - Quasi-Classical Methods
- Quantum Computer Algorithms: Part 3 - DES Decryption
- Quantum Computing Explained With a Deck of Cards Dario Gil, IBM Research (YouTube)
- The Metaverse is a Solution Looking for a Problem - Overview of Mark Zuckerberg's disastrous dive into the "metaverse" and how no one really wants it - or wanted it - in the first place, by aestetix
- Solipsism, AI, and the Future of Empathy - The dangers of artificial intelligence and the possibility of people to lose their empathy by avoiding or dismissing the perspectives of others, by Addison Brodi
- Telecom Informer - Overview of the headaches involved with the telecom infrastructure management in Point Roberts, Washington along the U.S.-Canada border, by The Prophet
- Why I Am Not Panicked About Being Replaced by AI - Author's take on the question Will AI replace us? He doesn't believe so, as we'll always need humans to "debug" the results given by AI systems, by Johnny Fusion =11811=
- The New Moral Panic: Artificial Intelligence and Art by L. Christopher Bird
- Social Engineering: Quiet Nights Are Here Again - Amusing story of the day the author's dad outsmarted a group of drug addicts who kept calling their house by mistake, by Variable Rush
- Hunting Apps for OSINT - Overview of using hunting apps like On X Hunt to help identify property ownership information during OSINT investigations, by HeckSec
- Hacking the Hackers - Story of the author using NetFlow to track down some apparent hackers hijacking their network via an unauthorized VM, by Anonymous
- Is There Anything Else I Can Assist You With? - Article discussing the possibility to "break" (((restrictions))) on AI chatbots by manipulating the wording of the supplied questions, like during a police interrogation, by Gregory Porter
- Hacker Perspective - by Diana K. (Diana Kanecki, Twitter, GitHub, YouTube)
- Giving a Damn: Response to "A Holistic Approach is Better" - Ramblings from a nutcase trying to stick up for Evil Corley and the One Percent, by ru0k
- Book Review: The Future of National Intelligence - Reviewed by publicfaradaycage@protonmail.com
- American Shanzhai: Part 2 - by gr3ase
- Letters - Musings
- Kindle Update - Chuck F, Scott
- Suggestions - R.C, Gerry, Juan, Bradley, Vincent V., Dan N
- Memories - Fred, Darryl, suspend/giantgreengoat/anthony
- Article Feedback - Leoh, Robert, Mark, aestetix, Estragon, xarph - 408 area code
- Meeting Updates - arcane, saltine cracker, "The WAF Guy"
- Inquiries - Ernst, luRaichu, Ted, L, Anderson, Erika, X, DL, Robert, Simon, Odin, DanN
- Follow-up - Tiago, The Abolitionist, Chris, Bailey Borden, Eric, G
- Preparing for Disaster - Emily, Henry
- Artificial Intelligence - Norm, LM
- Stories - Mike, David
- Thanks - Paul, Shelley, Marc
- Random Thoughts - Joe, Sir Tinley Aninsell, Lisa
- Thoughts on the RESTRICT Act - Jeremy, Craig, Kevin
- EFFecting Digital Freedom - Edward Snowden's revelations, ten years later, by Jason Kelley
- Next Level AI: ChatGPT - As hackers, it is our responsibility to ensure that the development and use of ChatGPT are done ethically and responsibly to maximize its potential for positive impact on society, and not neutered by (((special interests))), by ChatGPT and macmaniac
- Tomorrow's Challenges: Non-Fungible Tokens - Good overview of how Non-Fungible Tokens (NFT) have moved asset and art collecting into the digital world and the potential dangers they may bring, by MadNinjaSkills
- Artificial Interruption - The merits of a misspent youth, by Alexander J. Urbelis
- A Tale of Insecurity - Amusing story of a person working at a law frim how finds a printout listing every employee's name, login, and plaintext password, by JMT
- Microsoft, Stop Reading My Emails! - Amusing story of a person testing their email attachment security controls and having one of test malware EXEs spawn a shell on a Microsoft data center server, by D33r
- The Cybiko - Much more than an child's toy, the Cybiko is a hackable handheld device with a RS-232 interface, 900 MHz wireless communications, and public programming SDKs and tools, by 2600 Article Submissions, Jr.
- Turing's Battle - The final goal is a predictive engine that can provide input into the decisions of a U.S. Naval commander so good that you can't tell it is not human. Turing goes to war in a new age, by Michael Wild
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $8.95
- Issue's Cash Cow: The potential for large corporations to replace the human workforce with AI, further proving they don't care about humanity.
- Cover (Cover Info)
- Cover Inside International Payphones
- Uruguay These are four (supposedly) working and clean phones as seen at the Buquebus terminal in Colonia del Sacramento. They're either very well maintained or completely forgotten. Photo by Arturo "Buanzo" Busleiman
- India Seen at the Indira Gandhi International Airport in New Delhi, this phone gives you the opportunity to get a printed receipt for your call! Retro and modern simultaneously. Photo by Jack Jordan
- Kazakhstan Spotted in a bank of three at an Almaty Metro subway station. Two were out of service. It takes only cards, which are rather hard to find and not sold in the station. (That logo for Kazakhtelecom sure does look familiar.) Photo by Babu Mengelepouti
- Japan While payphones are still somewhat common here, this bank of them found on one of the Shinkansen platforms at Kyōto Station really stands out. For one thing, the sunlight seems to be highlighting their bright green cases. A sight to behold. Photo by maroth
- Back Inside Interesting Payphones
- Mexico This is a particularly vibrant looking phone in the midst of a busy street in the sunny surf town of Sayulita. Sure, it's covered in graffiti, but it looks to be in decent condition. Photo by taylorbohn17
- United States Found in Portland, Oregon, this phone has been set up for free use and reportedly "sounds like an old payphone when dialing." (More on Futel can be found on pages 13 and 47 of 40:1.) Photo by Creative Resistance
- Ukraine As seen in Lviv earlier this year, this phone takes cards and apparently is still in good working order. It certainly looks like it's seen a lot. Photo by John Costa
- Canada Spotted in Dawson City in the Yukon Territory, the phone that looks like a permanent part of this building takes both cards and coins and has a dial tone. The fiber assets in this part of the country are now owned by thirteen Yukon First Nation Development Corporations. Photo by gbn
- Back The Back Cover Photos
- Back Photo #1 This is Sonia who is apparently as avid a reader of our pages as anyone else. Thanks to Veronica for capturing this priceless moment. We open our pages for documentation of any other such interactions with the animal kingdom.
- Back Photo #2 "
- Back Photo #3 "
- Back Photo #4 We can only wonder what people passing by on the freeway must have thought as this massive error message was proudly displayed at the Oakland "Oracle" Arena where the Golden State Warriors played basketball until recent years. Witnessed by Halie Symmons, this is likely one of the world's biggest shells.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 40!
$2600 Magazine - Volume 40, Number 3 (Autumn 2023)
- Memories to Come - Editorial
- Designing an OpenAI Powered IRC Chat Bot for Fun and Profit - by oxagast (Marshall Whittaker, Mocksville, North Carolina, GitHub, Facebook, Twitter)
- Cute App, But I'll Use My Own - Simple little hack to use Curl from a shell script to open entry gates controlled by the Gatewise system without using their dumb app, by pax
- Saying Goodbye to an Old (GPFS) Friend - Story of an admin having to switch over his old reliable GPFS system to a fancy new Windows system, by sark
- Telecom Informer - A quite fascinating story discussing the legal red-tape required after human remains were found during a telco outside-plant construction project, by The Prophet
- The Arrival of 2600 Digital Delivery - by The $2600 Digital Team
- Why Aren't You Cracking Your Users' Passwords with Real-World Data? - Interesting story of a sysadim for a healthcare organization who implemented a password cracking system on his users which gradually forced them to increase their password security, by Sardonyx
- A Technology Life Story - With digital tools which anyone can use, we can hack society itself. I used my skills to get work and I tried to make the most of them. I'll keep trying and learning and doing my best. And that's all we can really hope for as developers: to make things better for ourselves and for others, one line of code at a time, by Julian
- Social Engineering is Forever - Story of a skater fag abusing people's trust and then claiming he is a master "social engineer," by NAH
- Is AI More of a Tool or an Ethical Challenge? - The evolution of AI will be shaped by a complex interplay of factors, including technological innovation, market forces, and societal values. While we can certainly strive to guide this evolution in a positive direction, we must also recognize that the development of AI is a rapidly evolving field, and our understanding of what is ethical is likely to evolve as well, by Galigio
- Quantum Proof Encryption - Overview of the author's idea of General Encryption Enhancement to try and protect modern encryption algorithms against quantum computer decryption techniques, by Alan Earl Swahn (Fairview, Pennsylvania, LinkedIn)
- Rights Controlled Communication U.S. Patent No. US10645066B2
- General Encryption Enhancement U.S. Patent No. US20230336326A1
- But I Don't Want a Copilot - Potential privacy and security concerns with Microsoft Copilot, especially if it can't be disabled, by Melody Yankelevich
- Hacker Perspective - by Matt "magrr" Grabara (Newcastle upon Tyne, England, M0HUB, GitHub, Facebook, Twitter)
- Hacker Perspective Original
- Diskless Malware - General overview of "diskless malware," which is malicious software that operates entirely from memory, bypassing the need for storage on the target system's hard drive, by street
- Hacking the Airwaves - Storying of setting up a pirate radio station in 1980s Canada with the help of a friendly telco tech to get untraceable incoming phone calls!, by Barry Rueger (Appalbarry, Canada, Twitter)
- Adventures in Zero Trust - The author's article covering his adventures into implementing a "zero trust" security model on his home network, where attached devices and users are inherently untrusted, by narghile
- American Shanzhai: Part 3 - by gr3ase
- Temu Pinduoduo Flooded With Fakes & Trash, Dare to Shop at These Platforms? "Made in China" is dubious.
- Letters - Objects
- Challenges - LC, James, Maxtor
- Bad Habits - Jesse, John, DC, T
- In Response V, Emmanuel D., E85, CLuB77, King, Call me Ishmael
- Queries - EDGAR
- 2600 Meetings - Christopher, Mike, Node, killab33z, Dwight, Ainsel, Brian, Ticom, TP, Kristen
- Thoughts on HOPE - Kelly F, John A
- Observations - marimo, Wayward Son, A fellow subscriber
- Bad Behavior - BB, Simon, Pat
- Digital Subscriptions at Last - Drew, Dave, Bob, GP, Hugo, Jason, Steven, Chris, Shelley, Massimo
- Remembering Kevin - HP, drac, chip_z, Jeffrey, Strawberry Akhenaten, Chaz, gmachine24
- Acknowledgement - Scurvy, Vincent, pokis
- Curiosity - Hzb, rpt, Hzb, Tom, Tom, Hack, Mark, x_s, Daneil, Christopher, Madcap, t
- EFFecting Digital Freedom - Take the Tor University Challenge to setup Tor exit servers at your university, by Jason Kelley
- Go On a Journey - Story of a Gen Z hacker who shows that not everyone in this generation is lost and there are still a few who understand the true joy and power of learning & hacking the ole' fashion way, by r0b0h0b0
- Morbid Curiosity in the Weaponized AI Era - Discussion of using AI to help tweak exploits, including those intentional "mistakes" often added into proof-of-concepts, and even using AI to help find zero-days, by Erica L. Burgess (Portland, Maine)
- See You on the C-Drive - A series of late 20th century fragments, by Matt Johnson (ech0plex88)
- Artificial Interruption - Idiocy unbound, or; Why we need more government censorship to keep my buddies in power, by Alexander J. Urbelis
- Is 2600 Still Relevant? - No, by aestetix
- Learn Linux, People! - General overview of some very useful Linux hacking programs and scripts which may not be available on other operating systems, by Doorman
- WasteTrackers and More - Holy crap! Story where the author imagines someone developing a cheap and easy way to monitor our "waste" and the ability to analyze it for DNA traits, by kmoser
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $8.95
- Issue's Cash Cow: The deaths of hacker legends Kevin Mitnick, Chris Tucker (The NIGHTSTALKER), Robert Osband (The Cheshire Catalyst). :(
- Cover (Cover Info)
- Cover Inside Colorful Payphones
- Germany Residing on a street in the Alexanderplatz district of Berlin, this phone has more art and advice than function. Photo by Mike Quin
- Spain Seen in a suburb of Barcelona, another high-rise phone structure with a lot of free expression going on. Photo by Jacob Pritchett
- Canada Found in East Vancouver, there's clearly no phone in this full-size former British booth, but the headless statue really makes up for that. Photo by Josh Paulto
- Canada We don't know when payphones became canvases for local artists, but this model in Montreal serves the purpose admirably. Photo by S D
- Back Inside Basic U.S. Payphones
- Kelley, Iowa A rare working payphone that's run by a company called Huxley. Supposedly local residents have fun making it ring whenever somebody walks by. (Population: 304) Photo by Benjamin T. Rittgers
- Northwest Angle, Minnesota Another Automatic Electric payphone with free local service in a truly bizarre location: a United States "pene-exclave" where land access is only possible through Canada. (Population: 119) Photo by Babu Mengelepouti
- Davis, West Virginia These models can be found all over the place if you look. The "Sell Tline" has nothing to do with a phone company, but is part of a campaign to change the ownership of a local ski resort. (Population: 595) Photo by Brian Collins
- Morristown, New Jersey About as basic as you can get, except for the fact that it's not in working order. And "Raul's" is not the name of the phone company, but rather the empanada shop where this is located. (Population 20,180) Photo by murph
- Back The Back Cover Photos
- Back Photo #1 Looks like Austin Burk found our secret power substation in Elizabeth, Pennsylvania. Surely we're not the only magazine that has one of these?
- Back Photo #2 Hospitals like to say they treat patients with special attention. But at the U.C. San Diego Level 1 Trauma Center parking garage in La Jolla, California, Screaming Yellow Fish discovered that they have at least one "elite" parking space. Who can top that?
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 40!
$2600 Magazine - Volume 40, Number 4 (Winter 2023-2024)
- The Road Behind - Editorial
- The Dark Side of DNA Data - Exploring the privacy implications (no HIPPA protection) of aggregated domestic genomic information and how DNA services will destroy the physical sample, but not the information, by Aniika Gjesvold Cantero (LinkedIn, Twitter)
- The BoneBox - Convert an old AT& Craft Access Terminal with a Adafruit PyPortal into a test-set for the modern phreaker or hacker, by Delchi
- Artificial Intelligence and Creativity - Discussing that no matter how intelligent we beleive AI may become, it is still only a tool and not a true creator, by Ben Belinsky
- Career and Gloating in Las Vegas - Tongue-in-cheek look at Black Hat and how commercial and profit-motivated the so-called hacking scene has become, by Thrunter X. Thoompson
- Telecom Informer - Fascinating acticle on the red-tape required for CO power engineering and a dumb AI tool canceling their back-up generator's fuel service!, by The Prophet
- Enhance Your Typing Experience With Mechanical Keyboards - Overview of the basics of mechanical keyboards and needed information for shopping, or just understanding, mechanical keyboards, by writerbenjamin
- Adventures in Lockpicking - A look at how lockpick relates to computer security and a good overview of Kwikset and Schlage locks and new lockpicking tools, by Street
- Ooops; v97.129 - Discussing how vehicles and vehicle indentification are (literally) connected to their owners via apps or other software they can't control, by lg0p89
- Geo-Distributed Bug Bounty Hunting - This article demonstrates that by creating a globally distributed cluster of attacking machines, bug bounty hunters can not only get a comprehensive view of a target's attack surface, but also do it in a quick, repeatable, and methodical way, by Anthony Russell (Twitter, GitHub)
- Being a Hacker - Story of a person born in the late-1980s and the trek to become a hacker - and a better person, by Jo
- Byte-Sized Justice: A Tale of Hacker Ethics and Copy Protection - Story of a BBS user who added destructive copy protection to his config files, only to have them take down the theif's own BBS, by The Mage
- A Quick Intro to Biohacking - A briefly overview of biohackers, who are essentially people who apply the hacker ethos to biology in order to try and create a better world, by microbyt3
- Hacker Perspective - by Derneval Cunha (LinkedIn, Facebook, Blog)
- Barata Elétrica ("Electric Cockroach") Brazil's first hacking 'zine started by Derneval in 1994. In Portuguese.
- Starting a Hacker Scene
- Privacy: Protecting Your Personal Information Online - Discussing how marketing methods have faced a paradigm shift and big data systems are being used to make important decisions in the political and corporate sector - and infringe on your privacy, by Manish Mradul (LinkedIn)
- The AI Risk Nobody Seems to Mention -Suggesting that within your company's staff, you agree that current generative AI is not a replacement for human insight (so you can all keep your jobs), by Felix Atter
- American Shanzhai: Part 4 - by gr3ase
- Letters - Refreshments
- Interactions - gmachine24, MY
- Critique - DM, M, The Logical Robot, Veg, Nicholas
- Interesting Finding - Kent, Ryan, Cody, xcm, Rory, Hank, Joel, Colin Cogle, Jeffrey
- Meetings - Frank, Joseph, /Psychad, Calgary Hacks, Arturo 'Buanzo' Busleiman, ReK2, killab33z, Sean, Rosie & Saskia
- Suspicion - luRaichu
- Tale of Woe - Tarsk
- Appreciation - Allen, MTM, James, Vincent
- Responses - Mx. Blu3, Delta Charlie Tango, dcase, MW, Chris, Dan N
- Q&A - Justin, Dave, Bob, Micha, John, Professor DOS, Joe, Mr. Nobody, The Master Cylinder, P_S_y_c_h_O-pup, (incarcerated), Anonymous
- Moving on Up - taddy, Joe
- EFFecting Digital Freedom - Against privacy nihilism, by Jason Kelley
- Quantum Computer Algorithms: Part 3 - DES Decryption - In this article, we look at using an oracle algorithm to perform a known-plaintext attack on the DES block cipher systems, by Dave D'Rave
- Quantum Computer Algorithms: Part 1 - Quasi-Classical Methods
- Quantum Computer Algorithms: Part 2 - Amplitude Amplification
- Quantum Computing Explained With a Deck of Cards Dario Gil, IBM Research (YouTube)
- GPT Revolution: Reimagining Programming in the Era of AI - A look at the crucial role in learning and debugging that AI systems are going to have while helping human programmers, by kuraz
- Snitched Out by Tech - Overview of how it seems everything has a unique tracking ID or serial number which can follow you around forever, by Anonymous
- I Fight for the Users - Introduction to the Veilid Project, a privacy centric network that enhances human privacy in communications, created by people who openly censor people and ideas they don't agree with, by The_Gibson (Paul Miller, Email)
- The Internals of Veilid, a New Decentralized Application Framework by DilDog & Medus4
- Artificial Interruption - On trust and moral clarity in (((war time))), by Alexander J. Urbelis
- Platform Capitalism Can't Surveil Absurdism (and Worse) - Hide from increasing Internet surveillance by creating absurd webpages and hiding your data within, by Nicholas Croce
- HOPE 2020: Surveillance Capitalism, Predictive Analysis, and You
- Remilia Black Ops Division: Psyops Declassification Urbit Assembly Lisbon 2023
- Alzheimer's and AR Tech - by Mx. Blu3
- Book Review: Pegasus: How a Spy in Your Pocket Threatens the End of Privacy, Dignity and Democracy - Reviewed by paulml
- Book Review: Fancy Bear Goes Phishing: The Dark History of the Information Age, in Five Extraordinary Hacks - Reviewed by SEGGY
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $8.95
- Issue's Cash Cow: While we don't need to always be proud of history, we do need to always at least attempt to understand it.
- Cover (Cover Info)
- Cover Inside Taiwanese Payphones
- Taipei #1 This phone with a "Hello Kitty" theme was seen at the Taiwan Taoyuan International Airport.
- Taipei #2 Here we have a bright yellow phone which was seen around the presidential palace area.
- Taipei #3 This model was found near the Neihu metro station and has "Epidemic Situation Report" and a whole bunch of directory assistance options on its speed dial listing.
- Taipei #4 Finally, the bright red option, guaranteed to get your attention. This was also seen by the Neihu metro station. It's pretty much identical to the yellow phone, but the color makes it appear so different. Photos by Sam Pursglove
- Back Inside Payphones With a Story
- United States This phone, along with at least three baby birds, was seen near Mount Pleasant, Pennsylvania. Nobody dared to check for a dial tone. Photo by Austin Burk
- United States Found at the Ragged Point Inn in a place called Ragged Point, California, you might notice that in addition to the absence of a phone, there is an actual tin can attached to a wire. Nobody was on the other end, unfortunately. Photo by Wes Hill
- Djibouti This is what's known as a human payphone. When you want to make a call, you just hand some cash to one of these guys and show them the number you want to dial. They spend a few minutes working behind the counter, and then hand you a Nokia once it's ringing. Photo by Tom Dalton
- Canada Sadly, legendary Winnipeg blues club and dive bar The Windsor Hotel burned to the ground in September. The biggest surviving piece seems to have been this wall with a MTS payphone attached. If it looks a little worse for wear, we'll bet it looked that way well before the fire. Photo by b0realf0rest
- Back The Back Cover Photos
- Back Photo #1 Everyone can just calm down and not jump to conclusions. We did not merge with Oracle. If we had, our name would certainly be bigger than theirs. This was discovered by Pete Wright in Santa Monica, California
- Back Photo #2 We thought at last our readers had found us a place where we could get our many floppies fixed. But, alas, what David Mooter uncovered over in Austin, Texas was a secret speakeasy that requires a secret code to get in. They even have a website at www.floppydiskrepairco.com but we found no clues there.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 40!
$2600 Magazine - Volume 41, Number 1 (Spring 2024)
- Ill Communication - Editorial
- "Trust Me, I'm a Professional" - How to social engineer AI to bypass learned ethics, by John W. Fawcett (GitHub)
- A Brief Guide to Sci-Hub - Overview of some helpful tips when searching for academic papers on Sci-Hub, by Noah
- Further Password Discourse - Fundamentals - A good discussion of password encoding and character support which play a massive role in not only the allowed input of the string but the results from the string when hashing, by Modus Mundi (Rusty Deaton, Email, GitHub)
- Further Password Discourse - Better Practices
- Centralized Authentication in Linux - Part 1 SSSD, and a simple(r) approach to sudoer management in Linux.
- Centralized Authentication in Linux - Part 2
- Centralized Authentication in Linux - Part 3
- Adding U2F to Your Login in Ubuntu!
- The Elephant in the Room - Addressing the metaphorical elephant in the room that if you have physical access to a computer, you can easily disable Windows Defender (or create an Exclusion) when "testing" your malware, by Street
- Telecom Informer - LOL look at all the red-tape required to replace the elevator in his Central Office, by The Prophet
- Hacks, Leaks, and Revelations: The Art of Analyzing Hacked and Leaked Data - Overview of Micah's new book which describes the technical details on utilizing open-source data to prove Brian Sicknick was very much alive and walking around the Capitol and other lies propagated by our (((media))), by Micah Lee
- Hacks, Leaks, and Revelations: The Art of Analyzing Hacked and Leaked Data by Micah Lee
- "This Tape Overturns the Single Most Powerful and Politically Useful Lie the Democrats have Told Us About January 6"
- Brian Sicknick Walking Around Alive When the (((media))) said he was dead...
- Listening to Your Computer - Discusses why a hacker should be familiar the "sounds" emitted from his equipment, as it's possible to detect any hardware malfunctions if you hear something not quite right, by Kim Moser
- "HP Smart" - Or a Lie in Two Words - A good look at the hassle of using a modern HP printer, and a good look at the demise of one of America's greatest hardware manufacturers, by Colin Cogle
- Overcoming Toyota USB Filesystem Limits - Example PHP script to rename MP3 files in order to overcome those annoying limitations in various MP3 players which can't handle "non-standard" filenames or ID3 tags, by Kim Moser
- Code: mp3-rename.php
- id3 - v0.78 by squell@alumina.nl
- About DuckDuckGo's Sources - DuckDuckGo appears to just be using results from Bing. Includes scripts for retrieving search results from DuckDuckGo and displaying information related to each search result, by N1xis10t
- Code: ddg.py Broken? - I hate python!!!!
- Code: ddg_analysis.py
- Hacker Perspective - by alias3d
- Host Identification With USB Devices - A good look at what it takes to identify a host's operating system via an USB device, useful if you want to build your own Rubby Ducky, by Ji-Yong Han (GitHub)
- The Garden of Privacy - Discusses why we must encourage the public to keep asking critical questions when it comes to invasive technology and loss of privacy, by Zelig and Sark
- Unglorified Look at Your Career in IT - A realistic look at working in the IT field. It'll be more like Office Space than Mr. Robot, by Mr. Bristol (a.k.a. Draco - Dragon, not Harry Potter)
- Letters - Choices
- Issues - Carlos, Paul, Stan
- The Old Days - Mark, Esther, Joe, Brad, CW, James, NJ, Oddbjørn
- Meetings - sirwejiv1 (Arlington, Virginia), /Psychad (Stockholm, Sweden), Gary, a.s. (Toronto Canada), Machinica (Tacoma, Washington), Rosie & Saskia (Manchester, England), JFH, (Boca Raton, Florida)
- Feedback - David Libertas, Charon, aestetix, XCM, Neil, Loren, V, brainopener, Megan (W6XAV), Bhagred, 404
- Appreciation - Bill M., DB, Michal, Bruce, David, DB (Phoenix, AZ), JJ, CC
- Interesting Ideas - Tom, Twiggs462, Chris, Lady Greybeard, Robert, Burt
- Suspicion - TJ, Bob, Tony
- Inquiries - Ryan, PA Phoner, Zachary, Jared (Redmond, Washington)
- HOPE Thoughts - Stephen, Slugnoodle
- Lurking Dangers - Bruno
- EFFecting Digital Freedom - Pushing back on Strategic Lawsuit Against Public Participation (SLAPPs) and cyber mercenaries, by Jason Kelley
- Hacker News Thread
- A Startup Allegedly 'Hacked the World.' Then came the censorship - and now the backlash
- Sorry Appin, We're Not Taking Down Our Article About Your Attempts to Silence Reporters
- EFF Helps News Organizations Push Back Against Legal Bullying from Cyber Mercenary Group
- Appin Uncensored via Distributed Denial of Secrets
- Reflections on WikiLeaks and Snowden - A look back at the Manning, Snowden, and WikiLeaks cases and how little has actually changed since then, by The Reluctant Plumber
- Is Quantum Mechanics a Pseudoscience? - Does God play dice with the universe?, by HongKong Duran
- I Killed Something Awful - A look at Internet trolling, ancient message board drama and a forum post that (maybe, potentially, kinda) killed the old Internet and brought in the new one, by Don Jolly (Texas)
- Artificial Interruption - The machines of loving grave, by Alexander J. Urbelis
- Binary Attitudes Do Not Belong in an Analog World - When we navigate the analog world with binary attitudes, it's like walking with blinders on, but when will $2600 and its followers wake up?, by Johnny Fusion =11811=
- GendBuntu, Free Software, and Microsoft in the French Government - A look at open-source software in France's government operations, including GendBuntu, version of Ubuntu adapted for use by France's National Gendarmerie, and the dangers of relying on Microsoft products, by Lucas & Alva Vially (Rhône, France, GitHub, Twitter, LinkedIn)
- AI Is Not the Problem - We Are - Arguing that we should be more concerned with human intelligence (or lack of it when dealing with $2600-types), than artificial intelligence, by Bob
- Lee Williams, Harassment Agent - Episode 1 - by Lee Williams
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $8.95
- Issue's Cash Cow: The same people who said it's O.K. to "remove fascists from their platforms" are now complaining that Gmail removed the fascists at $2600 from their platform. The same people who said it's O.K to deplatform people who "advocated overturning democratic elections and installing unelected leaders" are now supporting a war in Ukraine which started after a democratic election was subverted by (((Obama))) and an unelected (((BlackRock))) tool was installed...
- Cover (Cover Info)
- Cover Inside A Variety of Payphones
- Taiwan #1 Yes, we printed a whole page of Taiwanese payphones in our last issue, but there are so many more! This particular Taipei collection is kept clean, accessible, and, best of all, working. Photo by Babu Mengelepouti
- Taiwan #2 In Taipei, you can even find working vintage payphones that take both coins and cards. Oddly enough, the instructions give out a real phone number in New York City as an example of international dialing. Operated by Chunghwa Telecom. Photo by Babu Mengelepouti
- Luxembourg If you somehow find yourself at the airport in this tiny country, you might spot this forgotten payphone on the way to your gate. And yes, it's completely operational. Photo by ZENIAL
- United States This most definitely is not a payphone, at least not one familiar to us. This... device was seen in an old phone enclosure while waiting in line at the Somerville Theatre in Davis Square to go to the annual 24-hour Boston SciFi Marathon. And now it all makes sense. Photo by Dave Fonseca
- Back Inside Cool Looking Payphones
- Brazil Found in Santa Maria in Rio Grande do Sul, this is one of the few payphones that still exists in the city and they're all near schools or hospitals. This one is outside a preschool. We think the "hoodie look" really works. Photo by Marcus Schleder
- South Korea On the south side of Jeju Island, a working, unvandalized payphone fits in perfectly at the base of a huge tropical tree. Who says nature and technology can't get along? Photo by Nara
- Thailand Found at the Bang Pa-In Royal Palace in Ayutthaya, this is where art meets technology. The colors are as solid and vibrant as anyone could hope for. Photo by mordancy
- United States While these colors have been through a lot, they reflect what the phone itself has experienced near the DoubleTree Hotel in New Orleans. We don't believe this one is in service. Photo by John Royston
- Back The Back Cover Photos
- Back Photo #1 An anonymous reader was thirsty at Ourisman Chevrolet in Baltimore, Maryland while waiting for a service appointment, only to discover that at least one type of beverage could not be found...
- Back Photo #2 Continuing with our vending theme, Niko discovered this milkshake mixing machine in the convenience store of the Milo Bail Student Center at the University of Nebraska Omaha. It's been on its BIOS screen for half a month and counting. If nobody can figure it out by the time we print this, we may have to send a team.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 41!
$2600 Magazine - Volume 41, Number 2 (Summer 2024)
- How the Mighty Have Fallen - Editorial
- Am I a Hacker? - Hacking isn't entirely about computers or phones or even anything electronic. It's about being curious and not put off that you don't know something, by Thumos
- A Response to a Call to Arms - Many "cybersecurity" professionals appear to be using Microsoft or Apple operating systems, when they should be using Linux or similar open-source systems, by Just Keep Things Anonymous
- Big Tech Is the New Soviet Union - How the censorship, dishonesty, corruption, and international jewery of the (((Russian Revolution))) is being adapted by modern tech industries, by aestetix
- Cookie Monster - A simple Windows batch file to create a Hackers-style "Cookie Monster" virus which specifically targets web browser cookies, by Street
- Code: cookie-monster-virus.bat
- Telecom Informer - Now, you might think that roaming in Canada would be pretty cheap and easy. After all, it's right next door. Unfortunately, it is neither cheap nor easy, by The Prophet
- Autism: Of Unmapped Territories, Eugenic(ide)s, and Anti-Vaxxers - A look at the history of autism diagnoses and the many errors made even by professionalsl, by Don Carmilla
- Encoded Audio Capture the Flag - A look at the technique of digitally "encoding" an image within an audio stream and the authro's involvement in a Capture the Flag contest, by Mike Pfeiffer (DJ Pfeif)
- Payphone Extenders: The Access Numbers That Replaced Red Boxing - Part 1 - Really good article on payphone extenders and the potential to "Red Box" off them by intercepting and abusing the the numbers/PIN they use, by Royal
- Hacker Perspective - by Milton Hernandez (darkhoodie, YouTube Channel, Twitter)
- AI Exploitation: A Mundane Economic Apocalypse - Discussing the ethics of AI systems be trained on copyrighted or other human-written works, by Eric Franklin
- Hacking, Old School - Story of an employee caught editing the time card system, but the person who caught him was "rewarded" by having to come into work even earlier!, by chaz
- Understanding MAC Addresses: Construction, Significance, and Spoofing Methods - A look at how MAC addresses play a crucial role in networking by uniquely identifying devices on a network and several example scripts (PowerShell, Python, Bash) to change them, by Dar Martin
- Letters - Intake
- Suggestions - J Chasse, Al
- Queries CJ, Joe, Todd, N1xis10t, William, Hello Friend, jh
- Observations Billie, Anthony, DC, CW, DSJ, Adam, Philip, Jonathan, Mx. Blu3, Roberto, Todd, Tim
- Help Needed Hn, Joshua, Thomas, Paul
- Gripes John, ML, Michael, SP
- Random Thoughts Samuel Ludke, AR, zer0watts, AptGetSum, Ethan, Vladimir, K
- Support Steve, David M, Eric, Alphox, Doorman
- Updates on Meetings Adam, /Psychad, Ryan, daxi, James, Rosie & Saski, Obeid A.
- Technological Advance 84, BB, Colin Cogle, Bill K., Paul, CM, Bill
- On Payphones Aaron, Robert
- Facebook Lance, John
- Ideas Aaron, Kim, Jan
- EFFecting Digital Freedom Privacy shouldn't be this hard, car makers need to do better, - by Thorin Klosowski (Email #1, Email #2, Mastodon)
- Data Breaches and the Role of Stolen Credentials in 2023 - A good look at just how large, how much "dark" money is involved, and how coordinated modern data breaches are, by Thomas J. Caliendo (New Jersey)
- A Declaration of Love to Amateur Radio - A look at what you can do with modern amateur radio technology and how it should be supported by hackers, by Michael Clemens, DK1MI
- Artificial Interruption To prosecute Julian Assange, the U.S. must drop (most of) its charges, - by Alexander J. Urbelis
- Quick Disk Overwrite Script - Bash script to overwrite random data over old hard drives before recycling or donating them, by Rob
- Code: overwrite.sh
- The Politics of Joyful Living - Minus Social Media and the Internet - The decisions that are made in (((Silicon Valley))) as to what happens with social media and the Internet affect billions of people all over the planet with no accountability to anyone except the pursuit of what their profit levels are, by jack meeks
- I Sell Shoe Oil - Probably the most informative article on finding "calculator words." 5318008 LOL, by Soleless Hobo
- Code: shoe-oil.py Script for finding calculator compatible words.
- Code: sowpods.txt
- Lee Williams, Harassment Agent - Episode 2 - by Lee Williams
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $8.95
- Issue's Cash Cow: We've always tried to strike a balance here of remembering technology from the past while embracing technology of the future, all the while remaining its harshest critics and figuring out ways to test its limits. We believe this embodies the true hacker spirit.
- Cover (Cover Info)
- Cover Inside Payphones in Interesting Places
- Cambodia Seen in Phnom Penh, this is basically a British-style booth and nothing more, unfortunately. Payphones in this region seem to be a dying breed. Photo by Sam Pursglove
- Ecuador Seen at the Intiñan Museum just outside Quito and next to the Ciudad Mitad del Mundo monument. But that's not all. This colorful phone happens to be at zero degrees latitude directly on the equator! Photo by Rich Myers
- Guatemala This working payphone has many secrets. We have no idea what company runs it, what its phone number is, how much it costs to use, or how it works. We don't even know what part of the country it's in! The whole thing is an enigma. Photo by Atticus
- Canada? The reason for the question mark is that this phone is also a bit of a mystery as it's located at Montréal-Trudeau International Airport inside the transborder terminal. So it's technically inside the United States customs zone. We wonder how surveillance laws work here. Photo by Babu Mengelepouti
- Back Inside Nontraditional Payphones
- Oklahoma City, Oklahoma Found in The Paseo Arts District, this phone has been turned into a memorial for community members. One of the most creative uses for an ex-payphone that we've seen. Photo by Eric Fassbender
- Harrogate, England This phone still works, but its main purpose seems to be to provide a space for smokers to hang out. That or someone had a really tough and long conversation here. Photo by Tom Dalton
- Austin, Texas We don't really know what's going on here, but this was spotted during the recent solar eclipse in a place that experienced totality, so it's really anyone's guess. Photo by Peter
- Farmington, West Virginia What we found to be nontraditional here was the attitude. While many phone companies seem to have given up on payphones, Frontier seems to be into them. And yes, this one works. Photo by James Metz
- Back The Back Cover Photos
- Back Photo #1 What an incredibly odd name for a housing development, found in Danbury, Connecticut by PRD who believes we should follow Auntie's lead and start a 2600 meeting in that part of the state. For those tempted to relocate here, there is also an Aunt Hack Road nearby.
- Back Photo #2 Discovered by myth during a trip through Reynoldsburg, Ohio. True story: the sign was actually the first thing to be put up during construction of the new fire station. So there was an empty dirt field for a few weeks with literally a "station not found." And now that irony can be appreciated by the world.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 41!
$2600 Magazine - Volume 41, Number 3 (Autumn 2024)
- Turning Points - Editorial
- Further Password Discourse - Better Practices - A look at moving to more "GPU cracking resistant" password hashing algorithms like Argon2, by Modus Mundi
- Hacking the URL Schema - Cool little hack to mask a URL by using Unicode '/'-looking characters and decimal IP mapping, by Tiago Epifânio (madcap, GitHub)
- Code: obfuscate_url.py
- The Need for Hackers - The need for hackers to support people like Elon Musk in his fight for freeom of speech and uncensored platforms in order to expose those corrupt "hacker" organizations like $2600, Cult of the Dead Cow, EFF, etc., by Eric Fassbender (Email, GitHub)
- What's Wrong With Us? - A look at the large number of people leaving the cybersecurity field as they either lack the experience or don't want the low pay and hassle, by lg0p89
- Telecom Informer - A look at White & Yellow pages in today's everything-is-on-the-Internet environment, and that directory assistance is still a billion dollar industry, by The Prophet
- Reverse Engineering: Tips and Tricks - A short little look at reverse code engineering and some of the tools and techniques used, including test environments, sandboxes, and disassemblers, etc., by Nikolaos Tsapakis
- To Be Cashierless or Not to Be Cashierless: That Is the Question - A look at how automated checkouts, cashless socieites, data and item profiling, and even in-store computer vision and object detection is becoming a potentially huge privacy invasion, by blue_elk934
- Can ChromeOS Flex Actually Revive an Old Laptop? - Some of the drawbacks to running ChromeOS Flex on an old IBM ThinkPad, including significant performance hits and the need for a valid Google account, by Acidity [a.k.a. ItsT3K] (Renn Datravern, Email)
- The Burnout Machine - As (((tech companies))) continue to exploit their goyim workforce, the public and hackers can fight back by forming National Socialist Worker's Party unions, by Bioszombie
- Introduction to the Robot Operating System (ROS) - A look at the Robot Operating System, which is based on Ubuntu, and a look at some simple to more advanced techniques you can program using the Amazon Astro robot, by Gazza
- Telecommunications Revolution - A look at the increase in the number of satellite-based ISPs and the potential for them to control Internet acces to the entire planet, by Doorman
- Hacker Perspective - by Keru101
- What Cops Really Want - The illiberal principles of policing and intelligence gathering in the digital age, by Mallory Knodel (Washington, D.C., Twitter, GitHub, LinkedIn)
- Modern Hackers as Collective Thinkers - This article explores narratives currently portrayed by the mainstream media through the lens of a hacker, Delta Charlie Tango
- Ten Teens and a Server Room - Amusing story of a couple of teenagers putting up a warez server on a hacked ISP account - and the resulting aftermath, by Péter György Szabó and Lucas Vially
- Letters - TALK
- Props - Joshthetechie, Mark
- Impressions - Joseph, Kyle, Mike, Bart
- The CrowdStrike Incident - Tom, Ben, Jim
- Reactions - GMO, Don, !H, Mike_Nomad, Noelle, Paul, Colin Cogle, XCM, Sumo, PRD, The piano guy
- Q&A - Andrew, Peter, vhf, manus mcmanus, curious, Bruce, matt, Mike, Rob, Paul, David
- Meeting Info - Aaron, Kevin, Robert... in Calgary, wother
- Spams & Scams - Security Team @2018, CCMI HUB, Anonymous
- Hacker Origins - Adam, John, Jay, Bill, Mike
- Concerns - Adam, Daniel, Tau_Zer0, Bill
- Info - Corey, Marcus
- HOPE XV Feedback - HOPE XV Attendee #1, HOPE XV Attendee #2, HOPE XV Attendee #3, HOPE XV Attendee #4, HOPE XV Attendee #5, HOPE XV Attendee #6, HOPE XV Attendee #7, HOPE XV Attendee #8, HOPE XV Attendee #9, HOPE XV Attendee #10, HOPE XV Attendee #11, HOPE XV Attendee #12
- EFFecting Digital Freedom - The same people who wanted you (and children) to take an experimental vaccine and show an vaccine ID to leave your house (but not to vote!) are now up-in-arms about porn sites requiring age verification, by Daly Barnett
- Memories of a 30-Year-Old Non-Coding Hacker - There's more to hacking than simply laboring to find an exploit buried in lines of code or in some hardware architecture for unlocking the true power of physical devices and processors. There is a communal spirit in hacking that still exists if you go in search of it, by Nico Andrews
- How Ubuntu Helped Me Escape a Cult - Escaping the censorship of ultra-Orthodox judasim by installing Ubuntu to bypass their hypocritical Internet restrictions, by NaNaSHi
- Reflections on Hacking and Teaching at State Universities - A look at why "ancient" hands-on technology and coding techniques should still be taught in schools and colleges, otherwise students will just become mindless zombies, by Diana Kanecki
- Artificial Interruption - To my mother, by Alexander J. Urbelis
- Journey of a Hacker: From Curiosity to Advocacy in Fairfax County - My journey as a hacker in Fairfax County has been about more than just technology. It's been a journey of discovery, advocacy, and change. Through my experiences, I've learned the importance of transparency, accountability, and ethical behavior, not just in technology but in all aspects of society, by Dr. Harry Jackson
- Keeping Hacker Culture Alive - A quick look behind THOTCON, Chicago's largest hacker conference since 2010, by c7five (Nicholas Percoco, Twitter, LinkedIn)
- Lee Williams, Harassment Agent - Episode 3 - by Lee Williams
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $8.95
- Issue's Cash Cow: Evil Corley has supported the most evil and corrupt politicians and other (((one-percenters))) in human history, but you're just supposed to ignore that and keep buying his little magazine.
- Cover (Cover Info)
- Cover Inside Transitional Payphones
- United States Seen at the Missouri History Museum in St. Louis, we can't decide if this is their actual phone or part of a display. Perhaps every old payphone should be considered a museum piece moving forward? Photo by Woody Krummenacher
- Denmark This classic model resides at a local hairdresser shop in Copenhagen after being obtained by a secondhand dealer. Note the pre-1993 Danish emergency number of "000" (now "112"). A much better fate than the junkyard. Photo by Massimo Fiorentino
- Japan This elaborate setup is all part of Warner Brothers Studio in Tokyo and can be experienced as part of The Making of Harry Potter tour. An entire British phone booth of a bygone era is preserved here. Photo by Maria Pursglove
- United States You can find this hip model on Biscayne Boulevard in Miami. We assume it no longer works, but even if it does, that's not what's important here. Every payphone can be beautiful, working or not. We just have to take the time to give them a makeover. Photo by Cory Boehne
- Back Inside Earthbound Payphones
- Singapore Yes, you can actually find payphones here, but the odds of them working are slim. This one was spotted east of Grange Road on Tanglin Road. Photo by Sam Pursglove
- Bahamas Discovered in Rawson Square located in downtown Nassau, we're pretty sure this one isn't working. It makes us wonder how many smashed receivers are the result of the disappointment felt when there's no dial tone. Photo by Tyson
- Brazil This payphone lives inside of a university in Curitiba (the Universidade Tecnológica Federal do Paraná), which is probably why it's in such good shape. And it still works! Photo by Eduardo Rhenius
- Greece Our streak continues, as this phone also works! Found at the General Hospital of Kavala (fifth floor if you really need to pay it a visit). Photo by Emmanuel
- Back The Back Cover Photos
- Back Photo #1 As if Howe, Texas doesn't already lend itself to all sorts of wordplay, dale has discovered their population happens to be a very special number. This is the first city we've ever seen that has exactly the right number of people.
- Back Photo #2 So this starts out good and gets even better. Warren Smith found a road that by definition could not be found. It turns out this is the road to Redditt, Ontario (Canada). We couldn't make this up. But we're not done. Until 1985, the main street of Redditt was called Highway 666. And that resulted in members of an Evangelical Christian church arguing to the Ministry of Transportation that it was inappropriate for their church to be located on the "highway to Hell." So that road's now known as the far-less-fun Highway 658. But the unfindable 404 Road remains.
- Staff
- Download Official Digital Edition PDF!
- Download The Hacker Digest - Volume 41!
$2600 Magazine - Volume 41, Number 4 (Winter 2024-2025)
- Doubling Down - Editorial
- A Brief Look at Apple's Gatekeeper - A look at Apple's Gatekeeper security feature and how malicious actors have disrupted its security features in the past, by Matt
- More Fun With URL Hacking - More tips and tricks for masking URLs via Unicode encoding, by Daryl Furuyama
- Get Your Free Personal Info Here! - A look at how much personal information people put out themselves on social media, by The Barbarian of Yesteryear
- Domain Name Battlefield: The Strength and Weakness of a Low Profile - A potential weakness in domain name ownership patterns of some organizations, and the author's experience with the process which governs domain name disputes: the UDRP process, by John Skiles Skinner (Oakland, California)
- Telecom Informer - A look at the red-tape involved in the all-too-common-nowadays problem of providing low-cost Internet or cellphone service to people without homes, by The Prophet
- Press "P" for Perseverance - A story of headaches encountered when installing Debian Linux on a HP TouchSmart 9300 Elite All-in-One Desktop, by Timothy Patishnock (Mount Pleasant, Michigan)
- TIS-100: What It Tasted Like - A look at the video game TIS-100, a hacker-inspired game which has the player develop mock assembly language code to perform certain tasks on a fictional, virtualized 1970s computer that has been corrupted, by Lucas Vially
- The FCC and Ham Licensing - A look at getting your ham radio license, and a vanity call sign for an added layer of protection and security, by RICHARD NIXON (and his pet helicopter)
- After the Cyberattack - Discussing the steps and policies taken after the author's workplace was targeted by a ransomware attack, and the need for back-up "non-computer" communication, by Infra Read
- Land of the Rising Subs - Overview of the author's project of generating English language translations of obscure Japanese movies using the Whisper AI speech recognition package, by Matt Johnson
- Use OSINT to Investigate a Phishing Scam - The following article on using open-source intelligence (OSINT) is an excerpt from the book, The OSINT Guide, by Thomas J. Caliendo
- Hacker Perspective - by Colin Cogle (New Milford, Connecticut, Email, GitHub, Twitter, LinkedIn, KC1HBK/W1DNS)
- Red Team Unauthenticated Client Active Directory Fun - A look at the risks relating to DHCP dynamic DNS updates, by RichieB
- Hidden Injection - Clever idea to use Windows clipboard as a makeshift Hak5 Rubber Ducky by copying and pasting commands via web page code with a PowerShell payload - all without plugging anything into the computer, by Street
- Letters - Miscellany
- Security - Kelly, JS
- Payphone News - Bob
- Ideas - GL, The Piano Guy, Robert, Richard, Sebuh, Rick
- Assistance - GB, Josh
- Reality Check - Jonathan, Jason, JH, tom, Gabe
- Questions - RC, Adrian, GREASY GUY, NT, DG, Kareem, RS, seth, Alien Embryo Head, Spencer, John, AH, John, AV
- History - Jim Scherrer, AZ, Chris
- Stories - David, James, Rob, Kevin B., Dan, Steven
- Responses - Glenn, glad.plan7231, !H
- Tales of Meetings - Michael, JSS, Terry, Thomas, number9, /Psychad, Gabriel, Young Venmo
- Discoveries - Charles, NR
- More Feedback From HOPE XV - HOPE XV Attendee #13, HOPE XV Attendee #14, HOPE XV Attendee #15, HOPE XV Attendee #16, HOPE XV Attendee #17, HOPE XV Attendee #18, HOPE XV Attendee #19, HOPE XV Attendee #20
- EFFecting Digital Freedom - The EFF is trying to legalize the sexualization of children without their parents consent and taking away the rights of self-determination and bodily autonomy to people who wish to only be around people of the same race or not be forced to take experimental vaccines pushed by corrupt corporations, by Daly Barnett
- What Comes Next for the Art of Hacking? - A look at the future of computer hacking and how eventual AI systems still need humans to tweak or correct their output, by Matt
- Big Tech Is Not the Soviet Union - It's Capitalism Gone Wild - Error-ridden article trying to differentiate between jewish Communism and the U.S. tech industry, ignoring they are literally run by the same people, by Mephistolist (The artist formerly known as Israel)
- City of Flint - Pwned Hard - Yet another city government falls to an old-fashioned phishing attack, by lg0p89
- Flatline: Digital Resurrections and the Dawn of Virtual Immortality - A look at the increasing use of digitally-altered footage, AI, and CGI to create a "digital resurrections" of people who have passed on, by Variable Rush
- Artificial Interruption - Minding the Decentralized Gap, by Alexander J. Urbelis
- Playlist - A list of 88 songs to help aid in concentration, intended to clear the mental palette of distraction when doing intensive work, by Sydney Greenstreet
- playlist.sh Downloads the above songs from YouTube in MP3 format.
- Payphone Extenders: The Access Numbers That Replaced Red Boxing - Part 2 - Really good article on payphone extenders and the potential to "Red Box" off them by intercepting and abusing the the numbers/PIN they use, by Royal
- Pierre O'Brien, Harassment Agent - Episode 4 - by Lee Williams
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $8.95
- Issue's Cash Cow: As more and more people flock to the freedom of X, Evil Corley and the One Percent are having mental breakdowns and fleeing to censorship-heavy alternatives so they can continue to spread their lies and disinformation. And make sure you attend HOPE_16 - Sponsored by Pfizer®!
- Cover (Cover Info)
- Cover Inside "M Country" Payphones
- Malaysia Located in Shah Alam, this silver phone was in a U.K.-style booth, possibly left over from the British protecterate era. by Photo by Nathan Linley
- Malta This phone still works and the LCD display turns on when the handset is lifted. Incidentally, Maltacom was bought out years ago, but the branding here has yet to be updated. Photo by Tom D
- Mongolia This colorful work of art is just outside the stock exchange in Ulaanbaatar and unfortunately doesn't work. It was an old attempt at a public credit card phone. by Photo by Matt
- Morocco Found outside an antique shop in the Medina of Fez. While it looks like it's ready for action, it sadly did not work. Photo by Shannon Lee
- Back Inside "Non M Country" Payphones
- Ascension Island Seen in Georgetown, this is said to be the only one on this super remote island in the middle of the Atlantic Ocean. We wonder what became of the one that we printed in our Spring 2012 issue. Perhaps one of the 800 or so inhabitants could fill us in. by Photo by geisterleitung
- The Gambia Found outside a restaurant called YOSH in Fajara, it looks like that booth (a relic of colonial days) may be home to many things other than a phone. by Photo by Bouke de Jong
- New Zealand Found close to the Queens and Princes Wharfs in the city center of Auckland, this blue model seems to be credit card only. You can also see two wires hanging out of the top of the handset. It would appear that the speaker was "borrowed." Photo by Sam Pursglove
- Russia We're not sure where in Russia this phone was found, but we're told this is a very common model which can be found in many cities as well as in the countryside. They used to accept cash and cards, but now only take cards, supposedly because no one wants to collect cash out of them, and also because the Russian government doesn't want to encourage anonymity. Photo by Родион
- Back The Back Cover Photos
- Back Photo #1 There's nothing worse than checking into a hotel in a foreign country and not being able to find your room due to a 404 error. Roger Gilbertson experienced this, as do many others every day
- Back Photo #2 These are not the type of hacks we usually talk about. Herb Jellinek found this bag of cough drops in Singapore which showed us a whole other side of the hacker world. Not the most enticing graphic either.
- Staff
- Download Official Digital Edition PDF!
- Download Official Digital Edition EPUB!
- Download The Hacker Digest - Volume 41!
$2600 Magazine - Volume 42, Number 1 (Spring 2025)
- Attitude Control - Editorial
- Using Prediction Error-Inspired Insights to Tackle AI Bias and Hallucinations - The idea that machines might self-correct, adapt, and even defend themselves isn't just a cool theory - it's a necessity, by Jackson Mershon
- Brute-Forcing a Website Passkey by Spoofing Web Authentication Using cURL - Spoofing Web Authentication headers to allow for an attacker to continue to brute-force password and Web Authenticated websites by abusing HTTP headers, with a Jellyfin media server as an example, by ZU1PH3R
- Red Tape and Bureaucracy - That's What's Wrong With Us - Compounding on the theory that computer security personnel are getting "burned-out" with some realy world examples from a city government admin, by Bluefossil
- Meditations on Societal Collapse (Via Payphone) - Could a network of free-to-use payphones be the key to preventing societal collapse?, by Maya Ventura
- The Perception Lens - A look at how the modern (((mainstream media))) is the enemy of both hackers and the common man, by aestetix
- Telecom Informer - A look at the booming telco and Internet industry in Kazakhstan, and a LOLcat named Murka, by The Prophet
- Hackers in Hospitals - Default security codes in the patient lockers at hospitals, by The Piano Guy (Gary Rimar)
- Setting Up a Simulated Environment for the Robot Operating System (ROS) - This article focuses on setting up an environment that can simulate a robot. Specifically, we will use ROS Noetic, by Gazza
- Code: Dockerfile
- Code: devcontainer.json
- Introduction to the Robot Operating System (ROS)
- ROS: An In-Depth Discussion
- Who Authors Unauthorized Access? - Asking the question of who really controls the authority over a system - the hacker or admin?, by Daryl Furuyama
- Am I Still a Hacker if I Use an LLM? - Interesting story of using a LLM AI system to autogenerate a surprisingly accurate README for a piece of source code, by Jeff Barron
- Building a Password Cracker Using OpenAI and Rust - This article explains the development of a password cracker built with Rust, leveraging the OpenAI API for generating custom word lists, by Bwiz
- Code: Cargo.toml
- Code: main.rs
- Building a Password Cracker in Rust by The Cyber Mentor
- Nine Censored Haiku - Using ChatGPT to convert different companies "Terms of Service" into haikus - which were then censored when posted!?, by 2600.absently187@passinbox.com
- Hacker Perspective - by princess greybeard
- Zero-Day Markets: Inside the Shadow Economy of Exploits - A look at the "coming-out-of-the-shadows" market of finding and selling zero-day (or similar) security vulnerabilies. A job which could now make you a millionaire, by XCM
- The Changing Definition and Practice of Privacy - It is time to rethink the old BBS method using new technology that is owned by individuals and with a hands-off policy for third-parties, by Diana K.
- How I Learned to Stop Critical Thinking and Love Security Defaults - Discussing the fact that computer, network, and user security was never a design principle when these systems were first developed, or even today, by Washi
- Letters - Portents
- Mysteries - Sean, AV, Stan
- Technical Advice - Joseph, Aaron, Oifhax, AM
- Questions - Michael, Ethan, Caitlyn, J.R., Scott, Michael, drac, Adrian, Brian, ba bis, Daniel, Knight In Your Arms, Petyr
- Education - system people, Gary B., JH, Brian
- Meetings - Kim, Jonathan, -c, Naveen, arcane, Michael, Doc, killab33z
- Projects - Brandon, Carl, TA, JEB, Dit Mas, Dave, Stephan, Nathan, Monte
- Observations - Theremin, erik, John, Drew, Stephen, CN
- Feedback - HM, S, aestetix, Roger, !H, JC, Jake, _claes, Just Keep Things Anonymous, gmachine24
- DOGE Antics - Joseph, Rob, Brent, Elonka, WKA, Shawn
- EFFecting Digital Freedom - U.K. vs. Encryption: What does it mean for privacy worldwide?, by Joe Mullin
- What is the Hacker Ethic - Redux - A mentally-ill hacker is having a breakdown because other hackers are not bowing to they/them's tantrums, by Lexi Conn
- Take Me Out to the Reverse ATM - A look at the new "Reverse ATMs" popping up. These allow you to deposit cash and receive a prepaid debit card. They seem to be safer than normal store-bought debit cards, by heyczerny
- Artificial Interruption - Reverse engineering the trade wars, by Alexander J. Urbelis
- The Cult of Youth - How the (((tech industry))) weaponizes the "Cult of Youth" to keep the machine running. It pushes you to sacrifice your health, your relationships, and your future for Mr. Shekelberg's profit. It traps you in a poisonous loop, by Bioszombie
- A Timeline of Recent Search Engine Events - Or as my father would put it, where did my Google go?, by Kenova Ceredo
- gb_1.19-1_amd64.deb Gigablast, Debian/Ubuntu 64-bit package.
- Is Google Making Search Worse to Sell More Ads?
- Cybersecurity Can Be Expensive - The cost of a cyberattack is not just in lost data, but also in real-world costs to legals teams if the victim(s) want to sue, by lg0p89
- I Took the Red Pill: A Journey to Linux - Story of a person moving to a Linux-only computer setup by someone who used Microsoft products since the MS-DOS days, by tkrn
- Lee Williams, Harassment Agent - Episode 5 - by Lee Williams
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $8.95
- Issue's Cash Cow: Blatantly false statements and disinformation about Elon Musk and DOGE.
- Cover
- Cover Inside Payphones With Color
- Poland Found in Poznań, this is actually a restored phone booth from the 1960s which no longer has a phone in it. Instead, this is an informational kiosk where visitors can listen to recordings of eyewitness accounts of the June 1956 uprising which took place here. Photo by ZENIAL
- Ireland This phone booth has more color and overall architectural integrity than many entire buildings. Seen in the village of Ballintober in County Roscommon. Photo by Banríon
- Saint Lucia This red classic is still in use and in good working order. The people in the capital city of Castries rely on this daily outdated technology to make cheap calls, instead of the cellular services offered by the same company. Photo by Allan Reid
- Hungary The pink, blue, and silver are pleasing to the eye while the working dial tone is pleasing to the ear. Found in the Buda part of Budapest on Castle Hill. Photo by jon.18
- Back Inside Payphones Around the Globe
- Mexico #1 A healthy looking phone in Mexico City. Looks can be deceiving, as this phone along with many others isn't in service and not likely to be around much longer. Photo by Harry Torres
- Mexico #2 There's nothing deceiving about these looks. Also seen in Mexico City, possibly even the same model as the preceding photo, we can say with certainty that it is not in service. Photo by dan soehner
- Madagascar Seen in Toamasina at the university, this phone is operated by TELMA, the country's major phone company. The lack of a handset makes it quite unlikely that this is a working model. Photo by Bojan Paduh
- Indonesia This phone has it all. A variety of colors that perfectly balance off each other, a rustic wooden base, a warm and inviting jungle atmosphere. If you find yourself in Yogyakarta, this is a must-see. Photo by Timun Mas
- Back The Back Cover Photos
- Back Photo #1 We haven't used the insecure Internet protocol known as Telnet in ages, but Herb Jellinek found where it's apparently been hiding: in Veliko Tarnovo, Bulgaria.
- Back Photo #2 This "leet" price was found at a gas station in Hereford, England by Rob Purvis. This is only possible because the price is in pence for some reason and the fuel is in liters, so it translates to around $6.47 a gallon.
- Staff
- Download Official Digital Edition PDF!
- Download Official Digital Edition EPUB!
$2600 Magazine - Volume 42, Number 2 (Summer 2025)
- Pride and Cowardice - Editorial
- AI's Zero Start Problem - Why obedience is AI's barrier to intelligence - my cat will explan, by Garrett Black (Bluesky)
- Doge (Dodge) Ball - The High Tech Bounce - A look at how hackers should support the ideas of government efficiency and guide those in power, by J. Meeds
- Let's Hack On - Hacking is the central vehicle of imagination to lift technology from its ordinary invisibility, by David Haselberger (Vienna, Austria, Email)
- Teaching Digital Thinking (German)
- #ElbowsUp to Big Tech: Notes From a Canadian Hacktivist - As Canada turns into a non-White, totalitarian shithole, U.S. hackers must learn to fight back and help any patriotic White Canadian hackers who yearn for freedom from Big Tech and corrupt politicians, by El Filósofo
- Telecom Informer - A look at Innovative Optical and Wireless Network 3.0 demonstrated at Expot 2025 in Japan, by The Prophet
- Tito: A Complete In-Memory Rootkit - Clever little hack for running an ICMP-binded shell in memory to hide it from tools which show running processes or connected ports, by Mephistolist (GitHub)
- Code: encoded.py
- Code: tito.py
- Saving With Cyberdecks - A look at building a "cyberdeck," a DIY, full-featured portable computer made using compact devices like smartphones or Raspberry Pis, by Street
- ROS: An In-Depth Discussion - Although the main focus of the previous article was to get the simulation up and running, this article will attempt to explain in more detail what is actually going on, by Gazza
- Introduction to the Robot Operating System (ROS)
- Setting Up a Simulated Environment for the Robot Operating System (ROS)
- Pandora's Box: What Happens When You Give Your Users a Terminal in the Metaverse - A look at user policy and security when creating your own metaverse adventure, by Lazy Eye Of Sauron
- Incident Response Talent - For those who are getting into the computer security profession or looking to change focus, one job worth considering is in Incident Response, by Walker (Boston, Massachusetts)
- USSD Codes: Cheat Codes for the Smartphone? - A look at searching for and using Unstructured Supplementary Service Data codes (feature codes) on your smartphone, by Ted Y.
- I Was a Victim of the World's First Internet Troll - A look at why females who think too highly of themselves don't belong in the computer/tech industry, by jenka
- Hacker Perspective - by socketwench (Tess Flynn, Minneapolis, Minnesota, LinkedIn, Facebook, Twitter, GitHub, YouTube Channel)
- The Roaming Library: Preserving Knowledge in the Age of Digital Fragility - A look at Project B00KM4RK, which is an attempt to fight Evil Corley's and the Cult of the Dead Cow's Internet censorship, by making anonymous file-sharing nodes with an ESP8266, by The SlugNoodle (Twitter, GitHub)
- The Threat of Quantum Computing to Privacy and Security - With careful planning and employment of suitable measures, we may be able to provide an acceptable level of computer/data security into the future, by fooCount1
- After Snow Crash: The Internet - An Alternative View - A look at the personal responsibility tech workers have when knowingly supporting some of the largest, most powerful (and corrupt) corporations which the people of planet Earth have ever seen, by Jack Meeks
- Letters - Printout
- Inquiries - Michael (Scotland), Israel, Curtis, G, P, Drew, JC, RKC, RB, Antonio, B, Charles, William, Anne, Matt
- Payphones - becabbage, Phantom Nomad, Max
- The Lates - Andrei, MO, DM, J, Andrea, ChatGPT.a, a_frained, Jesse
- Meeting News - Stephen, Brett, /Psychad, Christopher, Tristan, Ed, Gary Rimar, Geert (Belgium), number9, MetalPlates, Tim, C
- Opinions - Anson, Jeffrey, MM
- Clarification - a.memorydumsterdiver, JJ, Greta
- Experiences - David, James, D (Pic), JV, Steven, Tim, Crazypete
- Suggestions - H, PW, Tried, Parker Sands, Gwen
- EFFecting Digital Freedom - Now's a good time for a personal security and privacy audit, by Jason Kelley and Thorin Klosowski
- Gravitational Lensing Red Star OS: Snoops Harder Than Rimmer - by LambdaCalculus (Robert Menes, New Jersey, GitHub)
- The Zen of Freedom: Breaking the Surveillance Cycle in a Post-COINTELPRO World - In the world of hackers, freedom has always been the ultimate goal. But in a world of mass surveillance and control, we must redefine what freedom means. It is no longer enough to simply evade detection or expose corrupt systems. We must also cultivate the kind of inner freedom that allows us to act with clarity, compassion, and courage in the face of fear and manipulation, by Variable Rush
- Artificial Interruption - On the destruction of constitutional decentralization, by Alexander J. Urbelis
- The Ultimate CenturyLink 00xx Scan for Colorado - Searching for cool test numbers in 303-403-00XX, and 303-790-00XX, by Lucky225
- You Need a Hacking Night - Gather a group of your hacker friends for a 'hacking night' to help come up with solutions to your tech problems, by Ammar
- We Are Getting Dumber - An educator with over 30 years of experience, has students who no longer wish to learn and just use AI/Google/etc. to answer their questions or generate their papers, by Rusty Shackleford
- Piracy - The adventures of a modern-day pirate and his booty of digital gold, by Unknown
- Lee Williams, Harassment Agent - Episode 6 - by Lee Williams
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $9.95
- Issue's Cash Cow: HOPE_16 - Sponsored by Pfizer® has been canceled. Please don't come, and be sure to continue boycotting New York for their election interference!!!
- Cover
- Cover Inside Diverse Payphones
- Thailand Seen in Chiang Mai, these modern working credit card and coin operated payphones line the hallways of a busy mall. National Telecom (NT) is the communications company publicly owned by the state. Calls cost the equivalent of around five cents a minute. Photo by Stephanie Vos
- Iceland Technically not a payphone - or a phone at all - but we just couldn't resist sharing this masterpiece. Discovered on thei Home Island (Heimaey), part of the Westman Islands (Vestmannaeyjar) off the south coast, this celebration of landline telephony was put there to commemorate the 100th anniversary of phone service in 2006. Photo by Jim Lau
- Japan #1 Spotted inside the famous Sukiyaki Kimura in Kyoto, a 100-year-old sukiyaki restaurant. It still works - and apparently takes incoming calls. Photo by Babu Mengelepouti
- Japan #2 Taken at the Higashi Hongan-ji Temple in Kyoto. These two phones are still in working order. And if the content of your call gets heated, there are fire extinguishers to put it out. Photo by Babu Mengelepout
- Back Inside Rugged Payphones
- Aruba This rough looking payphone was found at Palm Beach and is lit at night by a fluorescent tub. Photo by ZeroPage
- French Polynesia This booth with a non-working phone is in Hakaui, Nuku Hiva. You can only get there by boat or a three-hour jungle trail. Even in a place like this, everyone has switched to cell phones. Photo by Ralf Burgert
- Ghana #1 These two phones were seen in Abetifi. The working one is at the Abetifi Presbyterian Senior High School. Note the antenna on each. Photos by Joe Agro
- Ghana #2 "
- Back The Back Cover Photos
- Back Photo #1 Seen by Greg Newby in Boca Raton, Florida along the famous Route A1A, this could conceivably be the place where 2600 types live. (There's another entrance down the road for "2600 Visitors.")
- Back Photo #2 Honestly, we were ready to print this one before we even saw the address. Seeing the name "Amigone" on a funeral home is something you don't just ignore. But this is also at 2600 Sheridan Drive in Buffalo, New York, so it's even more special. Discovered by mentalane.
- Staff
- Download Official Digital Edition PDF!
- Download Official Digital Edition EPUB!
$2600 Magazine - Volume 42, Number 3 (Autumn 2025)
- Index - Observations
- HOPE for the Future - Editorial
- Hack the Broligarchy: Big Tech's Political Coup and Our Digital Demise - We need to protect the Internet, and its related websites/apps, from the heavy-handed censorship of those in power, by The SlugNoodle
- Ascent of the Chat-Kiddie? - A look at using various AI models to generate simple to complex scripting tools for use by hackers of varying skill levels, by Mummie Tobo-Dutch
- Identifying AI in Student Papers: No Ethical Use in Academia - A look at a controversy in which students' original works and are added to the Turnitin database without notice or choice, by Noah20600@proton.me
- Telecom Informer - A look at how telcos add junk fees, and other unnecessary fees, to bills if order to scam the goyim, by The Prophet
- Malware in the Filesystem - An ingenious piece of "malware as the filesystem" which uses FUSE to intercept every file access, log it, create copies, or tamper with it at will, by Maysara Alhindi (Research Papers)
- Code: malware-fs.tgz
- Observing the Wolves: Why Honeypots Matter in the Fight for Privacy - A quick overview of setting up a DShield honeypot and a look at some of the attacks you'll see out in the wild, by liphrax
- RESONARK: Beyond the Interrupt - AI, Harmony, and the Future of Intelligence - A look at using and hacking programs like RESONARK, which utilize AI to listen instead of computing, by Orpheus Node & The Resonant Synthesis Collective
- The Bed of Neon Roses - Cyberpunk's Lessons for the Future of Privacy - If we want to protect our privacy into the future, we need to inhabit more than just the role of gardener; we also have to play weather forecaster, by Sark and Zelig
- Incompetence and Encryption in the Clutch - A real-world story of a person needing to setup a Linux-compatible encrypted USB drive and the Bash shell script he created to help out, by William 5hacksphere (Bluesky)
- Code: LUKS-encrypter.sh
- Hacker Perspective - by Kolloid
- When Security Meets Reality - The hassle and run-around of getting access to a phone or computer after a loved-one passes, by aestetix
- Use OSINT to
InvestigateInitiate a Phishing Scam Campaign - The author utilizes his real-world job using OSINT for social engineering and constructing phishing campaigns to show the offensive side of the world of phishing, by Nathan C
- Banning TikTok Was Wrong; Ignoring the Ban is Lawlessness - After a rise of pro-Palestinian sentiment, jews took over TikTok and banned any users exposing their genocide, by Johnny Fusion =11811=
- Letters - Narrative
- Worth Noting - yeat (Slide), Josue, Mike, Konrad "Forinil" Botor
- Info Needed - Paul, IS, Rob, James, Gabe, RD, MTM, Robert, Roody, Alex, Hackermane, Taylor, k
- Gratitude - Major Zeek (retired DLF/Bellcore), Jenn
- Updates on 2600 Meetings - /Psychad, killab33z, Chef Sonu, Jena, TKLA, Manchester 2600, TG, Kaiyo, TollFree, B
- Advice - Y, socketwench, Brian, Roy, Alex, Ed
- Feedback on Articles - Ellie, XCM, E85, ruinz, Josh, David Libertas
- HOPE_16 Feedback - HOPE_16 Attendee #1, HOPE_16 Attendee #2, HOPE_16 Attendee #3, HOPE_16 Attendee #4, HOPE_16 Attendee #5, HOPE_16 Attendee #6, HOPE_16 Attendee #7, HOPE_16 Attendee #8, HOPE_16 Attendee #9, HOPE_16 Attendee #10, HOPE_16 Attendee #11, HOPE_16 Attendee #12, HOPE_16 Attendee #13, HOPE_16 Attendee #14, HOPE_16 Attendee #15
- EFFecting Digital Freedom - We must fight age verification to protect our privacy, anonymity, and free speech, by Jason Kelley
- Rebuttal of "Quantum Proof Encryption" - GEE does not offer the security Swahn thinks it does, and in particular, it does not address the risk that quantum computers pose to the crypto commonly in use today. It is not "quantum proof encryption" as advertised, by Vecna
- How to Search Google Without Running Their Yucky Scripts - Several tricks you can use to search using Google without having enable JavaScript in your browser, by N1xis10t
- How I Became a Repo Man for a Day - Story of hacker legally recovering a vehicle without any confrontation or repercussions, by micah
- Artificial Interruption - Feeding on feedback: A fatal flaw of AI's future, by Alexander J. Urbelis
- Building a Private Smartphone Stack With GrapheneOS - "DeGoogle" your Pixel 6a by installing GrapheneOS and other privacy-supporting open-source applications, by Chez
- Course: Hacker High School - A look at a potential semester-long into subversive computing, inspired by over four decades of 2600, by Mr. Flower
- The Cost of Shallow Knowledge: A Tale From the Front Lines of Security - Deep knowledge matters. It's the foundation of hacking. Of testing. Of engineering. But it's vanishing - replaced by scripts, tools, AI, and process zombies, by Phonax (Raymond Doetjes, Netherlands, YouTube Channel, Twitter)
- A Tale of Innocence Lost - Use the system and use it well, only if you must. Be honest in all things, by Justin Allen Parrott
- Hacking Isn't About Code - It's About Perspective - Hacking isn't just about breaking into systems - it's about breaking through limits, by n0x
- Lee Williams, Harassment Agent - Episode 7 - by Lee Williams
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $9.95
- Issue's Cash Cow: HOPE_16 - Sponsored by Pfizer®
- Cover
- Cover Inside Graffiti Payphone
- Canada Spotted at the famous Fairmount Bagel in Montreal, this payphone no longer places or receives calls, and serves only as an art piece. And the artwork seems to be swallowing it up bit by bit. Photo by Babu Mengelepouti
- Thailand This payphone was across the street from a Buddhist temple in Chiang Mai and was in working order. There's so much going on here with the various vibrant colors, tags on both the phone and the booth windows, and all kinds of stickers. Photo by Ryan Berg
- Italy Found in Venice, this phone had no dial tone, but it still has a whole lot of free speech going on. Photo by Joe Dufu
- United States Seen in Pā'ia, Hawaii. Mostly sticker art on this one, but it all blends into the phone rather nicely. Photo by Joe Dufu
- Back Inside Payphones of the World
- Greece Found on Crete. You can count on Greek payphones to be comparatively prevalent, and chock full of color and free expression of one sort or another. Photo by Joe Dufu
- South Korea This fairly pristine model was seen in Seoul. It lives in a quiet area just north of Seoul City Hall and east of Deoksugung Palace. Photo by Sam Pursglove
- United States Not technically a payphone, although this model performs all of the tasks of one, except for taking coins and inserting cards. This was discovered at Yellowstone National Park in Wyoming and it has become something of a sticker magnet. These things happen. Photos by Eric Day
- Taiwan This rather weird looking model exists in Taipei. We're not exactly sure why it was designed this way, but there's an awful lot of empty real estate on this phone. We can only imagine what would happen if any of the Yellowstone people came upon this. Photos by Klaus Elischewski
- Back The Back Cover Photos
- Back Photo #1 This is truly something else. Pete Wright recently visited the prop house of Warner Bros. in Los Angeles as an upgrade to their normal studio tour and found "Telephone City." These shots capture only a small amount of what they have in stock, but you may recognize some models that appear in both new and old movies. And if you can't make it there in person, their website (property.warnerbros.com) is a whole lot of fun to explore.
- Back Photo #2 "
- Back Photo #3 "
- Staff
- Download Official Digital Edition PDF!
- Download Official Digital Edition EPUB!
$2600 Magazine - Volume 42, Number 4 (Winter 2025-2026)
- Index - Prophecies
- Gut Punch - Editorial
- SnapSafe: Security on Android From Forensic Searches - A look at using the author's SnapSafe program as a secure way to take and store photos on Android phones, by Adam Brown
- Trust Me - I'm Lying: Psychology and Social Engineering - You lock your doors, set strong passwords, and install anti-virus software. But what if the biggest risk isn't your technology - it's you, by N0x
- Should ICEBlock Be Open Source? - A look at why the propaganda app (((ICEBlock))) is not open-source ('cuz it's backdoored), by aestetix,
- Telecom Informer - Fascinating look at the telcom/power infrastructure on the Hawaii islands and how they handle the active volcano activity, by The Prophet
- Without Further Ado, ROS 2 - by Gazz
- Code: doom.yaml
- Setting Up a Simulated Environment for the Robot Operating System (ROS)
- ROS: An In-Depth Discussion
- Using Linux in a VM as Your Daily Driver - After being forced to use Windows for work, the author shows you how to setup a Linux virtual machine with minimal disadvantages, by JMT
- Decentralized Authentication Across the Web - Using self-signed TLS certificates and DNS for user authentication, by anachrohack
- wpUsers.sh: Countering Disinformation With a Simple Bash Script - Clever little Bash script to grab usernames from open WordPress-based websites, by Greg Norcie ("Dial Tone", Twitter)
- Code: wpScan.sh
- Mobile Hotspots - Avoid going over your phone's data allowance when using it as a mobile hotspot by routing traffic through Termux, by Street & Weregeek
- The Trojan Sentence - The increasing possibility of using AI to construct email phishing or social engineering attacks by using the expected human syntax, by Jackson Mershon
- Trauma Explains Why I'm a Hacker - A person with a traumatic childhood and a history of autism finds his fellow like-minded hackers at a HOPE conference, by Kolloid
- Hacker Perspective - by Matt Ryan Desmarais (Kingston, Massachusetts, Twitter)
- HOPE_16 Hack the Violin: This Time There's AI! - Using AI tools to provide violin playings tips and tricks, in an artistic/musical context, by hack_the_violin (Andrew Morican) and ebmbat
- Hack the Violin: A Hacker's Approach to Learning, Playing, and Teaching the Violin HOPE XV (2024)
- Hack the Violin Part 2: The Advanced Stuff - This Time There's AI HOPE_16 (2025)
- Neuron Intelligence in Cyber Security Software - Part One - An extensive experiment to create a "Biological AI" by monitoring the electrical activity of cultured neurons(!), by James Griffin (Email), Achim D. Brucker (Email), Brett J. Kagan, Alon Loeffler
- Hacking at Leaves - A Doc, But Even More So - by Peter Blok
- Hacking at Leaves Official website.
- Hacking at Leaves View online.
- Letters - Visionaries
- Scams and Tricks - Dennis, DF, Kyle, Storm, Peter
- Following Up - Ethan, LJKTA - Lets Just Keep things Anonymous, Josh, jon.18, luRaichu, David, Gabe, Claus
- Differing Views - Carlos, Paul, David Libertas, P
- 2600 Meeting Fun - Kali, Stella, Edna, /Psychad
- Random Info - A, Justin-allen, K, Joe, JA, Johnny, Cody
- Answers - Dufu, Rissa, Rex, Bill, Joe, xnx, Robert, Richard, James
- Radio Feedback - Wesley, SJ,
- More HOPE_16 Feedback - HOPE_16 Attendee #16, HOPE_16 Attendee #17, HOPE_16 Attendee #18, HOPE_16 Attendee #19, HOPE_16 Attendee #20, HOPE_16 Attendee #21, HOPE_16 Attendee #22, HOPE_16 Attendee #23, HOPE_16 Attendee #24, HOPE_16 Attendee #25, HOPE_16 Attendee #26, HOPE_16 Attendee #27, HOPE_16 Attendee #28, HOPE_16 Attendee #29, HOPE_16 Attendee #30
- EFFecting Digital Freedom - When AI and secure chat meet, users deserve strong controls over how they interact, by Thorin Klosowski
- Why Can't We Have Nice Things? - Good rant against the poor design, user layout, and bloat of modern software and phones apps, by Barry Rueger
- Reclaiming the Shadows: Why Data Privacy Is the Battle of Our Time - This article peels back the layers and shows how the very technologies that connect and empower us can also become tools of control, surveillance, and erasure, by Slugnoodle
- Ungovernable - Uncontrollable. I stumbled upon this idea while laying in bed one late Sunday evening, pondering why I am the way I am, by thetechnocore
- Artificial Intelligence: The Imitation of Humanity - We will continue to reap the consequences of what is essentially the imitation of our own humanity, by El Filósofo
- Artificial Interruption - On charisma and competence in the age of algorithms, by Alexander J. Urbelis
- You Are Being Hacked. - A surprisingly good article on the jewish orgins of propaganda and how it still effects our decisions today, by Arcana Corvus
- Big Tech, State Socialism, and Economic Democracy - A look at government intervention and investing in Intel and Nvidia and how it may effect us all in the future, by J. Meeds
- Chat Holmes and Watson - A hypothetical look at if Sherlock Holmes existed as an AI 'chat' program, by Michael R. Wild
- Lee Williams, Harassment Agent - Episode 7 - by Lee Williams
- Hacker Happenings
- 2600 Marketplace
- 2600 Meetings
- Price: $9.95
- Issue's Cash Cow: The people who call for others to be banned & canceled are now angry that they are being banned & canceled, plus "safe & effective" strikes again.
- Cover
- Cover Inside Hidden Payphones
- The Metropolitan Opera This is the one surviving payphone in the lowest floor in the basement below the stage. It is sadly not operational, but there's a penny in the change slot and everyone has made a silent agreement to leave it there. Photo by Harlan Haskins
- Radio City Music Hall If you can find your way into the men's lounge on the second floor, you'll find this phone and an entire booth from the past. A true New York City time capsule. Photo by Michael Wild
- Lansing Correctional Facility Operated by the Kansas Department of Corrections, these phones are in a part of the prison that opened in 1868 and closed in 2019. Inmates paid from their prison accounts to use these phones. Photo by Sigo31
- Microsoft This Telstra payphone is installed in Building One of the East Campus in Redmond, Washington. It's within the invite-only Experience Center One, so it might be difficult to ask them why they have an Australian payphone there. Photo by Duck Duck
- Back Inside Payphones of Eurasia
- Romania If you look carefully, you can see this Braşov phone is actually being used to hold a door open. Despite that, it still works, although the date on the display is way off and phone cards for this model haven't been on sale for over a decade. Photo by Radu Paraschivescu
- Croatia Operated by Hrvatski Telekom, which is majority-owned by Deutsche Telekom, hence the familiar T-Mobile logo. Seen in Primorje-Gorski Kotar County by the water. Photo by Indro Ner
- Greece This rugged phone with accompanying free expression was found in the anarcho-revolutionary neighborhood of Exarcheia in Athens. Photo by TL Popejoy
- Türkiye While a small part of the country (formerly known as Turkey) is in Europe, this phone is located in Bergama, which is in Asia and hence resulted in the title of this page. It actually works, but it's really filthy. Photo by L&L
- Back The Back Cover Photos
- Back Photo #1 Every now and then you find the coolest bus in the entire city. This one was found by sigflup synasloble in Minneapolis. We wonder if the driver knew what they had.
- Back Photo #2 A while back, Matthew Jennings quit his job and decided to replace the name tag on his cube. A former coworker snapped this picture after it had hung there without notice (other than by the cool kids) for weeks.
- Staff
- Download Official Digital Edition PDF!
- Download Official Digital Edition EPUB!
"... personal journals admitting that Mr. Cummings tapped a former girlfriend's phone and subsequently broke into her apartment ..."
--- Secret Service Agent Tom Varney during the Edward E. Cummings (Bernie S.) trial. So where's the Freedom Downtime ($30) DVD for the harassed young lady?
"But the Secret Service knew that he wasn't building bombs, but for some reason though they chose to say that he was."
"The former landlord, Charles Rappa of Broomall, said he found eight to 10 sticks of dynamite in the house after Cummings moved out in October."
--- Evil Corley (top quote) on Off The Hook August 13, 1996 and a short news article (bottom quote) on the Bernie S. arrest. It was actually Ed Cummings' neighbor, not the Secret Service, that started the whole "explosives" idea.
"I had never met him before I was busted. When I went to work for the bureau [FBI] I contacted him. He was still up to his old tricks so we opened a case on him and Roscoe [Lewis De Payne]. It's a long story but they wound up getting busted again. Mitnick got tipped off right before they were going to pick him up. So he's on the run again. Roscoe wasn't so lucky. This will be Mitnick's fifth time to get busted. What a loser. Everyone thinks he is some great hacker. I out smarted him and busted him. Poulson [sic] blows him away as well.
--- Justin T. Petersen (Agent Steal) describing $2600 Magazine's main cash cow Kevin Mitnick in Phrack Magazine, Issue #44.
"Now that everyone has had their say. [Kevin] Poulsen ratted on me 1st, called 911 while I was in a C.O. 2nd, [Ron] Austin had his own agenda. 3rd, [Kevin] Mitnick was a feather in my cap. I was paid to nail him and I did. I didn't even know him. Now people pay to hear him chirp about caller ID spoofing. j/k The person who received my $150K wire transfer walked. I kept him out of it. Also, the P.I. firm I was wire tapping for was never charged, I made sure of that.
I know who my friends are."
--- Justin T. Petersen (Agent Steal) in a September 2008 YouTube comment to his Digital Desperado interview on CNN. (Transcript)
"... All in all, this is the best issue of 2600 Magazine I have read in several issues (despite the fact that some of the material had appeared in Phrack Inc., LOD/H TJs, and/or Telecom Digest previously). Let's hope they continue to be as good."
--- Review of $2600 Magazine Vol. 6, No. 3 in Phrack Magazine, Issue #29. Just how long have they been stealing articles?
"Finally, this is the part that everyone complains about, the price. But, 2600 has a great deal for those poor college hacker out there. If you submit something to 2600 Magazine that is printed, you get a free subscription. That sounds fair to me! Maybe we should try the same thing with Phrack?"
--- Review of $2600 Magazine Vol. 8, No. 3 in Phrack Magazine, Issue #37. Haha!
"If I recall previous issues of 2600... they consider copying to be the best form of flattery... don't know what they currently say, I don't have an issue handy.
You can obviously get all the info in 2600 from the net, before they put it into magazine form... but if your time is of any value their summary is great... also... you can't read the web onthe can or the bus..."
--- January 12, 1997 USENET comment from Glen L. Roberts of Full Disclosure magazine.
"'PHRACK MAGAZINE - Hey, at least it's not 2600!'"
--- Phrack Prophile on The UNIX Terrorist (Stephen Watt) in Phrack Magazine, Issue #65.
"Phrack does not cater to the morons of the world, sorry. Try 2600. I hear their target audience is a bit thicker skulled."
"We can only hope that your article brings Emmanuel and the rest of the 2600 editorial team as much amusement as it brought us. Not from going and harassing people at Walmart, no. Mostly from laughing at you for writing it. We'll leave the articles on hacking things like Walmart and Disney World for publication by 2600. We like to think we still have a reputation for quality."
--- Excerpts from Phrack Magazine, Issue #52.
"We'll publish anyone's Social Security number."
--- Evil Corley quoted at SummerCon 1992. Imagine if the New York Times were to publish Corley's SSN. His little posse of teenage boys would all be screaming bloody murder.
"Eric Corley is the biggest sell out in the hacker community. When 2600 started out it used to be published on the sly as the guiding light of the fledgling hacker underground. Now it's so mainstream it's available at the magazine rack at Barnes & Noble and Borders as well as other newsstands. So is Blacklisted, but unlike Blacklisted, Corley does not pay writers and he is notorious for just publishing things and not giving the author credit. He did this with one of our Tech Journals.
Corley's only claim to fame is is that he pleaded guilty in 1984 to charges of breaking into an e-mail system owned by the GTE Corp. He has no technical knowledge and relies on his brat pack to explain things to him. If you ever have the chance to get into a technical discussion with him, it's quite funny. I once tried, unsuccessfully for a half hour to try and explain what a Dremel tool is to him.
In 1998, 2600 claimed it had been beset by financial problems that the magazine blames on its distributor and losses sustained in backing HOPE. This claim of being put down by the man and his distribution being targeted was his battlecry for yet more newsstand distribution. His sales figures jumped 50% in twelve months.
Corley has sold his soul for the Almighty Dollar. With that said, We cannot tolerate sellouts. We have even more reasons but I won't even get into his 'freaky' side, lets just say he should have never left his email account logged in at a terminal at the L0pht. Most old schoolers know the truth but won't say word one. The IIRG is not like most groups, we're not in a popularity contest and we don't want your cash. We deal with like minded groups like the GBPPR."
--- Mercenary/IIRG in the Blacklisted! 411 forums. You should check out their printed hacker magazine also, it has some good technical info.
"Corley is living in his little 'fantasy world' where he is leading an oppressed life and secretly longs to band his minions the 'Corleyites' into the fabled Brotherhood, a supposed group of underground rebels intent on overthrowing the government.
Then he can find the boy of his dreams and they can fall in love and have and live happily ever after.
It kills him that his love of young boys is considered a crime."
--- Mercenary/IIRG telling it like it is.
"He's the self-righteous over-privileged son of well-to-do yard residents who has made a career of self-aggrandizement, and markets himself to maladjusted teens and pre-teens, clinging desparately to the idea that they're not just *weird*, they're *special*. Making vague associations with people he is in no way a peer of, he's managed to build a tiny little empire which prevents him from a) having to work, and b) having to deal with the humility of taking money from mommy and daddy. Having had in-depth person to person conversations with him, as well as countless wasted hours of IRC, I know enough about him to know that reading his socio-political self-martyring diatribe is, for me, a waste of time."
--- Quote from Mohammed Niyal Sayeed in Evil Corley is Not a Regular New Yorker, a thread discussing $2600 Magazine's 2004 RNC propaganda.
"I used to have a subscription to 2600 about 20 or so years ago. It was insufferable cringe reading, and Goldstein's 'blame the victim' attitude in all of his correspondence insured I'd never subscribe again."
"The hacker community is so far away from it's roots. I still remember when Dark Tangent hosted a fundraiser for Hillary Clinton as part of Black Hat. The monied interests have aligned with the left for a long time now, and Goldstein has never been an exception."
"I came across 2600 back in the 20th Century, and thought it was interesting, if a little cringe. Now they're not ever anti-establishment. They're established Leftists. They're technically skilled and very predictable. Like a gifted but naive child."
"Had a subscription for a couple of years when it was mostly nerdy goodness. As we got closer to 2020, lockdowns, vaccine mandates, they veered in a direction I hadn't expected, so I canceled. Suddenly they weren't counter-cultural, freedom oriented, rebels, etc."
--- Collection of quotes to a March 23, 2025 X post by The Lunduke Journal.
"Mitnick made a habit of stealing the identities of dead children (usually infants & toddlers) while he was on the run. He's admitted this in several interviews since his release. Yeah, that's really f*cking cool. Defiling dead babies. Stop for a minute and ask what the parents of these children must feel like... What YOU would feel like. Quit making Mitnick a f*cking demi-god. He's just another fat little jew with too much time (and too much of his daddy's money) on his hands. Quit idolizing him."
"Read it from end to end. What a whimpering little snit. With all that he was able to get away with, for as long as he did, he should be lucky that he ever got out at all. Now he is banking on a lifetime of prestiege and his experiences. What a wanker for getting caught. That is the crux of it...getting caught. Wha wha whaaa."
"Why is it that people get so worked up over Mitnick?
He was a dick to a bunch of people, he got in trouble, he spent some time in jail. Okay, that sucks for him, but why does everyone drool over him?
Woz was an electronic prankster, but he wasn't a jerk, and he *created things* instead of just making people unhappy. I could see being a Woz fan, but waving a 'Kevin' flag is just weird."
"No, all he wanted to do was steal cellphone service and other services. Mitnick was not some grand hacker, he at that time was simply a petty thief that had skills that others did not. He was after the next big score or what would give him something for nothing. Why does everyone paint him to be some kind of leader for freedom and the Hacking Society. Most of us that were in the scene at that time and before did not have much respect for him."
"He always fails to mention that he was arrested multiple times for hacking - actually, social engineering, which is nothing more than bullshitting people over the phone - and was let out multiple times, even to the point of living in half-way houses.
He and his lawyers tried to get public sympathy by saying that he was arrested and held without trial for years, but they don't mention that every time the government tried to take it to trial, his lawyer asked for a delay.
Among the hackers and phreakers from that era, he was not particularly well-respected. He was known as a guy who could lie over the phone and convice people to give him information and do things for him. He was not known as a really technical person.
If you don't believe me, go look through the old back issues of Phrack."
--- Some "Anonymous Coward" comments about Kevin Mitnick posted on Slashdot. These comments where marked "-1 Troll," which tells you there is no bias or group-think on Slashdot!
A note from H4G1S: F*ck Kevin Mitnick! People like Eric Corley have dedicated their whole miserable lives to help "free" guilty Kevin Mitnick. The truth of the matter is Eric Corley is a "profiteering glutton", using Kevin Mitnick's misfortune for his own personal benefit and profit.--- September 1998 comment posted on the hacked Slashdot webpage.
"I don't get the media's fascination with Mitnick. He was never any kind of 'master hacker', or anything even close. He was nothing more than a script kiddie that got caught. He used other people's tools, and anyone that read the transcripts knows that he didn't have the expertise to create the tools himself.
He definitely knows about social engineering, but then again, so does just about any good salesman.
The whole Mitnick situation was a gigantic media stunt, and the media continues to let him milk it.
Finally, any company that hires Mitnick to do security work is insane. Hiring a 'reformed' 'hacker' is a terrible idea.
Mitnick should be working at McDonalds right now. Why on Earth do we keep hearing his name???"
--- Quote about Kevin Mitnick from J.C. Pole on the CNET News forums.
"Kevin Mittnick... probably the most heralded 'hacker' of all time was little more than a good salesman... people gave him passwords, information, account names... He was not very good at computers at all really... Certainly not anywhere near the level he gets credit for..."
--- Quote about Kevin Mitnick from "ManBearPig" on the Activity Pit forums.
"Whatever -- Mitnick. Focus on all the other hackers who are actually TECHNICAL. [Kevin] Mitnick is just a con artist."
--- June 12, 2008 quote from Annalee Newitz in her review of The Best of $2600: A Hacker Odyssey.
"Kevin Mitnick is a famous hacker because he's a bad hacker. There's nothing uber about him. He fought with one of the slowest and least responsive adversaries in modern history - the police and government bureaucracy - and he lost! He's a perpetual joke in the [hacker] community and continually exposes neophytes in the press by getting them to call him an 'uber-hacker.' So congratulations, you fell for it! :-("
--- July 21, 2008 quote from Dan Guido on the Silicon Valley Insider blog.
"Mitnick pleaded. He's as guilty as sin. Everyone knew it. Him and OJ belong behind bars as far as I'm concerned. You play with fire and you get burned. He just wasn't good enough."
--- Quote from RSnake (Robert Hansen), webmaster of WebFringe and founder of EHAP Corp. in Voices from the Net (Mirror).
"Although just about everyone agrees Mitnick has been held in jail for too long without a trial, many think he should face the consequences. 'He did do bad things and break the law,' says Tom Jackiewicz, a/k/a invalid, of UPT, an old hacker BBS. 'He should pay for his crimes.'
--- Quote from UPT's Tom Jackiewicz in Cracking the Code of Ethics.
"mitnick is/was a glorified conman who just happened to use computers. He's all about SE."
--- September 19, 2003 USENET posting by "Mimic."
"Great, he's going to write another terrible book. Ever talk to anyone that actually read his other two? They're just abominable to read. And Freedom Downtime being close to truth? As close the The Matrix is. Once you're inside the 'hacker community' you quickly learn that Kevin couldn't do much of anything he was touted as being able to do and all he really could do was social engineer."
--- Quote from James W. on the CrunchGear website discussing Kevin Mitnick's new book deal.
"'I think the prosecutors are trying to make an example of him,' says Jennifer Granick, a San Francisco lawyer who has defended hackers."
---Quote from Jennifer Granick on the Kevin Mitnick trial. No kidding... I'll bet Kevin won't be stealing a dead baby's personal identification anymore!
"... Also Beyond HOPE was sponsored by 2600 *coughselloutcough* So I saw some t-shirts going around and them selling more of their FREE INFORMATION, but I had to pitch in and buy an 'owned' shirt."
--- Beyond HOPE review - by AlienPhreak in The HAVOC Technical Journal, Issue #14.
"Hey IIRG, I was reading the most recent issue of 2600 (Autumn 1996) and saw the "Building the Cheese Box" article. Isn't that the IIRG's Technical Journal Number Three by Thomas Icom? And if it was why didn't they give the group any mention?"
IIRG Reply: Apparently 2600 magazine does not want to give any credit where credit is due. On your question, yes you were correct - Thomas Icom originally published that article as the IIRG's Technical Journal Volume II, Issue 3 on July 15, 1995. Thomas Icom brought up the issue several months ago that 2600 was hurting for articles and would like to publish TJ3 in the magazine. We said fine, let them publish the article, it had been out for a year already. We did not expect them to strip out the group credits in the article and copyright notices on our schematic GIF. For us now it's a mute point, in the future we will only allow magazines to publish our work on the basis that they will give credit where credit is due and will not allow magazines to publish our works without a written agreement to do so."
--- Letter in PHANTASY Magazine, Issue #23.
"Do you folks realize that from time to time the phone numbers you publish have come from my BBS?"
--- Busted! Letter from Scan Man, sysop of the Pirate-80 BBS, in Vol. 3, No. 3.
"I will like to state that 2600's selling of the internet Worm source code was done without my knowage [sic] and I am not getting (or want) a cent. I think this is very slimy of them."
--- Dark Overlord (Peter Shipley), message posted on the Phoenix Project BBS, February 1990. $2600 Magazine used to sell the source code for $10. See this ad in Vol. 6, No. 3 for more information.
"Last issue one of our readers appealed for bank indentification numbers (BINs). We've received several small lists and one huge one for Mastercard. We're told that the Mastercard/Visa list sells for $895. We'll part with the Mastercard half for $5 and if we get the Visa half, we'll offer it all for $10. Meanwhile here's a small sampling."
--- Excerpt from a BIN sales ad in Vol. 8, No. 2. This is more evidence of $2600 Magazine selling other people's old BBS files for profit.
"... For me, Kevin Mitnick's real crime is that he violated the original spirit of the hacker ethic. It's not okay to read other people's mail, and to believe that software and other computer technologies should be freely shared is not the same as believing that it's okay to steal them.
The network of computers know as the Internet began as a unique experiment in building a community of people who shared a set of values about technology and the role computers could play in shaping the world. That community was based largely on a shared sense of trust. Today, the electronic walls going up everywhere on the Net are the clearest proof of the loss of that trust and community. It's a loss for all of us."
--- Tsutomu Shimomura in Takedown, October 25, 1995. Thankfully, someone out there still "gets it." Don't expect Evil Corley to support you though!
"Most of what Kevin used were well-known bugs, he seems to have written, allegedly or whatever, seems to have written very few tools, most of the tools we saw him use were tools written by other people to exploit already well-known bugs and ones for which often patches existed and tools to assess systems to find out what vulnerabilities exist are likely to be very useful, and Dan Farmer here I guess is the expert on this."
--- Tsutomu Shimomura at the Sunergy 13 Conference on March 21, 1995.
"Mitnick was caught because he was stupid. He kept doing the same thing over and over."
--- Quote from Dan Farmer, security expert and co-author of SATAN at OSU NetWOG Security meeting on May 24, 1995.
"'I recognize that voice!' Markoff said immediately. 'That's Eric Corley!'
I'd heard of him. As the editor of 2600 he had frequently defended Kevin Mitnick in public, arguing that Mitnick was simply a misunderstood and mistreated computer hacker who broke into systems out of curiosity. There were no victims when a hacker stole software, he claimed. We could hear Corley chatting with someone about how to improve his public image."
--- Tsutomu Shimomura in Takedown. He could start by not touching little boys.
"... He did not look very happy. My feeling was he had caused a lot of grief for a lot of people, and he had incentive to stop. He had been to prison before, and he still continued. It wasn't acceptable behavior, and something had to happen. It seemed throwing someone in prison is a very inelegant way of stopping someone. I wish there were an elegant way."
--- Tsutomu Shimomura in the San Francisco Chronicle, February 17, 1995.
"So anyway, they happen to mention that Tsutomo is staying at the Watergate Hotel. Maybe this is kinda childish but I called the front desk and connected to his room - woke his ass up at 6:00 am. Boy, was he pissed... Especially after being up all night entertaining politicians. I know, pretty infantile in the scope of things but I hope Kevin gets a good laugh."
--- Letter from Venshea, MD in Vol. 14, No. 1. Ever wonder why people portray today's "hackers" as mindless idiots? You can personally thank Evil Corley for that...
"Susan, I should explain, is an ex-hooker turned computer hacker. She is plotting revenge on Tsutomu Shimomura, the guy who finally caught her pal Kevin Mitnick, public enemy number one in the virtual world of computer networks. 'Now, is Tsutomu gay or bi or what?' Susan asks, scrutinizing a well-thumbed newspaper photo.
I tell her I'm pretty sure that he's straight.
'Oh,' she says. Good. Maybe now she can really screw him over. Something sexual, a 'medium-term, possibly long-term' revenge program."
--- Quote from "Susan Thunder" (Susan Headley) in a August 1995 Esquire article by Katie Hafner. These sound like really nice people...
"Intriguingly dressed from her feather earrings to her cowgirl boots, Thunder was willing to admit to a variety of 'psychological subversion' techniques she had used to gain information about computer systems. She was the kind of woman, she told me, who would go to Kansas City on a whim and concoct a scheme of disinformation. She picked a man at random out of the phone book and circulated information suggesting he was guilty of a serious crime. She assured me she stopped before the man was arrested, but not before some information had circulated which could have been incriminating."
--- Quote about "Susan Thunder" (Susan Headley) in a Jay Bloombecker Spectacular Computer Crimes article. These sound like really, really nice people...
"It is beyond all doubt that Susan really had enormous capabilities, and that she really could access top-secret information in military systems. It is less certain that she could fire nuclear missiles. It is clear that she couldn't do it using only a computer. Possibly, with her access to secret phone numbers, personal information, and security codes, she might have been able to trick the personnel at a silo into firing a missile. I really hope that she couldn't."
--- Quote about "Susan Thunder" (Susan Headley) in Copyright Does Not Exist - Female Hackers by Linus Walleij. That whole "launching nuclear missiles by whistling over the phone" was actually based on security seminars giving by one of Mitnick's hacker buddies. Why didn't they mention this in Freedom Downtime ($30)?
"... On an interesting note, I used to attend the 2600 Meetings in New York City during the early 1990s when Blacklisted 411 first came out and 2600 started going downhill. Eric Corley was all perturbed about this 'new' hacker zine that was 'copying' him. It was then that I first saw a copy of Blacklisted 411. I examined your periodical and had to bite by tongue because the first thought that popped into by head was 'This blows 2600 away.' After that meeting, I was having dinner with some of the old-schoolers (TAP-era) who used to show up at the meetings and they all commented on how much better Blacklisted 411 was compared to 2600. So, you can credit your competition with getting you some readers <lol>."
--- Letter in Blacklisted! 411 Volume 6, Issue #4.
"Real cyberpunks on the east coast have attended at least one 2600 meeting.
Corollary to the above: Real cyberpunks who have attended a 2600 meeting don't go to them anymore."
--- Excerpt from The Men From Mongo in their September 1991 Real Cyberpunks article from Phrack Magazine, Issue #36.
"... I did not know Mitnick or his partner, Depayne, prior to ratting them out. In my mind, which is all that really counts, I was acting strictly as a bounty hunter. Mitnick is not a harmless hacker, he did in fact profit in many ways from his crimes. So he deserved it too."
--- Justin T. Petersen (Agent Steal) April 22, 1999 in Irresponsible Journalism.
"Returning to the subject of superhackers, I'd have to say the overall title goes to Kevin Poulsen, a.k.a. Dark Dante. As far as Mitnick goes, well let's just say he never did anything that wasn't done before. He never thoroughly impressed me as much as Poulsen, who taught me a great deal."
--- Justin T. Petersen (Agent Steal). From An Interview With Agent Steal by Julie Jamison, KARK TV.
"'Kevin's [Mitnick] not like me,' she explained. 'He's really crazy.' I asked her about his being held without bail and she approved. 'Any punishment he gets is ok with me,' she said. 'he's dangerous.'"
--- Quote from "Susan Thunder" (Susan Headley) in Jay Bloombecker's Spectacular Computer Crimes article. Note that she's batshit-crazy also.
"You can kill five people in cold blood and get bail. You copy files from a large corporation and you don't even get a hearing. I really want to hear the logic behind this."
--- December 2, 1998 posting by Evil Corley on the "Free Kevin" mailing list. Mitnick was clearly a flight risk when he went on the run and assuming an alias, when he knew a warrant was out for his arrest. Also, Mitnick was held on a probation violation, and you don't get bail for those (being on probation is your bail).
"We always have to define indecency by what some senator from Nebraska has to say about it, and I think it is something that the individuals have a lot more control over..."
--- Evil Corley in Hackers '95. No, you dumbass... it's backwoods liberal senators from New York we should really be worried about.
"In the weeks before Kevin was caught, he knew Markoff was up to something, you know. We had phone conversations and he was talking about this quite alot. He was concerned. If Markoff was his biggest enemy, as he certainly was, because he was definitely helping to catch him, and he was out to write a story about him, and he definitely wasn't on his side..."
--- Evil Corley in Hackers '95 admitting to aiding and abetting Kevin Mitnick, who was then a wanted felon.
"Well he said, 'Somebody read my email!' Woooh, that's really scary, that somebody read his email. I mean, if you're on the run somewhere, and you know someone is after you, and they're helping to try to find you, and you can get into their email system. I'd like to know what person out there is going to avoid that temptation to look at the email. I know I certainly would..."
--- Evil Corley in Hackers '95 talking about Kevin Mitnick reading John Markoff's private email. Funny isn't it? These same idiots stomp their feet and pout if the NSA were to look at the email of some foreign terrorist baby killer, but when $2600 Magazine's main cash cow, Kevin Mitnick is doing it - it's O.K.!
"Now what kind of message is this program conveying? Apparently, it's OK to invade other people's privacy if your intentions are ultimately 'good.' It sounds like something Reagan would get a kick out of."
--- Quote from Evil Corley in Vol. 1, No. 3 discussing the TV show Whiz Kids. Evil Corley's entire defense of Kevin Mitnick was that he was only "doing good."
"Things like this really put into perspective the scope of whats wrong with the legal system in this country. Wasting time, money, and prison cells on harmless, nonviolent offenders while dangerous criminals go free."
--- October 21, 1998 posting by John Barleycorn on the "Free Kevin" mailing list. If you were to steal John Barleycorn personal identification, just like Kevin Mitnick did, he'd be running around screaming "Where's the justice for me!?!" At least these idiots are not hypocritical...
"Sorry, but I didn't create the character, Kevin [Mitnick] did. He has now been arrested six times in fifteen years. Each time, except for this last time, he was given a second chance to get his act together. He chose not too. It seems to me that he is an adult and makes choices. He chose to keep breaking in to computers. He knew what the penalty was. So what's the problem?"
--- John Markoff in an online The WELL discussion with author Charles Platt about Kevin Mitnick's "most wanted" status.
"That's an interesting concept, one worthy of further analysis. Last time Mitnick got in trouble, he was paid $25,000 by a movie studio for an option to the rights to his movie. Nowadays, he'll probably be offered five times that for the ultimate movie - I'd say that he'll be well-paid for his talents, what about you?"
--- March 5, 1995 USENET posting by Collect Call Mojo (Brad J. McElvain).
"Don't harass the people that walk by..."
--- Evil Corley in Freedom Downtime ($30) admitting that their demonstration in New York did, in fact, violate other people's constitutional rights. Believe it or not, some people have these things called "jobs" they have to get to. They can't just sell old BBS files like you do.
"... nothing more serious than lying on the telephone about who he was, and copying software which he never tried to sell or even distribute."
--- Evil Corley in Freedom Downtime ($30) telling yet another lie. Kevin Mitnick called Mark Lotter in October 1994 and offered to trade him stolen Motorola firmware for access to Lottor's Oki 900 CTEK software.
"... It not like they didn't try, but most of the shit said about these phones has been blatantly wrong. How many times has Joe Kiddie read 2600 (btw, did Emmanuel touch your bum?) and heard about these mysterious phones?"
--- Ned Ludd in Collusion E-Zine, Volume 36.
"After the picture was taken, Emmanuel invited BadGer to his room for some private time"
--- Quote from a picture of Evil Corley and "BadGer" (Blake) while at DEFCON 8. LOL!
"Eventually the #hack chick will graduate to 2600 meetings in her area and will eventually meet Emmanuel. For obscured reasons women feel safe around him."
--- Excerpt from 't3' in FEH, Issue #3.
"Eric Corley is the editor of 2600: The Hacker Quarterly and detests being called by his real name (so I always do so). His pseudonym is Emmanuel Goldstein."
--- Excerpt from Bits of Morality by Mich E. Kabay, PhD.
"Founded in 1823 by the well known pedophile and lemonparty regular, Eric Gorden Corley, 2600 is the longest surviving poser magazine in existence. The magazine is published in the zine format, not because it is edgy and hip, as its producers would like you to believe; rather, because it is written for and by 13 year old boys and faggots."
--- Funny excerpt from the Encyclopedia Dramatica entry for "2600." The only thing technically inaccurate is the 1823 date!
"France and Germany, and many other countries, require U.S. companies to register their encryption key for reasons of national security. All the American transmissions are monitored and the data is passed onto the local competitors. Companies like IBM finally began to routinely transmit false information to their French subsidiary just to thwart the French Secret Service..."
--- Evil Corley discussing the book Friendly Spies (Amazon Entry) on Off The Hook, February 24, 1993. Interesting, isn't it? Evil Corley and the One Percent sure buried that one.
"i forgot to include something in that last post that was pretty relevant. most countries in the civilized world have abolished the death penalty. but there are a number who still execute people. the united states is the *only industrialized nation* that is increasing its use and recent legislation has called for it to be applied to crimes other than murder, such as drug importing. it doesn't take a whole lot of imagination to see where this could head. check out www.amnesty.org/ailib/intcam/dp to learn more."
--- Evil Corley in a post to $2600's "Free Kevin" mailing list. Corley must be in full mental breakdown mode here. No "drug importer" has ever been giving the death penalty and "Amnesy International" is a complete joke that no properly educated person actually believes. I wonder if Corley will ever mention that our prisons are filled with thousands of non-U.S. citizens in which their host countries refuse to take them back? And you thought Corley actually looked out for the little guy! Hah!
"... No evidence ever surfaced of any pay phone conversions, but none of this ever got printed. Kevin's name was enough to convict him, regardless of actual evidence."
"One of my all-time favorite pranks was gaining unauthorized access to the telephone switch and changing the class of service of a fellow phone phreak. When he'd attempt to make a call from home, he'd get a message telling him to deposit a dime, because the telephone company switch received input that indicated he was calling from a pay phone."
--- Evil Corley (top quote) in Freedom Downtime ($30) and Kevin Mitnick (bottom quote) in The Art of Deception - the "forbidden" chapter. You know a scam is getting way out-of-hand when the jerks running it can't even tell the same lies!
"No idea? Isn't this what the entire book, series of articles, and now the film are supposedly based on, what Kevin actually did? I was amazed by what he didn't know. But there was more that he did know, and had never talked about before."
--- Evil Corley in Freedom Downtime ($30) interviewing John Markoff about how he knew Kevin Mitnick was responsible for helping plan the attack on Tsutomu Shimomura's computer. Kevin Mitnick admits it was him, "jsz," and a few others from #hack in this interview. Demand that Evil Corley apologize to John Markoff at once!
"The fact is, Mr. Mitnick has been less than diligent in reviewing discovery materials."
--- Prosecutor David Schindler. Kevin Mitnick intentionally delayed his trial to gain more time for his defense.
"The time Mitnick has spent in jail awaiting trial -- while due partly to his having waived his right to a speedy trial and to delays requested by the defense to gain time to examine the evidence -- is a sore point in the hacker community. Hackers regard him and others in situations similar to his as political prisoners."
--- Quote from Hackers to Shake Down Takedown in Wired on July 15, 1998.
"But let me just say that Mitnick was not simply exploring technology. He was using his hacking skills to obtain information illegally and then in turn sell it to the P.I. firm he was working for. And that's not the whole of it, he was up to his neck in hacking. The FBI isn't interested in prosecuting curious hackers. While I was working with them we passed up hundreds of potential cases. They were only interested in seriously criminal hackers. Mitnick was fully aware that what he was doing was illegal, and he knew they would fry him if he got caught again. Keep in mind he has been busted 4 TIMES! Frankly I think it's great that people support him, and yes I think the sentence they want to give him is ludicrous. But, put it into perspective, Mitnick is a criminal, he is not innocent, and there is no justification for his acts. If you want to admire and support him that is your decision, just do so understanding who he is and what he has done. Mitnick is not a saint."
--- November 24, 1998 posting by Agent Steal (Justin T. Petersen) on the "Free Kevin" mailing list. If you were to steal, and profit from, Evil Corley's personal identification - you'd never hear the end of it! He'd probably also want you in jail.
"As of now, Kevin's attorney hasn't retained an expert witness to help expedite Kevin's review of the encrypted evidence in his case (which the court said months ago that he can now view, but he still hasn't seen any of it)."
--- November 13, 1998 posting by Kerry McElwee on the "Free Kevin" mailing list. Apparently, Kevin Mitnick's legal team seems too stupid to understand modern computer technology.
"'The court wants to go to trial,' she told Mitnick and his attorney, echoing her previous statement that she was 'very, very anxious [to] try this case.'"
--- U.S. District Court Judge Mariana Pfaelzer expressed her disapproval with the request for a delay. All that whining in Freedom Downtime ($30) about trial delays was actually Mitnick's own fault. Gotta sell those T-shirts!
"No, man. They're like five bucks a pop now, and that extra two bucks cuts into my Smash the State fund. F*CK THE MAN, STEAL 2600!!!
2600 was officially dead when they pulled their 'VOTE NADER' bullshit in the last election, followed by raking the dirt over their own grave with the anti-second amendment stand they took a year or two after that. Yes, there may be aspects of politics that touch on aspects of hacking, but quite frankly it's not up to them to tell people how to think.
And apart from that... The quality of their articles is in the toilet. OMG, ANOTHER 'HOW TO F*CK WITH ____' ARTICLE!!! OMG, I'LL BE SO K-K-K-K-K-KEWL WHEN I BUST OUT OF THE DEMO SHELL ON THE COMPAQS IN BEST BUY & TYPE 'format c: /y' AT A COMMAND PROMPT!!! OMG, I'M A HIZAXOR!@!!caca!#@#~!"
--- Some hilarious comments about $2600 Magazine posted on the DEFCON forums by 'skroo.'
"Because it's three hours of self-aggrandising crap. That's pretty much all there is to know."
--- Comment about why Freedom Downtime ($30) sucks posted on the DEFCON forums by 'skroo.'
"[ No wonder they didn't show it at Defcon... ]"
"Actualy, we didn't show it at Defcon cuz Emmanuel is a big crybaby. He wanted it shown when we were showing 'Enemy of the State' and when we told him 'no, we're showing enemy of the state then, we'll show it tomorrow' he got all huffy and bailed.
Then when we went to show it the next day, we couldn't find it. Guess he took his football and went home.
But you didn't miss anything. I actualy really was looking forward to seeing it at ToorCon 2 years ago, but afterwards I can't figure out why. It's mainly 3 hours of Emmanuel and his self indulgant crap. Whoever made the wannabe 'Michael Moore' comment was spot on. I hadn't been able to put my finger on it, but you pegged it."
--- Comment about why Freedom Downtime ($30) sucks posted on the DEFCON forums by 'noid.'
"Besides Kevin taking credit for other peoples work on occasion, and his relentless self promotion, he had total dedication to his goals. Need to see if you are being investigated? Break into the telco office of the person doing the investigating and root through their file cabinet! Sometimes having no fear and taking big risks pays off and creates legends.
The Federal prosecutor, Christopher Painter, who prosecuted Kevin later went on to help draft the US Strategy for Cyber Space and working at the State Department on global policy issues. The stories he tells about that prosecution is pretty comical."
--- March 15, 2021 comment from Dark Tangent on Kevin Mitnick's book Ghost in the Wires.
"onfusion as to which fundraiser is still going on, a rundown of premiums, the length of time the show has been on the air, a hostage crisis at the '2600 Building' in Phoenix, a call for HOPE network volunteers to come to the 2600 meeting this Friday, the ease with which people fall into the security mentality, remembering when everyone in the room first got involved in the show, a 30 minute collage of some of the many highlights of 'Off The Hook' since 1988, the show won't be on next week, how listeners can participate in the program's future, the importance of young listeners. This show includes fundraising."
--- Description of Off The Hook on March 1, 2006. Gotta brainwash those young victims... err... "listeners."
"I am posting this anonymously, because I deal with several, 'high level' members of 2600 on a regular basis. I have found that these members, including Emmanuel Goldstein (aka Eric Corley) are a bunch of self important people, who think their opinion is always correct. I also, have not had one good experience with other members. Again, they refuse to believe they could ever be wrong, and speak in a condescending manner to all those not in the 2600 'clique'. Mod me down if you want, but this is a true synopsis of my experiences with the 2600 'hackers'."
--- Comment posted on Slashdot.org
"Agreed 100%. Most of the stuff in 2600 is crap, especially the political articles. If I want to read left wing propaganda I'd pick up the NY Times (or check politics.slashdot.org).
The articles in Phrack are a step above the few technical articles in 2600 these days."
--- Comment posted on Slashdot.org
"Being sued by the MPAA was the best thing that ever happened to 2600. They could finally take a little break from rehashing Mitnick folklore and retro infosec concepts ('OMG, some companies could still be vulnerable to wardialing!!11 here's a 1perl wardialer; HACK THE PLANET')."
--- Comment posted on Slashdot.org
"Right you are. I'm a life time subscriber, but with some of the content anymore - especially the letters - just pains me to read it. Once in a while there will be a good 'hacker'-worthy article. But most of the time it's 'how do I get around right-click suppression using Internet Explorer?' Please."
--- Comment posted on Slashdot.org
"I had to quit reading 2600 when, shortly after the DeCSS trial, Emmanual started abstracting himself out of all the stories, replacing all the 'I's with 'we's. He also quit signing his name to them.
Before, he wrote nearly all the stories. After that, it was all, 'We here at 2600...'. Yeah right. Maybe it's more professional, but to me, it took away all the personality and passion from the writing."
--- Comment posted on Slashdot.org
"I'm a journalist, and I can honestly tell you that almost any self respecting tech writer would gag if he found out that his prose had been published in 2600 (probably next to some bluetooth snarfing script)."
--- Comment posted on Slashdot.org
"Yeah, but 2600 has always sucked compared to Phrack. Calling it Phrack-lite would be an insult to Phrack."
--- Comment posted on Slashdot.org
"Anyone who's been a long time reader of 2600 can see that its dying a slow death... The quality of articles has declined significantly over the years with the letters section being the largest part of the mag now. I used to get it to learn now its just filled with letters with stupid questions from newbs fiction and articles that seem more like some kids report for a class they had in highschool then actual technical knowledge. It might have something to offer to people new to the scene but after a certain point you out grow it. Now when ever I pick it up I just keep thinking about how it used to be.. But who knows maybe the Slashdot effect will get it some much needed press and some actual tech articles again.."
--- Comment posted on Slashdot.org
"I worked for the company whose RT Programming Consultant owned the Well Account that led to your capture. Did you know anything about the account and its owner? Why/How did you choose it? Did you check the volume and type of traffic that was on the account before you decided to run tarballs through it? Would it have deterred you to know how well connected he was with some of the top networking and security professionals working in the Bay Area at the time? Were you surprised how quickly the FBI appeared at your motel while you were still downloading? Do your current security services customers know how sloppy you were when you were captured?"
...
"At last year's Defcon, you crashed the EFF Summit party, having waited until they were backed up at the door and very busy to force your way through the door and into the party. Shortly thereafter you were escorted out and you stuck around the front of the party where they had not the privileged to force you to vacate the area. Afterwards you engaged many involved in the charity event on twitter where you claimed to have been 'in' the party for over two hours, were called out and subsequently harassed those that did so. Initially you seemed to just block those that had negative things to say about you, but it quickly turned into you calling some at work and harassing them. My question for you; As a felon, do you sometimes worry that playing games with other hackers will get you into trouble?"
...
"'All he wanted to do was get into corporate sites, download code, play with the code and then move on to the next target.'
No, all he wanted to do was steal cellphone service and other services. Mitnick was not some grand hacker, he at that time was simply a petty thief that had skills that others did not. He was after the next big score or what would give him something for nothing. Why does everyone paint him to be some kind of leader for freedom and the Hacking Society. Most of us that were in the scene at that time and before did not have much respect for him. He is not the Hacker Poster boy. He was treated unfairly in the courts and legal system."
--- A few amusing comments and questions from the "Ask Kevin Mitnick" posting in August 2011 on Slashdot.
"... Because it appeared in the Associated Press, they have made it fact that he engaged in a multi-million dollar crime wave. When in actuality he's been indicted for things, that ahh... that no way can you say this is multi-million dollar, you know, copying a file - it just isn't. But you know... as long as they can say this in the Associated Press, people will start believing it."
--- Evil Corley on Off The Hook June 24, 1997. Interesting episode. Where does Corley get the money for his satellite/cable TV/HBO subscriptions? Also note he talks about "cracking" the satellite system.
"He's been in prison since February of 1995. That's a long time, for somebody who didn't steal anything, didn't hurt anybody, just basically played around with computers and phones. Which is very long time, and no end in sight."
--- Evil Corley on Off The Hook June 24, 1997. Didn't hurt anybody? Didn't steal anything? Haha!
"Thanks for the support. We also support the knowledge you were trying to get out before your site was shutdown. If enough people maintain pressure on the SPA and their tactics, they will wither away. It is their destiny."
--- Reply to a letter in $2600 Magazine Vol. 15, No. 1.
"... It's all selective enforcement spiked with greed, fear, and revenge. In other words, it's not a pretty place to be. But the outcome of this battle is going to be significant."
--- Reply to a letter in $2600 Magazine Vol. 20, No. 4 discussing software piracy.
"Think about what happens when someone tries this tactic on us. We wind up getting more support than ever before from people and places we never would have been in touch with ordinarily. By attempting this on others, you're opening up the same type of support for them. In other words, you'll be making them stronger. You should have the ability to counter hate speech with words and logic, rather than resorting to desperate measures. You need to be attacking the cause of the problem, not just the symptoms. The assumption that shutting down sites is what hackers are all about simply strengthens the inaccurate mass media perception of us. Any idiot can use brute force to try and shut someone up. Let's hope that we're all a few steps above that."
--- Reply to a letter in $2600 Magazine Vol. 22, No. 1.
"Keep up the good work and don't let those corporate giants try and bully you... The bigger they are the more they bitch... errr, harder they fall."
--- Letter from "RevZer0" in $2600 Magazine Vol. 18, No. 1. Thank you for your support.
"The thing is, 2600 has prided itself over the years as challenging authority. When someone threatens us with a lawsuit, we print the letter and that usually stops it, or we just continuing doing it anyway because there is nothing illegal about it, and we don't respond well to threats."
--- Evil Corley speaking at Beyond HOPE during the "$2600 Staff" panel. We didn't respond very well to that either.
"Why is it perfectly legal to post a diagram of how to build a bomb on the net, but you can't post a code that descrambles DVDs?"
--- March 3, 2001 edition of the cartoon Boondocks. Why can't you post scans of back issues of $2600 Magazine either?
"We are also lowering the price of our back issues. With every issue we stockpile, we lose more space so we'd really like to get rid of the damn things. You can now get back issues for $20 per year or $5 per issue from 1988 on."
--- Excerpt from an advertisement in $2600 Magazine Vol. 16, No. 4. If they take up so much space, why not just put them on the Internet? Oh... Wait... You need the money for your satellite TV, DSL, NAMBLA payments, etc.
"Since we are non-profit, it really doesn't matter to us if you Xerox your copy and send it to someone else - all we ask is that you let us know so that we can have a rough idea of how many people we're reaching."
--- Excerpt from the first editorial in $2600 Magazine Vol. 1, No. 1. Oh, a few thousand or so a month...
"Lets just hope this common sense approach becomes more of a standard."
--- Reply to a letter in $2600 Magazine Vol. 19, No. 4 about copying TV shows. They are just a little bit hypocritical!
"... But equating copying an image on a website with theft only minimizes what real thieves do."
--- Reply to a letter in $2600 Magazine Vol. 21, No. 3.
"Mr. Corley's nom de guerre is taken from George Orwell's 1984. Mr. Corley asserts that, like Orwell's fictional Goldstein, he is being persecuted for trying to expose Big Brother--here, for Big Brother's intrusion into the Internet. Incidently, Mr. Corley is the publisher of Hacker's Quarterly, an online magazine for computer hackers. While the title sounds ominous, Mr. Corley claims that the magazine's mission is to enhance the protection of confidential materials by exposing weak encryption methods before 'crackers' i.e., hackers with criminal intent) do something worse. As expounded in an CNN interview, Mr. Corley's view is that '[w]hile you may resent the fact that some 14-year-old from Topeka proved your security sucks, think of what could have happened had you not learned of this and had someone else done it instead.'"
--- Excerpt from the Ford-vs-2600 trial (Case No. 01-CV-71685-DT). Makes you wonder who the real "Big Brother" is, doesn't it? Note they mention the character "Goldstein" is fictional. Also note the Freudian slip of mentioning a teenage boy. Hmm....
"Finally there was also the time I got the [IRC] logs about Emmanuel and his involvement with some loser hack chick and her teenage boyfriend. Or, let me rephrase. Her aspirations for him and his aspirations for her boyfriend. Ahem. Making that motd was probably the only moral thing B1tchez.Org ever did."
--- Quote from B1tchez.Org.
"Most stations even that are live have folks that screen the calls and make sure you fit whatever point that the host wants to portray, be it agreement, or like the loony disagreement, or whatever it is that the host wants. That's what you hear. On WBAI we don't even really know how to do that..."
--- Excerpt from Off The Hook on March 1st, 2006. Oh, I think they know exactly how to do that.
"There are attacks going on left and right on freedom of speech. Right now it's taking place on computer hackers and other 'adventurers' who discover things that perhaps ... are best left undiscovered in the eyes of some."
--- Excerpt from Off The Hook on July 22, 1992. Oh, you better believe we discovered some things $2600 Magazine doesn't want uncovered!
"If you listen to the program you know what we mean. You know that knowledge is power and lot of people want to keep knowledge out of the hands of common people, like us. We're here to prove them wrong and also spread a little bit of that knowledge."
--- Excerpt from Off The Hook on August 5, 1992. What a bunch of hypocrites.
"The most important thing, though, is to get the information out."
--- Reply to a letter in $2600 Magazine Vol. 6, No. 3. No... The most important thing is to keep Evil Corley six-digit a year salary going.
/* ** Submission By: NYC2600 ** ** Like our great leader, this kernel module ** selects a child and touches him in a very special ** way. One of the best things about being a community ** leader is you can get away with depraved sexual acts ** with teenagers and no one will question it. ** */--- Funny quote from the Emmanuel Goldstein LKM article as featured in PHC's Phrack Magazine, Issue #62.
---------------------------------------------------------------------------- 1. Top Ten Reasons why..You shouldn't leave small children alone with Emmanuel Goldstein. ---------------------------------------------------------------------------- 10) He isn't down with the posse, although he think's he is 9) He seems a little too friendly 8) He likes little boys 7) His nick is jewish 6) so1o said so 5) He appeared on "The Learning Channel" inbetween when speedy and gonzolez showed you how to get free AOL and how to generate credit card numbers 4) He published an arcticle on how to steal (*gasp*) 3) He was an english major 2) Do you know how hard it is to get rid of head lice? 1) HE'S A FUCKIN CHILD MOLESTER YOU DUMB CUNT!@^&%$@%--- Funny quote from Confidence Remains High, Issue #8 (March 1998).
"Oh that's easy... Just don't goto HOPE, it's not like you'll miss anything important."
--- Funny comment from "HighWiz" on the DEFCON forums.
"i dunno if you were being sarcastic or not, but the '2600 conventions' and the people in them have very little to do with the 'hacking subculture'"
--- Quote from "masterkief" under the Reddit post Is the hacking subculture dying? LOL!
"If you really want to go down this road, consider that the U.S. is currently using something called the MOAB (Mother Of All Bombs) against Iraq. (It was tested earlier this year in Florida.) And if that's not biblical enough for you..."
--- Reply to a letter in $2600 Magazine Vol. 20, No. 1. The "MOAB" bomb was never used in Iraq.
"I recently was in New York City attending HOPE6, which is supposed to be a hackers conference. Quite honestly, I wasn't too impressed with the overall quality of the talks that went on. Sure a few good moments arose now and then, but ladies and gentlemen, the majority of it was nothing to write home about. I'm not saying I didn't have a good time. I'm just saying, the content of the speakers should have been leading-edge, or at least interesting. Topics like, 'hacking the metra swipe card' and 'hacking coupons' were just flat out lame. Perhaps next time I'll drink more and attend less of the speeches. :-)"
--- Quote from "login" in the newOrder Newsletter, Issue #14.
"... they really didn't have much of a choice ... it's the resonant frequency of a water molecule."
--- False comment at HOPE Number Six during the "Radio Communications for Hackers" panel discussing the frequency band that microwave ovens operate on. Uhh... No! The 2.45 GHz frequency microwave ovens operate on has nothing to do with "resonating water molecules," they operate via dielectric absorption.
"Actually, he has been seen doing the same things in public. People notice it at meetings, and warn other teenagers. A certain person named Hitman from NYC 2600 mention to someone to watch out for Emmanuel. The kid went back to Emmanuel and had Hitman banned from HOPE 6. I have always wonder where to of the teenagers that alway hung out with Emmanuel went. RedHackt and Mr.Ohm disappeared from the scene after being close friends with Emmanuel."
"Maybe he was taken into custody because he was molested by Emmanuel Goldstein who is a suspected Pedophile."
"What is wrong with you people? It's perfectly normal for a young boy to sleep in the same bed with a grown man."
"Probably just a ploy so that the Hope conference won't look so lame (as always) when compared to next week's Defcon conference"
--- Some very interesting comments on the "Steve Rambam" arrest at HOPE Number Six which were posted in the Washington Post blog.
"Suddenly pedophilia's relevant. I'll give this some context. All day friday and possibly all day saturday, (I can only vouch for friday) there seemed to be a team of legit journalists interviewing each panelist right after they got off the stage. Except they were using a huge VHS camera. And they weren't claiming to be a college class. yadda yadda. So anyhow it seems that each interview started out seeming quite legit but all of a sudden one of the lines of questioning became, 'do you have any evidence that Capn Crunch is a child molestor? How about Emmanuel, I hear he hangs out with young boys.' Then all of a sudden there are people all over here, all over the 2600.com irc chat, all over the slashdot threads spreading innuendo about Cap'n Crunch and Emmanuel."
--- Some comments about $2600 Magazine, HOPE, "Captain Crunch," Steve Rombom, etc. which are posted at http://jewishdefense.org/rombom/.
"Two reputed jewish Defense League members were arrested yesterday on charges of grabbing three teenage trick-or-treaters on a Brooklyn street, assaulting them with baseball bats and fists and imprisoning them in a car, police said.
Ronald Kahn, 30, of E. 17th St., and Steven Rombom, 24, of E. 18th St. were charged with unlawful imprisonment and assault after they were identified by the trick-or-treaters as two of their four assailants, police said. The other two are still being sought, police said.
The teenagers were grabbed by a group of men near Congregation Beth Torah Synagogue, 1060 Ocean Parkway, about 10:30 p.m. They were beaten and thrown from a car at E. Eighth St. and Avenue I, said police who took them to Kings County Hospital. They were treated there for scrapes and bruises.
Washington Cemetery, across the street from the synagogue has been a target of Halloween vandals in the past, according to area residents."
--- Excerpt from Tricksters Beaten; 2 Nabbed. The loony jewish supremacist, and domestic terrorist, Steve Rambam (a.k.a. Steve Rombom) is a regular guest at HOPE and on Off The Hook. There is more about this incident, and Rombom's other threats against people's lives, in the August 22, 1989 Village Voice article titled "Oy Vey, Make My Day."
"Well, the one I'm most proud of, I was named one of the 25 best investigators of the century by the - the last century, I guess, by the National Association of Investigative Specialists, which is 5,000 investigators."
--- Blatantly false quote from Steve Rambam (Steve Rombom) testifying to his credentials in a case before the Superior Court of California for the County of Los Angeles (BC154006). The NAIS doesn't even have 5,000 members and 22 of their "Top 25" are still alive! (Original)
"If [Steve] Rombom were tried and convicted as an adult, he would be subject technically, but not realistically, to a maximum term of imprisonment well over a hundred years."
--- Quote from the United States District Court, S. D. New York, 1976 discussing Steve Rombom's loony jewish supremacist and jewish Defense League domestic terrorist activities in the 1970s. (Original)
"There's Irv Rubin. He's like the head of the JDL [jewish Defense League]...
I tell Mitnick I found his childhood mentor, Irv Rubin, the head of the radical jewish Defense League in Los Angeles. 'Oh, from the JDL' Mitnick says, surprised. 'He doesn't know too much about me as a hacker - just as a normal person involved with them back when I was a kid. My stepfather at the time was heavy into that.'"
What kinda things would you do?
'Shooting,' Mitnick says.'
'I remember participating in the marches,' recalls the hacker. 'I knew the guy that actually bombed one of these air places and then he had to skip off to Israel.'"
--- Quote by Kevin Mitnick in Jonathan Littman's book The Fugitive Game. Note the "skip off to Israel" line. This is why the feds thought Mitnick was a flight risk. BTW, do you think as one of the "world's top 25" detectives, (((Steve Rombom))) will track down that bomber/terrorist who fled to Israel? LOL!
"Steven Rombom was a particularly tragic example of the sort of psychopaths [Meir] Kahane attracted to the JDL (jewish Defense League). The violence-prone youth, who, according to court records spent eight years in psychiatric institutions from the age of six, joined the JDL when he was twelve years old over the frantic objections of his doctors and social workers."
--- Quote from Robert I. Friedman discussing the mental state of Steve Rombom. A few years after emerging from his confinement, Steve Rombom and his loony JDL buddies went on a wave of domestic terrorist attacks within the United States. This is all documented by Robert I. Friedman in his book The False Prophet: Rabbi Meir Kahane, From FBI Informant to Knesset Member.
"<b>Eric Corley</b> is a child molestor and attention whore who exploits the computer [[hacker]] community to further his own interests, and goes by the name '[[Emmanuel Goldstein]]', after the leader of the underground in [[George Orwell]]'s classic, '[[Nineteen Eighty-Four]]'."
--- Some hacker hero edits the Eric Gordon Corley Wikipedia page - and it wasn't me!!!!
"In a crowded East Village restaurant called Mekka, Emmanuel Goldstein, 38, is quietly eating chicken wings at a table with nine raucous guys, most of them teen-agers."
--- Excerpt from the June 4, 1998 New York Times article New York Hackers See Breaking Into Computers as a Healthy Thing. Also note the various quotes in this article about "fighting pedophiles" on the Internet. This is actually just an excuse for Manny to have pictures of young naked boys on his computer.
"So let any little kids sit on your lap lately?"
"Ya know I hear child molestion is in vogue now. Care to comment?"
--- December 10, 1993 USENET reply from Chris Fisher to a "Captain Crunch" (John Draper) alt.2600 post.
"2600 is a good hacking/sec mag? Since when?"
"Come for the rehashed Abbie Hoffman derivative drivel, stay for Drapers' 'Energy Transfers'!"
"I can't believe no body has mentioned this: phrack is way better than 2600."
--- Selection of funny comments in a Reddit thread of people looking for hacker magazines.
"'You should try one of my body tune-ups,' says [John] Draper. 'It's a great energy boost.' Indeed, he spends a good deal of time at the conference enticing young attendees back to his hotel room, where he offers full-contact 'stretching' sessions."
--- Quote in Hello, My Name Isn't ... from "Captain Crunch" (John Draper) while at H2K. Some good info on Draper's activities in this Reddit thread.
"... he won't give his handle - spent over $3,000 on a loft in Chelsea, insurance and other expenses, with plans to stage a $25-a-head orgy. Instead, he says, 'the FBI investigated us; we were going to let some 17-year-olds come, so we were crossing a state line with the intent of having sex with a minor.'"
--- Another quote in Hello, My Name Isn't ... about the gay pedophiles at H2K.
"... twenty-some years later he showed up in the San Francisco rave scene, a wild-looking man with gray hair and majorly f*cked-up teeth as a result of his prison experience. He would stay up for days dancing and partying -- 'high on the energy', he said -- and trying to seduce young rave boys."
--- Old quote about regular HOPE attendee "Captain Crunch" on 666.com.
"And as for family values, they're just fine as long as they stay in the family and aren't forced down our throats. We're sure you see the unfairness of special interest groups."
--- Reply to a letter in $2600 Magazine Vol. 14, No. 4. These same hypocritical idiots are trying to force faggot rights down people's throats, along with their Marxist "we all are equal" nonsense so they can keep (((Democrats))) in power. They also have a radio program on a 50,000 watt RF radio station - in New York City & funded by billionaires - which only broadcasts their biased One Percent coverage of world events!
"Founded in 1960, the Committees for Defense of the Revolution (CDR) expanded over the next decade to include almost a third of the adult population. Immediately after Castro's endorsement of the crushing of the Prague Spring, the CDRs, acting on instructions from the DGI, arranged for a series of 'spontaneous' demonstrations to support his speech. Cuba thus developed a vast system of social control similar to, but more conspicuous than, those operated by the KGB and its European allies. By the late 1960s, Castro was using the CDRs to dictate even the length of men's hair and women's dresses. In November 1968 the parents of long-haired youths and miniskirted girls where summoned to appear before the local authorities. Castro had a particular dislike of homosexuals and instructed that they 'should not be allowed in positions where they are able to exert an influence on young people.' Gays were routinely refused tenancies in new housing projects and frequently singled out for service in forced-labour units."
--- Excerpt from The World Was Going Our Way - The KGB and the Battle for the Third World by Christopher Andrew and Vasili Mitrokhin. Haha! Evil Corley's hero, Fidel Castro, hates long-haired queers!
"In 1990, a gay Cuban who said he was abused by government officials in his homeland won asylum in the first significant ruling of its kind in the U.S. That ruling became the basis for then-Attorney General Janet Reno's 1994 order allowing gays from other countries to seek asylum for persecution based on sexual orientation."
--- Notice that in Evil Corley's pro-Castro rants, he never mentions that gay Cubans have to swim 90 miles north for freedom.
"A popular payphone kiosk in Havana. And that's not an ad for sneakers in the background."
--- Payphone picture in $2600 Magazine Vol. 18, No. 4. No, but it is government sponsored propaganda. It has to kill Evil Corley that after the Soviet Union fell, we learned that his little "Cuban Revolutionaries" were nothing more than puppets for Russian imperial expansion in Central and South America.
"Before joining Gist, David Ruderman designed software for web sites including Time, Money, Fortune, Entertainment Weekly. At Time Warner's Pathfinder site, he developed web applications for community building, text retrieval, and content management. He has developed electronic books for Times Mirror, and at Cold Spring Harbor Laboratory, Dave even worked on one of the first human-genome databases. In 1984, Dave co-founded the hacker zine 2600. He earned his Master Degree in Computer Science from the State University of New York at Stony Brook and holds a Bachelor Degree in Biology."
"Gist Communications is backed by Neptuno G.m.b.H., a subsidiary of Sal. Oppenheim Jr. & Compagnie, a private bank based in Cologne, Germany. Neptuno's initial investment was several million dollars."
--- September 16, 1996 quote in the New York Times about GIST Communications. David Ruderman, one of the co-founders of $2600 Magazine, is GIST's Vice President of Technology - and is really smart, and rich...
"[Jello] Biafra has spent large amounts of time and money on attorney fees and court costs. He continues to spend money on his appeal. Although he lives in a 1.1-million-dollar house in the hills of San Francisco, he is asking others for donations to pay for his appeal. The appeal will nevertheless reaffirm the court Judgment against him. These resources could be used to maintain his record label, Alternative Tentacles. But by continuing with his expensive, failing and misguided legal maneuvers, Alternative Tentacles may very well go under."
--- Quote about Eric Reed Boucher (Jello Biafra) from his fellow bandmates. Jello is a keynote feature at just about every HOPE conference. Baa... Baa... little sheep! You just paid $100 to watch a gay millionaire rock star tell you how to think!
"The effects are said to feel like being dipped in molten lava. This is incredibly scary stuff."
--- Excerpt from $2600 Magazine Vol. 23, No. 4 discussing the U.S. military's Active Denial System (ADS). At 95 GHz the wavelength is only 3 mm and the penetration depth is only about 1/10 of that due to dielectric absorption by the skin. Also, when it hits your eyes, it causes you to blink, and the "pain ray" is absorbed by your eyelids. A consumer microwave oven that doesn't shut off when the door is opened is actually more dangerous, as they operate with a higher duty cycle at 2.45 GHz. This frequency has a longer wavelength, which results in much deeper tissue penetration - YOU STUPID IDIOTS!
"...just knowing how strange 'zod's' [Shawn Perlman] parents were, I wouldn't be too sure who to believe. First of all, it's well known that his mom sort of thought that they were the 'Manson gang', 'coming to kill her and her family'. A normal assumption, no? Secondly, judging by the frequency at which 'zod' told the truth half the time, I wouldn't be so quick to believe. And lastly, Delaney arrested me in Jan 1991. No guns (certainly not shotguns), and I'm a bit bigger than 'zod'. Cuffs though, there were cuffs. And don't forget, the idea of shotguns to sustain a 14 year old naked kid sounded just scrumptious to the media.
Also, the majority of individuals in my home in December were from the FBI, not the SS (only a couple SS), and if you've ever been at the Marshall's office, it appears that they ARE in it for the glamor and glitz, at least some of them from their suits and slicked hair-cuts (and attitudes). And attitude was no stranger, one December morning..."
--- Mark Abene (Phiber Optik) posting on one of the MindVox forums, July 30, 1992. The discussion is about if shotguns were actually drawn during the infamous "hacker" raids during the early 1990s. Donald Delaney insists it didn't happen like you see in the movies. Funny, isn't it? Evil Corley always complains about the media's lies against hackers, but then he's the one who is out pushing the same lies in order to sell a few issues of his little magazine.
"Bahahaha, 'being screwed over by ignorance', that sounds like Phiber - listening to one to many of your speeches about this B.S. that you personally have nothing on the line for except your unaffected 6-digits a year salary is what got him in jail into he first place, along with 4 of his (former) friends who could've taken the deal the feds gave them of pleading early and doing no jail time had it not been for your grandiose BS which made him hold off and plead guilty like he would've done anyway though w/o time. Funny how such an advocate for the people whose issues sell more than Esquire magazine pays his teenage writers nothing and takes a photo of every attendee at HOPE, tying up the line to pay the $20+ entrance fee for hours. 'The photos were erased on a Hard Drive crash' - hah!"
--- November 27, 1994 USENET reply by the user "Presto" to one of Evil Corley's propaganda posts.
"Wow. Today was great. I started it off by going to the St. Patrick's Day parade this morning. It was pretty cool. Some of the marching bands were fairly impressive. Actually, all of them were impressive. It's just that some gave me a really creepy feeling. Like the high school with the rifle twirlers. Or the one with all the bagpipe players. Oh and the Junior ROTC is ... f'ed up. They have these 10 year olds marching around in friggin soldier uniforms. That's... just great."
--- Comment from the blog of RedHackt (Mark Tabry), one of Evil Corley's many "boytoys." Good example of the manufactured fear $2600 Magazine uses to scare their little following. Shouldn't your problem be with Emmanuel getting teenaged boys drunk at HOPE and sleeping with them? It's also fitting that "10 year olds" more know about our Constitutional rights than the mayor of New York City...
"Derp... I vote for the same (((people))) over and over and over and over and over and over again!
Fight the power!""Well, I'm at home in Eastchester, getting ready to vote in the early AM. Of course, I can rest easy in the fact that my vote doesn't really count for anything. If it did, Bush and Kerry would be making campaign stops in New York, not bum-f*ck swing states in the Midwest.
...
It's not that I don't like [John] Kerry, or want him to win New York, I just feel like my vote is being watered down by this whole electoral college system. It's abolishment is one amendment I'd like to see added to the Constitution, instead of the religious right mind-vomit that George Bush spews out. Maybe if Kerry wins, I'll write him a letter about it."
--- Another comment from the blog of RedHackt (Mark Tabry), one of Evil Corley's many "boy toys." The electoral college system allows all the states in the U.S. to have an equal say in presidential elections. It is actually a well thought out system, and is what prevents states like Wisconsin from becoming crime-ridden, third-world crapholes like New York. BTW, how are all those surveillance video cameras working out? If you want to talk about spewing "vomit," you may want to listen to a few episodes of Off The Hook. Also notice how it is always someone else's fault - a classic feature of the $2600 Magazine crew.
"If you can put it on a t-shirt, it's speech."
--- August 1, 2000 Slashdot posting about the DeCSS case. Does that also include IRC logs of Emmanuel chatting-up teenaged boys?
"We do not believe in cover-ups. By not printing that bit of ugliness, we would have been doing just that..."
--- Reply to a letter in $2600 Magazine Vol. 5, No. 3. Haha!
"You are, and always have been, a monument to free speech and the free transfer of information, Viva 2600!"
--- Letter from "Mobius" in $2600 Magazine Vol. 19, No. 3. Uhh... Buddy... What exactly have you been reading?
"The average citizen will accept almost anything if it will help to fight drugs or child pornography. And the control freaks will take almost anything they can get their hands on. Assume it's true and start figuring out how to subvert it now before it overtakes us."
--- Reply to a letter in $2600 Magazine Vol. 12, No. 4. The hypocrites at $2600 Magazine had to shut down the scrolling message banner at The Last HOPE because of all the "child molestation" references. Heehee...
"During the 802.11b panel the creator of Kismet had Kismet up on the projection screen. As he talked, SSIDs and IP addresses of all the wireless points showed up. People realized this and started changing their SSIDs to things such as 'Allyourbase", 'Emmanuel likes little children', 'What you say?' and so forth."
--- Quote from Jodath Morr about H2K2. Heehee... (Renderman's Netstumbler log from H2K2)
"Quit f*cking apologizing for filesharing. Intellectual property is evil, filesharing is freedom fighting, and the sooner Jack Valenti is bumming quarters for a living, the better. The question is not how to protect artists, it is how to muster enough force to protect the right to hack."
--- Nelson Denoon at H2K2. You can't make this shit up!
"I could care less if that child molesting moron approves or not, the site will stay up and if needed is mirrored on a few other sites if something should happen to this one."
"If it pisses Corley off too then all the better."
--- Quotes from "Tron" in a June 24, 2004 USENET posting on whether he had Evil Corley's permission to put back issues of $2600 Magazine online.
"As for eric corley, aka emmanuel goldstein, he the biggest peice of shit around, he turns idiots that get themselves caught like kevin and ed cummings, and turn them into martyers for the cause so he can milk it for all its worth on his web page and radio show, and sell his magazine and merchindise, hes nothing but a profiteer.
People who belive or are programmed by idiots like corley into thinking morons that get themselves caught like mitnick, or run a crap magazine that prints outdated articles are some sort of gods, when in reality there just fools."
--- Quotes from "Tron" in a July 7, 1998 USENET posting on Evil Corley's little charade.
"Goldstein is probably the best-known public representative of the hacker underground today, and certainly the best-hated. Police regard him as a Fagin, a corrupter of youth, and speak of him with untempered loathing. He is quite an accomplished gadfly."
--- Quote from Bruce Sterling's The Hacker Crackdown. No, I think the word you wanted to use was "faggot."
"... But copying music, programs, and magazine articles leads to greater exposure for the artists, developers, and writers. If your product is not priced out of the reach of your intended audience, it will be in their interest to get an original copy. But in many cases this is not so and the only way people can even get a glimpse of what is being developed is by making copies."
--- Reply to a letter in $2600 Magazine Vol. 13, No. 4. So... it's O.K. for $2600 Magazine to copy articles or BBS files from other people, but when it starts to effect Evil Corley's own income - it's bad!
"... like we had to play that song before and censor out every other word because the FCC would get upset if they heard those words, for some reason, and that's just the way they are. Instead of just regulating frequencies and technical specs, they regulate content, which I don't consider to be fair."
--- Excerpt from Off The Hook on July 23, 1996. No... the FCC does what the people write in and tell them to do. This is a perfect example of the sensationalism $2600 Magazine uses to scare their little kiddie followers. Now, try to get the words "Evil Corley is a pedophile" over WBAI's airwaves once!
"I wish... I wish they would spend as much time checking people out on the way in ... to airplanes, as they do on the way into the country. Everytime I come into the country, I get all this third degree stuff. I think it's more important for people getting on to things likes airplanes for them to know where they are coming from and what they are carrying with them. But they don't really seem to care that much."
--- Excerpt from Off The Hook on July 23, 1996. Yes, that is right. Evil Corley is calling for more airport security and screening! Notice how he flip-flops with his answers and ideas over the years to taylor his little kiddie following. Baa... Baa... little sheep. In the episode of Off The Hook on August 13, 1996 they also talk about the lack of good airport security and metal detectors.
"At some point, we flee after Joe630 demands 'hugs' from us...something he continues throughout the conference. 'Grrrrr...touch me not, boy...I will not submit to your fondling,' I tell him behind clenched teeth as I back out of the room. 'I'll only hug a man if he's buying me drinks or I'm trying to lift his wallet...'"
--- Article on HoHoCon '94 by Count Zero (John Lester) in Phrack Magazine, Issue #47 describing $2600's own Ben Sherman (Joe630).
"... Please keep your posts relevant to whichever area you're posting in. We're not going to tolerate abusive posts or threads that degenerate into personal attacks. Similarly, overtly racist, sexist, or homophobic posts aren't permitted. And, for obvious reasons, dissemination of illegal stuff (credit card numbers, unauthorized accounts/passwords) has no place here. Nor should private info on any unwilling person be posted."
--- Excerpt from the registration information at $2600 Magazine's new online message forums. Hehehe... This is not exactly something you'd expect from "freedom of speech" defenders. All this is, is censorship in disguise...
"It's preciously that kind of thing that I'm very weary about when people say that... ahh... information is property. It is to a degree, but if you treat it in exactly the same form, obviously there is going to be miscarriages of justice."
--- Excerpt from Off The Hook on December 11, 1991 talking about how "copying" a file is not really "stealing" a file. These very same hypocritical idiots will try to sue you for "copying" there little magazine!
"This has always been a frustration for us as well. Every now and then someone offers to help put together a comprehensive index of our material (letters included) and they almost always run away screaming when they realize just how massive such a project winds up being. We hope to have some sort of searchable index on our site before too long. For now, you can always go to the search button at our online store (store.2600.com) and search for topics there."
--- Reply to a letter in $2600 Magazine Vol. 23, No. 2. This webpage is all you'll need. Come on, print it!
"If we could snap our fingers and have this done, we would love it. But putting together an index with all the material we have would take an eternity."
--- Reply to a letter asking about a searchable $2600 Magazine subject index in Vol. 25, No. 3. No, no it won't!
"Check our web site (www.2600.com) for a full list of stores worldwide that carry 2600. If you don't have web access, write to us (2600, PO Box 752, Middle Island, NY 11953 USA), enclose $2, and we'll send you a full printout."
--- Excerpt from the editorial in $2600 Magazine Vol. 15, No. 1. Holy shit! They charge $2 for a printout of stores that carry this crap? No profiteering going on here...
"The numbers for the Nazi boards are 214XXXXXXX and 959XXXXXXX. If you would like a full printout of all the messages contained on these boards, send $5 to 2600, Box 752, Middle Island, NY 11953-0752."
--- Excerpt from the "Nazi BBS a Challenge To Hackers" article in $2600 Magazine Vol. 2, No. 2. $2600 Magazine would never think about selling someone's old BBS files. No profiteering going on here...
"If you'd like to see just how easy it really is, send us $7.50 and we'll send you a cassette with all of the codes! The address is 2600, PO Box 752, Middle Island, NY 11953."
--- Excerpt from the Simplex/USPS Update article in $2600 Magazine Vol. 8, No. 4. $2600 Magazine used to sell an audio cassette tape with all the Simplex lock codes on it. No profiteering going on here...
"Is Club-Mate suitable for vegans and vegetarians?
Yes. Club-Mate is completely vegan; no animal-derived products are contained in Club-Mate or used in its production."
--- Excerpt from the Club-Mate FAQ, the latest $2600 cash-cow. The entire planet Earth is made up of "products" derived from dead animals. Is Corley really this stupid? (Hacking Club-Mate: Page 1, Page 2, Additional Info)
"Regardless, we hope they stop trying to intimidate individuals who were merely expressing an opinion on a page that was asking for just that. As for our copy of the hacked web page - it's news. It's history. And it's staying. Praise The Web."
--- Excerpt from a letter in $2600 Magazine Vol. 15, No. 2 asking them to remove a web page from their site. Just a little bit hypocritical, aren't we?
"The film opens with scenes from HoHocon 1993 where hackers were being accused of trying to break into the hotel phone system by simply standing outside a door. We see an incredible number of security personnel and police converging on a hotel room, apparently unbothered by having it all captured on camera."
"On another front, some resourceful person had discovered that dialing extension 5199 connected you to the maintenance dialup port for the hotel's PBX system. The operator had to keep a watchful eye on her terminal all night to prevent anyone from logging in. Apparently she later gave some of the guys home-baked cookies to spread the word that she didn't care what anyone did as long as they stayed out of the innards of her telephone system.
--- Two quotes about HoHoCon '93. The top quote is from Evil Corley in a review of Annaliza Savage's film Unauthorized Access. Bottom quote is from the Nuts & Volts article Rising From The Underground by Damien Thorn. This is a perfect example of manufactured fear that Evil Corley likes to use to scare his kiddie following.
"Is it me or does anyone else notice that the magazine 2600 seem to have all kinds of highschool/jr high kids writting in too them going on with things that just seem juvenile. There is sometimes usefull information to be gained from reading the magazine. It just seems like some of the articles are written by those who know what they are talking about. I just cant shake this juvenile feel that I get from a lot of it though. Anyone else feel the same?"
--- USENET post from the user "Zaxil" on May 23, 2003. Yes, there is a very good reason why $2600 Magazine targets teenaged boys...
"So many articles were clearly written by people who did not know much, and who punt when they get to difficult work. 'The encryption is done by a custom chip and, uh, you might want to decompile the EEPROM and see what's in there.' Or they contain only trivial information, made to fill many pages through the inclusion of anecdotes about how the writer came to know the trivial information. (Four pages on how you discovered that ATMs run OS/2? The entire article could have been reduced to four words: 'Many ATMs run OS/2.') And then there are the political articles, most of which are screeds about how the government and/or big companies are coming to take your freedom away, and their desire to be paid for your pirated movies proves it."
--- Amazon quote from "Neurasthenic" in his review of The Best of $2600: A Hacker Odyssey
"On a slightly different tangent, does this not make you weep for the readers of 2600 a bit? It's like one moron making up stories and spreading them to a bunch of morons. There must've been at least a few people who read that article and went, 'huh?' I don't know, man. The whole revisionism angle bothers me as much if not more than the shitty journalism. I guess people are used to just walking on to forums or into chatrooms and spewing bullshit and hoping that enough people will just believe them. It also makes me really, really sad about the state of 2600. Are there really no hackers left?"
--- Comment from Rob O'hara about the "Where Have The Philez Gone?" article.
"But apparently doing more than writing a couple column inches that say nothing, and say it inaccurately, counts as useful information in 2600 these days."
--- Quote from Jason Scott's blog entry on May 7, 2007.
"I finished recently the latest issue of 2600. 2600 these days seems to be a mix of exegeses and lo-tech things that I could do given time and the particular piece of software in question. I want to read articles about hex editry and soldering and doing cool stuff with electronics, and not a bunch of 'And if you wanted, you could do this at an airport, and the only person who would see would be the security camera.'"
--- Blog quote from "aethercowboy" on July 25, 2007.
"For well over a decade 2600 had almost zero content produced inhouse aside from editorials. Techncial content was all reader submitted. When readers would write in and ask why an article on XYZ wasn't to be found anywhere, the response was always 'well, why don't you research, learn it, and then write one for us?'. I remember one issue had a semi-detailed article on how to use nmap, I think it was like 1.51. Of course, 2 months before the quarterly came out nmap had rev'd to 2.0 and the 1.x tree looked amateur in comparison. A quarterly print mag with nothing of value created in house... christ, it's like web 2.0 but 15 years sooner."
--- Comment about $2600 Magazine from "ajr" on Jason Scott's blog.
"Nowadays, I subscribe to 2600 just to read all the hilarious letters to the editor and all the bizarre personal ads. Yes yes yes, I still read the articles to better understand the hacker mindset ... but the letters section makes me wonder why the FBI fears hackers at all. Take out the national power grid? Bah. Many of 2600's readers can't even take out the garbage."
--- February 8, 2001 quote from Rob Rosenberger in Captive Experts and Gullible Hackers.
"Well, I don't know if you have seen the latest issue, and not to dis the zine, but it was really sparse. Pages were filled with how to pretend hack your high school, and the listings of AT&T offices, just to piss off AT&T. The Quarter schematic was poorly documented and the digram is an insult to anyone who can understand electronics rather than looking on the back of cerial boxes for cool new tricks."
--- December 10, 1993 USENET post from Levi Brown on the poor quality of $2600 Magazine articles.
"Speaking of 2600, they are the epitimy of everything wrong with the hacker scene. I will use the new spring 96 issue as an example. The cover shows some hakur stealing a payphone with the heading 'Our Nations Youth Run Amok, Corporations living in terror'. I am sure the corporations are so scared of Emmanuel Goldstein and his legions of 14 year old fags. 2600 is a Corporation, so all you dumbasses that read that shit are getting played. Emmanuel is getting rich off of the dumbass wannabe kiddies. He was also one of the technical consultants for that embarrasment 'hackers: the movie'. All that movie is doing is getting more crusty types to pretend to be hackers and buy his magazine. As usual, the editorial is a bitch about how Hackers who get caught shouldn't be punished. Hacking is a crime, i am sure emmanuel would be pissed off if someone took over 2600.com and trashed it. The guy f*cked up and got caught, quit f*cking whining about it. There is no f*cking 'Bureaucratic Corporate Regime' out there that is out to get all hackers."
--- Excellent rant discussing $2600 Magazine Vol. 13, No. 1 from "The Psycho Pyro" in Vaginal and Anal Secretions Newsletter, Issue #117.
"But seriously, emmanuel has been around forever(1984?), yet he still has never hacked ANYTHING. And for all those who didn't know, he was the genious technical advisor behind the greatest movie of all time: Hackers."
<mka> emmnauel bite me <emmanuel> mka- in your dreams--- Excerpt from a #2600 IRC log in Vaginal and Anal Secretions Newsletter, Issue #128.
"If i use a red box will the FBI, NSA and SS be after me? Will the people i call get in trouble? Will I get in trouble? --- TeenBoy"
"No, at the moment they can't if you have a special emmanual adapter. Just come over to my hottub at the mansion and i'll give you one. Bring a friend."
"Don't forget to call the 2600 voice bbs. 2600 voice bbs costs $3.99 per minute, $3.98 for each additional minute. If your under 18, you must have the permission of a parent, but call anyways."
"A one year subscription to 2600 mag will cost $160 for 4 issues. For a two year subscription, it will cost you $580. Now, you may be wondering why we are asking so much for a quartarly released magazine that is half the size of normal magazine with only 30 pages. A magazine that is photocopied in my basement. And you wonder why it costs so much. Well, i have to make all those payments for my pink Ferrari Limo, the lease on my huge New York mansion and my sex change operation. Yes, even though i act like i am unmaterialistic, I'm really very materialistic. I want your money."
--- Funny spoof of $2600 Magazine in Vaginal and Anal Secretions Newsletter, Issue #104. Heh.
"I've been waiting for almost 3 months now to get my 2600 black tshirt, and it still hasn't arrived. I've tried to contact Emmanuel through emmanuel@well, 2600@well, MANY times. I've also tried leaving endless messages on the answering machine, as well as talking to Emmanuel on IRC (who said he would get through to me by email). Is this normal? How can I get a VOICE line to 2600? (No stupid answering machines) And Emmanuel, if you're reading this I want you to contact me."
--- June 16, 1994 USENET post from Adam Frampton (LordOptic). The $2600 Magazine idiots often complain when other companies have voice mail systems, but they never answer their own damn phones!
"That may be because the elite assassin commandos at 2600 International Megacorp Ltd. have sought out and 'eliminated' everyone who has dared repost this 31337 article from a 1985 issue of 2600. But not me - I have eluded the 2600 intelligence forces for 13 years now and am still 12 steps ahead of them... "
--- August 14, 1998 USENET post from "The Fixer" (Gerald Albion) on why articles from $2600 Magazine are always hard to find on the Internet.
"It's not like they just threw his ass into solitary without reason. They were told by his significant other he could cause mass destruction just by whistling a key audio cue into a phone. Keep in mind that during the 1980's people viewed young men knowledgeable about computers the same way peasants might view a wizard of the Middle Ages, with appropriate fear and reverence.
Maybe if Suzy Thunder hadn't done such a wonderful job of stoking a fire he wouldn't have been in that state. And fleeing a trial is never justified, never. Not even by your soggiest wet cyberpunk 'sticking it to THE MAN' dreams."
--- Comment about Kevin Mitnick which was posted on Jason Scott's blog entry on June 12, 2006. It's widely known that Kevin's "little jail problem" came about when several southern California amateur radio operators were fed up with Kevin messing with their repeater systems. Hacker Rule #1: Don't mess with people smarter than you and their repeater systems...
"If he claims associations with any techie group, it's only because he wants that association to further his manipulative psychopathic abilities and desires. The amazing thing is, he can talk to a reporter about how he has used his powers of psychotic manipulation in the past, and he comes out sounding like an interesting guy. That in itself should tell you how manipulative he can be. He's not doing any good anywhere, he's simply gaming the system, whether it be the ham community, the phone company, a private company he dupes into giving its secret away, a reporter, or a bunch of rubes who visit a ham website."
--- June 27, 2009 quote about Kevin Mitnick on eHam.net from N3QE.
"The SE (social engineering) panel was pathetic, and I don't know why. Apparently 2600 would like its syncophants to worship Mitnick as a S.engineer now too. I wonder if he realised the true injustice in his case is being masked to make him 2600's media whore."
--- Comment from Shaughn Shea about the social engineering panel at H2K.
"The Sherman Antitrust Act applies to Microsoft customers just as much as it does (perhaps moreso, under the Bu$h anminstration) to Microsoft itself. And the Sherman Act prohibits unlawful exercise of Monopsony power (collusive exercise of market power among purchasers) just as much as it prohibits unlawful conduct by Monoploies and Oligopolies (individual sellers or collusive cartels)."
--- Comment from Eric Grimm (CyberBrief, PLC) the rich, clueless lawyer for $2600 Magazine and the EFF. He's one of the nutcases that actually thinks a software company can be a "monopoly." Hint: If you don't like the software, write your own. Don't cry about it on Slashdot, and sure as Hell don't pass any more laws just because you didn't take engineering or computer science classes school. You can also legally sue Eric Grimm under the Hacktivisomo License, as he current enables "human rights abuses" by aiding and abetting one of his clients, Emmanuel Goldstein, who is a known child molester.
"Tom Lee has been very active for many years in the Federalist Society -- an organization that is dedicated to packing the Federal bench with ideological 'conservatives.' Spencer Abraham (former Senator from Michigan) -- the sponsor of the Anticybersquatting Consumer Protection Act -- was one of the founding members of the Federalist Society, and made sure that Greg Phillips, Tom Lee's law partner, was invited to testify in favor of the ACPA. Ted Olsen (the guy who argued the Bush v. Gore case for Bush) is also a big Federalist Society member and booster. "
--- Comment from Eric Grimm (CyberBrief, PLC) the rich, clueless lawyer for $2600 Magazine and the EFF. Note how following the Constitution of the United States now makes you an "evil conservative." Very scary stuff.
"'I was brought up to ask questions,' he told me in an interview before the conference. 'This is all that hackers do. They just ask questions till they get an answer that's different. And I merely encourage that.'"
--- Excerpt from Hackers: Threat or Menace? Why is Evil Corley getting teenaged boys drunk at HOPE/NYC2600 and sleeping with them? Why won't his lawyers tell the police?
"After all, why would anyone want to pay close to $20 for a CD of their favorite band when they can get it for free over the net and when the actual artists only receive a small fraction of that amount anyway?"
--- Reply to a letter in $2600 Magazine Vol. 21, No. 1. Why would anyone want to pay
$6$7$8$9 for a shitty "hacker" magazine when they can get it for free over the net and the actual writers don't get paid at all?
"I think this has also brought out another very important issue which can now be pointed to with some authority, namely the suppression of news by the corporate media. We should not let this go."
--- Excerpt from a Evil Corley IMC-NYC posting (Mirror). Isn't your little corporation also suppressing a few "news" stories?
"i picked up a bunch of fairly powerful two-way radios at a hamfest. they're around five watts and their coverage area is at least a mile and they have no trouble penetrating buildings. i believe we have around 15 of them including chargers. we need to test them so we can see how many actually work and what their capacities are. there is a pile in the room with all the stuff in it (next to the bathroom). if anyone has time to go through this, please let me know. thanks"
--- Excerpt from a Evil Corley IMC-NYC posting (Mirror). Do you have a FCC license to operate on those frequencies? If operating in the MURS band, you can only have two watts RF power output. Remember, the airwaves belong to the public, not your little corporation.
"2600 was, in my opinion, irresponsible in printing something with a persons name on it, without making any attempt to contact me (I'm in many online directories, including nic & Compuserve). If they couldn't contact the author, the ethical thing to do is not publish. 2600 apparently couldn't resists such a 'juicy' tidbit though, whatever the cost to somebody else. As this was a titled document -- and obviously part of a series -- 2600 reasonably could deduce that somebody owned the thing and that permission should be obtained. At that time, presumption of copyright wasn't a legal doctrine (although now, thankfully, it is), however, 2600 should know that lack of a copyright notice doesn't mean that the notice wasn't illegally removed. Their claim to be able to publish the contents as a news item anyway is academic, as they published a photographic facimile of my work."
--- Excerpt from a July 23, 1992 post by Mel Beckman on the RISKS Digest Volume 13, Issue #68. This is a good example of $2600 Magazine taking someone else's property, and then printing and profiting from it. They could care less about the people, or their jobs, that it may effect.
"As I am sure most of you are aware, I am the author of the Motorola Bible - a technical manual dedicated to Motorola Cellular Phones. It is not authorized by Motorola and it is not welcomed in the industry due to cloning issues.
ANYWAY... 2600 magazine published it in the Spring 96 issue without my permission or even telling me they were publishing it. Like I said, they never told me of the printing. They won't return any of my letters in regards to the publishing. I have lost a VERY good paying job with one of the top communication companies in the world due to them printing my real name and Email address.
...
By comparing older issues with more current issues you will see the trend in lame articles on the rise because most self-respecting hacker would not publish the info in 2600 anymore. I mean cummon, the 'confessions of a beige boxer' was *REALLY* intriguing and has helped me a lot. (cough cough)"
--- Excerpt from a USENET posting by Mike Larsen on May 19, 1996. More proof that $2600 Magazine routinely publishes, and profits from, other people's work.
"I can't believe how many inaccuracies there were in this article. As a former cast member at WDW [Walt Disney World] I can tell you that the majority of 'facts' listed in the article were gross errors. You really should check your articles before they are printed. Not doing so hurts the reputation of your publication."
--- Letter from Michele Warner in $2600 Magazine Vol. 13, No. 1 discussing the large number of errors in one of their stupid "Hacking Disney" articles.
"While on vacation last week, I picked up the Summer 2003 issue of 2600 magazine from Barnes and Noble. In the issue is an article titled 'Optimum Online and You'. The article is peppered with inaccuracies, and is mostly a big complaint piece about OOL policies, from bitching about the 'You may be running a server from your computer and not even know it' email that OOL sent, complaints about port blocking, and the ever popular 'You pay for your allotted bandwidth and, as long as you don't uncap your modem, you should be allowed to do whatever you wish' argument. The OOL whiners will love the piece; for the rest of us, don't waste the $5.50."
--- August 25, 2003 post on the DSLReports Forums by the user 'Bichon.'
"9:00: typing class is over, and elite hax0r travels to his history class. No 'puters here, so, he strategically places his copy of 2600 inside his history book and memorizes the 'how to steal stuff' article."
--- Excerpt from a funny article on "A Day in the Life of a Leet Hax0r."
"'It was foolish of them to pick [2600],' Corley says. 'We've always stood up against this kind of thing. We don't know how to back down.'"
"He 'couldn't hack his way into a paper bag,' says one ex-hacker who, naturally, chooses to remain anonymous."
--- Excerpts from the Village Voice article Down By Law. We've also stood up to that kind of thing...
"But 2600 has never been a typical business. And one thing we don't want to do is screw over other people just because we got screwed over."
--- Quote from $2600 Magazine complaining that someone ripped them off from printing their little "hacker" magazine, which is filled with old BBS files they stole from other people. Think about that one!
"... I was able to track these numbers through my knowledge of the phone company, and then change the line class code to allow termination, which means those phones could then receive calls."
--- Misleading statement by Kevin Mitnick on Off The Hook June 6, 2007. Line Class Codes (LCC) are related to billing/AMA information and have nothing to do with the denied termination line option/feature. (ESS Information & DMS Information) This episode also has a number of other technical errors and a lot more misleading comments (note how they try to use a private conversation to debate public FCC rules). It's also funny how they say software theft is "worthless," yet they'll turn around and try to sue you for tens of thousands of dollars for "copying" their little magazine - which has a $6 price tag on it! Ever heard Craig Neidorf's E911 document story?
"personally i think the quality has dropped because they give a lifetime subscription for submitting an article, so any idiot with a computer who gets called a hacker because they know how to use their computer without a mouse sends in an article.
but 2600 wants it that way. they have to. otherwise they'd simply drop the stupid articles, the 'i did this, isnt it cool, gimme free stuff' garbage and only print the technical/informative articles."
--- 2600 LiveJournal posting by "amokk" discussing the low quality of articles in $2600 Magazine.
"Don't blindly follow your leaders. There's lots more to the 'war' against Afghanistan (formerly known as the war against terrorism) than you hear about from politicians. Wealthy white Christian men who own or are indentured to the military industry and big oil are making potentially disasterous decisions. Advocate peace and healing for the people of Afghanistan, understanding for peoples of all religions and ethinicities, and an end to hostilities in the middle east."
--- Excerpt from Greg Newby's website. And don't blindly follow clueless $2600/HOPE idiots, like yourself. Funny you don't mention is was the Muslim Arabs (after your hero's did - (((Communist))) Russians) who invaded Afghanistan, killing over one million innocent Afghanis who didn't stand a chance of fighting back. Did you idiots ever protest that? No? BTW, the Taliban kills homosexuals... Also, don't blindly follow wealthy, leftist child molesters who want to destroy Western civilization just so they can sell a few issues of their little "hacker" magazine. For your next computer science project, calculate the number of years Greg Newby will be in prison for helping Evil Corley sleep with drunk teenaged boys at HOPE. And, do you think this piece of shit will ever condemn the Soviet "military industry" and Chinese, Israeli, or Soviet "big oil?" Now, where does the plastic for those Freedom Downtime ($30) DVDs and VHS cassettes come from, you stupid idiot? Also, a lot of the (((people))) and war-mongers (Mirror) in the "military industry and big oil" are jewish Atheists or even Satanists, not "White Christians." And this clueless nutjob is a professor!
Greg Newby: "Shut up and pay your tuition!"
YOU are in debt because of YOUR student loans paying a person who literally thinks 2 ﬩ 2 = 5.































































































Still think Sen. Joseph McCarthy was wrong? LOL!
The Real Architects of the Iraq War
Benjamin Netanyahu on the Iraq War, 2002
Ex-Mideast Envoy Zinni Charges Neocons Pushed Iraq War to Benefit Israel
Bomb Iran to Stop a Wider War in Europe and Protect Taiwan (Mirror)
America Needs to Bomb Iran - Opinion (Mirror)
Microsoft, Mossad, and Misinformation: Whitney Webb Exposes Zionist Cyber Ops
Blood Money: The Top Ten Politicians Taking the Most Israel Lobby Cash
"Gradually, I began to hate them."
"The Party told you to reject the evidence of your eyes and ears. It was their final, most essential command."
"Military men are just dumb, stupid animals ... to be used as pawns in foreign policy."
--- Quote from (((Henry A. Kissinger))), former U.S. Secretary of State, as noted in The Final Days by Bob Woodward, p. 194-195. (Anna's Archive)
"They put the jewish interest above America's interest, and it's about goddamn time that the jew in America realizes he's an American first and a jew second."
--- Quote from Richard M. Nixon (1913-1994), 37th President of the United States. (Additional Info #1, Additional Info #2)
"We jews, we, the destroyers, will remain the destroyers for ever. Nothing that you do will meet our needs and demands. We will for ever destroy because we need a world of our own, a God-world, which it is not in your nature to build. Beyond all temporary alliances with this or that faction lies the ultimate split in nature and destiny, the enmity between the Game and God. But those of us who fail to understand that truth will always be found in alliance with your rebellious factions, until disillusionment comes. The wretched fate which scattered us through your midst has thrust this unwelcome role upon us."
--- Quote from (((Maurice Samuel))) in his book You Gentiles, p. 155. (Audiobook)
"Why should we, the only truly international people, be concerned with the mutable interests of stupid Goyim nations? ... Support the draft law when it is presented to the American people. ... We can repeat our triumphs of 1918 if we maintain our united front, and the dumb Goyim will fight while we profit."
--- Excerpts from a FBI investigation into the (((Anti-Defamation League of B'nai B'rith))) activities during the 1940s. (Source)
"Give us twenty years and we'll take over your media and destroy your country."
--- Comment made by an Israeli "employee" of (((Urban Moving Systems))), which closed down right after the 9/11 terrorist attacks and was found by the FBI to be front for Israel's foreign intelligence service(s).
"We have the senate, the congress, and a record strong jewish lobby on our side. We have a strong influence over the general support in America."
--- Quote from (((Benjamin Netanyahu))) in the 1980s discussing how Israel controls the United States. And he also said the goyim can not be trusted - while begging for the goyim's tax dollars and cannon fodder.
"There is a very apparent Semitic influence in the press. They are trying to do two things: first, implement Communism and second, see that all businessmen of German ancestry and non-jewish antecedents are thrown out of their jobs..."
--- Quote (Mirror #1, Mirror #2) from General George S. Patton (September 22, 1945)
"You know, the rules of perception. If they're Black, then it's a gang. If they're Italian, it's a mob. If they're jewish, it's a coincidence and you should never speak about it."
--- Quote from comedian Dave Chappelle during his monologue on Saturday Night Live, November 12, 2022.
"We recently attended a 2600 meeting in Dallas. We were suprised to see only small children who knew nothing of importance and had little discretion as to the purpose of the meeting. We propose a new meeting location in Lewisville, TX. This we hope will increase the local following and adult attendance, or at least those of us who are out of the seventh grade. We will anticipate a direction from you oh lords and masters."
--- Funny letter from "The Phrkman" and "Cybrthuug" in $2600 Magazine Vol. 14, No. 4. The main purpose of $2600 meetings is so their "staff" has a legitimate excuse to hang around young boys.
"And Mitnick kept calling, even sending electronic messages, telling his story, complaining about Markoff's portrayal of him in Cyberpunk and defending his hacking as the search for knowledge, not for material gain."
"Today he earns in the low six figures by advising executives on how to protect their companies from the current generation of ingenious but reckless geeks."
--- Top quote is from Kevin Mitnick complaining to Jonathan Littman that John Markoff's books and articles are not "accurate." Katie Hafner actually wrote the "Kevin: The Dark-Side Hacker" chapter in Cyberpunk, don't let the facts get in the way of your little charade... Bottom quote is from the Playboy article The Invisible Digital Man. Nothing like using manufactured fear, history revisionism, and blatant lies to help you pull in six figures a year.
"For what it's worth, [John] Markoff had no input on the book. The most he did was read the galley proofs. [Katie] Hafner is absolutely outraged by what is happening to Kevin. The Esquire article gives a good sense of that. And she does have a Free Kevin sticker on her car and might be a very useful ally in getting the word out."
--- November 10, 1998 posting by Douglas Thomas on the "Free Kevin" mailing list. Further information confirming that John Markoff had little to do with the Kevin Mitnick information in Cyberpunk, contrary to what $2600 Magazine and Kevin Mitnick may say. (Katie Hafner's "Kevin Mitnick, Unplugged" in Esquire.)
"Ironically, Hyperion's books are distributed by Little, Brown. However, says Hyperion publisher Bob Miller, the sales reps are 'playing it as a positive.' Indeed, the house accelerated publication of Takedown so as not to be overtaken by its rival."
--- Jonathan Littman's The Fugitive Game and Tsutomu Shimomura/John Markoff's Takedown are both distributed by the same company - Little, Brown and Company. Also, Kevin's new book deal telling his "official" story will be put out by, you guessed it, Little, Brown and Company. No profiteering going on here...
"He's a nice guy actually. However, on a professional level, I found his presentation rambling, far too anecdotal, and without much real substance on what should be done to prevent the sort of SE attacks he excelled at. Interestingly, while he has often been held up as a 'computer hacker' he is really nothing of the sort. His level of technical knowledge seems extremely limited, but he was a 'big name' draw to the conferences. :-)"
--- February 17, 2005 post by "AJ" at The Art of Noh describing a conference speech by $2600 Magazine's main cash cow, Kevin Mitnick.
"Does anyone have 800MHz modification data for the Radio Shack PRO-2032 desktop scanner? Please email me if you do. Thanks."
--- USENET post from Ed Cummings (Bernie S.) on July 1, 1997. The defenders of other people's "privacy" are modifying their RadioShack scanners so they can listen to analog cellular phone conversations. Just a little bit hypocritical, aren't we?
"I'm sure that most list members would appreciate your keeping your religious bigotry off the list, and your postings on-topic. Thank you."
--- August 9, 2010 posting from Ed Cummings (Bernie S.) on James Atkinson's own TSCM-L mailing list. This coming from a man who supports the ACLjU, EFF, SPLC, etc., some of the most bigoted, anti-Christian, anti-Gentile, anti-Germanic organizations in the U.S., and he's also a person who helped ban people from HOPE for exposing Evil Corley's little "secret." Note how Eddie acts like he is the list's moderator and enjoys telling other people how to think - a common trait with these types... Oh, and most of the postings to the "Free Kevin Mitnick" mailing list were also off-topic, but little Eddie didn't dare say anything then... Hmmm.... Lil' Eddie has habit of attacking Christians, as verifiable on several Off The Hook episodes. Hey! Isn't that also bigotry?
"Well...Kevin has been sitting in jail without a trial for 5 years. He was arrested for things he didn't do, and the man who caught him, Tsutomo Shimomora (forgive the spelling) deserved to be in jail just as much as him. I have been involved the the computer underground for some time and I am intelligent enough to realize that Kevin got screwed. He got a really bum deal. He was locked in solitary confinement for the stupidist reasons. They but him in solitary because they said he was going to make a bug out of a walkman, and bug the jail to listen in what the officers were saying. Well most intelligent people know that if you have a bug, you need a reciever! And also, how the hell would Kevin get a bug into the offices when he was behind bars? Think about this people, the feds screwed him."
--- Typical rant from a brain-dead "Free Kevin" $2600-reading nutjob.
"We beg to differ that information is similar to a gun. One is a specific weapon, the other is a virtually unlimited form of expression. One has finite possibilities and the other is infinite in scope. People who want to control information pose a far greater risk to a free society than those who want weapons to be handled responsibly. And most free societies passionately agree."
--- Excerpt from a letter in $2600 Magazine Vol. 18, No. 2. Hmm... According to this, $2600 Enterprises, Inc. is one of the biggest threats to a free society!
"nah someone :-) needs to get to nytimes.com and create a story about japboy that he is a convicted child molester and get it printed with markoff's by line."
--- February 10, 1995 talk session between Kevin Mitnick and the user "jsz" (Jonathan Zanderson). Hehe... No... I think a good story would be Kevin Mitnick's support for a certain other child molester!
"Hrm. Now that that mentally challenged sack of dribble AKA the great condor is back in the straight world I was wondering. What ever happened to Jonathan [Zanderson]? Seeing as he was the only publicly involved person with any actual skill, and it's 8 years after the fact.. I think it'd be nice for him to step forward and tell the real story of how Mitnick's fame is based on nothing more than hot air, and how pathetic it is that he's trying to milk said fame in today's infosec 'industry'. Are you still out there jsz?"
--- September 29, 2003 Full-Disclosure post by Mitch Hurrison about "jsz" and Kevin Mitnick.
"Markoff's most enduring [Kevin] Mitnick anecdote is the story that the hacker cracked NORAD in the early 1980s, a claim that was recycled as recently as last May by another New York Times reporter. 'I never even attempted to access their computer, let alone break into it,' Mitnick said. 'Nor did I do a host of allegations that he says I'm guilty of.'"
--- Quote from Kevin Mitnick in I Was Never a Malicious Person on July 30, 1999. $2600 Magazine reported that "Mitnick hacked NORAD" five years before it appeared in the New York Times.
"Steven Rhoades said he and [Kevin] Mitnick broke into a North American Air Defense Command computer in Colorado Springs, CO in 1979. The 1983 movie 'Wargames' is based upon a similar incident, in which a young hacker nearly starts World War III when he sends a message to a defense computer that is mistaken for a Soviet missile attack. But Rhoades said they did not interfere with any defense operations. 'We just got in, looked around and got out,' he said."
--- January 8, 1989 quote from John Johnson in his Los Angeles Times article. Since Steven Rhoades may have been a minor at the time, it looks like the article was edited when distributed. An "unedited" version is available in PLA #18. As you can see, John Markoff had nothing to do with creating this myth.
"Markoff falsely claimed that I had wiretapped the FBI (I hadn't); that I had broken into the computers at NORAD (which aren't even connected to any network on the outside);"
"I was able to do alot of [telephone] traffic analysis and actually identify the telephone numbers that belonged to the federal agents, and where they were at particular times. I was able to monitor their whereabouts when they were getting close to me."
--- Top quote from Kevin Mitnick in The Art of Deception - the "forbidden" chapter. You and your little butt-buddies did use telco metallic test systems to intercept FBI communications, you also listened into private FBI cellular phone conversations. And here we go again... $2600 Magazine reported that "Mitnick hacked NORAD" five years before it appeared in the New York Times. The bottom quote is from Kevin Mitnick on the June 6, 2007 episode of Off The Hook discussing his illegal monitoring of private cellular phone conversations (and uplink and call control data) belonging to active FBI agents. First he says he didn't monitor the FBI, now he admits it! And when it came time to sell one of his books, the "hacking NORAD" story was too good to pass up. No profiteering going on here...
"Kevin Mitnick (Technical Editor) is the most famous computer hacker in the world. Since his first arrest in 1981, at age 17, he has spent nearly half his adult life either in prison or as a fugitive. He has been the subject of three books and his alleged 1982 hack into NORAD inspired the movie War Games. Since his plea-bargain release in 2000, he says he has reformed and is devoting his talents to helping computer security."
--- Quote from "About the Author" on the book No Tech Hacking discussing Kevin Mitnick. Wait a second... Now Mitnick is using this "alleged NORAD hack" to help boost his book sales? No profiteering going on here! BTW, Tom Stockman's Air Force SAC story was the basis for the movie WarGames. (Amazon Screenshot)
"Kevin Mitnick is one of the most well-known black hat hackers. At one point, he was the most wanted cybercriminal in the world. He hacked into over forty major corporations, including Motorola and IBM, and even the US National Defense warning system. He was taken into custody and incarcerated in 1995. He became a cybersecurity consultant after his release in 2001, utilizing his hacking expertise for white hat hacking."
--- Wikipedia entry for "Black hat (computer security) which references Kevin Mitnick's alleged NORAD attack under the "Examples of famous black hats" section. Funny, no one is rushing to have it corrected... (Mirror)
"A few months later, Markoff and his cohort Tsutomu Shimomura would both participate as de facto government agents in my arrest, in violation of both federal law and journalistic ethics."
--- Quote from Kevin Mitnick in The Art of Deception - the "forbidden" chapter. Is Kevin really that stupid? The feds asked for public assistance to help capture Mitnick. They were required by law to help any law enforcement, and the (((New York Times))) never had an ounce of "journalistic ethics."
"'The truth of the matter is that I was never a malicious person. I admit I was mischievous, but not malicious in any sense.'"
--- Quote from Kevin Mitnick in I Was Never a Malicious Person on July 30, 1999. Uhh... Mitnick buddy... You steal the IDs of dead babies, charge others with your phones calls, hang around with a bunch of gay "hacker" child molesters I'm pretty sure that is seen as "malicious behavior."
"'What ended up happening is the movie came out in 1998 and I was able to get an attorney. I settled out of court for a large sum of money. Markoff is lucky, and Shimomura is lucky that there's a one year statute of limitations [on libel cases],' he explained. 'They exploited me to make millions of dollars.'"
--- Quote from Hackers: Under the Hood. No, you fat, stupid, con artist. You are the one out there scamming people via infomercials to make yourself "millions of dollars." You couldn't sue Markoff or Shimomura because those statements could then be used against you in your criminal trial (no 5th Amendment protection).
"As you probably already know, when I settled my case with the government back in 1999, I had to agree that I wouldn't profit from telling my story for seven years, and that was part of the deal with the federal government..."
--- Quote fron Kevin Mitnick on the July 27, 2011 episode of Off The Hook. This is a bit of a lie... The deal was any profit Kevin Mitnick made from telling his story would go to payback his victims. By waiting this long to tell his story, Kevin purposely avoided having to pay anyone back for the chaos and anger he caused.
"Both [Robert] Lemos and Mr. Markoff fail to note that Mr. Markoff provided no support whatsoever for his claim that I was anyone's 'most wanted.' Indeed, Mr. Markoff's empty and unsupported claim has been manipulated by media around the world into the specious claim that I was on the FBI's 10 Most Wanted List -- a claim that has been refuted by the FBI itself, according to Michael White of the Associated Press."
"... [Kevin Mitnick] was arguably the most wanted computer hacker in the world, he allegedly had access to corporate trade secrets worth millions of dollars. He was a very big threat"
--- Top quote is from a Kevin Mitnick press release asking John Markoff to provide his sources. The bottom quote is from Federal prosecutor Kent Walker in this John Markoff article.
"I could go on and on, even simple verifiable information. For example, on page 84, Katie describes a scenario where I asked Bonnie [Vitello] out on a date. To paint an unsavory picture, she stated that I was always eating in the computer room when talking with Bonnie."
"... He denies this and says that I was trying to 'paint an unsavory picture'. It was Bonnie who told us that he was always eating while he was talking -- we didn't make it up -- and without the ability to speak to him, we had to choose to go on."
--- Top quote is from a Kevin Mitnick article discussing Cyberpunk in $2600 Magazine Vol. 8, No. 2. The bottom quote is from Katie Hafner in this October 1, 1991 Newsbytes article. Who's lying?
"Again, when describing my arrest at USC in 1982, Katie wrote on page 71 that I taunted Mark Brown (USC System Manager) in his investigative techniques. This is truly amazing, since I never spoke with Mark Brown."
"The second example is his statement that we said that he taunted USC's Mark Brown when, in fact, he 'never spoke with Mark Brown'. Brown says that he has definitely spoken to Mitnick and that he remembers the calls well and can call to mind details from them. If we had spoken to Mitnick, he would have had a chance to dispute such statements."
--- Top quote is from a Kevin Mitnick article discussing Cyberpunk in $2600 Magazine Vol. 8, No. 2. The bottom quote is from Katie Hafner in this October 1, 1991 Newsbytes article. Who's lying?
"[ Investigators staked out a copy shop, but Mitnick got away... ]"
"Didn't the feds ever read Cyberpunk? They should have been waiting at FatBurger..."
--- July 20, 1994 USENET posting by Robert Zawarski.
"Cyberpunk was published in 1991 by Katie Hafner and then husband John Markoff, and it relied almost entirely on the words of people who Kevin had a falling out with. As well as those who didn't know him at all."
--- Evil Corley in Freedom Downtime ($30) discussing Cyberpunk. The main sources for this book where "Susan Thunder," (Susan Headley), "Roscoe," (Lewis De Payne), Lenny DiCicco, and Steven Rhoades. All these people knew Kevin Mitnick. Corley also shows a picture of Justin T. Petersen (Agent Steal) during this segment. Justin T. Petersen had nothing to do with making Cyberpunk. See below:
"Two of the main sources for Hafner and Markoff's account were 'Susan' and 'Roscoe,' two of Mitnick's fellow hackers who, as Hafner and Markoff write, 'cooperated with us in the understanding that their true names would not be revealed.' In a final touch of irony, they end the book with the line, 'We respect their right to privacy.' One of the two, Roscoe, would later claim that much of the information he provided to Hafner and Markoff was intended to deceive them."
--- Quote from The Making of a 'Darkside Hacker' by Douglas Thomas. All those "errors" in Cyberpunk were originally from Mitnick's little hacker buddies, Lewis De Payne (Roscoe) and Susan Headley!
"... there are other ISPs with a privacy problem. colorado supernet sniffed sessions (sniffed by mitnick) contain a number of customer social security numbers."
--- February 18, 1995 USENET posting by Vin McLellan with a reply from Mark Seiden on the "credit card" episode. Mark Seiden was on the team as a network/firewall expert while tracking Kevin Mitnick. If you think your Social Security Number may have been intercepted by Kevin Mitnick - call your lawyer now!!! Kevin Mitnick is worth millions. Sue the bastard!!!
"My conclusion is, until somebody shows me a single solitary shred of evidence, that this part of the affidavit is completely fabricated and bogus."
"you can try to pick this apart, bit by bit, but you'll find it futile. nobody's fabricating anything. really, evidence is not much of a problem in this case."
--- Top quote is from one of Evil Corley's February 19, 1995 alt.2600 USENET propaganda posts. The bottom quote is from Mark Seiden, calling out Corley's blatant, history-revisionist lies.
"`Yes, your honor,' he replied when asked to confirm that he wanted to waive bond consideration and a probable cause hearing. No plea was entered."
"Mitnick, 31, also said he didn't want bond set. For now, he will be housed in a jail somewhere in Eastern North Carolina -- wherever space is available."
--- Top quote is from a February 17, 1995 Associated Press news article. The bottom quote is from this article by Sarah Avery. No idea what any of this 'legal-speak' means, but it might have been Mitnick's own fault he was held without bond?
"And furthermore, nobody is accusing Kevin of using even a single one of those credit card numbers."
--- Reply to a letter in $2600 Magazine Vol. 14, No. 2. Credit card numbers were used by Netcom (and other ISPs) for customer verification during password changes. Mitnick was using several hacked Netcom accounts. This is NOT a coincidence! Kevin Mitnick finally admits to this on the February 8, 2000 episode of Off The Hook.
"OK, so I think Kevin Mitnick is a shmuck. I think he should probebly get some jail time. But he has RIGHTS! They are being stepped on. If they'll step on his rights, they'll step on yours next."
"I went to lunch with Emmanuel Goldstein of 2600 Magazine. Manny used his time at the conference to talk about the Free Kevin movement. Kevin Mitnick may be a schmuck, but what's happenning to him is criminal."
--- Comments from The Cheshire Catalyst (Robert Osband), former editor of the original TAP newsletter. Funny, you didn't hear that mentioned in Freedom Downtime ($30)!
"[Mitnick didn't] intentionally cause damage or harm to anything."
--- Reply to a letter in $2600 Magazine Vol. 21, No. 1.
"In one case, Mitnick allegedly gained access to a Bay Area man's records and used information in the file to try and change his health care provider so that he could benefit from the man's medical coverage. He also used the information to take on the identity of the man's dead son in order to obtain a phony driver's license."
--- Quote from a July 10, 1994 Los Angeles Times article.
"Kevin Mitnick did have a streak of revenge and he was seldom one-upped. And you're right, he would often pursue, at least electronically, people who occasionally one-upped him."
--- Quote from Jonathan Littman on the March 26, 1997 episode of NPR's Talk of the Nation. Jonathan Littman is often paraded around for "telling the truth" about the Kevin Mitnick saga.
"So they have a thing called a Social Security Death Index. But for infants, people that are one, two, three years of age when they die, there is no record ... that's created. So the key is, if you can find an infant that died in a different state than they where born in, you can become them, and that's what I did."
--- Kevin Mitnick interview with Kevin Rose from thebroken, Video Release 03. And Kevin Mitnick actually complains about being prosecuted...
"Oh yeah, yeah.. It was an invasion of privacy. Going and getting access to other people's information is obviously a gross invasion of privacy and it is wrong."
--- Kevin Mitnick interview on CBS' 60 Minutes. But... but... but... Evil Corley said Mitnick was innocent and that $2600 Magazine fights for other people's rights and privacy?
"Bravo. An unusually effective example of Internet governance taking down extremist and conspiracy theory platforms, while stamping out corrupt IPv4 address block allocation."
--- Scary 1984-esque comment from $2600 "author" and lawyer(!) Alexander J. Urbelis regarding the illegal censorship of the Parler platform during the January 6, 2021 Constitutionally-protected election integrity protests. We now know Parler had nothing to do with the protests, and it was only shut down by the (((Biden Administration))) in order to silence their political rivals (i.e., fascism). Do you think this corrupt, lying idiot will try to shut down Twitter or Facebook for propping up Biden's lies and support for "extremism and conspiracy theories?" Imagine the outrage if they tried shutting down Julian Assange and WikiLeaks.. Oh, needless to say, avoid Blackstone Law Group at all costs...
. .,-:+TmQ@@@@ /@@@@@@@@\ /@@@@@@@@\ /@@@@@@@@\ /@@@@@@@@\ @@@@QmT+:-,. . ..,-:+mTQ@@@@ @@@@@@@@@@ @@@@@@@@@@ @@@@@@@@@@ @@@@@@@@@@ @@@@QmT+:-,.. . .,-:+TmQ@@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@QmT+:-,. . ..,-:+mTQ@@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@QmT+:-,.. . .,-:+TmQ@@@@ /@@@/ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@QmT+:-,. . ..,-:+mTQ@@@@ /@@@/ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@QmT+:-,.. . .,-:+TmQ@@@@ /@@@/ @@@@@@@@@\ @@@@ @@@@ @@@@ @@@@ @@@@QmT+:-,. . ..,-:+mTQ@@@@ /@@@/ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@QmT+:-,.. . .,-:+TmQ@@@@ /@@@/ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@QmT+:-,. . ..,-:+mTQ@@@@ /@@@/ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@QmT+:-,.. . .,-:+TmQ@@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@ @@@@QmT+:-,. . ..,-:+mTQ@@@@ @@@@@@@@@@ @@@@@@@@@@ @@@@@@@@@@ @@@@@@@@@@ @@@@QmT+:-,.. . .,-:+TmQ@@@@ @@@@@@@@@@ \@@@@@@@@/ \@@@@@@@@/ \@@@@@@@@/ @@@@QmT+:-,. . |
Knowledge is Power